Introduction to cyber PowerPoint Presentation Templates and Google Slides
-
Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Company Introduction PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by ABS healthcare company introduction pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like restrict data accessibility, programs and firewall softwares, security management, techniques and provide. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
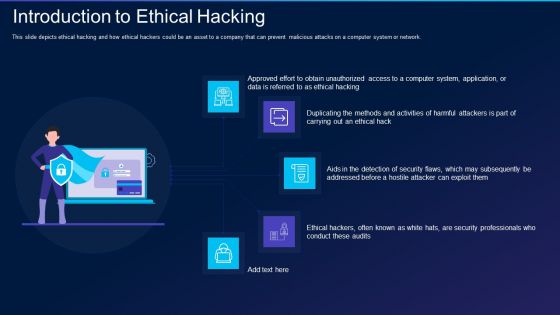
Cyber Exploitation IT Introduction To Ethical Hacking Introduction PDF
This slide depicts ethical hacking and how ethical hackers could be an asset to a company that can prevent malicious attacks on a computer system or network. This is a cyber exploitation it introduction to ethical hacking introduction pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like introduction to ethical hacking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Cyberspace Simulation Platform Fundraising Elevator An Introduction To Our Product Solution Icons PDF
The following slide displays the introduction about the product as it provides highlight of the VR by depicting the product segments such as HMD GTD and PDW along with key USP of the organization. Deliver an awe inspiring pitch with this creative cyberspace simulation platform fundraising elevator an introduction to our product solution icons pdf bundle. Topics like an introduction to our product solution can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Introduction PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring introduction pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
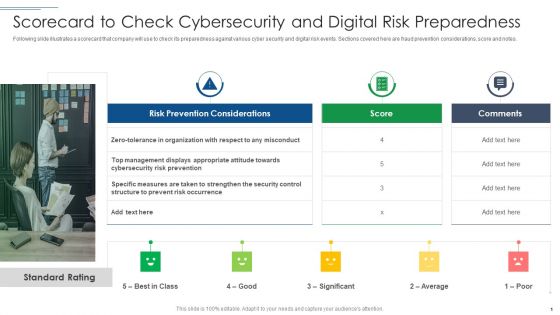
IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. This is a IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Specific Measures, Security Control, Cybersecurity Risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
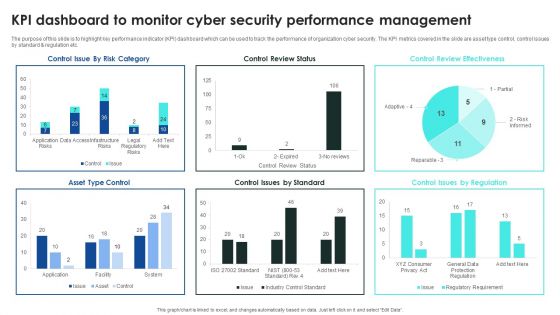
Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. This Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
-
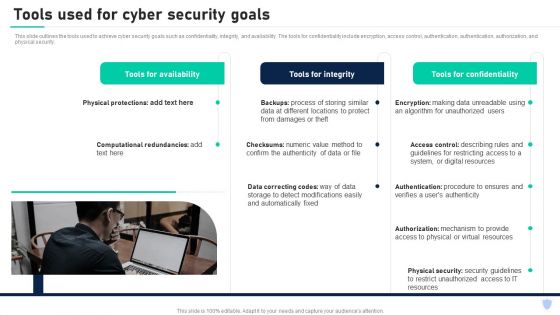
Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF
This slide outlines the tools used to achieve cyber security goals such as confidentiality, integrity, and availability. The tools for confidentiality include encryption, access control, authentication, authentication, authorization, and physical security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
-
Cyber Physical System To Enhance Cyber Physical Systems Architecture Physical Layer Introduction PDF
This slide represents the physical layer of cyber-physical system architecture, including the devices used at this level, such as sensor units and actuator units and their tasks. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Cyber Physical System To Enhance Cyber Physical Systems Architecture Physical Layer Introduction PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
-
Cyber Physical System To Enhance Pricing For Cyber Physical Systems Development Introduction PDF
This slide describes the pricing for cyber-physical systems development, including the price for the project, project size, and provided assistance. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cyber Physical System To Enhance Pricing For Cyber Physical Systems Development Introduction PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cyber Physical System To Enhance Pricing For Cyber Physical Systems Development Introduction PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
-
Cybersecurity Guidelines IT Introduction To Information Technology Policy Icons PDF
This slide represents the introduction to information technology policy, and it also describes the components of IT policy, such as investments, business applications, architecture, and infrastructure. The Cybersecurity Guidelines IT Introduction To Information Technology Policy Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
-
Icons Slide For Cyber Physical System To Enhance Introduction PDF
Download our innovative and attention grabbing Icons Slide For Cyber Physical System To Enhance Introduction PDF template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.
-
WAF Introduction Types Of Cyberattacks WAF Is Designed To Stop Ideas PDF
This slide represents the key cyberattacks that a WAF is designed to stop. It includes ddos attacks, zero-day threats, cross-site scripting XSS, cookie poisoning, web scrapping, parameter tampering, and SQL injection. The WAF Introduction Types Of Cyberattacks WAF Is Designed To Stop Ideas PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
-
Introduction To Cybernetics System With Its Related Field Cybernetic Integration Diagrams Pdf
This slide provides an overview of cybernetics and related fields. The purpose of this slide is to give an outline of cybernetics, as well as of its model and closely related areas. Want to ace your presentation in front of a live audience Our Introduction To Cybernetics System With Its Related Field Cybernetic Integration Diagrams Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
-
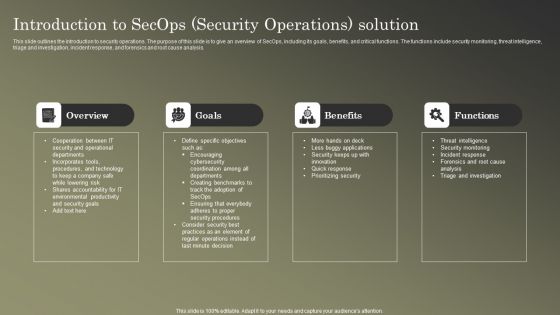
Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF
This slide outlines the introduction to security operations. The purpose of this slide is to give an overview of SecOps, including its goals, benefits, and critical functions. The functions include security monitoring, threat intelligence, triage and investigation, incident response, and forensics and root cause analysis. Want to ace your presentation in front of a live audience Our Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
-
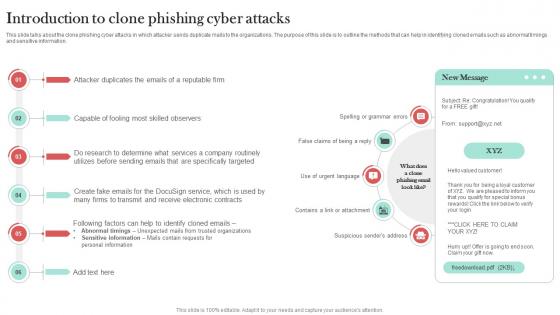
Introduction To Clone Phishing Cyber Man In The Middle Phishing IT
This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information. This Introduction To Clone Phishing Cyber Man In The Middle Phishing IT from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
-
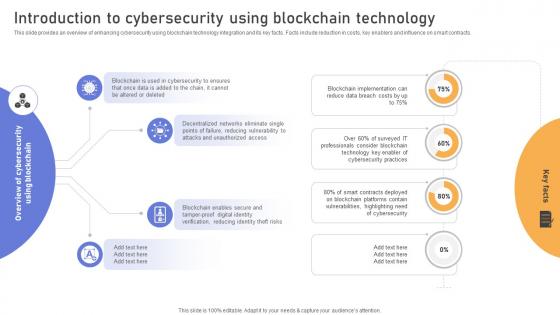
Comprehensive Look At Blockchain Introduction To Cybersecurity Using Blockchain BCT SS V
This slide provides an overview of enhancing cybersecurity using blockchain technology integration and its key facts. Facts include reduction in costs, key enablers and influence on smart contracts. Retrieve professionally designed Comprehensive Look At Blockchain Introduction To Cybersecurity Using Blockchain BCT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
-
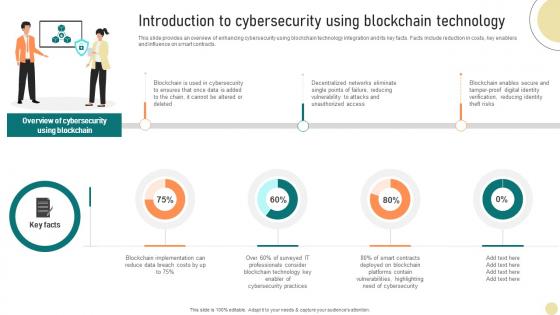
Visionary Guide To Blockchain Introduction To Cybersecurity Using Blockchain BCT SS V
This slide provides an overview of enhancing cybersecurity using blockchain technology integration and its key facts. Facts include reduction in costs, key enablers and influence on smart contracts. Slidegeeks has constructed Visionary Guide To Blockchain Introduction To Cybersecurity Using Blockchain BCT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.