Identify threats PowerPoint Presentation Templates and Google Slides
-
Identify Critical Threats Powerpoint Slides Background Designs
This is a identify critical threats powerpoint slides background designs. This is a five stage process. The stages in this time process are define initial team, complete situation analysis, identify critical threats, plan actions and monitoring, define scope vision targets.
-
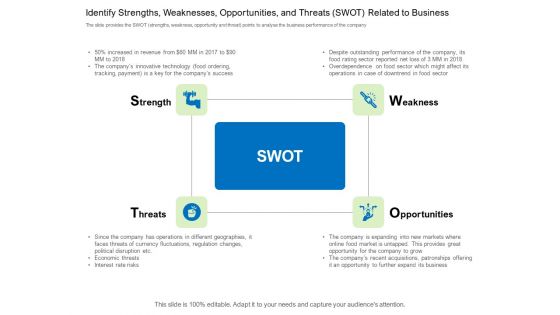
Crowd Sourced Equity Funding Pitch Deck Identify Strengths Weaknesses Opportunities And Threats SWOT Related To Business Rules PDF
The slide provides the SWOT strengths, weakness, opportunity and threat points to analyse the business performance of the company. Presenting crowd sourced equity funding pitch deck identify strengths weaknesses opportunities and threats swot related to business rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like strength, opportunity, weakness, threat. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Equity Crowdfunding Pitch Deck Identify Strengths Weaknesses Opportunities And Threats SWOT Related To Business Icons PDF
The slide provides the SWOT strengths, weakness, opportunity and threat points to analyse the business performance of the company. Presenting equity crowdfunding pitch deck identify strengths weaknesses opportunities and threats swot related to business icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like strength, opportunity, weakness, threat. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Option Pool Funding Pitch Deck Identify Strengths Weaknesses Opportunities And Threats SWOT Related To Business Portrait PDF
The slide provides the SWOT strengths, weakness, opportunity and threat points to analyse the business performance of the company. Presenting option pool funding pitch deck identify strengths weaknesses opportunities and threats swot related to business portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like strength, opportunity, weakness, threat. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Substitute Financing Pitch Deck Identify Strengths Weaknesses Opportunities And Threats SWOT Related To Business Formats PDF
The slide provides the SWOT strengths, weakness, opportunity and threat points to analyse the business performance of the company. This is a substitute financing pitch deck identify strengths weaknesses opportunities and threats swot related to business formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strength, weakness, threat, opportunity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Collective Equity Funding Pitch Deck Identify Strengths Weaknesses Opportunities And Threats SWOT Related To Business Inspiration PDF
The slide provides the SWOT strengths, weakness, opportunity and threat points to analyse the business performance of the company. This is a collective equity funding pitch deck identify strengths weaknesses opportunities and threats swot related to business inspiration pdf. template with various stages. Four and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like opportunities, strength, tracking, success, opportunity, business, patronships, market, geographies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
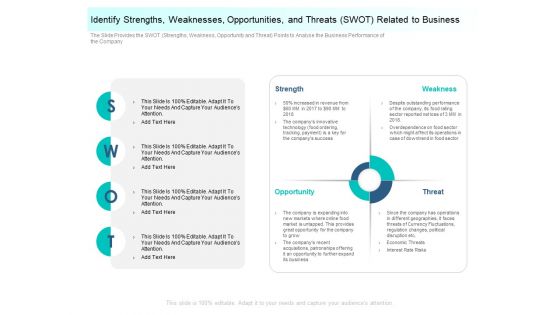
Identify Strengths Weaknesses Opportunities And Threats SWOT Related To Business Introduction PDF
The slide provides the SWOT strengths, weakness, opportunity and threat points to analyse the business performance of the company. Presenting identify strengths weaknesses opportunities and threats SWOT related to business introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like identify strengths, weaknesses, opportunities, threats SWOT related to business. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Community Capitalization Pitch Deck Identify Strengths Weaknesses Opportunities And Threats Swot Related To Business Professional Pdf
The Slide Provides the SWOT Strengths, Weakness, Opportunity and Threat Points to Analyse the Business Performance of the Company. Deliver an awe inspiring pitch with this creative community capitalization pitch deck identify strengths weaknesses opportunities and threats swot related to business professional pdf bundle. Topics like strength, weakness, opportunity, threat, company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Issue Log In Project Management Icon To Identify Project Threats Ppt PowerPoint Presentation File Layout Ideas PDF
Presenting issue log in project management icon to identify project threats ppt powerpoint presentation file layout ideas pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including issue log in project management icon to identify project threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
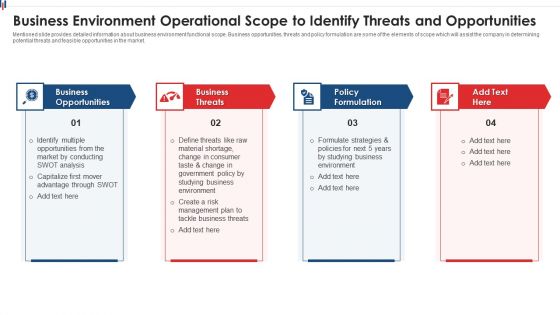
Business Environment Operational Scope To Identify Threats And Opportunities Clipart PDF
Mentioned slide provides detailed information about business environment functional scope. Business opportunities, threats and policy formulation are some of the elements of scope which will assist the company in determining potential threats and feasible opportunities in the market. Presenting business environment operational scope to identify threats and opportunities clipart pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including business opportunities, business threats, policy formulation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Handling Cyber Threats Digital Era Criticality Assessment Of Identified Assets Ppt Slides Backgrounds PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. This is a handling cyber threats digital era criticality assessment of identified assets ppt slides backgrounds pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like extremely critical, reasonably critical, least critical. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
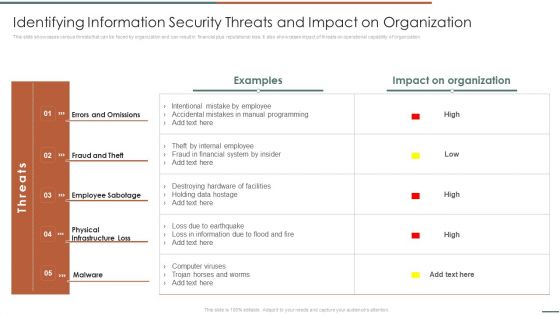
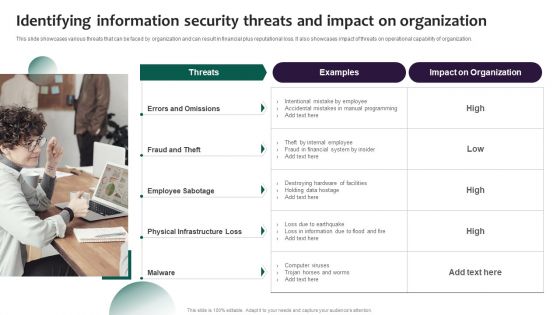
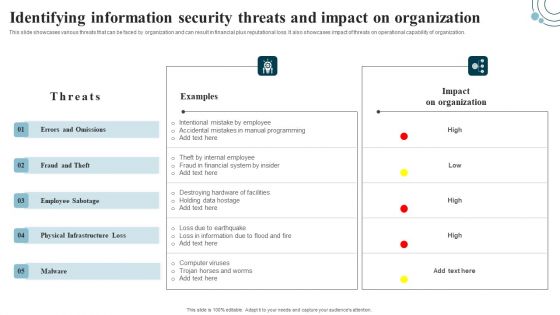
Information Security Risk Evaluation Identifying Information Security Threats And Impact On Organization Sample PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Identifying Information Security Threats And Impact On Organization Sample PDF bundle. Topics like Errors And Omissions, Fraud And Theft, Employee Sabotage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Fraud Reporting Process For Identified Risk Event Fraud Threat Administration Guide Summary PDF
Mentioned slide depicts a risk reporting and management process that the company is currently using to effectively handle any fraud event.Deliver an awe inspiring pitch with this creative Fraud Reporting Process For Identified Risk Event Fraud Threat Administration Guide Summary PDF bundle. Topics like Employee Suspected, Human Resource, Financial Director can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
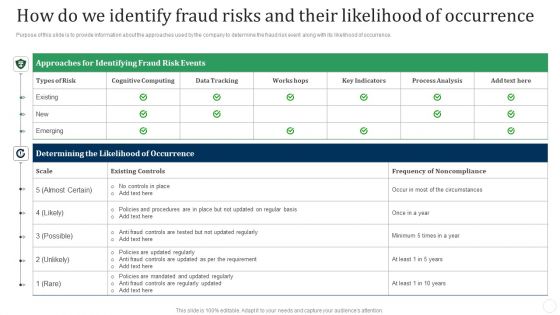
How Do We Identify Fraud Risks And Their Likelihood Of Occurrence Fraud Threat Administration Guide Download PDF
Purpose of this slide is to provide information about the approaches used by the company to determine the fraud risk event along with its likelihood of occurrence.Deliver an awe inspiring pitch with this creative How Do We Identify Fraud Risks And Their Likelihood Of Occurrence Fraud Threat Administration Guide Download PDF bundle. Topics like Approaches Identifying, Fraud Risk, Existing Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Identifying The Ways In Which Fraudster Targets Our Business Fraud Threat Administration Guide Topics PDF
This slide depicts various methods by which a fraudster can target the companys business. WIFI hacking, business email compromise, and ransomware are the methods covered in the slide.This is a Identifying The Ways In Which Fraudster Targets Our Business Fraud Threat Administration Guide Topics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Business Compromise, Ransomware, Malicious Software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Use Case Fraud Risk Identified And Measures Taken Fraud Threat Administration Guide Icons PDF
Following slide depicts a use case for a fraud risk profile. It contains information about the identified risk as well as the organizations efforts to mitigate it.This is a Use Case Fraud Risk Identified And Measures Taken Fraud Threat Administration Guide Icons PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risk Significance, Residual Risk, False Identity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Identifying Employees For Potential Insider Threat Icon Portrait PDF
Presenting Identifying Employees For Potential Insider Threat Icon Portrait PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Identifying Employees, Potential Insider, Threat Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
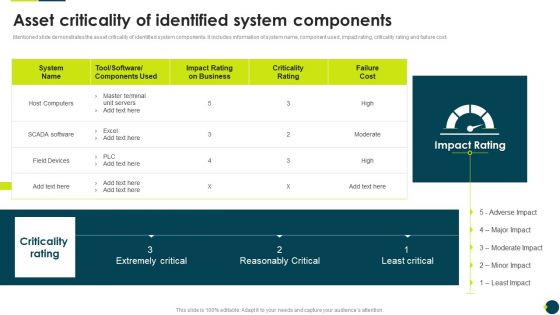
IT Threats Response Playbook Asset Criticality Of Identified System Components Themes PDF
Mentioned slide demonstrates the asset criticality of identified system components. It includes information of system name, component used, impact rating, criticality rating and failure cost.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Asset Criticality Of Identified System Components Themes PDF. Use them to share invaluable insights on Master Terminal, Extremely Critical, Reasonably Critical and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
IT Threats Response Playbook Identifying The Origin And Type Of Cyber Incident Rules PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack.This is a IT Threats Response Playbook Identifying The Origin And Type Of Cyber Incident Rules PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like External Removable, Malicious Attachment, Loss Valuable. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
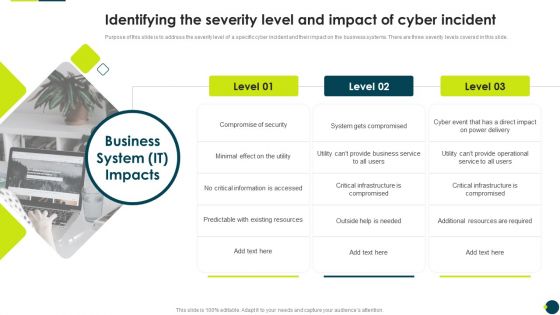
IT Threats Response Playbook Identifying The Severity Level And Impact Of Cyber Incident Portrait PDF
Purpose of this slide is to address the severity level of a specific cyber incident and their impact on the business systems. There are three severity levels covered in this slide.Presenting IT Threats Response Playbook Identifying The Severity Level And Impact Of Cyber Incident Portrait PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Compromise Security, Information Accessed, Existing Resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Identifying Information Security Threats And Impact On Organization Information Security Risk Administration Icons PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization.If you are looking for a format to display your unique thoughts, then the professionally designed Identifying Information Security Threats And Impact On Organization Information Security Risk Administration Icons PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Identifying Information Security Threats And Impact On Organization Information Security Risk Administration Icons PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
-
Identifying Information Security Threats And Impact On Organization Cybersecurity Risk Assessment Formats PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Identifying Information Security Threats And Impact On Organization Cybersecurity Risk Assessment Formats PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Identifying Information Security Threats And Impact On Organization Cybersecurity Risk Assessment Formats PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
-
Online Security Assessment Tools Used To Identify Security Threats Slides PDF
This slide showcases digital safety assessment tools used to safeguard vulnerable operations systems in the organization. It provides information regarding protocol scanner, web application scanner, network scanner and attack simulation tool. Persuade your audience using this Online Security Assessment Tools Used To Identify Security Threats Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Network Scanners, Attack Simulation Tool, Web Application Scanner. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Information Systems Security And Risk Management Plan Identifying Information Security Threats And Impact On Organization Topics PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. Want to ace your presentation in front of a live audience Our Information Systems Security And Risk Management Plan Identifying Information Security Threats And Impact On Organization Topics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
-
Identify Threat And Vulnerabilities Within Information System Ppt PowerPoint Presentation File Example PDF
The following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Are you searching for a Identify Threat And Vulnerabilities Within Information System Ppt PowerPoint Presentation File Example PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Identify Threat And Vulnerabilities Within Information System Ppt PowerPoint Presentation File Example PDF from Slidegeeks today.
-
Key Phase Of Crisis Communication Management Plan Stage 1 Pre Crisis Analysis For Identifying Potential Threats Mockup PDF
The slide illustrates the steps involved in pre-crisis stage to minimize the potential threats. Various steps included are crisis anticipation, crisis communication team, selection and training of spokesperson, etc Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Key Phase Of Crisis Communication Management Plan Stage 1 Pre Crisis Analysis For Identifying Potential Threats Mockup PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
-
Developing IT Security Strategy Identifying Information Security Threats And Impact On Download PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. There are so many reasons you need a Developing IT Security Strategy Identifying Information Security Threats And Impact On Download PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
-
Online Risk And Threat Identifying Icon Ideas PDF
Presenting Online Risk And Threat Identifying Icon Ideas PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Online Risk, Threat Identifying Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.