Formation security PowerPoint Presentation Templates and Google Slides
-
Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF
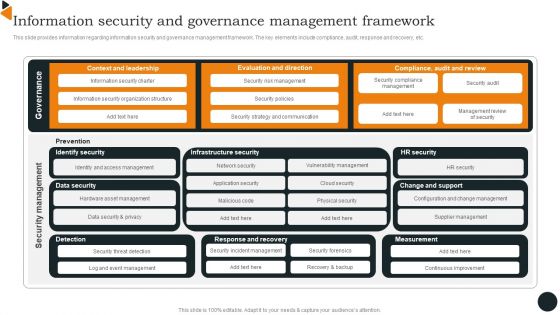
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
-
Software Defined Networking And Security Ppt Slides File Formats PDF
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and ddos. It also includes security components for SDN such as infrastructure, controller, API, and application security. Slidegeeks is here to make your presentations a breeze with Software Defined Networking And Security Ppt Slides File Formats PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
-
Cyber Security Incident Communication Strategy Formats PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. This modern and well arranged Cyber Security Incident Communication Strategy Formats PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
-
Cyber Security Systems Monitoring Report Formats PDF
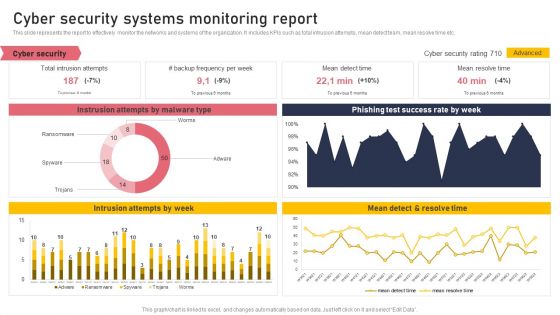
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Boost your pitch with our creative Cyber Security Systems Monitoring Report Formats PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
-
User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. If you are looking for a format to display your unique thoughts, then the professionally designed User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
-
Table Of Contents For Cyber Security Breache Response Strategy Formats PDF
Want to ace your presentation in front of a live audience Our Table Of Contents For Cyber Security Breache Response Strategy Formats PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
-
CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Explore a selection of the finest CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
-
Threat Security Before And After Artificial Intelligence Formats PDF
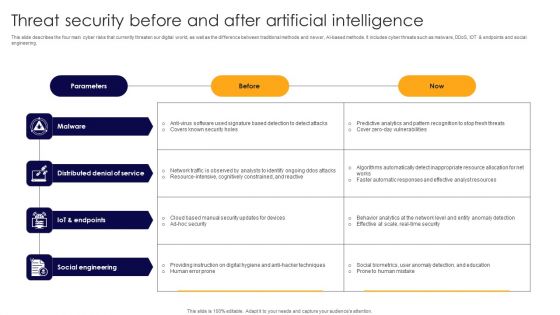
This slide describes the four main cyber risks that currently threaten our digital world, as well as the difference between traditional methods and newer, AI based methods. It includes cyber threats such as malware, DDoS, IOT and endpoints and social engineering. Showcasing this set of slides titled Threat Security Before And After Artificial Intelligence Formats PDF. The topics addressed in these templates are Malware, Distributed Denial Service, Social Engineering. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Formation Of Effective HR Security Plan Information PDF
This slide showcases effective HR safety plan for continuous safety management in organization. This template aims to evaluate the quality of working environment to minimize the risk of accidents and injuries and enhance overall well being of the employee. It also provides details regarding time period and status of activities. Presenting Formation Of Effective HR Security Plan Information PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Activity, Responsible Person, Basic Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Security Software Company Investor Funding Pitch Deck Financial Performance Formats PDF
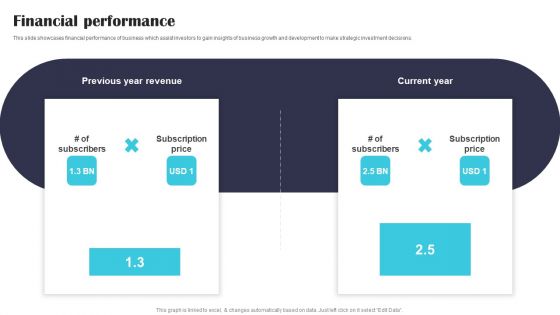
This slide showcases financial performance of business which assist investors to gain insights of business growth and development to make strategic investment decisions. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Security Software Company Investor Funding Pitch Deck Financial Performance Formats PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
-
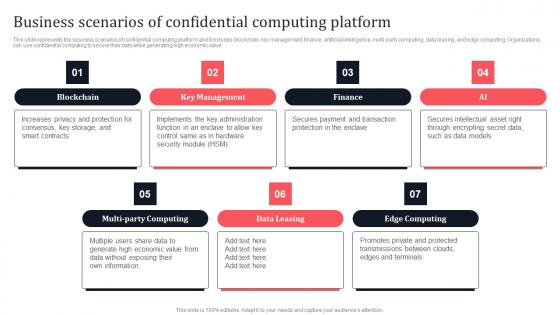
Business Scenarios Of Confidential Computing Platform Secure Multi Party Formats Pdf
This slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. Boost your pitch with our creative Business Scenarios Of Confidential Computing Platform Secure Multi Party Formats Pdf Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
-
Confidential Computing Architecture Implementation Roadmap Secure Multi Party Formats Pdf
This slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Confidential Computing Architecture Implementation Roadmap Secure Multi Party Formats Pdf can be your best option for delivering a presentation. Represent everything in detail using Confidential Computing Architecture Implementation Roadmap Secure Multi Party Formats Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
-
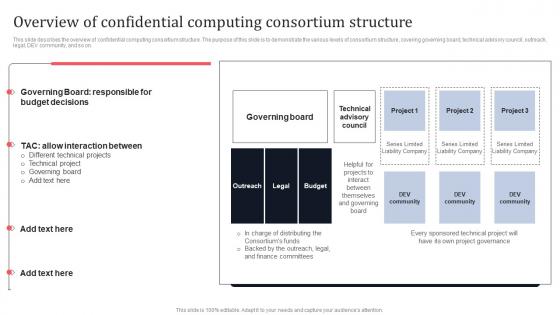
Overview Of Confidential Computing Consortium Structure Secure Multi Party Formats Pdf
This slide describes the overview of confidential computing consortium structure. The purpose of this slide is to demonstrate the various levels of consortium structure, covering governing board, technical advisory council, outreach, legal, DEV community, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Overview Of Confidential Computing Consortium Structure Secure Multi Party Formats Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Overview Of Confidential Computing Consortium Structure Secure Multi Party Formats Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
-
Analysis For Investment Segregation In Internet Security Formats Pdf
The slide showcase cyber security and technology investment related top data security are presented in FY 2021 to 2022.It helps organization to provides a visual overview of data security and technology investment trends, aiding informed decision making and strategic planning for cybersecurity measures within the organization.Pitch your topic with ease and precision using this Analysis For Investment Segregation In Internet Security Formats Pdf This layout presents information on Highest Investment, Register Investor Advisors, Key Insights It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
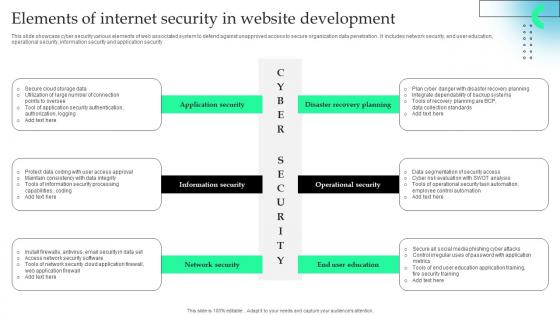
Elements Of Internet Security In Website Development Formats Pdf
This slide showcase cyber security various elements of web associated system to defend against unapproved access to secure organization data penetration . It includes network security, end user education, operational security, information security and application security.Pitch your topic with ease and precision using this Elements Of Internet Security In Website Development Formats Pdf This layout presents information on Information Security, Network Security, Operational Security It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
General Data Protection Regulation Security Strategic Agenda Formats Pdf
This slide represents action plan of GDPRgeneral data protection regulation. It further includes identify data location, remove unwanted data, risk assessment, being ready to respond to data subjects requests, etc. Pitch your topic with ease and precision using this General Data Protection Regulation Security Strategic Agenda Formats Pdf. This layout presents information on Identify Data Location, Build Governance Framework, Build Incident. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
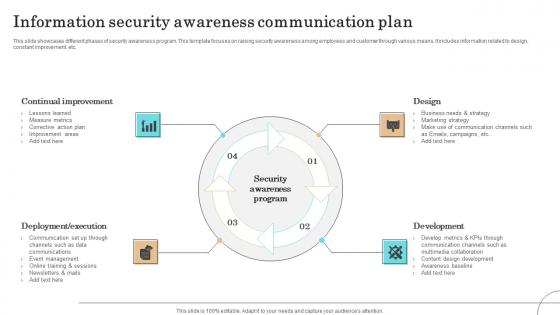
Information Security Awareness Communication Plan Formats Pdf
This slide showcases different phases of security awareness program. This template focuses on raising security awareness among employees and customer through various means. It includes information related to design, constant improvement, etc.Pitch your topic with ease and precision using this Information Security Awareness Communication Plan Formats Pdf This layout presents information on Continual Improvement, Deployment Execution, Communication It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
Multiple Device Based Internet Of Things Security Icon Formats Pdf
Showcasing this set of slides titled Multiple Device Based Internet Of Things Security Icon Formats Pdf The topics addressed in these templates are Multiple Device Based, Internet Of Things, Security Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
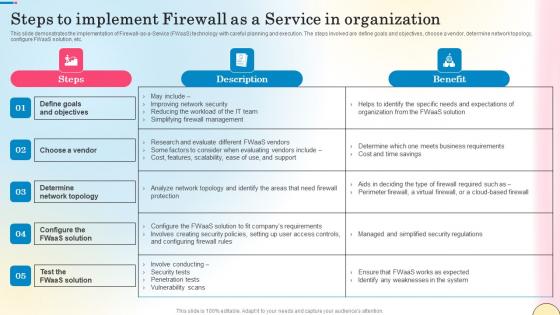
Steps To Implement Firewall As A Service In Organization Network Security Formats Pdf
This slide demonstrates the implementation of Firewall-as-a-Service FWaaS technology with careful planning and execution. The steps involved are define goals and objectives, choose a vendor, determine network topology, configure FWaaS solution, etc. Get a simple yet stunning designed Steps To Implement Firewall As A Service In Organization Network Security Formats Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Steps To Implement Firewall As A Service In Organization Network Security Formats Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
-
Leverage Cryptography To Boost Comprehensive Guide To Blockchain Digital Security Formats Pdf
The following slide showcases how cryptography assists in securing blockchain transactions and maintaining confidentiality. It includes elements such as data confidentiality, data integrity, digital signatures, consensus mechanism, etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Leverage Cryptography To Boost Comprehensive Guide To Blockchain Digital Security Formats Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Leverage Cryptography To Boost Comprehensive Guide To Blockchain Digital Security Formats Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
-
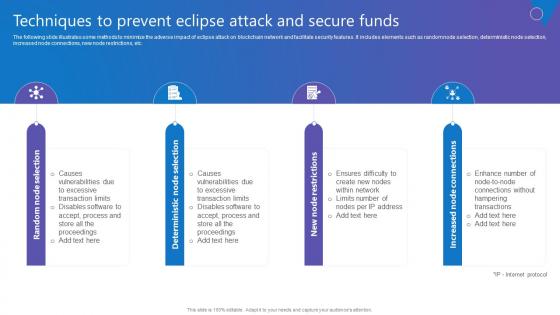
Techniques To Prevent Eclipse Comprehensive Guide To Blockchain Digital Security Formats Pdf
The following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Create an editable Techniques To Prevent Eclipse Comprehensive Guide To Blockchain Digital Security Formats Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Techniques To Prevent Eclipse Comprehensive Guide To Blockchain Digital Security Formats Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
-
Critical Principles Of Zero Trust Network Access Security Formats Pdf
This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Critical Principles Of Zero Trust Network Access Security Formats Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Critical Principles Of Zero Trust Network Access Security Formats Pdf today and make your presentation stand out from the rest
-
Key Characteristics Of Modern ZTNA Solution Zero Trust Network Security Formats Pdf
This slide outlines the top features that a modern ZTNA model should include. This slide highlights the characteristics of modern ZTNA solutions, including data loss prevention, scalable performance, granular visibility and reporting, BYOD deployment options, advanced threat protection, and SASE offering. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Key Characteristics Of Modern ZTNA Solution Zero Trust Network Security Formats Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
-
Key Points To Choose Zero Trust Solution Zero Trust Network Security Formats Pdf
This slide highlights the main criteria while choosing the right zero trust solution for the organization. The purpose of this slide is to showcase the key points the businesses should keep in mind while selecting the ZTNA vendor. The main points include vendor support, zero trust technology type, and so on. This modern and well-arranged Key Points To Choose Zero Trust Solution Zero Trust Network Security Formats Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
-
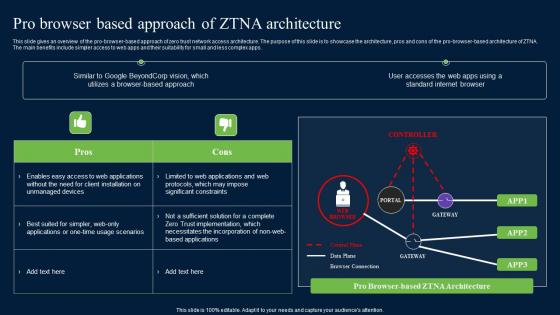
Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf
The main benefits include simpler access to web apps and their suitability for small and less complex apps. Presenting this PowerPoint presentation, titled Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Pro Browser Based Approach Of ZTNA Architecture Zero Trust Network Security Formats Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
-
Data Security In Cloud Computing Cloud Data Security Using Cryptography Formats Pdf
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues. Retrieve professionally designed Data Security In Cloud Computing Cloud Data Security Using Cryptography Formats Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
-
Factors Responsible For Cloud Security Cloud Data Security Using Cryptography Formats Pdf
The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low level encryption, reliance on cloud service providers for data protection, poor key management, etc. Take your projects to the next level with our ultimate collection of Factors Responsible For Cloud Security Cloud Data Security Using Cryptography Formats Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
-
Data Encryption Method In Application Security Testing Ppt Powerpoint Formats
This slide discusses the introduction of encryption in application security for protection of specific fields in an application. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Data Encryption Method In Application Security Testing Ppt Powerpoint Formats to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
-
Icons Slide For Application Security Testing Ppt Powerpoint Formats
Download our innovative and attention grabbing Icons Slide For Application Security Testing Ppt Powerpoint Formats template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.