Determine vulnerabilities PowerPoint Presentation Templates and Google Slides
-
Company Vulnerability Administration Determine Approved Methods Of Vulnerability Assessment Microsoft PDF
Presenting company vulnerability administration determine approved methods of vulnerability assessment microsoft pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like determine the methods required by regulation, determine the methods required to meet the operational requirements, determine the legal implications, determine the impact imposed by candidate methods. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Company Vulnerability Administration Determine Effectiveness Of Vulnerability Dispositions Microsoft PDF
This is a company vulnerability administration determine effectiveness of vulnerability dispositions microsoft pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluate disposition efforts, update vulnerability repository, repeat disposition process as necessary. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Company Vulnerability Administration Determine The Scope Of Vulnerability Management Designs PDF
This is a company vulnerability administration determine the scope of vulnerability management designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like document the candidate assets and services to be assessed and monitored, determine the operational environment for analysis and monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Company Vulnerability Administration Determine The State Of The Program Summary PDF
Presenting company vulnerability administration determine the state of the program summary pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like review the strategy with stakeholders, determine what each stakeholder need, determine what the current process provides. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Company Vulnerability Administration Determine Tools Aligned To The Strategy Demonstration PDF
Deliver and pitch your topic in the best possible manner with this company vulnerability administration determine tools aligned to the strategy demonstration pdf. Use them to share invaluable insights on identify candidate tools, publish authorized tool list, define the exception process, conduct periodic reviews and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Determining The Level Of Job Vulnerability During Pandemic Ppt Slides Summary PDF
Following slide displays informational stats about the vulnerability level of job in automobile sector by income band and annual income. Deliver an awe inspiring pitch with this creative determining the level of job vulnerability during pandemic ppt slides summary pdf bundle. Topics like determining the level of job vulnerability during pandemic can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Determine Sequence Phases For Mitigating Cybersecurity Threats And Vulnerabilities Inspiration PDF
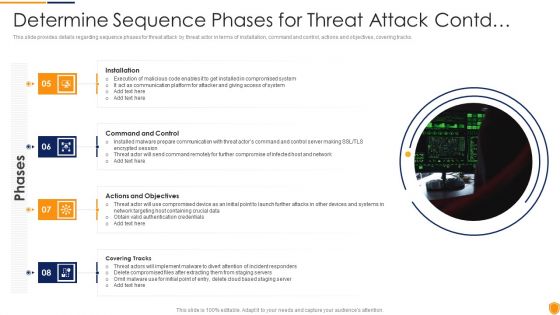
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. This is a determine sequence phases for mitigating cybersecurity threats and vulnerabilities inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Mitigating Cybersecurity Threats And Vulnerabilities Determine Sequence Phases Elements PDF
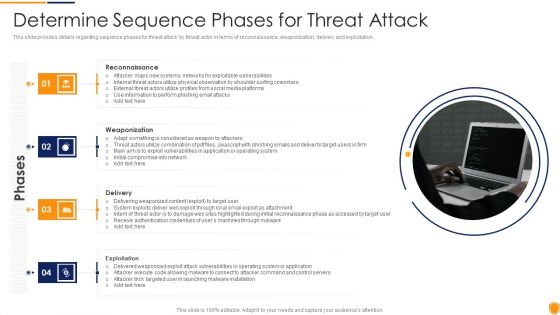
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a mitigating cybersecurity threats and vulnerabilities determine sequence phases elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reconnaissance, weaponization, delivery, exploitation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Mitigating Cybersecurity Threats And Vulnerabilities Determine Several Threat Structure PDF
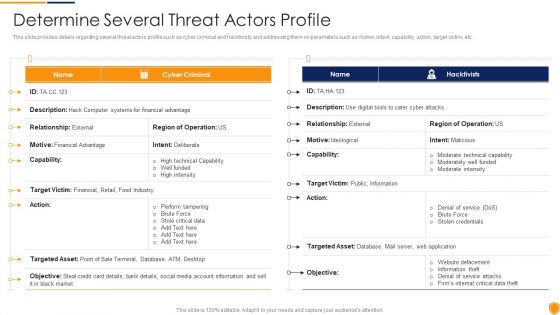
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities determine several threat structure pdf bundle. Topics like determine several threat actors profile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Mitigating Cybersecurity Threats And Vulnerabilities Determine Staff Training Rules PDF
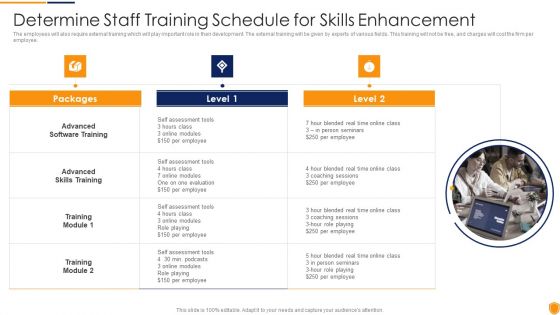
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. This is a mitigating cybersecurity threats and vulnerabilities determine staff training rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like advanced software training, advanced skills training, training module. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Mitigating Cybersecurity Threats And Vulnerabilities Determine Threat Management Brochure PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting mitigating cybersecurity threats and vulnerabilities determine threat management brochure pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like determine threat management team structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Mitigating Cybersecurity Threats And Vulnerabilities Determine Threat Scenario Rules PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities determine threat scenario rules pdf bundle. Topics like determine threat scenario analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Determining Residual Risks Through Minimizing Customer Transaction Vulnerabilities Slides Pdf
This slide showcases assessment matrix to determine residual risks. It provides information about inherent risks, control assessment, satisfaction, visibility, risk management controls, data analytics, etc. Slidegeeks has constructed Determining Residual Risks Through Minimizing Customer Transaction Vulnerabilities Slides Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.