Data Breaches Attack PowerPoint Presentation Templates and Google Slides
-
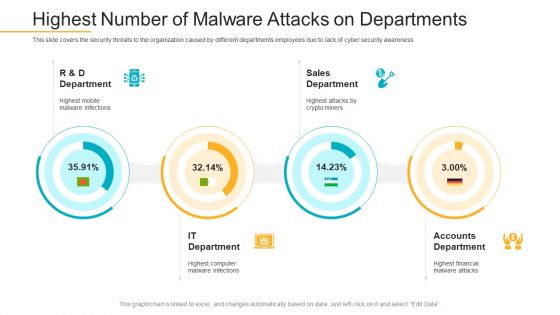
Data Breach Prevention Recognition Highest Number Of Malware Attacks On Departments Pictures PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition highest number of malware attacks on departments pictures pdf. Use them to share invaluable insights on sales department, accounts department, it department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
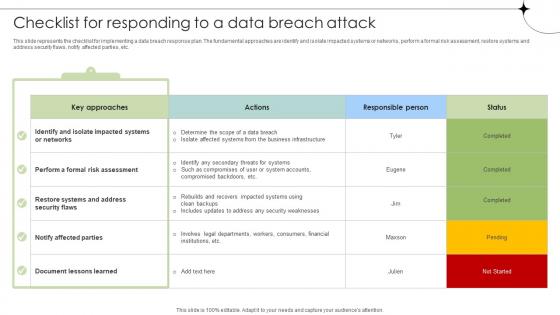
Checklist For Responding To A Data Breach Attack Data Breach Prevention Microsoft Pdf
This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Responding To A Data Breach Attack Data Breach Prevention Microsoft Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
-
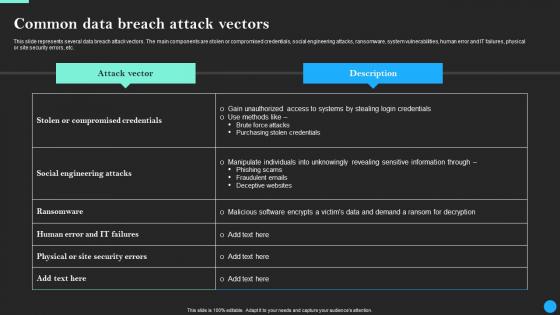
Common Data Breach Attack Vectors Data Breach Prevention Clipart Pdf
This slide represents several data breach attack vectors. The main components are stolen or compromised credentials, social engineering attacks, ransomware, system vulnerabilities, human error and IT failures, physical or site security errors, etc. Present like a pro with Common Data Breach Attack Vectors Data Breach Prevention Clipart Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
-
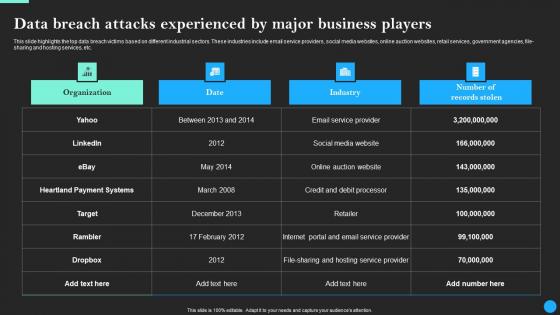
Data Breach Attacks Experienced By Major Business Data Breach Prevention Diagrams Pdf
This slide highlights the top data breach victims based on different industrial sectors. These industries include email service providers, social media websites, online auction websites, retail services, government agencies, file-sharing and hosting services, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Data Breach Attacks Experienced By Major Business Data Breach Prevention Diagrams Pdf can be your best option for delivering a presentation. Represent everything in detail using Data Breach Attacks Experienced By Major Business Data Breach Prevention Diagrams Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
-
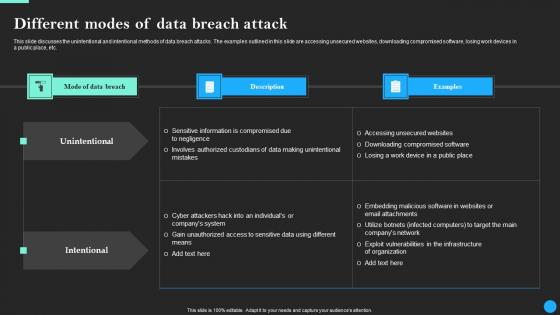
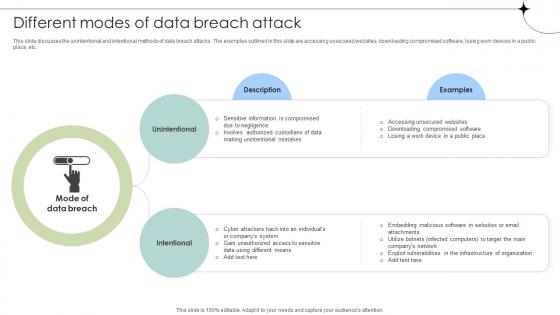
Different Modes Of Data Breach Attack Data Breach Prevention Rules Pdf
This slide discusses the unintentional and intentional methods of data breach attacks. The examples outlined in this slide are accessing unsecured websites, downloading compromised software, losing work devices in a public place, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Different Modes Of Data Breach Attack Data Breach Prevention Rules Pdf from Slidegeeks and deliver a wonderful presentation.
-
Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf
This slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss. Presenting this PowerPoint presentation, titled Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Major Consequences Of Data Breach Cyber Attack Data Breach Prevention Sample Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
-
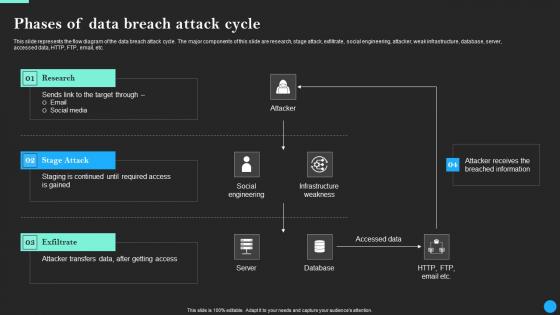
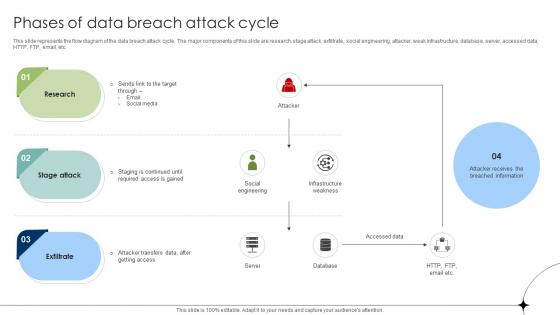
Phases Of Data Breach Attack Cycle Data Breach Prevention Template Pdf
Find a pre-designed and impeccable Phases Of Data Breach Attack Cycle Data Breach Prevention Template Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
-
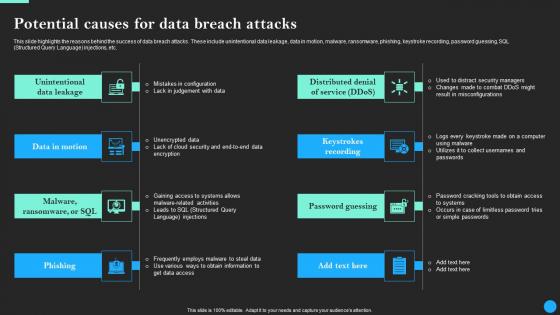
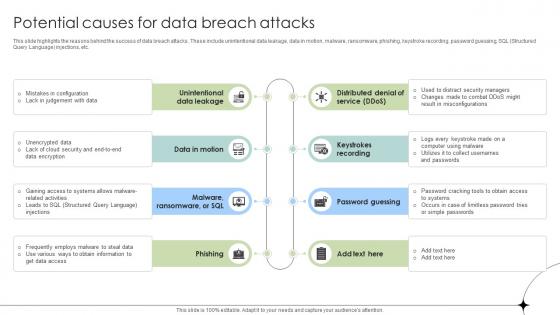
Potential Causes For Data Breach Attacks Data Breach Prevention Ideas Pdf
Boost your pitch with our creative Potential Causes For Data Breach Attacks Data Breach Prevention Ideas Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
-
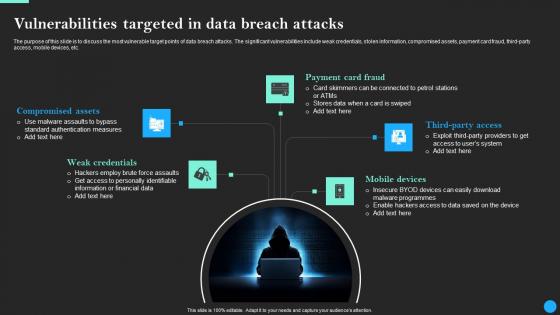
Vulnerabilities Targeted In Data Breach Attacks Data Breach Prevention Inspiration Pdf
Slidegeeks is here to make your presentations a breeze with Vulnerabilities Targeted In Data Breach Attacks Data Breach Prevention Inspiration Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
-
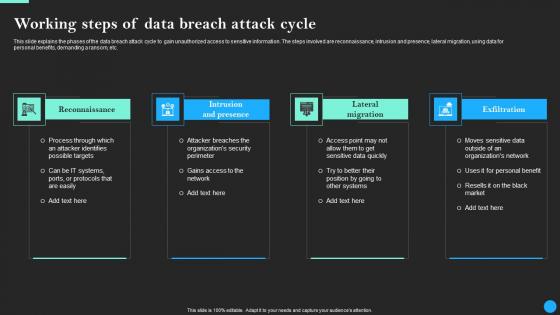
Working Steps Of Data Breach Attack Cycle Data Breach Prevention Infographics Pdf
This slide explains the phases of the data breach attack cycle to gain unauthorized access to sensitive information. The steps involved are reconnaissance, intrusion and presence, lateral migration, using data for personal benefits, demanding a ransom, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Working Steps Of Data Breach Attack Cycle Data Breach Prevention Infographics Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Working Steps Of Data Breach Attack Cycle Data Breach Prevention Infographics Pdf today and make your presentation stand out from the rest
-
Checklist For Responding To A Data Breach Attack Data Fortification Strengthening Defenses
This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Responding To A Data Breach Attack Data Fortification Strengthening Defenses will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
-
Common Data Breach Attack Vectors Data Fortification Strengthening Defenses
This slide represents several data breach attack vectors. The main components are stolen or compromised credentials, social engineering attacks, ransomware, system vulnerabilities, human error and IT failures, physical or site security errors, etc. Present like a pro with Common Data Breach Attack Vectors Data Fortification Strengthening Defenses. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
-
Data Breach Attacks Experienced By Major Business Players Data Fortification Strengthening Defenses
This slide highlights the top data breach victims based on different industrial sectors. These industries include email service providers, social media websites, online auction websites, retail services, government agencies, file-sharing and hosting services, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Data Breach Attacks Experienced By Major Business Players Data Fortification Strengthening Defenses can be your best option for delivering a presentation. Represent everything in detail using Data Breach Attacks Experienced By Major Business Players Data Fortification Strengthening Defenses and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
-
Different Modes Of Data Breach Attack Data Fortification Strengthening Defenses
This slide discusses the unintentional and intentional methods of data breach attacks. The examples outlined in this slide are accessing unsecured websites, downloading compromised software, losing work devices in a public place, etc.Explore a selection of the finest Different Modes Of Data Breach Attack Data Fortification Strengthening Defenses here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Different Modes Of Data Breach Attack Data Fortification Strengthening Defenses to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
-
Major Consequences Of Data Breach Cyber Attack Data Fortification Strengthening Defenses
This slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss. Slidegeeks has constructed Major Consequences Of Data Breach Cyber Attack Data Fortification Strengthening Defenses after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
-
Phases Of Data Breach Attack Cycle Data Fortification Strengthening Defenses
This slide represents the flow diagram of the data breach attack cycle. The major components of this slide are research, stage attack, exfiltrate, social engineering, attacker, weak infrastructure, database, server, accessed data, HTTP, FTP, email, etc. Do you know about Slidesgeeks Phases Of Data Breach Attack Cycle Data Fortification Strengthening Defenses These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
-
Potential Causes For Data Breach Attacks Data Fortification Strengthening Defenses
This slide highlights the reasons behind the success of data breach attacks. These include unintentional data leakage, data in motion, malware, ransomware, phishing, keystroke recording, password guessing, SQL Structured Query Language injections, etc.Find a pre-designed and impeccable Potential Causes For Data Breach Attacks Data Fortification Strengthening Defenses. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
-
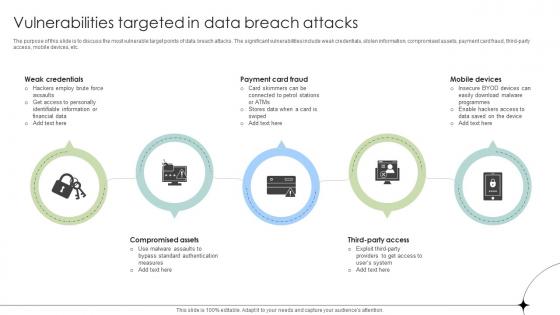
Vulnerabilities Targeted In Data Breach Attacks Data Fortification Strengthening Defenses
The purpose of this slide is to discuss the most vulnerable target points of data breach attacks. The significant vulnerabilities include weak credentials, stolen information, compromised assets, payment card fraud, third-party access, mobile devices, etc. Slidegeeks is here to make your presentations a breeze with Vulnerabilities Targeted In Data Breach Attacks Data Fortification Strengthening Defenses With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
-
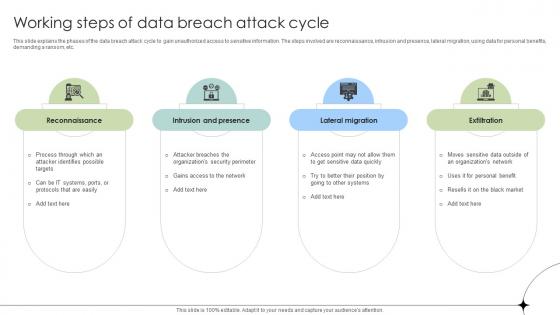
Working Steps Of Data Breach Attack Cycle Data Fortification Strengthening Defenses
This slide explains the phases of the data breach attack cycle to gain unauthorized access to sensitive information. The steps involved are reconnaissance, intrusion and presence, lateral migration, using data for personal benefits, demanding a ransom, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Working Steps Of Data Breach Attack Cycle Data Fortification Strengthening Defenses. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Working Steps Of Data Breach Attack Cycle Data Fortification Strengthening Defenses today and make your presentation stand out from the rest