Data breach PowerPoint Presentation Templates and Google Slides
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Tools To Be Implemented Portrait PDF
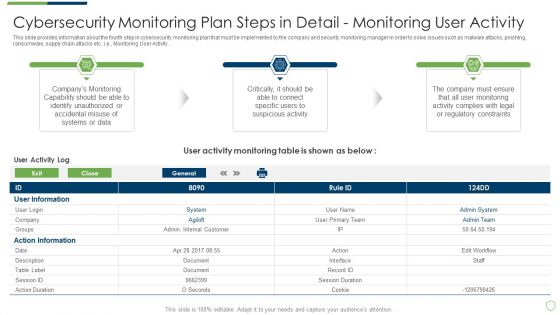
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring tools to be implemented portrait pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring user activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Structure PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring structure pdf. Use them to share invaluable insights on cybersecurity monitoring tools to be implemented and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Essential Elements Of Security Monitoring Plan Sample PDF
This slide provides information about some of the essential elements that must be a part of security monitoring plan in order to protect sensitive information. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach essential elements of security monitoring plan sample pdf bundle. Topics like critical infrastructure, cloud security, application security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
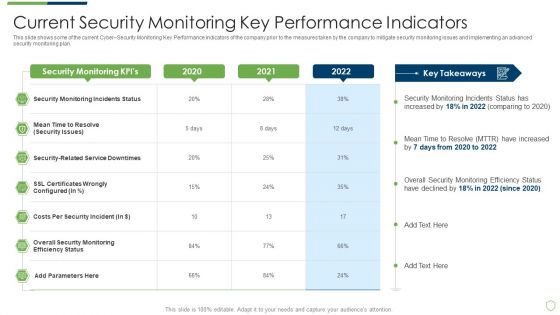
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Estimated Security Monitoring Guidelines PDF
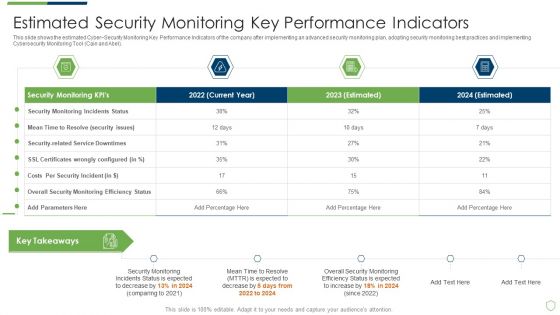
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach estimated security monitoring guidelines pdf. Use them to share invaluable insights on estimated security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Major Reasons For Poor Security Elements PDF
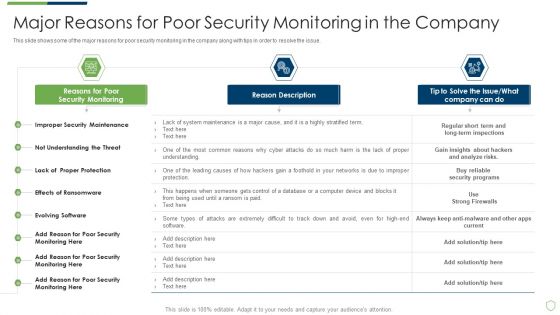
This slide shows some of the major reasons for poor security monitoring in the company along with tips in order to resolve the issue. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach major reasons for poor security elements pdf bundle. Topics like major reasons for poor security monitoring in the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Measures And Ways To Mitigate Rules PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach measures and ways to mitigate rules pdf. Use them to share invaluable insights on measures and ways to mitigate security monitoring challenges and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard Sample PDF
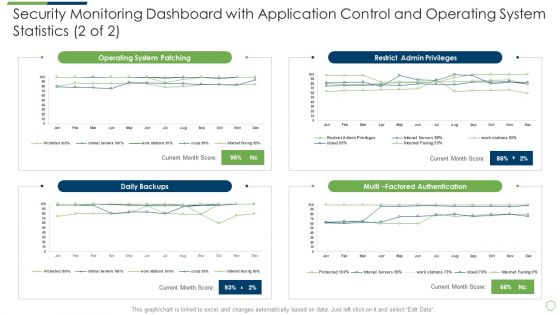
Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard sample pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard With Application Slides PDF
Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard with application slides pdf. Use them to share invaluable insights on security monitoring dashboard with application control and operating system statistics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard With Malicious Icons PDF
Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard with malicious icons pdf bundle. Topics like security monitoring dashboard with malicious requests and average latency rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Way To Overcome Security Introduction PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a modern security observation plan to eradicate cybersecurity risk and data breach way to overcome security introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
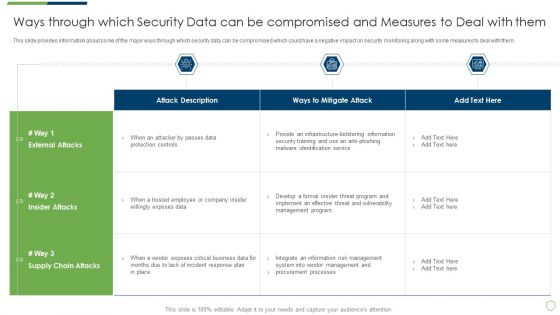
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Ways Through Which Security Data Themes PDF
This slide provides information about some of the major ways through which security data can be compromised which could have a negative impact on security monitoring along with some measures to deal with them. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach ways through which security data themes pdf bundle. Topics like ways through which security data can be compromised and measures to deal with them can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Table Of Contents Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Information PDF
Deliver and pitch your topic in the best possible manner with this table of contents modern security observation plan to eradicate cybersecurity risk and data breach information pdf. Use them to share invaluable insights on essential elements of security, compromised and measures, performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Agenda For Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Information PDF
This is a agenda for modern security observation plan to eradicate cybersecurity risk and data breach information pdf template with various stages. Focus and dispense information on senen stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda for modern security observation plan to eradicate cybersecurity risk and data breach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Icons Slide For Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Clipart PDF
Introducing our well designed icons slide for modern security observation plan to eradicate cybersecurity risk and data breach clipart pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Market Trends Inspiration PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. This is a modern security observation plan to eradicate cybersecurity risk and data breach current market trends inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like increasing digitization of sensitive data, outsourcing, general data protection laws. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Security Monitoring Challenges Slides PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach current security monitoring challenges slides pdf bundle. Topics like current security monitoring challenges the company is facing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Security Monitoring Pictures PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach current security monitoring pictures pdf. Use them to share invaluable insights on current security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Best Practices Introduction PDF
This slide provides information about some of the best practices related to security monitoring that must be followed by the company. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring best practices introduction pdf bundle. Topics like cybersecurity monitoring best practices to be followed by the company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Fine Sample PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring Network Traffic. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail fine sample pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail monitoring network traffic and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
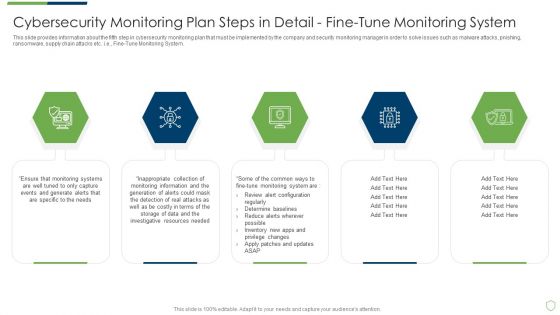
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Introduction PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring introduction pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Providing Sample PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail providing sample pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring all systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
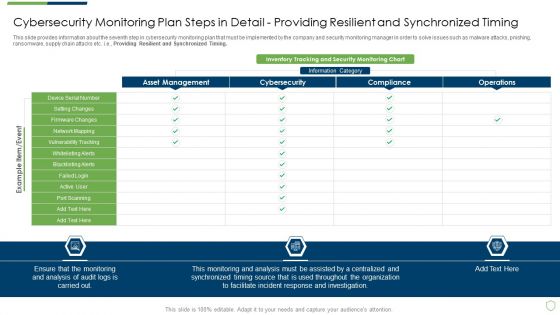
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Setting Brochure PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail setting brochure pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail providing resilient and synchronized timing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Detail Structure PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in detail structure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps In Professional PDF
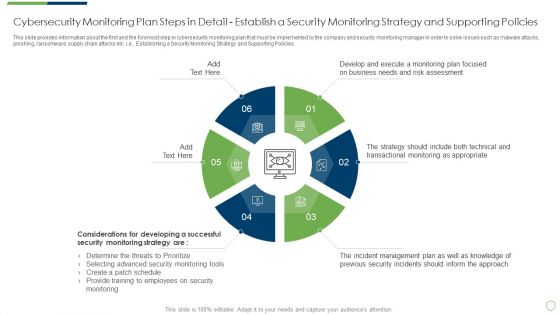
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Establishing a Security Monitoring Strategy and Supporting Policies. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps in professional pdf bundle. Topics like cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Steps Elements PDF
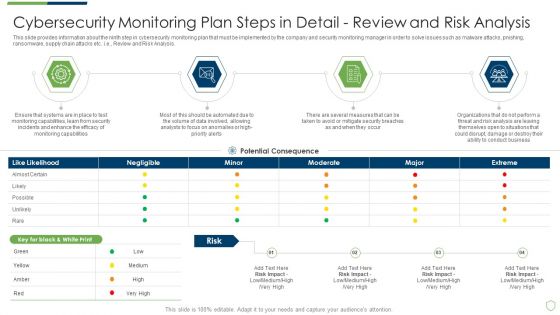
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan steps elements pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail review and risk analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Steps For Developing Data Breach Strategic Action Plan Professional PDF
This slide covers the steps for developing data breach response plan which focuses on breach identification, internal notification and engagement of legal compliance which helps the organization proper management of security response plan. Persuade your audience using this steps for developing data breach strategic action plan professional pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including breach identification, internal notification, engaging law compliance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
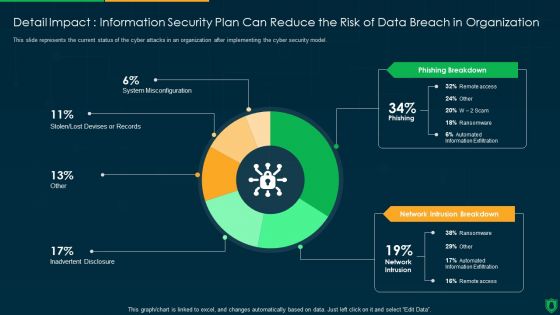
Detail Impact Information Security Plan Can Reduce The Risk Of Data Breach Ppt PowerPoint Presentation File Visual Aids PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver an awe inspiring pitch with this creative detail impact information security plan can reduce the risk of data breach ppt powerpoint presentation file visual aids pdf bundle. Topics like phishing breakdown, network intrusion breakdown, inadvertent desclosure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
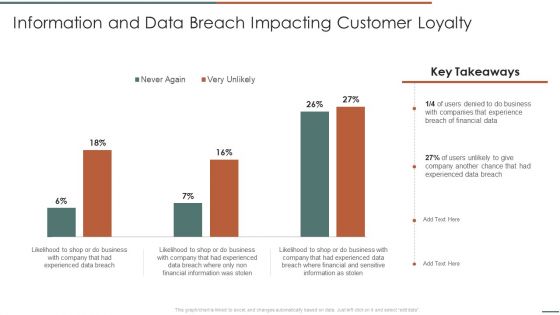
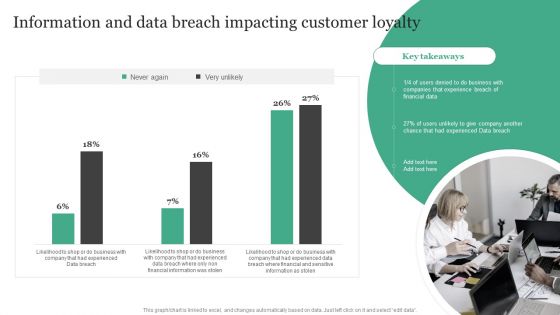
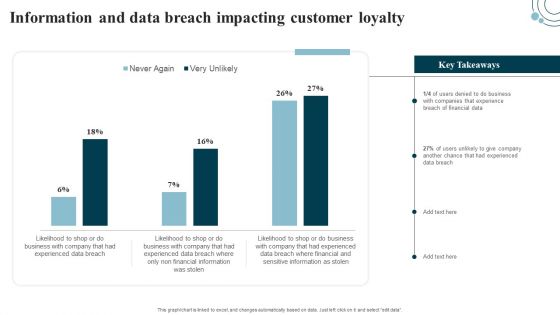
Information Security Risk Evaluation Information And Data Breach Impacting Customer Loyalty Structure PDF
Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Information And Data Breach Impacting Customer Loyalty Structure PDF bundle. Topics like Companies Experience, Financial Information, Breach Of Financial can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
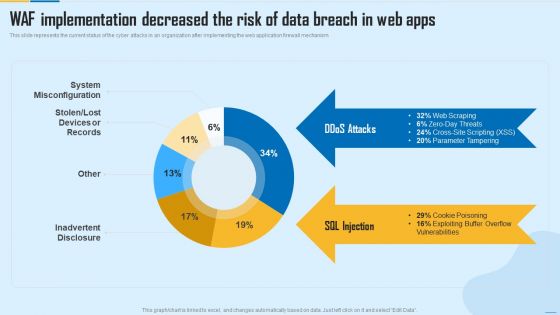
WAF Implementation Decreased The Risk Of Data Breach In Web Apps WAF Platform Summary PDF
This slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Deliver and pitch your topic in the best possible manner with this WAF Implementation Decreased The Risk Of Data Breach In Web Apps WAF Platform Summary PDF. Use them to share invaluable insights on System Misconfiguration, Inadvertent Disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
Fundraising Pitch Deck For Evervault We Can End The Data Breach Epidemic Ppt Infographics Graphics Example PDF
This slide depicts the major issues which organizations are facing such as breaches of customers, cost of breaches, protection of data, etc. This is a Fundraising Pitch Deck For Evervault We Can End The Data Breach Epidemic Ppt Infographics Graphics Example PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Breaches, Involving Customers, Violation Skyrocketing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Data Theft And Breach Threats Monitoring Dashboard Ppt Outline Designs PDF
This slide covers dashboard to monitor top data breaches and loss of confidential data in organization. It includes KPIs such percentage of data risks detected, number of data risks, data risk analysis, response progress for data risks, data risk ratings. Showcasing this set of slides titled Data Theft And Breach Threats Monitoring Dashboard Ppt Outline Designs PDF. The topics addressed in these templates are Number Risk Threshold, Data Analysts Progress, Action Plan Breakdown. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
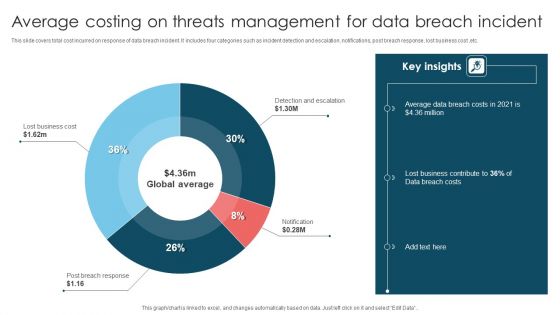
Average Costing On Threats Management For Data Breach Incident Demonstration PDF
This slide covers total cost incurred on response of data breach incident. It includes four categories such as incident detection and escalation, notifications, post breach response, lost business cost ,etc. Pitch your topic with ease and precision using this Average Costing On Threats Management For Data Breach Incident Demonstration PDF. This layout presents information on Lost Business Cost, Detection And Escalation, Notification. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
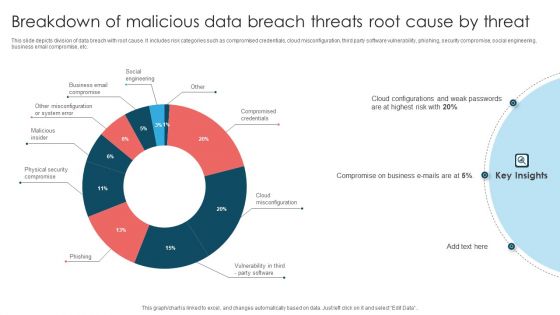
Breakdown Of Malicious Data Breach Threats Root Cause By Threat Themes PDF
This slide depicts division of data breach with root cause. It includes risk categories such as compromised credentials, cloud misconfiguration, third party software vulnerability, phishing, security compromise, social engineering, business email compromise, etc. Showcasing this set of slides titled Breakdown Of Malicious Data Breach Threats Root Cause By Threat Themes PDF. The topics addressed in these templates are Compromise On Business, Cloud Configurations, Weak Passwords. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
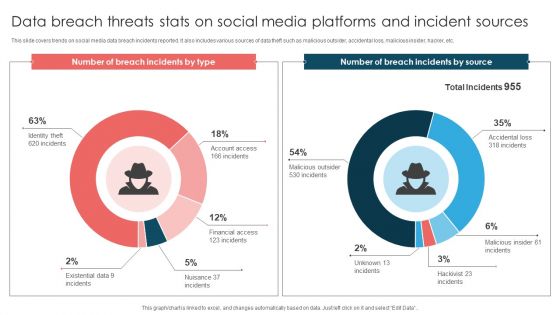
Data Breach Threats Stats On Social Media Platforms And Incident Sources Introduction PDF
This slide covers trends on social media data breach incidents reported. It also includes various sources of data theft such as malicious outsider, accidental loss, malicious insider, hacker, etc. Pitch your topic with ease and precision using this Data Breach Threats Stats On Social Media Platforms And Incident Sources Introduction PDF. This layout presents information on Number Breach, Total Incidents, Malicious Insider. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
Information And Data Breach Impacting Customer Loyalty Information Security Risk Administration Demonstration PDF
Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Information And Data Breach Impacting Customer Loyalty Information Security Risk Administration Demonstration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Information And Data Breach Impacting Customer Loyalty Information Security Risk Administration Demonstration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
-
Information And Data Breach Impacting Customer Loyalty Cybersecurity Risk Assessment Infographics PDF
Retrieve professionally designed Information And Data Breach Impacting Customer Loyalty Cybersecurity Risk Assessment Infographics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
-
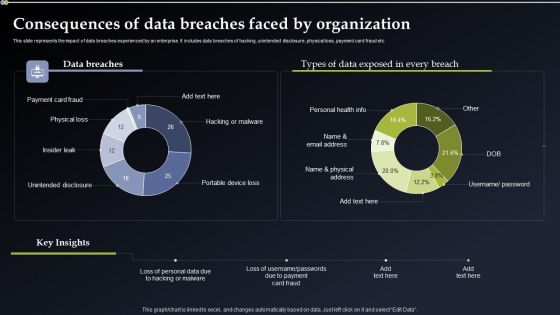
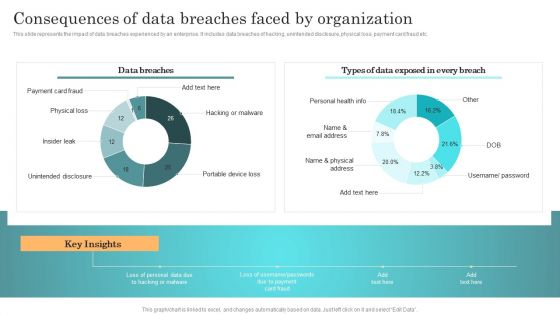
Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
-
Information Systems Security And Risk Management Plan Information And Data Breach Impacting Customer Loyalty Brochure PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable Information Systems Security And Risk Management Plan Information And Data Breach Impacting Customer Loyalty Brochure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
-
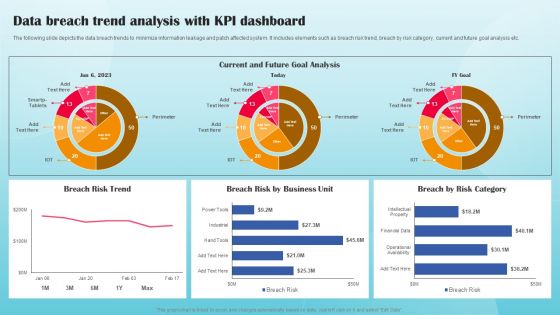
Data Breach Trend Analysis With KPI Dashboard Ppt PowerPoint Presentation File Portfolio PDF
The following slide depicts the data breach trends to minimize information leakage and patch affected system. It includes elements such as breach risk trend, breach by risk category, current and future goal analysis etc. This modern and well arranged Data Breach Trend Analysis With KPI Dashboard Ppt PowerPoint Presentation File Portfolio PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
-
Incident Response Techniques Deployement Consequences Of Data Breaches Faced By Organization Structure PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. There are so many reasons you need a Incident Response Techniques Deployement Consequences Of Data Breaches Faced By Organization Structure PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
-
Developing IT Security Strategy Information And Data Breach Impacting Customer Loyalty Template PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select edit data. Get a simple yet stunning designed Developing IT Security Strategy Information And Data Breach Impacting Customer Loyalty Template PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Developing IT Security Strategy Information And Data Breach Impacting Customer Loyalty Template PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
-
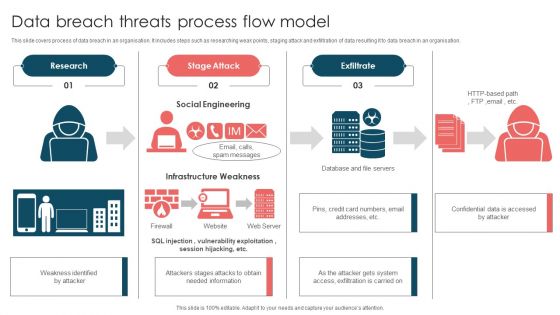
Data Breach Threats Process Flow Model Ppt Model Maker PDF
This slide covers process of data breach in an organisation. It includes steps such as researching weak points, staging attack and exfiltration of data resulting it to data breach in an organisation. Persuade your audience using this Data Breach Threats Process Flow Model Ppt Model Maker PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Research, Stage Attack, Exfiltrate, Social Engineering. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Four Steps Of Cyber Security Data Breach Threats Process Ppt Icon Format Ideas PDF
This slide covers steps utilised to breach data. It includes stages such as probing, performing initial attack, expansion of attacks and data lifting. Presenting Four Steps Of Cyber Security Data Breach Threats Process Ppt Icon Format Ideas PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Probe, Initial Attack, Expanded Attack, Data Lift. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Survey Insights On Data Breach Threats Incidents Icon Ppt Infographics Sample PDF
Presenting Survey Insights On Data Breach Threats Incidents Icon Ppt Infographics Sample PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Survey Insights, Data Breach Threats, Incidents Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Survey Insights On Threats Of Data Breach With Employees Byod Policy Brochure PDF
This slide covers insights on data breach incidents pertaining to companys BYOD policy. It includes stats on balancing employee freedom, company app functionality and data theft incidents by employees. Presenting Survey Insights On Threats Of Data Breach With Employees Byod Policy Brochure PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Employee Mobility, Data Breaches, Employees Use. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Cyber Protection Icon To Reduce Data Breaches Clipart PDF
Showcasing this set of slides titled Cyber Protection Icon To Reduce Data Breaches Clipart PDF. The topics addressed in these templates are Reduce Data Breaches, Cyber Protection Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Safety Breach Response Playbook Best Work From Home Data Security Practices Topics PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc. Explore a selection of the finest Safety Breach Response Playbook Best Work From Home Data Security Practices Topics PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Safety Breach Response Playbook Best Work From Home Data Security Practices Topics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
-
Safety Breach Response Playbook Checklist For Work From Home Data Security Slides PDF
The Safety Breach Response Playbook Checklist For Work From Home Data Security Slides PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
-
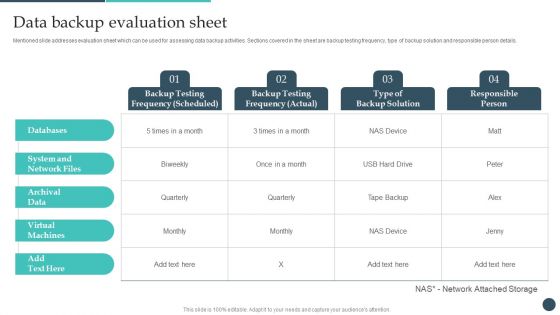
Safety Breach Response Playbook Data Backup Evaluation Sheet Microsoft PDF
Mentioned slide addresses evaluation sheet which can be used for assessing data backup activities. Sections covered in the sheet are backup testing frequency, type of backup solution and responsible person details. Create an editable Safety Breach Response Playbook Data Backup Evaluation Sheet Microsoft PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Safety Breach Response Playbook Data Backup Evaluation Sheet Microsoft PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
-
Security For Cloud Based Systems Icon To Reduce Data Breaches Download PDF
Presenting Security For Cloud Based Systems Icon To Reduce Data Breaches Download PDF to dispense important information. This template comprises Three stages. It also presents valuable insights into the topics including Security For Cloud, Based Systems Icon, Reduce Data Breaches . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Emerging Cyber Security Incident And Data Breaches Amid Pandemic Ppt Ideas Skills PDF
The given slide reflects the upcoming cyber threats due to remote working amid of COVID -19. Some of them are pandemic associated attacks, cloud breaches and mobile security threats. Persuade your audience using this Emerging Cyber Security Incident And Data Breaches Amid Pandemic Ppt Ideas Skills PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Pandemic Associated Attacks, Cloud Breaches, Mobile Security Threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Information Technology Security Data Breach And Trend Analysis Professional PDF
The following slide reflects some trends in information technology security to assess financial loss occurred to companies due to data breach. It includes average cost and average number of days to determine and report data breach, number of new malware detected per day etc. Presenting Information Technology Security Data Breach And Trend Analysis Professional PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Data Breach, Average Cost, Determine. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
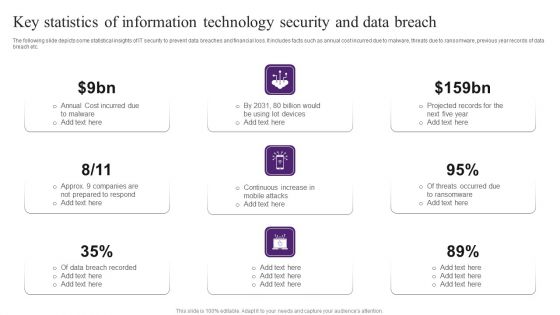
Key Statistics Of Information Technology Security And Data Breach Brochure PDF
The following slide depicts some statistical insights of IT security to prevent data breaches and financial loss. It includes facts such as annual cost incurred due to malware, threats due to ransomware, previous year records of data breach etc. Persuade your audience using this Key Statistics Of Information Technology Security And Data Breach Brochure PDF. This PPT design covers nine stages, thus making it a great tool to use. It also caters to a variety of topics including Cost Incurred, Data Breach Recorded, Projected Records. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
5 Steps Of Data Breach Response Management Topics PDF
Persuade your audience using this 5 Steps Of Data Breach Response Management Topics PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Communication Plan, Develop Contact List, Identify Response Team. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
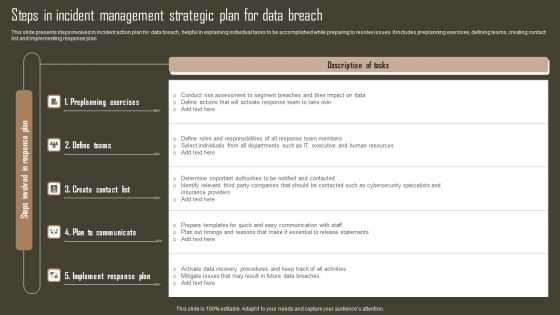
Steps In Incident Management Strategic Plan For Data Breach Pictures PDF
This slide presents steps involved in incident action plan for data breach, helpful in explaining individual tasks to be accomplished while preparing to resolve issues. It includes preplanning exercises, defining teams, creating contact list and implementing response plan. Showcasing this set of slides titled Steps In Incident Management Strategic Plan For Data Breach Pictures PDF. The topics addressed in these templates are Preplanning Exercises, Plan To Communicate, Implement Response Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
-
Incident Management Strategic Plan For Data Breach Pictures PDF
This slide presents incident action plan for data breach along with responsibility division, helpful in making planning out management of multiple types of breaches. It includes breaches related to contact information, financial information, health information and tax related information. Pitch your topic with ease and precision using this Incident Management Strategic Plan For Data Breach Pictures PDF. This layout presents information on Financial Information, Contact Information, Health Information. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Create an editable Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Implementing Cyber Security Incident Consequences Of Data Breaches Faced By Organization Infographics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
-
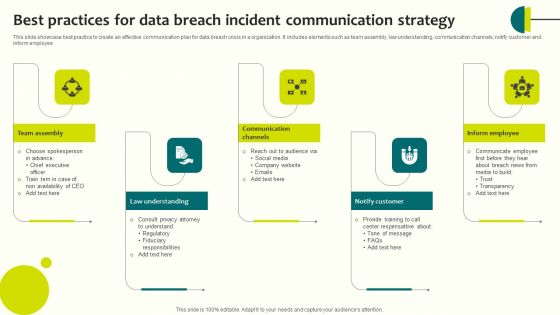
Best Practices For Data Breach Incident Communication Strategy Guidelines PDF
This slide showcase best practice to create an effective communication plan for data breach crisis in a organization. It includes elements such as team assembly, law understanding, communication channels, notify customer and inform employee Presenting Best Practices For Data Breach Incident Communication Strategy Guidelines PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Inform Employee, Communication Channels, Notify Customer . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Cloud Data Breach Incident Communication Strategy Icon Brochure PDF
Pitch your topic with ease and precision using this Cloud Data Breach Incident Communication Strategy Icon Brochure PDF. This layout presents information on Cloud Data, Breach Incident, Communication. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
Cyber Security Data Breach Post Incident Communication Strategy Slides PDF
This slides provide information about post crisis communication plan how to handle it in effective manner. It includes elements such as crisis team, fast, precise, and sincereresponses, clear line of communication and restorative services Presenting Cyber Security Data Breach Post Incident Communication Strategy Slides PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Crisis Team, Communication, Restorative Services. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.