Cybersecurity monitoring tools to be implemented PowerPoint Presentation Templates and Google Slides
-
Cybersecurity Monitoring Tools To Be Implemented Topics PDF
Deliver and pitch your topic in the best possible manner with this cybersecurity monitoring tools to be implemented topics pdf. Use them to share invaluable insights on security monitoring, password auditing tool, tool implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
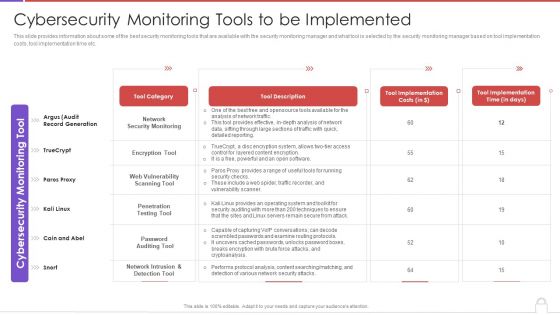
Methods To Develop Advanced Cybersecurity Monitoring Tools To Be Implemented Guidelines PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver an awe inspiring pitch with this creative methods to develop advanced cybersecurity monitoring tools to be implemented guidelines pdf bundle. Topics like network security monitoring, encryption tool, web vulnerability scanning tool can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Tools To Be Implemented Portrait PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring tools to be implemented portrait pdf bundle. Topics like cybersecurity monitoring plan steps in detail monitoring user activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.