Cybercrime PowerPoint Presentation Templates and Google Slides
-
Cybercrime Trends Ppt PowerPoint Presentation Pictures Display Cpb Pdf
Presenting this set of slides with name cybercrime trends ppt powerpoint presentation pictures display cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like cybercrime trends to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
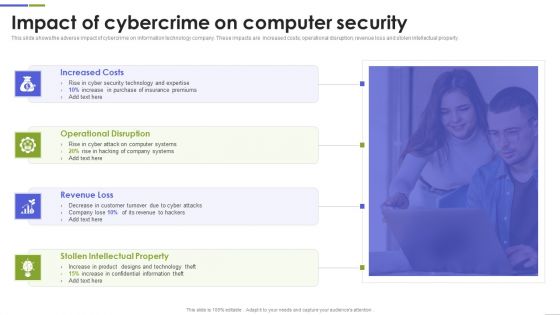
Impact Of Cybercrime On Computer Security Formats PDF
This slide shows the adverse impact of cybercrime on information technology company. These impacts are increased costs, operational disruption, revenue loss and stolen intellectual property. Persuade your audience using this Impact Of Cybercrime On Computer Security Formats PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Increased Costs, Operational Disruption, Revenue Loss Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Various Impact Of Cybercrime On It Protection Slides PDF
This slide shows the adverse impact of cybercrime on information technology companies. These impacts are increased costs, operational disruption, revenue loss and stolen intellectual property. Persuade your audience using this Various Impact Of Cybercrime On It Protection Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Operational Disruption, Revenue Loss, Stolen Intellectual Property. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
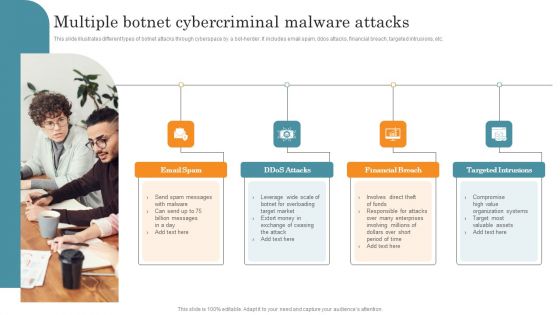
Multiple Botnet Cybercriminal Malware Attacks Elements PDF
This slide illustrates different types of botnet attacks through cyberspace by a bot-herder. It includes email spam, ddos attacks, financial breach, targeted intrusions, etc. Persuade your audience using this Multiple Botnet Cybercriminal Malware Attacks Elements PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Email Spam, Financial Breach, Targeted Intrusions. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Stages Of Botnet Malware Cybercriminal Attacks Themes PDF
This slide illustrates how to create a bot and orchestrating a botnet attack. It includes stages such as expose, infect and grow, activate, etc. Persuade your audience using this Stages Of Botnet Malware Cybercriminal Attacks Themes PDF. This PPT design covers Three stages, thus making it a great tool to use. It also caters to a variety of topics including Expose, Infect And Grow, Activate. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Robotic Process Automation Security Best Practices To Minimize Cybercrime Risk Themes PDF
This slide outlines strategies to minimize security failure in RPA projects. Some of the best practices such as maintain accountability for BOT actions, prevent fraud and abuse, preserve log integrity, and authorize secure RPA development. Presenting Robotic Process Automation Security Best Practices To Minimize Cybercrime Risk Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Maintain Accountability, Prevent Fraud And Abuse, Preserve Log Integrity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
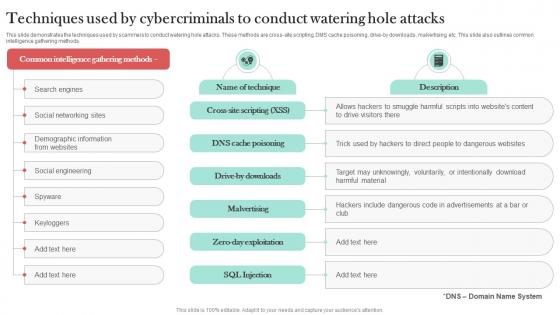
Techniques Used By Cybercriminals To Man In The Middle Phishing IT
This slide demonstrates the techniques used by scammers to conduct watering hole attacks. These methods are cross-site scripting, DMS cache poisoning, drive-by downloads, malvertising, etc. This slide also outlines common intelligence gathering methods. This modern and well-arranged Techniques Used By Cybercriminals To Man In The Middle Phishing IT provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.