Cloud and access PowerPoint Presentation Templates and Google Slides
-
Applications And Websites Access With Cloud Hosting Vector Icon Ppt PowerPoint Presentation Gallery Graphics Tutorials PDF
Presenting applications and websites access with cloud hosting vector icon ppt powerpoint presentation gallery graphics tutorials pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including applications and websites access with cloud hosting vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
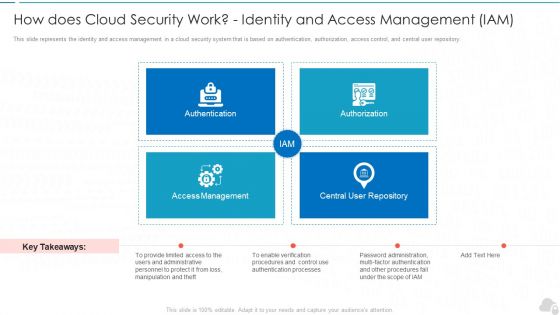
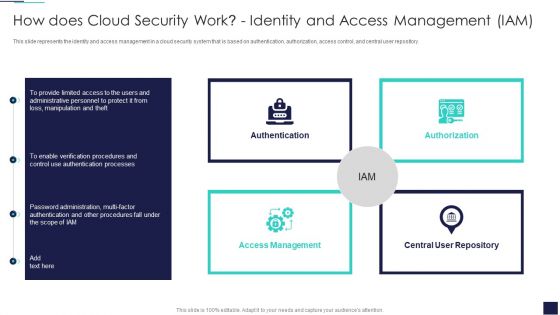
How Does Cloud Security Work Identity And Access Management Iam Cloud Computing Security IT Ppt Infographics Picture PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting how does cloud security work identity and access management iam cloud computing security it ppt infographics picture pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like authentication, authorization, access management, central user repository. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Google Cloud Console IT Accessing Resources Through Services And Across Regions And Zones Ppt Ideas Designs PDF
This slide describes how resources can be accessed on the Google Cloud platform, and they can be accessed through services and across regions and zones. Deliver an awe inspiring pitch with this creative google cloud console it accessing resources through services and across regions and zones ppt ideas designs pdf bundle. Topics like resources, cloud computing, networks, develop can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
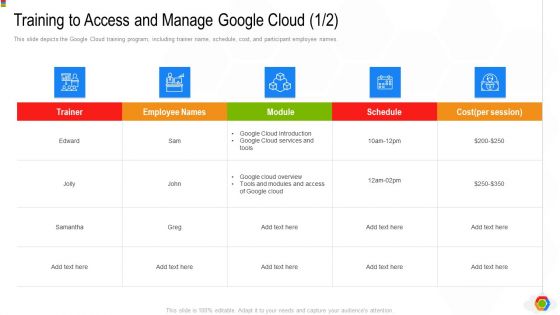
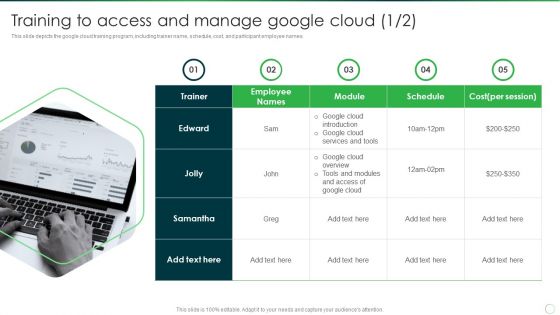
Google Cloud Console IT Training To Access And Manage Google Cloud Cost Ppt Ideas Guide PDF
This slide depicts the Google Cloud training program, including trainer name, schedule, cost, and participant employee names. Deliver an awe inspiring pitch with this creative google cloud console it training to access and manage google cloud cost ppt ideas guide pdf bundle. Topics like trainer, cost, cloud services, module, schedule can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
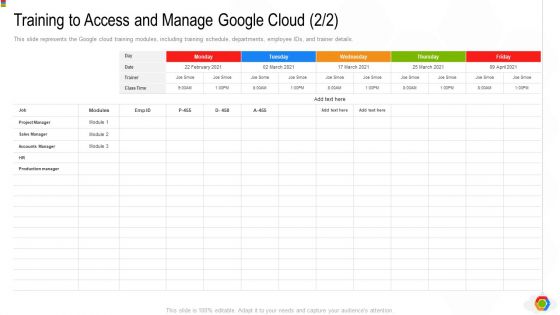
Google Cloud Console IT Training To Access And Manage Google Cloud Sales Ppt Styles Clipart PDF
This slide represents the Google cloud training modules, including training schedule, departments, employee IDs, and trainer details. Deliver and pitch your topic in the best possible manner with this google cloud console it training to access and manage google cloud sales ppt styles clipart pdf. Use them to share invaluable insights on project manager, sales manager, accounts manager, trainer and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
-
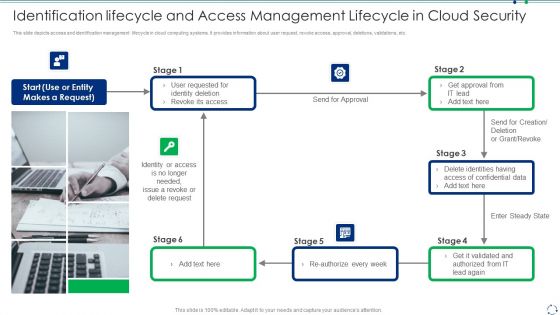
Identification Lifecycle And Access Management Lifecycle In Cloud Security Guidelines PDF
This slide depicts access and identification management lifecycle in cloud computing systems. It provides information about user request, revoke access, approval, deletions, validations, etc.Presenting identification lifecycle and access management lifecycle in cloud security guidelines pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including identity deletion, revoke its access, identity or access This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
Cloud Information Security How Does Cloud Security Work Identity And Access Management IAM Formats PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting Cloud Information Security How Does Cloud Security Work Identity And Access Management IAM Formats PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Central Repository, Access Management, Authorization Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Google Cloud Computing System Training To Access And Manage Google Cloud Infographics PDF
This slide depicts the google cloud training program, including trainer name, schedule, cost, and participant employee names. This is a Google Cloud Computing System Training To Access And Manage Google Cloud Infographics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Services And Tools, Cost, Services And Tools. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Training To Access And Manage Google Cloud Google Cloud Computing System Portrait PDF
This slide depicts the Google Cloud training program, including trainer name, schedule, cost, and participant employee names.Deliver an awe inspiring pitch with this creative Training To Access And Manage Google Cloud Google Cloud Computing System Portrait PDF bundle. Topics like Google Cloud, Introduction, Google Cloud Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
How Does Cloud Security Work Identity And Access Management IAM Professional PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. This is a How Does Cloud Security Work Identity And Access Management IAM Professional PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Accessibility, Security, Quality. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Cloud Security Assessment How Does Cloud Security Work Identity And Access Management IAM Background PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored.Presenting Cloud Security Assessment How Does Cloud Security Work Identity And Access Management IAM Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Accessibility, Knowledge, Technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
-
Cloud-Based Identify And Access Management Technique Best Practices Slides PDF
This slide shows ideal practices for IAM strategy. The purpose of this strategy is to highlight all effective practices along with concerned activities. It include practices such as defining IAM vision, building strong foundation , etc. Presenting Cloud-Based Identify And Access Management Technique Best Practices Slides PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Vision Clearly, Strong Foundation, Secure Generic Accounts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
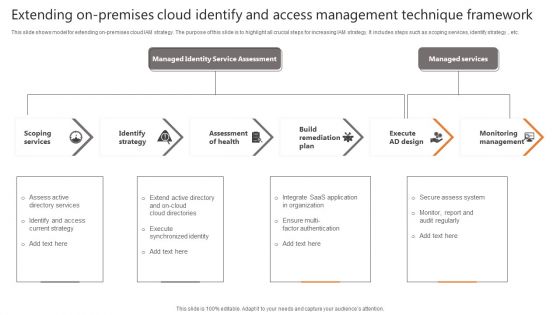
Extending On-Premises Cloud Identify And Access Management Technique Framework Formats PDF
This slide shows model for extending on-premises cloud IAM strategy. The purpose of this slide is to highlight all crucial steps for increasing IAM strategy. It includes steps such as scoping services, identify strategy , etc. Persuade your audience using this Cloud-Based Identify And Access Management Technique Best Practices Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Scoping Services, Identify Strategy, Assessment Of Health. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
Cloud Based Identify And Access Management Technique Introduction PDF
Presenting Cloud Based Identify And Access Management Technique Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cloud Based Identify, Access Management, Technique. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
-
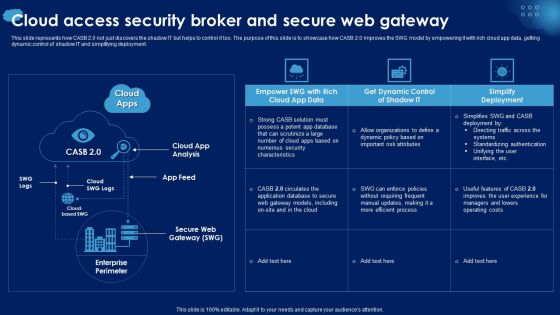
Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
-
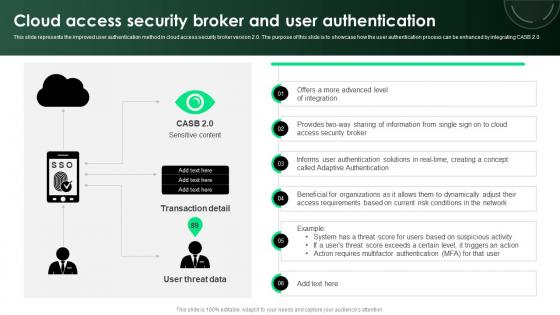
Cloud Access Security Broker And User Authentication Ppt PowerPoint Presentation File Deck PDF
This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Make sure to capture your audiences attention in your business displays with our gratis customizable Cloud Access Security Broker And User Authentication Ppt PowerPoint Presentation File Deck PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
-
Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF
This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Presenting this PowerPoint presentation, titled Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
-
CASB 2 0 IT Cloud Access Security Broker And Encryption
This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Make sure to capture your audiences attention in your business displays with our gratis customizable CASB 2 0 IT Cloud Access Security Broker And Encryption. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
-
CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway.
-
CASB 2 0 IT Cloud Access Security Broker And User Authentication
This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created CASB 2 0 IT Cloud Access Security Broker And User Authentication to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.