Clone Phishing PowerPoint Presentation Templates and Google Slides
-
Clone Phishing Attacks Preventive Measures Man In The Middle Phishing IT
This slide talks about the various steps that can be taken to prevent clone phishing attacks. These include review senders address, preview links before opening them, use a password manager, investigate spoofed replies, double check URL addresses, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Clone Phishing Attacks Preventive Measures Man In The Middle Phishing IT. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
-
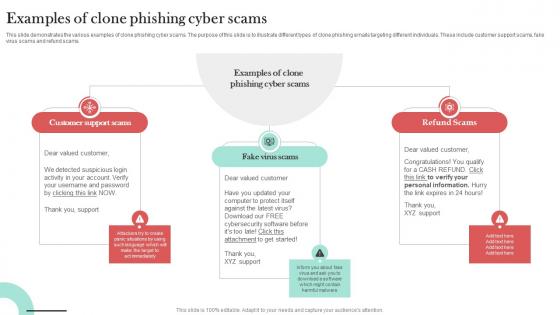
Examples Of Clone Phishing Cyber Scams Man In The Middle Phishing IT
This slide demonstrates the various examples of clone phishing cyber scams. The purpose of this slide is to illustrate different types of clone phishing emails targeting different individuals. These include customer support scams, fake virus scams and refund scams. This Examples Of Clone Phishing Cyber Scams Man In The Middle Phishing IT is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Examples Of Clone Phishing Cyber Scams Man In The Middle Phishing IT features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
-
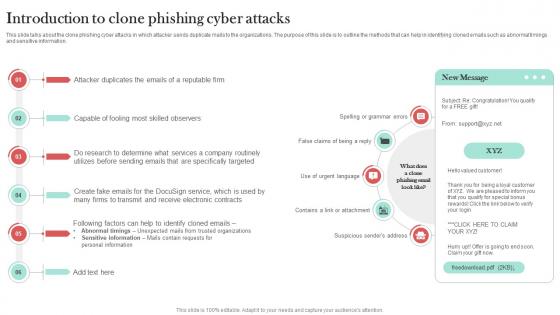
Introduction To Clone Phishing Cyber Man In The Middle Phishing IT
This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information. This Introduction To Clone Phishing Cyber Man In The Middle Phishing IT from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.