Authentication of users PowerPoint Presentation Templates and Google Slides
-
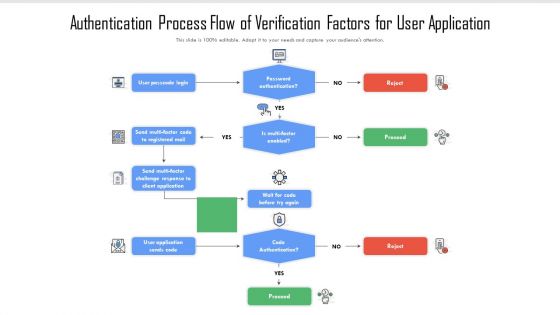
Authentication Process Flow Of Verification Factors For User Application Rules PDF
Pitch your topic with ease and precision using this authentication process flow of verification factors for user application rules pdf. This layout presents information on password authentication, code authentication, user passcode login. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
-
Authentication Process Flow Of Verification Factors For User Profile Authentication Icon Portrait PDF
Persuade your audience using this authentication process flow of verification factors for user profile authentication icon portrait pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including authentication process flow of verification factors for user profile authentication icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
User Authentication Process Flow Of Verification Factors For Smart Phone Authorization Rules PDF
Persuade your audience using this user authentication process flow of verification factors for smart phone authorization rules pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including additional authentication credential required, send authentication request with session and passcode, response returns with token . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
-
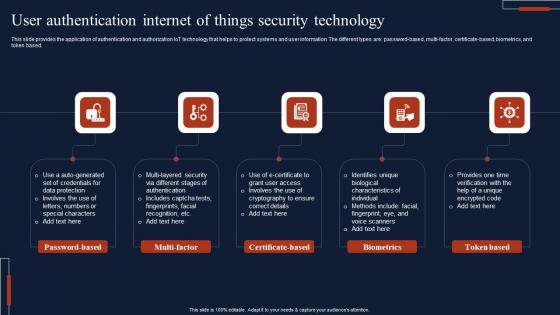
User Authentication Internet Of Things Security Technology Microsoft Pdf
This slide provides the application of authentication and authorization IoT technology that helps to protect systems and user information. The different types are password based, multi-factor, certificate-based, biometrics, and token based. Pitch your topic with ease and precision using this User Authentication Internet Of Things Security Technology Microsoft Pdf This layout presents information on Password Based, Multi Factor, Certificate Based It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.