Approaches to obtain PowerPoint Presentation Templates and Google Slides
-
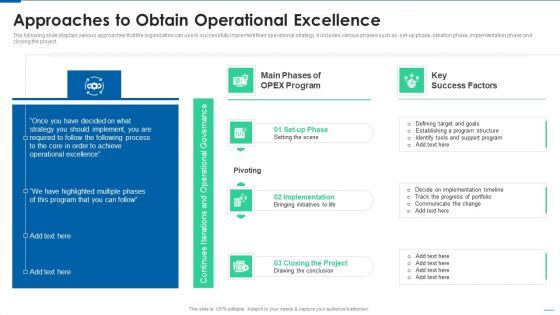
Six Sigma Continuous Process Approaches To Obtain Operational Excellence Template PDF
The following slide displays various approaches that the organization can use to successfully implement their operational strategy, it includes various phases such as set-up phase, ideation phase, implementation phase and closing the project. Deliver an awe inspiring pitch with this creative Six Sigma Continuous Process Approaches To Obtain Operational Excellence Template PDF bundle. Topics like Pivoting, Implementation, Closing Project, Key Success Factors can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
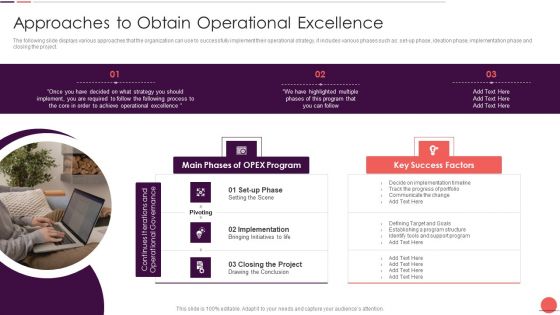
Continuous Enhancement Strategy Approaches To Obtain Operational Excellence Microsoft PDF
The following slide displays various approaches that the organization can use to successfully implement their operational strategy, it includes various phases such as set-up phase, ideation phase, implementation phase and closing the project. This is a Continuous Enhancement Strategy Approaches To Obtain Operational Excellence Microsoft PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Implementation, Project, Key Success Factors, Achieve Operational Excellence, Process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
Playbook For Improving Production Process Approaches To Obtain Operational Infographics PDF
The following slide displays various approaches that the organization can use to successfully implement their operational strategy, it includes various phases such as set-up phase, ideation phase, implementation phase and closing the project. This is a Playbook For Improving Production Process Approaches To Obtain Operational Infographics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Main Phases, OPEX Program, Key Success Factors, Implementation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
-
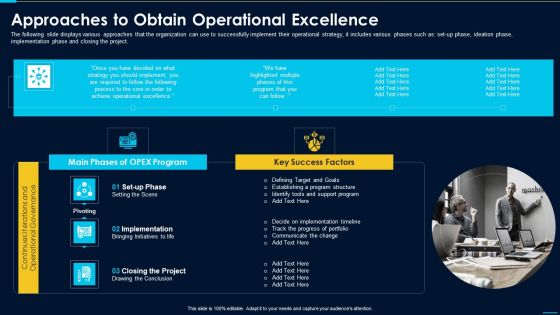
Approaches To Obtain Operational Excellence Template PDF
The following slide displays various approaches that the organization can use to successfully implement their operational strategy, it includes various phases such as set up phase, ideation phase, implementation phase and closing the project.Deliver an awe inspiring pitch with this creative approaches to obtain operational excellence template pdf bundle. Topics like establishing a program structure, identify tools and support program , decide on implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
-
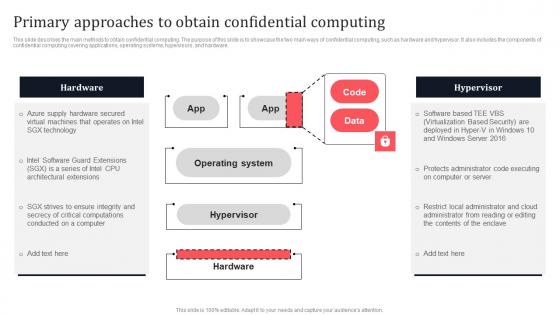
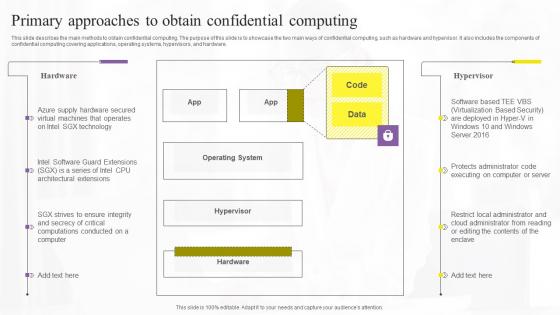
Confidential Computing System Technology Primary Approaches To Obtain Confidential Sample PDF
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Do you have an important presentation coming up Confidential Computing System Technology Primary Approaches To Obtain Confidential Sample PDF Are you looking for something that will make your presentation stand out from the rest Look no further than Confidential Computing System Technology Primary Approaches To Obtain Confidential Sample PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Confidential Computing System Technology Primary Approaches To Obtain Confidential Sample PDF today and make your presentation stand out from the rest.
-
Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Primary Approaches To Obtain Confidential Computing Secure Multi Party Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
-
Primary Approaches To Obtain Confidential Computing Technologies Guidelines Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Primary Approaches To Obtain Confidential Computing Technologies Guidelines Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
-
Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf
This slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Slidegeeks is here to make your presentations a breeze with Primary Approaches To Obtain Confidential Computing Secure Computing Framework Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first