Vulnerability Dashboard
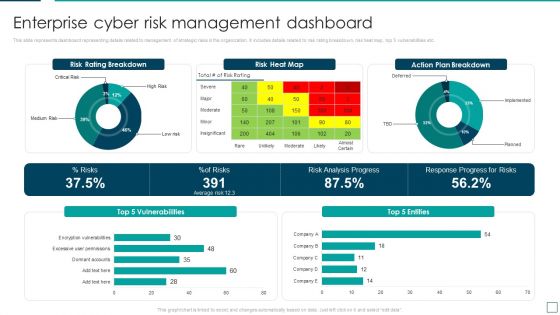
Strategic Risk Management And Mitigation Plan Enterprise Cyber Risk Management Dashboard Diagrams PDF
This slide represents dashboard representing details related to management of strategic risks in the organization. It includes details related to risk rating breakdown, risk heat map, top 5 vulnerabilities etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Strategic Risk Management And Mitigation Plan Enterprise Cyber Risk Management Dashboard Diagrams PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Company Risk Assessment Plan Financial Risk Management Key Metrics Dashboard Brochure PDF
This slide covers dashboard to manage and monitor financial risks faced by the enterprise. It includes details related to kpis such as risk heat map, risk rating breakdown, top 5 vulnerabilities etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straight forward Company Risk Assessment Plan Financial Risk Management Key Metrics Dashboard Brochure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Company Risk Assessment Plan Financial Risk Management Key Metrics Dashboard Brochure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
Operational Risk Assessment And Management Plan Enterprise Cyber Risk Management Dashboard Icons PDF
This slide represents dashboard representing details related to management of strategic risks in the organization. It includes details related to risk rating breakdown, risk heat map, top 5 vulnerabilities etc. Slidegeeks is here to make your presentations a breeze with Operational Risk Assessment And Management Plan Enterprise Cyber Risk Management Dashboard Icons PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
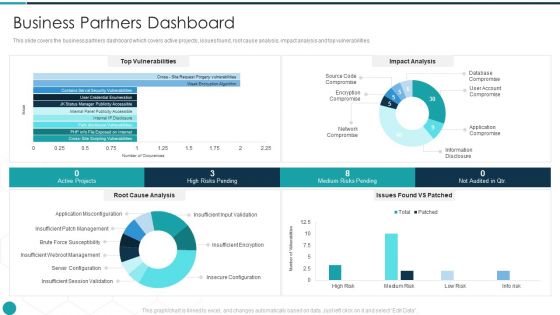
Upgrade Management Of Complex Business Associates Business Partners Dashboard Brochure PDF
This slide covers the business partners dashboard which covers active projects, issues found, root cause analysis, impact analysis and top vulnerabilities. Deliver and pitch your topic in the best possible manner with this upgrade management of complex business associates business partners dashboard brochure pdf. Use them to share invaluable insights on business partners dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Risk Management Dashboard For Information Security Summary PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Risk Management Dashboard For Information Security Summary PDF. Use them to share invaluable insights on Rating Breakdown, Vulnerabilities, Response Progress and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Strategies To Mitigate Cyber Security Risks Dashboard Cyber Risk Management Ppt Professional Display PDF
Presenting this set of slides with name strategies to mitigate cyber security risks dashboard cyber risk management ppt professional display pdf. The topics discussed in these slides are risks threshold top 5 vulnerabilities, risk rating breakdown, action plan breakdown, risk heat map. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

International Online Security Dashboard With Incident Management Ppt PowerPoint Presentation File Background PDF
Presenting this set of slides with name international online security dashboard with incident management ppt powerpoint presentation file background pdf. The topics discussed in these slides are management, vulnerabilities, cybersecurity. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
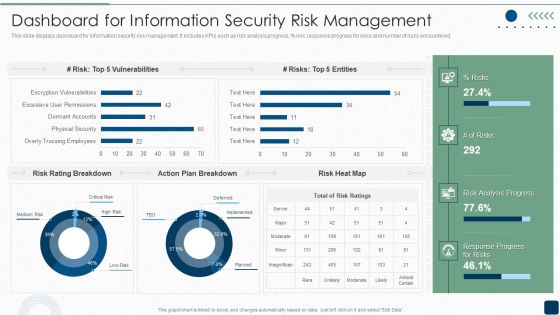
ISO 27001 Certification Procedure Dashboard For Information Security Risk Management Sample PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, persent risk, response progress for risks and number of risks encountered.Deliver an awe inspiring pitch with this creative ISO 27001 Certification Procedure Dashboard For Information Security Risk Management Sample PDF bundle. Topics like Vulnerabilities, Rating Breakdown, Plan Breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
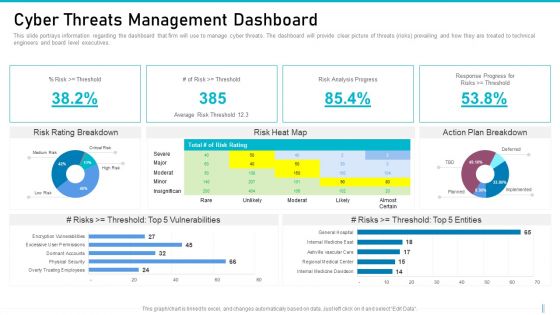
Risk Management For Organization Essential Assets Cyber Threats Management Dashboard Graphics PDF
This slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver and pitch your topic in the best possible manner with this risk management for organization essential assets cyber threats management dashboard graphics pdf. Use them to share invaluable insights on risk analysis, vulnerabilities, entities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
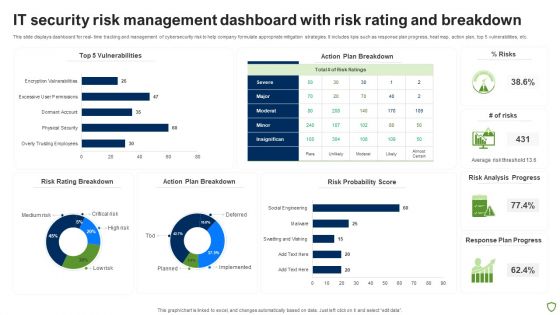
IT Security Risk Management Dashboard With Risk Rating And Breakdown Pictures PDF
This slide displays dashboard for real- time tracking and management of cybersecurity risk to help company formulate appropriate mitigation strategies. It includes kpis such as response plan progress, heat map, action plan, top 5 vulnerabilities, etc. Pitch your topic with ease and precision using this IT Security Risk Management Dashboard With Risk Rating And Breakdown Pictures PDF. This layout presents information on Risk Rating Breakdown, Action Plan Breakdown, Risk Probability Score, Risk Analysis Progress. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
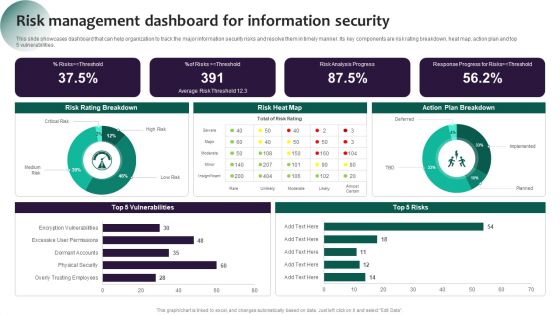
Information Systems Security And Risk Management Plan Risk Management Dashboard For Information Security Pictures PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Information Systems Security And Risk Management Plan Risk Management Dashboard For Information Security Pictures PDF from Slidegeeks and deliver a wonderful presentation.
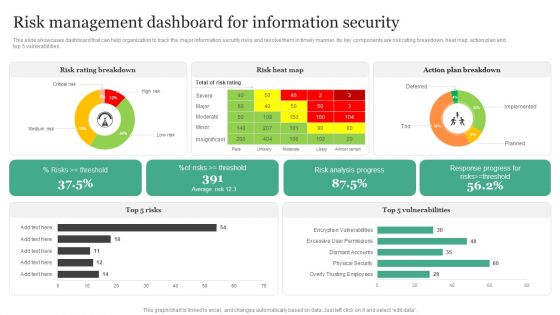
Risk Management Dashboard For Information Security Information Security Risk Administration Diagrams PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities.Create an editable Risk Management Dashboard For Information Security Information Security Risk Administration Diagrams PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Risk Management Dashboard For Information Security Information Security Risk Administration Diagrams PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Developing IT Security Strategy Risk Management Dashboard For Information Security Mockup PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities. Welcome to our selection of the Developing IT Security Strategy Risk Management Dashboard For Information Security Mockup PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
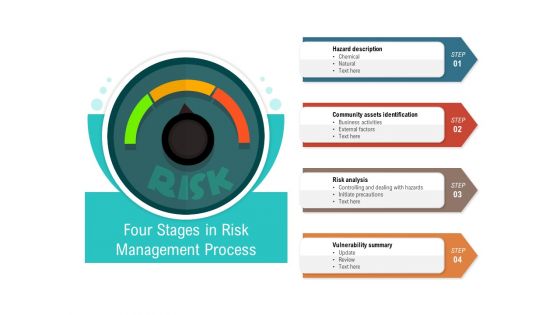
Four Stages In Risk Management Process Ppt PowerPoint Presentation Professional Grid PDF
Persuade your audience using this four stages in risk management process ppt powerpoint presentation professional grid pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including hazard description, community assets identification, risk analysis, vulnerability summary. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Enterprise Integration Solution Diagram Powerpoint Guide
This is a enterprise integration solution diagram powerpoint guide. This is a six stage process. The stages in this process are policy management, log management, vulnerability assessment, web application scanning, file integrity monitoring, vulnerability management, discovery, protection, monitoring, reporting, security, risk and compliance.
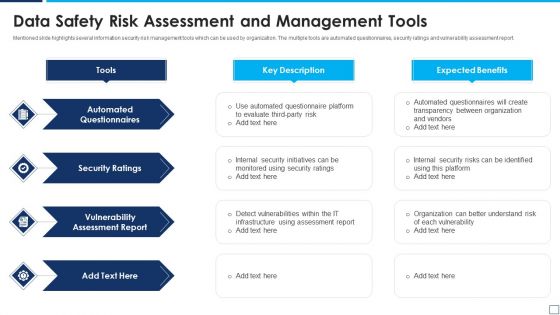
Data Safety Risk Assessment And Management Tools Demonstration PDF
Mentioned slide highlights several information security risk management tools which can be used by organization. The multiple tools are automated questionnaires, security ratings and vulnerability assessment report. Presenting data safety risk assessment and management tools demonstration pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including automated questionnaires, security ratings, vulnerability assessment report. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
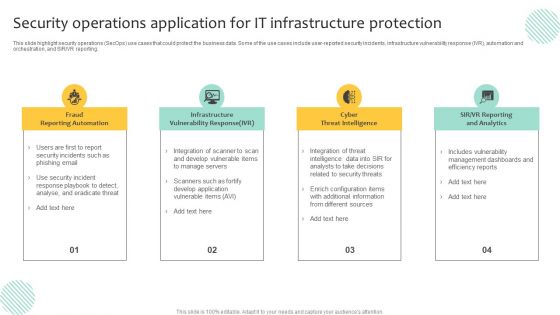
Security Operations Application For IT Infrastructure Protection Template PDF
This slide highlight security operations SecOps use cases that could protect the business data. Some of the use cases include user-reported security incidents, infrastructure vulnerability response IVR, automation and orchestration, and SIR or VR reporting. Presenting Security Operations Application For IT Infrastructure Protection Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infrastructure Vulnerability Response, Cyber Threat Intelligence, Fraud Reporting Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
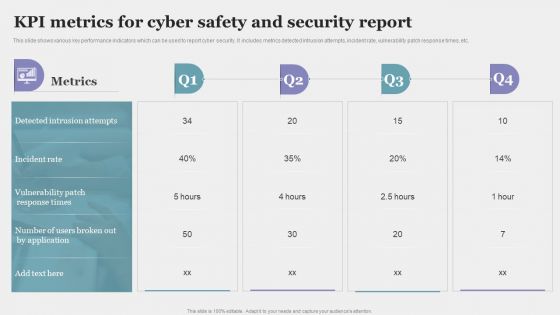
KPI Metrics For Cyber Safety And Security Report Elements PDF
This slide shows various key performance indicators which can be used to report cyber security. It includes metrics detected intrusion attempts, incident rate, vulnerability patch response times, etc. Showcasing this set of slides titled KPI Metrics For Cyber Safety And Security Report Elements PDF. The topics addressed in these templates are Incident Rate, Application, Metrics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
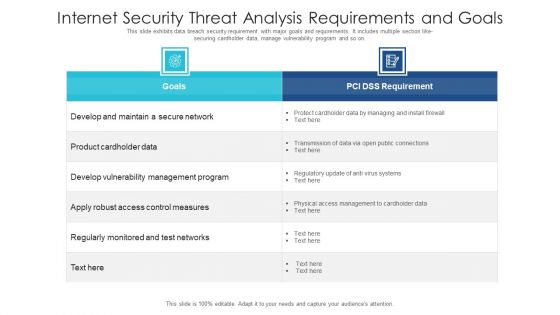
Internet Security Threat Analysis Requirements And Goals Ideas PDF
This slide exhibits data breach security requirement with major goals and requirements. It includes multiple section like- securing cardholder data, manage vulnerability program and so on. Showcasing this set of slides titled internet security threat analysis requirements and goals ideas pdf. The topics addressed in these templates are internet security threat analysis requirements and goals. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
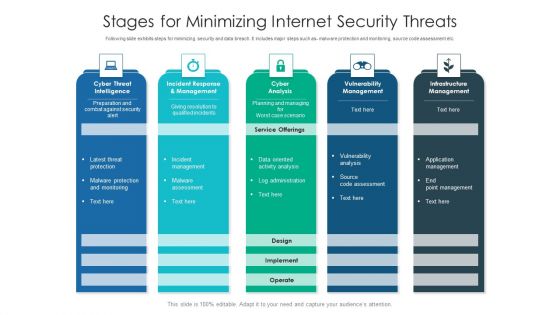
Stages For Minimizing Internet Security Threats Ideas PDF
Following slide exhibits steps for minimizing security and data breach. It includes major steps such as- malware protection and monitoring, source code assessment etc. Pitch your topic with ease and precision using this stages for minimizing internet security threats ideas pdf. This layout presents information on infrastructure management, cyber analysis, vulnerability management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Risk Management Model For Data Introducing Information Security Risk Assessment Process Sample PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. This is a Risk Management Model For Data Introducing Information Security Risk Assessment Process Sample PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Incident Reports, Characterize System, Identify Vulnerabilities, Assigned Remediation Measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Distributed Computing Security Of Data And Networks In Edge Computing Ideas PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable.This is a Distributed Computing Security Of Data And Networks In Edge Computing Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Conduct Analytics, Devices Themselves, Vulnerability You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
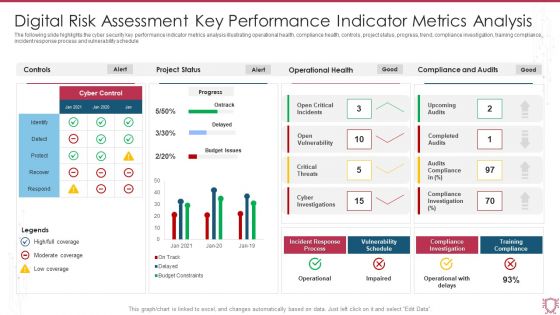
Digital Risk Assessment Key Performance Indicator Metrics Analysis Infographics PDF
The following slide highlights the cyber security key performance indicator metrics analysis illustrating operational health, compliance health, controls, project status, progress, trend, compliance investigation, training compliance, incident response process and vulnerability schedule. Showcasing this set of slides titled Digital Risk Assessment Key Performance Indicator Metrics Analysis Infographics PDF. The topics addressed in these templates are Project Status, Operational Health, Compliance And Audits. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Real Time Assessment Of Security Threats Fully Managed Service Model Demonstration PDF
This slide covers the SIEM as a service model wherein all the steps are taken care by our company and the client just have to provide us the relevant data. Deliver an awe inspiring pitch with this creative real time assessment of security threats fully managed service model demonstration pdf bundle. Topics like threat and vulnerability management processes, reporting, retention, correlation, collection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
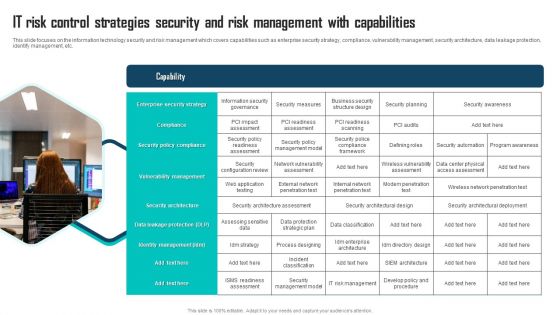
IT Risk Control Strategies Security And Risk Management With Capabilities Ppt Professional Graphics Example PDF
This slide focuses on the information technology security and risk management which covers capabilities such as enterprise security strategy, compliance, vulnerability management, security architecture, data leakage protection, identify management, etc. Presenting IT Risk Control Strategies Security And Risk Management With Capabilities Ppt Professional Graphics Example PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Enterprise Security Strategy, Compliance, Security Policy Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Reinforcement Learning Unveiled Challenges Of Using Reinforcement Learning Models AI SS V
This slide showcases challenges of using reinforcement learning models, to make developers aware about uncertain situations. It provides details about vulnerability to attacks, inaccuracies, data quality, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Reinforcement Learning Unveiled Challenges Of Using Reinforcement Learning Models AI SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Reinforcement Learning Unveiled Challenges Of Using Reinforcement Learning Models AI SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
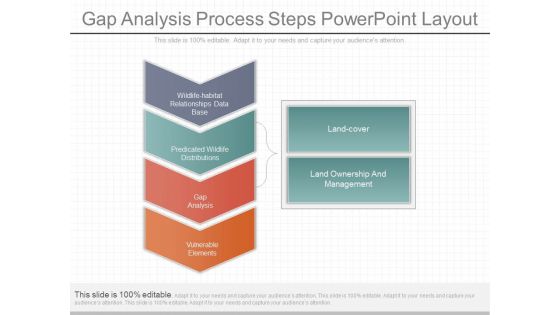
Gap Analysis Process Steps Powerpoint Layout
This is a gap analysis process steps powerpoint layout. This is a six stage process. The stages in this process are wildlife habitat relationships data base, predicated wildlife distributions, gap analysis, vulnerable elements, land cover, land ownership and management.

Enterprise Risk Management And Mitigation Program Designs PDF
This slide represents dashboard representing details related to management of strategic risks in the organization. It includes details related to risk rating breakdown, risk heat map, top 5 vulnerabilities etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Enterprise Risk Management And Mitigation Program Designs PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Enterprise Risk Management And Mitigation Program Designs PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Comparative Analysis Of Standard And Distributed Ledger Security Mockup Pdf
This slide analyses comparison of standard and blockchain security aimed at assessing respective security considerations to prevent attacks against both paradigms. The basis of challenges are denial of service, endpoint security, intentional misuse, code vulnerabilities and data protection Pitch your topic with ease and precision using this Comparative Analysis Of Standard And Distributed Ledger Security Mockup Pdf This layout presents information on Denial Of Service, Endpoint Security, Code Vulnerabilities It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
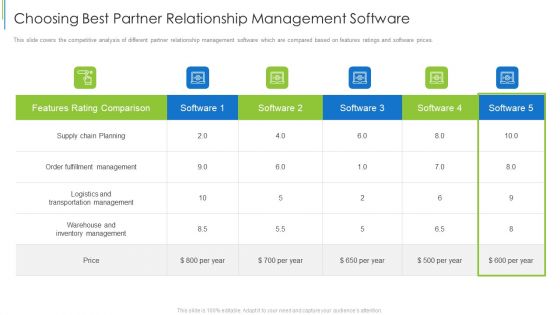
Choosing Best Partner Relationship Management Software Ideas PDF
This slide covers the business partners dashboard which covers active projects, issues found, root cause analysis, impact analysis and top vulnerabilities. Deliver an awe inspiring pitch with this creative choosing best partner relationship management software ideas pdf bundle. Topics like impact analysis, vulnerabilities, root cause analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
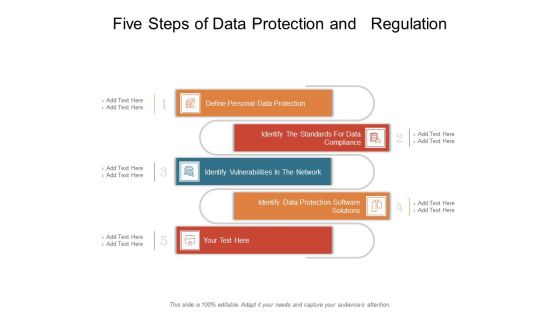
Five Steps Of Data Protection And Regulation Ppt PowerPoint Presentation File Tips PDF
Presenting this set of slides with name five steps of data protection and regulation ppt powerpoint presentation file tips pdf. This is a five stage process. The stages in this process are define personal data protection, identify the standards for data compliance, identify vulnerabilities in the network, identify data protection software solutions. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Nine Steps Of Data Protection And Regulation Ppt PowerPoint Presentation Slides Graphics PDF
Presenting this set of slides with name nine steps of data protection and regulation ppt powerpoint presentation slides graphics pdf. This is a nine stage process. The stages in this process are define personal data protection, identify the standards for data compliance, identify vulnerabilities in the network, identify data protection software solutions. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
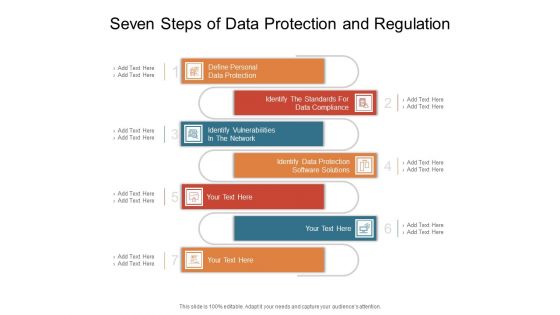
Seven Steps Of Data Protection And Regulation Ppt PowerPoint Presentation Show Example File PDF
Presenting this set of slides with name seven steps of data protection and regulation ppt powerpoint presentation show example file pdf. This is a seven stage process. The stages in this process are define personal data protection, identify the standards for data compliance, identify vulnerabilities in the network, identify data protection software solutions. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
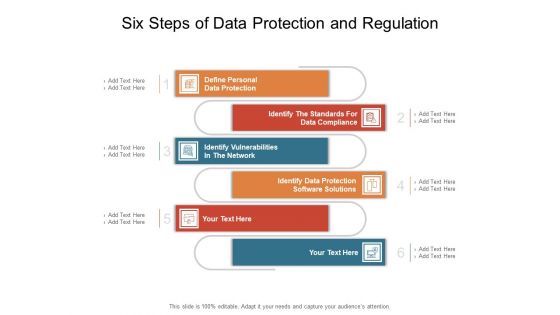
Six Steps Of Data Protection And Regulation Ppt PowerPoint Presentation Graphics PDF
Presenting this set of slides with name six steps of data protection and regulation ppt powerpoint presentation graphics pdf. This is a six stage process. The stages in this process are define personal data protection, identify the standards for data compliance, identify vulnerabilities in the network, identify data protection software solutions. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Three Steps Of Data Protection And Regulation Ppt PowerPoint Presentation Outline Files PDF
Presenting this set of slides with name three steps of data protection and regulation ppt powerpoint presentation outline files pdf. This is a three stage process. The stages in this process are define personal data protection, identify the standards for data compliance, identify vulnerabilities in the network, identify data protection software solutions. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Business Project Management Program Hazards Assessment Icons PDF
The following slide provide a risk management dashboard which helps business and organisation to identify the error levels and take necessary actions accordingly. Key elements are risk heat map, vulnerabilities, action plan breakdown, risk rating etc.Showcasing this set of slides titled Business Project Management Program Hazards Assessment Icons PDF. The topics addressed in these templates are Average Risk Threshold, Risk Threshold. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
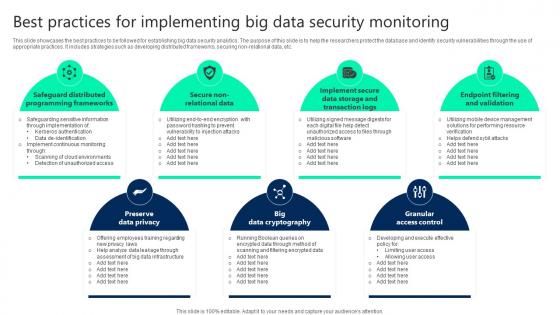
Best Practices For Implementing Big Data Security Monitoring Sample pdf
This slide showcases the best practices to be followed for establishing big data security analytics. The purpose of this slide is to help the researchers protect the database and identify security vulnerabilities through the use of appropriate practices. It includes strategies such as developing distributed frameworks, securing non-relational data, etc. Showcasing this set of slides titled Best Practices For Implementing Big Data Security Monitoring Sample pdf. The topics addressed in these templates are Preserve Data Privacy, Big Data Cryptography, Granular Access Control. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Multiple Challenges Of Business Cyber Threat Prevention Sample PDF
The following slide represent the statistical data of various cyber safety challenges reported by business and organizations which helps to determine the most vulnerable one. Major areas are information security, business agility, automation, integration, etc. Showcasing this set of slides titled Multiple Challenges Of Business Cyber Threat Prevention Sample PDF. The topics addressed in these templates are Key Takeaways, Cyber Safety, Prevention. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
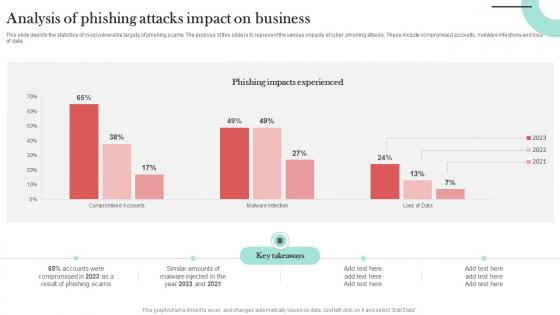
Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT
This slide depicts the statistics of most vulnerable targets of phishing scams. The purpose of this slide is to represent the various impacts of cyber phishing attacks. These include compromised accounts, malware infections and loss of data. If you are looking for a format to display your unique thoughts, then the professionally designed Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Empowering The Future Security Issues In IoT Based Smart Grid IoT SS V
This slide exhibits security issues and vulnerabilities in IoT-based smart grids that may expose sensitive information to unauthorized parties. It covers issues such as data tampering, cyberattack, privacy issue, and identity spoofing. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Empowering The Future Security Issues In IoT Based Smart Grid IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Cloud Computing Configuration Management Audit Checklist Professional PDF
This slide covers cloud infrastructure management audit checklist. It involves data encryption, security controls, tested visibility, fully independent data centres, customer penetration and vulnerability.Presenting Cloud Computing Configuration Management Audit Checklist Professional PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Management, Customer, Data Centres. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Fundamental Concepts Of Ethical Hacking Ppt Slides Outfit PDF
This slide represents the fundamental concepts of ethical hacking, such as staying legal, defining the scope, reporting vulnerabilities, and respecting data sensitivity. This is a fundamental concepts of ethical hacking ppt slides outfit pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like stay legal, report vulnerabilities, define the scope, respect data sensitivity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Interpretation And Analysis Playbook Business Intelligence And Predictive Analytics Challenges Template PDF
This template covers the problems while implementing BI and predictive analytics in the organization. The challenges are undefined KPIs and metrics, and unable to hire right data science talent. Presenting data interpretation and analysis playbook business intelligence and predictive analytics challenges template pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like security vulnerabilities, operationalizing, perform analysis, deployed. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda For Risk Management Model For Data Security Structure PDF
This is a Agenda For Risk Management Model For Data Security Structure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information Security, Effectively Managing, Organizational Risks Arising, Threats And Vulnerabilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Analysis Of Comparative Analysis Of Cloud And Traditional Computing Data Storage Guidelines PDF
This slide enable the managers to analyse the difference among various categories of cloud and traditional data storage system. It compares categories such as data recovery, privacy, price, expandability, data usage etc. Showcasing this set of slides titled Analysis Of Comparative Analysis Of Cloud And Traditional Computing Data Storage Guidelines PDF. The topics addressed in these templates are Provides Less, Because Vulnerable, Expandability. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Information Visualizations Playbook Business Intelligence And Predictive Analytics Challenges Icons PDF
This template covers the problems while implementing BI and predictive analytics in the organization. The challenges are undefined KPIs and metrics, and unable to hire right data science talent. Presenting Information Visualizations Playbook Business Intelligence And Predictive Analytics Challenges Icons PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Raw Data Organized, Security Vulnerabilities, Perform Analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
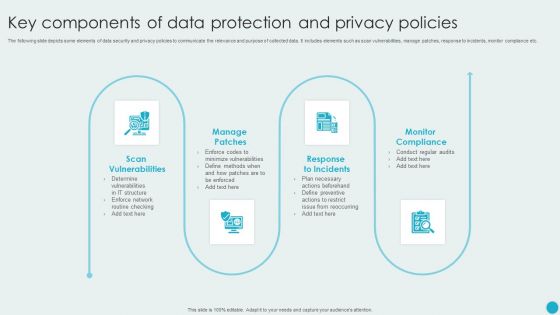
Key Components Of Data Protection And Privacy Policies Graphics PDF
The following slide depicts some elements of data security and privacy policies to communicate the relevance and purpose of collected data. It includes elements such as scan vulnerabilities, manage patches, response to incidents, monitor compliance etc. Presenting Key Components Of Data Protection And Privacy Policies Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Patches, Response To Incidents, Monitor Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Client Side Encryption To Protect Client Side Encryption PPT Example
This slide discusses client-side encryption to protect the data after storing it in the cloud network. This slide also highlights the importance of client-side encryption in different scenarios, such as secure collaboration, protection against cloud provider vulnerabilities, etc. There are so many reasons you need a Client Side Encryption To Protect Client Side Encryption PPT Example. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Cloud Intelligence Framework For Application Consumption Financial Losses To The Organizations Due To Security Issues Mockup PDF
The slide provides total financial losses from the year 2017 to 2021 reported by the organizations in United states along with the key reasons behind those losses. Deliver an awe inspiring pitch with this creative cloud intelligence framework for application consumption financial losses to the organizations due to security issues mockup pdf bundle. Topics like security vulnerabilities, primary reasons for the growing, physical theft of a data-carrying device, 2016 to 2020 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Software Risk Assessment Tools And Techniques Architecture Ppt PowerPoint Presentation Gallery Template PDF
This slide depicts software risk assessment tools and techniques framework. It includes threat database, threat data, compliance management, asset vulnerabilities, asset register etc. Persuade your audience using this Software Risk Assessment Tools And Techniques Architecture Ppt PowerPoint Presentation Gallery Template PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Assessment Tool, Risk Control Tools, Risk Reporting, Risk Calculation, Asset Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

It Security Assessment Techniques Framework Introduction PDF
The following slide represents the security assessment of technological assets to assist IT team in improving the data structure. It includes key elements such as risk identification, security threat, vulnerabilities, impact analysis, risk level, controllable actions etc. Persuade your audience using this It Security Assessment Techniques Framework Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Impact Analysis, Risk Level, Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
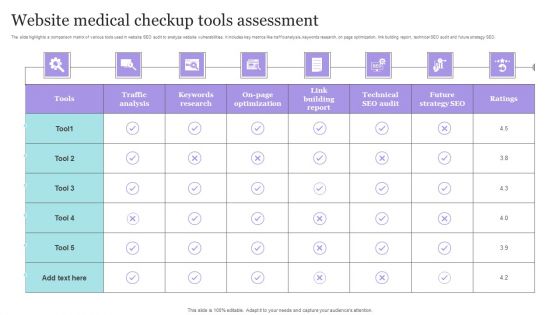
Website Medical Checkup Tools Assessment Elements PDF
The slide highlights a comparison matrix of various tools used in website SEO audit to analyze website vulnerabilities. It includes key metrics like traffic analysis, keywords research, on page optimization, link building report, technical SEO audit and future strategy SEO. Pitch your topic with ease and precision using this Website Medical Checkup Tools Assessment Elements PDF. This layout presents information on On Page Optimization, Traffic Analysis, Future Strategy SEO. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Building Trust With IoT Security Intrusion Detection Using AI And ML In IoT Ecosystem IoT SS V
This slide provides information on intrusion detection system that helps to monitor and analyse user data, networks and services to detect vulnerabilities. It includes three stages such as monitoring stage, analysing stage and detection stage. This Building Trust With IoT Security Intrusion Detection Using AI And ML In IoT Ecosystem IoT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Building Trust With IoT Security Intrusion Detection Using AI And ML In IoT Ecosystem IoT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

 Home
Home