Timeline Risk

Evolving BI Infrastructure How Firm Handle Various Insider Threats At Workplace Topics PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a evolving bi infrastructure how firm handle various insider threats at workplace topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan How Firm Handle Various Insider Threats At Workplace Elements PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a developing firm security strategy plan how firm handle various insider threats at workplace elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Types Of Threats In Data Security Ppt Layouts File Formats PDF
This slide depicts the main types of threats in data security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a information security types of threats in data security ppt layouts file formats pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber attack. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Addressing Internal And External Clipart PDF
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. This is a mitigating cybersecurity threats and vulnerabilities addressing internal and external clipart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internal sources, external sources, targeted intelligence, malware intelligence, reputation intelligence. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Addressing Ways To Handling Professional PDF
This slide provides details regarding handling financial threats by safeguarding financial stability and protecting the firm from costly effects that financial threats can have. Presenting mitigating cybersecurity threats and vulnerabilities addressing ways to handling professional pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like cash requirement, key financial statements, overheads analysis, currency hedging. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
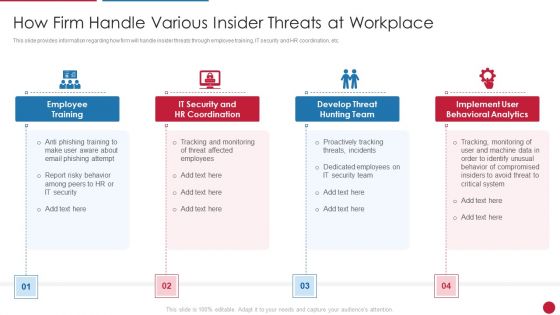
Facilitating IT Intelligence Architecture How Firm Handle Various Insider Threats At Workplace Formats PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a Facilitating IT Intelligence Architecture How Firm Handle Various Insider Threats At Workplace Formats PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employee Training, Develop Threat Hunting Team, Implement User Behavioral Analytics You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security Plan Best Practices To Defend Against Threats Icons PDF
This slide represents cyber security strategy best practices to defend against threats such a development of insider threat program, training employees, maintaining compliance etc. Persuade your audience using this IT Security Plan Best Practices To Defend Against Threats Icons PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Updating Systems And Software, Data Backup, Maintaining Compliance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
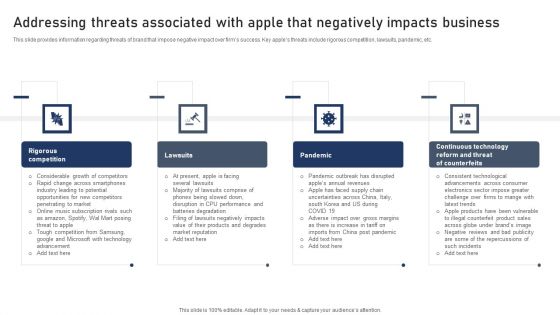
Discovering Apples Billion Dollar Branding Secret Addressing Threats Associated With Apple Negatively Impacts Portrait PDF
This slide provides information regarding threats of brand that impose negative impact over firms success. Key apples threats include rigorous competition, lawsuits, pandemic, etc. Boost your pitch with our creative Discovering Apples Billion Dollar Branding Secret Addressing Threats Associated With Apple Negatively Impacts Template PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Addressing Threats Associated With Apple That Negatively Impacts Business Ideas PDF
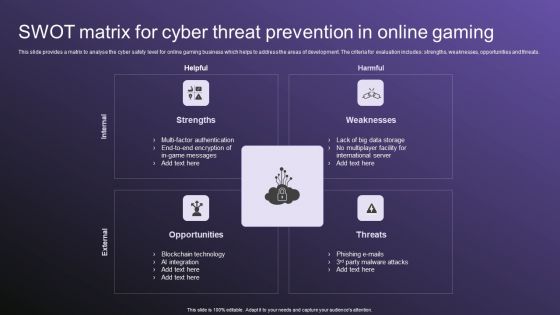
SWOT Matrix For Cyber Threat Prevention In Online Gaming Download PDF
This slide provides a matrix to analyse the cyber safety level for online gaming business which helps to address the areas of development. The criteria for evaluation includes strengths, weaknesses, opportunities and threats. Persuade your audience using this SWOT Matrix For Cyber Threat Prevention In Online Gaming Download PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strengths, Weaknesses, Threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Venture Capital Fund Addressing The Major Problems Faced By Customers Demonstration PDF
This slide displays information about the pain points faced by customers. Problems covered in the slide are outdated data, and low engagement. Deliver an awe inspiring pitch with this creative Venture Capital Fund Addressing The Major Problems Faced By Customers Demonstration PDF bundle. Topics like Outdated Data, Poor Engagement, Poor Data Quality, Poor Customer Relations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

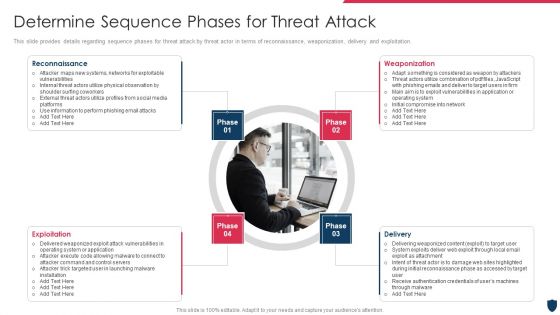
cyber security administration in organization determine sequence phases for threat attack infographics pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber security administration in organization determine sequence phases for threat attack infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internal, threat, perform, phishing, combination . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
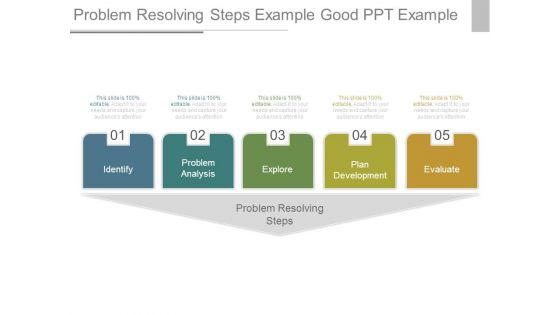
Problem Resolving Steps Example Good Ppt Example
This is a problem resolving steps example good ppt example. This is a five stage process. The stages in this process are identify, problem analysis, explore, plan development, evaluate, problem resolving steps.

Five Steps To Effective Problem Solving Ppt Powerpoint Slides
This is a five steps to effective problem solving ppt powerpoint slides. This is a five stage process. The stages in this process are describe, decide, define, monitor, brainstorm.

Digital Advertising And Promotion One Stop Solution For All Problems Designs PDF
Purpose of the following slide is to show the solution for multiple problems that are identified by the organization , these solution can be creating engaging software for organization, having team of experienced professionals and providing customer with integrated solution. This is a digital advertising and promotion one stop solution for all problems designs pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like engaging and analytical, website engagement, team innovators, digital marketing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Project Security Administration IT Various Ways To Manage Project Safety By Managing Threats Contd Sample PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of active remediation implementation, deactivating orphaned user accounts, etc. This is a project security administration it various ways to manage project safety by managing threats contd sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like deactivate orphaned user accounts, develop strict access management policies, implement active remediation, investigate remote access policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cybersecurity Types Of Latest Threats In Electronic Information Security Ppt Portfolio Icon PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. This is a cybersecurity types of latest threats in electronic information security ppt portfolio icon pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like dridex malware, romance scams, emotet malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
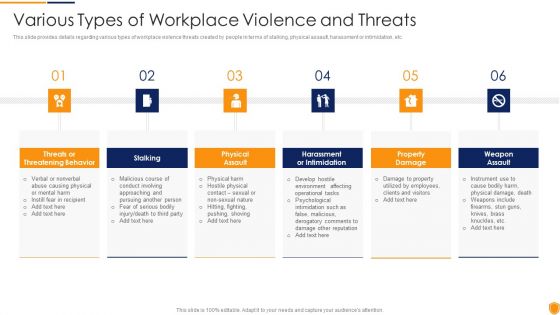
Mitigating Cybersecurity Threats And Vulnerabilities Various Types Of Workplace Download PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a mitigating cybersecurity threats and vulnerabilities various types of workplace download pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threatening behavior, stalking, assault harassment, property damage. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Incident Management Various Types Of Workplace Violence And Threats Infographics PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. This is a cyber safety incident management various types of workplace violence and threats infographics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like stalking, physical assault, harassment or intimidation, property damage, weapon assault . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
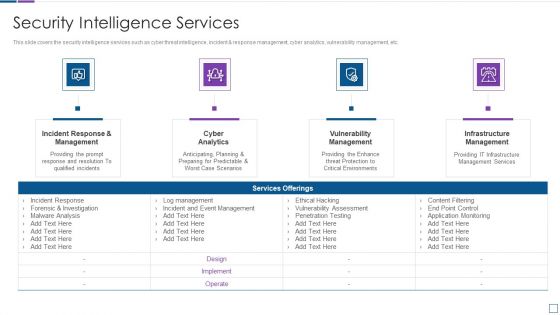
Real Time Assessment Of Security Threats Security Intelligence Services Formats PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting real time assessment of security threats security intelligence services formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
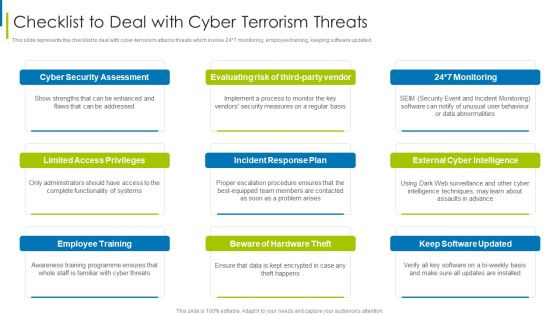
Cyber Terrorism Assault Checklist To Deal With Cyber Terrorism Threats Guidelines PDF
This slide represents the checklist to deal with cyber-terrorism attacks threats which involve 24 7 monitoring, employee training, keeping software updated.This is a cyber terrorism assault checklist to deal with cyber terrorism threats guidelines pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like German Businesses, Average Loss , Cyber Terrorist Attack You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack Threat Actors Supporting Russia And Ukraine Brochure PDF
This slide shows the threat actors supporting Russia and Ukraine, such as hacker organization Anonymous, Cyber Partisan hacking organization, and Conti ransomware gang.This is a data wiper spyware attack threat actors supporting russia and ukraine brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like encrypting data on servers, hacking organization, collective planned You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
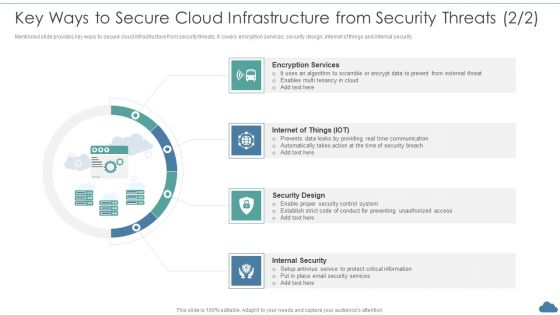
Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF
Mentioned slide provides key ways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Encryption Services, Security Design, Internal Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Various Types Of Workplace Violence And Threats Ppt Pictures Outline PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. Present like a pro with Various Types Of Workplace Violence And Threats Ppt Pictures Outline PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
cyber security administration in organization determine sequence phases for threat attack access inspiration pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Presenting cyber security administration in organization determine sequence phases for threat attack access inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communication, platform, access, compromised, session . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
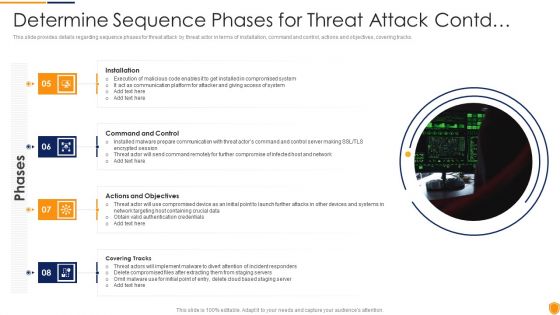
Determine Sequence Phases For Mitigating Cybersecurity Threats And Vulnerabilities Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. This is a determine sequence phases for mitigating cybersecurity threats and vulnerabilities inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

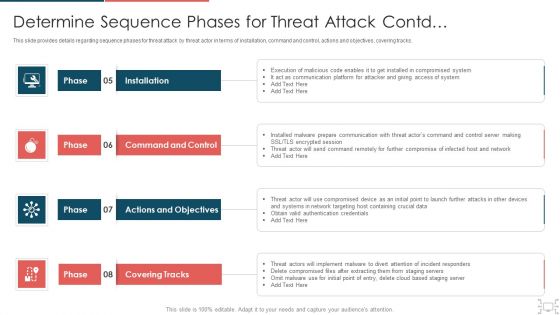
Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Contd Control Inspiration PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber safety incident management determine sequence phases for threat attack contd control inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, covering tracks, actions and objectives, command and control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cyber Safety Incident Management Determine Sequence Phases For Threat Attack Rules PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting cyber safety incident management determine sequence phases for threat attack rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, exploitation, delivery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF
The Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
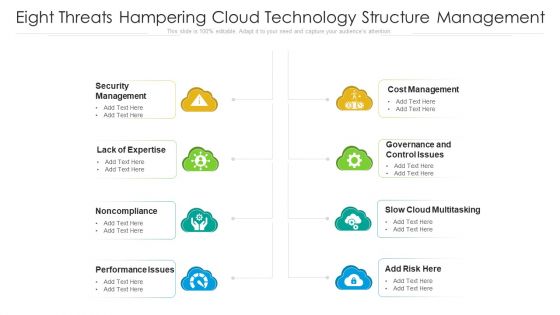
Eight Threats Hampering Cloud Technology Structure Management Ppt PowerPoint Presentation Gallery Slideshow PDF
Presenting eight threats hampering cloud technology structure management ppt powerpoint presentation gallery slideshow pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including performance issues, cost management, security management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data Icons Slide Inspiration PDF
Introducing our well designed Executing security management program to mitigate threats and safeguard confidential organizational data icons slide inspiration pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

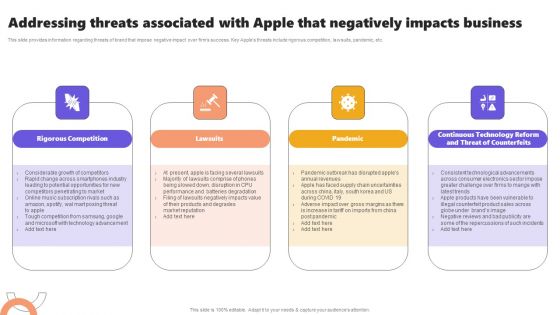
Addressing Threats Associated With Apple That Negatively Impacts Business Rules PDF
Find a pre designed and impeccable Addressing Threats Associated With Apple That Negatively Impacts Business Rules PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
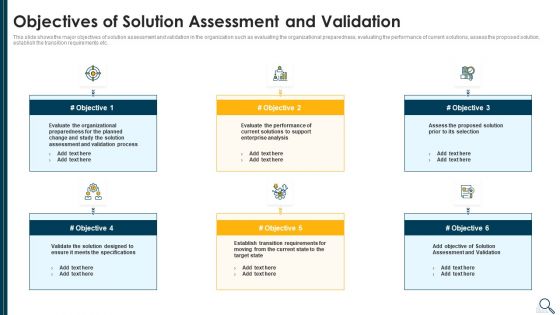
Solution Evaluation Criteria Assessment And Threat Impact Matrix Objectives Of Solution Assessment Rules PDF
This slide shows the major objectives of solution assessment and validation in the organization such as evaluating the organizational preparedness, evaluating the performance of current solutions, assess the proposed solution, establish the transition requirements etc. This is a solution evaluation criteria assessment and threat impact matrix objectives of solution assessment rules pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizational, process, enterprise analysis, performance, evaluate. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
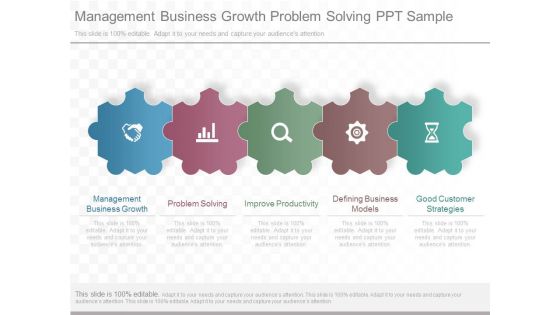
Management Business Growth Problem Solving Ppt Sample
This is a management business growth problem solving ppt sample. This is a five stage process. The stages in this process are management business growth, problem solving, improve productivity, defining business models, good customer strategies.

Problem Solving Case Studies Example Powerpoint Ideas
This is a problem solving case studies example powerpoint ideas. This is a six stage process. The stages in this process are gather information, define goal, root cause analysis, fault isolation, revise decision, problem definition.
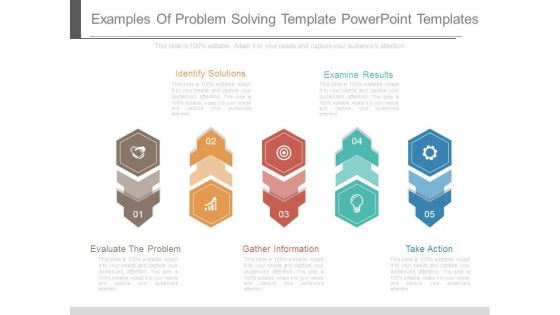
Examples Of Problem Solving Template Powerpoint Templates
This is a examples of problem solving template powerpoint templates. This is a five stage process. The stages in this process are evaluate the problem, identify solutions, gather information, examine results, take action.

Key Cloud Computing Threats In It Industry Ppt PowerPoint Presentation Gallery Slides PDF
Persuade your audience using this key cloud computing threats in it industry ppt powerpoint presentation gallery slides pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including complex architecture, legal issues, compliance issues. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Threats Of Cloud Technology In Business Ppt PowerPoint Presentation Gallery Microsoft PDF
Persuade your audience using this key threats of cloud technology in business ppt powerpoint presentation gallery microsoft pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including cost centric, data backup and recovery, manageability. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Establishing Information Security Management System To Manage Internet Threats Ppt PowerPoint Presentation File Visuals PDF
Persuade your audience using this establishing information security management system to manage internet threats ppt powerpoint presentation file visuals pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including documentation, departments, management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
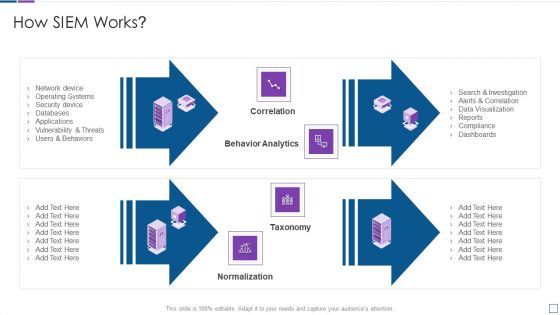
Real Time Assessment Of Security Threats How SIEM Works Inspiration PDF
Presenting real time assessment of security threats how siem works inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like correlation, behavior analytics, taxonomy, normalization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
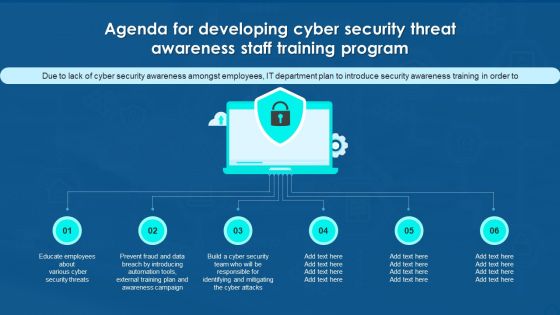
Agenda For Developing Cyber Security Threat Awareness Staff Training Program Inspiration PDF
This is a Agenda For Developing Cyber Security Threat Awareness Staff Training Program Inspiration PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Agenda. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
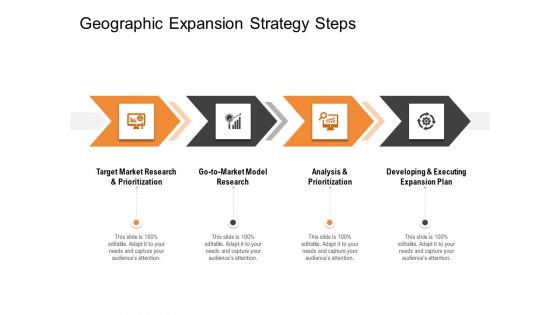
Opportunities And Threats For Penetrating In New Market Segments Geographic Expansion Strategy Steps Introduction PDF
This is a opportunities and threats for penetrating in new market segments geographic expansion strategy steps introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like target market research and prioritization, go to market model research, analysis and prioritization, developing and executing expansion plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
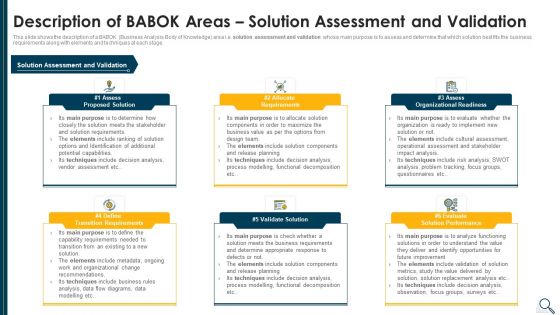
Solution Evaluation Criteria Assessment And Threat Impact Matrix Description Of Babok Slides PDF
This slide shows the description of a BABOK Business Analysis Body of Knowledge area i.e. solution assessment and validation whose main purpose is to assess and determine that which solution best fits the business requirements along with elements and techniques at each stage. Presenting solution evaluation criteria assessment and threat impact matrix description of babok slides pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like requirements, organizational readiness, validate solution, potential. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Solution Evaluation Criteria Assessment And Threat Impact Matrix Assess Organizational Readiness Icons PDF
This slide explains the various elements of force field analysis framework such as proposed change, pushing forces, forces resisting change etc. along with the benefits of force field analysis tool. This is a solution evaluation criteria assessment and threat impact matrix assess organizational readiness icons pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reduce issues, execution. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Executing Advance Data Analytics At Workspace Contingency Plan For Threat Handling Slides PDF
This slide covers details regarding the network optimization capabilities in terms of advanced caching capabilities, TCP layer optimization, global balancing of load, etc. This is a executing advance data analytics at workspace contingency plan for threat handling slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like caching capabilities, routing optimization, layer optimization, distributed. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
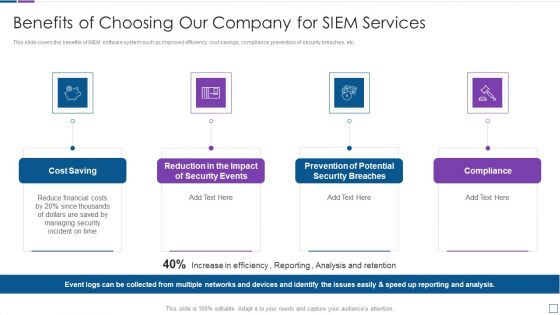
Real Time Assessment Of Security Threats Benefits Of Choosing Our Company For SIEM Services Introduction PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a real time assessment of security threats benefits of choosing our company for siem services introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, security events, compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats SIEM Logging Sources Infographics PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. This is a real time assessment of security threats siem logging sources infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security devices, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Handling Cyber Threats Digital Era Employee Upskilling Training Program Ppt Professional Master Slide
Mentioned slide displays a five day employee upskilling training program that company will use to provide an in-dept details about information security program activities and deliverables. This is a handling cyber threats digital era employee upskilling training program ppt professional master slide template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assess security requirements, perform a gap analysis, develop gap initiatives. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Handling Cyber Threats Digital Era Criticality Assessment Of Identified Assets Ppt Slides Backgrounds PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. This is a handling cyber threats digital era criticality assessment of identified assets ppt slides backgrounds pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like extremely critical, reasonably critical, least critical. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
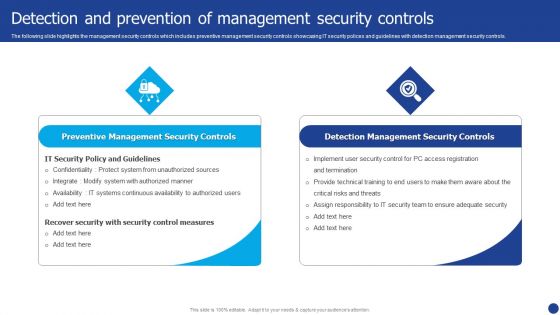
Information Technology Threat Mitigation Methods Detection And Prevention Of Management Security Controls Themes PDF
The following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Presenting Information Technology Threat Mitigation Methods Detection And Prevention Of Management Security Controls Themes PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Preventive Management Security Controls, Detection Management Security Controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
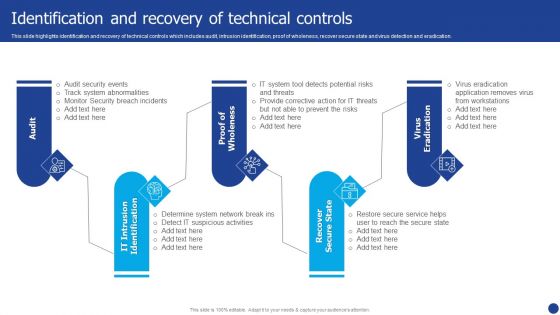
Information Technology Threat Mitigation Methods Identification And Recovery Of Technical Controls Demonstration PDF
This slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. Presenting Information Technology Threat Mitigation Methods Identification And Recovery Of Technical Controls Demonstration PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Recover Secure State, Virus Eradication, Audit. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
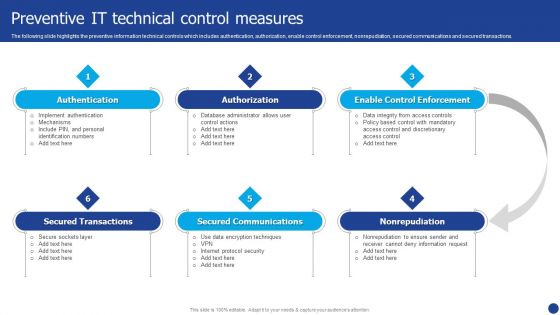
Information Technology Threat Mitigation Methods Preventive IT Technical Control Measures Information PDF
The following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. Presenting Information Technology Threat Mitigation Methods Preventive IT Technical Control Measures Information PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Authorization, Secured Communications, Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Problem Solving Approach Ppt Background Graphics
This is a business problem solving approach ppt background graphics. This is a four stage process. The stages in this process are business goal, dependent variables, independent variables, business drivers and relationship.
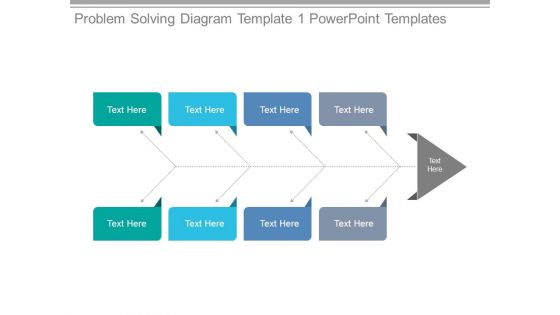
Problem Solving Diagram Template 1 Powerpoint Templates
This is a problem solving diagram template 1 powerpoint templates. This is a four stage process. The stages in this process are business, management, marketing, planning, process.
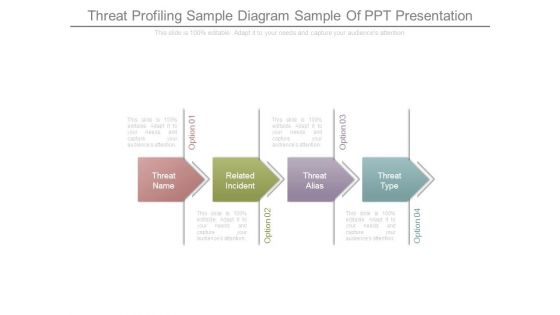
Threat Profiling Sample Diagram Sample Of Ppt Presentation
This is a threat profiling sample diagram sample of ppt presentation. This is a four stage process. The stages in this process are threat name, related incident, threat alias, threat type.
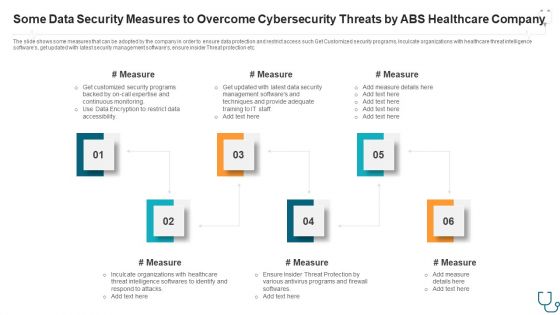
Some Data Security Measures To Overcome Cybersecurity Threats By Abs Healthcare Company Ppt Styles Slide Portrait PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by abs healthcare company ppt styles slide portrait pdf. template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like some data security measures to overcome cybersecurity threats by abs healthcare company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

PowerPoint Backgrounds Chain Links Teamwork Ppt Design Slides
PowerPoint Backgrounds Chain Links Teamwork PPT Design Slides-Most events and in every aspect of life are invariably interlinked. Use this chains graphic to outline your thoughts and their inherent interdependance to acheive the final outcome. Highlight the strength and durability of your thoughts, ideas and products-PowerPoint Backgrounds Chain Links Teamwork PPT Design Slides-This ppt can be used for presentations relating to-3d, Abstract, Apart, Attached, Background, Break, Breaking, Broken, Business, Chain, Connection, Danger, Elements, Failure, Glossy, Golden, Illustration, Join, Link, Metallic, Network, Object, Reflections, Rendering, Risky, Security, Separated, Split, Strength, Strong, Symbol

Data Driven Marketing Trends Significant To Marketers Ppt Slides Clipart Images PDF
This slide represents the latest and emerging trends to help marketers in gaining insights related to future of data driven marketing in order to avoid potential dangers and take benefit of potential opportunities. It includes details related to trends such as deliver personalized experience etc. Retrieve professionally designed Data Driven Marketing Trends Significant To Marketers Ppt Slides Clipart Images PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Data Driven Marketing Trends Significant To Marketers Ppt Infographic Template Example File
This slide represents the latest and emerging trends to help marketers in gaining insights related to future of data driven marketing in order to avoid potential dangers and take benefit of potential opportunities. It includes details related to trends such as deliver personalized experience etc. Retrieve professionally designed Data Driven Marketing Trends Significant To Marketers Ppt Infographic Template Example File to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Problem Cause Recognition Template Slides Styles
This is a problem cause recognition template slides styles. This is a four stage process. The stages in this process are assemble team, determine the root cause or collect data, state the problem or effect, determine the categories, brainstorm potential causes, draw the cause and effect diagram.

 Home
Home