Speech Bubbles
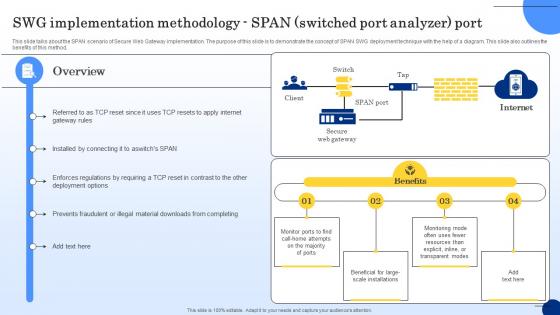
SWG Implementation Methodology Span Web Threat Protection System
This slide talks about the SPAN scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of SPAN SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than SWG Implementation Methodology Span Web Threat Protection System. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab SWG Implementation Methodology Span Web Threat Protection System today and make your presentation stand out from the rest
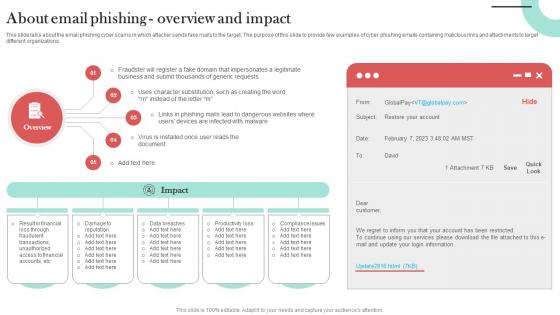
About Email Phishing Overview And Impact Man In The Middle Phishing IT
This slide talks about the email phishing cyber scams in which attacker sends fake mails to the target. The purpose of this slide to provide few examples of cyber phishing emails containing malicious links and attachments to target different organizations. Create an editable About Email Phishing Overview And Impact Man In The Middle Phishing IT that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. About Email Phishing Overview And Impact Man In The Middle Phishing IT is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
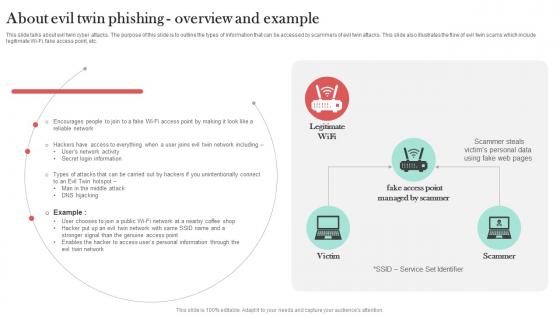
About Evil Twin Phishing Overview And Example Man In The Middle Phishing IT
This slide talks about evil twin cyber attacks. The purpose of this slide is to outline the types of information that can be accessed by scammers of evil twin attacks. This slide also illustrates the flow of evil twin scams which include legitimate Wi-Fi, fake access point, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate About Evil Twin Phishing Overview And Example Man In The Middle Phishing IT for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
About Identity Theft Overview And Techniques Man In The Middle Phishing IT
This slide talks about the major crime committed by phishers named as identity theft. The purpose of this slide is to outline the ways of stealing information such as robbery, computer fraud, social networking sites, mail theft and dumpster diving. Want to ace your presentation in front of a live audience Our About Identity Theft Overview And Techniques Man In The Middle Phishing IT can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

About Pharming Phishing Identification Man In The Middle Phishing IT
This slide talks about the pharming phishing cyber scams. The purpose of this slide is to illustrate the ways of recognizing pharming scams such as URL, design and HTTP vs HTTPS. This slide also illustrates the architecture of pharming phishing attack. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give About Pharming Phishing Identification Man In The Middle Phishing IT a try. Our experts have put a lot of knowledge and effort into creating this impeccable About Pharming Phishing Identification Man In The Middle Phishing IT. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

About Phishing Attacks Overview And Impact Man In The Middle Phishing IT
This slide demonstrates the overview of cyber phishing attacks. The purpose of this slide is to talk about the effectiveness of phishing scams. This slide also outlines the issues which can be caused by phishing attacks such as disclosure of private data, etc. Get a simple yet stunning designed About Phishing Attacks Overview And Impact Man In The Middle Phishing IT. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit About Phishing Attacks Overview And Impact Man In The Middle Phishing IT can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
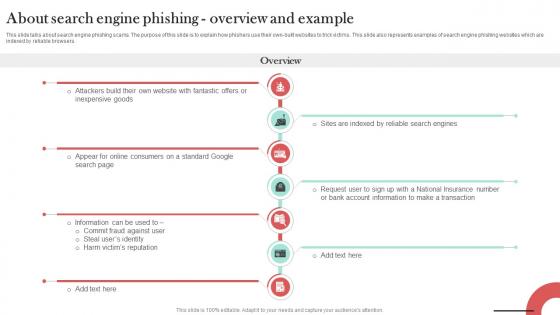
About Search Engine Phishing Overview Man In The Middle Phishing IT
This slide talks about search engine phishing scams. The purpose of this slide is to explain how phishers use their own-built websites to trick victims. This slide also represents examples of search engine phishing websites which are indexed by reliable browsers. Present like a pro with About Search Engine Phishing Overview Man In The Middle Phishing IT. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

About Spear Phishing Overview And Example Man In The Middle Phishing IT
This slide talks about spear phishing cyber attacks in which scammer targets a specific individual or specific group of persons. The purpose of this slide is to illustrate example of a mail used by phishers to conduct spear phishing cyber attacks. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than About Spear Phishing Overview And Example Man In The Middle Phishing IT. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab About Spear Phishing Overview And Example Man In The Middle Phishing IT today and make your presentation stand out from the rest
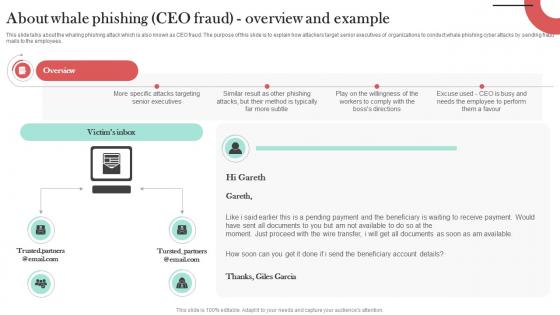
About Whale Phishing CEO Fraud Overview Man In The Middle Phishing IT
This slide talks about the whaling phishing attack which is also known as CEO fraud. The purpose of this slide is to explain how attackers target senior executives of organizations to conduct whale phishing cyber attacks by sending fraud mails to the employees. Find highly impressive About Whale Phishing CEO Fraud Overview Man In The Middle Phishing IT on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download About Whale Phishing CEO Fraud Overview Man In The Middle Phishing IT for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
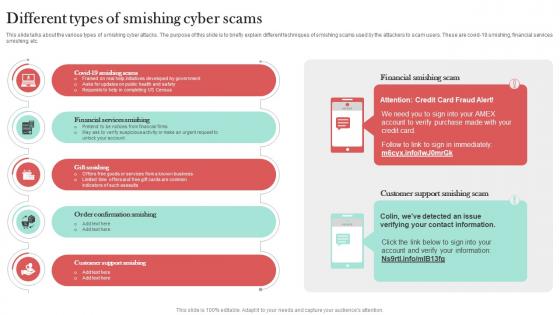
Different Types Of Smishing Cyber Scams Man In The Middle Phishing IT
This slide talks about the various types of smishing cyber attacks. The purpose of this slide is to briefly explain different techniques of smishing scams used by the attackers to scam users. These are covid-19 smishing, financial services smishing, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Different Types Of Smishing Cyber Scams Man In The Middle Phishing IT to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Different Types Of Vishing Cyber Attacks Man In The Middle Phishing IT
This slide talks about the various types of vishing cyber attacks. The purpose of this slide is to briefly explain different techniques of vishing scams used by the attackers to scam users. These are caller ID spoofing, dumpster diving, wardialing, etc. This modern and well-arranged Different Types Of Vishing Cyber Attacks Man In The Middle Phishing IT provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

How To Protect Users From Vishing Attacks Man In The Middle Phishing IT
This slide talks about the ways to protect users from vishing attacks. These include avoid calls from robots, never respond to audio-automated calls, verify the identity of the caller, never share personal information over the call, use multi-factor authentication, etc. Are you searching for a How To Protect Users From Vishing Attacks Man In The Middle Phishing IT that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download How To Protect Users From Vishing Attacks Man In The Middle Phishing IT from Slidegeeks today.
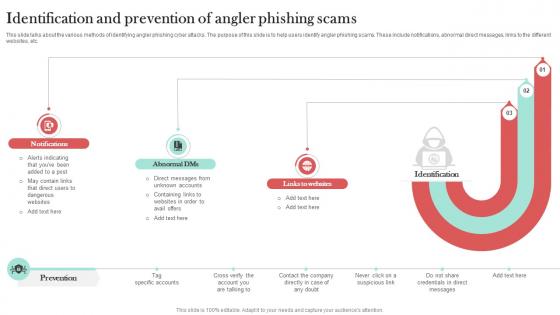
Identification And Prevention Of Angler Man In The Middle Phishing IT
This slide talks about the various methods of identifying angler phishing cyber attacks. The purpose of this slide is to help users identify angler phishing scams. These include notifications, abnormal direct messages, links to the different websites, etc. Slidegeeks has constructed Identification And Prevention Of Angler Man In The Middle Phishing IT after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
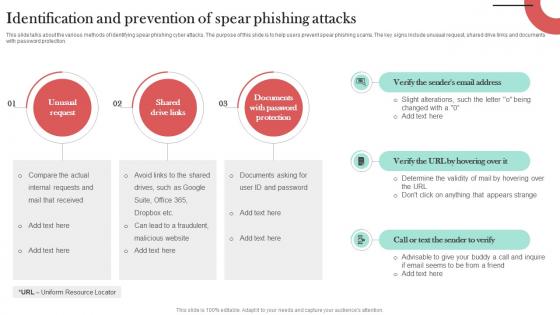
Identification And Prevention Of Spear Man In The Middle Phishing IT
This slide talks about the various methods of identifying spear phishing cyber attacks. The purpose of this slide is to help users prevent spear phishing scams. The key signs include unusual request, shared drive links and documents with password protection. Presenting this PowerPoint presentation, titled Identification And Prevention Of Spear Man In The Middle Phishing IT, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Identification And Prevention Of Spear Man In The Middle Phishing IT. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Identification And Prevention Of Spear Man In The Middle Phishing IT that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT
This slide talks about the damage caused by phishing attacks. The purpose of this slide is to explain the impact of phishing scams on organizations. The key points included are information loss, damaged credibility, direct financial loss and productivity loss. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT.
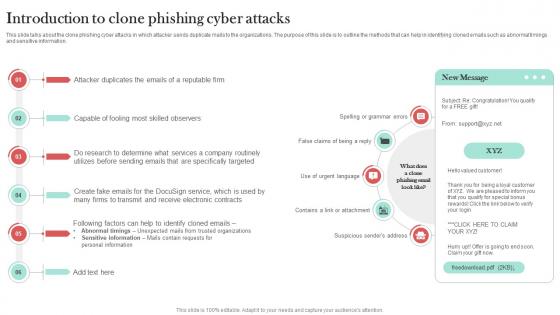
Introduction To Clone Phishing Cyber Man In The Middle Phishing IT
This slide talks about the clone phishing cyber attacks in which attacker sends duplicate mails to the organizations. The purpose of this slide is to outline the methods that can help in identifying cloned emails such as abnormal timings and sensitive information. This Introduction To Clone Phishing Cyber Man In The Middle Phishing IT from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Introduction To Watering Hole Phishing Man In The Middle Phishing IT
This slide talks about the watering hole phishing attacks which trick the victim to do activities compromising their personal data. The purpose of this slide is to describe the idea behind the working of watering hole scams which can target a group of individuals. Take your projects to the next level with our ultimate collection of Introduction To Watering Hole Phishing Man In The Middle Phishing IT. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT
This slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Steps To Identify Whaling Phishing Attacks Man In The Middle Phishing IT and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
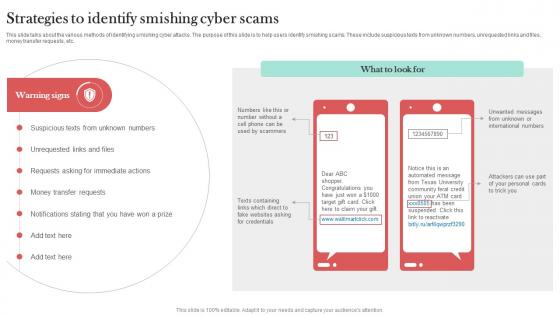
Strategies To Identify Smishing Cyber Scams Man In The Middle Phishing IT
This slide talks about the various methods of identifying smishing cyber attacks. The purpose of this slide is to help users identify smishing scams. These include suspicious texts from unknown numbers, unrequested links and files, money transfer requests, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Strategies To Identify Smishing Cyber Scams Man In The Middle Phishing IT template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Strategies To Identify Smishing Cyber Scams Man In The Middle Phishing IT that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
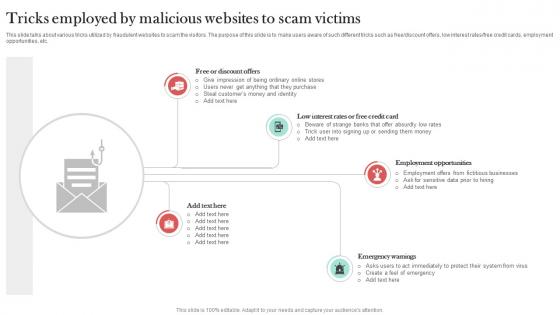
Tricks Employed By Malicious Websites Man In The Middle Phishing IT
This slide talks about various tricks utilized by fraudulent websites to scam the visitors. The purpose of this slide is to make users aware of such different tricks such as free discount offers, low interest rates free credit cards, employment opportunities, etc. Explore a selection of the finest Tricks Employed By Malicious Websites Man In The Middle Phishing IT here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Tricks Employed By Malicious Websites Man In The Middle Phishing IT to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
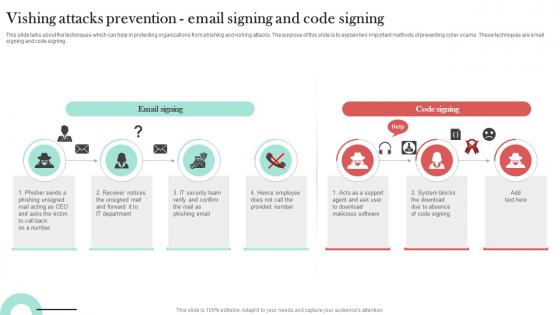
Vishing Attacks Prevention Email Signing Man In The Middle Phishing IT
This slide talks about the techniques which can help in protecting organizations from phishing and vishing attacks. The purpose of this slide is to explain two important methods of preventing cyber scams. These techniques are email signing and code signing. The Vishing Attacks Prevention Email Signing Man In The Middle Phishing IT is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Warning Signs To Recognize Phishing Email Man In The Middle Phishing IT
This slide talks about the warning signs that can help the user to recognize phishing email. The purpose of this slide is to outline the signs of phishing mails such as no greeting, misleading hyperlinks, unauthorized attachments, spelling and grammatical errors, etc. Slidegeeks has constructed Warning Signs To Recognize Phishing Email Man In The Middle Phishing IT after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Working Process Of Cyber Phishing Attacks Man In The Middle Phishing IT
This slide talks about the implementation and working of phishing attacks. The purpose of this slide is to explain how are cyber phishing scams conducted. The components include hacker, phishing mail, target, phishing website and original website. Do you know about Slidesgeeks Working Process Of Cyber Phishing Attacks Man In The Middle Phishing IT These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
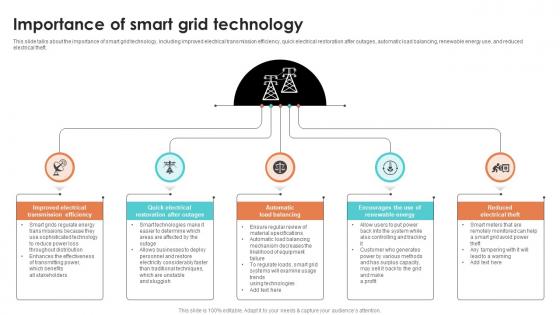
Importance Of Smart Grid Technology Smart Grid Working
This slide talks about the importance of smart grid technology, including improved electrical transmission efficiency, quick electrical restoration after outages, automatic load balancing, renewable energy use, and reduced electrical theft. If you are looking for a format to display your unique thoughts, then the professionally designed Importance Of Smart Grid Technology Smart Grid Working is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Importance Of Smart Grid Technology Smart Grid Working and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
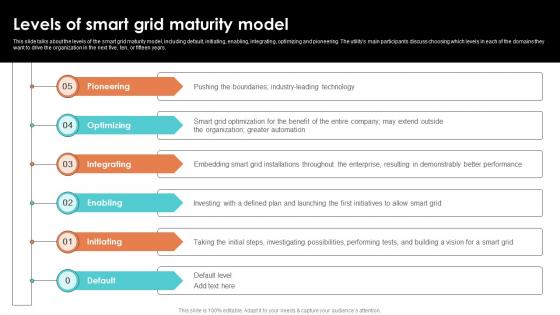
Levels Of Smart Grid Maturity Model Smart Grid Working
This slide talks about the levels of the smart grid maturity model, including default, initiating, enabling, integrating, optimizing and pioneering. The utilitys main participants discuss choosing which levels in each of the domains they want to drive the organization in the next five, ten, or fifteen years. This modern and well arranged Levels Of Smart Grid Maturity Model Smart Grid Working provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Zero Trust Network Access Solutions To Overcome ZTNA Implementation Challenges
This slide talks about the various solutions to overcome the ZTNA deployment challenges. The purpose of this slide is to showcase the remedies to overcome ZTNA obstacles. The leading solutions include running zero-trust trials, starting small, scaling slowly, and keeping people and zero trust in mind. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Zero Trust Network Access Solutions To Overcome ZTNA Implementation Challenges. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Zero Trust Network Access Solutions To Overcome ZTNA Implementation Challenges today and make your presentation stand out from the rest

CASB 2 0 IT Cloud Access Security Broker Pillar Data Security
This slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. The CASB 2 0 IT Cloud Access Security Broker Pillar Data Security is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

CASB 2 0 IT Overview Of CASB Deployment Models
This slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give CASB 2 0 IT Overview Of CASB Deployment Models a try. Our experts have put a lot of knowledge and effort into creating this impeccable CASB 2 0 IT Overview Of CASB Deployment Models. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Third Approach Streaming Data Integration Data Integration Strategies For Business
This slide talks about the streaming data integration process. The purpose of this slide is to explain the third method used in data extraction, here, data is continuously transferred in real-time from sources to target without any batch loading hence saving time. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Third Approach Streaming Data Integration Data Integration Strategies For Business can be your best option for delivering a presentation. Represent everything in detail using Third Approach Streaming Data Integration Data Integration Strategies For Business and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Secure Web Gateway Implementation Methodology Inline Web Access Control Solution
This slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Create an editable Secure Web Gateway Implementation Methodology Inline Web Access Control Solution that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Secure Web Gateway Implementation Methodology Inline Web Access Control Solution is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
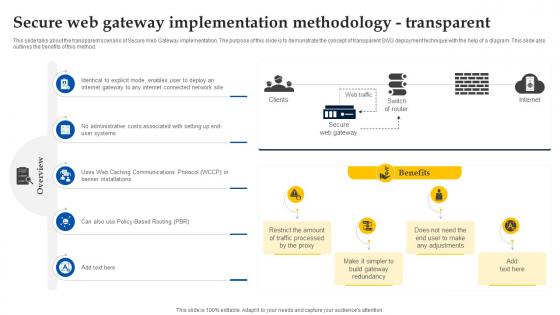
Secure Web Gateway Implementation Methodology Transparent Web Access Control Solution
This slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Secure Web Gateway Implementation Methodology Transparent Web Access Control Solution for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Web Access Control Solution Applications Of Secure Web Gateway In Various Industries
This slide talks about how Secure Web Gateway is used in several industrial domains. The purpose of this slide is to explain how SWG is used in different sectors. The industries covered are financial services, healthcare, education, manufacturing, etc. Present like a pro with Web Access Control Solution Applications Of Secure Web Gateway In Various Industries. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
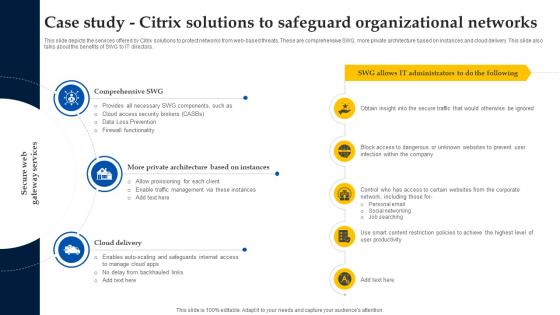
Web Access Control Solution Case Study Citrix Solutions To Safeguard Organizational Networks
This slide depicts the services offered by Citrix solutions to protect networks from web-based threats. These are comprehensive SWG, more private architecture based on instances and cloud delivery. This slide also talks about the benefits of SWG to IT directors. Find highly impressive Web Access Control Solution Case Study Citrix Solutions To Safeguard Organizational Networks on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Web Access Control Solution Case Study Citrix Solutions To Safeguard Organizational Networks for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
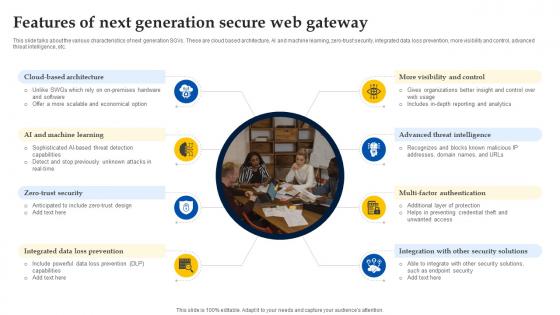
Web Access Control Solution Features Of Next Generation Secure Web Gateway
This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Web Access Control Solution Features Of Next Generation Secure Web Gateway to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Web Access Control Solution Future Of Secure Web Gateway Technology
This slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. This modern and well-arranged Web Access Control Solution Future Of Secure Web Gateway Technology provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Web Access Control Solution Importance Of Secure Web Gateway For Businesses
This slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc. Explore a selection of the finest Web Access Control Solution Importance Of Secure Web Gateway For Businesses here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Web Access Control Solution Importance Of Secure Web Gateway For Businesses to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
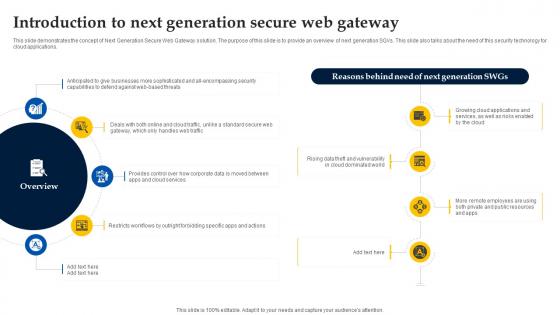
Web Access Control Solution Introduction To Next Generation Secure Web Gateway
This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications. Are you searching for a Web Access Control Solution Introduction To Next Generation Secure Web Gateway that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Web Access Control Solution Introduction To Next Generation Secure Web Gateway from Slidegeeks today.
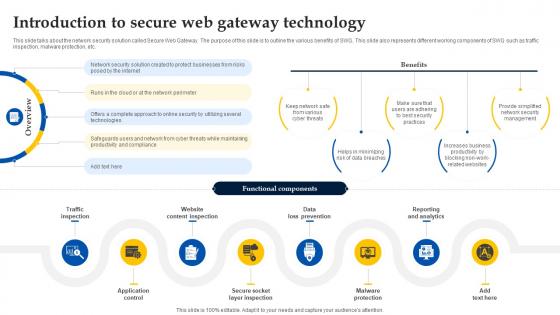
Web Access Control Solution Introduction To Secure Web Gateway Technology
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Retrieve professionally designed Web Access Control Solution Introduction To Secure Web Gateway Technology to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
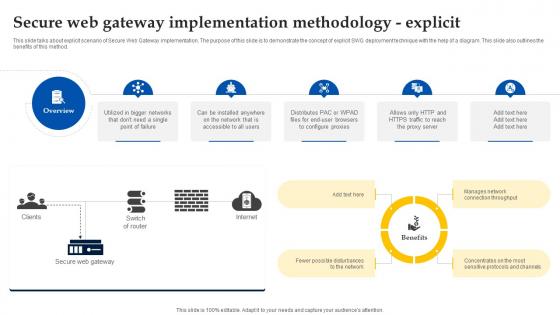
Web Access Control Solution Secure Web Gateway Implementation Methodology Explicit
This slide talks about explicit scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of explicit SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Web Access Control Solution Secure Web Gateway Implementation Methodology Explicit a try. Our experts have put a lot of knowledge and effort into creating this impeccable Web Access Control Solution Secure Web Gateway Implementation Methodology Explicit. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
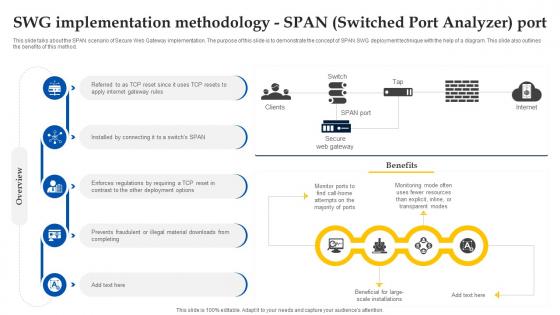
Web Access Control Solution Swg Implementation Methodology Span Switched Port Analyzer Port
This slide talks about the SPAN scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of SPAN SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Find highly impressive Web Access Control Solution Swg Implementation Methodology Span Switched Port Analyzer Port on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Web Access Control Solution Swg Implementation Methodology Span Switched Port Analyzer Port for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
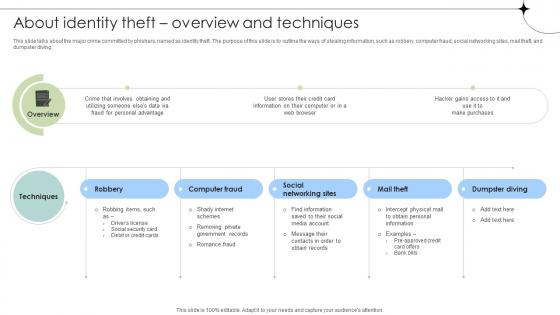
About Identity Theft Overview And Techniques Data Fortification Strengthening Defenses
This slide talks about the major crime committed by phishers, named as identity theft. The purpose of this slide is to outline the ways of stealing information, such as robbery, computer fraud, social networking sites, mail theft, and dumpster diving.Create an editable About Identity Theft Overview And Techniques Data Fortification Strengthening Defenses that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. About Identity Theft Overview And Techniques Data Fortification Strengthening Defenses is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

About Cloud Computing Overview And Services Data Security In Cloud Computing Ppt Template
This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc. Create an editable About Cloud Computing Overview And Services Data Security In Cloud Computing Ppt Template that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. About Cloud Computing Overview And Services Data Security In Cloud Computing Ppt Template is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

About Cloud Cryptography Overview And Features Data Security In Cloud Computing Ppt Powerpoint
This slide talks about the cloud cryptography which helps in securing information travelling through cloud network. The purpose of this slide is to briefly explain the concept of cloud cryptography. This slide also outlines the features of this technology. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate About Cloud Cryptography Overview And Features Data Security In Cloud Computing Ppt Powerpoint for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
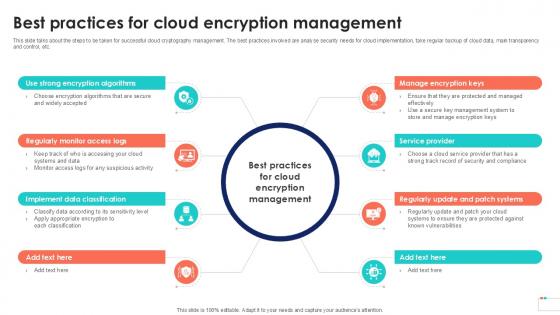
Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template
This slide talks about the steps to be taken for successful cloud cryptography management. The best practices involved are analyse security needs for cloud implementation, take regular backup of cloud data, main transparency and control, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Best Practices For Cloud Encryption Data Security In Cloud Computing Ppt Template today and make your presentation stand out from the rest

Cloud Security Enhancement Using Data Security In Cloud Computing Ppt Presentation
This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cloud Security Enhancement Using Data Security In Cloud Computing Ppt Presentation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide
This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cryptographic Algorithms Used In Data Security In Cloud Computing Ppt Slide
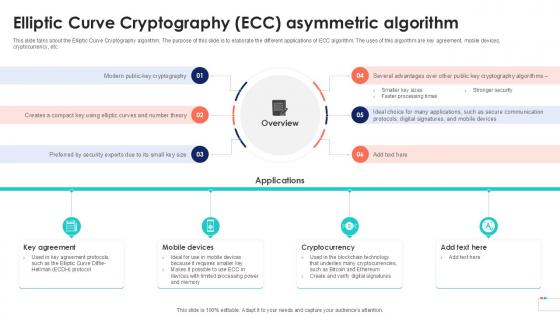
Elliptic Curve Cryptography ECC Data Security In Cloud Computing Ppt Template
This slide talks about the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different applications of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc. Welcome to our selection of the Elliptic Curve Cryptography ECC Data Security In Cloud Computing Ppt Template. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation
This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc. Presenting this PowerPoint presentation, titled Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample
This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc. Create an editable Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Methods Used By Symmetric Algorithm Data Security In Cloud Computing Ppt Sample is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample
This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample a try. Our experts have put a lot of knowledge and effort into creating this impeccable Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Working Steps Of Cryptography Data Security In Cloud Computing Ppt Slide
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data-in-transit, data-at-rest and legal and regulatory issues. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Steps Of Cryptography Data Security In Cloud Computing Ppt Slide to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Microscopy Technology Overview Silicon Photonics SiPh It Ppt Template
This slide talks about microscopy technology, including its various types and applications. The purpose of this slide is to provide an overview of microscopy and its types, such as optical, confocal, fluorescence, transmission electron microscopes and scanning electron, etc.Presenting this PowerPoint presentation, titled Microscopy Technology Overview Silicon Photonics SiPh It Ppt Template, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Microscopy Technology Overview Silicon Photonics SiPh It Ppt Template. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Microscopy Technology Overview Silicon Photonics SiPh It Ppt Template that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Case Study IAC Transformation At IAC Tools For Performance Analysis PPT Slide
This slide showcases the case study of acme inc. In infrastructure as code. The purpose of this slide is to highlight the conclusion of the case study. That case study talks about the need for infrastructure as code in an organization. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Case Study IAC Transformation At IAC Tools For Performance Analysis PPT Slide. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Case Study IAC Transformation At IAC Tools For Performance Analysis PPT Slide today and make your presentation stand out from the rest

Case Study IAC Transformation IAC Tools For Performance Analysis PPT Presentation
This slide showcases the case study of acme inc. In infrastructure as code. The purpose of this slide is to highlight the challenges, implementations, and results of the case study. That case study talks about the need for infrastructure as code in an organization. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Case Study IAC Transformation IAC Tools For Performance Analysis PPT Presentation can be your best option for delivering a presentation. Represent everything in detail using Case Study IAC Transformation IAC Tools For Performance Analysis PPT Presentation and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Dashboard To Track Performance Of Inside Vs Outside Sales PPT PowerPoint Strategy SS V
This slide showcases dashboard that can help organization to track the performance of different inside sales call executives. Its key elements are average time per lead, call back ration, total conversion, leads called etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Dashboard To Track Performance Of Inside Vs Outside Sales PPT PowerPoint Strategy SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Dashboard To Track Performance Of Inside Vs Outside Sales PPT PowerPoint Strategy SS V today and make your presentation stand out from the rest

Strategies To Optimize Consumer Touchpoints For Customer Journey Transformation Ideas PDF
This slide covers the various methods to optimize customer touchpoints such as websites, Live Chat, social media, etc. It also includes its impact on buyer retention and conversion. Persuade your audience using this Strategies To Optimize Consumer Touchpoints For Customer Journey Transformation Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Strategy, Social Media, Fast Response-. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
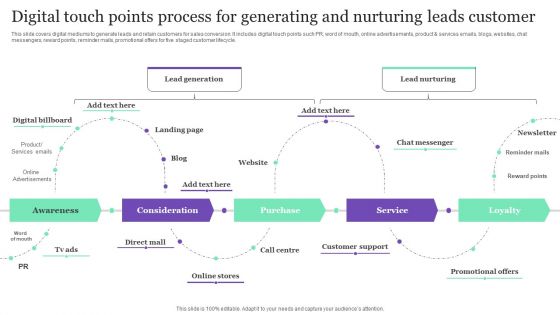
Digital Touch Points Process For Generating And Nurturing Leads Customer Ideas PDF
This slide covers digital mediums to generate leads and retain customers for sales conversion. It includes digital touch points such PR, word of mouth, online advertisements, product and services emails, blogs, websites, chat messengers, reward points, reminder mails, promotional offers for five staged customer lifecycle. Persuade your audience using this Digital Touch Points Process For Generating And Nurturing Leads Customer Ideas PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Awareness, Consideration, Purchase, Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Facts Medical Benefits Navigation Platform Pitch Deck Ppt Powerpoint
This slide covers key facts associated with HealthJoy company. It includes number of employees, total funding amount and total number of conversations. Slidegeeks has constructed Key Facts Medical Benefits Navigation Platform Pitch Deck Ppt Powerpoint after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Top 5 Messaging Apps And Platforms For Business Template PDF
This slide showcase top 5 messaging apps and platforms for business which contains various applications beneficial for inter departmental conversations and making various decisions. it includes information about search feature, security, group chat feature, data backup, audio and video conferencing, document management, etc.Showcasing this set of slides titled top 5 messaging apps and platforms for business template pdf. The topics addressed in these templates are document management, security, conferencing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
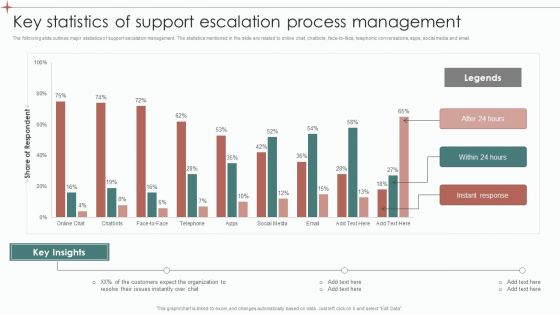
Key Statistics Of Support Escalation Process Management Ppt Model Graphics Pictures PDF
The following slide outlines major statistics of support escalation management. The statistics mentioned in the slide are related to online chat, chatbots, face-to-face, telephonic conversations, apps, social media and email. Showcasing this set of slides titled Key Statistics Of Support Escalation Process Management Ppt Model Graphics Pictures PDF. The topics addressed in these templates are Legends, Key Insights, Customers Expect. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

 Home
Home