Security

Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Competitive Guidelines PDF
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver and pitch your topic in the best possible manner with this security information and event management strategies for financial audit and compliance siem competitive guidelines pdf. Use them to share invaluable insights on siem competitive advantage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
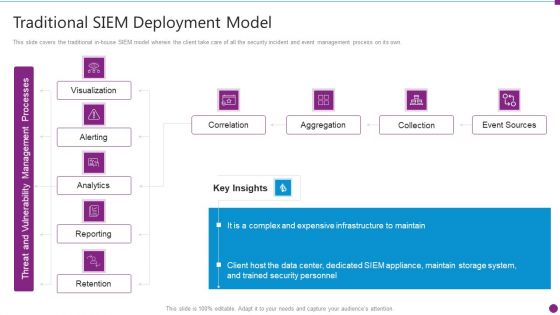
Security Information And Event Management Strategies For Financial Audit And Compliance Traditional SIEM Deployment Guidelines PDF
This slide covers the traditional in-house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver an awe inspiring pitch with this creative security information and event management strategies for financial audit and compliance traditional siem deployment guidelines pdf bundle. Topics like correlation, aggregation, collection, event sources can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
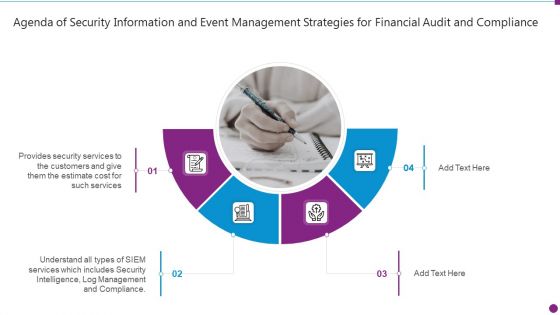
Agenda Of Security Information And Event Management Strategies For Financial Audit And Compliance Infographics PDF
This is a agenda of security information and event management strategies for financial audit and compliance infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like customers, security intelligence, log management and compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Recognition Automation Security Information And Event Management Dashboard Activity Ppt Styles Influencers PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification, Deliver an awe inspiring pitch with this creative risk recognition automation security information and event management dashboard activity ppt styles influencers pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Recognition Automation Security Information And Event Management Dashboard Source Ppt Professional Display PDF
This slide covers the SIEM dashboard which focuses on server status, log sources, total logs, last log, collectors, log sources etc. Deliver and pitch your topic in the best possible manner with this risk recognition automation security information and event management dashboard source ppt professional display pdf. Use them to share invaluable insights on security information and event management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents For Application Development Life Cycle Security Sample PDF
This is a table of contents for application development life cycle security sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, implementation, models. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Handling Cyber Threats Digital Era Security Lifecycle Ppt Summary Brochure PDF
This is a handling cyber threats digital era security lifecycle ppt summary brochure pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security lifecycle. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Information Technology Security Requirement Ppt Styles Sample PDF
This slide depicts the categories of recent threats that table of contents for information technology security requirement ppt styles sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like latest threats in information technology security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

What Is Information Technology Security And How Does It Work Ppt Portfolio Sample PDF
This is a what is information technology security and how does it work ppt portfolio sample pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like it risk assessment, it risk identification, key elements it security, steps mitigation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
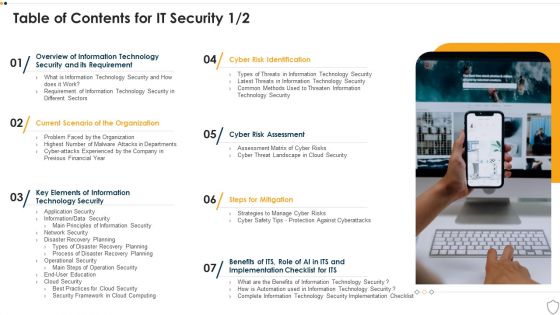
Table Of Contents For IT Security Cyber Ppt Inspiration Introduction PDF
This is a table of contents for it security cyber ppt inspiration introduction pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology security, implementation, organization, cyber risk assessment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Methods To Develop Advanced IT Security Monitoring Plan Graphics PDF
This is a agenda for methods to develop advanced it security monitoring plan graphics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collecting and analyzing, key performance indicators, potential security monitoring threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Information PDF
This is a agenda for modern security observation plan to eradicate cybersecurity risk and data breach information pdf template with various stages. Focus and dispense information on senen stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda for modern security observation plan to eradicate cybersecurity risk and data breach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Info Security Wd Ppt PowerPoint Presentation Gallery Maker PDF
Presenting table of contents for info security wd ppt powerpoint presentation gallery maker pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like cyber risk assessment, steps for mitigation, cyber risk identification, key elements of information security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
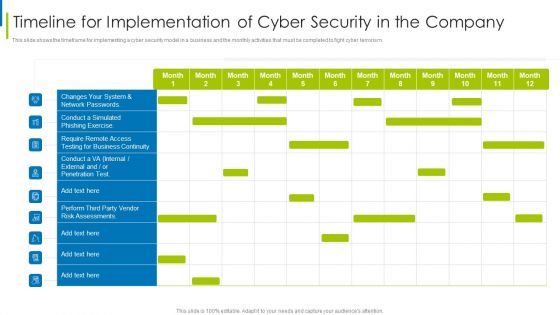
Cyber Terrorism Assault Timeline For Implementation Of Cyber Security In The Company Sample PDF
This slide shows the timeframe for implementing a cyber security model in a business and the monthly activities that must be completed to fight cyber terrorism.Deliver an awe inspiring pitch with this creative cyber terrorism assault timeline for implementation of cyber security in the company sample pdf bundle. Topics like require remote access, testing for business continuity, risk assessments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security System Management Checklist With Key Activities Guidelines PDF
Following slide displays system management checklist. It includes system management activities and frequency of performing them. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security System Management Checklist With Key Activities Guidelines PDF bundle. Topics like System Monitoring, Data Backup, Security Patches, Virus Scanning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Table Of Contents Brochure PDF
This is a Risk Management Model For Data Security Table Of Contents Brochure PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Managing Risks, Defining Risk Level, Setting Scenario, Security Control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Role Of Technical Competence In Organizational Cloud Security Architect Skills Scope Portrait PDF
This slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational technical, etc.Deliver an awe inspiring pitch with this creative Role Of Technical Competence In Organizational Cloud Security Architect Skills Scope Portrait PDF bundle. Topics like Architecture And Strategy, Technical, Leadership can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
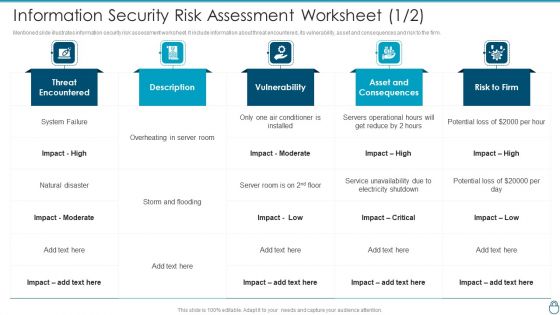
Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Asset Graphics PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Asset Graphics PDF bundle. Topics like Conditioner Is Installed, Asset And Consequences, Electricity Shutdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan Impact On Security Infrastructure Performance Background PDF
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Impact On Security Infrastructure Performance Background PDF Use them to share invaluable insights on Assessment Process, Target Met After Introducing, Standard And Technology and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF
Following slide covers information security risk management dashboard. It include kpis such as risk analysis progress, percent risk, response progress for risks and number of risks encountered.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF bundle. Topics like Risk Rating Breakdown, Action Plan Breakdown, Risk Analysis Progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Smart Home Security Solutions Company Profile Competitive Analysis Of Companies Ideas PDF
This slide highlights the security company competitive analysis which includes contract length, yearly fees, activation fee, end to end platform integration, customer retention and mobile application. Deliver an awe inspiring pitch with this creative Smart Home Security Solutions Company Profile Competitive Analysis Of Companies Ideas PDF bundle. Topics like Minimum Contract Period, Activation Fee Hidden, Customer Retention Mobile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
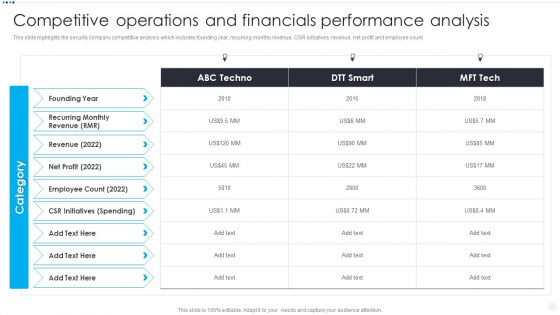
Smart Home Security Solutions Company Profile Competitive Operations And Financials Background PDF
This slide highlights the security company competitive analysis which includes founding year, recurring monthly revenue, CSR initiatives, revenue, net profit and employee count. Deliver and pitch your topic in the best possible manner with this Smart Home Security Solutions Company Profile Competitive Operations And Financials Background PDF. Use them to share invaluable insights on Recurring Monthly Revenue, Employee Count 2022, CSR Initiatives Spending and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
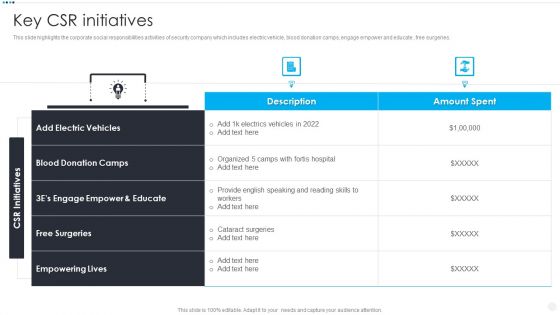
Smart Home Security Solutions Company Profile Key CSR Initiatives Background PDF
This slide highlights the corporate social responsibilities activities of security company which includes electric vehicle, blood donation camps, engage empower and educate , free surgeries. Deliver and pitch your topic in the best possible manner with this Smart Home Security Solutions Company Profile Key CSR Initiatives Background PDF. Use them to share invaluable insights on Add Electric Vehicles, Blood Donation Camps, 3Es Engage Empower and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Developing Business Analytics Framework Enabling Data Security Risk Management Elements PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative Developing Business Analytics Framework Enabling Data Security Risk Management Elements PDF bundle. Topics like Required Resources, Responsible Person, Communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
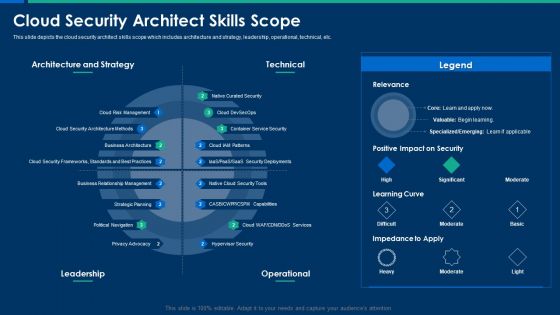
CIO Role In Digital Evolution Cloud Security Architect Skills Scope Structure PDF
This slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational, technical, etc. Deliver and pitch your topic in the best possible manner with this CIO Role In Digital Evolution Cloud Security Architect Skills Scope Structure PDF. Use them to share invaluable insights on Architecture Strategy, Risk Management, Business Architecture and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
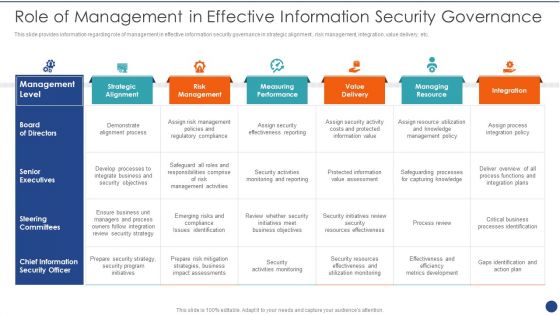
Cios Value Optimization Role Of Management In Effective Information Security Governance Ideas PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative Cios Value Optimization Role Of Management In Effective Information Security Governance Ideas PDF bundle. Topics like Management Level, Strategic Alignment, Risk Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Based Procedures To IT Security Categorization Worksheet For Assets Owned By Organization Microsoft PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Categorization Worksheet For Assets Owned By Organization Microsoft PDF. Use them to share invaluable insights on Server Computer, System Location, System Accessibility and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF
This slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF bundle. Topics like Cyber Security, Existing Enterprise, IoT products can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Information Security Phase 1 Understand Cloud Utilization And Risk Ppt Infographics Topics PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of. Deliver and pitch your topic in the best possible manner with this Cloud Information Security Phase 1 Understand Cloud Utilization And Risk Ppt Infographics Topics PDF. Use them to share invaluable insights on Recognize Critical, Discover Malicious, Risk Assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Ways To Accomplish ISO 27001 Accreditation Dashboard For Information Security Risk Management Clipart PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative Ways To Accomplish ISO 27001 Accreditation Dashboard For Information Security Risk Management Clipart PDF bundle. Topics like Risk Heat, Action Plan, Risk Rating Breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security KPI Dashboard With Various Charts And Graphs Ppt Summary Background Image PDF
Persuade your audience using this Security KPI Dashboard With Various Charts And Graphs Ppt Summary Background Image PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Various Charts, Security KPI Dashboard, Graphs. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cios Methodologies To Improve IT Spending Role Of Management In Effective Information Security Microsoft PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative Cios Methodologies To Improve IT Spending Role Of Management In Effective Information Security Microsoft PDF bundle. Topics like Risk Management, Measuring Performance, Managing Resource can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
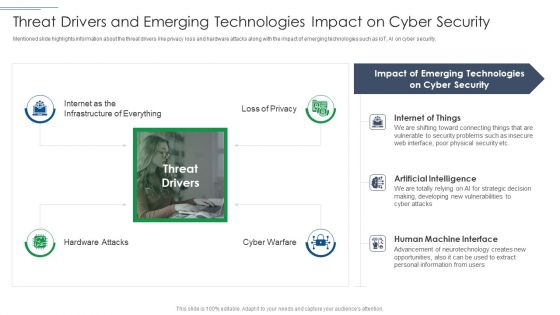
IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF
Presenting IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Cyber Security, Emerging Technologies, Artificial Intelligence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Computer System Interface Icon Depicting Mobile Security Ppt Show Example PDF
Persuade your audience using this Computer System Interface Icon Depicting Mobile Security Ppt Show Example PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Computer System, Interface Icon, Depicting Mobile Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Security Computer System Interface Icon With Cloud Storage Ppt File Backgrounds PDF
Persuade your audience using this Security Computer System Interface Icon With Cloud Storage Ppt File Backgrounds PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Security Computer System, Interface Icon, Cloud Storage. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
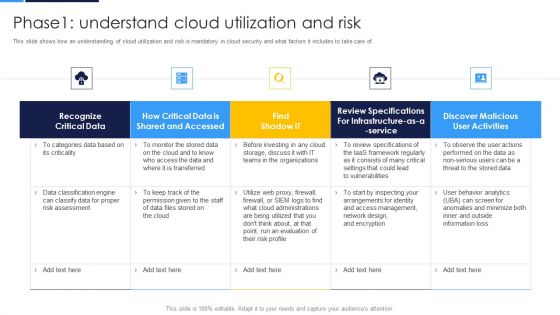
Cloud Security Assessment Phase1 Understand Cloud Utilization And Risk Professional PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Phase1 Understand Cloud Utilization And Risk Professional PDF bundle. Topics like Shared And Accessed, Risk Assessment, Review Specifications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
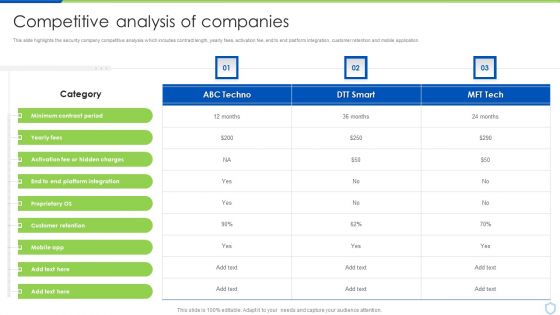
Security And Surveillance Company Profile Competitive Analysis Of Companies Brochure PDF
This slide highlights the security company competitive analysis which includes contract length, yearly fees, activation fee, end to end platform integration, customer retention and mobile application.Deliver and pitch your topic in the best possible manner with this Security And Surveillance Company Profile Competitive Analysis Of Companies Brochure PDF. Use them to share invaluable insights on Customer Retention, Platform Integration, Minimum Contract and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
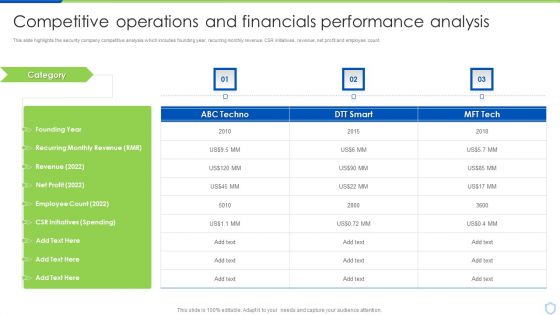
Security And Surveillance Company Profile Competitive Operations And Financials Designs PDF
This slide highlights the security company competitive analysis which includes founding year, recurring monthly revenue, CSR initiatives, revenue, net profit and employee count.Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Competitive Operations And Financials Designs PDF bundle. Topics like Employee Count, Recurring Revenue, Spending can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
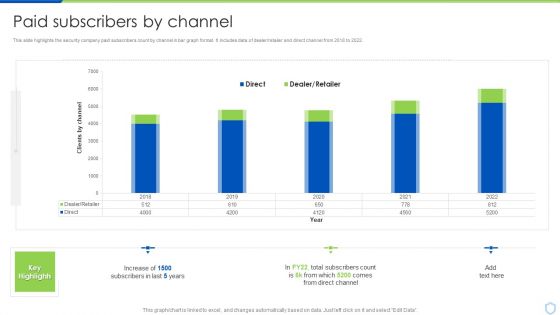
Security And Surveillance Company Profile Paid Subscribers By Channel Background PDF
This slide highlights the security company paid subscribers count by channel in bar graph format. It includes data of dealer retailer and direct channel from 2018 to 2022. Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Paid Subscribers By Channel Background PDF bundle. Topics like Direct Channel, Subscribers In Last, Key Highlights can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
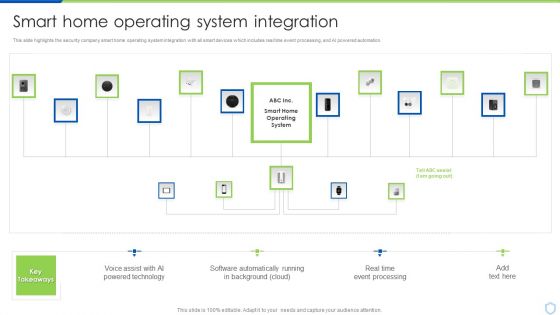
Security And Surveillance Company Profile Smart Home Operating System Integration Clipart PDF
This slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation.Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Smart Home Operating System Integration Clipart PDF bundle. Topics like Powered Technology, Software Automatically, Event Processing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Camera System Company Profile Competitive Analysis Of Companies Mockup PDF
This slide highlights the security company competitive analysis which includes contract length, yearly fees, activation fee, end to end platform integration, customer retention and mobile application.Deliver and pitch your topic in the best possible manner with this Security Camera System Company Profile Competitive Analysis Of Companies Mockup PDF. Use them to share invaluable insights on Customer Retention, Hidden Charges, Minimum Contract and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
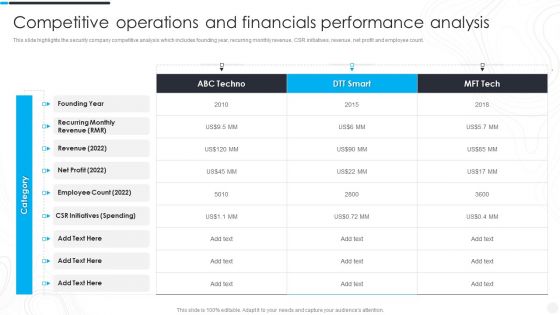
Security Camera System Company Profile Competitive Operations And Financials Slides PDF
This slide highlights the security company competitive analysis which includes founding year, recurring monthly revenue, CSR initiatives, revenue, net profit and employee count.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Competitive Operations And Financials Slides PDF bundle. Topics like Employee Count, Initiatives Spending, Revenue can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
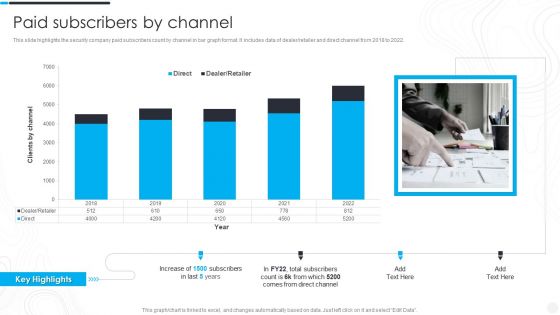
Security Camera System Company Profile Paid Subscribers By Channel Sample PDF
This slide highlights the security company paid subscribers count by channel in bar graph format. It includes data of dealer retailer and direct channel from 2018 to 2022. Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Paid Subscribers By Channel Sample PDF bundle. Topics like Total Subscribers, Direct Channel, Key Highlights can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
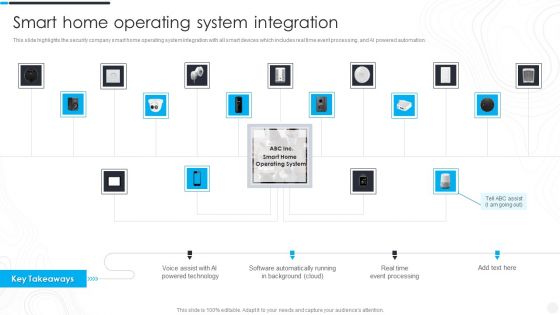
Security Camera System Company Profile Smart Home Operating System Integration Background PDF
This slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Smart Home Operating System Integration Background PDF bundle. Topics like Powered Technology, Software Automatically, Event Processing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Hacker Altered Business Practices Due To Hacking Structure PDF
This slide represents that hackers forced the company to alter business practices followed by years and shut down online shopping stores in some regions.Deliver an awe inspiring pitch with this creative IT Security Hacker Altered Business Practices Due To Hacking Structure PDF bundle. Topics like Stored Information, Personal Information, Social Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Saas Cloud Security Best Practices Icon Ppt PowerPoint Presentation File Guidelines PDF
Persuade your audience using this Saas Cloud Security Best Practices Icon Ppt PowerPoint Presentation File Guidelines PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Saas Cloud Security, Best Practices, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

ISO 27001 Certification Procedure Current Security Management Capabilities Overview Diagrams PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating.Deliver and pitch your topic in the best possible manner with this ISO 27001 Certification Procedure Current Security Management Capabilities Overview Diagrams PDF. Use them to share invaluable insights on Assessing Information, Occurrence Identification, Communication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
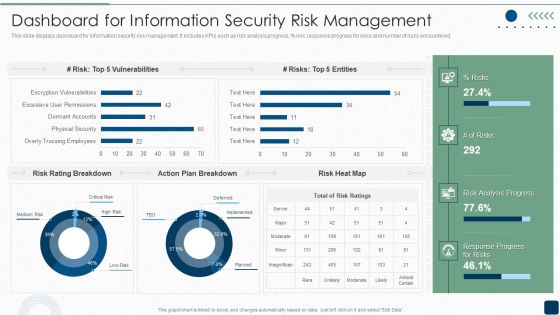
ISO 27001 Certification Procedure Dashboard For Information Security Risk Management Sample PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, persent risk, response progress for risks and number of risks encountered.Deliver an awe inspiring pitch with this creative ISO 27001 Certification Procedure Dashboard For Information Security Risk Management Sample PDF bundle. Topics like Vulnerabilities, Rating Breakdown, Plan Breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
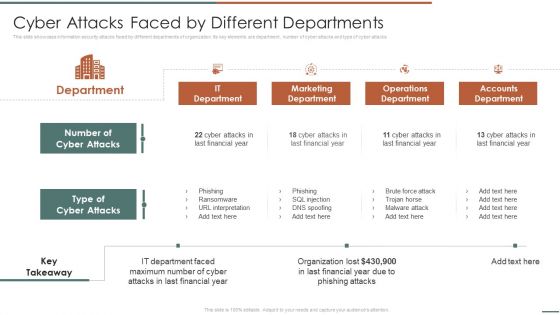
Information Security Risk Evaluation Cyber Attacks Faced By Different Departments Professional PDF
This slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Cyber Attacks Faced By Different Departments Professional PDF bundle. Topics like Marketing Department, Operations Department, Accounts Department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Information Security Risk Evaluation And Administration Plan Formats PDF
Presenting Table Of Contents For Information Security Risk Evaluation And Administration Plan Formats PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Scenario Assessment, Security Capabilities, Overview Of Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF
This is a IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Policies, Incident Reporting, Remote Workstations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Classifying Various Security Issues And Attacks Professional PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Classifying Various Security Issues And Attacks Professional PDF. Use them to share invaluable insights on External Issues, Audio Steganography, Malware Injection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
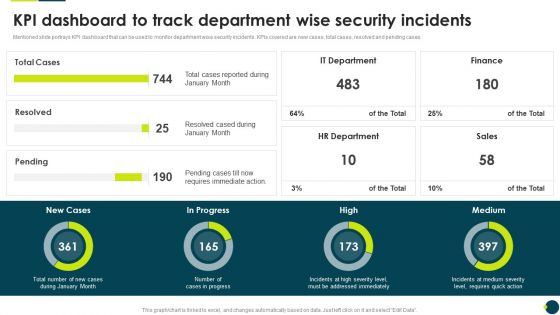
IT Threats Response Playbook KPI Dashboard To Track Department Wise Security Incidents Brochure PDF
Mentioned slide portrays KPI dashboard that can be used to monitor department wise security incidents. KPIs covered are new cases, total cases, resolved and pending cases.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook KPI Dashboard To Track Department Wise Security Incidents Brochure PDF bundle. Topics like It Department, Hr Department, Requires Immediate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

8 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Rules PDF
Persuade your audience using this 8 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Rules PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Business Goals, Security Plan, Management Program. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

6 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Brochure PDF
Persuade your audience using this 6 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Business Goals, Security Plan, Business Goals. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Improved Digital Expenditure Role Of Management In Effective Information Security Governance Microsoft PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative Improved Digital Expenditure Role Of Management In Effective Information Security Governance Microsoft PDF bundle. Topics like Management Level, Board Directors, Senior Executives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Complete Online Marketing Audit Guide IT Security Audit With Risk Level Clipart PDF
This slide highlights the security audit which showcase the risks related to accounts and user computers and also states the data which are at high risk. Deliver and pitch your topic in the best possible manner with this Complete Online Marketing Audit Guide IT Security Audit With Risk Level Clipart PDF. Use them to share invaluable insights on Risks, Current Value, Risk Level and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
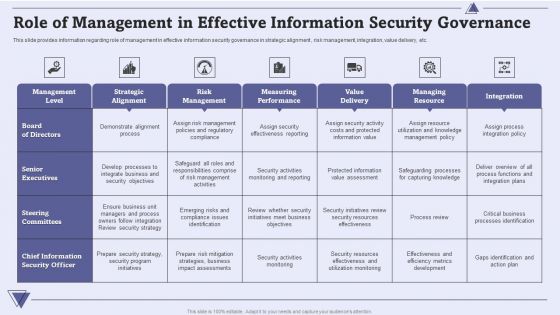
CIO For IT Cost Optimization Techniques Role Of Management In Effective Information Security Governance Themes PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver and pitch your topic in the best possible manner with this CIO For IT Cost Optimization Techniques Role Of Management In Effective Information Security Governance Themes PDF. Use them to share invaluable insights on Management Level, Strategic Alignment, Risk Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
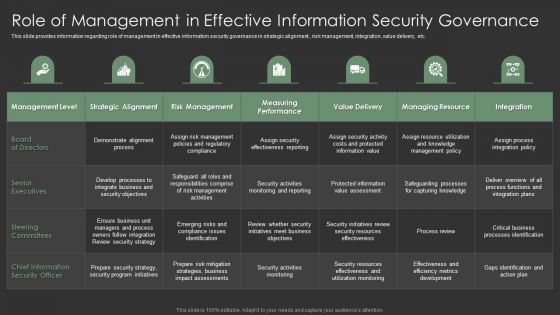
IT Spend Management Priorities By Cios Role Of Management In Effective Information Security Governance Graphics PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative IT Spend Management Priorities By Cios Role Of Management In Effective Information Security Governance Graphics PDF bundle. Topics like Senior Executives, Strategic Alignment, Risk Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

ISO 27001 Organizational Qualifying Procedure Current Security Management Capabilities Overview Ideas PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Current Security Management Capabilities Overview Ideas PDF bundle. Topics like Occurrence Identification, Communication, Required Standard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home