Security
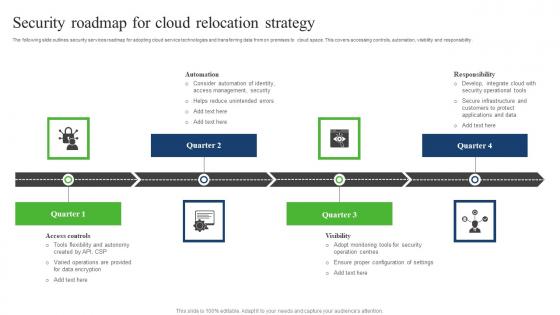
Security Roadmap For Cloud Relocation Strategy Sample Pdf
The following slide outlines security services roadmap for adopting cloud service technologies and transferring data from on premises to cloud space. This covers accessing controls, automation, visibility and responsibility. Showcasing this set of slides titled Security Roadmap For Cloud Relocation Strategy Sample Pdf. The topics addressed in these templates are Responsibility, Automation, Security Roadmap, Cloud Relocation Strategy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
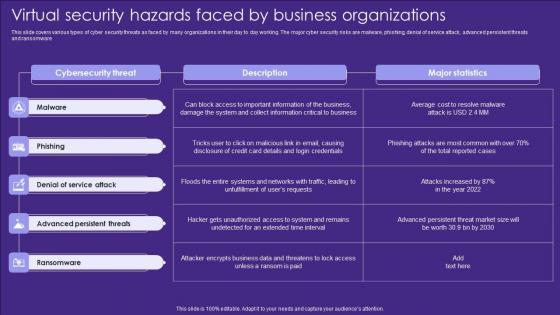
Virtual Security Hazards Faced By Business Organizations Sample Pdf
This slide covers various types of cyber security threats as faced by many organizations in their day to day working. The major cyber security risks are malware, phishing, denial of service attack, advanced persistent threats and ransomware Pitch your topic with ease and precision using this Virtual Security Hazards Faced By Business Organizations Sample Pdf. This layout presents information on Ransomware, Threats, Attack. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
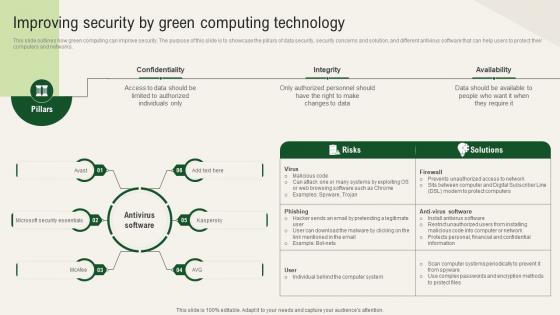
Solar Computing IT Improving Security By Green Computing Technology
This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Are you searching for a Solar Computing IT Improving Security By Green Computing Technology that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Solar Computing IT Improving Security By Green Computing Technology from Slidegeeks today.
Employee Incentives Icon For Healthcare And Financial Security Designs Pdf
Showcasing this set of slides titled Employee Incentives Icon For Healthcare And Financial Security Designs Pdf The topics addressed in these templates are Employee Incentives, Icon For Healthcare, Financial Security All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Internet Of Things Security Icon For Software Management Template Pdf
Showcasing this set of slides titled Internet Of Things Security Icon For Software Management Template Pdf The topics addressed in these templates are Internet Of Things Security, Icon For Software, Management All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Data Transfer Security Using Distributed Ledger Technology Icon Topics Pdf
Pitch your topic with ease and precision using this Data Transfer Security Using Distributed Ledger Technology Icon Topics Pdf This layout presents information on Data Transfer Security, Distributed Ledger, Technology Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Distributed Ledger Security Protocol List Icon Structure Pdf
Pitch your topic with ease and precision using this Distributed Ledger Security Protocol List Icon Structure Pdf This layout presents information on Data Transfer Security, Distributed Ledger, Technology Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf
Showcasing this set of slides titled Ecommerce Payment Security Using Distributed Ledger Technology Icon Portrait Pdf The topics addressed in these templates are Ecommerce Payment Security, Distributed Ledger, Technology Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
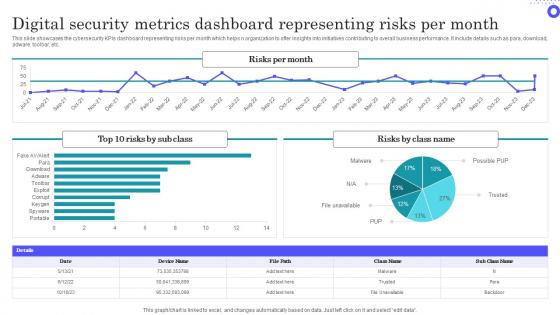
Digital Security Metrics Dashboard Representing Risks Per Month Themes Pdf
Showcasing this set of slides titled Digital Security Metrics Dashboard Representing Risks Per Month Themes Pdf The topics addressed in these templates are Digital Security, Metrics Dashboard, Representing Risks All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cyber Security Breach Icon Corrupting Devices Files Pictures Pdf
Pitch your topic with ease and precision using this Cyber Security Breach Icon Corrupting Devices Files Pictures Pdf This layout presents information on Cyber Security Breach, Icon Corrupting Devices Files It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf
Showcasing this set of slides titled Cyber Security Breach Icon Sending Malicious Emails Guidelines Pdf The topics addressed in these templates are Cyber Security Breach, Icon Sending Malicious Emails All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Data Security Strategic Agenda Checklist Icon Mockup Pdf
Pitch your topic with ease and precision using this Data Security Strategic Agenda Checklist Icon Mockup Pdf. This layout presents information on Data Security Strategic, Agenda Checklist. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
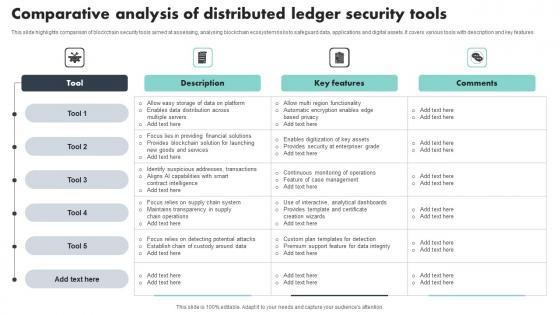
Comparative Analysis Of Distributed Ledger Security Tools Sample Pdf
This slide highlights comparison of blockchain security tools aimed at assessing, analysing blockchain ecosystem risks to safeguard data, applications and digital assets. It covers various tools with description and key features Showcasing this set of slides titled Comparative Analysis Of Distributed Ledger Security Tools Sample Pdf The topics addressed in these templates are Key Features, Comparative Analysis, Security Tools All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Security Threat Prevention Strategic Agenda Introduction Pdf
This slide represents threat prevention measures action plan for information security system. It further includes threats such as insider threats, viruses and worms, botnets, ransomware, and phishing attack. Pitch your topic with ease and precision using this Information Security Threat Prevention Strategic Agenda Introduction Pdf. This layout presents information on Security Threats, Priority Level, Action Taken. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

CASB 2 0 IT Cloud Access Security Broker And Encryption
This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Make sure to capture your audiences attention in your business displays with our gratis customizable CASB 2 0 IT Cloud Access Security Broker And Encryption. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
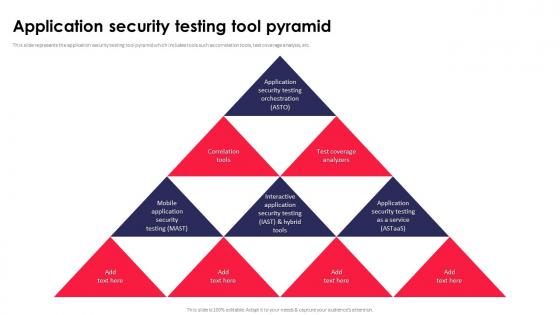
Application Security Testing Tool Pyramid Ppt Powerpoint Download
This slide represents the application security testing tool pyramid which includes tools such as correlation tools, test coverage analysis, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Application Security Testing Tool Pyramid Ppt Powerpoint Download a try. Our experts have put a lot of knowledge and effort into creating this impeccable Application Security Testing Tool Pyramid Ppt Powerpoint Download. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Zero Trust Model Traditional Perimeter Based Network Security Overview
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. If you are looking for a format to display your unique thoughts, then the professionally designed Zero Trust Model Traditional Perimeter Based Network Security Overview is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Zero Trust Model Traditional Perimeter Based Network Security Overview and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
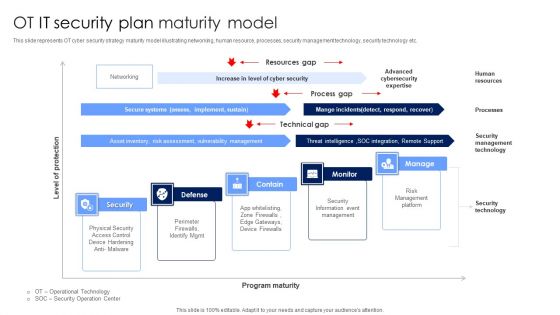
OT IT Security Plan Maturity Model Designs PDF
This slide represents OT cyber security strategy maturity model illustrating networking, human resource, processes, security management technology, security technology etc. Showcasing this set of slides titled OT IT Security Plan Maturity Model Designs PDF. The topics addressed in these templates are Security Information Event Management, Risk Management Platform, Security Technology. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
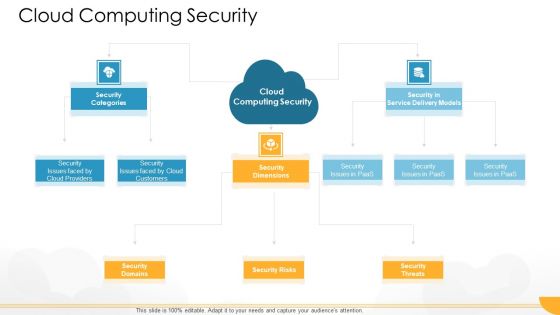
Technology Guide For Serverless Computing Cloud Computing Security Designs PDF
Presenting technology guide for serverless computing cloud computing security designs pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security categories, security domains, security risks, security threats, security dimensions. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
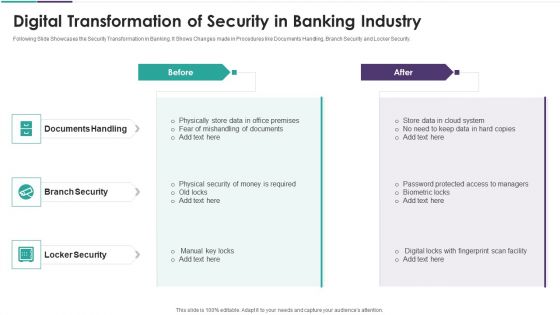
Digital Transformation Of Security In Banking Industry Elements PDF
Following Slide Showcases the Security Transformation in Banking. It Shows Changes made in Procedures like Documents Handling, Branch Security and Locker Security. Presenting digital transformation of security in banking industry elements pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including documents handling, branch security, locker security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Levels Of Security Concerns In Cloud Network Download PDF
The slide showcases levels of security concerns that measure user and device authentication. The elements are virtual machine security , network security , interface security , privacy concerns etc. Presenting Levels Of Security Concerns In Cloud Network Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Virtual Machine Security, Interface Security, Network Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
5G Network Security Technologies To Overcome Threats Icons Pdf
This slide shows 5G network technologies to overcome threats in network. It further includes dos attacks, hijacking attacks, user identity theft, scanning attacks, timings attacks and boundary attacks. Showcasing this set of slides titled 5G Network Security Technologies To Overcome Threats Icons Pdf. The topics addressed in these templates are Security Threat, Impact, Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
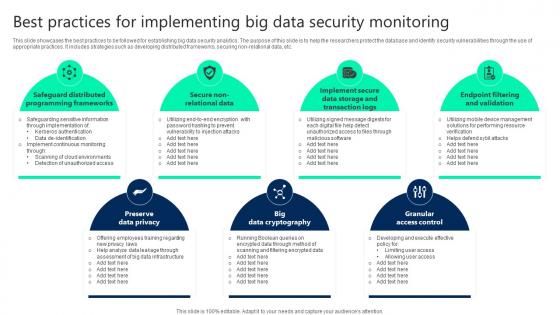
Best Practices For Implementing Big Data Security Monitoring Sample pdf
This slide showcases the best practices to be followed for establishing big data security analytics. The purpose of this slide is to help the researchers protect the database and identify security vulnerabilities through the use of appropriate practices. It includes strategies such as developing distributed frameworks, securing non-relational data, etc. Showcasing this set of slides titled Best Practices For Implementing Big Data Security Monitoring Sample pdf. The topics addressed in these templates are Preserve Data Privacy, Big Data Cryptography, Granular Access Control. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Network Security Enterprise Ppt Powerpoint Presentation Infographics Templates Cpb
This is a network security enterprise ppt powerpoint presentation infographics templates cpb. This is a five stage process. The stages in this process are network security enterprise.
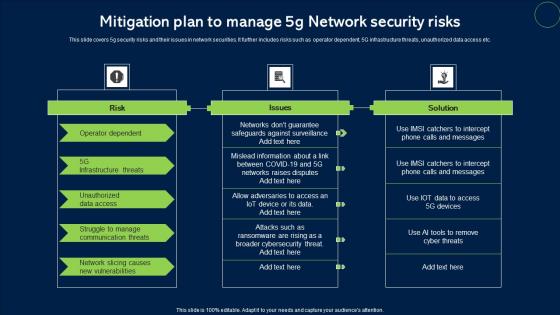
Mitigation Plan To Manage 5G Network Security Risks Microsoft Pdf
This slide covers 5g security risks and their issues in network securities. It further includes risks such as operator dependent, 5G infrastructure threats, unauthorized data access etc. Showcasing this set of slides titled Mitigation Plan To Manage 5G Network Security Risks Microsoft Pdf. The topics addressed in these templates are Risk, Issues, Solution. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Major Types Of Data Security Breaches Data Fortification Strengthening Defenses
This slide discusses the significant categories of information loss. The purpose of this slide is to describe several types of data security breaches. These include human error, device loss, cyberattacks, internal breaches, etc. Presenting this PowerPoint presentation, titled Major Types Of Data Security Breaches Data Fortification Strengthening Defenses, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Major Types Of Data Security Breaches Data Fortification Strengthening Defenses. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Major Types Of Data Security Breaches Data Fortification Strengthening Defenses that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
Security Systems Trendy Business Ppt PowerPoint Presentation Gallery Objects
This is a security systems trendy business ppt powerpoint presentation gallery objects. This is a six stage process. The stages in this process are security systems, trendy business.
Private Security Organizational Structure Ppt PowerPoint Presentation Inspiration Pictures
This is a private security organizational structure ppt powerpoint presentation inspiration pictures. This is a five stage process. The stages in this process are private security organizational structure.

Information Security Tool Ppt PowerPoint Presentation Summary Portrait Cpb
This is a information security tool ppt powerpoint presentation summary portrait cpb. This is a three stage process. The stages in this process are information security tool.
Security Growth Ppt Powerpoint Presentation Show Infographic Template Cpb
This is a security growth ppt powerpoint presentation show infographic template cpb. This is a six stage process. The stages in this process are security growth.

Enterprise Security Tools Ppt PowerPoint Presentation Infographics Skills Cpb
This is a enterprise security tools ppt powerpoint presentation infographics skills cpb. This is a four stage process. The stages in this process are enterprise security tools.

Cyber Security Business Ppt PowerPoint Presentation Inspiration Example Introduction Cpb
This is a cyber security business ppt powerpoint presentation inspiration example introduction cpb. This is a two stage process. The stages in this process are cyber security business.

Security Workforce Ppt PowerPoint Presentation Infographics Format Ideas Cpb
This is a security workforce ppt powerpoint presentation infographics format ideas cpb. This is a five stage process. The stages in this process are security workforce.
Cyber Security Solutions Ppt PowerPoint Presentation Layouts Icon Cpb
This is a cyber security solutions ppt powerpoint presentation layouts icon cpb. This is a six stage process. The stages in this process are cyber security solutions.
Types Data Security Ppt PowerPoint Presentation Styles Objects Cpb
This is a types data security ppt powerpoint presentation styles objects cpb. This is a ten stage process. The stages in this process are types data security.

Online Security Ppt PowerPoint Presentation Pictures Layout Ideas Cpb
This is a online security ppt powerpoint presentation pictures layout ideas cpb. This is a four stage process. The stages in this process are online security.

Media Security Ppt PowerPoint Presentation Inspiration File Formats Cpb
This is a media security ppt powerpoint presentation inspiration file formats cpb. This is a three stage process. The stages in this process are media security.

Security Identity Management Ppt Powerpoint Presentation Pictures Portrait Cpb
This is a security identity management ppt powerpoint presentation pictures portrait cpb. This is a eight stage process. The stages in this process are security identity management.

Cyber Security Technology Ppt PowerPoint Presentation File Template Cpb
This is a cyber security technology ppt powerpoint presentation file template cpb. This is a six stage process. The stages in this process are cyber security technology.
Cyber Security Relationship Ppt PowerPoint Presentation Layouts Designs Download Cpb
This is a cyber security relationship ppt powerpoint presentation layouts designs download cpb. This is a four stage process. The stages in this process are cyber security relationship.
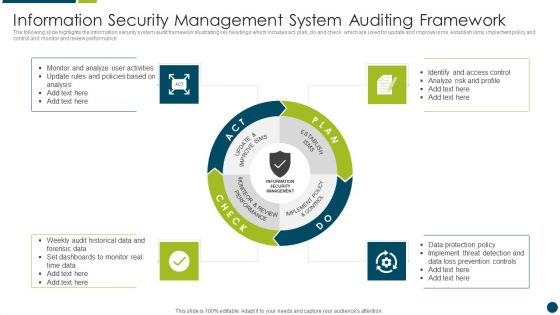
Information Security Management System Auditing Framework Microsoft PDF
The following slide highlights the information security management system audit checklist illustrating matrix consisting of domain, objective, description, identification and audit for information security policies, information security organization and human resource security Showcasing this set of slides titled Information Security Management System Auditing Framework Microsoft PDF. The topics addressed in these templates are Information Security Organization, Information Security Policies, Human Resource Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting
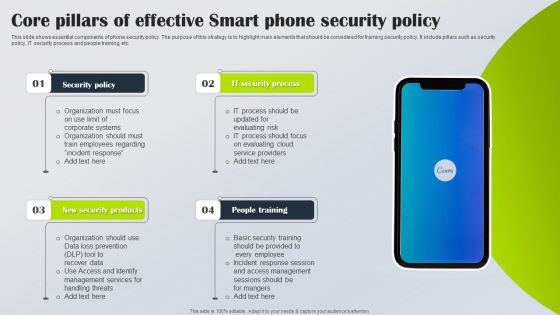
Core Pillars Of Effective Smart Phone Security Policy Slides PDF
This slide shows essential components of phone security policy. The purpose of this strategy is to highlight main elements that should be considered for framing security policy. It include pillars such as security policy, IT security process and people training, etc. Persuade your audience using this Core Pillars Of Effective Smart Phone Security Policy Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Policy, IT Security Process, New Security Products. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Comparative Analysis Of Internet Security Models Slides Pdf
This slide showcase comparison of security model for organsation data protection and app development. It include PCI DSS, MITRE, CIS and NIST Pitch your topic with ease and precision using this Comparative Analysis Of Internet Security Models Slides Pdf This layout presents information on Operative Techniques, Development Stage, Benchmark Configuration It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Digital Security Metrics Icon Showcasing Threat Protection Topics Pdf
Pitch your topic with ease and precision using this Digital Security Metrics Icon Showcasing Threat Protection Topics Pdf This layout presents information on Digital Security, Metrics Icon, Showcasing Threat Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Cyber Security Strategic Agenda For Data Protection Icon Template Pdf
Pitch your topic with ease and precision using this Cyber Security Strategic Agenda For Data Protection Icon Template Pdf. This layout presents information on Cyber Security Strategic, Agenda For Data Protection. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

It Security Training Courses Strategic Agenda To Employees Portrait Pdf
This slide represents action plan for various training courses. It includes training courses such as complete cyber security courses, etc and their description, mode, duration, and budget. Showcasing this set of slides titled It Security Training Courses Strategic Agenda To Employees Portrait Pdf. The topics addressed in these templates are Training Courses, Description, Trainer Name. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
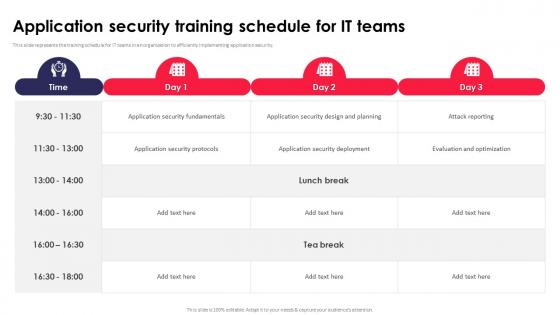
Application Security Training Schedule For IT Teams Ppt Powerpoint Portrait
This slide represents the training schedule for IT teams in an organization to efficiently implementing application security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Application Security Training Schedule For IT Teams Ppt Powerpoint Portrait will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
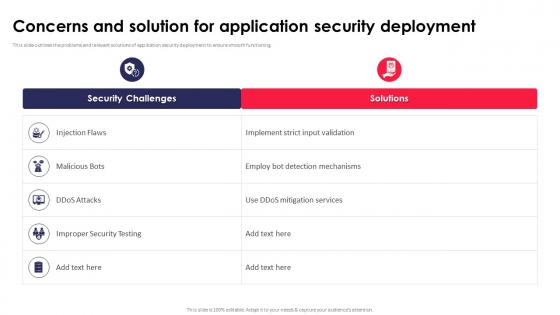
Concerns And Solution For Application Security Testing Ppt Powerpoint Infographics
This slide outlines the problems and relevant solutions of application security deployment to ensure smooth functioning. Make sure to capture your audiences attention in your business displays with our gratis customizable Concerns And Solution For Application Security Testing Ppt Powerpoint Infographics. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Architecture Of Security Harnessing The World Of Ethical Ppt Template
This slide highlights the architecture of security testing components such as user interface, controller, tester, controller, test report, test case, etc. There are so many reasons you need a Architecture Of Security Harnessing The World Of Ethical Ppt Template The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
5G Wi Fi Signal Icon For Network Security Inspiration Pdf
Pitch your topic with ease and precision using this 5G Wi Fi Signal Icon For Network Security Inspiration Pdf. This layout presents information on 5G Wi Fi Signal, Network Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
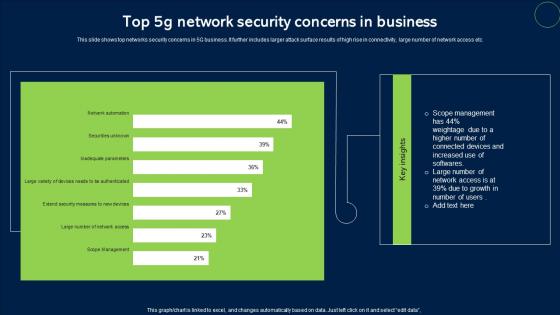
Top 5G Network Security Concerns In Business Sample Pdf
This slide shows top networks security concerns in 5G business. It further includes larger attack surface results of high rise in connectivity, large number of network access etc. Pitch your topic with ease and precision using this Top 5G Network Security Concerns In Business Sample Pdf. This layout presents information on Network Security, Concerns In Business. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Global 5G Network Security Market Size Analysis Topics Pdf
This slide shows global 5G security market size growth analysis from 2021 to 2030. It further includes key insights for technology and resources upgradation, 33percent increase in CAGR because of international funding. Pitch your topic with ease and precision using this Global 5G Network Security Market Size Analysis Topics Pdf. This layout presents information on Network Security, Market Size. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
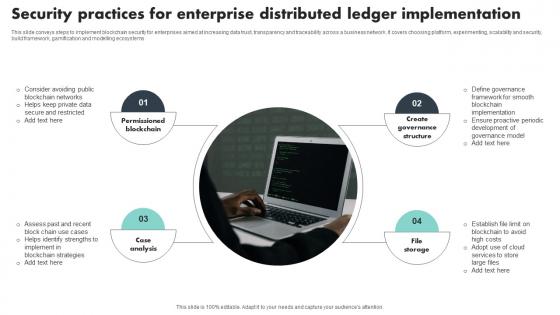
Security Practices For Enterprise Distributed Ledger Implementation Template Pdf
This slide conveys steps to implement blockchain security for enterprises aimed at increasing data trust, transparency and traceability across a business network. It covers choosing platform, experimenting, scalability and security, build framework, gamification and modelling ecosystems Showcasing this set of slides titled Security Practices For Enterprise Distributed Ledger Implementation Template Pdf The topics addressed in these templates are Permissioned Blockchain, Case Analysis, Create Governance Structure All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Distributed Ledger Security Algorithms For Business Enterprises Structure Pdf
This slide outlines blockchain security algorithms aimed at solving specific problems by safeguarding security on blockchain networks. It covers cryptography algorithms, peer to peer network controls, zero knowledge proofs and consensus algorithms Showcasing this set of slides titled Distributed Ledger Security Algorithms For Business Enterprises Structure Pdf The topics addressed in these templates are Cryptography Algorithms, Knowledge Proofs, Consensus Algorithms All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Smart Radio Military And Security Applications Icon Structure Pdf
Pitch your topic with ease and precision using this Smart Radio Military And Security Applications Icon Structure Pdf. This layout presents information on Smart Radio Military, Security Applications Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Data Breach Security Communication Plan Icon Demonstration Pdf
Showcasing this set of slides titled Data Breach Security Communication Plan Icon Demonstration Pdf The topics addressed in these templates are Data Breach, Security Communication, Plan Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Security Incident Response Communication Plan Icon Professional Pdf
Showcasing this set of slides titled Security Incident Response Communication Plan Icon Professional Pdf The topics addressed in these templates are Security Incident, Response Communication, Plan Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Security Strategic Agenda For Hotels Icon Professional Pdf
Showcasing this set of slides titled Security Strategic Agenda For Hotels Icon Professional Pdf. The topics addressed in these templates are Security Strategic, Agenda For Hotels. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Email Phishing And Internet Security Icon Microsoft Pdf
Showcasing this set of slides titled Email Phishing And Internet Security Icon Microsoft Pdf The topics addressed in these templates are Email Phishing, Internet Security Icon All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Internet Security And Data Audit Icon Pictures Pdf
Pitch your topic with ease and precision using this Internet Security And Data Audit Icon Pictures Pdf This layout presents information on Internet Security, Data Audit Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

 Home
Home