Security Risk Assessment

Cyber Security Implementation Framework Staff Training Schedule With Cost Ppt PowerPoint Presentation Pictures Slideshow PDF
Presenting this set of slides with name cyber security implementation framework staff training schedule with cost ppt powerpoint presentation pictures slideshow pdf. This is a one stage process. The stages in this process are advanced skills training, advanced software training, training module, supplier relationship management, risk management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Table Of Contents Ppt Design Ideas PDF
Presenting this set of slides with name cyber security for your organization table of contents ppt design ideas pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, role personnel, dashboard, impact analysis, cost associated firm, cybersecurity contingency plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

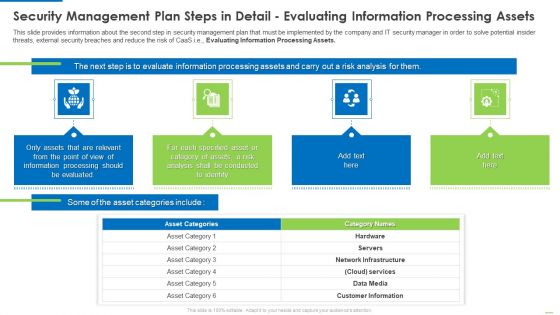
Security Management Plan Steps In Detail Evaluating Information Processing Assets Template PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Evaluating Information Processing Assets. Deliver an awe inspiring pitch with this creative security management plan steps in detail evaluating information processing assets template pdf bundle. Topics like information, network infrastructure, services, customer information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
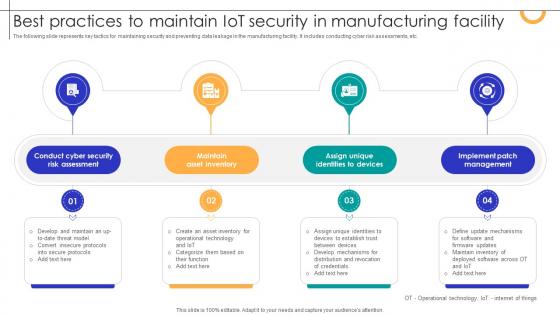
Best Practices To Maintain IOT Security In Manufacturing Facility Streamlining Production Ppt Template
The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Best Practices To Maintain IOT Security In Manufacturing Facility Streamlining Production Ppt Template With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Best Practices To Maintain IOT Security In Manufacturing Facility Streamlining Production Ppt Template today and make your presentation stand out from the rest

Key Steps Of Saas Cloud Security Process Ppt PowerPoint Presentation Gallery Design Ideas PDF
The following slide depicts the SaaS security process to acknowledge the gap and have proactive approach. It mainly constitutes of three phases discover, monitor and protect. Persuade your audience using this Key Steps Of Saas Cloud Security Process Ppt PowerPoint Presentation Gallery Design Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Discover, Monitor, Protect, Identify Utility, Assess Risk. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Developing Business Analytics Framework Facilities Offered By Implementation Of Security Centre Information PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting Developing Business Analytics Framework Facilities Offered By Implementation Of Security Centre Information PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Detection And Investigation, Phishing Detection, Left Employees In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Incident Response Techniques Deployement Cyber Security Incident Response Process Flow Chart Slides PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Incident Response Techniques Deployement Cyber Security Incident Response Process Flow Chart Slides PDF from Slidegeeks and deliver a wonderful presentation.

Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide
This slide represents the security in Infrastructure as Code tracking dashboard. The key components include container image, misconfigured workload, risk assets, failed codes by credentials, transit, valuable public interface, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Infrastructure As Code Security IAC Tools For Performance Analysis PPT Slide.

Table Of Contents For Cloud Computing Security IT Business Ppt File Inspiration PDF
Deliver an awe inspiring pitch with this creative table of contents for cloud computing security it business ppt file inspiration pdf bundle. Topics like cloud security implementation, cloud security responsibilities, cloud security management, cloud security solutions, cloud security risks or threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
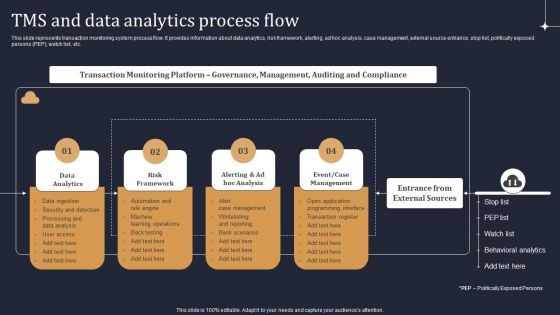
KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF
This slide represents transaction monitoring system process flow. It provides information about data analytics, risk framework, alerting, ad hoc analysis, case management, external source entrance, stop list, politically exposed persons PEP, watch list, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

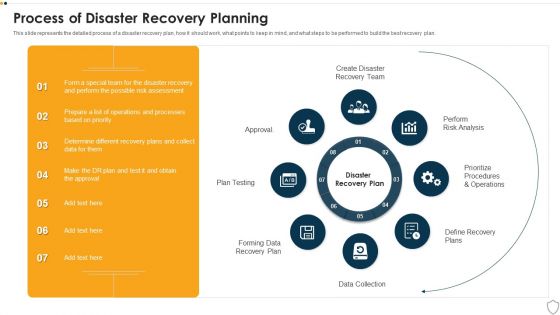
Process Of Disaster Recovery Planning IT Security IT Ppt Outline Example Introduction PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. This is a process of disaster recovery planning it security it ppt outline example introduction pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data collection, plan testing, approval, perform risk analysis, prioritize procedures and operations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

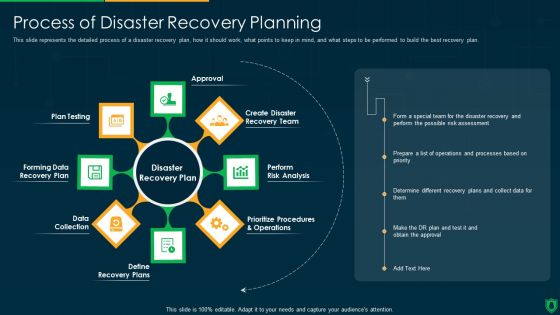
Information Security Process Of Disaster Recovery Planning Ppt Portfolio Backgrounds PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Presenting information security process of disaster recovery planning ppt portfolio backgrounds pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like recovery team, risk analysis, prioritize procedures, recovery plan, data collection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Security Process Of Disaster Recovery Planning Ppt Portfolio Microsoft PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Presenting it security process of disaster recovery planning ppt portfolio microsoft pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like plan testing, perform risk analysis, data collection, prioritize procedures and operations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Info Security Process Of Disaster Recovery Planning Ppt PowerPoint Presentation File Summary PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. This is a info security process of disaster recovery planning ppt powerpoint presentation file summary pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like approval, perform risk analysis, define recovery plans, data collection, forming data recovery plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Security Management Plan Steps In Detail Evaluating Information Processing Assets Summary PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e.Evaluating Information Processing Assets. This is a security management plan steps in detail evaluating information processing assets summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like processing should be evaluated, conducted to identify, category of assets You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Evaluating Information Processing Assets Demonstration PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Evaluating Information Processing Assets. This is a security management plan steps in detail evaluating information processing assets demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluate information, conducted to identify, specified asset You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Kpi Dashboard For Tracking Virtual Security Hazards Of Healthcare Organization Professional Pdf
This slide depicts dashboard for tracking cyber security risks faced by healthcare organizations to effectively manage the major threats and take action accordingly. The key performing indicators are percentage of risks exceeding threshold limit, breakdown of threat rating, action plan etc. Showcasing this set of slides titled Kpi Dashboard For Tracking Virtual Security Hazards Of Healthcare Organization Professional Pdf. The topics addressed in these templates are Analysis Progress, Resolution Progress, Threshold Limit. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
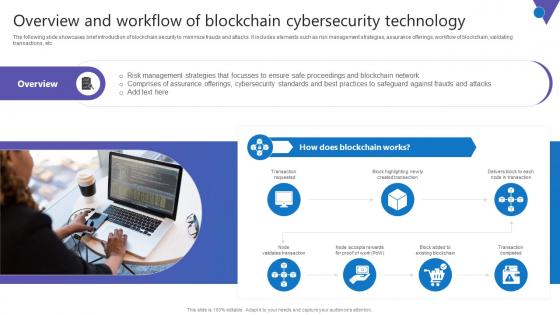
Overview And Workflow Comprehensive Guide To Blockchain Digital Security Summary Pdf
The following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc. Explore a selection of the finest Overview And Workflow Comprehensive Guide To Blockchain Digital Security Summary Pdf here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Overview And Workflow Comprehensive Guide To Blockchain Digital Security Summary Pdf to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
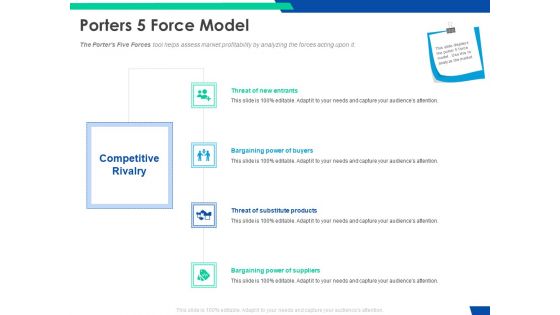
Cloud Based Email Security Market Report Porters 5 Force Model Ppt Inspiration Sample PDF
The Porters Five Forces tool helps assess market profitability by analyzing the forces acting upon it. This is a cloud based email security market report porters 5 force model ppt inspiration sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threat of new entrants, bargaining power of buyers, threat of substitute products, bargaining power of suppliers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
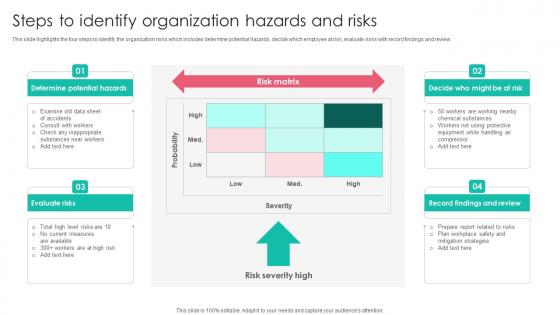
Steps To Identify Organization Hazards Workplace Safety Protocol And Security Practices Template Pdf
This slide highlights the four steps to identify the organization risks which includes determine potential hazards, decide which employee at risk, evaluate risks with record findings and review. Want to ace your presentation in front of a live audience Our Steps To Identify Organization Hazards Workplace Safety Protocol And Security Practices Template Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
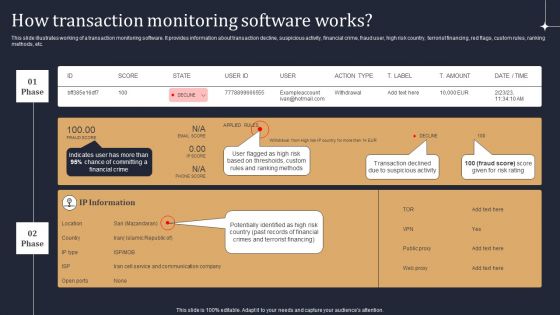
KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF
This slide illustrates working of a transaction monitoring software. It provides information about transaction decline, suspicious activity, financial crime, fraud user, high risk country, terrorist financing, red flags, custom rules, ranking methods, etc. Are you searching for a KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF from Slidegeeks today.

Aftereffects Of IT Security Threats On Business And Customers Ppt PowerPoint Presentation Layouts Background PDF
Persuade your audience using this aftereffects of it security threats on business and customers ppt powerpoint presentation layouts background pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including violation of law, crucial information loss, loss of productivity, cyber espionage, risk of losing work in future, contract breach, trust among business people, ransom ware, online banking transactions are compromised, identity theft, credit card detail theft, spam mails or other attacks violates the law, fraud to customers by scare ware or other fraud tools. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
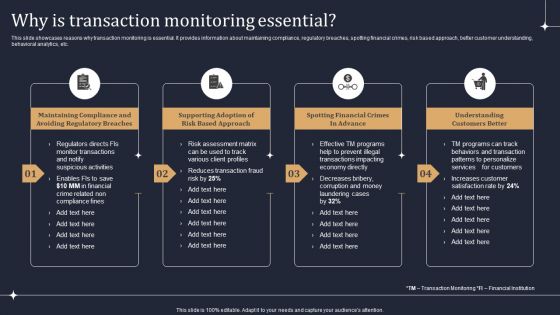
KYC Transaction Monitoring System Business Security Why Is Transaction Monitoring Essential Designs PDF
This slide showcases reasons why transaction monitoring is essential. It provides information about maintaining compliance, regulatory breaches, spotting financial crimes, risk based approach, better customer understanding, behavioral analytics, etc. Present like a pro with KYC Transaction Monitoring System Business Security Why Is Transaction Monitoring Essential Designs PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Global Data Security Industry Report Key Considerations Assumptions Of Cybersecurity Industry Report IR SS V
The slide represents key considerations and limitations while building the cybersecurity industry report. The purpose of this slide is to provide framework and context for analysis and projections in addition to acknowledging uncertainties and potential risks in the future. Make sure to capture your audiences attention in your business displays with our gratis customizable Global Data Security Industry Report Key Considerations Assumptions Of Cybersecurity Industry Report IR SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

PESTEL Analysis To Understand The Global Security Industry PPT PowerPoint IR SS V
The slide highlights the PESTEL analysis of Defense industry. The main purpose of this side is to evaluating and assessing the impact of external factors on defense market. It further helps in mitigating the potential risks. Key components include political, legal, economic, social, technological and environmental aspects. Explore a selection of the finest PESTEL Analysis To Understand The Global Security Industry PPT PowerPoint IR SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our PESTEL Analysis To Understand The Global Security Industry PPT PowerPoint IR SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Porters Framework Analysis To Global Security Industry PPT PowerPoint IR SS V
The slide highlights the porters framework analysis of Defense industry. The main purpose of this side is to evaluating and assessing the impact of external and internal factors on Defense market. It further helps in mitigating the potential risks. Key components include threat of new entrants, bargaining power, supplier power, threat of substitute, competitive rivalry. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Porters Framework Analysis To Global Security Industry PPT PowerPoint IR SS V from Slidegeeks and deliver a wonderful presentation.

Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF today and make your presentation stand out from the rest
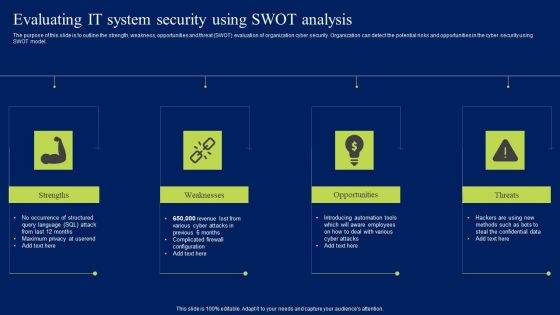
Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF today and make your presentation stand out from the rest.
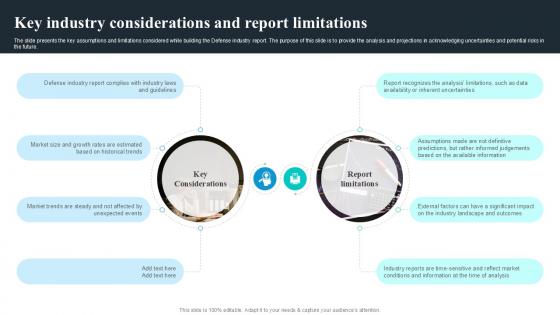
Key Industry Considerations And Report Global Security Industry PPT PowerPoint IR SS V
The slide covers the segmentation analysis in the Defense industry report. It includes attributes related to technology, type of product, services, distribution channel, geographical analysis, and key market player profile. The slide presents the key assumptions and limitations considered while building the Defense industry report. The purpose of this slide is to provide the analysis and projections in acknowledging uncertainties and potential risks in the future. Make sure to capture your audiences attention in your business displays with our gratis customizable Key Industry Considerations And Report Global Security Industry PPT PowerPoint IR SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Contd Topics PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Contd Topics PDF bundle. Topics like Security Awareness, Current Assessment, Security Standard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Internet Security Threat Analysis Plan With Icons Ppt PowerPoint Presentation Ideas Influencers PDF
Pitch your topic with ease and precision using this internet security threat analysis plan with icons ppt powerpoint presentation ideas influencers pdf. This layout presents information on inspect, preliminary assessment, extended assessment. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

How To Increase Cloud Security Threats Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name how to increase cloud security threats ppt powerpoint presentation complete deck. The topics discussed in these slides are security assessments, security threats, cloud computing security, infrastructure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Saas Cloud Security Implementation Checklist For Managers Ppt PowerPoint Presentation File Professional PDF
The following slide represents checklist for SaaS security implementation and assessment. It includes activities such as run security test, training staff, planning backup, installing automated security alert along with their status. Presenting Saas Cloud Security Implementation Checklist For Managers Ppt PowerPoint Presentation File Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Run Security Test, Planned Backup, New Threats. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
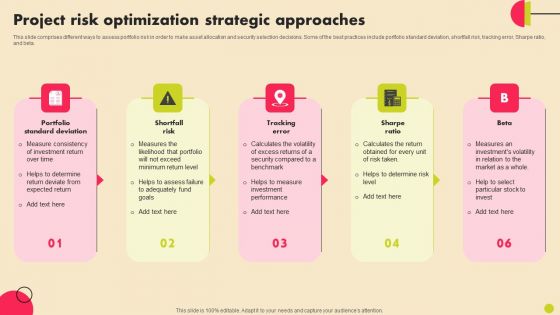
Project Risk Optimization Strategic Approaches Formats PDF
This slide comprises different ways to assess portfolio risk in order to make asset allocation and security selection decisions. Some of the best practices include portfolio standard deviation, shortfall risk, tracking error, Sharpe ratio, and beta. Persuade your audience using this Project Risk Optimization Strategic Approaches Formats PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Portfolio Standard Deviation, Shortfall Risk, Tracking Error. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Slide Microsoft PDF
Deliver and pitch your topic in the best possible manner with this Table Of Contents For Developing Cyber Security Threat Awareness Staff Training Program Slide Microsoft PDF. Use them to share invaluable insights on Current Assessment, Determining Actors, Understanding Frequency and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Dashboard To Track IT Security Playbook For Strategic Actions To Improve IT Performance Summary Pdf
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Dashboard To Track IT Security Playbook For Strategic Actions To Improve IT Performance Summary Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
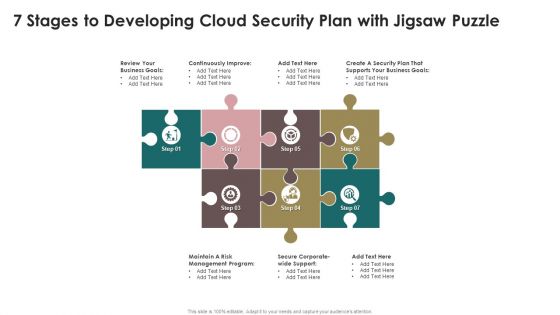
7 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Mockup PDF
Presenting 7 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Mockup PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Security Plan, Business Goals, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

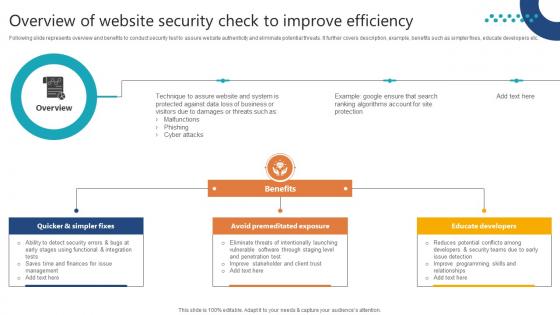
Overview Of Website Security Check To Improve Efficiency Step By Step Guide Slides PDF
Following slide represents overview and benefits to conduct security test to assure website authenticity and eliminate potential threats. It further covers description, example, benefits such as simpler fixes, educate developers etc. Want to ace your presentation in front of a live audience Our Overview Of Website Security Check To Improve Efficiency Step By Step Guide Slides PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF
The following slide highlights multistep process of managed security service to mitigate IT risks. It covers step such as operational readiness review, use cases, email notification, security analysis and event resolution. Presenting Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Event Resolution, Security Analysis, Use Cases, Operational Readiness Review. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Assessment Tools And Techniques Ppt PowerPoint Presentation Gallery Picture PDF
The slide highlights various tools of cloud audit to guide and improve the vendors performance. Various tools and techniques included are cloud controls matrix, STAR questionnaire and CSA best practices. Persuade your audience using this Cloud Assessment Tools And Techniques Ppt PowerPoint Presentation Gallery Picture PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Controls Matrix, Security, Trust, Assurance, Risk Security Questionnaire. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Introduction Of Security Testing Harnessing The World Of Ethical Ppt Powerpoint
This slide highlights the overview of security testing such as discovering and securing vulnerabilities, ensuring a threat-free software environment, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Introduction Of Security Testing Harnessing The World Of Ethical Ppt Powerpoint is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Introduction Of Security Testing Harnessing The World Of Ethical Ppt Powerpoint and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Complete Guide To Launch Overview Of Website Security Check To Improve
Following slide represents overview and benefits to conduct security test to assure website authenticity and eliminate potential threats. It further covers description, example, benefits such as simpler fixes, educate developers etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Complete Guide To Launch Overview Of Website Security Check To Improve for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Business Internet Security Threat Management And Compliance Framework Ppt PowerPoint Presentation Gallery Picture PDF
Presenting business internet security threat management and compliance framework ppt powerpoint presentation gallery picture pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including governance, risk, compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

cyber security administration in organization threat management action plan introduction pdf
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting cyber security administration in organization threat management action plan introduction pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like responsibilities, manager, assessment, manager . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Various CSR Initiatives Taken Global Security Industry PPT Presentation IR SS V
The slide highlights csr initiatives taken in Defense sector. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes financial education and literacy, supporting vulnerable communities, disaster relief and preparedness. This Various CSR Initiatives Taken Global Security Industry PPT Presentation IR SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
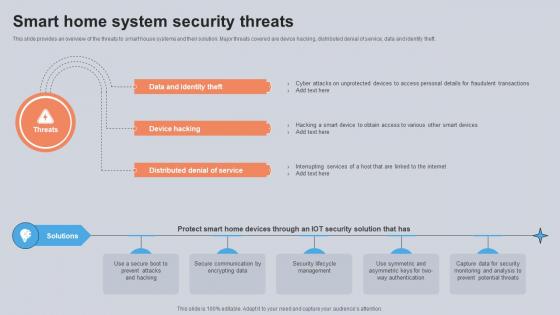
Smart Home System Security Threats Utilizing Smart Appliances IoT SS V
This slide provides an overview of the threats to smart house systems and their solution. Major threats covered are device hacking, distributed denial of service, data and identity theft. Take your projects to the next level with our ultimate collection of Smart Home System Security Threats Utilizing Smart Appliances IoT SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V
The purpose of the slide is to provide a comprehensive overview of the growth prospects in the cybersecurity market. It assists stakeholders to navigate the evolving landscape and make informed strategic decisions. It includes various growth factors such as increasing cyber threats, digital transformation, zero trust architecture, cyber insurance, IoT devices. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Global Data Security Industry Report Growth Drivers Accelerating Cybersecurity Industry IR SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
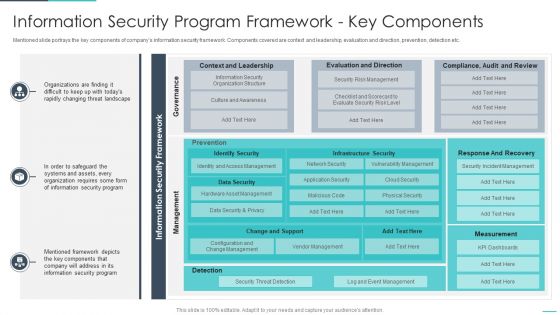
Handling Cyber Threats Digital Era Information Security Program Framework Ppt Model Summary PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era information security program framework ppt model summary pdf. Use them to share invaluable insights on information security program framework key components and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
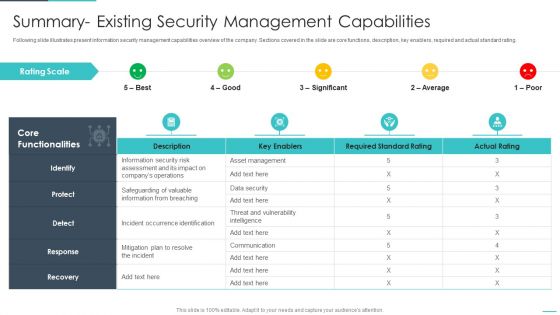
Handling Cyber Threats Digital Era Summary Existing Security Management Capabilities Ppt File Demonstration PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an awe inspiring pitch with this creative handling cyber threats digital era summary existing security management capabilities ppt file demonstration pdf bundle. Topics like summary existing security management capabilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Stages To Develop Strong Cyber Security Analysis Process Ppt PowerPoint Presentation Outline Example File PDF
Persuade your audience using this stages to develop strong cyber security analysis process ppt powerpoint presentation outline example file pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including formulate remediation steps and prioritize risks, analysing collected, recipient on the phone, teleconference. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
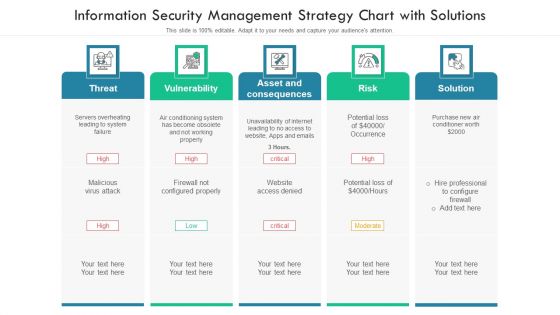
Information Security Management Strategy Chart With Solutions Ppt PowerPoint Presentation File Slides PDF
Persuade your audience using this information security management strategy chart with solutions ppt powerpoint presentation file slides pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including threat, vulnerability, risk, solution. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF today and make your presentation stand out from the rest.

Global Data Security Industry Report Porters Framework Detailed Five Forces Analysis For Cybersecurity IR SS V
The slide highlights Porters framework and its implications in the cybersecurity industry. Evaluating the five forces can assist businesses in anticipating changes in the competition, influencing the evolution of industry structure, and finding more beneficial strategic positions. It covers the threat of new entrants and substitutes, competitive rivalry, and the bargaining power of suppliers and buyers. Welcome to our selection of the Global Data Security Industry Report Porters Framework Detailed Five Forces Analysis For Cybersecurity IR SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Upgrading Total Project Safety IT Determine Established Security Centre Overview Sample PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a upgrading total project safety it determine established security centre overview sample pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident response, forensics, threat intelligence, command and control, network security monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
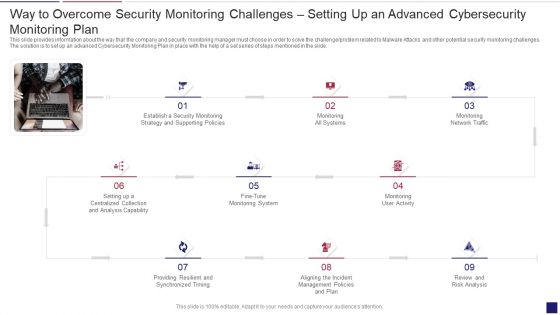
Continuous Development Evaluation Plan Eliminate Cyber Attacks Way To Overcome Security Monitoring Themes PDF
This slide provides information about the way that the company and security monitoring manager must choose in order to solve the challenge problem related to Malware Attacks and other potential security monitoring challenges. The solution is to set up an advanced Cybersecurity Monitoring Plan in place with the help of a set series of steps mentioned in the slide. This is a continuous development evaluation plan eliminate cyber attacks way to overcome security monitoring themes pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like monitoring, systems, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Overview And Key Levels Comprehensive Guide To Blockchain Digital Security Diagrams Pdf
The following slide illustrates brief introduction of honeypot scams to determine malicious activities and mitigate risks. It includes elements such as etheruem virtual machine, solidity compiler, etherscan blockchain explorer, etc. Welcome to our selection of the Overview And Key Levels Comprehensive Guide To Blockchain Digital Security Diagrams Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today

Program Evaluation Templates Bundle Security Checklist Ppt Outline Graphics Tutorials PDF
Deliver and pitch your topic in the best possible manner with this program evaluation templates bundle security checklist ppt outline graphics tutorials pdf. Use them to share invaluable insights on project it project, human threats, general threats and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
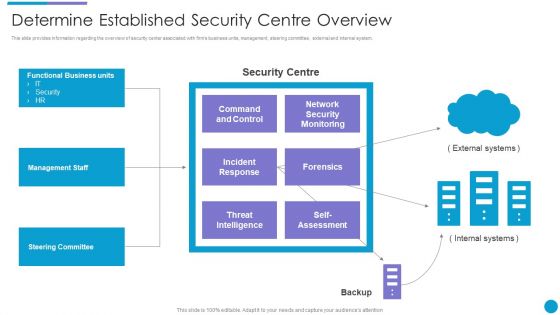
Major Techniques For Project Safety IT Determine Established Security Centre Overview Summary PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Presenting major techniques for project safety it determine established security centre overview summary pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like management staff, steering committee, functional business units, threat intelligence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
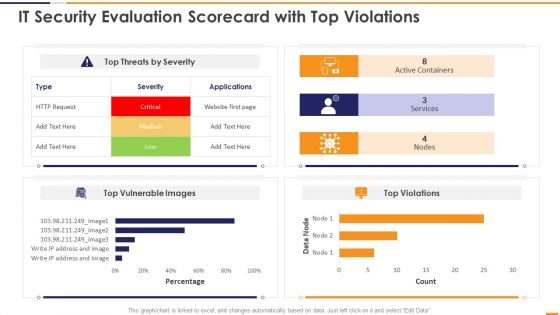
IT Security Evaluation Scorecard With Top Violations Ppt Portfolio Deck PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard With Top Violations Ppt Portfolio Deck PDF bundle. Topics like Top Threats Severity, Active Containers Services, Top Vulnerable Images can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home