Security Risk Assessment

Continuous Development Evaluation Plan Eliminate Cyber Attacks Measures And Ways To Mitigate Template PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks measures and ways to mitigate template pdf. Use them to share invaluable insights on malware attacks, pnishing attacks, ransomware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Main Concepts Of Big Data Statistical Analysis Ppt PowerPoint Presentation Pictures Introduction PDF
Presenting this set of slides with name main concepts of big data statistical analysis ppt powerpoint presentation pictures introduction pdf. This is a four stage process. The stages in this process are customer insights, security and risks, resource optimization, productivity. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Digital Transformation Toolkit Accounting Finance Accounting And Financial Software Features Slides PDF
In this slide, we have showcased key specifications and features that can help in achieving maximum efficiency in business operations like sales invoice, registration, advance security and input tax credit. This is a digital transformation toolkit accounting finance accounting and financial software features slides pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like export management, client authentication, latest security features. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Process Safety Management Sample Diagram Presentation Examples
This is a process safety management sample diagram presentation examples. This is a four stage process. The stages in this process are risk management, assess, treat, monitor, identify.
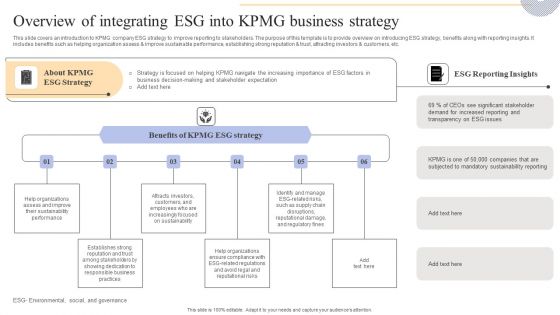
Overview Of Integrating Esg Into KPMG Business Strategy Background PDF
This slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc. This Overview Of Integrating Esg Into KPMG Business Strategy Background PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Overview Of Integrating Esg Into KPMG Business Strategy Background PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
Zero Trust Model Zero Trust Network Access Performance Tracking
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Model Zero Trust Network Access Performance Tracking is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP
This slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. The Zero Trust Network Access Performance Tracking Dashboard Software Defined Perimeter SDP is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Distributor Onboarding And Underwriting Process Slides PDF
This slide highlights the distributor onboarding process. Key stages of onboarding process involves prescreening, verification of distributors, history check, business model analysis, check for online presence, information security compliance check and credit risk analysis. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Distributor Onboarding And Underwriting Process Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Distributor Onboarding And Underwriting Process Slides PDF.
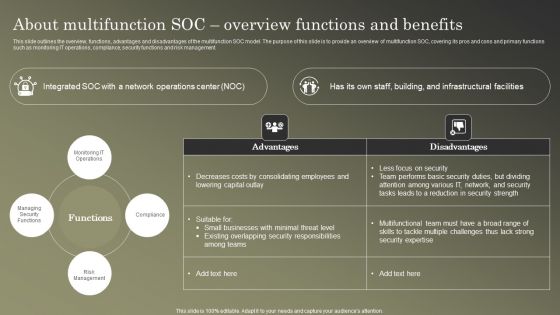
Cybersecurity Operations Cybersecops About Multifunction SOC Overview Functions Microsoft PDF
This slide outlines the overview, functions, advantages and disadvantages of the multifunction SOC model. The purpose of this slide is to provide an overview of multifunction SOC, covering its pros and cons and primary functions such as monitoring IT operations, compliance, security functions and risk management. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cybersecurity Operations Cybersecops About Multifunction SOC Overview Functions Microsoft PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

The Ultimate Guide To KPMG Other Cyber Strategies Of KPMG For Client Data Strategy SS V
This slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc. Take your projects to the next level with our ultimate collection of The Ultimate Guide To KPMG Other Cyber Strategies Of KPMG For Client Data Strategy SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Post COVID Organizational Planning Model Use Of Protective Equipment At Workplace Sample PDF
This template depicts that employers are encouraged to complete a risk assessment to determine when and which protective equipment may be required. It also illustrates workers must use protective equipment as required by their employer. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Post COVID Organizational Planning Model Use Of Protective Equipment At Workplace Sample PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Post COVID Organizational Planning Model Use Of Protective Equipment At Workplace Sample PDF today and make your presentation stand out from the rest.

Post COVID Organizational Planning Model Employer Responsibilities At Post Pandemic Workplace Elements PDF
This template depicts that employers are encouraged to complete a risk assessment to determine when and which protective equipment may be required. It also illustrates workers must use protective equipment as required by their employer. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Post COVID Organizational Planning Model Employer Responsibilities At Post Pandemic Workplace Elements PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
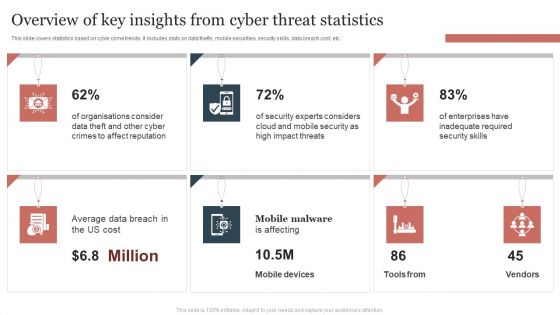
Overview Of Key Insights From Cyber Threat Statistics Themes PDF
This slide covers statistics based on cyber crime trends. It includes stats on data thefts, mobile securities, security skills, data breach cost, etc. Showcasing this set of slides titled Overview Of Key Insights From Cyber Threat Statistics Themes PDF. The topics addressed in these templates are Overview Of Key Insights, Cyber Threat Statistics . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Major Challenges Neobanks Are Facing Currently Ppt Portfolio Master Slide PDF
This slide shows information about various problems and issues which are faced by neobanks in the market. These challenge includes security issues, regulatory challenges, technological risks and no physical existence. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Major Challenges Neobanks Are Facing Currently Ppt Portfolio Master Slide PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Achieving Financial Operational Efficiency In Treasury Framework Ppt PowerPoint Presentation Summary Slide Portrait
Presenting this set of slides with name achieving financial operational efficiency in treasury framework ppt powerpoint presentation summary slide portrait. This is a nine stage process. The stages in this process are liquidity risk management, capital structure management, interest rate risk management, foreign exchange risk management, cost savings, yield enhancement, directing resources to best opportunities, profitability protection, efficiency gains. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Most Effective Measures For Ict Contingency Planning Ppt Slides
This is a most effective measures for ict contingency planning ppt slides. This is a six stage process. The stages in this process are risk analysis business impact analysis, residual risk, threat models threat assessments, legislation tasks protected assets, available resources, protective measures, incident management measures, recovery measures.

Supply Chain Management With Inventory And Planning Topics PDF
This slide shows the supply chain services model which covers network, transport, risk, cost to serve, inventory planning, with network design, source optimization, carrier selection, transport optimization, auditing risk, transport benchmarking, sales policies, etc. Pitch your topic with ease and precision using this Supply Chain Management With Inventory And Planning Topics PDF. This layout presents information on Optimizing Transport, Supply Risk, Risk Auditing. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Safety Planning Example Powerpoint Layout
This is a safety planning example powerpoint layout. This is a five stage process. The stages in this process are emergency response, plan development, plan testing, risk assessment, disaster recovery.

Safety Management Model Ppt Sample Presentations
This is a safety management model ppt sample presentations. This is a six stage process. The stages in this process are incident risk assessment, safety meeting management, worksite inspections, action item tracking, incident tracking, employee qualifications training, effective safety management.

Effective Safety Management Business Diagram Ppt Slides
This is a effective safety management business diagram ppt slides. This is a six stage process. The stages in this process are incident risk assessment, worksite inspections, safety meeting management, action item tracking, incident tracking, employee qualifications and training.
Construction Safety Management Plan Powerpoint Slides Ideas
This is a construction safety management plan powerpoint slides ideas. This is a five stage process. The stages in this process are risk assessment, incident management, standard operating products, employee training, continual improvement.

Stages Of Ensuring Data Protection Regulation Ppt PowerPoint Presentation Inspiration Gallery PDF
Persuade your audience using this stages of ensuring data protection regulation ppt powerpoint presentation inspiration gallery pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including risk assessment, certification, report and remediation, complete checklist, collect documentary evidences, complete risk assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Challenges Faced By Job Safety Professionals Topics PDF
This slide shows the key challenges that workplace safety professionals are facing such as incidents, proactive risk assessment, task management, communication and managing training requirements Presenting key challenges faced by job safety professionals topics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including incidents, proactive risk assessment, task management, communication. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Problem Solution Payment Gateway Provider Startup GTM Strategy GTM SS V
The following slide showcases various gaps addressed in market along with desired state through the launch of ABC digital payment provider startup. It includes gaps such as security concerns and fraud risks, lacks responsive support team, etc.The following slide showcases various gaps addressed in market along with desired state through the launch of ABC digital payment provider startup. It includes gaps such as security concerns and fraud risks, lacks responsive support team, etc.This Problem Solution Payment Gateway Provider Startup GTM Strategy GTM SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Problem Solution Payment Gateway Provider Startup GTM Strategy GTM SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
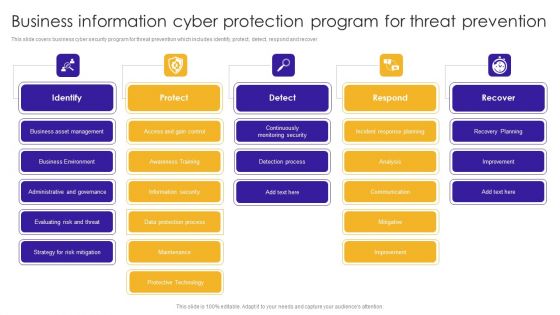
Business Information Cyber Protection Program For Threat Prevention Background PDF
This slide covers business cyber security program for threat prevention which includes identify, protect, detect, respond and recover.Showcasing this set of slides titled Business Information Cyber Protection Program For Threat Prevention Background PDF. The topics addressed in these templates are Business Environment, Administrative Governance, Evaluating Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Weekly Project Status Report To Review Overall Progress Information PDF
Persuade your audience using this Weekly Project Status Report To Review Overall Progress Information PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cybersecurity Risk, Action Plan, Security Awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
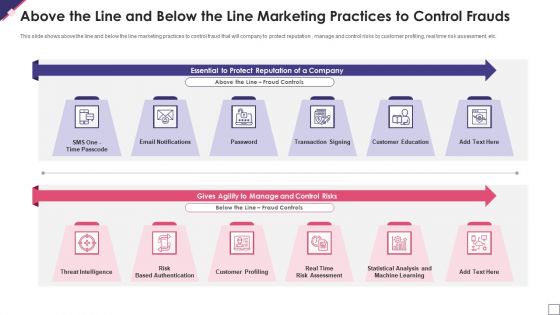
Above The Line And Below The Line Marketing Practices To Control Frauds Brochure PDF
This slide shows above the line and below the line marketing practices to control fraud that will company to protect reputation , manage and control risks by customer profiling, real time risk assessment, etc. Persuade your audience using this above the line and below the line marketing practices to control frauds brochure pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including essential to protect reputation of a company, gives agility to manage and control risks. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Steps To Formulate Emergency Response Planning Plan Clipart PDF
This template covers the procedure for creating disaster tackling plan. This slide highlights the importance of creating teams and conducting risk assessments to frame successful business continuity plans. It includes assembling continuity team, ensuring employee safety, etc. Presenting Steps To Formulate Emergency Response Planning Plan Clipart PDF Infographics to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Assemble Continuity Team, Understand Company Risks, Implement Recovery Strategies. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Enterprise Integration Solution Diagram Powerpoint Guide
This is a enterprise integration solution diagram powerpoint guide. This is a six stage process. The stages in this process are policy management, log management, vulnerability assessment, web application scanning, file integrity monitoring, vulnerability management, discovery, protection, monitoring, reporting, security, risk and compliance.

Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF
This slide talks about the overview of the co-managed security operation center, including its objective and benefits. The purpose of this slide is to highlight the main benefits of co-managed SOC, covering enhancing threat detection and response, scalability, cost savings and increased security knowledge. If you are looking for a format to display your unique thoughts, then the professionally designed Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cybersecurity Operations Cybersecops About Co Managed SOC Overview Objectives Template PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
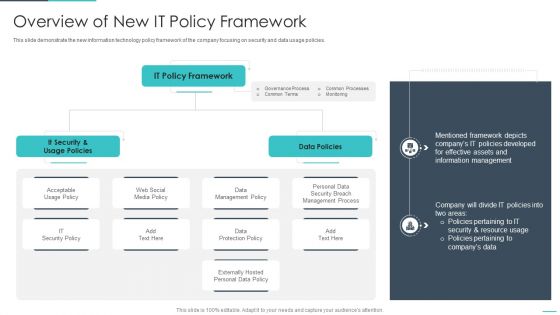
Handling Cyber Threats Digital Era Overview Of New IT Policy Framework Ppt Summary Guidelines PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era overview of new it policy framework ppt summary guidelines pdf. Use them to share invaluable insights on overview of new it policy framework and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Safety Incident Management Determine Threat Scenario Analysis Background PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Presenting cyber safety incident management determine threat scenario analysis background pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like determine threat scenario analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Key Template PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. Presenting global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats key template pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Infographics PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. This is a global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats infographics pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Wireless Banking To Improve Digital Major Challenges Neobanks Are Facing Currently Fin SS V
This slide shows information about various problems and issues which are faced by neobanks in the market. These challenge includes security issues, regulatory challenges, technological risks and no physical existence Welcome to our selection of the Wireless Banking To Improve Digital Major Challenges Neobanks Are Facing Currently Fin SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Uses Of Data Stewardship Program In Business Inspiration PDF
This slide represents the uses of a data stewardship program that includes resolving any data or data-related challenges, decreasing risks by security measures, improving data documentation, developing and using quality measures, and so on. Are you searching for a Uses Of Data Stewardship Program In Business Inspiration PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Uses Of Data Stewardship Program In Business Inspiration PDF from Slidegeeks today.

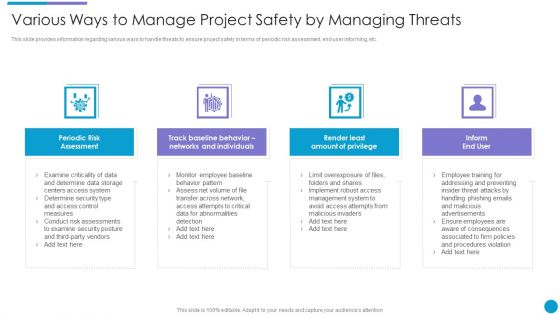
Upgrading Total Project Safety IT Various Ways To Manage Project Safety By Managing Threats Designs PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. This is a upgrading total project safety it various ways to manage project safety by managing threats designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like periodic risk assessment, inform end user, render least amount of privilege, track baseline behavior networks and individuals. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Major Techniques For Project Safety IT Various Ways To Manage Project Safety By Managing Threats Access Structure PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. This is a major techniques for project safety it various ways to manage project safety by managing threats access structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like periodic risk assessment, track baseline behavior networks and individuals, render least amount of privilege, inform end user. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
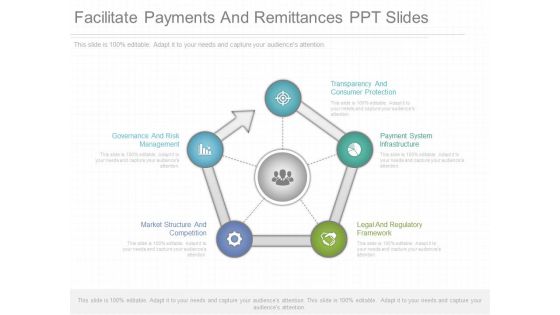
Facilitate Payments And Remittances Ppt Slides
This is a facilitate payments and remittances ppt slides. This is a five stage process. The stages in this process are governance and risk management, market structure and competition, legal and regulatory framework, payment system infrastructure, transparency and consumer protection.

Application Development Life Cycle Phase 2 Designing The Product Architecture Template PDF
This slide depicts the designing of the product architecture phase of SDLC, including the factors documented in the DDS sheet such as risk assessment, product resilience, design flexibility, cost, etc. Presenting application development life cycle phase 2 designing the product architecture template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like overview and importance of secure sdlc. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Tools And Methods For Industrial Hazard Control Methods Ppt Icon Skills PDF
This slide shows induction tools for industrial safety which ensures reduction in accidents and injuries in company. It includes risk assessment, emergency management, HAZOP study, and general public awareness. Presenting Tools And Methods For Industrial Hazard Control Methods Ppt Icon Skills PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Risk Assessment, HAZOP Study, General Public Awareness, Emergency Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
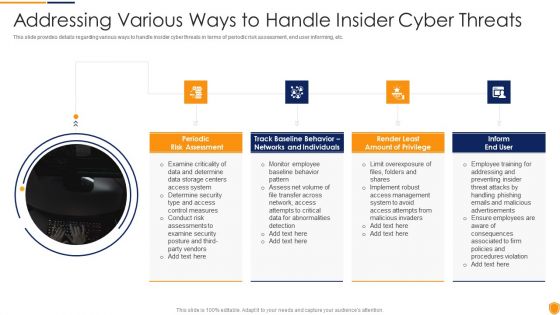
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Various Ways Template PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a mitigating cybersecurity threats and vulnerabilities addressing various ways template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like periodic risk assessment, networks and individuals, inform end user. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agile Machine Learning Fraud Detection Ensuring Organizational Safety Using AML Transaction Demonstration PDF
This slide showcases agile machine learning fraud detection framework. It provides details about banking risk, merchant risk, acquiring risk, case manager, risk engine, connectors, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Agile Machine Learning Fraud Detection Ensuring Organizational Safety Using AML Transaction Demonstration PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Business Application Threat Modeling Procedure Designs PDF
This slide contains application threat modeling process to evaluate and manage risks. It includes four steps identify fundamentals, data flow, security profile and recommendations. Persuade your audience using this Business Application Threat Modeling Procedure Designs PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Examine Existing, Understand Capabilities, Recommendations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Ways To Accomplish ISO 27001 Accreditation Incorporation Of ISMS Framework Into Corporate Microsoft PDF
Mentioned slide displays the incorporation of information security management system framework within the corporate control process. This is a Ways To Accomplish ISO 27001 Accreditation Incorporation Of ISMS Framework Into Corporate Microsoft PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Company Objectives, Company Management, Company Risks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
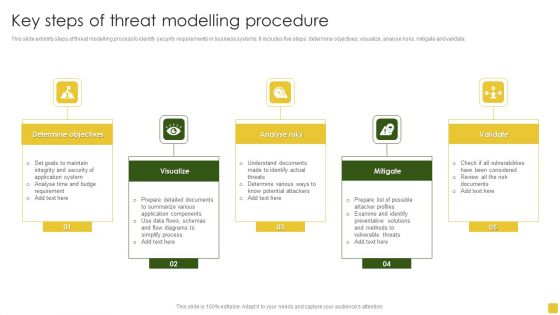
Key Steps Of Threat Modelling Procedure Brochure PDF
This slide exhibits steps of threat modelling process to identify security requirements in business systems. It includes five steps determine objectives, visualize, analyse risks, mitigate and validate.Persuade your audience using this Key Steps Of Threat Modelling Procedure Brochure PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Determine Objectives, Preventative Solutions, Determine Various Ways. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
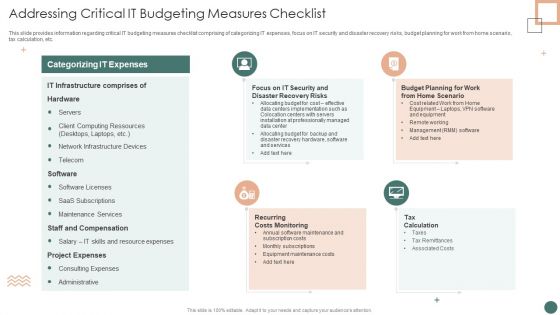
Improved Digital Expenditure Addressing Critical IT Budgeting Measures Checklist Diagrams PDF
This slide provides information regarding critical IT budgeting measures checklist comprising of categorizing IT expenses, focus on IT security and disaster recovery risks, budget planning for work from home scenario, tax calculation, etc. Deliver and pitch your topic in the best possible manner with this Improved Digital Expenditure Addressing Critical IT Budgeting Measures Checklist Diagrams PDF. Use them to share invaluable insights on Infrastructure Comprises, Budget Planning, Costs Monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Digitalization Of Operative Enterprises Launch Of Cyber IT OT Strategy Themes PDF
This slide covers IT or OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT teams etc. Presenting Digitalization Of Operative Enterprises Launch Of Cyber IT OT Strategy Themes PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Cybersecurity, Cyber Risk, Process Of Evaluating. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Devsecops Pipeline Continuous Integration Commit Stage Role Of Devsecops Ppt Sample
This slide discusses the continuous integration commit stage of the DevSecOps pipeline. The purpose of this slide is to explain the commit phase, which includes automating testing, speed, immediate feedback, identifying risk, security scanning, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable Devsecops Pipeline Continuous Integration Commit Stage Role Of Devsecops Ppt Sample These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
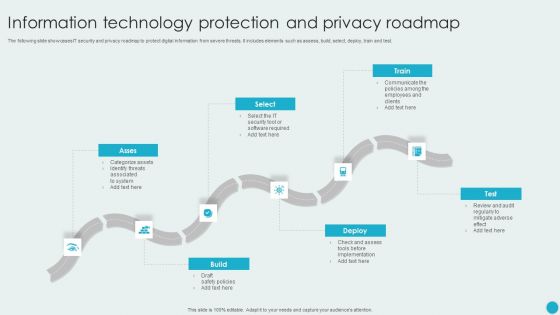
Information Technology Protection And Privacy Roadmap Sample PDF
The following slide showcases IT security and privacy roadmap to protect digital information from severe threats. It includes elements such as assess, build, select, deploy, train and test. Persuade your audience using this Information Technology Protection And Privacy Roadmap Sample PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Deploy, Build, Select, Train. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Online Safety Training Program Course Matrix Ppt Layouts Example PDF
The following slide highlights the various online safety training courses for various professional roles to identify hazards and maintain safe workplace environment. It includes professional roles such as, risk control, presentation etc. Persuade your audience using this online safety training program course matrix ppt layouts example pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including safety professional roles, data gathering and assessment, risk control, program evaluation and control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
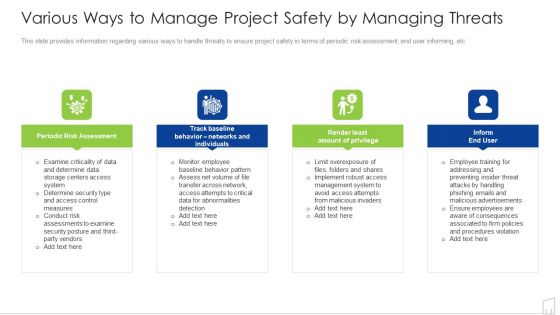
Various Ways To Manage Project Safety By Managing Threats Ppt Ideas Deck PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of periodic risk assessment, end user informing, etc. Presenting various ways to manage project safety by managing threats ppt ideas deck pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like determine, system, data, risk, periodic. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
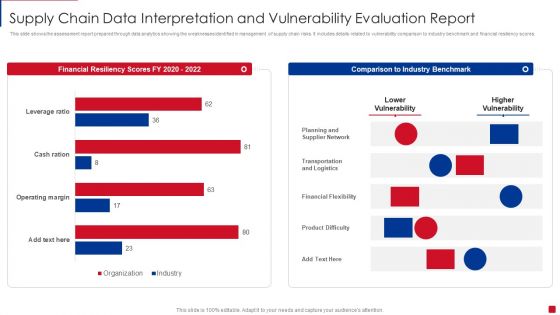
Supply Chain Data Interpretation And Vulnerability Evaluation Report Pictures PDF
This slide shows the assessment report prepared through data analytics showing the weaknesses identified in management of supply chain risks. It includes details related to vulnerability comparison to industry benchmark and financial resiliency scores Showcasing this set of slides titled Supply Chain Data Interpretation And Vulnerability Evaluation Report Pictures PDF. The topics addressed in these templates are Planning And Supplier Network, Transportation And Logistics, Financial Flexibility. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Agile Threat Modeling Overview About Duration Process Guide For Ethical Technology Icons Pdf
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Create an editable Agile Threat Modeling Overview About Duration Process Guide For Ethical Technology Icons Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agile Threat Modeling Overview About Duration Process Guide For Ethical Technology Icons Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
Agile Threat Modeling Overview About Duration Responsible Tech Guide To Manage Inspiration Pdf
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Create an editable Agile Threat Modeling Overview About Duration Responsible Tech Guide To Manage Inspiration Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agile Threat Modeling Overview About Duration Responsible Tech Guide To Manage Inspiration Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Agile Threat Modeling Overview About Duration Process Crafting A Sustainable Company Designs Pdf
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Create an editable Agile Threat Modeling Overview About Duration Process Crafting A Sustainable Company Designs Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agile Threat Modeling Overview About Duration Process Crafting A Sustainable Company Designs Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Iot Device Updates And Maintenance Overview Iot Device Management Guidelines Pdf
This slide exhibits IoT device updates management overview and benefits in order to improve device performance. It includes benefits such as a reduction in security threats, fewer bugs, enhance user experience and an increase in performance. Find a pre-designed and impeccable Iot Device Updates And Maintenance Overview Iot Device Management Guidelines Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
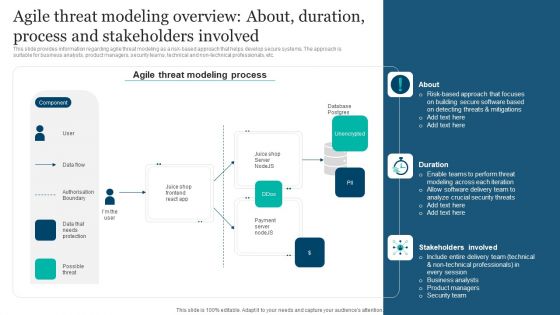
Responsible Technology Playbook Agile Threat Modeling Overview About Duration Process Elements PDF
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. This modern and well-arranged Responsible Technology Playbook Agile Threat Modeling Overview About Duration Process Elements PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
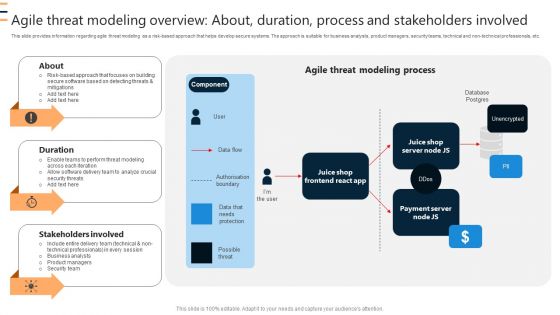
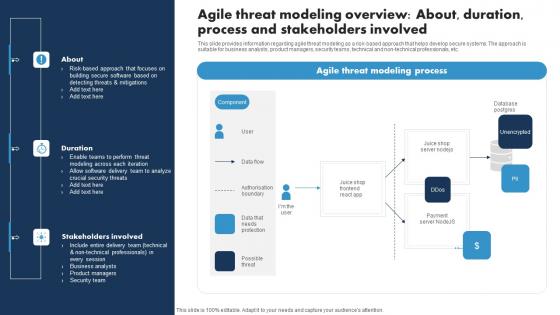
Agile Threat Modeling Overview About Duration Process And Stakeholders Involved Ppt Pictures Graphics Template PDF
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Boost your pitch with our creative Agile Threat Modeling Overview About Duration Process And Stakeholders Involved Ppt Pictures Graphics Template PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
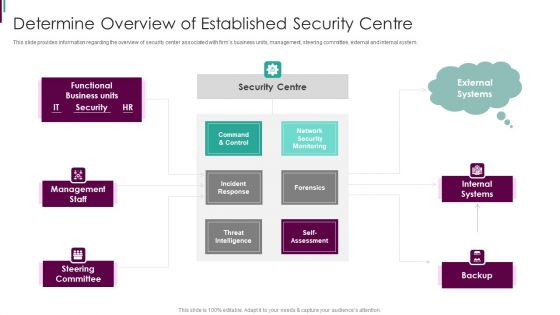
Developing Business Analytics Framework Determine Overview Of Established Themes PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a Developing Business Analytics Framework Determine Overview Of Established Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Command And Control, Incident Response, Threat Intelligence You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

 Home
Home