Scam
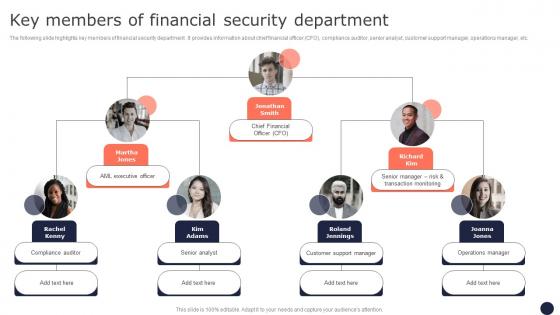
Key Members Of Financial Security Department Mitigating Corporate Scams And Robberies Designs Pdf
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. This Key Members Of Financial Security Department Mitigating Corporate Scams And Robberies Designs Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Key Members Of Financial Security Department Mitigating Corporate Scams And Robberies Designs Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
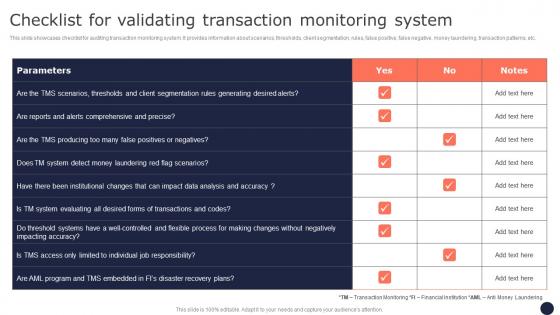
Checklist For Validating Transaction Monitoring Mitigating Corporate Scams And Robberies Infographics Pdf
This slide showcases checklist for auditing transaction monitoring system. It provides information about scenarios, thresholds, client segmentation, rules, false positive, false negative, money laundering, transaction patterns, etc. There are so many reasons you need a Checklist For Validating Transaction Monitoring Mitigating Corporate Scams And Robberies Infographics Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
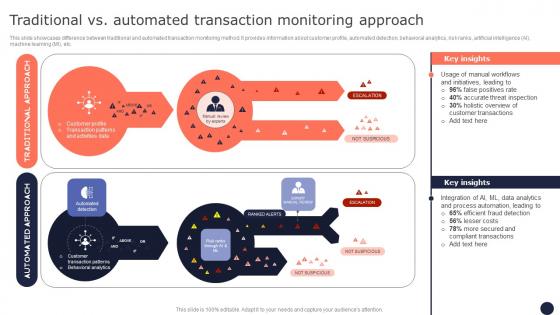
Traditional Vs Automated Transaction Monitoring Mitigating Corporate Scams And Robberies Clipart Pdf
This slide showcases difference between traditional and automated transaction monitoring method. It provides information about customer profile, automated detection, behavioral analytics, risk ranks, artificial intelligence AI, machine learning MI, etc. There are so many reasons you need a Traditional Vs Automated Transaction Monitoring Mitigating Corporate Scams And Robberies Clipart Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

5 Key Practices To Prevent Cyber Phishing Scams And Attacks Graphics PDF
Mentioned slide showcases best practices which can be implemented to prevent cyber phishing. The practices are recognizing hyperlinks attached in an email, backup system copies, secure robust HTTPs connections, installing a firewall and using anti spam tools. Presenting 5 key practices to prevent cyber phishing scams and attacks graphics pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including secure, device, reduced. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
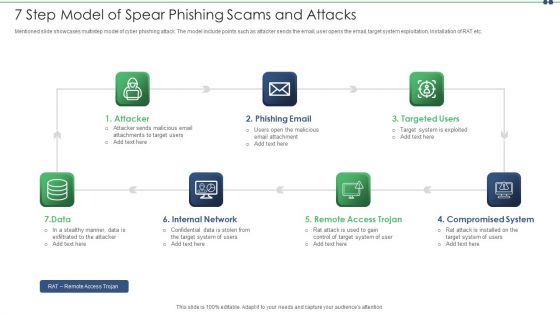
7 Step Model Of Spear Phishing Scams And Attacks Designs PDF
Mentioned slide showcases multistep model of cyber phishing attack. The model include points such as attacker sends the email, user opens the email, target system exploitation, installation of RAT etc. Persuade your audience using this 7 step model of spear phishing scams and attacks designs pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including internal network, compromised system, targeted users. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Major Cyber Phishing Scams And Attacks With Key Strategies Slides PDF
Mentioned slide showcases various cyber phishing attacks such as deceptive, spear, whaling and vishing. It provides detailed information about likelihood of attack, examples of attacks and strategies which can be implemented to overcome phishing attacks. Showcasing this set of slides titled major cyber phishing scams and attacks with key strategies slides pdf. The topics addressed in these templates are target, information, email. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
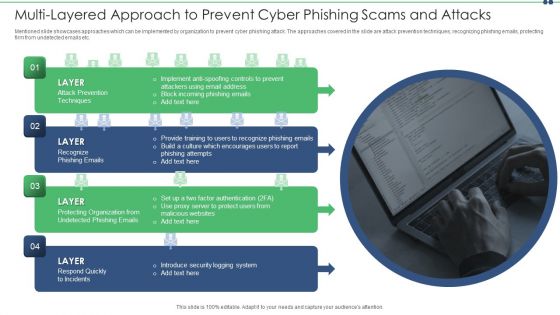
Multi Layered Approach To Prevent Cyber Phishing Scams And Attacks Themes PDF
Mentioned slide showcases approaches which can be implemented by organization to prevent cyber phishing attack. The approaches covered in the slide are attack prevention techniques, recognizing phishing emails, protecting firm from undetected emails etc. Presenting multi layered approach to prevent cyber phishing scams and attacks themes pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including email, implement, system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Phishing Scams And Attacks Assessment And Cyber Security Training Inspiration PDF
Mentioned slide showcases phishing awareness training program used to prevent cyber attacks. It provides detailed information about deploying phishing program within the organization, analyzing and preparing reports, developing training and education etc. Persuade your audience using this phishing scams and attacks assessment and cyber security training inspiration pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including analyze, develop, measure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
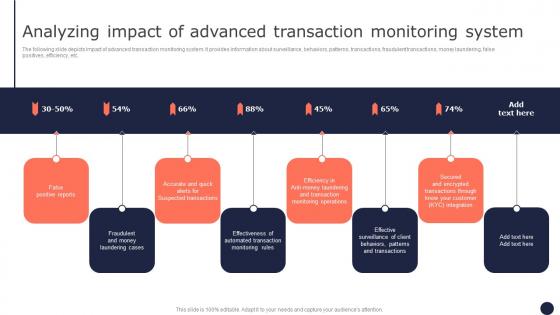
Analyzing Impact Of Advanced Transaction Mitigating Corporate Scams And Robberies Mockup Pdf
The following slide depicts impact of advanced transaction monitoring system. It provides information about surveillance, behaviors, patterns, transactions, fraudulent transactions, money laundering, false positives, efficiency, etc. Boost your pitch with our creative Analyzing Impact Of Advanced Transaction Mitigating Corporate Scams And Robberies Mockup Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Blockchain Technology For AML Transactions Mitigating Corporate Scams And Robberies Microsoft Pdf
This slide showcases blockchain technology for anti money laundering AML and transaction monitoring. It provides information about transaction subsets, input data, monitoring, analysis, alerts, record, red flags, Want to ace your presentation in front of a live audience Our Blockchain Technology For AML Transactions Mitigating Corporate Scams And Robberies Microsoft Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Enhancing Identification Process Through Customer Mitigating Corporate Scams And Robberies Sample Pdf
This slide showcases improving transaction monitoring process through customer segmentation. It provides information about algorithm , membership, transaction patterns and activities, customer data, fraud, compliance, false positives, data analysis, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Enhancing Identification Process Through Customer Mitigating Corporate Scams And Robberies Sample Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
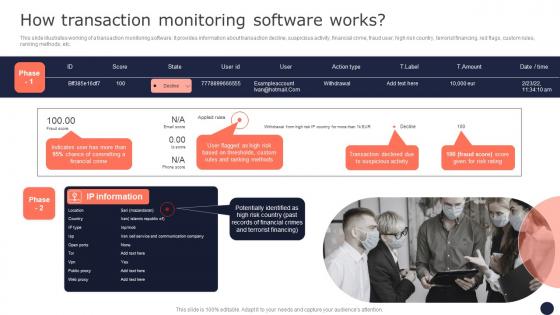
How Transaction Monitoring Software Works Mitigating Corporate Scams And Robberies Demonstration Pdf
This slide illustrates working of a transaction monitoring software. It provides information about transaction decline, suspicious activity, financial crime, fraud user, high risk country, terrorist financing, red flags, custom rules, ranking methods, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable How Transaction Monitoring Software Works Mitigating Corporate Scams And Robberies Demonstration Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
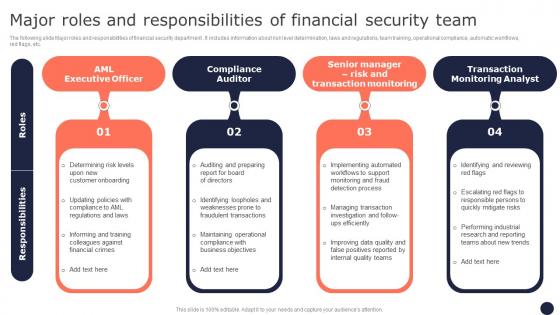
Major Roles And Responsibilities Of Financial Mitigating Corporate Scams And Robberies Topics Pdf
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Major Roles And Responsibilities Of Financial Mitigating Corporate Scams And Robberies Topics Pdf from Slidegeeks and deliver a wonderful presentation.

Numerous Types Of Transaction Monitoring Mitigating Corporate Scams And Robberies Diagrams Pdf
This slide showcases cryptocurrency transaction monitoring with alert status. It provides information about address, risk level, currencies, bitcoin, Ethereum, date added, deposits, case status, alerts, deposits, darknet, etc. Slidegeeks has constructed Numerous Types Of Transaction Monitoring Mitigating Corporate Scams And Robberies Diagrams Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
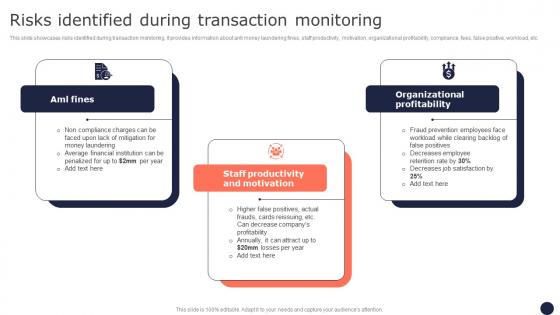
Risks Identified During Transaction Monitoring Mitigating Corporate Scams And Robberies Background Pdf
This slide showcases risks identified during transaction monitoring. It provides information about anti money laundering fines, staff productivity, motivation, organizational profitability, compliance, fees, false positive, workload, etc. Take your projects to the next level with our ultimate collection of Risks Identified During Transaction Monitoring Mitigating Corporate Scams And Robberies Background Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest.
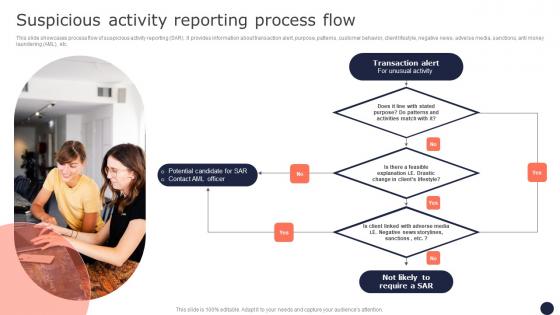
Suspicious Activity Reporting Process Flow Mitigating Corporate Scams And Robberies Demonstration Pdf
This slide showcases process flow of suspicious activity reporting SAR. It provides information about transaction alert, purpose, patterns, customer behavior, client lifestyle, negative news, adverse media, sanctions, anti money laundering AML, etc. Find a pre-designed and impeccable Suspicious Activity Reporting Process Flow Mitigating Corporate Scams And Robberies Demonstration Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
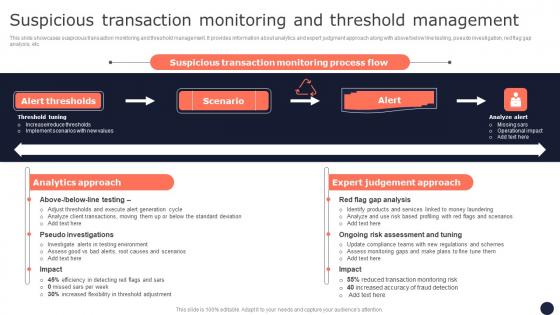
Suspicious Transaction Monitoring And Threshold Mitigating Corporate Scams And Robberies Diagrams Pdf
This slide showcases suspicious transaction monitoring and threshold management. It provides information about analytics and expert judgment approach along with abovebelow line testing, pseudo investigation, red flag gap analysis, etc. Boost your pitch with our creative Suspicious Transaction Monitoring And Threshold Mitigating Corporate Scams And Robberies Diagrams Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Timeline Implementing Transaction Monitoring Mitigating Corporate Scams And Robberies Topics Pdf
This slide showcases timeline to introduce transaction monitoring system. It provides information about scenario planning, threshold setting, deployment, project management office PMO, project planning, scenario identification, data source identification, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Timeline Implementing Transaction Monitoring Mitigating Corporate Scams And Robberies Topics Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
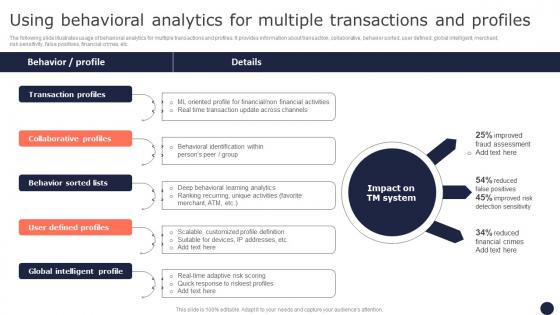
Using Behavioral Analytics For Multiple Mitigating Corporate Scams And Robberies Themes Pdf
The following slide illustrates usage of behavioral analytics for multiple transactions and profiles. It provides information about transaction, collaborative, behavior sorted, user defined, global intelligent, merchant, risk sensitivity, false positives, financial crimes, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Using Behavioral Analytics For Multiple Mitigating Corporate Scams And Robberies Themes Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cyber Phishing Scams And Attacks Ppt PowerPoint Presentation Complete With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this cyber phishing scams and attacks ppt powerpoint presentation complete with slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the fourteen slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Communication Plan For Strengthening Finance Mitigating Corporate Scams And Robberies Template Pdf
This slide showcases communication plan for strengthening finance and compliance teams. It provides information about money laundering, data intelligence, vulnerabilities, loopholes, customer education, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give PRODUCT NAME a try. Our experts have put a lot of knowledge and effort into creating this impeccable Communication Plan For Strengthening Finance Mitigating Corporate Scams And Robberies Template Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Customer Onboarding Framework Through Kyc Mitigating Corporate Scams And Robberies Structure Pdf
This slide showcases customer onboarding framework through know your customer KYC approach. It provides information about assess, implement, validation, testing, monitoring, control, risk rating, risk score, enhanced due diligence EDD, etc. Present like a pro with Customer Onboarding Framework Through Kyc Mitigating Corporate Scams And Robberies Structure Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Dashboard For Monitoring Fraud And Money Mitigating Corporate Scams And Robberies Background Pdf
This slide showcases dashboard for monitoring fraudulent and money laundering transactions. It provides information about legitimacy, total transaction, unusual transactions, bank, client, investigation, in peer review, etc. Slidegeeks is here to make your presentations a breeze with Dashboard For Monitoring Fraud And Money Mitigating Corporate Scams And Robberies Background Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
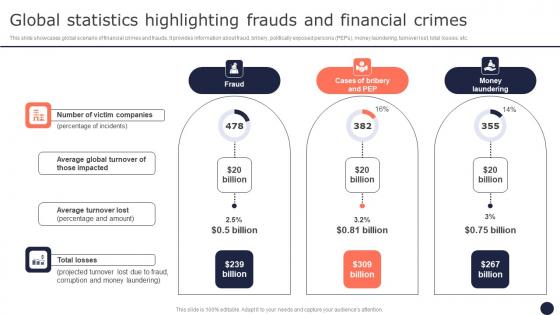
Global Statistics Highlighting Frauds And Financial Mitigating Corporate Scams And Robberies Clipart Pdf
This slide showcases global scenario of financial crimes and frauds. It provides information about fraud, bribery, politically exposed persons PEPs, money laundering, turnover lost, total losses, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Global Statistics Highlighting Frauds And Financial Mitigating Corporate Scams And Robberies Clipart Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
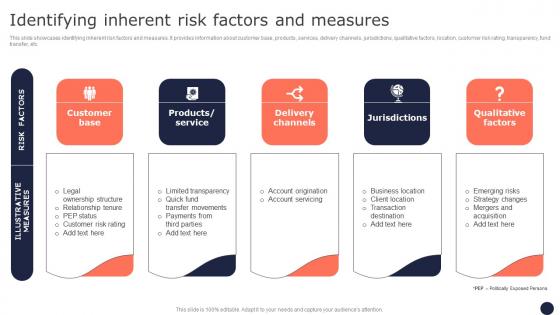
Identifying Inherent Risk Factors And Measures Mitigating Corporate Scams And Robberies Summary Pdf
This slide showcases identifying inherent risk factors and measures. It provides information about customer base, products, services, delivery channels, jurisdictions, qualitative factors, location, customer risk rating, transparency, fund transfer, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Identifying Inherent Risk Factors And Measures Mitigating Corporate Scams And Robberies Summary Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
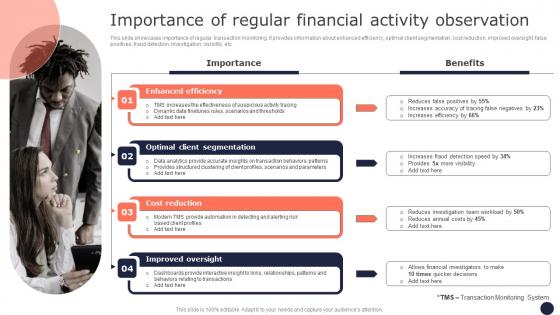
Importance Of Regular Financial Activity Mitigating Corporate Scams And Robberies Information Pdf
This slide showcases importance of regular transaction monitoring. It provides information about enhanced efficiency, optimal client segmentation, cost reduction, improved oversight, false positives, fraud detection, investigation, visibility, etc. This modern and well-arranged Importance Of Regular Financial Activity Mitigating Corporate Scams And Robberies Information Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Key Trends Of Transaction Monitoring Across Us Mitigating Corporate Scams And Robberies Pictures Pdf
This slide showcases transaction monitoring landscape of united states US. It provides information about transaction volume, suspicious activity report SAR, transaction patterns, structuring, funds circulation, scenarios, cash usage, etc. Welcome to our selection of the Key Trends Of Transaction Monitoring Across Us Mitigating Corporate Scams And Robberies Pictures Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
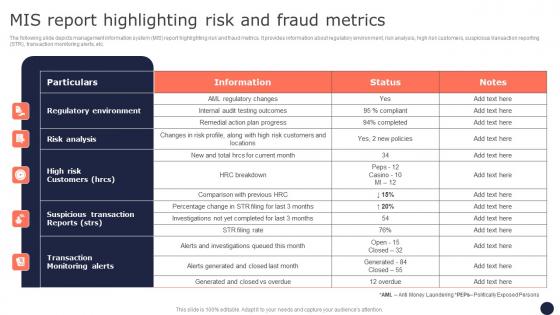
Mis Report Highlighting Risk And Fraud Metrics Mitigating Corporate Scams And Robberies Portrait Pdf
The following slide depicts management information system MIS report highlighting risk and fraud metrics. It provides information about regulatory environment, risk analysis, high risk customers, suspicious transaction reporting STR, transaction monitoring alerts, etc. The Mis Report Highlighting Risk And Fraud Metrics Mitigating Corporate Scams And Robberies Portrait Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
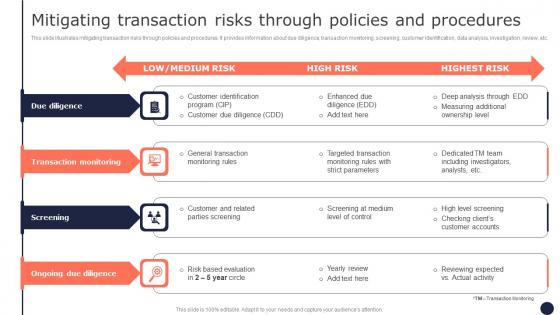
Mitigating Transaction Risks Through Policies Mitigating Corporate Scams And Robberies Guidelines Pdf
This slide illustrates mitigating transaction risks through policies and procedures. It provides information about due diligence, transaction monitoring, screening, customer identification, data analysis, investigation, review, etc. Retrieve professionally designed Mitigating Transaction Risks Through Policies Mitigating Corporate Scams And Robberies Guidelines Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
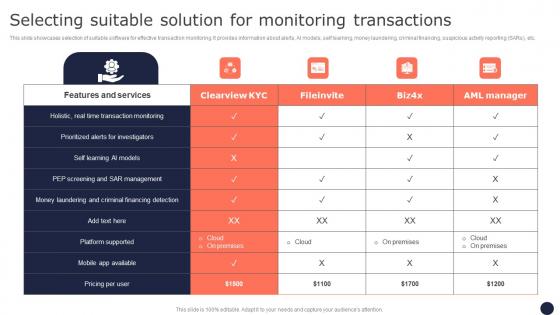
Selecting Suitable Solution For Monitoring Mitigating Corporate Scams And Robberies Guidelines Pdf
This slide showcases selection of suitable software for effective transaction monitoring. It provides information about alerts, AI models, self learning, money laundering, criminal financing, suspicious activity reporting SARs, etc. Do you know about Slidesgeeks Selecting Suitable Solution For Monitoring Mitigating Corporate Scams And Robberies Guidelines Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Transaction Monitoring And AML Training Plan Mitigating Corporate Scams And Robberies Clipart Pdf
The following slide represents training program for transaction monitoring and anti money laundering AML. It provides information about certification, assessment, compatibility, surveillance, operational efficiency, escalation, unusual transactions, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give PRODUCT NAME a try. Our experts have put a lot of knowledge and effort into creating this impeccable Transaction Monitoring And AML Training Plan Mitigating Corporate Scams And Robberies Clipart Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Real World Examples Of Watering Hole Attacks Man In The Middle Phishing IT
This slide describes the real-world examples of watering hole phishing scams. These include Facebook, Twitter, Microsoft, and Apple scam, LuckyMouse scam, International Civil Aviation OrganizationICAO scam, Ccleaner scam and Holy Water scam. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Real World Examples Of Watering Hole Attacks Man In The Middle Phishing IT can be your best option for delivering a presentation. Represent everything in detail using Real World Examples Of Watering Hole Attacks Man In The Middle Phishing IT and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Different Types Of Vishing Cyber Attacks Man In The Middle Phishing IT
This slide talks about the various types of vishing cyber attacks. The purpose of this slide is to briefly explain different techniques of vishing scams used by the attackers to scam users. These are caller ID spoofing, dumpster diving, wardialing, etc. This modern and well-arranged Different Types Of Vishing Cyber Attacks Man In The Middle Phishing IT provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Monitoring Financial Transactions Software Market Highlights Topics PDF
This slide depicts highlights of transaction monitoring software market. It provides information about application market, sector wise market, continent, anti money laundering, manufacturing, scam detection, etc.Showcasing this set of slides titled Monitoring Financial Transactions Software Market Highlights Topics PDF. The topics addressed in these templates are Market Continent, Asia Pacific, Market Sector. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
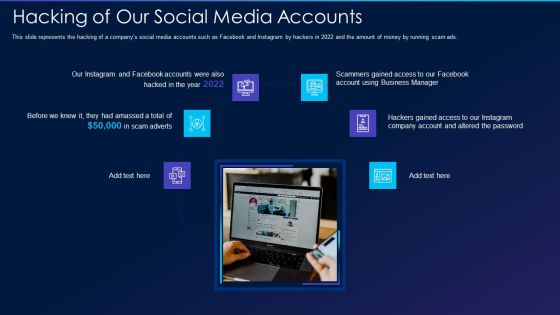
Cyber Exploitation IT Hacking Of Our Social Media Accounts Template PDF
This slide represents the hacking of a companys social media accounts such as Facebook and Instagram by hackers in 2022 and the amount of money by running scam ads. This is a cyber exploitation it hacking of our social media accounts template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like hacking of our social media accounts. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Hacking Of Our Social Media Accounts Formats PDF
This slide represents the hacking of a companys social media accounts such as Facebook and Instagram by hackers in 2019 and the amount of money by running scam ads.Presenting IT Security Hacker Hacking Of Our Social Media Accounts Formats PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Scammers Gained, Business Manager, Altered The Password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Comparative Analysis Of Tokenization Strategies For Data Security PPT Template
This slide highlights the differences between security and utility tokens. The purpose of this slide is to compare security and utility tokens on various aspects such as purpose, expectations, scam potential, etc. Find a pre-designed and impeccable Comparative Analysis Of Tokenization Strategies For Data Security PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
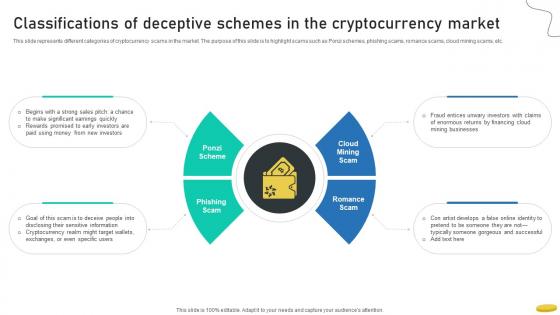
Classifications Of Deceptive Schemes In The Cryptocurrency Management With Blockchain
This slide represents different categories of cryptocurrency scams in the market. The purpose of this slide is to highlight scams such as Ponzi schemes, phishing scams, romance scams, cloud mining scams, etc.Find highly impressive Classifications Of Deceptive Schemes In The Cryptocurrency Management With Blockchain on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Classifications Of Deceptive Schemes In The Cryptocurrency Management With Blockchain for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
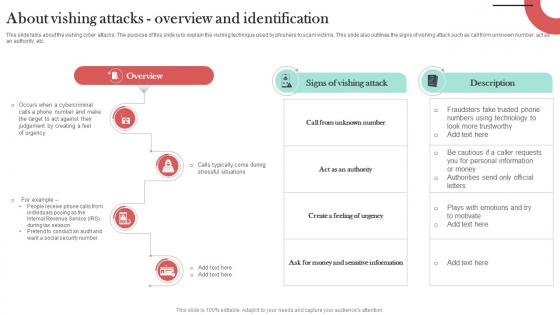
About Vishing Attacks Overview And Identification Man In The Middle Phishing IT
This slide talks about the vishing cyber attacks. The purpose of this slide is to explain the vishing technique used by phishers to scam victims. This slide also outlines the signs of vishing attack such as call from unknown number, act as an authority, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. About Vishing Attacks Overview And Identification Man In The Middle Phishing IT can be your best option for delivering a presentation. Represent everything in detail using About Vishing Attacks Overview And Identification Man In The Middle Phishing IT and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Real World Examples Of Smishing Attacks Man In The Middle Phishing IT
This slide demonstrates the real-world example of smishing cyber attacks which targeted different individuals and organizations. The popular scams are early access apple iPhone 12 scam, USPS and FedEx scams and mandatory online COVID-19 test scam. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Real World Examples Of Smishing Attacks Man In The Middle Phishing IT. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Real World Examples Of Smishing Attacks Man In The Middle Phishing IT today and make your presentation stand out from the rest
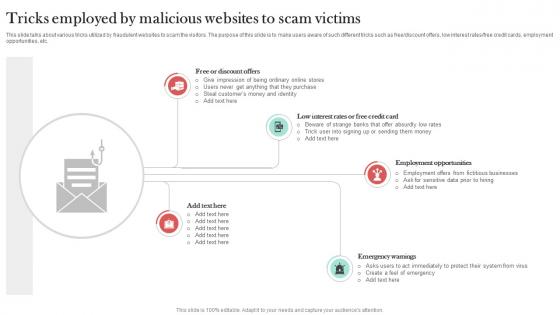
Tricks Employed By Malicious Websites Man In The Middle Phishing IT
This slide talks about various tricks utilized by fraudulent websites to scam the visitors. The purpose of this slide is to make users aware of such different tricks such as free discount offers, low interest rates free credit cards, employment opportunities, etc. Explore a selection of the finest Tricks Employed By Malicious Websites Man In The Middle Phishing IT here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Tricks Employed By Malicious Websites Man In The Middle Phishing IT to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template
This slide highlights the differences between security and utility tokens. The purpose of this slide is to compare security and utility tokens on various aspects such as purpose, expectations, scam potential, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template can be your best option for delivering a presentation. Represent everything in detail using Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Global Cyber Terrorism Incidents On The Rise IT Phishing Techniques Misused For Cyber Assault Ideas PDF
This slide represents phishing techniques used for cyber assaults or cyber terrorism, such as email phishing scams and whaling. Presenting global cyber terrorism incidents on the rise it phishing techniques misused for cyber assault ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like spear phishing, smishing and vishing, whaling, email phishing scams. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Major Cryptocurrency Blockchain Comprehensive Guide To Blockchain Digital Security Download Pdf
The following slide showcases major cryptocurrency and blockchain cybersecurity scams throughout the globe. It includes elements such as Decentralized autonomous organization DAO attack, gox attack, plus token scams, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Major Cryptocurrency Blockchain Comprehensive Guide To Blockchain Digital Security Download Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

About Pharming Phishing Identification Man In The Middle Phishing IT
This slide talks about the pharming phishing cyber scams. The purpose of this slide is to illustrate the ways of recognizing pharming scams such as URL, design and HTTP vs HTTPS. This slide also illustrates the architecture of pharming phishing attack. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give About Pharming Phishing Identification Man In The Middle Phishing IT a try. Our experts have put a lot of knowledge and effort into creating this impeccable About Pharming Phishing Identification Man In The Middle Phishing IT. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
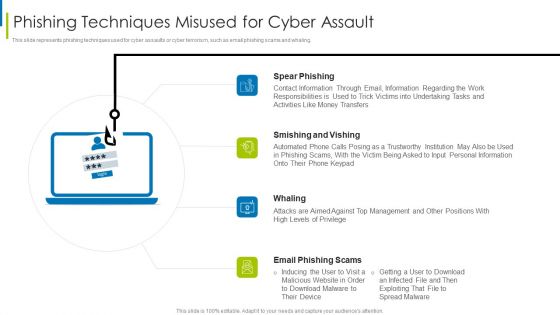
Cyber Terrorism Assault Phishing Techniques Misused For Cyber Assault Slides PDF
This slide represents phishing techniques used for cyber assaults or cyber terrorism, such as email phishing scams and whaling. This is a cyber terrorism assault phishing techniques misused for cyber assault slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like smishing and vishing, spear phishing, contact information through You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
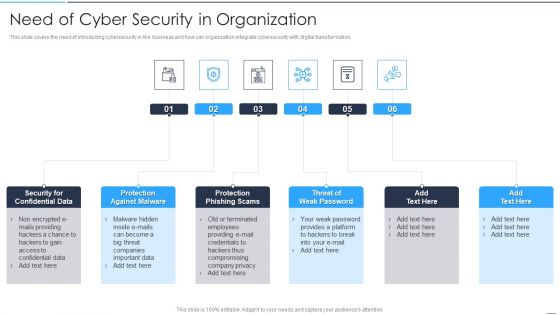
Accelerate Online Journey Now Need Of Cyber Security In Organization Professional PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation.Presenting Accelerate Online Journey Now Need Of Cyber Security In Organization Professional PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Confidential Data, Against Malware, Phishing Scams In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Strategies To Prevent Bankruptcy And Monitor Credit Formats PDF
This slide showcases crucial strategies to overcome bankruptcy . It includes making sure correct credit filing , monitoring credit regularly , avoiding high interest products , avoiding credit repair scams , getting errors removed from credit report etc. Persuade your audience using this Key Strategies To Prevent Bankruptcy And Monitor Credit Formats PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information, Key Strategies, Prevent Bankruptcy Monitor Credit. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Identity Fraud Reports And Losses By Contact Method Elements PDF
This slide showcases common means through which criminals engage fraudulent activities. This template focuses on reducing number of scamming taking place across different mediums. It includes information related to phone calls, emails, websites, etc. Showcasing this set of slides titled Identity Fraud Reports And Losses By Contact Method Elements PDF. The topics addressed in these templates are Contact Method, Phone Call, Social Media. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Approaches To Protect Comprehensive Guide To Blockchain Digital Security Brochure Pdf
The following slide illustrates some methods to protect blockchain network users from honeypot scams and implement defensive actions. It includes elements such as no dead coins, audits, check social media, scrutinize website, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Key Approaches To Protect Comprehensive Guide To Blockchain Digital Security Brochure Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

How Does A Phishing Attack Work Man In The Middle Phishing IT
This slide demonstrates the working flow of a phishing attack. The purpose of this slide is to outline the various phases of phishing scams such as campaign crafted, payloads, impersonation, execution, ransomware and encrypts on target. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download How Does A Phishing Attack Work Man In The Middle Phishing IT from Slidegeeks and deliver a wonderful presentation.

Overview And Key Levels Comprehensive Guide To Blockchain Digital Security Diagrams Pdf
The following slide illustrates brief introduction of honeypot scams to determine malicious activities and mitigate risks. It includes elements such as etheruem virtual machine, solidity compiler, etherscan blockchain explorer, etc. Welcome to our selection of the Overview And Key Levels Comprehensive Guide To Blockchain Digital Security Diagrams Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today
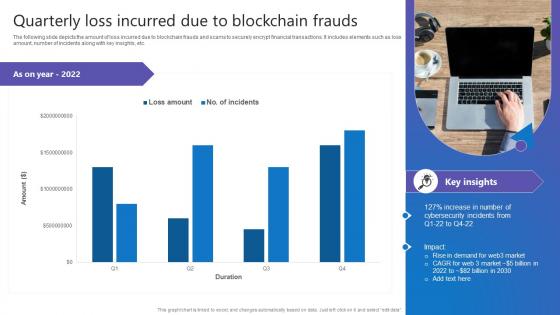
Quarterly Loss Incurred Due Comprehensive Guide To Blockchain Digital Security Themes Pdf
The following slide depicts the amount of loss incurred due to blockchain frauds and scams to securely encrypt financial transactions. It includes elements such as loss amount, number of incidents along with key insights, etc. This Quarterly Loss Incurred Due Comprehensive Guide To Blockchain Digital Security Themes Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
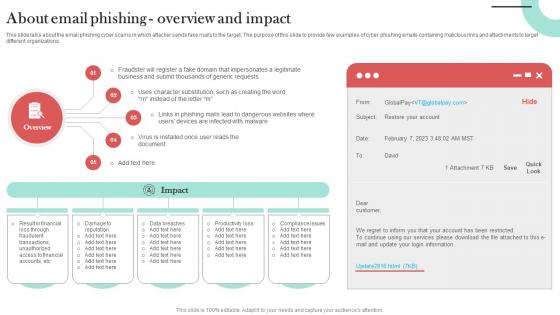
About Email Phishing Overview And Impact Man In The Middle Phishing IT
This slide talks about the email phishing cyber scams in which attacker sends fake mails to the target. The purpose of this slide to provide few examples of cyber phishing emails containing malicious links and attachments to target different organizations. Create an editable About Email Phishing Overview And Impact Man In The Middle Phishing IT that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. About Email Phishing Overview And Impact Man In The Middle Phishing IT is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
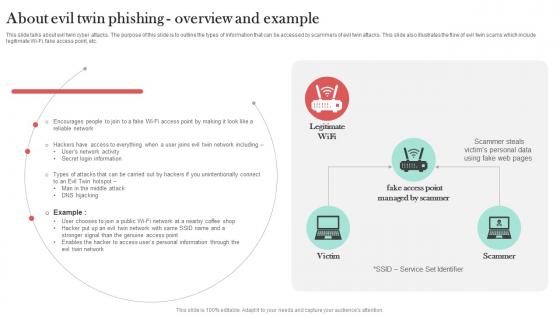
About Evil Twin Phishing Overview And Example Man In The Middle Phishing IT
This slide talks about evil twin cyber attacks. The purpose of this slide is to outline the types of information that can be accessed by scammers of evil twin attacks. This slide also illustrates the flow of evil twin scams which include legitimate Wi-Fi, fake access point, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate About Evil Twin Phishing Overview And Example Man In The Middle Phishing IT for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Introduction To Watering Hole Phishing Man In The Middle Phishing IT
This slide talks about the watering hole phishing attacks which trick the victim to do activities compromising their personal data. The purpose of this slide is to describe the idea behind the working of watering hole scams which can target a group of individuals. Take your projects to the next level with our ultimate collection of Introduction To Watering Hole Phishing Man In The Middle Phishing IT. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Working Process Of Cyber Phishing Attacks Man In The Middle Phishing IT
This slide talks about the implementation and working of phishing attacks. The purpose of this slide is to explain how are cyber phishing scams conducted. The components include hacker, phishing mail, target, phishing website and original website. Do you know about Slidesgeeks Working Process Of Cyber Phishing Attacks Man In The Middle Phishing IT These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Internal Adulteration Restaurant Fraud With Prevention Strategy Topics Pdf
This slide showcase frauds that is happening internally in food restaurant with mitigation plan. It includes elements such as auto-gratuity scams, undercharging scams, time theft and food theft Pitch your topic with ease and precision using this Internal Adulteration Restaurant Fraud With Prevention Strategy Topics Pdf. This layout presents information on Description, Mitigation Plan, Frauds. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
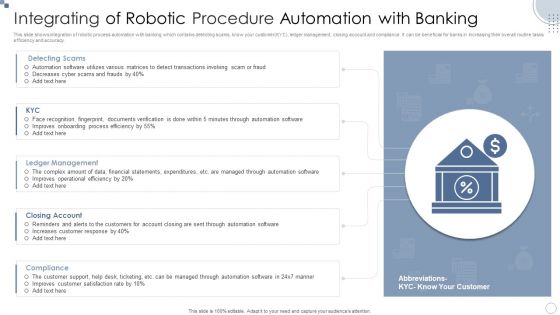
Integrating Of Robotic Procedure Automation With Banking Ppt PowerPoint Presentation Inspiration Samples PDF
This slide shows integration of robotic process automation with banking which contains detecting scams, know your customer KYC, ledger management, closing account and compliance. It can be beneficial for banks in increasing their overall routine tasks efficiency and accuracy.Showcasing this set of slides titled Integrating Of Robotic Procedure Automation With Banking Ppt PowerPoint Presentation Inspiration Samples PDF. The topics addressed in these templates are Automation Software, Detecting Scams, Ledger Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Addressing The Practices To Protect Business Against Fraud Fraud Threat Administration Guide Sample PDF
Purpose of this slide is to portray the existing ways of protecting business from fraud events such as WIFI hacking, business email compromise scams, and ransomware.This is a Addressing The Practices To Protect Business Against Fraud Fraud Threat Administration Guide Sample PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Compromise Scams, Ransomware, Confidential Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

 Home
Home