Safety

What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf
This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into What Are Benefits Of Using Cloud Data Security Using Cryptography Sample Pdf
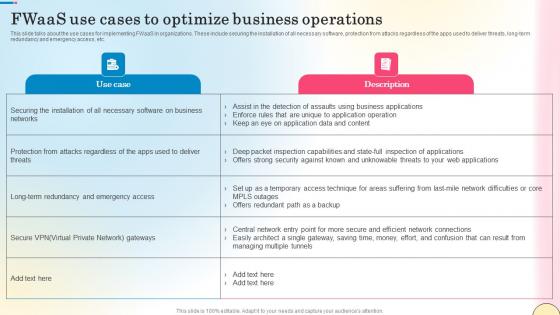
Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf
This slide talks about the use cases for implementing FWaaS in organizations. These include securing the installation of all necessary software, protection from attacks regardless of the apps used to deliver threats, long-term redundancy and emergency access, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Fwaas Use Cases To Optimize Business Operations Network Security Summary Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Client Testimonials Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf
This slide showcases customer testimonials of customer which are using open source platform for virtual assistance application which is offered by business. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Client Testimonials Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Client Testimonials Voice Assistance Security Platform Investor Funding Presentation Pictures Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
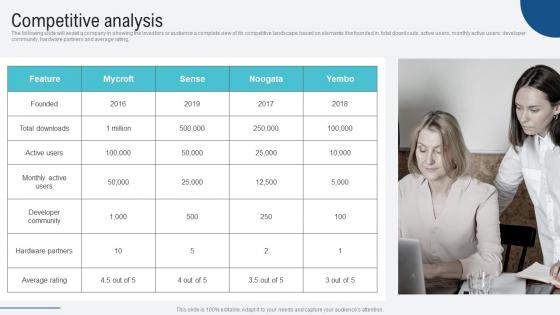
Competitive Analysis Voice Assistance Security Platform Investor Funding Presentation Themes Pdf
The following slide will assist a company in showing the investors or audience a complete view of its competitive landscape based on elements like founded in, total downloads, active users, monthly active users, developer community, hardware partners and average rating. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Competitive Analysis Voice Assistance Security Platform Investor Funding Presentation Themes Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Competitive Analysis Voice Assistance Security Platform Investor Funding Presentation Themes Pdf
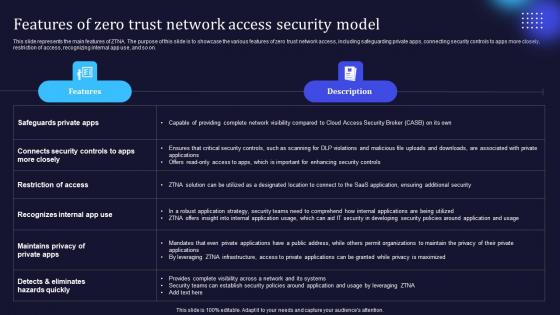
Zero Trust Model Features Of Zero Trust Network Access Security Model
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. This modern and well-arranged Zero Trust Model Features Of Zero Trust Network Access Security Model provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Steps To Integrate Secure Web Gateway Into Organization Web Threat Protection System
This slide demonstrates the steps for successful implementation of SWG into firms. The purpose of this slide is to outline the procedure of Secure Web integration. The steps included are determine use case, select best solution, plan deployment, etc. Present like a pro with Steps To Integrate Secure Web Gateway Into Organization Web Threat Protection System. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
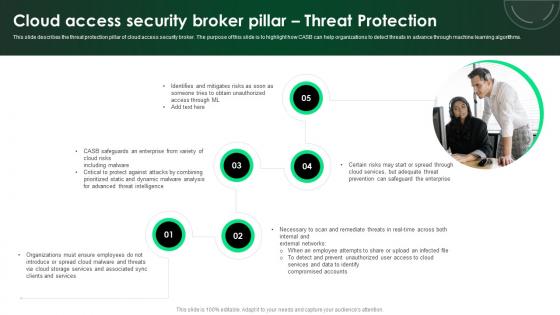
CASB 2 0 IT Cloud Access Security Broker Pillar Threat Protection
This slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Retrieve professionally designed CASB 2 0 IT Cloud Access Security Broker Pillar Threat Protection to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
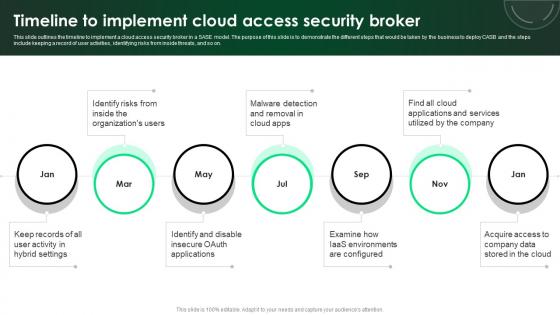
CASB 2 0 IT Timeline To Implement Cloud Access Security Broker
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable CASB 2 0 IT Timeline To Implement Cloud Access Security Broker. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Secure Method For Storing Private Keys Offline In Paper Cryptocurrency Management With Blockchain
This slide highlights the overview of paper wallets in the crypto world. The purpose of this slide is to outline some basic features of a paper wallet such as present in a physical medium, having to download the code for transactions, have a unique identifiers, etc.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Secure Method For Storing Private Keys Offline In Paper Cryptocurrency Management With Blockchain can be your best option for delivering a presentation. Represent everything in detail using Secure Method For Storing Private Keys Offline In Paper Cryptocurrency Management With Blockchain and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Mastering Blockchain Wallets Mobile Wallets Key Security Issues And Solutions BCT SS V
This slide covers security concerns linked with mobile wallets and potential solutions to mitigate the risks. The purpose of this template is provide an overview on challenges associated such as lost or stolen devices, phishing scams, weak passwords along with risk involved with solutions to prevent risks and reduce its impact. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mastering Blockchain Wallets Mobile Wallets Key Security Issues And Solutions BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
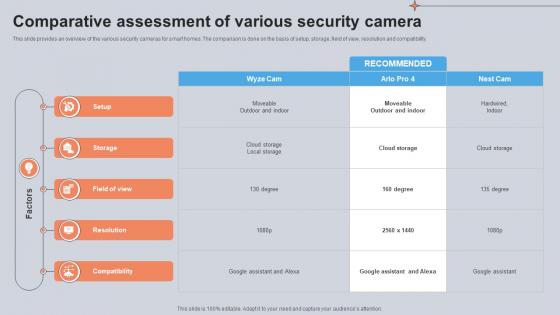
Comparative Assessment Of Various Security Camera Utilizing Smart Appliances IoT SS V
This slide provides an overview of the various security cameras for smart homes. The comparison is done on the basis of setup, storage, field of view, resolution and compatibility. Present like a pro with Comparative Assessment Of Various Security Camera Utilizing Smart Appliances IoT SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
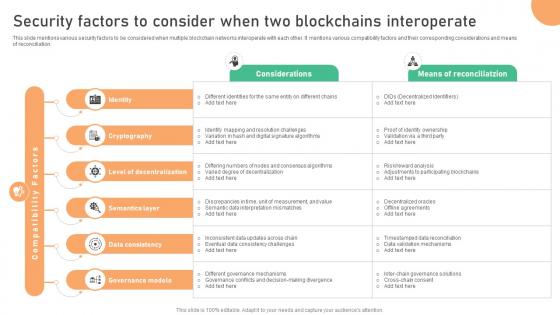
Seamless Integration The Power Security Factors To Consider When Two Blockchains BCT SS V
This slide mentions various security factors to be considered when multiple blockchain networks interoperate with each other. It mentions various compatibility factors and their corresponding considerations and means of reconciliation. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Seamless Integration The Power Security Factors To Consider When Two Blockchains BCT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
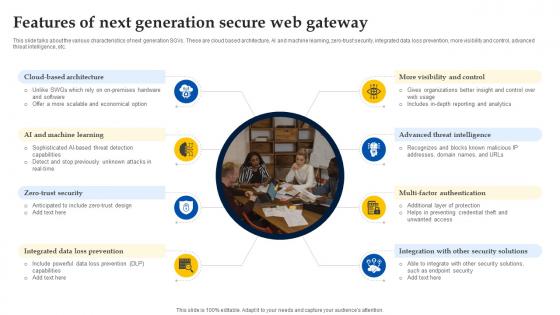
Web Access Control Solution Features Of Next Generation Secure Web Gateway
This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Web Access Control Solution Features Of Next Generation Secure Web Gateway to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Web Access Control Solution Secure Web Gateway Set Up Planning And Preparation
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the planning and preparation phase of SWG set-up. The key points included are define scope of project, identify network architecture, etc. Present like a pro with Web Access Control Solution Secure Web Gateway Set Up Planning And Preparation. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
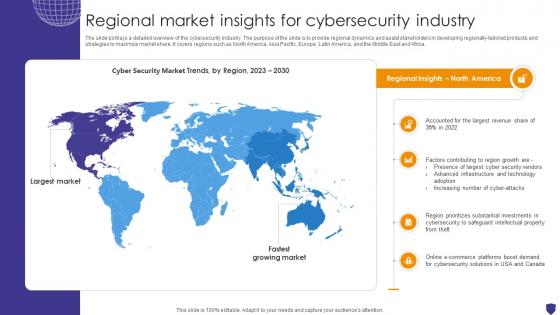
Global Data Security Industry Report Regional Market Insights For Cybersecurity Industry IR SS V
The slide portrays a detailed overview of the cybersecurity industry. The purpose of the slide is to provide regional dynamics and assist stakeholders in developing regionally-tailored products and strategies to maximize market share. It covers regions such as North America, Asia Pacific, Europe, Latin America, and the Middle East and Africa. Explore a selection of the finest Global Data Security Industry Report Regional Market Insights For Cybersecurity Industry IR SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Global Data Security Industry Report Regional Market Insights For Cybersecurity Industry IR SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Global Data Security Industry Report Risk Evaluation Within Cybersecurity Industry IR SS V
The slide depicts risk assessment for the cybersecurity industry. It aims to educate the audience on the need of successfully recognizing and managing risks to maintain the stability. It covers potential hazards associated with data beaches, phishing attacks, malware, regulatory compliance, and IoT security issues. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Global Data Security Industry Report Risk Evaluation Within Cybersecurity Industry IR SS V from Slidegeeks and deliver a wonderful presentation.
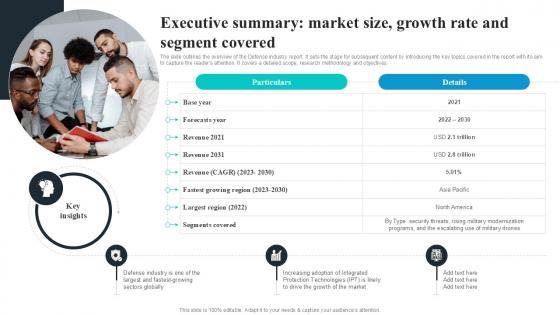
Executive Summary Market Size Growth Rate Global Security Industry PPT Presentation IR SS V
The slide outlines the overview of the Defense industry report. It sets the stage for subsequent content by introducing the key topics covered in the report with its aim to capture the readers attention. It covers a detailed scope, research methodology and objectives. Find highly impressive Executive Summary Market Size Growth Rate Global Security Industry PPT Presentation IR SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Executive Summary Market Size Growth Rate Global Security Industry PPT Presentation IR SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V
The slide highlights industry laws and regulations in Defense industry. It is to ensure market stability, consumer protection and foster innovation while mitigating risks. It includes regulatory compliance and intellectual property, legal and regulatory. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Industry Laws And Regulations In Global Security Industry PPT Slide IR SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Different Phases Of Implementing Tokenization In Ds Securing Your Data Ppt Presentation
This slide highlights the steps for working of tokenization. The purpose of this slide is to outline the various ways of creating token and the phases which include initiating card transaction, producing tokens, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Different Phases Of Implementing Tokenization In Ds Securing Your Data Ppt Presentation template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Different Phases Of Implementing Tokenization In Ds Securing Your Data Ppt Presentation that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Training Schedule For It Teams To Conduct Tokenization Securing Your Data Ppt Presentation
This slide represents the training schedule for IT teams in an organization to efficiently carry out tokenization. It includes the time slots for training, total days of training, and the modules to be covered in the training. If you are looking for a format to display your unique thoughts, then the professionally designed Training Schedule For It Teams To Conduct Tokenization Securing Your Data Ppt Presentation is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Training Schedule For It Teams To Conduct Tokenization Securing Your Data Ppt Presentation and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

About Cloud Cryptography Overview And Features Data Security In Cloud Computing Ppt Powerpoint
This slide talks about the cloud cryptography which helps in securing information travelling through cloud network. The purpose of this slide is to briefly explain the concept of cloud cryptography. This slide also outlines the features of this technology. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate About Cloud Cryptography Overview And Features Data Security In Cloud Computing Ppt Powerpoint for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Training Program For Cryptographic Data Security In Cloud Computing Ppt Powerpoint
This slide describes the training program for employees to implement cloud cryptography in an organization. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Training Program For Cryptographic Data Security In Cloud Computing Ppt Powerpoint can be your best option for delivering a presentation. Represent everything in detail using Training Program For Cryptographic Data Security In Cloud Computing Ppt Powerpoint and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
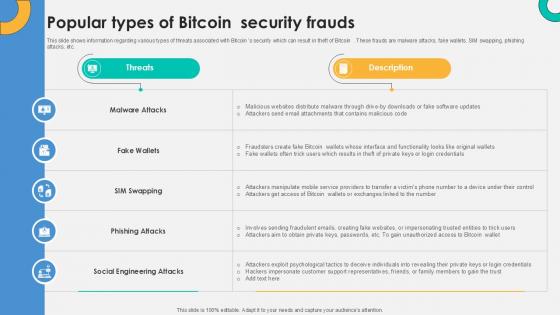
Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V
This slide shows information regarding various types of threats associated with Bitcoin s security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Popular Types Of Bitcoin Security Everything About Bitcoin PPT Slide Fin SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

What Is The Cyber Security Role Web Designing User Engagement Rules PDF
Boost your pitch with our creative What Is The Cyber Security Role Web Designing User Engagement Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
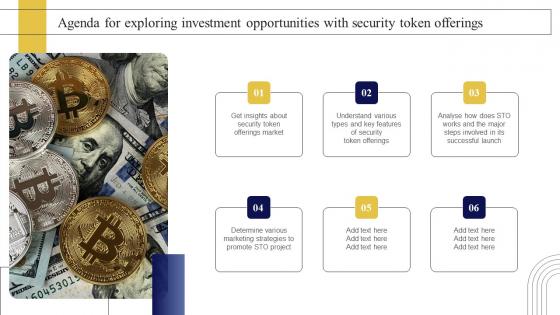
Agenda For Exploring Investment Opportunities With Security Token Offerings Designs Pdf
Boost your pitch with our creative Agenda For Exploring Investment Opportunities With Security Token Offerings Designs Pdf. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Exploring Investment Opportunities With Security Token Table Of Contents Infographics Pdf
The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Exploring Investment Opportunities With Security Token Table Of Contents Infographics Pdf from Slidegeeks and deliver a wonderful presentation.

Table Of Contents Of Tokenization For Improved Data Security PPT Sample
Boost your pitch with our creative Table Of Contents Of Tokenization For Improved Data Security PPT Sample. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cybersecurity Best Practices For Cloud Security Ppt Ideas Images PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting cybersecurity best practices for cloud security ppt ideas images pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like measures, security, planning, network, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Need For Cyber Security Awareness Training Professional PDF
The purpose of this slide is to highlight the importance of conducting cyber security awareness training. It provides information about the prevention from cyber attack and data breach, build a culture of cyber security, to robust technological defenses etc. Presenting Need For Cyber Security Awareness Training Professional PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Organization Different, Technological Defenses, Awareness Organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda For Comprehensive Guide To Blockchain Digital Security Risk Management Structure Pdf
Slidegeeks has constructed Agenda For Comprehensive Guide To Blockchain Digital Security Risk Management Structure Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Zero Trust Network Security Ppt PowerPoint Presentation Complete Deck With Slides
Use this Zero Trust Network Security Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in eighty nine slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Training Program For Zero Trust Network Access Model Security Inspiration Pdf
This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. Find a pre-designed and impeccable Training Program For Zero Trust Network Access Model Security Inspiration Pdf. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
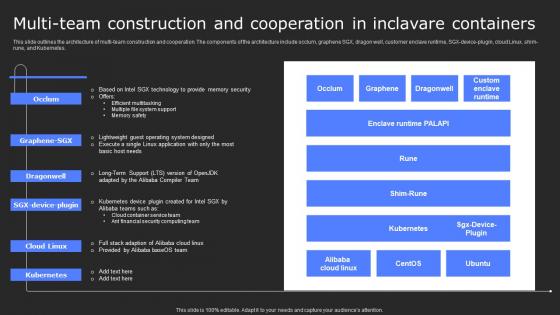
Multi Team Construction And Cooperation In Secure Computing Framework Background Pdf
This slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Multi Team Construction And Cooperation In Secure Computing Framework Background Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cloud Data Security Using Cryptography Ppt Powerpoint Presentation Complete Deck With Slides
This incisive,comprehensive Cloud Data Security Using Cryptography Ppt Powerpoint Presentation Complete Deck With Slides details important features of running a business. One learns about things like result areas,planning and strategic framework just a glance of this comprehensive deck of eighty five slides. Use this PPT template to present your unique perspective of business technicalities and experience the way a good presentation can give new meaning to similarly placed facts. Use this template to leave a roomful of people wondering at the expert you have gathered in closing a business deal. The completely editable and customisable nature of the presentation is a unique bonus. Download now.

Monitoring Digital Assets To Enhance Cyber Security Ppt Powerpoint Presentation Complete Deck
Take advantage of this well-researched and professionally-designed Monitoring Digital Assets To Enhance Cyber Security Ppt Powerpoint Presentation Complete Deck to ace your next business meeting. Use this PPT complete deck to impress the management with your ideas for business growth and revenue increase. Use the twenty one-slide Template Bundle to leave no stone unturned as you present each step of your process. Employ the visual tools within the slides such as graphs, charts, and tables to ensure that the audience can never look away from the presentation. With attractive visuals, easy to understand structure, and your knowledge, your presentation will have the attention it deserves. Download this PPT Template from the link below.

Company Introduction Voice Assistance Security Platform Investor Funding Presentation Professional Pdf
This slide represents the overview of Mycroft company which offers open source voice assistant and can be used in any field. It showcases industry, customer, headquarters, founded year, founders and legal name. Make sure to capture your audiences attention in your business displays with our gratis customizable Company Introduction Voice Assistance Security Platform Investor Funding Presentation Professional Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Funding History Voice Assistance Security Platform Investor Funding Presentation Portrait Pdf
This slide showcases timeframe of funding rounds of business along with date, funding type, number of investors, amount raised and personnel name through whom funding is lead by. The Funding History Voice Assistance Security Platform Investor Funding Presentation Portrait Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Why Invest With Us Voice Assistance Security Platform Investor Funding Presentation Icons Pdf
This purpose of the following slide is to convince investors to invest in business by highlighting business growth potential and benefits they will get by making investment. Want to ace your presentation in front of a live audience Our Why Invest With Us Voice Assistance Security Platform Investor Funding Presentation Icons Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
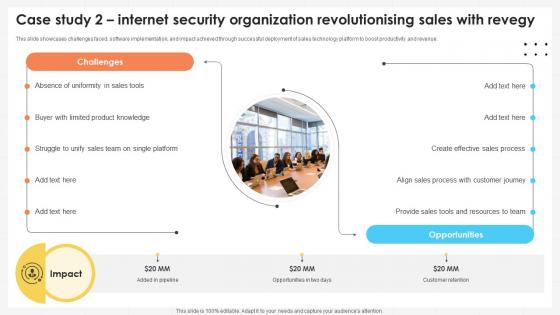
Business Development Team Case Study 2 Internet Security Organization SA SS V
This slide showcases challenges faced, software implementation, and impact achieved through successful deployment of sales technology platform to boost productivity and revenue. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Business Development Team Case Study 2 Internet Security Organization SA SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
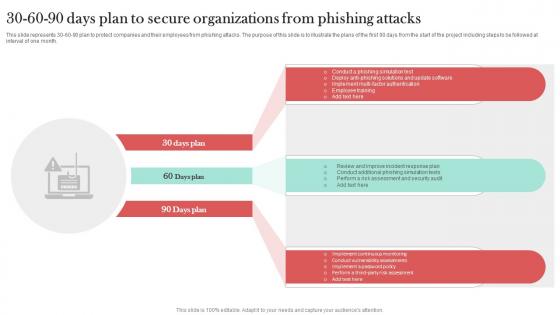
30 60 90 Days Plan To Secure Organizations Man In The Middle Phishing IT
This slide represents 30-60-90 plan to protect companies and their employees from phishing attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Secure Organizations Man In The Middle Phishing IT. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Ethical And Data Security Considerations For Digital Innovation DT SS V
This slide presents important ethical and legal considerations in the digital landscape. It mentions description, laws necessary for maintaining regulations including data privacy, cybersecurity and intellectual property.Find a pre-designed and impeccable Ethical And Data Security Considerations For Digital Innovation DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Table Of Contents Global Data Security Industry Report IR SS V
Slidegeeks has constructed Table Of Contents Global Data Security Industry Report IR SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Competitive Dynamics And Developments Global Security Industry PPT Template IR SS V
The slide represents a detailed overview of competitive landscape. The purpose of this slide is to help stakeholders in understanding the competitive environment and aids in making informed strategic decision. The key players list include major Defense companies. There are so many reasons you need a Competitive Dynamics And Developments Global Security Industry PPT Template IR SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

30 60 90 Days Plan To Implement Tokenization Securing Your Data Ppt Example
This slide depicts the 30 60 90 days plan for implementing tokenization. The plan includes the activities and goals such as assessment, planning, selecting tokenization solutions, etc. Find a pre-designed and impeccable 30 60 90 Days Plan To Implement Tokenization Securing Your Data Ppt Example The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Tokenization Case Study Comforte Fashion Retailer Securing Your Data Ppt Example
This slide represents the tokenization case study at comforte fashion retailer. The purpose of this slide is to give an overview of the retailer, including the challenges they face and the solutions provided by tokenization. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Tokenization Case Study Comforte Fashion Retailer Securing Your Data Ppt Example will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

What Are Benefits Of Using Data Security In Cloud Computing Ppt Template
This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit What Are Benefits Of Using Data Security In Cloud Computing Ppt Template and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
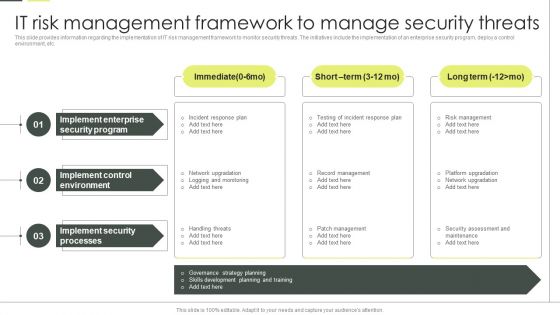
Building An IT Strategy Plan For Business Expansion IT Risk Management Framework To Manage Security Threats Background PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Building An IT Strategy Plan For Business Expansion IT Risk Management Framework To Manage Security Threats Background PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Building An IT Strategy Plan For Business Expansion IT Risk Management Framework To Manage Security Threats Background PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cloud Security Checklist Backup And Data Recovery Inspiration PDF
This slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them. This is a Cloud Security Checklist Backup And Data Recovery Inspiration PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Plan, Cloud Service, Location Of Data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
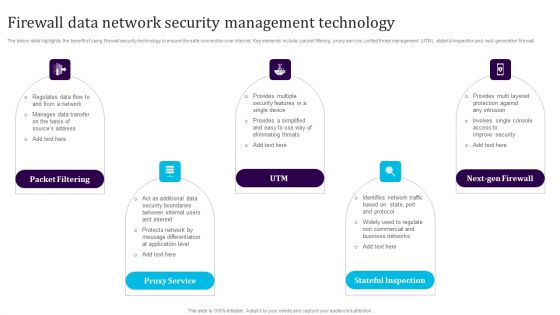
Firewall Data Network Security Management Technology Template PDF
The below slide highlights the benefit of using firewall security technology to ensure the safe connection over internet. Key elements include packet filtering, proxy service, unified threat management UTM, stateful inspection and next-generation firewall. Persuade your audience using this Firewall Data Network Security Management Technology Template PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Packet Filtering, Proxy Service, Utm, Next Gen Firewall, Stateful Inspection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
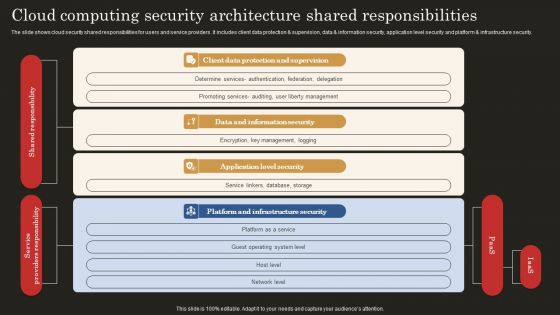
Cloud Computing Security Architecture Shared Responsibilities Brochure PDF
The slide shows cloud security shared responsibilities for users and service providers. It includes client data protection and supervision, data and information security, application level security and platform and infrastructure security. Showcasing this set of slides titled Cloud Computing Security Architecture Shared Responsibilities Brochure PDF. The topics addressed in these templates are Client Data Protection, Data Information Security, Application Level Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Secure Multi Party Computation SMPC Ppt Powerpoint Presentation Complete Deck With Slides
This Secure Multi Party Computation SMPC Ppt Powerpoint Presentation Complete Deck With Slides is meant for audiences who need a new vision and mission to bring energy back to their enterprise. The eighty three-slides in the complete deck complement the spirit of risk-taking and investment that the adventure of business requires. There is also scope for ample customization, which is a hallmark of a good presentation. Improvise on the presentations or even while you make your point before you esteemed audience. There is no better way to win new clients in business than a passionate presentation we have the raw material, what is stopping you from giving your best Download now and showcase your business potential to the world.
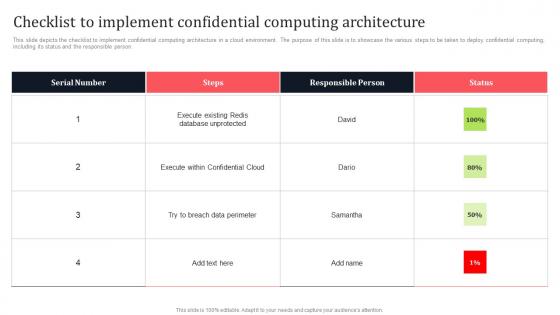
Checklist To Implement Confidential Computing Architecture Secure Multi Party Guidelines Pdf
This slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Checklist To Implement Confidential Computing Architecture Secure Multi Party Guidelines Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
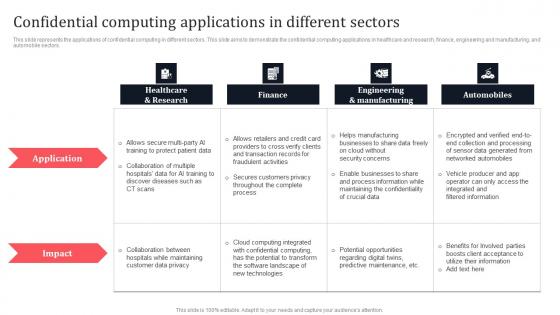
Confidential Computing Applications In Different Sectors Secure Multi Party Slides Pdf
This slide represents the applications of confidential computing in different sectors. This slide aims to demonstrate the confidential computing applications in healthcare and research, finance, engineering and manufacturing, and automobile sectors. Present like a pro with Confidential Computing Applications In Different Sectors Secure Multi Party Slides Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
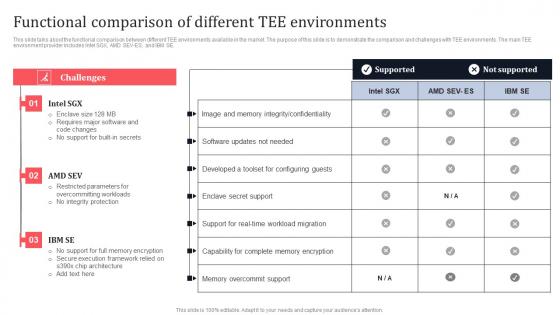
Functional Comparison Of Different Tee Environments Secure Multi Party Inspiration Pdf
This slide talks about the functional comparison between different TEE environments available in the market. The purpose of this slide is to demonstrate the comparison and challenges with TEE environments. The main TEE environment provider includes Intel SGX, AMD SEV-ES, and IBM SE. Retrieve professionally designed Functional Comparison Of Different Tee Environments Secure Multi Party Inspiration Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Best Practices For Website Security Management Step By Step Guide Ideas PDF
Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Best Practices For Website Security Management Step By Step Guide Ideas PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
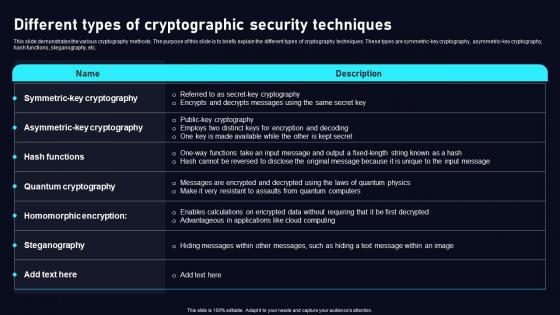
Different Types Of Cryptographic Cloud Data Security Using Cryptography Template Pdf
This slide demonstrates the various cryptography methods. The purpose of this slide is to briefly explain the different types of cryptography techniques. These types are symmetric key cryptography, asymmetric key cryptography, hash functions, steganography, etc. Slidegeeks has constructed Different Types Of Cryptographic Cloud Data Security Using Cryptography Template Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
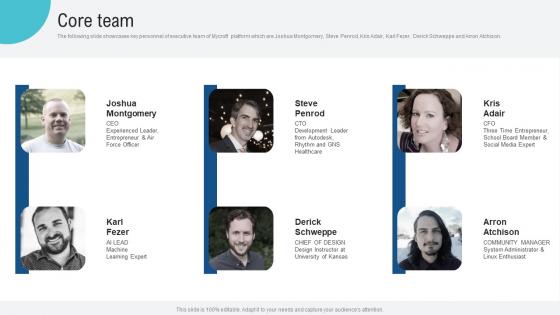
Core Team Voice Assistance Security Platform Investor Funding Presentation Mockup Pdf
The following slide showcases key personnel of executive team of Mycroft platform which are Joshua Montgomery, Steve Penrod, Kris Adair, Karl Fezer, Derick Schweppe and Arron Atchison. This modern and well arranged Core Team Voice Assistance Security Platform Investor Funding Presentation Mockup Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Key Facts Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf
The following slide showcases various factors that presents how company is becoming a leading in market. It highlights growth rate, current ratio, quick ratio, gross profit, net profit and EPS. Retrieve professionally designed Key Facts Voice Assistance Security Platform Investor Funding Presentation Demonstration Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Major Milestones Achieved Voice Assistance Security Platform Investor Funding Presentation Slides Pdf
The following slide showcases various milestones that an open source virtual assistant platform providing company achieves. It outlines milestones such as the release of new versions and new launches. Slidegeeks has constructed Major Milestones Achieved Voice Assistance Security Platform Investor Funding Presentation Slides Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

 Home
Home