Safety Plan

Information Security Programs Ppt PowerPoint Presentation Ideas Design Inspiration Cpb
Presenting this set of slides with name information security programs ppt powerpoint presentation ideas design inspiration cpb. This is an editable Powerpoint eleven stages graphic that deals with topics like information security programs to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Technology Security Program Ppt PowerPoint Presentation Infographic Template Deck Cpb
Presenting this set of slides with name technology security program ppt powerpoint presentation infographic template deck cpb. This is an editable Powerpoint three stages graphic that deals with topics like technology security program to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
IT Security Awareness Training Program Icons Ppt Layouts Structure PDF
Persuade your audience using this IT Security Awareness Training Program Icons Ppt Layouts Structure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including IT Security Awareness, Training Program, Icons. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Security Functioning Centre Various Metrics To Measure Secops System Performance Icons PDF
This slide portrays information regarding the various metrics that considered in order to assess SecOps system performance such as mean time to detection, mean time to resolution, total cases per month, etc. This is a security functioning centre various metrics to measure secops system performance icons pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security analysts productivity, escalation breakdown, average time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Info Security Hardware And Software Update In Company Ppt PowerPoint Presentation File Mockup PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Presenting info security hardware and software update in company ppt powerpoint presentation file mockup pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like peripheral devices, technology, computers and servers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Reverse Proxy Server IT Secure Client Connection To Proxy Server Ppt Icon Graphics Template PDF
This slide represents the secure client connection to the proxy server and is effective for a little or no risk for data transmission between networks. This is a reverse proxy server it secure client connection to proxy server ppt icon graphics template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like server, proxy, cache. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Intelligent Infrastructure Facilities Offered By Implementation Of Security Centre Inspiration PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a Intelligent Infrastructure Facilities Offered By Implementation Of Security Centre Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Malware Detection And Investigation, Investigations by HR, Phishing Detection And Prevention, Risk Mitigation of Left Employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Revolution In Online Business Need Of Cyber Security In Organization Professional PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Revolution In Online Business Need Of Cyber Security In Organization Professional PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Confidential Data, Protection Against Malware, Protection Phishing Scams, Threat Weak Password. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
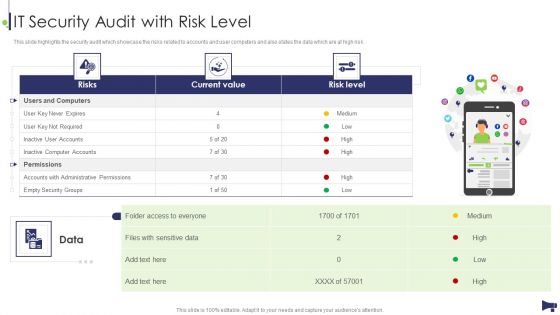
Website And Social Media IT Security Audit With Risk Level Ppt Styles Pictures PDF
This slide highlights the security audit which showcase the risks related to accounts and user computers and also states the data which are at high risk. Presenting Website And Social Media IT Security Audit With Risk Level Ppt Styles Pictures PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Current Value, Risk, Risk Level. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Automation Tools Integration Extended Detection And Response For Endpoint Elements PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. This is a IT Security Automation Tools Integration Extended Detection And Response For Endpoint Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Endpoint Protection, Network Protection, User Protection, Deception. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Tools Integration Managed Detection And Response Layer For Expert Microsoft PDF
This slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. This is a IT Security Automation Tools Integration Managed Detection And Response Layer For Expert Microsoft PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Alert Monitoring, Attack Investigation, Threat Hunting, Incident Response. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
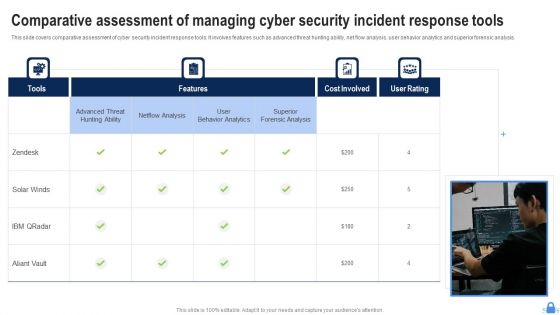
Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF
This slide covers comparative assessment of cyber security incident response tools. It involves features such as advanced threat hunting ability, net flow analysis, user behavior analytics and superior forensic analysis. Presenting Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Superior Forensic Analysis, User Behavior Analytics, Netflow Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
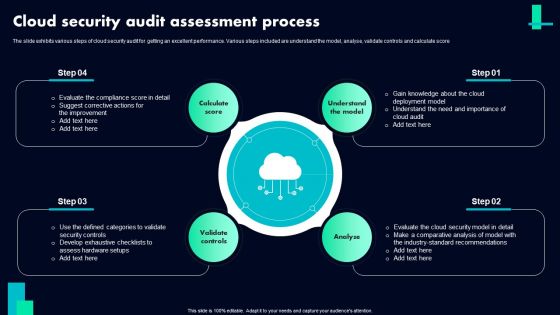
Cloud Security Audit Assessment Process Ppt PowerPoint Presentation Gallery Summary PDF
The slide exhibits various steps of cloud security audit for getting an excellent performance. Various steps included are understand the model, analyse, validate controls and calculate score. Persuade your audience using this Cloud Security Audit Assessment Process Ppt PowerPoint Presentation Gallery Summary PDF. This PPT design covers FOUR stages, thus making it a great tool to use. It also caters to a variety of topics including Calculate Score, Understand The Model, Analyse Validate Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Qualified Traffic Generation Through Search Engines How An Ad Auction Works To Secure Structure PDF
This Qualified Traffic Generation Through Search Engines How An Ad Auction Works To Secure Structure PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Qualified Traffic Generation Through Search Engines How An Ad Auction Works To Secure Structure PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Cyber Security Prevention Strategy Ppt PowerPoint Presentation Ideas Format Ideas Cpb
Presenting this set of slides with name cyber security prevention strategy ppt powerpoint presentation ideas format ideas cpb. This is an editable Powerpoint eight stages graphic that deals with topics like cyber security prevention strategy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Endpoint Security Strategy Ppt PowerPoint Presentation Visual Aids Deck Cpb Pdf Pdf
Presenting this set of slides with name endpoint security strategy ppt powerpoint presentation visual aids deck cpb pdf pdf. This is an editable Powerpoint three stages graphic that deals with topics like endpoint security strategy to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
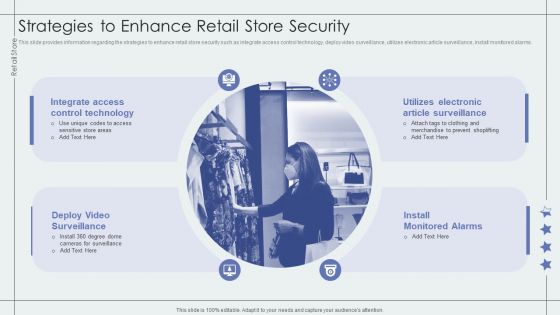
Strategies To Enhance Retail Store Security Retail Outlet Performance Assessment Professional PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms.Deliver an awe inspiring pitch with this creative Strategies To Enhance Retail Store Security Retail Outlet Performance Assessment Professional PDF bundle. Topics like Integrate Access, Control Technology, Prevent Shoplifting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Analysis Ppt PowerPoint Presentation Background Image
This is a security analysis ppt powerpoint presentation background image. This is a two stage process. The stages in this process are business, analysis, strategic, finance, management.

CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Presenting this PowerPoint presentation, titled CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Steps To Develop Strategic IT Security Program Structure PDF
This slide shows the steps to develop strategic security program which covers program assessment, organizational culture, emerging threats, measuring outcome, continual learning and development, etc.Persuade your audience using this Steps To Develop Strategic IT Security Program Structure PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Program Assessment, Emerging Threats, Organizational Culture Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
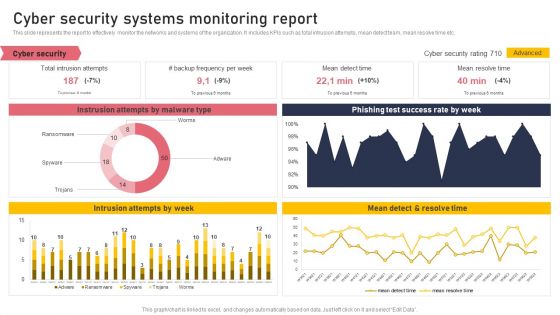
Cyber Security Systems Monitoring Report Formats PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Boost your pitch with our creative Cyber Security Systems Monitoring Report Formats PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Security Analysis Bar Graph Ppt Slides
This is a security analysis bar chart ppt slides. This is a one stage process. The stages in this process are business, finance, marketing.
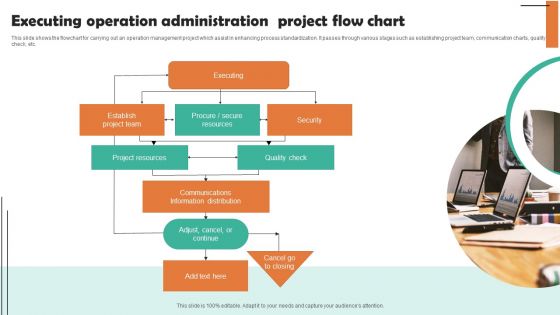
Executing Operation Administration Project Flow Chart Clipart PDF
This slide shows the flowchart for carrying out an operation management project which assist in enhancing process standardization. It passes through various stages such as establishing project team, communication charts, quality check, etc. Presenting Executing Operation Administration Project Flow Chart Clipart PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Executing Security, Establish Project Team. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Role Of Management In Effective Information Security Governance Topics PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Slidegeeks has constructed Role Of Management In Effective Information Security Governance Topics PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
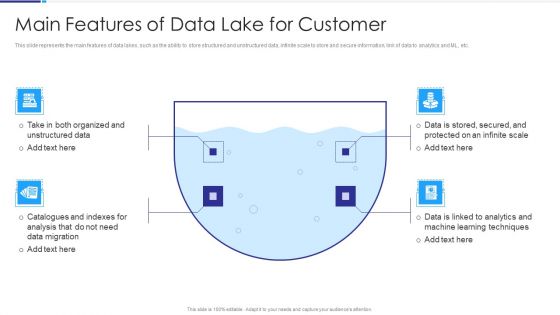
Data Lake Architecture Main Features Of Data Lake For Customer Pictures PDF
This slide represents the main features of data lakes, such as the ability to store structured and unstructured data, infinite scale to store and secure information, link of data to analytics and ML, etc. Deliver an awe inspiring pitch with this creative Data Lake Architecture Main Features Of Data Lake For Customer Pictures PDF bundle. Topics like Organized And Unstructured, Data Analysis, Data Migration, Analytics And Machine Learning Techniques can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Four Month Project Timeline Swimlane Timeline Guidelines PDF
This slide represents four month project scheduling swimlane timeline illustrating departments and there tasks such as team members, technology , security, resource allocation, employee staffing etc. Showcasing this set of slides titled four month project timeline swimlane timeline guidelines pdf. The topics addressed in these templates are security, technology, team members. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack.Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF can be your best option for delivering a presentation. Represent everything in detail using Cyber Security Awareness Training Program Improving Cybersecurity With Incident Microsoft PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Find The Right Time For Solution PowerPoint Templates Ppt Backgrounds For Slides 0513
Your thoughts are dripping with wisdom. Lace it with our Find The Right Time For Solution PowerPoint Templates PPT Backgrounds For Slides. Give a new drift to your views. Change tack with our Clocks PowerPoint Templates. Do not allow things to drift. Ring in changes with our Puzzles or jigsaws PowerPoint Templates.
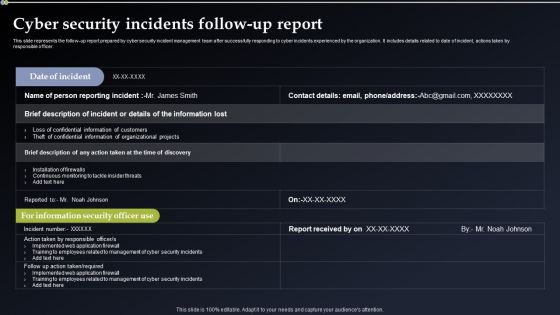
Deploying Cyber Security Incident Response Administration Cyber Security Incidents Follow Up Report Guidelines PDF
This slide represents the follow up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. Explore a selection of the finest Deploying Cyber Security Incident Response Administration Cyber Security Incidents Follow Up Report Guidelines PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Deploying Cyber Security Incident Response Administration Cyber Security Incidents Follow Up Report Guidelines PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Public Relations Guide To Enhance Brand Credibility Budget Securing Tips For Public Relations Summary PDF
This slide shows various tips which can be used by organizations to while developing marketing budget. It includes aligning marketing outcome with organizational goals, strategic insights and highlight impacts. Get a simple yet stunning designed Public Relations Guide To Enhance Brand Credibility Budget Securing Tips For Public Relations Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Public Relations Guide To Enhance Brand Credibility Budget Securing Tips For Public Relations Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
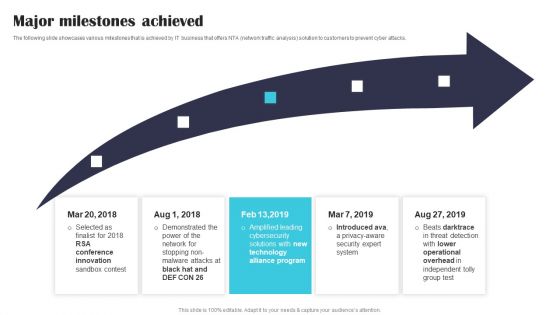
Security Software Company Investor Funding Pitch Deck Major Milestones Achieved Mockup PDF
The following slide showcases various milestones that is achieved by IT business that offers NTA network traffic analysis solution to customers to prevent cyber attacks. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Security Software Company Investor Funding Pitch Deck Major Milestones Achieved Mockup PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Security Software Company Investor Funding Pitch Deck Major Milestones Achieved Mockup PDF.
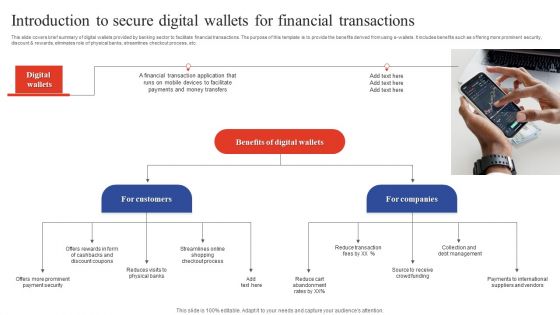
Deployment Of Omnichannel Banking Solutions Introduction To Secure Digital Wallets For Financial Transactions Template PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e-wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. Retrieve professionally designed Deployment Of Omnichannel Banking Solutions Introduction To Secure Digital Wallets For Financial Transactions Template PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Exit Strategy Email And Data Protection Platform Capital Funding Pitch Deck PPT Template
This slide covers the exit strategy of the email security software company. It includes various exit options such as merger and acquisition and initial public offering. Present like a pro with Exit Strategy Email And Data Protection Platform Capital Funding Pitch Deck PPT Template. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Security Functioning Centre Timeframe For Incident Management Ppt Slides Template PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. This is a security functioning centre timeframe for incident management ppt slides template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeframe for incident management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Info Security Dispose Data And Equipment Properly Ppt PowerPoint Presentation File Model PDF
This is a info security dispose data and equipment properly ppt powerpoint presentation file model pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data and hardware, protect it, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Theft Or Loss Of Intellectual Property Ppt Show Guidelines PDF
Presenting Cloud Information Security Theft Or Loss Of Intellectual Property Ppt Show Guidelines PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Crucial Data, Businesses Experience, Cloud Storage. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
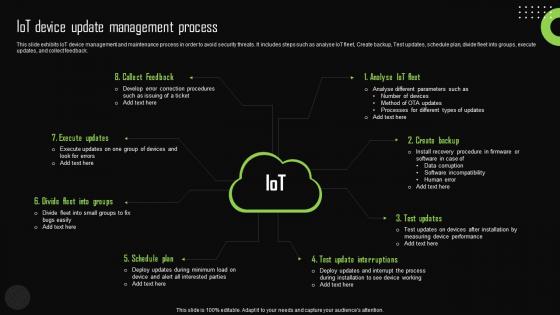
Iot Device Update Management Process Iot Device Management Background Pdf
This slide exhibits IoT device management and maintenance process in order to avoid security threats. It includes steps such as analyse IoT fleet, Create backup, Test updates, schedule plan, divide fleet into groups, execute updates, and collect feedback. This Iot Device Update Management Process Iot Device Management Background Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Competitive Guidelines PDF
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver and pitch your topic in the best possible manner with this security information and event management strategies for financial audit and compliance siem competitive guidelines pdf. Use them to share invaluable insights on siem competitive advantage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Integrations Ideas PDF
This is a security information and event management strategies for financial audit and compliance siem integrations ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security events, network logs, applications and devices, it infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
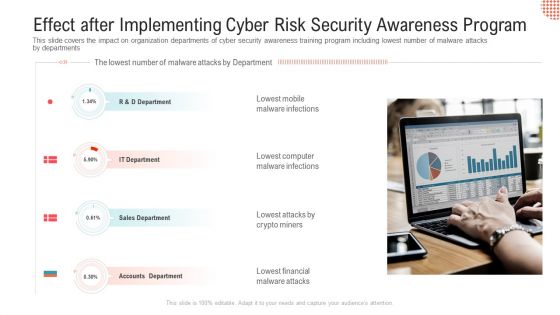
Effect After Implementing Cyber Risk Security Awareness Program Professional PDF
This slide covers the impact on organization departments of cyber security awareness training program including lowest number of malware attacks by departments.This is a effect after implementing cyber risk security awareness program professional pdf. template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like lowest mobile malware infections, lowest computer malware infections. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Logging Sources Mockup PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. Presenting security information and event management strategies for financial audit and compliance siem logging sources mockup pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security devices, network devices, applications, servers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Management Matrix For IT Risk Control Strategies Security Ppt Professional Show PDF
This slide shows the risk management matrix for information technology security which covers the business workflow and technical systems with IT risks and threats such as software security, business controls, control risk modelling, penetration testing, attack modelling, etc. Pitch your topic with ease and precision using this Risk Management Matrix For IT Risk Control Strategies Security Ppt Professional Show PDF. This layout presents information on Corporate Workflow, Technical Systems, Risk. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Expert Systems Design And Implementation Component Clipart PDF
Presenting expert systems design and implementation component clipart pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like service, design, access, ssl security, market. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Best Frameworks For Cybersecurity In Medical Industry Guidelines Pdf
This slide presents best cybersecurity frameworks helpful in allowing external and internal stakeholders to understand and manage network security together as team. It includes NIST, HITRUST, Critical security controls and ISO 27000 series Showcasing this set of slides titled Best Frameworks For Cybersecurity In Medical Industry Guidelines Pdf. The topics addressed in these templates are Frameworks, Description, Adoption Percentage. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
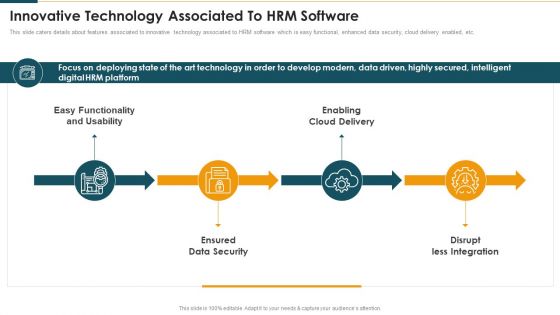
Innovative Technology Associated To Hrm Software Mockup PDF
This slide caters details about features associated to innovative technology associated to HRM software which is easy functional, enhanced data security, cloud delivery enabled, etc. This is a Innovative Technology Associated To Hrm Software Mockup PDF template with various stages. Focus and dispense information on fourstages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Functionality And Usability, Enabling Cloud Delivery, Ensured Data Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
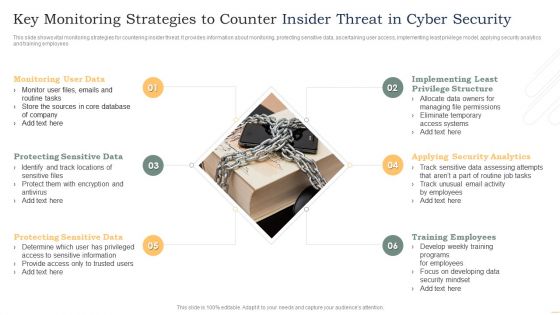
Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF
This slide shows vital monitoring strategies for countering insider threat. It provides information about monitoring, protecting sensitive data, ascertaining user access, implementing least privilege model, applying security analytics and training employees. Persuade your audience using this Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitoring User Data, Protecting Sensitive Data, Protecting Sensitive Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Strategies To Enhance Retail Store Security Retail Outlet Operations Performance Evaluation Clipart PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms.This is a Strategies To Enhance Retail Store Security Retail Outlet Operations Performance Evaluation Clipart PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Utilizes Electronic, Integrate Access, Monitored Alarms. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Retail Outlet Operational Efficiency Analytics Strategies To Enhance Retail Store Security Ideas PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms. This is a Retail Outlet Operational Efficiency Analytics Strategies To Enhance Retail Store Security Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Utilizes Electronic, Article Surveillance, Install Monitored Alarms. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Data Services Certification Programs Cisco Certified Internetwork Expert CCIE Examination Details Rules PDF
This slide covers CCIE examination details including certification, exam number, exam name duration and fees per attempt along with specialist courses. Deliver and pitch your topic in the best possible manner with this IT Data Services Certification Programs Cisco Certified Internetwork Expert CCIE Examination Details Rules PDF. Use them to share invaluable insights on Data Center, Service Provider, Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Info Security Minimize Administrative And Staff Privileges Ppt PowerPoint Presentation Icon Files PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. Presenting info security minimize administrative and staff privileges ppt powerpoint presentation icon files pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like employees, prevent cyber attacks, administrative staff. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
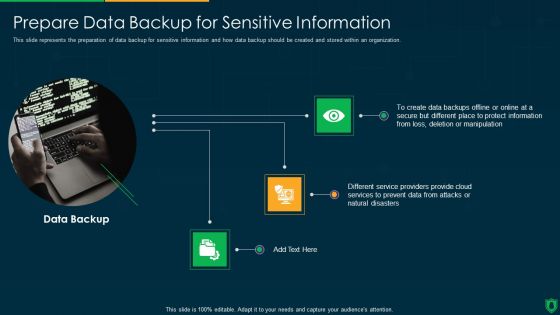
Info Security Prepare Data Backup For Sensitive Information Ppt PowerPoint Presentation File Rules PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. This is a info security prepare data backup for sensitive information ppt powerpoint presentation file rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data backup, provide cloud, prevent data, natural disasters. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Facilitating IT Intelligence Architecture Timeframe For Incident Management In Security Centre Guidelines PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases.This is a Facilitating IT Intelligence Architecture Timeframe For Incident Management In Security Centre Guidelines PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Incident Categorization, Incident Resolution, Incident Prioritization You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Hacking Of Our Social Media Accounts Formats PDF
This slide represents the hacking of a companys social media accounts such as Facebook and Instagram by hackers in 2019 and the amount of money by running scam ads.Presenting IT Security Hacker Hacking Of Our Social Media Accounts Formats PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Scammers Gained, Business Manager, Altered The Password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
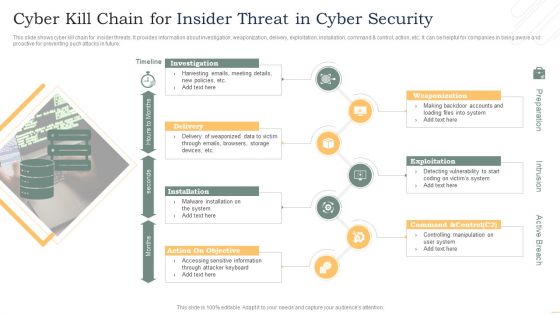
Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF
This slide shows cyber kill chain for insider threats. It provides information about investigation, weaponization, delivery, exploitation, installation, command and control, action, etc. It can be helpful for companies in being aware and proactive for preventing such attacks in future. Presenting Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Investigation, Delivery, Installation, Exploitation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF
This slide represents the reverse proxy server-side technology, which is load balancing, and how reverse proxy side servers help high-traffic websites manage traffic. The Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Addressing Mobile Device Management Business Mobile Device Security Management Download PDF
This slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. This modern and well-arranged Addressing Mobile Device Management Business Mobile Device Security Management Download PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Mobile Device Management Assistance Business Mobile Device Security Management And Mitigation Template PDF
This slide provides information regarding mobile device management technology assistance to employees and to IT department associated to firm. Present like a pro with Mobile Device Management Assistance Business Mobile Device Security Management And Mitigation Template PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Security Software Company Investor Funding Pitch Deck Why Invest With Us Structure PDF
This purpose of the following slide is to convince investors to invest in business by highlighting business growth potential and benefits they will get by making investment. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Security Software Company Investor Funding Pitch Deck Why Invest With Us Structure PDF from Slidegeeks and deliver a wonderful presentation.

 Home
Home