Safety Plan

Information Security Challenges Businesses Face To Protect Consumers Data Privacy Professional PDF
This slide depicts the challenges faced by businesses to protect consumers data privacy, including communication issues, data breaches, cybercrimes, and threats inside the organization. Make sure to capture your audiences attention in your business displays with our gratis customizable Information Security Challenges Businesses Face To Protect Consumers Data Privacy Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cloud Access Security Broker Pillar Visibility Ppt PowerPoint Presentation File Infographics PDF
This slide outlines the overview of the visibility pillar of cloud access security broker. The purpose of this slide is to showcase the working process of the visibility pillar of CASB and it also represents the topography of CASB visibility. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cloud Access Security Broker Pillar Visibility Ppt PowerPoint Presentation File Infographics PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Computing Technology Industry Association Certification Career Roadmap Professional PDF
The following slide showcases certification roadmap for computing technology industry. It shows accreditations in information security, network and cloud technologies, hardware services infrastructure and IT management and strategy for beginner, intermediate, advanced and expert levels. Persuade your audience using this Computing Technology Industry Association Certification Career Roadmap Professional PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information Security, Network And Cloud Technologies, IT Management And Strategy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Risks And Incident Response Playbook Best Work From Home Data Security Practices Pictures PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc. Do you have to make sure that everyone on your team knows about any specific topic. I yes, then you should give Cyber Risks And Incident Response Playbook Best Work From Home Data Security Practices Pictures PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cyber Risks And Incident Response Playbook Best Work From Home Data Security Practices Pictures PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
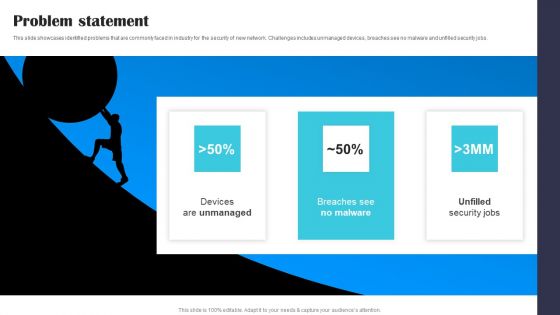
Security Software Company Investor Funding Pitch Deck Problem Statement Themes PDF
This slide showcases identified problems that are commonly faced in industry for the security of new network. Challenges includes unmanaged devices, breaches see no malware and unfilled security jobs. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Security Software Company Investor Funding Pitch Deck Problem Statement Themes PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Evolving BI Infrastructure Facilities Offered By Implementation Of Security Centre Formats PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting evolving bi infrastructure facilities offered by implementation of security centre formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
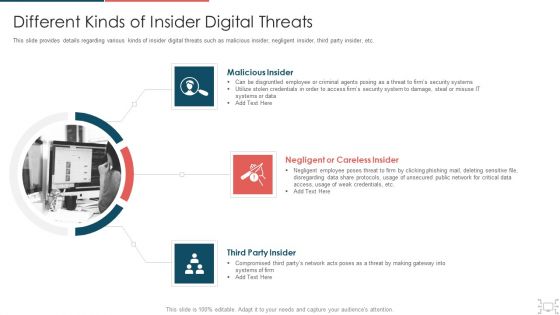
Cyber Security Administration In Organization Different Kinds Of Insider Digital Threats Microsoft PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber security administration in organization different kinds of insider digital threats microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disgruntled, employee, criminal, agents, damage, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
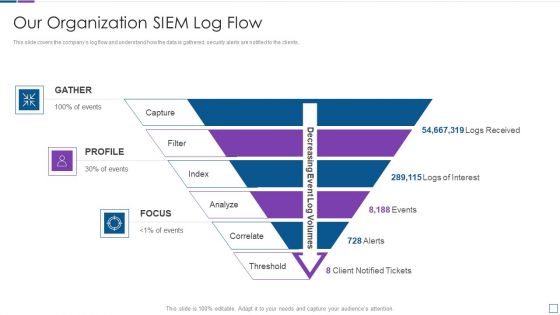
Real Time Assessment Of Security Threats Our Organization SIEM Log Flow Topics PDF
This slide covers the companys log flow and understand how the data is gathered, security alerts are notified to the clients. This is a real time assessment of security threats our organization siem log flow topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our organization siem log flow. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Types Of Threats In Information Technology Security Ppt Slides Example File PDF
This slide depicts the main types of threats in network security, such as network crime, network terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a types of threats in information technology security ppt slides example file pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber attack . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
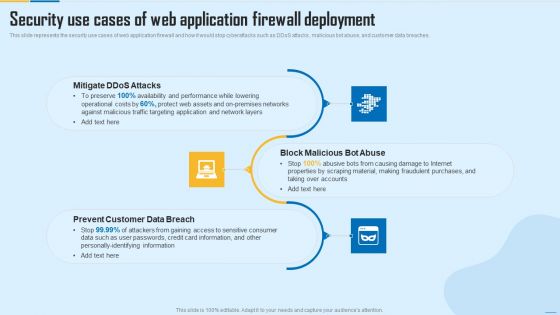
Security Use Cases Of Web Application Firewall Deployment WAF Platform Ideas PDF
This slide represents the security use cases of web application firewall and how it would stop cyberattacks such as DDoS attacks, malicious bot abuse, and customer data breaches. This is a Security Use Cases Of Web Application Firewall Deployment WAF Platform Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Mitigate Ddos Attacks, Prevent Customer Data Breach, Block Malicious Bot Abuse. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
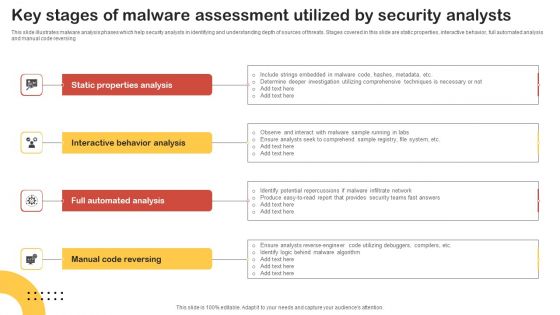
Key Stages Of Malware Assessment Utilized By Security Analysts Graphics PDF
This slide illustrates malware analysis phases which help security analysts in identifying and understanding depth of sources of threats. Stages covered in this slide are static properties, interactive behavior, full automated analysis and manual code reversing. Presenting Key Stages Of Malware Assessment Utilized By Security Analysts Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Static Properties Analysis, Interactive Behavior Analysis, Full Automated Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF.

Four Components Of Information Security With Integrity Ppt PowerPoint Presentation File Gallery PDF
Presenting four components of information security with integrity ppt powerpoint presentation file gallery pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including confidentiality, authentication, integrity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Post It Notes Hacking Prevention Awareness Training For IT Security Slides PDF
Presenting post it notes hacking prevention awareness training for it security slides pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like post it notes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Information And Event Management Strategies For Financial Audit And Compliance Next Evolution Of Siem Software Download PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Presenting security information and event management strategies for financial audit and compliance next evolution of siem software download pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like user entity and behavior analytics, network traffic analysis, endpoint monitoring, threat intelligence, siem foundation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
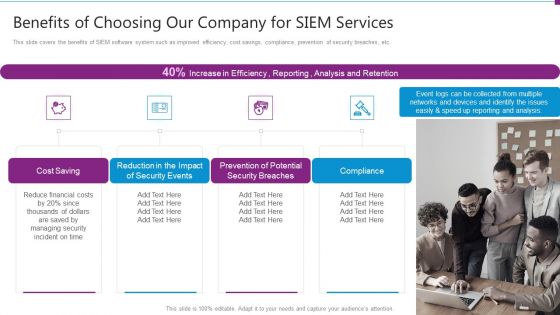
Security Information And Event Management Strategies For Financial Audit And Compliance Benefits Of Choosing Our Company Topics PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a security information and event management strategies for financial audit and compliance benefits of choosing our company topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, security events, security breaches, compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Prevention Of Information Overview Of Cyber Security Awareness Course Icons PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. This Prevention Of Information Overview Of Cyber Security Awareness Course Icons PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF
This slide showcases risks identified during transaction monitoring. It provides information about anti money laundering fines, staff productivity, motivation, organizational profitability, compliance, fees, false positive, workload, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
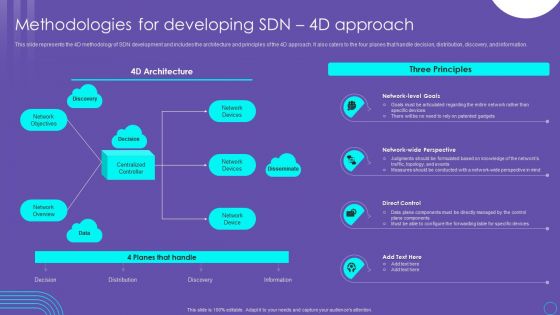
SDN Security Architecture Methodologies For Developing SDN 4D Approach Download PDF
This slide represents the 4D methodology of SDN development and includes the architecture and principles of the 4D approach. It also caters to the four planes that handle decision, distribution, discovery, and information. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download SDN Security Architecture Methodologies For Developing SDN 4D Approach Download PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the SDN Security Architecture Methodologies For Developing SDN 4D Approach Download PDF.
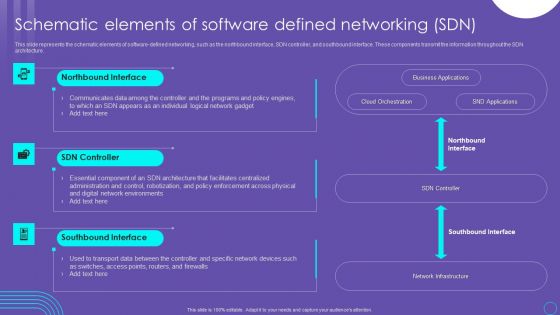
SDN Security Architecture Schematic Elements Of Software Defined Networking SDN Pictures PDF
This slide represents the schematic elements of software defined networking, such as the northbound interface, SDN controller, and southbound interface. These components transmit the information throughout the SDN architecture. Create an editable SDN Security Architecture Schematic Elements Of Software Defined Networking SDN Pictures PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. SDN Security Architecture Schematic Elements Of Software Defined Networking SDN Pictures PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF
This slide represents the information related to the investment requirements to the investors for seeking needed funds and the purpose of seeking finance. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Security Software Company Investor Funding Pitch Deck Investment Ask Clipart PDF today and make your presentation stand out from the rest.

Securing Market Leadership Through Competitive Excellence Company Overview Five Guys Designs PDF
The following slide exhibits complete overview of Five Guys company related to food industry. Information covered in this slide is related to companys mission statement, major stakeholders, products offered, key details and facts and figures. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Securing Market Leadership Through Competitive Excellence Company Overview Five Guys Designs PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Securing Market Leadership Through Competitive Excellence Company Overview Five Guys Designs PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Securing Market Leadership Through Competitive Excellence Conducting USP Analysis For The Brand Topics PDF
The following slide exhibits evaluation of various unique selling point USP which will guide organizations in defining the brand USP and stand out from the major competitors. The analysis is drawn on the basis of common, interesting, unique and dull USP. Get a simple yet stunning designed Securing Market Leadership Through Competitive Excellence Conducting USP Analysis For The Brand Topics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Securing Market Leadership Through Competitive Excellence Conducting USP Analysis For The Brand Topics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
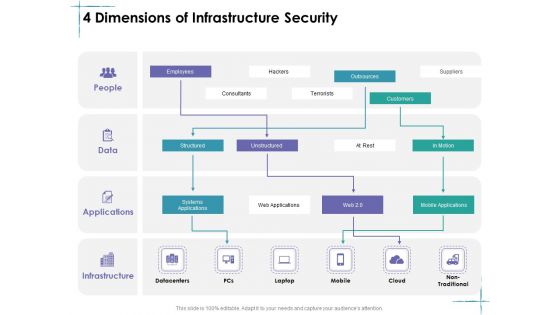
Facility Management 4 Dimensions Of Infrastructure Security Ppt File Layout PDF
This is a facility management 4 dimensions of infrastructure security ppt file layout pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people, data, applications, infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Infrastructure Administration 4 Dimensions Of Infrastructure Security Ppt Model Example Topics PDF
This is a it infrastructure administration 4 dimensions of infrastructure security ppt model example topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people, data, applications, infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
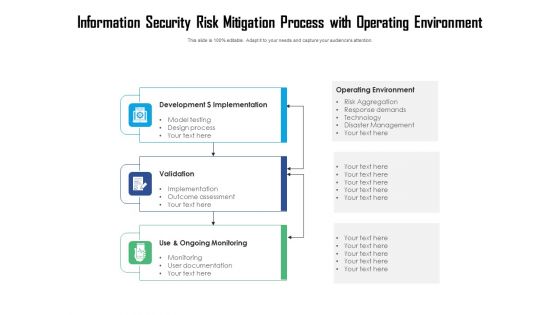
Information Security Risk Mitigation Process With Operating Environment Ppt PowerPoint Presentation File Templates PDF
Persuade your audience using this information security risk mitigation process with operating environment ppt powerpoint presentation file templates pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including development dollar implementation, validation, use and ongoing monitoring. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

E Payment Transaction System Payment Security And Fraud Management Solutions Analysis Infographics PDF
Presenting E payment transaction system payment security and fraud management solutions analysis infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like market basket analysis, device fingerprinting, customer velocity, optimization of your anti fraud measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Infrastructure Designing And Administration 4 Dimensions Of Infrastructure Security Pictures PDF
This is a infrastructure designing and administration 4 dimensions of infrastructure security pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people, data, applications, infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
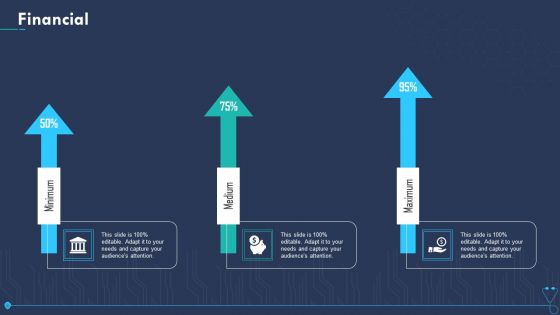
Case Competition Overpower The Obstacle Of Cyber Security In Medicare Financial Elements PDF
Presenting case competition overpower the obstacle of cyber security in medicare financial elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like minimum, medium, maximum. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Case Competition Overpower The Obstacle Of Cyber Security In Medicare Post It Sample PDF
Presenting case competition overpower the obstacle of cyber security in medicare post it sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like post it. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Internet Security Threat Analysis With Attacks Target And Purpose Ppt PowerPoint Presentation Pictures Structure PDF
Presenting internet security threat analysis with attacks target and purpose ppt powerpoint presentation pictures structure pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including social and phishing, passwords and configs, smart and mobile hacking. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Post It Notes Cloud Computing Security IT Ppt Portfolio Graphics Example PDF
This is a post it notes cloud computing security it ppt portfolio graphics example pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Post It Notes IT Security IT Ppt Icon Infographic Template PDF
This is a post it notes it security it ppt icon infographic template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Financing Catalogue For Security Underwriting Agreement Post It Notes Sample PDF
This is a financing catalogue for security underwriting agreement post it notes sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like post it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data Poste It Notes Clipart PDF
This is a Executing security management program to mitigate threats and safeguard confidential organizational data poste it notes clipart pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like poste it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information And Technology Security Operations Facilities Offered By Successful Implementation Guidelines PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a information and technology security operations facilities offered by successful implementation guidelines pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Functioning Centre Various Technologies For Effective Secops Process Template PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. Presenting security functioning centre various technologies for effective secops process template pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like event management, cyber threat intelligence, network traffic analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Dispose Data And Equipment Properly IT Security IT Ppt Icon Clipart Images PDF
This slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Presenting dispose data and equipment properly it security it ppt icon clipart images pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dispose data and equipment properly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Financing Catalogue For Security Underwriting Agreement Key Objectives Of The IPO Issue Mockup PDF
The slide provides the companys objectives behind issuing IPO. Key Objectives include Future Expansion, Option of Alternative Currency, Cash-Out Option, Paying off Debts etc. Presenting financing catalogue for security underwriting agreement key objectives of the ipo issue mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organic and future expansion, option of alternative currency, cash out option, paying debts. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Addressing Several Financial Scenarios And Signs Threat Template PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Presenting cyber security administration in organization addressing several financial scenarios and signs threat template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like insolvency, scenario, bankruptcy, situation, fluctuations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
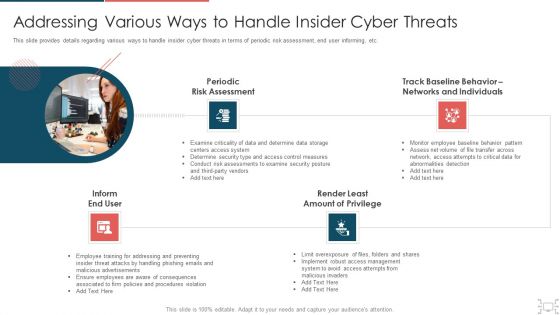
Cyber Security Administration In Organization Addressing Various Ways To Handle Insider Cyber Threats Designs PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a cyber security administration in organization addressing various ways to handle insider cyber threats designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assessment, networks, individuals, determine. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Determine Threat Management Team Structure Information PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting cyber security administration in organization determine threat management team structure information pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like determine threat management team structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Evaluating Financial Practices In Firm Rules PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Presenting cyber security administration in organization evaluating financial practices in firm rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like evaluating financial practices in firm. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
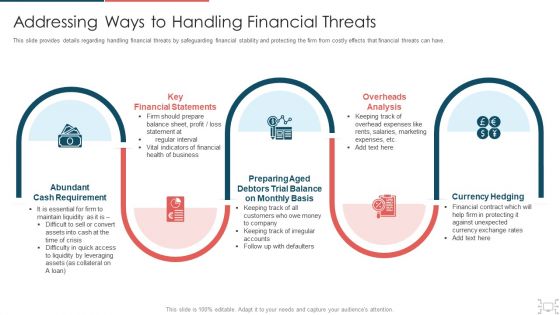
cyber security administration in organization addressing ways to handling financial threats summary pdf
This slide provides details regarding handling financial threats by safeguarding financial stability and protecting the firm from costly effects that financial threats can have. This is a cyber security administration in organization addressing ways to handling financial threats summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like financial, statements, requirement, preparing, balance . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
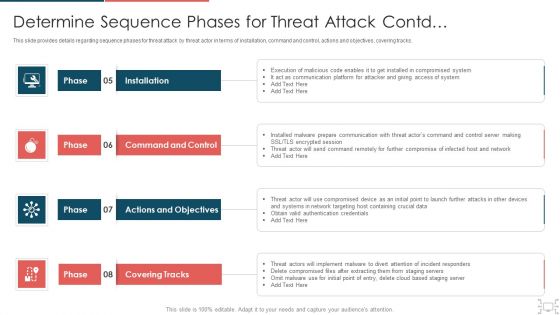
cyber security administration in organization determine sequence phases for threat attack access inspiration pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Presenting cyber security administration in organization determine sequence phases for threat attack access inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communication, platform, access, compromised, session . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

cyber security administration in organization determine sequence phases for threat attack infographics pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber security administration in organization determine sequence phases for threat attack infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internal, threat, perform, phishing, combination . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Secured Video Hosting Platform Investor Capital Funding Solutions Provided By Online Video Hosting Platform Introduction PDF
This slide caters details about solutions rendered by video hosting platform in order to solve issues by providing platform to upload videos and video conversion for accessibility. Presenting secured video hosting platform investor capital funding solutions provided by online video hosting platform introduction pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like solutions provided by online video hosting platform. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
How Is Automation Used In Information Technology Security Ppt File Icon PDF
This slide depicts the network protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting how is automation used in information technology security ppt file icon pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human detection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Security Define Access Control Measures For Employees Ppt Professional Design Templates PDF
This slide represents how it is essential to minimize the rights access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a information technology security define access control measures for employees ppt professional design templates pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like staff duties, organization, roles, access, permissions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Security Minimize Administrative And Staff Privileges Ppt Professional Graphics PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. Presenting information technology security minimize administrative and staff privileges ppt professional graphics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like minimize administrative and staff privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
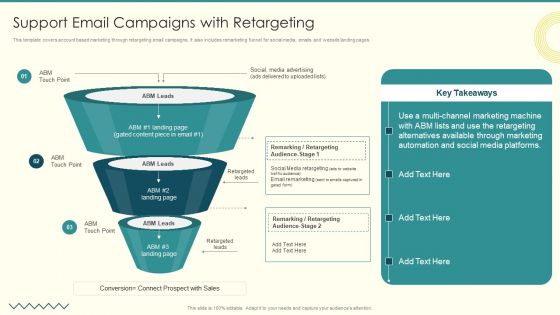
Security And Performance Digital Marketing Support Email Campaigns With Retargeting Elements PDF
This template covers account based marketing through retargeting email campaigns. It also includes remarketing funnel for social media, emails and website landing pages.Presenting Security And Performance Digital Marketing Support Email Campaigns With Retargeting Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Alternatives Available, Remarking Retargeting, Media Advertising. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Features Associated To Mobile Device Management Mobile Device Security Management Mockup PDF
This slide provides information regarding key features associated to mobile device management such as mobile device enrolment, user profile management, mobile device management support. This is a Key Features Associated To Mobile Device Management Mobile Device Security Management Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Device Enrolment, Profile Management, Management Support. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
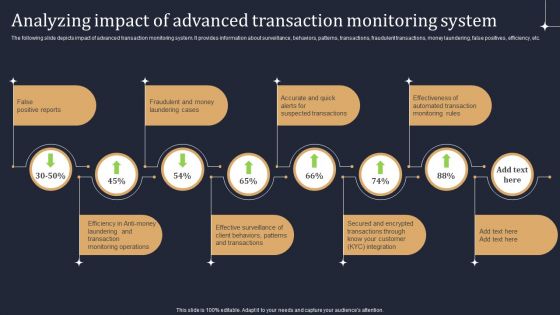
KYC Transaction Monitoring System Business Security Analyzing Impact Of Advanced Transaction Guidelines PDF
The following slide depicts impact of advanced transaction monitoring system. It provides information about surveillance, behaviors, patterns, transactions, fraudulent transactions, money laundering, false positives, efficiency, etc. Boost your pitch with our creative KYC Transaction Monitoring System Business Security Analyzing Impact Of Advanced Transaction Guidelines PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Biometric Technology For Enhancing Mobile Banking Security Ppt Model Graphics PDF
This slide shows information which can be used by organizations to get insights about biometric technology growth in mobile banking. It includes details about process and types of biometric data. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Biometric Technology For Enhancing Mobile Banking Security Ppt Model Graphics PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Security Software Company Investor Funding Pitch Deck Our Solution Demonstration PDF
The following slide showcases solution offered by IT company for its customers which are see the new network, know current threats and protect with high ROI. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Security Software Company Investor Funding Pitch Deck Our Solution Demonstration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Cyber Security Components To Enhance Processes Types Of Cyber Attackers Professional PDF
This slide represents the types of cyber attackers, including cyber criminals, hacktivists, state sponsored attackers, and insider threats. Insider threats can be occurred from within the organization and can be malicious, accidental or negligent. Present like a pro with Cyber Security Components To Enhance Processes Types Of Cyber Attackers Professional PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

KYC Transaction Monitoring System Business Security Importance Of Regular Financial Activity Observation Elements PDF
This slide showcases importance of regular transaction monitoring. It provides information about enhanced efficiency, optimal client segmentation, cost reduction, improved oversight, false positives, fraud detection, investigation, visibility, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate KYC Transaction Monitoring System Business Security Importance Of Regular Financial Activity Observation Elements PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
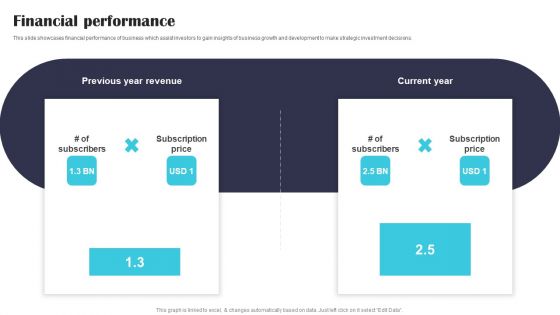
Security Software Company Investor Funding Pitch Deck Financial Performance Formats PDF
This slide showcases financial performance of business which assist investors to gain insights of business growth and development to make strategic investment decisions. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Security Software Company Investor Funding Pitch Deck Financial Performance Formats PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
Table Of Contents For Virtual Storage Ppt Icon Guide PDF
Presenting table of contents for virtual storage ppt icon guide pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like benefits businesses, applications, services, source, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Hospitality Sector Laws And Regulations Lodging And Accommodation Industry IR SS V
This slide showcases the hospitality industry laws and regulations which includes licensing and permits, health and safety, employment laws and alcohol regulations. Welcome to our selection of the Hospitality Sector Laws And Regulations Lodging And Accommodation Industry IR SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

 Home
Home