Safety Plan
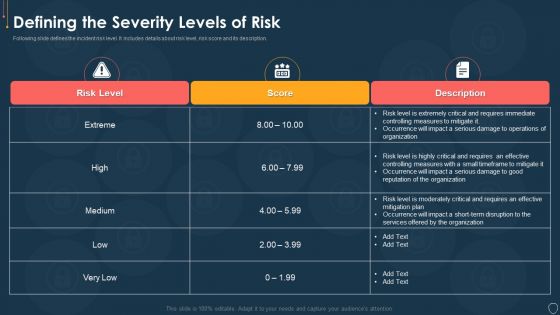
Cyber Security Risk Management Plan Defining The Severity Levels Of Risk Template PDF
Following slide defines the incident risk level. It includes details about risk level, risk score and its description. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan defining the severity levels of risk template pdf. Use them to share invaluable insights on risk level, risk score, description and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
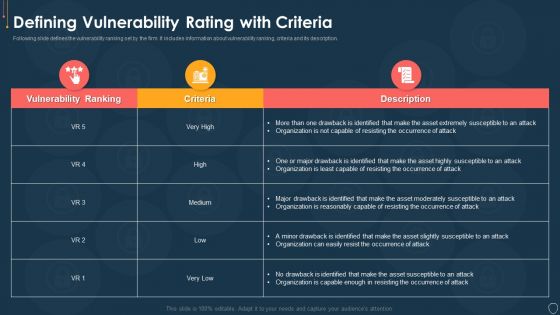
Cyber Security Risk Management Plan Defining Vulnerability Rating With Criteria Summary PDF
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver an awe inspiring pitch with this creative cyber security risk management plan defining vulnerability rating with criteria summary pdf bundle. Topics like vulnerability ranking, criteria, description can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
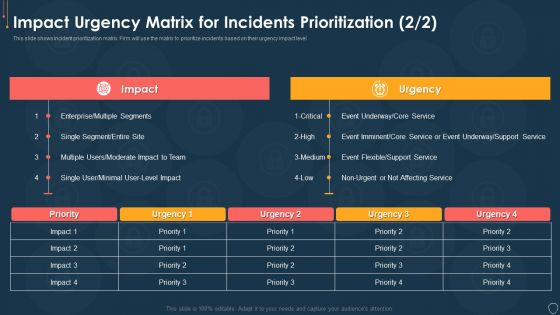
Cyber Security Risk Management Plan Impact Urgency Matrix For Incidents Prioritization Event Topics PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level. Deliver an awe inspiring pitch with this creative cyber security risk management plan impact urgency matrix for incidents prioritization event topics pdf bundle. Topics like impact urgency matrix for incidents prioritization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
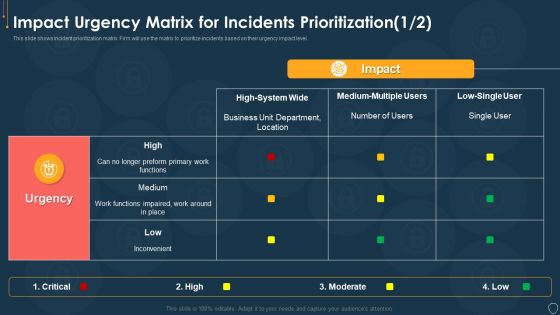
Cyber Security Risk Management Plan Impact Urgency Matrix For Incidents Prioritization Location Information PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan impact urgency matrix for incidents prioritization location information pdf. Use them to share invaluable insights on business, location, inconvenient, moderate, preform and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Incident Management Tool We Will Use Mockup PDF
Mentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform. Deliver an awe inspiring pitch with this creative cyber security risk management plan incident management tool we will use mockup pdf bundle. Topics like incident management tool we will use can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Risk Reporting And Likelihood Elements PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an awe inspiring pitch with this creative cyber security risk management plan risk reporting and likelihood elements pdf bundle. Topics like risk encountered, frequency, reported by status, attack scenario, affected asset, likelihood can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
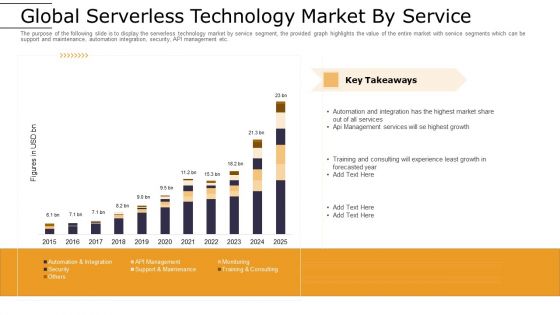
Cloud Computing Technology Implementation Plan Global Serverless Technology Market By Service Information PDF
The purpose of the following slide is to display the serverless technology market by service segment, the provided graph highlights the value of the entire market with service segments which can be support and maintenance, automation integration, security, API management etc. Deliver an awe inspiring pitch with this creative cloud computing technology implementation plan global serverless technology market by service information pdf bundle. Topics like global serverless technology market by service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
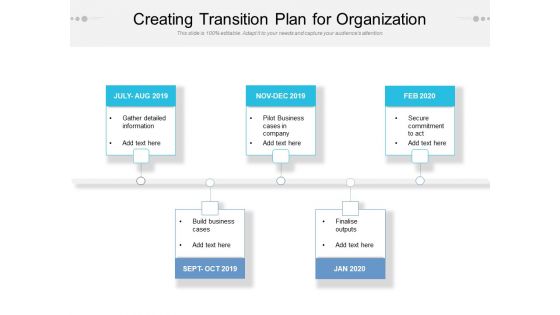
Creating Transition Plan For Organization Ppt PowerPoint Presentation Ideas Grid PDF
Presenting this set of slides with name creating transition plan for organization ppt powerpoint presentation ideas grid pdf. This is a five stage process. The stages in this process are gather detailed information, pilot business cases in company, secure commitment to act, build business cases, finalise outputs. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
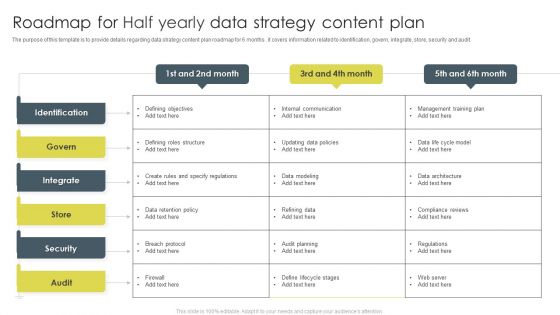
Roadmap For Half Yearly Data Strategy Content Plan Ppt Professional Background PDF
The purpose of this template is to provide details regarding data strategy contents plan roadmap for 6months. It covers information related to identification, govern, integrate, store, security and audit. Showcasing this set of slides titled Roadmap For Half Yearly Data Strategy Content Plan Ppt Professional Background PDF. The topics addressed in these templates are Identification, Integrate, Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Systems Security And Risk Management Plan Steps For Information Security Risk Management Clipart PDF
This slide steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond. Slidegeeks is here to make your presentations a breeze with Information Systems Security And Risk Management Plan Steps For Information Security Risk Management Clipart PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Operational Efficiency Execution Strategy Improve Quality Operational Process Improvement Plan Graphics PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Assigning Resources. This is a operational efficiency execution strategy improve quality operational process improvement plan graphics pdfS template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like team, resource, process, communication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan Facilities Offered By Implementation Of Security Centre Formats PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a developing firm security strategy plan facilities offered by implementation of security centre formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Execute Operational Procedure Plan Steps In Detail Communication And Execution Clipart PDF
This slide provides information about the Sixth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Communication and Execution.Deliver an awe inspiring pitch with this creative execute operational procedure plan steps in detail communication and execution clipart pdf bundle. Topics like operational process improvement deliverables, project team meetings, project status meetings can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Monitoring Plan Steps In Detail Aligning The Incident Management Policies Sample PDF
This slide provides information about the eighth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, punishing, ransomware, supply chain attacks etc. i.e., Aligning the Incident Management Policies and Plan. Presenting cybersecurity monitoring plan steps in detail aligning the incident management policies sample pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security monitoring solutions, ongoing management, incident logging, incident categorization, incident prioritization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Execute Operational Procedure Plan Steps In Detail Process Redesigning Professional PDF
This slide provides information about the Third and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Redesigning. Deliver an awe inspiring pitch with this creative execute operational procedure plan steps in detail process redesigning professional pdf bundle. Topics like potential consequence, several practices, process redesigning practices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Areas Of Operation In Chief Information Officer Transition Plan Template PDF
This slide presents key areas of operation for chief information officer during transition plan, helpful in providing insights on assessment of workforce and strategies by CIO. It includes operating costs, delivery process, talent, architecture, security and compliance. Presenting Key Areas Of Operation In Chief Information Officer Transition Plan Template PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Operating Costs Delivery Process, Talent Architecture, Security Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Map Mapping With Action Plan Ppt PowerPoint Presentation Gallery Slideshow PDF
This slide shows data inventory mapping with action plan. It provides information such as personal data, category, purpose, location, access, security controls, data duration, privacy notice, action required, etc. Persuade your audience using this Data Map Mapping With Action Plan Ppt PowerPoint Presentation Gallery Slideshow PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Security Controls, Data Storing Time, Payroll Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Operational Process Improvement Plan Steps In Detail Communication And Execution Information PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Communication and Execution. Presenting operational process improvement plan steps in detail communication and execution information pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like communicate, team, process, reduces, strategy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
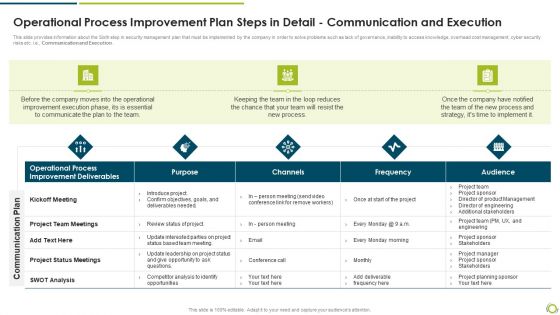
Operational Process Improvement Plan Steps In Detail Communication And Execution Rules PDF
This slide provides information about the Sixth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Communication and Execution.Deliver an awe inspiring pitch with this creative operational process improvement plan steps in detail communication and execution rules pdf bundle. Topics like improvement deliverables, operational process, project team meetings can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Operational Process Improvement Plan Steps In Detail Communication And Execution Guidelines PDF
This slide provides information about the Sixth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Communication and Execution. Presenting operational process improvement plan steps in detail communication and execution guidelines pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like improvement, communicate, team, process, implement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
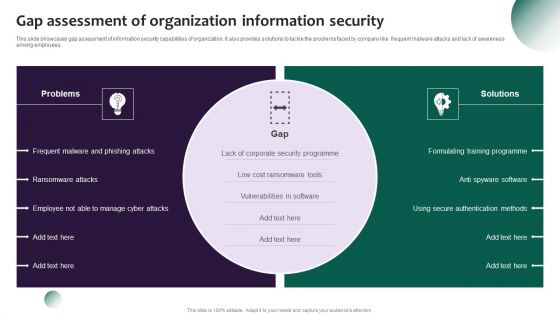
Information Systems Security And Risk Management Plan Gap Assessment Of Organization Information Security Formats PDF
This slide showcases gap assessment of information security capabilities of organization. It also provides solutions to tackle the problems faced by company like frequent malware attacks and lack of awareness among employees. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Information Systems Security And Risk Management Plan Gap Assessment Of Organization Information Security Formats PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Information Systems Security And Risk Management Plan Timeline For Information Security Risk Management Training Inspiration PDF
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress. Present like a pro with Information Systems Security And Risk Management Plan Timeline For Information Security Risk Management Training Inspiration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Table Of Contents Demonstration PDF
Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks table of contents demonstration pdf. Use them to share invaluable insights on security, market, elements, compromised, implemented and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Operational Process Improvement Plan Steps In Detail Process Redesigning Slides PDF
This slide provides information about the Third and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Redesigning. Deliver and pitch your topic in the best possible manner with this operational process improvement plan steps in detail process redesigning slides pdf. Use them to share invaluable insights on potential consequence, implementation, strategies, risk analysis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Operational Process Improvement Plan Steps In Detail Process Analysis Formats PDF
This slide provides information about the second step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Analysis. Presenting operational process improvement plan steps in detail process analysis formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technique implementation, process analysis techniques, process improvement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Monitoring Plan Steps In Detail Monitoring All Systems Introduction PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative cybersecurity monitoring plan steps in detail monitoring all systems introduction pdf bundle. Topics like system network category, monitoring done can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Methods To Develop Advanced IT Security Monitoring Plan Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This methods to develop advanced it security monitoring plan ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fourty four slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Operational Process Improvement Plan Steps In Detail Process Redesigning Elements PDF
This slide provides information about the third step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Process Redesigning. Deliver an awe inspiring pitch with this creative operational process improvement plan steps in detail process redesigning elements pdf bundle. Topics like risk analysis, metrics, implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Operational Process Improvement Plan Steps In Detail Monitoring And Optimization Clipart PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Monitoring and Optimization.Deliver and pitch your topic in the best possible manner with this operational process improvement plan steps in detail monitoring and optimization clipart pdf. Use them to share invaluable insights on technical business process monitoring, process improvement, implementation costs and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Operational Process Improvement Plan Steps In Detail Process Mapping Pictures PDF
This slide provides information about the first step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e, Process Mapping.Deliver an awe inspiring pitch with this creative operational process improvement plan steps in detail process mapping pictures pdf bundle. Topics like process mapping applications, workflow applications, process mapping can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Operational Process Improvement Plan Steps In Detail Process Redesigning Graphics PDF
This slide provides information about the Third step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Redesigning. Deliver and pitch your topic in the best possible manner with this operational process improvement plan steps in detail process redesigning graphics pdf. Use them to share invaluable insights on potential consequence, process redesigning practices, practice implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Operational Process Improvement Plan Steps In Detail Assigning Resources Background PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Assigning Resources. Presenting operational process improvement plan steps in detail assigning resources background pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like reducing communication issues, perform process visualizations, roles and responsibilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Assigning Resources Professional PDF
This slide provides information about the fourth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Assigning Resources. This is a operational process improvement plan steps in detail assigning resources professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like processes, team, cost. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Operational Process Improvement Plan Steps In Detail Monitoring And Optimization Demonstration PDF
This slide provides information about the seventh and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Monitoring and Optimization. Presenting operational process improvement plan steps in detail monitoring and optimization demonstration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like process improvement, performance, team. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Process Mapping Mockup PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Mapping. Presenting operational process improvement plan steps in detail process mapping mockup pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like process improvement, graphic software, applications, accountability, productivity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing Firm Security Strategy Plan Determine Staff Training Schedule For Skills Enhancement Infographics PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Presenting developing firm security strategy plan determine staff training schedule for skills enhancement infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like determine staff training schedule for skills enhancement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
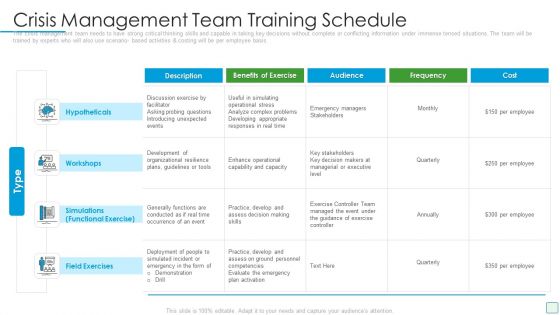
Developing Firm Security Strategy Plan Crisis Management Team Training Schedule Demonstration PDF
The crisis management team needs to have strong critical thinking skills and capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario- based activities and costing will be per employee basis. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan crisis management team training schedule demonstration pdf. Use them to share invaluable insights on hypotheticals, workshops, simulations, field exercises and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Methods To Develop Cybersecurity Monitoring Plan Steps In Detail Review And Risk Analysis Structure PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, punishing, ransomware, supply chain attacks etc. i.e., Review and Risk Analysis. Deliver an awe inspiring pitch with this creative methods to develop cybersecurity monitoring plan steps in detail review and risk analysis structure pdf bundle. Topics like potential consequence, low, medium, high can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description.Presenting Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Category Of Security Controls, Controls Description, Secured Firewall Configuration In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Operational Process Improvement Plan Steps In Detail Developing An Implementation Brochure PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Developing an Implementation Plan and Timeline. This is a operational process improvement plan steps in detail developing an implementation brochure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project, budget, risk, required, goals. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
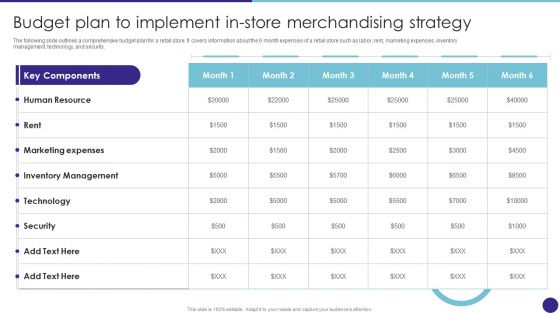
Budget Plan To Implement In Store Merchandising Strategy Retail Merchandising Techniques Inspiration PDF
The following slide outlines a comprehensive budget plan for a retail store. It covers information about the 6 month expenses of a retail store such as labor, rent, marketing expenses, inventory management, technology, and security.Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Budget Plan To Implement In Store Merchandising Strategy Retail Merchandising Techniques Inspiration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Budget Plan To Implement In Store Merchandising Strategy Retail Merchandising Techniques Inspiration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Current Security Monitoring Key Portrait PDF
This slide shows some of the current Security Monitoring challenges and issues that are faced by the company and cyber security monitoring managers. This is a continuous development evaluation plan eliminate cyber attacks current security monitoring key portrait pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware attacks, pnishing attacks, ransomware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan How Firm Handle Various Insider Threats At Workplace Elements PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a developing firm security strategy plan how firm handle various insider threats at workplace elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan Selecting Data Centre Management Solution Pictures PDF
This slide will help firm in choosing the suitable data center management solution by analyzing on various parameters such as server health management, firmware update, ghost server detection, equipment scheduling, etc. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan selecting data centre management solution pictures pdf. Use them to share invaluable insights on monitoring, management, develop, ghost server and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
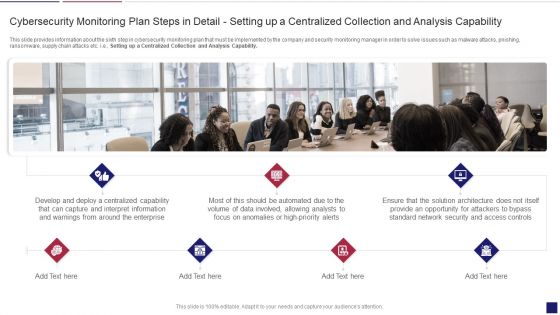
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Apability Inspiration PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring apability inspiration pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
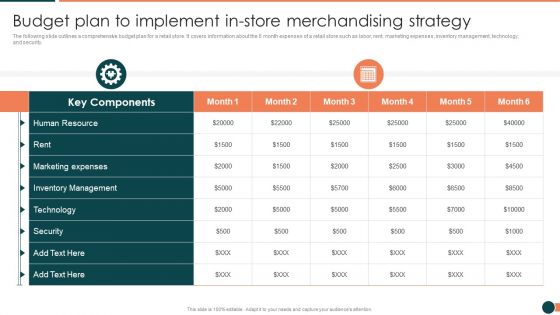
Developing Retail Marketing Strategies To Increase Revenue Budget Plan To Implement Template PDF
The following slide outlines a comprehensive budget plan for a retail store. It covers information about the 6 month expenses of a retail store such as labor, rent, marketing expenses, inventory management, technology, and security.Deliver an awe inspiring pitch with this creative Developing Retail Marketing Strategies To Increase Revenue Budget Plan To Implement Template PDF bundle. Topics like Marketing Expenses, Inventory Management, Technology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Addressing Three Essential Attributes Of Information Summary PDF
This slide provides information about essential attributes of information in terms of protecting confidentiality, ensuring integrity and maintaining availability. This is a developing firm security strategy plan addressing three essential attributes of information summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protecting confidentiality, ensuring integrity, maintaining availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
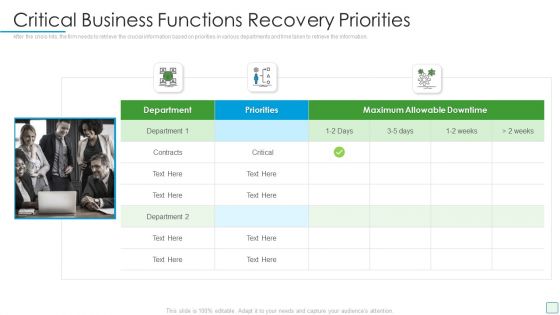
Developing Firm Security Strategy Plan Critical Business Functions Recovery Priorities Infographics PDF
After the crisis hits, the firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. This is a developing firm security strategy plan critical business functions recovery priorities infographics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like critical business functions recovery priorities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
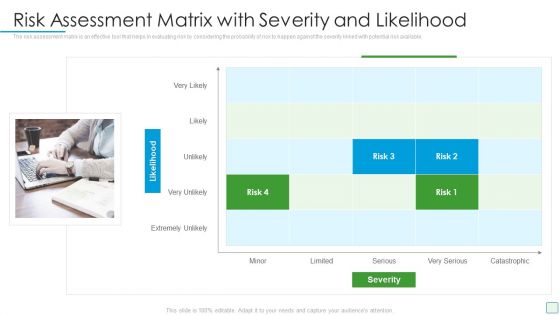
Developing Firm Security Strategy Plan Risk Assessment Matrix With Severity And Likelihood Portrait PDF
The risk assessment matrix is an effective tool that helps in evaluating risk by considering the probability of risk to happen against the severity linked with potential risk available. This is a developing firm security strategy plan risk assessment matrix with severity and likelihood portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk assessment matrix with severity and likelihood. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Execution Of ICT Strategic Plan ICT Business Security KPI Dashboard Designs PDF
This slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc. Boost your pitch with our creative Execution Of ICT Strategic Plan ICT Business Security KPI Dashboard Designs PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Information Systems Security And Risk Management Plan Ppt PowerPoint Presentation Complete Deck With Slides
Use this Information Systems Security And Risk Management Plan Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy eight slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

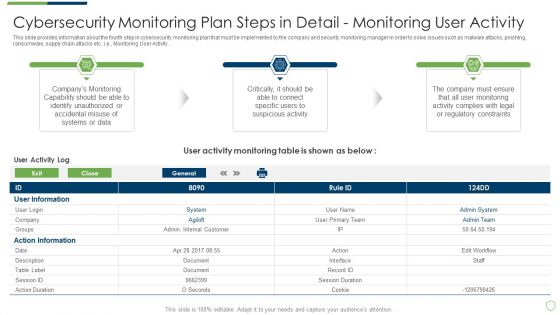
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Activity Structure PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring activity structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring user activity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Monitoring Plan Steps In Detail Monitoring Network Traffic Summary PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring Network Traffic. Presenting cybersecurity monitoring plan steps in detail monitoring network traffic summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like inbound and outbound traffic, could indicate attacks, unusual network traffic. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cyber Security Categorical Cases Action Plan Response Ppt PowerPoint Presentation Icon Deck PDF
This slide highlights security risks occurred in the company. The purpose of this template is to report the severity of security threats. It also includes action steps taken in prevention or resolution of security incidents along with risk categories. Showcasing this set of slides titled Cyber Security Categorical Cases Action Plan Response Ppt PowerPoint Presentation Icon Deck PDF. The topics addressed in these templates are Incidents, Category, Severity, Response Action Steps. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
IT Security Plan Best Practices To Defend Against Threats Icons PDF
This slide represents cyber security strategy best practices to defend against threats such a development of insider threat program, training employees, maintaining compliance etc. Persuade your audience using this IT Security Plan Best Practices To Defend Against Threats Icons PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Updating Systems And Software, Data Backup, Maintaining Compliance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Gaming Cyber Security Cases Action Plan Scorecard For Response Ppt PowerPoint Presentation File Styles PDF
This slide highlights scorecard related to security breaches in gaming field. The purpose of this template is to rate the incidents based on severity. It includes elements such as account taken over, personal details posting on web, spyware, data breaches and cyber bullying. Showcasing this set of slides titled Gaming Cyber Security Cases Action Plan Scorecard For Response Ppt PowerPoint Presentation File Styles PDF. The topics addressed in these templates are Incident, Score, Data Breaches, Low, High. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Structure PDF
This slide provides information about some of the best security monitoring tools that are available with the security monitoring manager and what tool is selected by the security monitoring manager based on tool implementation costs, tool implementation time etc. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring structure pdf. Use them to share invaluable insights on cybersecurity monitoring tools to be implemented and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
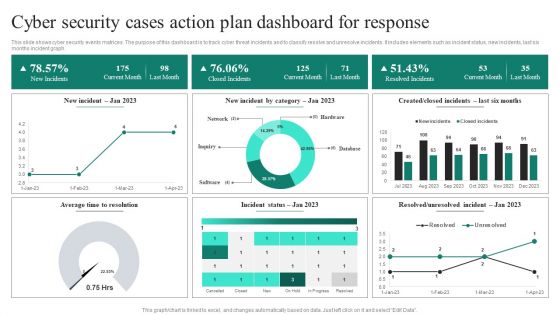
Cyber Security Cases Action Plan Dashboard For Response Ppt PowerPoint Presentation File Deck PDF
This slide shows cyber security events matrices. The purpose of this dashboard is to track cyber threat incidents and to classify resolve and unresolve incidents. It includes elements such as incident status, new incidents, last six months incident graph. Showcasing this set of slides titled Cyber Security Cases Action Plan Dashboard For Response Ppt PowerPoint Presentation File Deck PDF. The topics addressed in these templates are Current Month, Closed Incidents, Last Month, Resolved Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
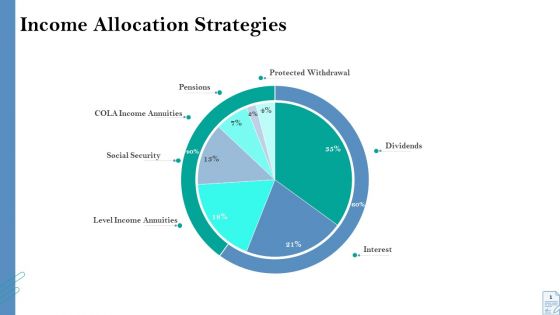
Retirement Insurance Benefit Plan Income Allocation Strategies Ppt Infographic Template Files PDF
Deliver and pitch your topic in the best possible manner with this retirement insurance benefit plan income allocation strategies ppt infographic template files pdf. Use them to share invaluable insights on social security, interest, protected withdrawal, pensions, level income annuities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
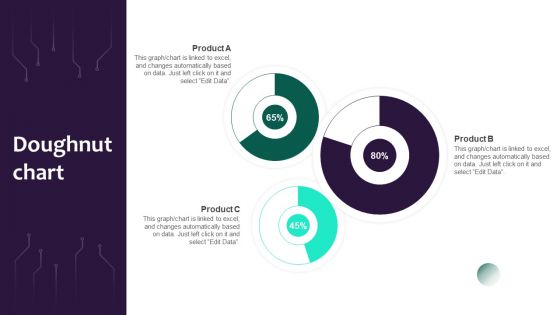
Information Systems Security And Risk Management Plan Doughnut Chart Rules PDF
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Information Systems Security And Risk Management Plan Doughnut Chart Rules PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

 Home
Home