Safety Management
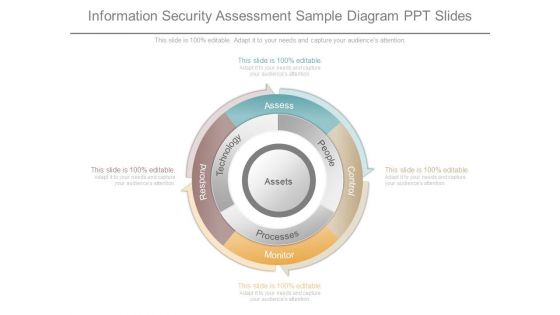
Information Security Assessment Sample Diagram Ppt Slides
This is a information security assessment sample diagram ppt slides. This is a four stage process. The stages in this process are assess, people, processes, technology, respond, monitor, control.

Market Restraints Impacting The Global Security Industry PPT Template IR SS V
The slide provides an insight on the market restraints existing in the Defense market. The purpose of this slide is to aware about the different areas of Defense which are impacted. It capture the information related to short comings faced in the industry. This modern and well-arranged Market Restraints Impacting The Global Security Industry PPT Template IR SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Key Elements Of Iso Standards Harnessing The World Of Ethical Ppt Presentation
This slide represents the elements of ISO standards for security testing such as confidentiality, integrity, availability, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Key Elements Of Iso Standards Harnessing The World Of Ethical Ppt Presentation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

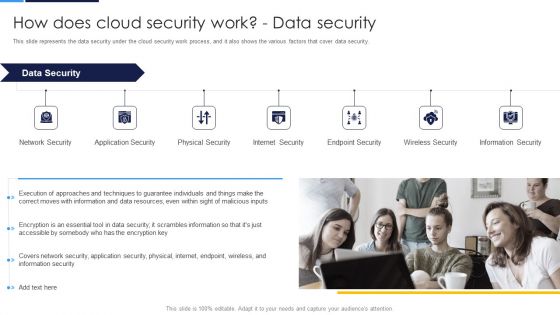
How Does Cloud Security Work Data Security Cloud Computing Security IT Ppt Ideas Slide Download PDF
This slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. Presenting how does cloud security work data security cloud computing security it ppt ideas slide download pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like network security, internet security, endpoint security, wireless security, physical security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Workforce Security Realization Coaching Plan Effect After Implementing Cyber Risk Security Awareness Program Structure PDF
This slide covers the impact on organization departments of cyber security awareness training program including lowest number of malware attacks by departments. Presenting workforce security realization coaching plan effect after implementing cyber risk security awareness program structure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like it department, sales department, accounts department. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Data Security Industry Report Csr Initiatives Taken By Companies In Cybersecurity Industry IR SS V
The slide outlines CSR initiatives undertaken by the cybersecurity industry. The purpose of the slide is to encourage ethical practices, social responsibility, and sustainable development. The key components include cybersecurity education and training, community engagement. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Global Data Security Industry Report Csr Initiatives Taken By Companies In Cybersecurity Industry IR SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Organization Three Months Automation Machinery Roadmapping With Security And Compliance Rules
Introducing our organization three months automation machinery roadmapping with security and compliance rules. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Organization Half Yearly Automation Machinery Roadmapping With Security And Compliance Background
Presenting our jaw dropping organization half yearly automation machinery roadmapping with security and compliance background. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

30 60 90 Days Plan To Implement Data Security In Cloud Computing Ppt Sample
This slide represents 30-60-90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Find a pre-designed and impeccable 30 60 90 Days Plan To Implement Data Security In Cloud Computing Ppt Sample. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
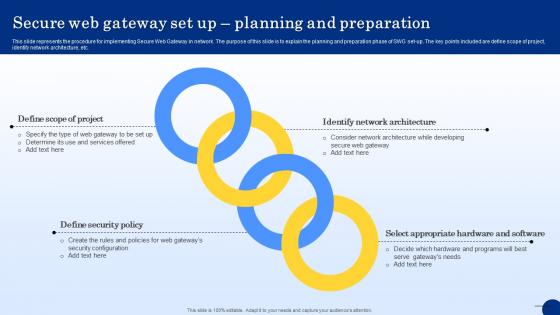
Secure Web Gateway Set Up Planning And Preparation Web Threat Protection System
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the planning and preparation phase of SWG set-up. The key points included are define scope of project, identify network architecture, etc. Get a simple yet stunning designed Secure Web Gateway Set Up Planning And Preparation Web Threat Protection System. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Secure Web Gateway Set Up Planning And Preparation Web Threat Protection System can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

DISC Assessment Profile Worksheet Of An Effective Leader Rules PDF
This slide covers profile sheet for expected traits for an efficient team leader. It includes trait styles such as dominance, , influence, conscientiousness and steadiness with different behavioural approach for recognition, preferred work environment, pace, security, motivation, metrics, fears, etc. Showcasing this set of slides titled DISC Assessment Profile Worksheet Of An Effective Leader Rules PDF. The topics addressed in these templates are Metrics, Preferred Work Environment, High Self Confidence. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

How Amazon Secured Brand Position By Maintaining Leadership Ppt PowerPoint Presentation File Slides PDF
This slide provides information regarding key initiatives taken by Amazon to leverage its leadership through maintaining product selection, several features and services, and subsidiaries. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our How Amazon Secured Brand Position By Maintaining Leadership Ppt PowerPoint Presentation File Slides PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into How Amazon Secured Brand Position By Maintaining Leadership Ppt PowerPoint Presentation File Slides PDF
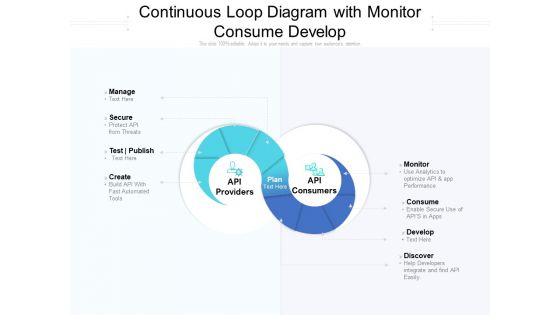
Continuous Loop Diagram With Monitor Consume Develop Ppt PowerPoint Presentation Outline Example Topics
Presenting this set of slides with name continuous loop diagram with monitor consume develop ppt powerpoint presentation outline example topics. This is a two stage process. The stages in this process are manage, secure, protect api, test publish, create, api providers, api consumers, monitor, consume, develop, discover. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
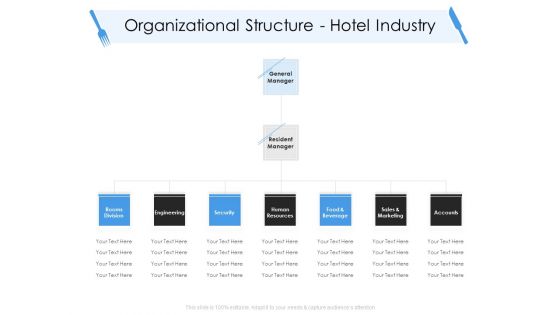
Tourism And Hospitality Industry Organizational Structure Hotel Industry Information PDF
Presenting tourism and hospitality industry organizational structure hotel industry information pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like human resources, food and beverage, sales and marketing, accounts, security, general manager. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Technology Guide For Serverless Computing Disadvantages Of Public Cloud Professional PDF
Presenting technology guide for serverless computing disadvantages of public cloud professional pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like lacks correct managements, performance, weak on security, customization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Keys Tied To Chain Security PowerPoint Templates Ppt Background For Slides 1112
We present our Keys Tied To Chain Security PowerPoint Templates PPT Background For Slides 1112.Use our Business PowerPoint Templates because, Spell out your advertising plans to increase market share. The feedback has been positive and productive Use our Success PowerPoint Templates because,This Slide offers an excellent background to build up the various stages of your business process. Use our Chains PowerPoint Templates because,Our PowerPoint templates designed for your ideas to sell. Use our Finance PowerPoint Templates because,Let this slide illustrates others piggyback on you to see well over the horizon Use our Marketing PowerPoint Templates because,Networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilitiesUse these PowerPoint slides for presentations relating to Keys tied to chain, business, success, chains, finance, marketing. The prominent colors used in the PowerPoint template are Yellow, Brown, White
Local Security Policy In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Local Security Policy In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Local Security Policy that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Security Icon In Powerpoint And Google Slides Cpb
Introducing our well designed Security Icon In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Security Icon. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.
Email Security Industry Report In Powerpoint And Google Slides Cpb
Introducing our well-designed Email Security Industry Report In Powerpoint And Google Slides Cpb This PowerPoint design presents information on topics like Email Security Industry Report As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.

Default Network Security In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Default Network Security In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Default Network Security that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Secure Streaming Essentials In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Secure Streaming Essentials In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Secure Streaming Essentials that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Protection Technology Security In Powerpoint And Google Slides Cpb
Introducing our well-designed Protection Technology Security In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Protection Technology Security. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.
Machine Driven Learning Roles And Responsibilities Ppt Icon Graphic Tips PDF
This slide depicts the roles of solution architect, business analyst, project manager, IT security admin, process owner of the robotic process automation and their responsibilities and duties. Deliver an awe inspiring pitch with this creative machine driven learning roles and responsibilities ppt icon graphic tips pdf bundle. Topics like machine driven learning roles and responsibilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
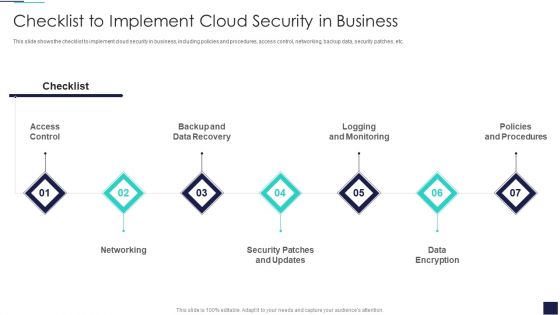
Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. This is a Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Policies And Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Topics That Fall Under The Umbrella Of Cloud Security Ppt Layouts Inspiration PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance. This is a Cloud Information Security Topics That Fall Under The Umbrella Of Cloud Security Ppt Layouts Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Threat Prevention, Threat Detection. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Security In Cloud Computing Cloud Data Security Using Cryptography Formats Pdf
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues. Retrieve professionally designed Data Security In Cloud Computing Cloud Data Security Using Cryptography Formats Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
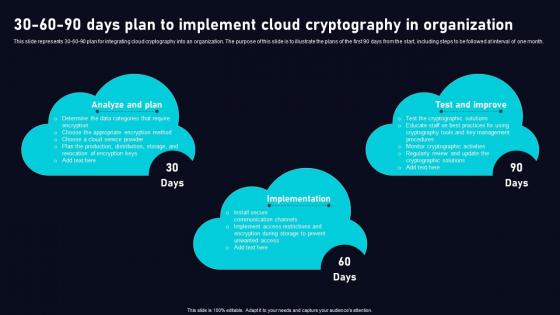
30 60 90 Days Plan To Implement Cloud Data Security Using Cryptography Slides Pdf
This slide represents 30 60 90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give 30 60 90 Days Plan To Implement Cloud Data Security Using Cryptography Slides Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable 30 60 90 Days Plan To Implement Cloud Data Security Using Cryptography Slides Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Secure Web Gateway For Remote And On Site Workers Web Threat Protection System
This slide represents the on-premise and cloud based SWG technology solution for organizations. The purpose of this slide is to provide visualization of Secure Web Gateway structure enabling encrypted web surfing for both on-site and remote employees. Do you know about Slidesgeeks Secure Web Gateway For Remote And On Site Workers Web Threat Protection System These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Cybersecurity Considerations For Technology Transformation In Local Administration Topics pdf
This slide highlights cybersecurity factors for local governments digital transformation. The purpose of this template is to protect digital assets and data during the conversion processes. It includes elements such as risk assessment, access controls, network security, etc. Showcasing this set of slides titled Cybersecurity Considerations For Technology Transformation In Local Administration Topics pdf. The topics addressed in these templates are Risk Assessment, Cybersecurity Governance, Access Controls. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
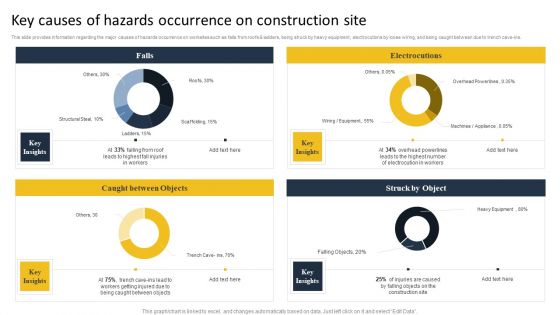
Security Control Techniques For Real Estate Project Key Causes Of Hazards Occurrence On Construction Site Formats PDF
This slide provides information regarding the major causes of hazards occurrence on worksites such as falls from roofs AND ladders, being struck by heavy equipment, electrocutions by loose wiring, and being caught between due to trench cave-ins. Find a pre designed and impeccable Security Control Techniques For Real Estate Project Key Causes Of Hazards Occurrence On Construction Site Formats PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for. Download the template from Slidegeeks today and give a unique touch to your presentation.

Organization Five Years Automation Machinery Roadmapping With Security And Compliance Diagrams
Presenting the organization five years automation machinery roadmapping with security and compliance diagrams. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF
This slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF today and make your presentation stand out from the rest.

Bar Graph With Business Success PowerPoint Templates Ppt Backgrounds For Slides 0613
Play the doctor with our Bar Graph With Business Success PowerPoint Templates PPT Backgrounds For Slides. Control operations with your ideas. Document your views on our Business PowerPoint Templates. They will create a strong impression. Plan your documentary shot by shot. Break them down on our Security PowerPoint Templates.
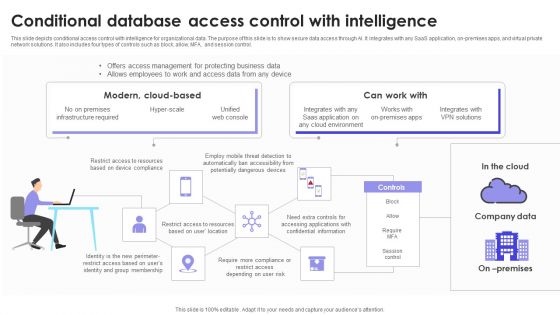
Conditional Database Access Control With Intelligence Download PDF
This slide depicts conditional access control with intelligence for organizational data. The purpose of this slide is to show secure data access through AI. It integrates with any SaaS application, on-premises apps, and virtual private network solutions. It also includes four types of controls such as block, allow, MFA, and session control. Pitch your topic with ease and precision using this Conditional Database Access Control With Intelligence Download PDF. This layout presents information on Company Data, Modern, Intelligence. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc.This is a Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Logging And Monitoring You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Awareness Training Program Challenges Rules PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Presenting Security Awareness Training Program Challenges Rules PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Outdated Content, Burden On Administrators, Employee Participation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
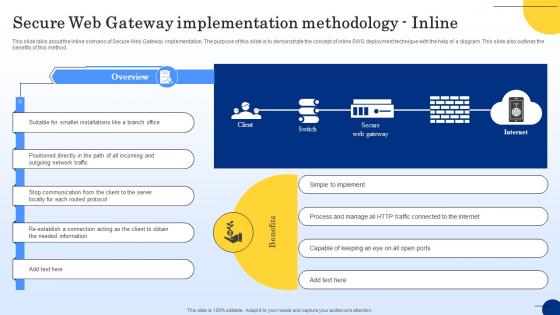
Secure Web Gateway Implementation Methodology Inline Web Threat Protection System
This slide talks about the inline scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of inline SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Boost your pitch with our creative Secure Web Gateway Implementation Methodology Inline Web Threat Protection System. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example
This slide demonstrates the working structure of hashing technique of cloud cryptography with the help of an illustrative diagram. The key components included are original data, hashing algorithm, one-way hash, digital signature, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Securing Market Leadership Through Competitive Excellence Pros And Cons Of Red Ocean Strategy Microsoft PDF
The following slide exhibits the advantages and disadvantages of red ocean strategy. The advantages mentioned in the slide are no need to create new marketplace, high demand of products and services etc. The disadvantages are difficult to survive in the existing market, no extraordinary profits etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Securing Market Leadership Through Competitive Excellence Pros And Cons Of Red Ocean Strategy Microsoft PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Securing Market Leadership Through Competitive Excellence Pros And Cons Of Red Ocean Strategy Microsoft PDF today and make your presentation stand out from the rest.
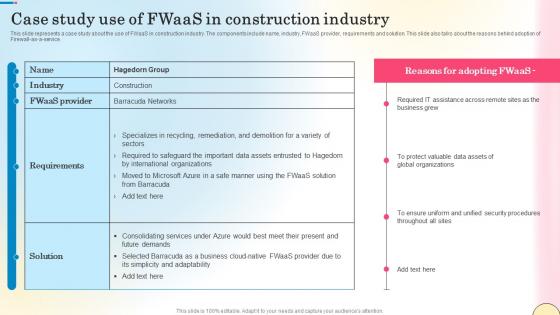
Case Study Use Of Fwaas In Construction Industry Network Security Guidelines Pdf
This slide represents a case study about the use of FWaaS in construction industry. The components include name, industry, FWaaS provider, requirements and solution. This slide also talks about the reasons behind adoption of Firewall-as-a-service. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Case Study Use Of Fwaas In Construction Industry Network Security Guidelines Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Case Study Use Of Fwaas In Construction Industry Network Security Guidelines Pdf today and make your presentation stand out from the rest

Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf
This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf from Slidegeeks and deliver a wonderful presentation.
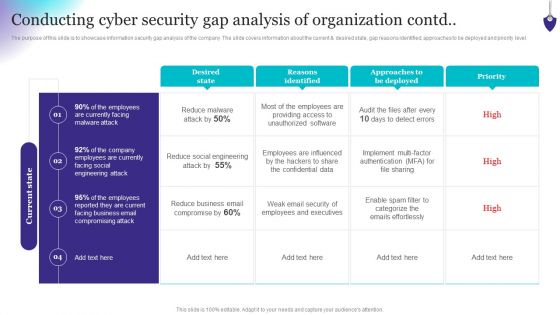
Organizing Security Awareness Conducting Cyber Security Gap Analysis Of Organization Contd Portrait PDF
The purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. There are so many reasons you need a Organizing Security Awareness Conducting Cyber Security Gap Analysis Of Organization Contd Portrait PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
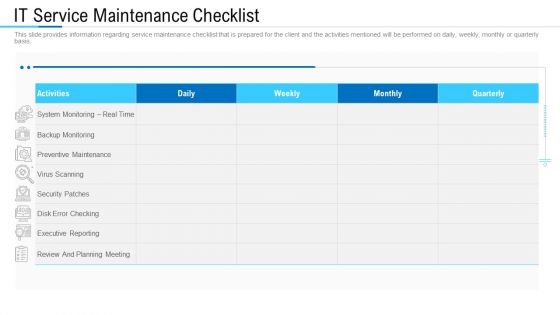
Information Technology Facility Flow Administration IT Service Maintenance Checklist Inspiration PDF
This slide provides information regarding service maintenance checklist that is prepared for the client and the activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this information technology facility flow administration it service maintenance checklist inspiration pdf. Use them to share invaluable insights on review and planning meeting, monitoring, security patches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Based Procedures To IT Security Information Security Program Framework Key Components Themes PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. This is a Risk Based Procedures To IT Security Information Security Program Framework Key Components Themes PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Context Leadership, Evaluation Direction, Change Support. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Various Data Security Threats That Might Affect Your Business Ppt PowerPoint Presentation Professional Information PDF
Persuade your audience using this various data security threats that might affect your business ppt powerpoint presentation professional information pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including data compliance, data corruption, dark data risk, data remanence. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cloud Security Assessment How Does Cloud Security Work Data Security Diagrams PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan.Presenting Cloud Security Assessment How Does Cloud Security Work Data Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Impact Analysis, Recovery Strategies, Plan Development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
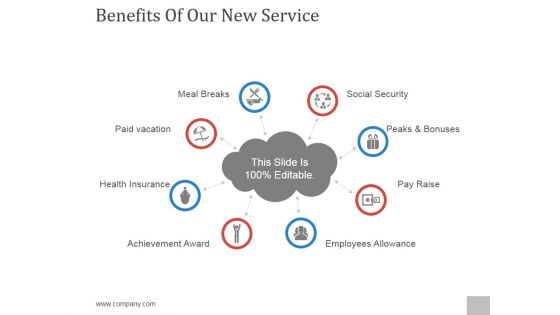
Benefits Of Our New Service Ppt PowerPoint Presentation Slide Download
This is a benefits of our new service ppt powerpoint presentation slide download. This is a eight stage process. The stages in this process are social security, peaks and bonuses, pay raise, employees allowance, achievement award, health insurance, paid vacation, meal breaks.
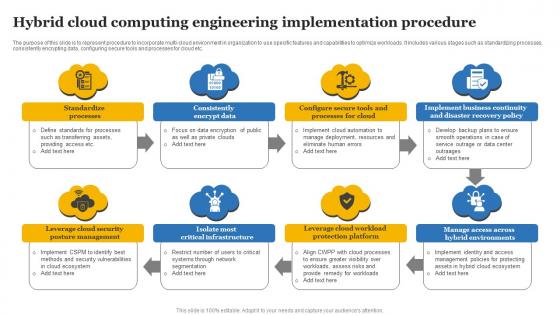
Hybrid Cloud Computing Engineering Implementation Procedure Designs Pdf
The purpose of this slide is to represent procedure to incorporate multi-cloud environment in organization to use specific features and capabilities to optimize workloads. It includes various stages such as standardizing processes, consistently encrypting data, configuring secure tools and processes for cloud etc. Showcasing this set of slides titled Hybrid Cloud Computing Engineering Implementation Procedure Designs Pdf The topics addressed in these templates are Standardize Processes, Consistently Encrypt Data, Business Continuity All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Circular Chart 9 Distinct Views On Single Issue Charts And Networks PowerPoint Templates
We present our circular chart 9 distinct views on single issue Charts and Networks PowerPoint templates.Present our Circle Charts PowerPoint Templates because analyse your plans with equal sincerity. Use our Arrows PowerPoint Templates because the structure of our templates allows you to effectively highlight the key issues concerning the growth of your business. Use our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Download our Shapes PowerPoint Templates because you should explain the process by which you intend to right it. Download our Flow Charts PowerPoint Templates because the great Bald headed Eagle embodies your personality. the eagle eye to seize upon the smallest of oppurtunities.Use these PowerPoint slides for presentations relating to abstract, arrow, art, background, ball, blue, business, button, chart, circle, circular, clip, company, concept, cycle, diagram, edit, editable, element, green, guide, icon, leader, management, marketing, model, numbers, organization, plans, point, presentation, purple, red, report, representation, seven, sphere, stakeholder, team, text, tool, vector, white. The prominent colors used in the PowerPoint template are Purple, Green, Yellow. Customers tell us our circular chart 9 distinct views on single issue Charts and Networks PowerPoint templates are Charming. PowerPoint presentation experts tell us our ball PowerPoint templates and PPT Slides are Dazzling. People tell us our circular chart 9 distinct views on single issue Charts and Networks PowerPoint templates are Magical. People tell us our blue PowerPoint templates and PPT Slides will impress their bosses and teams. Customers tell us our circular chart 9 distinct views on single issue Charts and Networks PowerPoint templates are Graceful. People tell us our chart PowerPoint templates and PPT Slides are Dynamic.

CIO Role In Digital Evolution Role Of Chief Information Security Officer Infographics PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc. Presenting CIO Role In Digital Evolution Role Of Chief Information Security Officer Infographics PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Dependable Business, Security Information, Team Members. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Winning Strategies To Improve Organization Data Security Pictures PDF
The following slide highlights a winning strategy to avoid data security breach in the organization. Businesses can protect the confidential data by following strategies such as security audit, establishing strong password, back up sensitive data, and improve cyber-security. Presenting Winning Strategies To Improve Organization Data Security Pictures PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Audit, Establish Strong, Sensitive Data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
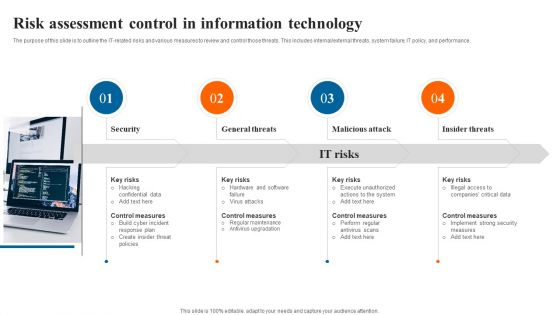
Risk Assessment Control In Information Technology Download PDF
The purpose of this slide is to outline the IT related risks and various measures to review and control those threats. This includes internal or external threats, system failure, IT policy, and performance. Presenting Risk Assessment Control In Information Technology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including General Threats, Malicious Attack, Insider Threats, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
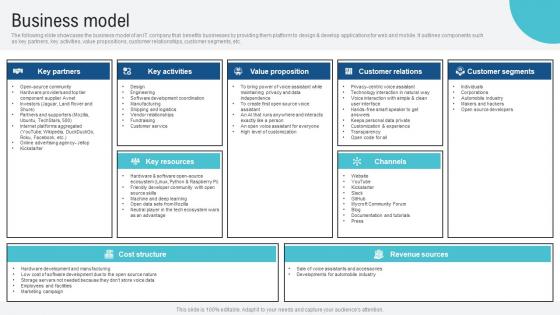
Business Model Voice Assistance Security Platform Investor Funding Presentation Guidelines Pdf
The following slide showcases the business model of an IT company that benefits businesses by providing them platform to design and develop applications for web and mobile. It outlines components such as key partners, key activities, value propositions, customer relationships, customer segments, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Business Model Voice Assistance Security Platform Investor Funding Presentation Guidelines Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Food Ingredient Adulteration Vulnerability Prevention Strategy Information Pdf
This slide provide information about food ingredient fraud vulnerability mitigation plan to protect organization image. It includes elements such as facility security, building security and security assessments Showcasing this set of slides titled Food Ingredient Adulteration Vulnerability Prevention Strategy Information Pdf. The topics addressed in these templates are Security Assessments, Building Security, Facility Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Regulatory Compliance Report Security Dashboard With Gateways Information PDF
This slide shows the dashboard depicting regulatory compliance report. It covers information about monitoring practices, gateways, blades with review percentage such as secure, good, medium and poor. Showcasing this set of slides titled Regulatory Compliance Report Security Dashboard With Gateways Information PDF. The topics addressed in these templates are Regulatory Compliance Report Security, Dashboard With Gateways. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
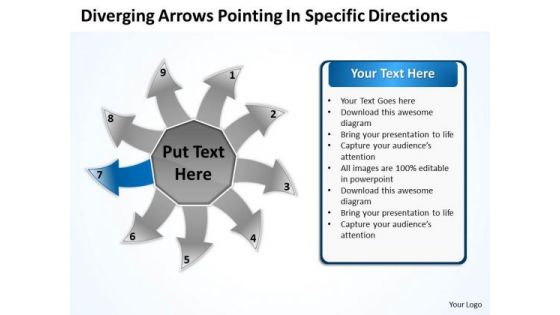
Diverging Arrows Pointing Specific Directions Cycle Process PowerPoint Slide
We present our diverging arrows pointing specific directions Cycle Process PowerPoint Slide.Use our Communication PowerPoint Templates because you have the moves to sway the market. Download our Arrows PowerPoint Templates because readymade PowerPoint templates can prove best of your knowledge for your slides to show. Download our Circle Charts PowerPoint Templates because your business and plans for its growth consist of processes that are highly co-related. Use our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Present our Shapes PowerPoint Templates because you can Explore the various hues and layers existing in your in your plans and processes using this slide.Use these PowerPoint slides for presentations relating to Arrow, Bio, Business, Chart, Circle, Concept, Control, Cycle, Design, Development, Diagram, Eco, Ecology, Environmental, Evaluate, Flow, Flowchart, Fresh, Graphic, Green, Idea, Infographic, Iterative, Life, Lifecycle, Management, Method, Model, Natural, Nature, Organic, Process, Quality, Recycle, Research, Schema, Spiral, Step, Strategy, Success, System. The prominent colors used in the PowerPoint template are Blue, Gray, White. Customers tell us our diverging arrows pointing specific directions Cycle Process PowerPoint Slide are Reminiscent. Customers tell us our Design PowerPoint templates and PPT Slides are incredible easy to use. Presenters tell us our diverging arrows pointing specific directions Cycle Process PowerPoint Slide are Fancy. PowerPoint presentation experts tell us our Cycle PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Customers tell us our diverging arrows pointing specific directions Cycle Process PowerPoint Slide are Radiant. Professionals tell us our Business PowerPoint templates and PPT Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire.

Major Target Areas Of Virtual Security Hazards Summary Pdf
The following slide consists of major target points of cyber security attacks aimed at accessing, changing, or destroying sensitive information extorting money from users or interrupting normal business processes. The major targets are electronic devices, critical information, financial resources and public opinion Pitch your topic with ease and precision using this Major Target Areas Of Virtual Security Hazards Summary Pdf. This layout presents information on Financial Resources, Public Opinion, Electronic Devices. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
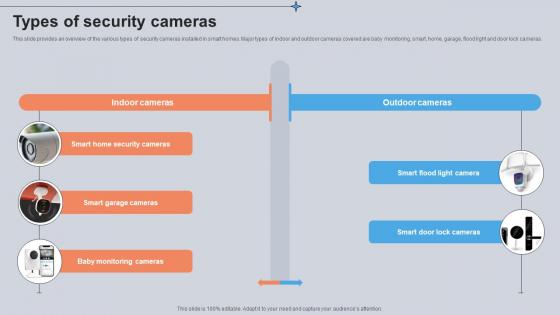
Types Of Security Cameras Utilizing Smart Appliances IoT SS V
This slide provides an overview of the various types of security cameras installed in smart homes. Major types of indoor and outdoor cameras covered are baby monitoring, smart, home, garage, flood light and door lock cameras. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Types Of Security Cameras Utilizing Smart Appliances IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Types Of Security Cameras Utilizing Smart Appliances IoT SS V today and make your presentation stand out from the rest

Cybersecurity Compliance Dashboard Of Electronic Information Security Ppt Outline Graphic Tips PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative cybersecurity compliance dashboard of electronic information security ppt outline graphic tips pdf bundle. Topics like compliance dashboard of electronic information security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
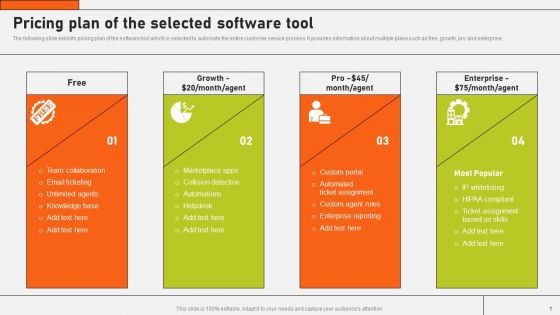
Securing Market Leadership Through Competitive Excellence Pricing Plan Of The Selected Software Tool Themes PDF
The following slide exhibits pricing plan of the software tool which is selected to automate the entire customer service process. It provides information about multiple plans such as free, growth, pro and enterprise. Slidegeeks is here to make your presentations a breeze with Securing Market Leadership Through Competitive Excellence Pricing Plan Of The Selected Software Tool Themes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

 Home
Home