Safety Management
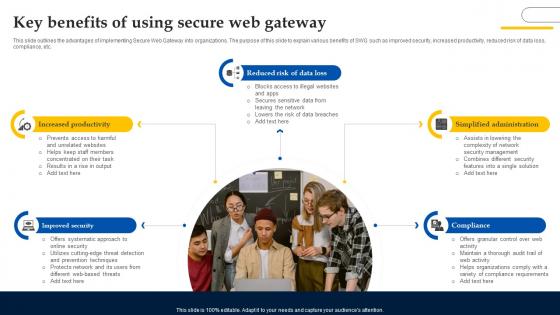
Web Access Control Solution Key Benefits Of Using Secure Web Gateway
This slide outlines the advantages of implementing Secure Web Gateway into organizations. The purpose of this slide to explain various benefits of SWG such as improved security, increased productivity, reduced risk of data loss, compliance, etc. Slidegeeks has constructed Web Access Control Solution Key Benefits Of Using Secure Web Gateway after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Web Access Control Solution Estimated Budget Of Secure Web Gateway
This slide represents the budget of integrating Secure Web Gateway in organization. The purpose of this slide is to showcase the estimated and actual cost for installing SWG. These include hardware and software, maintenance and support, training, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Web Access Control Solution Estimated Budget Of Secure Web Gateway was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Web Access Control Solution Estimated Budget Of Secure Web Gateway.

Web Access Control Solution Different Types Of Secure Web Gateway Deployment
This slide demonstrates the various kinds of SWG deployments. The purpose of this slide is to explain the different types of Secure Web Gateway deployment methods such as on-premises deployment, cloud-based deployment and hybrid deployment. Make sure to capture your audiences attention in your business displays with our gratis customizable Web Access Control Solution Different Types Of Secure Web Gateway Deployment. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Best Frameworks For Cybersecurity In Medical Industry Guidelines Pdf
This slide presents best cybersecurity frameworks helpful in allowing external and internal stakeholders to understand and manage network security together as team. It includes NIST, HITRUST, Critical security controls and ISO 27000 series Showcasing this set of slides titled Best Frameworks For Cybersecurity In Medical Industry Guidelines Pdf. The topics addressed in these templates are Frameworks, Description, Adoption Percentage. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
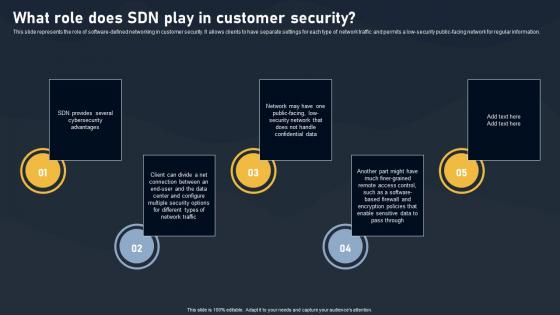
What Role Does SDN Play In Customer Security SDN Building Blocks Topics Pdf
This slide represents the role of software-defined networking in customer security. It allows clients to have separate settings for each type of network traffic and permits a low-security public-facing network for regular information.This modern and well-arranged What Role Does SDN Play In Customer Security SDN Building Blocks Topics Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Estimated Budget Of Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc. This Estimated Budget Of Cloud Data Security Using Cryptography Brochure Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Retail Store Operations Retail Store Administration Operational Challenges Mockup PDF
This slide represents the major challenges associated with successful retail store administrations such as staff time keeping, managing store cleanliness, proper cash handling, ensuring premises security. Present like a pro with Retail Store Operations Retail Store Administration Operational Challenges Mockup PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
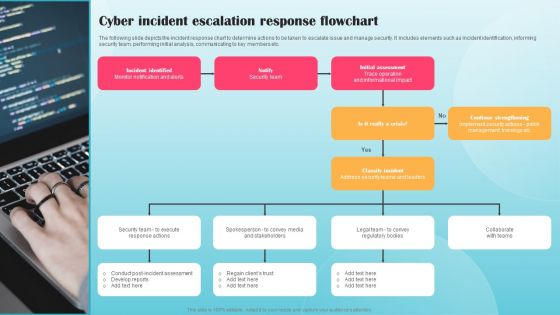
Cyber Incident Escalation Response Flowchart Ppt PowerPoint Presentation File Infographic Template PDF
The following slide depicts the incident response chart to determine actions to be taken to escalate issue and manage security. It includes elements such as incident identification, informing security team, performing initial analysis, communicating to key members etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Incident Escalation Response Flowchart Ppt PowerPoint Presentation File Infographic Template PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Building Trust With IoT Security Edge Computing Role In Securing IoT Data IoT SS V
This slide showcases the significant role of edge computing in enhancing IoT data security and privacy. It include role such as data filtering and processing, localised threat identification, and reduce attack surface. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Building Trust With IoT Security Edge Computing Role In Securing IoT Data IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Measures And Ways To Mitigate Template PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks measures and ways to mitigate template pdf. Use them to share invaluable insights on malware attacks, pnishing attacks, ransomware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
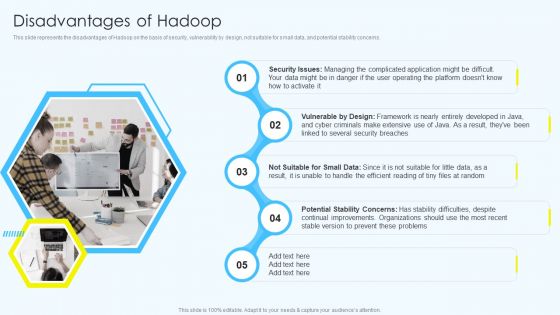
Apache Hadoop Software Deployment Disadvantages Of Hadoop Structure PDF
This slide represents the disadvantages of Hadoop on the basis of security, vulnerability by design, not suitable for small data, and potential stability concerns.This is a Apache Hadoop Software Deployment Disadvantages Of Hadoop Structure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Managing Complicated, Security Breaches, Potential Stability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategic Cyber Assessment And Assurance Model Microsoft PDF
The following slide illustrates cyber assessment framework aimed at analysing the extent to which cyber risks from functions are being managed by organisations. It covers roles and responsibilities under NIS objectives and principles. Showcasing this set of slides titled Strategic Cyber Assessment And Assurance Model Microsoft PDF. The topics addressed in these templates are Security Cases, System Security, Network And Systems. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
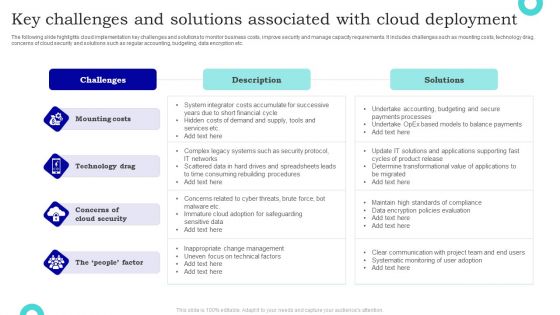
Key Challenges And Solutions Associated With Cloud Deployment Introduction PDF
The following slide highlights cloud implementation key challenges and solutions to monitor business costs, improve security and manage capacity requirements. It includes challenges such as mounting costs, technology drag, concerns of cloud security and solutions such as regular accounting, budgeting, data encryption etc. Pitch your topic with ease and precision using this Key Challenges And Solutions Associated With Cloud Deployment Introduction PDF. This layout presents information on Challenges, Description, Solutions. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Web Access Control Solution Secure Web Gateway Set Up Configuration And Implementation
This slide represents the procedure for implementing Secure Web Gateway in network. The purpose of this slide is to explain the configuration and implementation phase of SWG set-up. The key points included are configure web gateway software, establish security policies, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Web Access Control Solution Secure Web Gateway Set Up Configuration And Implementation will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Enhancing Hospital Software System Challenges Faced By Healthcare Administrators Clipart PDF
This slide focuses on challenges faced by healthcare administrators which covers rising costs, hiring top nursing talent, security issues, managing large amount of data, payment processing, etc. Presenting enhancing hospital software system challenges faced by healthcare administrators clipart pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like challenges faced by healthcare administrators. In addition, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Business Flow Diagram Example 3d Men With Group Of People Under Black Umbrella PowerPoint Slides
We present our business flow diagram example 3d men with group of people under black umbrella PowerPoint Slides.Download our Leadership PowerPoint Templates because Our PowerPoint Templates and Slides are created with admirable insight. Use them and give your group a sense of your logical mind. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides will effectively help you save your valuable time. They are readymade to fit into any presentation structure. Download and present our Umbrellas PowerPoint Templates because Our PowerPoint Templates and Slides come in all colours, shades and hues. They help highlight every nuance of your views. Use our Shapes PowerPoint Templates because You have gained great respect for your brilliant ideas. Use our PowerPoint Templates and Slides to strengthen and enhance your reputation. Present our People PowerPoint Templates because You can Inspire your team with our PowerPoint Templates and Slides. Let the force of your ideas flow into their minds.Use these PowerPoint slides for presentations relating to 3d, Adult, Black, Briefcase, Business, Businessman, Concept, Cooperation, Corporate, Cover, Elegant, Executive, Formal, Friend, Friendship, Group, Guy, Hand, Holding, Human, Icon, Idea, Lifestyle, Manager, Men, Metaphor, Partner, Partnership, People, Person, Professional, Protect, Protection, Rain, Safety, Security, Shielding, Standing, Suitcase, Team, Teamwork, Tie, Together, Umbrella, Under, Wait, Weather. The prominent colors used in the PowerPoint template are White, Gray, Black. The feedback we get is that our business flow diagram example 3d men with group of people under black umbrella PowerPoint Slides have awesome images to get your point across. Customers tell us our Black PowerPoint templates and PPT Slides have awesome images to get your point across. The feedback we get is that our business flow diagram example 3d men with group of people under black umbrella PowerPoint Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Professionals tell us our Concept PowerPoint templates and PPT Slides are visually appealing. Presenters tell us our business flow diagram example 3d men with group of people under black umbrella PowerPoint Slides will get their audience's attention. You can be sure our Cooperation PowerPoint templates and PPT Slides are visually appealing.

Web Access Control Solution Checklist To Implement Secure Web Gateway
This slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Web Access Control Solution Checklist To Implement Secure Web Gateway and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
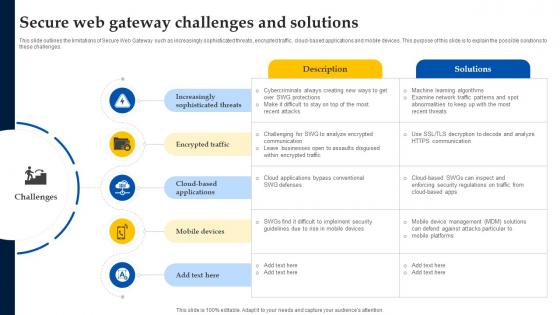
Web Access Control Solution Secure Web Gateway Challenges And Solutions
This slide outlines the limitations of Secure Web Gateway such as increasingly sophisticated threats, encrypted traffic, cloud-based applications and mobile devices. This purpose of this slide is to explain the possible solutions to these challenges. Want to ace your presentation in front of a live audience Our Web Access Control Solution Secure Web Gateway Challenges And Solutions can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Business Application Threat Modeling Procedure Designs PDF
This slide contains application threat modeling process to evaluate and manage risks. It includes four steps identify fundamentals, data flow, security profile and recommendations. Persuade your audience using this Business Application Threat Modeling Procedure Designs PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Examine Existing, Understand Capabilities, Recommendations. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Machine To Machine Communication Outline Iot Best Practices Ppt Inspiration Model PDF
The slide highlights the best IoT practices which companies should follow. This is a machine to machine communication outline iot best practices ppt inspiration model pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like understand your endpoints, track and manage your devices, identify what it security cannot address, consider patching and remediation, use a risk driven strategy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Web Access Control Solution Secure Web Gateway Training Program
This slide represents the training program for the Secure Web Gateway. The main components of training program are agenda, system requirements, mode such as online, offline or recorded videos, and cost. Slidegeeks is here to make your presentations a breeze with Web Access Control Solution Secure Web Gateway Training Program With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first

Cloud Security Assessment Roadmap Of Cloud Security Implementation Information PDF
This slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January.Presenting Cloud Security Assessment Roadmap Of Cloud Security Implementation Information PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Configuration Management, Services Management, Security Measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Auditing And Corporate Governance With Legal Structure Ppt PowerPoint Presentation Icon Infographic Template PDF
This slide shows the relationship between corporate governance and internal audit committee which includes legal framework, managing improvements, information security, transparency, planning, implementing, reporting, evaluating, etc. Persuade your audience using this auditing and corporate governance with legal structure ppt powerpoint presentation icon infographic template pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including accountability, evaluation, implementation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Reverse Proxy Server IT What Is A Proxy Server Ppt Infographics Infographics PDF
This slide depicts the meaning of proxy servers, where it is used, and how it manages traffic based on pre-defined policies and blocks the unknown traffic. This is a reverse proxy server it what is a proxy server ppt infographics infographics pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network, unfamiliar traffic, enforce security protocols, controls traffic based. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Web Access Control Solution Impact Of Secure Web Gateway On Application Security
This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Welcome to our selection of the Web Access Control Solution Impact Of Secure Web Gateway On Application Security. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Critical Challenges Related To Data Lake Ppt PowerPoint Presentation Diagram Lists PDF
This slide depicts the challenges of data lakes such as high cost, managed difficulty, long time to value, immature data security and governance, and lack of skills. Make sure to capture your audiences attention in your business displays with our gratis customizable Critical Challenges Related To Data Lake Ppt PowerPoint Presentation Diagram Lists PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Data Lake Implementation Critical Challenges Related To Data Lake Mockup PDF
This slide depicts the challenges of data lakes such as high cost, managed difficulty, long time-to-value, immature data security and governance, and lack of skills. Present like a pro with Data Lake Implementation Critical Challenges Related To Data Lake Mockup PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Google Cloud Features For Disaster Recovery Plan Google Cloud Computing System Summary PDF
This slide represents the Google cloud features of the disaster recovery plan, and it includes global network, redundancy, scalability, security, and compliance.Presenting Google Cloud Features For Disaster Recovery Plan Google Cloud Computing System Summary PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Virtualization, Networking, Managed Customer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Emotional Marketing Strategy To Nurture Key Strategies For Brands To Empower Customers Icons PDF
This slide showcases major branding techniques to empower customers which can assist managers in retaining them for long run. It provides details such as technology, support desk, security, feedback, compliance, etc. Take your projects to the next level with our ultimate collection of Emotional Marketing Strategy To Nurture Key Strategies For Brands To Empower Customers Icons PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.
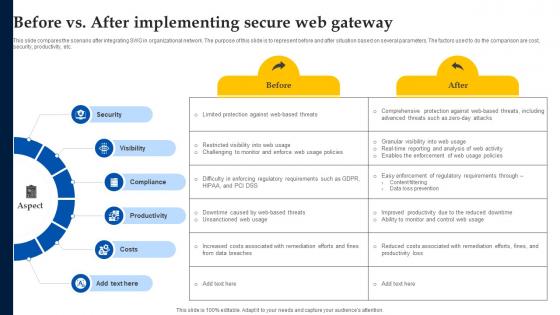
Web Access Control Solution Before Vs After Implementing Secure Web Gateway
This slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Web Access Control Solution Before Vs After Implementing Secure Web Gateway. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Web Access Control Solution Before Vs After Implementing Secure Web Gateway today and make your presentation stand out from the rest

Table Of Contents Building Trust With IoT Security And Privacy Measures IoT SS V
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Table Of Contents Building Trust With IoT Security And Privacy Measures IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
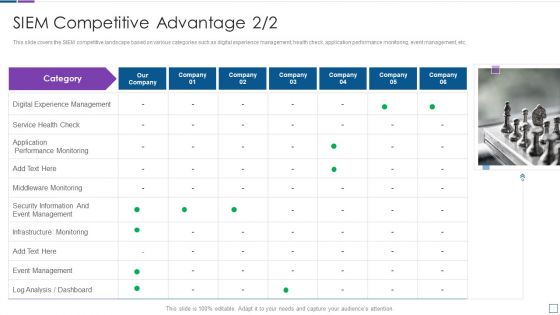
Real Time Assessment Of Security Threats SIEM Competitive Advantage Service Structure PDF
This slide covers the SIEM competitive landscape based on various categories such as digital experience management, health check, application performance monitoring, event management, etc. Presenting real time assessment of security threats siem competitive advantage service structure pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like digital experience management, service health check, application performance monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
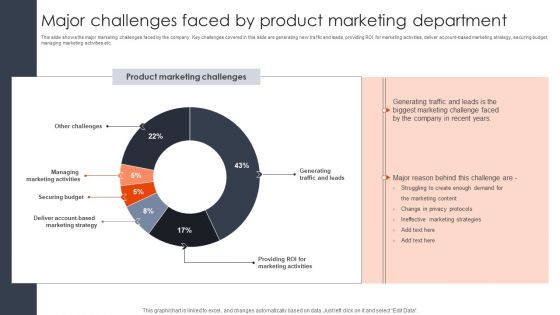
Major Challenges Faced By Product Marketing Department Client Acquisition Techniques To Boost Sales Designs PDF
This slide shows the major marketing challenges faced by the company. Key challenges covered in this slide are generating new traffic and leads, providing ROI for marketing activities, deliver account based marketing strategy, securing budget, managing marketing activities etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Major Challenges Faced By Product Marketing Department Client Acquisition Techniques To Boost Sales Designs PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Checklist To Implement Digital Twin Digital Twins For Enhanced Industrial Infographics Pdf
This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team. Present like a pro with Checklist To Implement Digital Twin Digital Twins For Enhanced Industrial Infographics Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
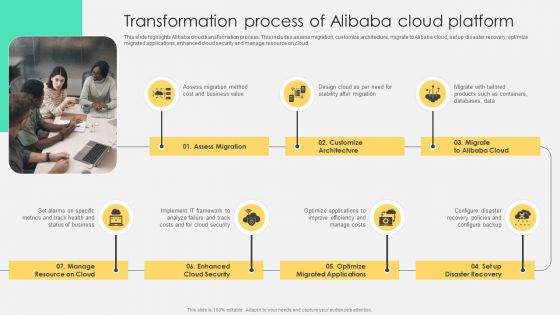
Transformation Process Of Alibaba Cloud Platform Introduction PDF
This slide highlights Alibaba cloud transformation process. This includes assess migration, customize architecture, migrate to Alibaba cloud, set up disaster recovery, optimize migrated applications, enhanced cloud security and manage resource on cloud. Find a pre-designed and impeccable Transformation Process Of Alibaba Cloud Platform Introduction PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
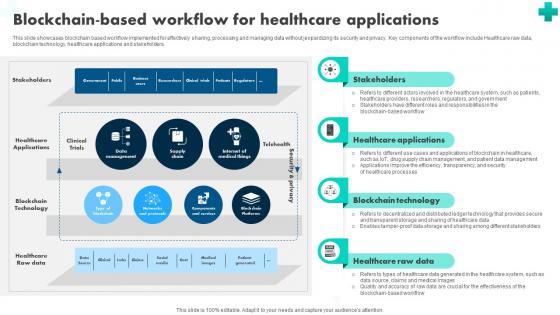
A56 How Blockchain Is Reshaping Blockchain Based Workflow For Healthcare BCT SS V
This slide showcases blockchain based workflow implemented for effectively sharing, processing and managing data without jeopardizing its security and privacy. Key components of the workflow include Healthcare raw data, blockchain technology, healthcare applications and stakeholders. Want to ace your presentation in front of a live audience Our A56 How Blockchain Is Reshaping Blockchain Based Workflow For Healthcare BCT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
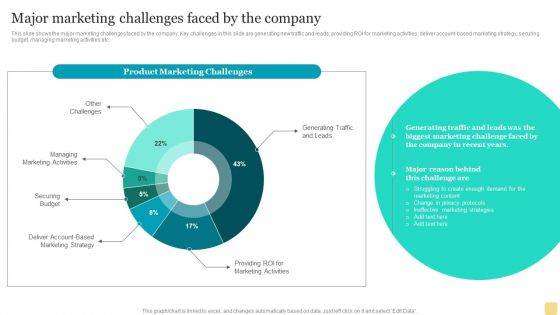
Product Marketing Plan To Enhance Organizational Growth Major Marketing Challenges Faced By The Company Topics PDF
This slide shows the major marketing challenges faced by the company. Key challenges in this slide are generating new traffic and leads, providing ROI for marketing activities, deliver account-based marketing strategy, securing budget, managing marketing activities etc.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Product Marketing Plan To Enhance Organizational Growth Major Marketing Challenges Faced By The Company Topics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Cybersecurity Monitoring Plan Steps In Detail Providing Resilient And Synchronized Timing Background PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this cybersecurity monitoring plan steps in detail providing resilient and synchronized timing background pdf. Use them to share invaluable insights on monitoring and analysis, incident response, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
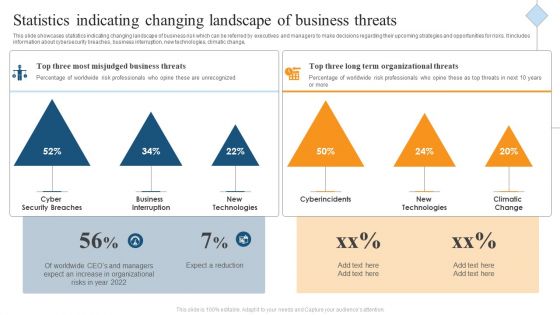
Statistics Indicating Changing Landscape Of Business Threats Ppt Model Design Templates PDF
This slide showcases statistics indicating changing landscape of business risk which can be referred by executives and managers to make decisions regarding their upcoming strategies and opportunities for risks. It includes information about cybersecurity breaches, business interruption, new technologies, climatic change, Persuade your audience using this Statistics Indicating Changing Landscape Of Business Threats Ppt Model Design Templates PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Breaches, Business Interruption, New Technologies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
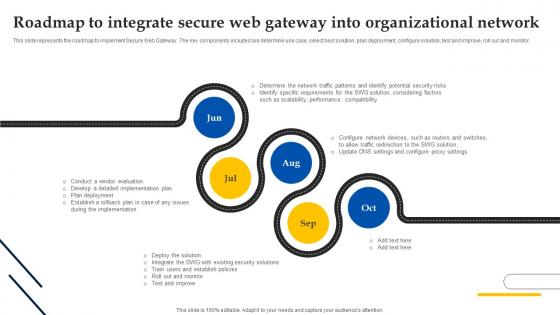
Web Access Control Solution Roadmap To Integrate Secure Web Gateway Into Organizational Network
This slide represents the roadmap to implement Secure Web Gateway. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Create an editable Web Access Control Solution Roadmap To Integrate Secure Web Gateway Into Organizational Network that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Web Access Control Solution Roadmap To Integrate Secure Web Gateway Into Organizational Network is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Information Technology Governance Example Ppt Presentation Slides
This is a information technology governance example ppt presentation slides. This is a three stage process. The stages in this process are computer audit, it governance, it risk management, information security management.

Business Project Planning Of Real Estate Venture Ppt PowerPoint Presentation Gallery Visual Aids PDF
This slide shows the work breakdown structure for managing real estate project which includes flats, testing and inspecting, operations, etc. With foundations, electrical, plumbing, ventilation, sales and marketing, insurance, security, etc. Presenting business project planning of real estate venture ppt powerpoint presentation gallery visual aids pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including flats, test and inspect, operations. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Product Kick Off Strategy Product Launch Timeline Ppt Model Background Images PDF
This slide shows timeline to help manage planning of launch event. Task lead time is relative to the date of launch event. Presenting product kick off strategy product launch timeline ppt model background images pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like develop, social media, plan, secure venue. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Go To Market Strategy For New Product Product Launch Timeline Designs PDF
This slide shows timeline to help manage planning of launch event. Task lead time is relative to the date of launch event. This is a go to market strategy for new product product launch timeline designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like develop, social media, plan, secure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Analysis Brochure PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Review and Risk Analysis. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring analysis brochure pdf bundle. Topics like cybersecurity monitoring plan steps in detail review and risk analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Timing Clipart PDF
This slide provides information about the seventh step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Providing Resilient and Synchronized Timing. Deliver and pitch your topic in the best possible manner with this continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring timing clipart pdf. Use them to share invaluable insights on cybersecurity monitoring plan steps in detail providing resilient and synchronized timing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
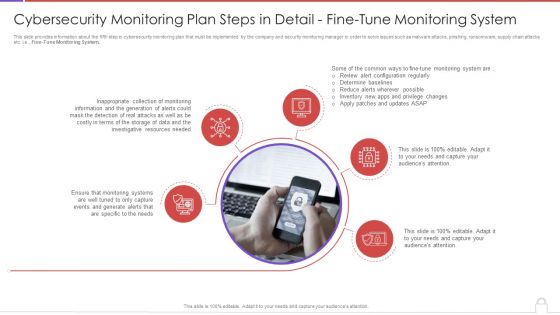
Cybersecurity Monitoring Plan Steps In Detail Fine Tune Monitoring System Slides PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Fine-Tune Monitoring System. Presenting cybersecurity monitoring plan steps in detail fine tune monitoring system slides pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like inappropriate collection, monitoring information, investigative resources needed. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Monitoring Plan Steps In Detail Monitoring All Systems Introduction PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Deliver an awe inspiring pitch with this creative cybersecurity monitoring plan steps in detail monitoring all systems introduction pdf bundle. Topics like system network category, monitoring done can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Monitoring Plan Steps In Detail Monitoring Network Traffic Summary PDF
This slide provides information about the third step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring Network Traffic. Presenting cybersecurity monitoring plan steps in detail monitoring network traffic summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like inbound and outbound traffic, could indicate attacks, unusual network traffic. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
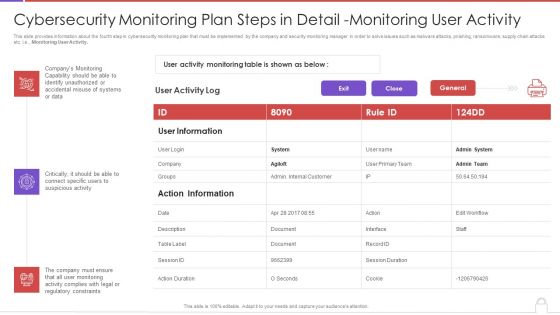
Cybersecurity Monitoring Plan Steps In Detail Monitoring User Activity Guidelines PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring User Activity. Deliver an awe inspiring pitch with this creative cybersecurity monitoring plan steps in detail monitoring user activity guidelines pdf bundle. Topics like action information, user information, monitoring capability can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Methods To Develop Cybersecurity Monitoring Plan Steps In Detail Review And Risk Analysis Structure PDF
This slide provides information about the ninth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, punishing, ransomware, supply chain attacks etc. i.e., Review and Risk Analysis. Deliver an awe inspiring pitch with this creative methods to develop cybersecurity monitoring plan steps in detail review and risk analysis structure pdf bundle. Topics like potential consequence, low, medium, high can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Infrastructure Supervision Time Spent On Monitoring IT Infrastructure Demonstration PDF
This slide covers the time spend in monitoring the IT infrastructure such as extracting and analyzing logs, interpreting reports and alerts, managing tools and agents, etc. Deliver and pitch your topic in the best possible manner with this Infrastructure Supervision Time Spent On Monitoring IT Infrastructure Demonstration PDF. Use them to share invaluable insights on Virtual, Cloud Platforms, Security Infrastructure, Systems Software Components, Hardware Systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Digital Twin Tech IT Checklist To Implement Digital Twin Technology Summary PDF
This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Digital Twin Tech IT Checklist To Implement Digital Twin Technology Summary PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Various Aspects And Steps Of Software Test Scenarios Formats PDF
This slide shows types of software test scenarios that helps to measure and manage different aspects. It contains test scenario types components, security, usability with details, steps, expected outcomes and status.Showcasing this set of slides titled Various Aspects And Steps Of Software Test Scenarios Formats PDF. The topics addressed in these templates are Expected Outcomes, Characters Requests, Assure Provided. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Project Tracking Risk Tracker Matrix Themes PDF
The following slide depicts the risk assessment matrix of project tracking to manage uncertain activities and improve decision making. It includes activities such as assessment, configuration, advancement, security check and dispose etc. Persuade your audience using this Project Tracking Risk Tracker Matrix Themes PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Project Tracking Risk, Tracker Matrix. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Implementing Effective Ecommerce Managemnet Platform Challenges Faced By Ecommerce Marketing Topics PDF
This slide represents the hurdles and business challenges faced by marketing manager of ABC ecommerce firm in the current scenario. It includes business challenges such as customers exploding expectations, agility, data security, customer retention and omni-channel experience. There are so many reasons you need a Implementing Effective Ecommerce Managemnet Platform Challenges Faced By Ecommerce Marketing Topics PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Physical Fitness Program Budget Plan For Small Business Guidelines PDF
Following slide provide insight about budget plan which can be used by small firms for managing organisation finance. It includes key components such as expense category, estimated budget, actual cost, variance and variance percentage. Showcasing this set of slides titled Physical Fitness Program Budget Plan For Small Business Guidelines PDF. The topics addressed in these templates are Revenue, Expenses, Event Security . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
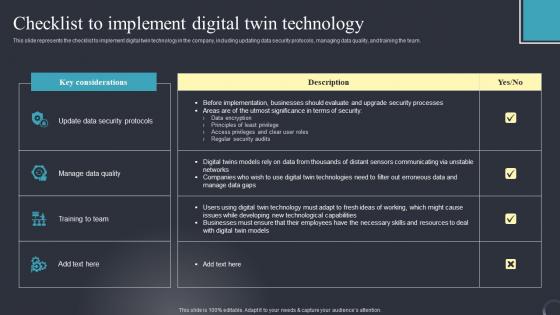
Checklist To Implement Digital Industrial Transformation Using Digital Twin Elements Pdf
This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Checklist To Implement Digital Industrial Transformation Using Digital Twin Elements Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Strategies For Navigating Growth Raising Venture Capital A Holistic Approach Fin SS V
This slide outlines key strategies for managing and sustaining growth, including expanding operations, entering new markets, and scaling the business effectively, helping companies chart a successful path forward after securing venture capital funding. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Strategies For Navigating Growth Raising Venture Capital A Holistic Approach Fin SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

 Home
Home