Safety Management

Successful Quality Assurance Transition Techniques To Enhance Product Quality Implement Code Quality Measurements Formats PDF
This slide shows the details about Code Quality Measurements Approach for Effective QA Transformation along with details on Software Quality Indicators and Test Metrics such as Reliability, Security, Testability, Rate of Delivery etc. This is a successful quality assurance transition techniques to enhance product quality implement code quality measurements formats pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reliability, performance efficiency, security, maintainability, rate of delivery. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Monetary Investment Portfolio Growth And Administration Role Of Bond In Portfolio Investment Growth Structure PDF Themes PDF
This slide represents role of bond in portfolio investment growth. It covers equities, bonds, average return, market volatility, portfolio risk etc. Deliver and pitch your topic in the best possible manner with this Monetary Investment Portfolio Growth And Administration Role Of Bond In Portfolio Investment Growth Structure PDF Themes PDF. Use them to share invaluable insights on Low Risk, Securities, Income Generating and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

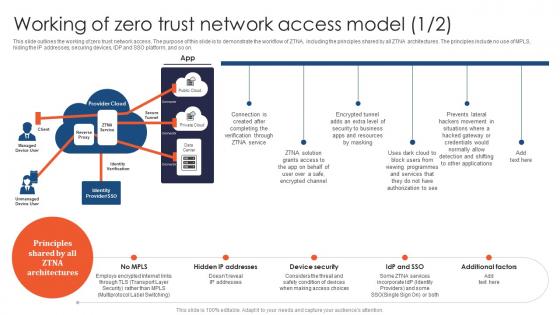
Zero Trust Model Working Of Zero Trust Network Access Model
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Model Working Of Zero Trust Network Access Model to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Our Solution Email And Data Protection Platform Capital Funding Pitch Deck PPT Sample
This slide covers key solutions provided by email security application for the problems faced by customers. It includes an email filtering service, secure file sharing, and HIPAA-compliant email encryption. Make sure to capture your audiences attention in your business displays with our gratis customizable Our Solution Email And Data Protection Platform Capital Funding Pitch Deck PPT Sample. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
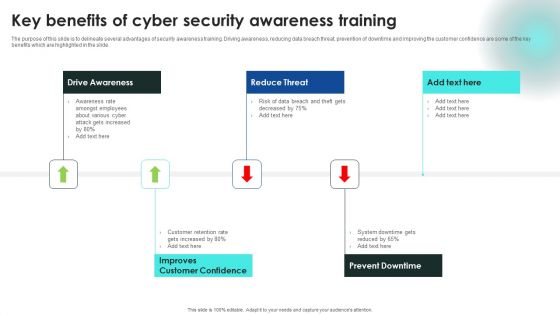
Implementing Cybersecurity Awareness Program To Prevent Attacks Key Benefits Of Cyber Security Awareness Clipart PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Implementing Cybersecurity Awareness Program To Prevent Attacks Key Benefits Of Cyber Security Awareness Clipart PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Implementing Cybersecurity Awareness Program To Prevent Attacks Key Benefits Of Cyber Security Awareness Clipart PDF

Transforming Manufacturing With Automation Role Of Cyber Security In Manufacturing Rules PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Find highly impressive Transforming Manufacturing With Automation Role Of Cyber Security In Manufacturing Rules PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Transforming Manufacturing With Automation Role Of Cyber Security In Manufacturing Rules PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
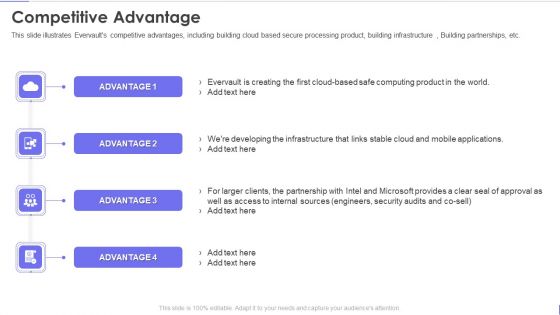
Evervault Capital Investment Elevator Pitch Deck Competitive Advantage Portrait PDF
This slide illustrates Evervaults competitive advantages, including building cloud based secure processing product, building infrastructure , Building partnerships, etc. This is a evervault capital investment elevator pitch deck competitive advantage portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like competitive advantage. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
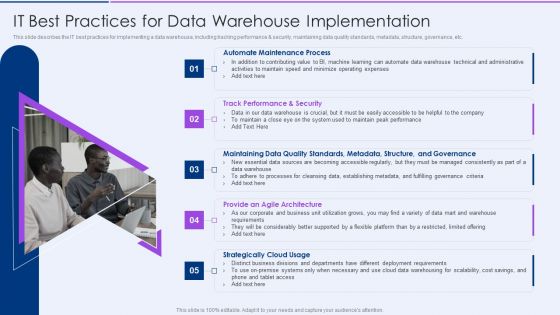
Executive Information Database System It Best Practices For Data Warehouse Implementation Sample PDF
This slide describes the IT best practices for implementing a data warehouse, including tracking performance security, maintaining data quality standards, metadata, structure, governance, etc.This is a Executive Information Database System It Best Practices For Data Warehouse Implementation Sample PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Automate Maintenance, Track Performance, Maintaining Data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
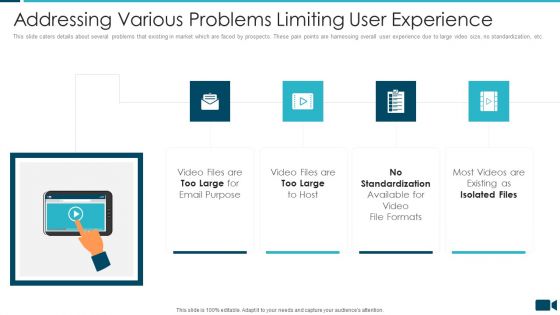
Secured Video Hosting Platform Investor Capital Funding Addressing Various Problems Limiting User Experience Topics PDF
This slide caters details about several problems that existing in market which are faced by prospects. These pain points are harnessing overall user experience due to large video size, no standardization, etc. This is a secured video hosting platform investor capital funding addressing various problems limiting user experience topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like addressing various problems limiting user experience. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
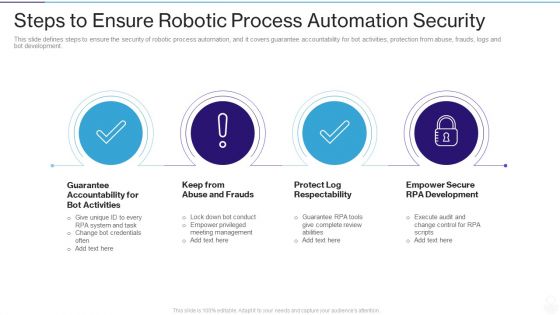
RPA IT Steps To Ensure Robotic Process Automation Security Ppt Layouts Layout Ideas PDF
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development. This is a rpa it steps to ensure robotic process automation security ppt layouts layout ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like guarantee accountability for bot activities, keep from abuse and frauds, protect log respectability, empower secure rpa development. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Manpower Corporate Security Business Profile Revenue By Customer Type Download PDF
This slide highlights the security company revenue by customer type which includes government, financial institutions, major corporate and industries, retail, transport, leisure and tourism. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Revenue By Customer Type Download PDF bundle. Topics like Revenue, Financial Institutions, Transport And Logistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Process Integration How Firm Handle Insider Threats Template PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a security and process integration how firm handle insider threats template pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Integrating Naas Service Model Naas As An Enabler For Cloud Transformation Ppt Gallery Graphics Pictures PDF
This slide talks about how NaaS works as a key driver for cloud transformation by providing secure and protected connectivity between businesses and their customers, internet of things devices with corporate applications, and so on. Retrieve professionally designed Integrating Naas Service Model Naas As An Enabler For Cloud Transformation Ppt Gallery Graphics Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Offshore Vs Outsourced Call Center Comparative Analysis Icons Pdf
The following slide highlights points like labor cost, service quality, communication, data security, time zone and customer feedback to show offshore vs onshore call center comparative analysis. It helps organization to make informed decision between offshore and onshore call center outsourcing based on important factors. Pitch your topic with ease and precision using this Offshore Vs Outsourced Call Center Comparative Analysis Icons Pdf. This layout presents information on Service Quality, Communication, Data Security, Customer Feedback. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF today and make your presentation stand out from the rest.

Determining The Suitable Software For Organization Ppt File Objects PDF
The slide provides the key features comparison of various software that will help the company to achieve its objective of process automation and data security Deliver and pitch your topic in the best possible manner with this determining the suitable software for organization ppt file objects pdf. Use them to share invaluable insights on improve productivity, process automation, data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Zero Trust Network Access Working Of Zero Trust Network Access Model
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Presenting this PowerPoint presentation, titled Zero Trust Network Access Working Of Zero Trust Network Access Model, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Working Of Zero Trust Network Access Model. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Working Of Zero Trust Network Access Model that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Cloud Data Repository Sync Process With Firewall And Security Brochure PDF
Presenting cloud data repository sync process with firewall and security brochure pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including synergy database server, scheduled cloud sync, firewall and security, synergy cloud data repository . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Four Step Process Of Digitization Of Security Systems Ppt Icon Show PDF
The following slide highlights multistep process of digitization of security systems. The company can detect security breach after following steps such as investigating the steps of IT analyst, determining responsive action, eradication and closing the ticked. Presenting Four Step Process Of Digitization Of Security Systems Ppt Icon Show PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Investigating Steps, Security Analysts, Determining Responsive Action. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Implementing Cyber Security Incident Comparative Analysis Of Web Application Microsoft PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. Boost your pitch with our creative Implementing Cyber Security Incident Comparative Analysis Of Web Application Microsoft PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
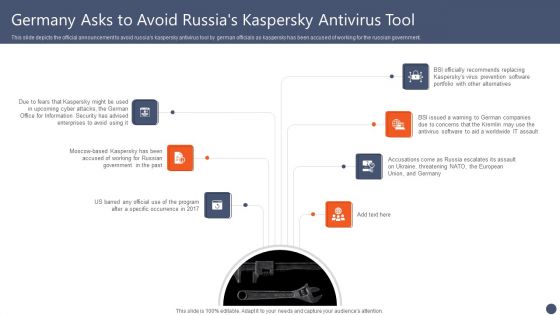
Series Of Cyber Security Attacks Against Ukraine 2022 Germany Asks To Avoid Russias Kaspersky Antivirus Tool Diagrams PDF
This slide depicts the official announcement to avoid russias kaspersky antivirus tool by german officials as kaspersky has been accused of working for the russian government. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Germany Asks To Avoid Russias Kaspersky Antivirus Tool Diagrams PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Germany Asks To Avoid Russias Kaspersky Antivirus Tool Diagrams PDF today and make your presentation stand out from the rest.

Information And Technology Security Operations Prerequisites For Effective Secops Implementation Designs PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a information and technology security operations prerequisites for effective secops implementation designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, data available, security with compliance, operations team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF
The following slide showcases some facts and figures to generate awareness about cyber-crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Awareness Facts And Statistics Ppt PowerPoint Presentation File Background Images PDF

Blockchain Security Solutions Deployment Phases To Perform Blockchain Penetration Graphics PDF
This slide highlights the main phases of blockchain penetration testing. The purpose of this slide is to showcase the different stages of penetration testing, including information gathering and threat modeling, testing and discovery, and exploitation. Find highly impressive Blockchain Security Solutions Deployment Phases To Perform Blockchain Penetration Graphics PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Blockchain Security Solutions Deployment Phases To Perform Blockchain Penetration Graphics PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Employee Engagement Model With Recognition And Security Ppt File Templates PDF
Persuade your audience using this employee engagement model with recognition and security ppt file templates pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including recognition, exciting work, security, education, conditions. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
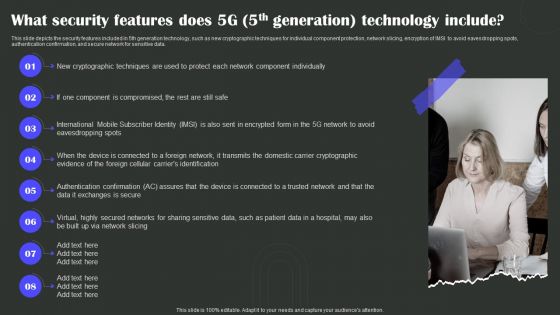
What Security Features Does 5G 5Th Generation Technology Include Wireless Technology Transformation Mockup PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Present like a pro with What Security Features Does 5G 5Th Generation Technology Include Wireless Technology Transformation Mockup PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Requirement Of IT Security IT In Different Sectors Ppt Inspiration Deck PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative requirement of it security it in different sectors ppt inspiration deck pdf bundle. Topics like corporate, financial, organizations, process, computers, servers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Rising Number Of Information Security Attacks Cybersecurity Risk Assessment Brochure PDF
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection. Boost your pitch with our creative Rising Number Of Information Security Attacks Cybersecurity Risk Assessment Brochure PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Post Implementation Challenges And Risks Of Saas Program Ppt PowerPoint Presentation File Graphics PDF
The following slide highlights the post implementation challenges and risks of SaaS platform illustrating key headings which includes control issues, version control, hard to switch and security issues. Presenting post implementation challenges and risks of saas program ppt powerpoint presentation file graphics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including control issues, version controls, hard to switch, security issues. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Policy And Processes Overview Of Network Security Policy For Workers Pictures PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Information Technology Policy And Processes Overview Of Network Security Policy For Workers Pictures PDF from Slidegeeks and deliver a wonderful presentation.
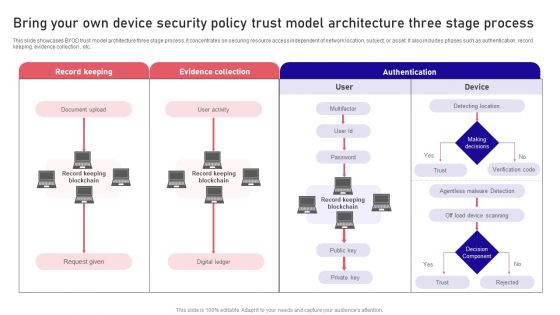
Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF
This slide showcases BYOD trust model architecture three stage process, it concentrates on securing resource access independent of network location, subject, or asset. It also includes phases such as authentication, record keeping. evidence collection , etc. Persuade your audience using this Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Record Keeping, Evidence Collection, Authentication . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Intelligent Architecture Growing Cyber Security Issues Ppt Professional Design Templates PDF
The slide provides the major cyber security issues Unprecedented Attacks, Cyber Espionage, and Data Theft along with the split of total information security incidents by the type of incident Deliver an awe inspiring pitch with this creative intelligent architecture growing cyber security issues ppt professional design templates pdf bundle. Topics like organizations, cyber security, business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cyber Security Testing Process With Icons Ppt PowerPoint Presentation Infographic Template Demonstration
Presenting this set of slides with name cyber security testing process with icons ppt powerpoint presentation infographic template demonstration. This is a five stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Five Steps Circular Process For Application Security Testing Ppt PowerPoint Presentation Styles Icon
Presenting this set of slides with name five steps circular process for application security testing ppt powerpoint presentation styles icon. This is a five stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Role And Responsibility Analysis For Technical Support Framework Download PDF
This slide explains various levels of client assistance for technical and IT problem resolution in organization to ensure constant compliance and security. It further includes details about client service desk, support engineers and developers. Presenting Role And Responsibility Analysis For Technical Support Framework Download PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Client Service Desk, Support Engineers, Developers, Test Engineers. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
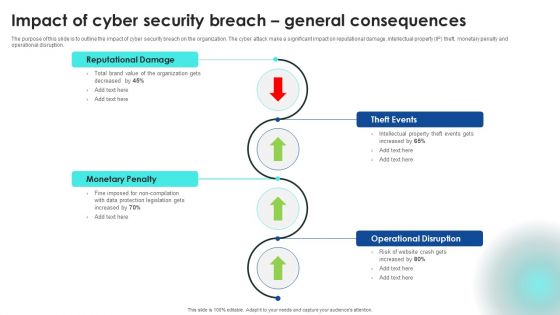
Implementing Cybersecurity Awareness Program To Prevent Attacks Impact Of Cyber Security Breach General Clipart PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Implementing Cybersecurity Awareness Program To Prevent Attacks Impact Of Cyber Security Breach General Clipart PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Multistep Process To Internet Security Threat Analysis Ppt PowerPoint Presentation Layouts Maker PDF
Presenting multistep process to internet security threat analysis ppt powerpoint presentation layouts maker pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including identify, protect, detect, respond, recover. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Solution Development Process Overview And Importance Of Secure SDLC Demonstration PDF
This slide depicts the overview and importance of a secure software development life cycle, including how it helps to reduce total software development time and cost.Presenting Solution Development Process Overview And Importance Of Secure SDLC Demonstration PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Security Components, Software Development, Vulnerabilities Detected. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF today and make your presentation stand out from the rest

Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cybersecurity Awareness Program To Prevent Attacks Evaluating IT System Security Formats PDF today and make your presentation stand out from the rest.

Key Steps Of Saas Cloud Security Process Ppt PowerPoint Presentation Gallery Design Ideas PDF
The following slide depicts the SaaS security process to acknowledge the gap and have proactive approach. It mainly constitutes of three phases discover, monitor and protect. Persuade your audience using this Key Steps Of Saas Cloud Security Process Ppt PowerPoint Presentation Gallery Design Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Discover, Monitor, Protect, Identify Utility, Assess Risk. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cyber Intelligent Computing System Security Strategic Planning Process For CPS Icons PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Deliver an awe inspiring pitch with this creative Cyber Intelligent Computing System Security Strategic Planning Process For CPS Icons PDF bundle. Topics like Gap Analysis, Environmental Trends, Business Strategy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
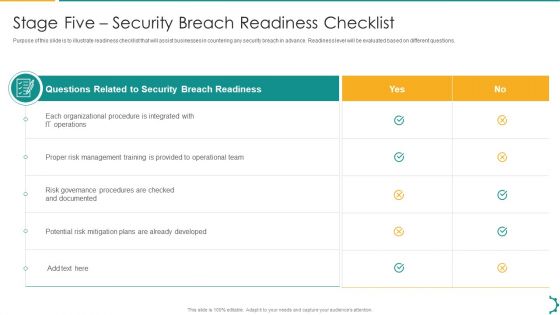
Artificial Intelligence Playbook Stage Five Security Breach Readiness Checklist Topics PDF
Purpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions. Deliver an awe inspiring pitch with this creative artificial intelligence playbook stage five security breach readiness checklist topics pdf bundle. Topics like questions related, security breach readiness, each organizational procedure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
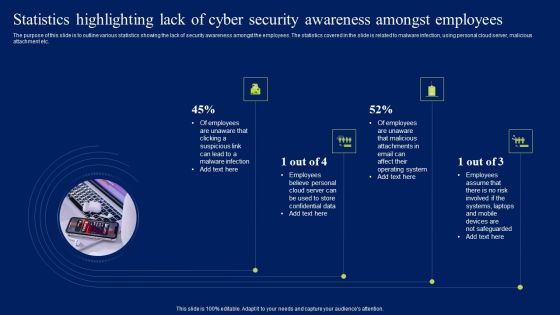
Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Diagrams PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc. Present like a pro with Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Diagrams PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
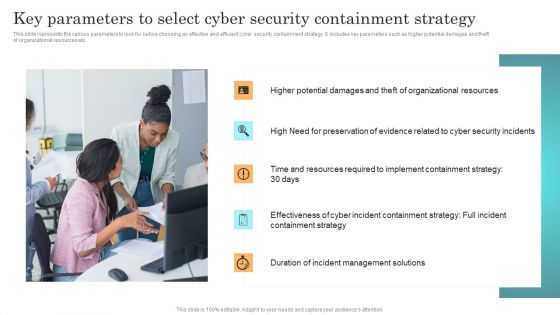
Incident Response Techniques Deployement Key Parameters To Select Cyber Security Containment Strategy Information PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Present like a pro with Incident Response Techniques Deployement Key Parameters To Select Cyber Security Containment Strategy Information PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
Requirement For Security Planning And Risk Mitigation Process Ppt PowerPoint Presentation Infographics Icon PDF
Pitch your topic with ease and precision using this requirement for security planning and risk mitigation process ppt powerpoint presentation infographics icon pdf. This layout presents information on main requirements, supporting requirements, security plan review, threat levels, impact risks, risk steward. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security And Process Integration Contingency Plan For Threat Handling Template PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative security and process integration contingency plan for threat handling template pdf bundle. Topics like contingency considerations, mainframe systems, security, implementation, technologies integration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Process Integration Insider Attacker Method And Behaviour Assessment Microsoft PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this security and process integration insider attacker method and behaviour assessment microsoft pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
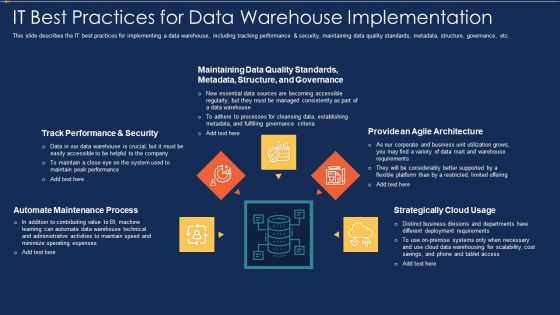
Data Warehousing IT IT Best Practices For Data Warehouse Implementation Ppt Show Rules PDF
This slide describes the IT best practices for implementing a data warehouse, including tracking performance and security, maintaining data quality standards, metadata, structure, governance, etc. This is a data warehousing it it best practices for data warehouse implementation ppt show rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like automate maintenance process, track performance and security, maintaining data quality standards, metadata, structure, and governance, provide an agile architecture, strategically cloud usage. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
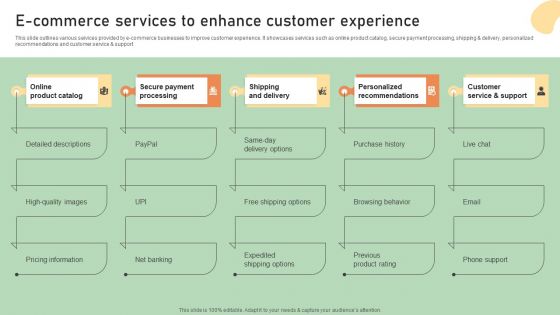
E Commerce Business Development Plan E Commerce Services To Enhance Customer Experience Graphics PDF
This slide outlines various services provided by e-commerce businesses to improve customer experience. It showcases services such as online product catalog, secure payment processing, shipping and delivery, personalized recommendations and customer service and support. Explore a selection of the finest E Commerce Business Development Plan E Commerce Services To Enhance Customer Experience Graphics PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our E Commerce Business Development Plan E Commerce Services To Enhance Customer Experience Graphics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

IT Threats Response Playbook Addressing The Various Security Incidents And Attacks Brochure PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques.This is a IT Threats Response Playbook Addressing The Various Security Incidents And Attacks Brochure PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Incidents, Security Attacks, Common Techniques. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
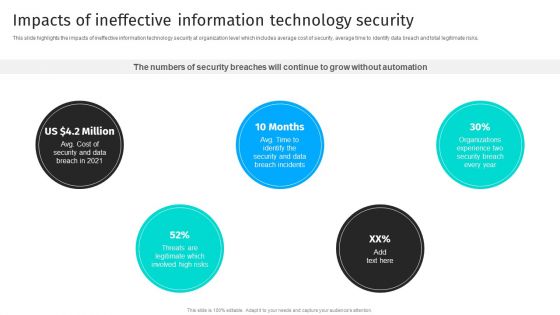
Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks.If you are looking for a format to display your unique thoughts, then the professionally designed Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Security Automation To Analyze And Mitigate Cyberthreats Impacts Of Ineffective Information Designs PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Addressing Hazard Analysis In Different Focus Areas Food Security Excellence Ppt Infographics Slides PDF
This slide provides information regarding addressing hazard analysis in different focus areas such as ingredients, facility design, equipment design, etc. Deliver an awe inspiring pitch with this creative addressing hazard analysis in different focus areas food security excellence ppt infographics slides pdf bundle. Topics like ingredients, processing procedure, facility design, equipment design and usage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Customer Experience Strategy Payment Gateway Provider Startup GTM Strategy GTM SS V
The following slide showcases the customer experience strategy to build trust among target audience. It showcases strategies which includes multilingual customer support, trust and security programs, transparency in policies, etc.The following slide showcases the customer experience strategy to build trust among target audience. It showcases strategies which includes multilingual customer support, trust and security programs, transparency in policies, etc.Get a simple yet stunning designed Customer Experience Strategy Payment Gateway Provider Startup GTM Strategy GTM SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Customer Experience Strategy Payment Gateway Provider Startup GTM Strategy GTM SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Quarterly IT Security Awareness Training Program Plan Ppt Gallery Topics PDF
This slide covers quarterly cybersecurity awareness training program plan. It involves activities such as cybersecurity knowledge and survey, compliance training, phishing simulation etc. Pitch your topic with ease and precision using this Quarterly IT Security Awareness Training Program Plan Ppt Gallery Topics PDF. This layout presents information on Key Message, Core Awareness Activities, Responsible Person, Budget. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
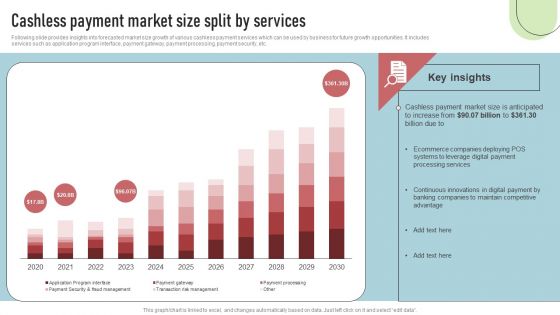
Cashless Payment Strategies To Enhance Business Performance Cashless Payment Market Size Split By Services Rules PDF
Following slide provides insights into forecasted market size growth of various cashless payment services which can be used by business for future growth opportunities. It includes services such as application program interface, payment gateway, payment processing, payment security, etc. Create an editable Cashless Payment Strategies To Enhance Business Performance Cashless Payment Market Size Split By Services Rules PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Cashless Payment Strategies To Enhance Business Performance Cashless Payment Market Size Split By Services Rules PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Our Team For Security Camera Sarvices One Pager Sample Example Document
This slide shows the project execution team with the individual members name, designation, and brief work description. Presenting you an exemplary Our Team For Security Camera Sarvices One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Team For Security Camera Sarvices One Pager Sample Example Document brilliant piece now.

Communication Plan General Format Hacking Prevention Awareness Training For IT Security Download PDF
This slide covers the schedule communication plan for security awareness program including brief description, frequency and audience. Deliver an awe inspiring pitch with this creative communication plan general format hacking prevention awareness training for it security download pdf bundle. Topics like security awareness, communication, organizations, frequency can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Network Security Awareness Staff Learning Communication Plan General Format Infographics PDF
This slide covers the schedule communication plan for security awareness program including brief description, frequency and audience. Deliver an awe-inspiring pitch with this creative organizational network security awareness staff learning communication plan general format infographics pdf bundle. Topics like communication, security awareness, organizations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
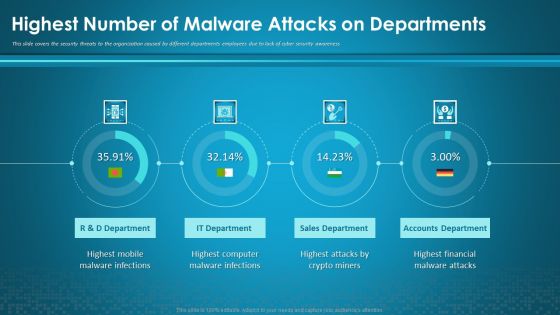
Organizational Network Security Awareness Staff Learning Highest Number Of Malware Attacks On Departments Information PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this organizational network security awareness staff learning highest number of malware attacks on departments information pdf. Use them to share invaluable insights on sales department, accounts department, financial, computer, mobile and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

 Home
Home