Safety Management

Best Data Security Software Why Us For Company Online Database Security Proposal Themes PDF
Presenting this set of slides with name best data security software why us for company online database security proposal themes pdf. This is a four stage process. The stages in this process are our team includes elite software engineers and cyber security experts to keep our culture fresh, innovative and energetic. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Business Process PowerPoint Templates Business Weak Broken Chains And Links Ropes Ppt Slides
Business Process PowerPoint Templates Business Weak Broken Chains And Links Ropes PPT Slides- At times, however, there is a crucial aspect that requires extra attention. Illustrate your chain of ideas focusing on that aspect or resource in order to enhance the quality of your product.-Business Process PowerPoint Templates Business Weak Broken Chains And Links Ropes PPT Slides-This template can be used for presentations relating to Analysing, Broken, Chain, Colour, Curiosity, Discovery, Equipment, Examining, Exploration, Eyesight, Focus, Glass, Handle, Horizontal, Isolated, Large, Lens, Link, Looking, Loupe, Magnification, Magnifying, Mystery, Nobody, Object, Optical, Photography, Reading, Research, Science, Scrutiny, Searching
Business Process PowerPoint Templates Business Weak Links And Chains Ppt Slides
Business Process PowerPoint Templates Business Weak Links and Chains PPT Slides-Chain reactions and the element of teamwork add value to your efforts. At times, however, there is a crucial aspect that requires extra attention. Illustrate your chain of ideas focusing on that aspect or resource in order to enhance the quality of your product.-Business Process PowerPoint Templates Business Weak Links and Chains PPT Slides-This template can be used for presentations relating to Analysing, Broken, Chain, Colour, Curiosity, Discovery, Equipment, Examining, Exploration, Eyesight, Focus, Glass, Handle, Horizontal, Isolated, Large, Lens, Link, Looking, Loupe, Magnification, Magnifying, Mystery, Nobody, Object, Optical, Photography, Reading, Research, Science, Scrutiny, Searching
Security Awareness Tracking Kpis Ppt Slides Shapes PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction. Deliver and pitch your topic in the best possible manner with this security awareness tracking kpis ppt slides shapes pdf. Use them to share invaluable insights on security awareness tracking kpis and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF
This slide signifies cyber security roadmap of an organization with seven millstone achieved within 4 year timeline. Persuade your audience using this Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Security Assessment Team, Identify Digital Assets, Provide Access Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Introduction Of Utility Tokenization Strategies For Data Security PPT Presentation
This slide showcases the overview of utility tokens in data security. The purpose of this slide is to discuss the introduction of utility tokens required for data security and preventing thefts. Boost your pitch with our creative Introduction Of Utility Tokenization Strategies For Data Security PPT Presentation. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
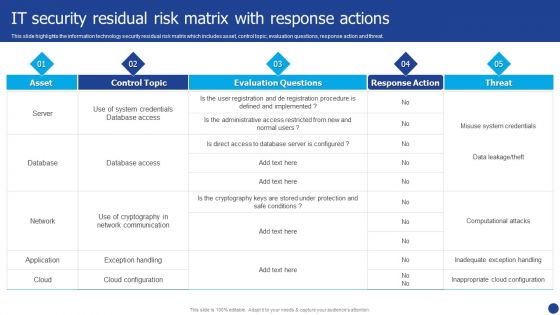
Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF. Use them to share invaluable insights on Database, Network, Application and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Integration Architecture Creation Best Practices Data Integration Strategies For Business
This slide highlights the best practices followed in data integration architecture. The purpose of this slide is to explain these practices, such as business objectives, collaboration, automation, flexibility, and security. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Data Integration Architecture Creation Best Practices Data Integration Strategies For Business. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Data Integration Architecture Creation Best Practices Data Integration Strategies For Business today and make your presentation stand out from the rest
Prevention Of Information Key Stakeholders Of Cyber Security Awareness Training Icons PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Prevention Of Information Key Stakeholders Of Cyber Security Awareness Training Icons PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Implementing Cybersecurity Awareness Program To Prevent Attacks Key Stakeholders Of Cyber Security Themes PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Implementing Cybersecurity Awareness Program To Prevent Attacks Key Stakeholders Of Cyber Security Themes PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Process Of Information Security System Diagram Powerpoint Slide Background Picture
This is a process of information security system diagram powerpoint slide background picture. This is a four stage process. The stages in this process are information security, confidentiality, availability, integrity.
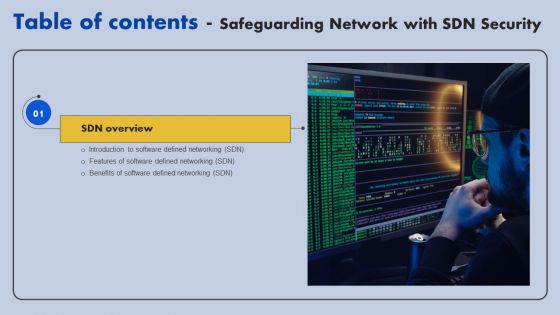
Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF
This slide represents the schematic elements of software-defined networking, such as the northbound interface, SDN controller, and southbound interface. These components transmit the information throughout the SDN architecture. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Our Market Selection Process Series A Capital Funding Elevator Pitch Deck For Real Estate Professional PDF
This slide highlights the companys process of selecting a suitable market based on various factors such as crime rates, disposable income, job specific location areas and millennial preferences. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Our Market Selection Process Series A Capital Funding Elevator Pitch Deck For Real Estate Professional PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Our Market Selection Process Series A Capital Funding Elevator Pitch Deck For Real Estate Professional PDF.
Eight Key Steps Of Successful Testing Process Ppt PowerPoint Presentation Model Visuals PDF
Persuade your audience using this eight key steps of successful testing process ppt powerpoint presentation model visuals pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including keyword testing, object driven testing, manual tests. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
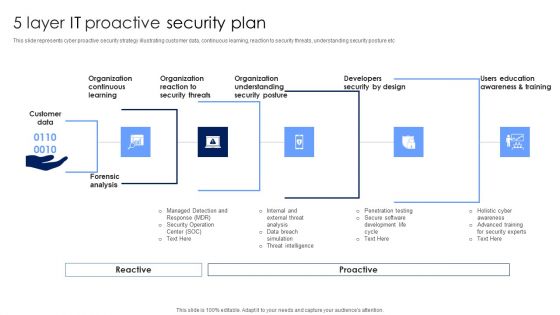
5 Layer IT Proactive Security Plan Topics PDF
This slide represents cyber proactive security strategy illustrating customer data, continuous learning, reaction to security threats, understanding security posture etc. Persuade your audience using this 5 Layer IT Proactive Security Plan Topics PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Organization Understanding, Organization Reaction, Organization Continuous Learning. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
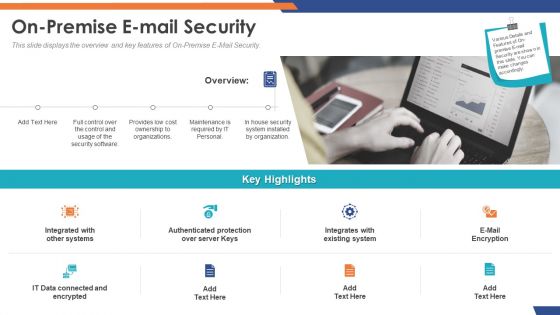
Email Security Market Research Report On Premise E Mail Security Mockup PDF
Presenting this set of slides with name email security market research report on premise e mail security mockup pdf. This is a two stage process. The stages in this process are integrated with other systems, authenticated protection over server keys, integrates with existing system, e mail encryption. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cloud Based Email Security Market On Premise E Mail Security Topics PDF
Presenting this set of slides with name global cloud based email security market on premise e mail security topics pdf. This is a two stage process. The stages in this process are integrated with other systems, authenticated protection over server keys, integrates with existing system, e mail encryption. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Data Tokenization Tools Tokenization Strategies For Data Security PPT Template
Boost your pitch with our creative Data Tokenization Tools Tokenization Strategies For Data Security PPT Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Working Capital Loan Without Security Ppt PowerPoint Presentation Slides Samples Cpb
Presenting this set of slides with name working capital loan without security ppt powerpoint presentation slides samples cpb. This is an editable Powerpoint seven stages graphic that deals with topics like working capital loan without security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
IT Security Automation Systems Guide Security Automation Stages With Maturity Level Icons PDF
This slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than IT Security Automation Systems Guide Security Automation Stages With Maturity Level Icons PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab IT Security Automation Systems Guide Security Automation Stages With Maturity Level Icons PDF today and make your presentation stand out from the rest.

Major Cybersecurity Challenges With Required Actions Ppt Pictures Background Designs PDF
The slide provides the key cybersecurity challenges information security, protecting infrastructure, protecting privacy and sensitive data etc. along with the critical actions required from the organization to resolve those challenges This is a major cybersecurity challenges with required actions ppt pictures background designs pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like infrastructure, cybersecurity strategy, performing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF can be your best option for delivering a presentation. Represent everything in detail using Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Disaster Recovery Planning Element Of Cyber Security Template PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. It also contains the types of disaster recovery plans and planning process. Slidegeeks is here to make your presentations a breeze with Disaster Recovery Planning Element Of Cyber Security Template PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
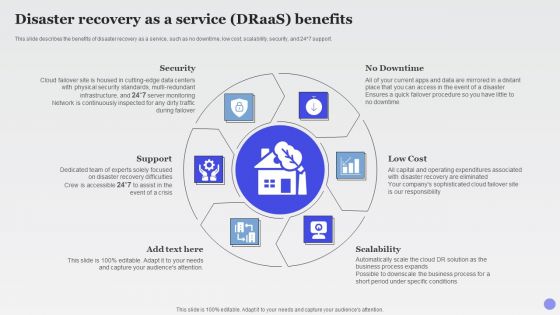
Disaster Recovery As A Service Draas Benefits Xaas Cloud Computing Models Ppt PowerPoint Presentation Guidelines PDF
This slide describes the benefits of disaster recovery as a service, such as no downtime, low cost, scalability, security, and 24 7 support.This is a Disaster Recovery As A Service Draas Benefits Xaas Cloud Computing Models Ppt PowerPoint Presentation Guidelines PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Failover Procedure, Recovery Eliminated, Expenditures Associated. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Implementation Process Of Network Infra Cyber Security Introduction PDF
The following slide showcases process to implement network infra security to ensure that underlying infrastructure remains protected. It presents information related to segmentation networks, validation of hardware, etc. Presenting Implementation Process Of Network Infra Cyber Security Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Segmentation Networks, Secure Access Infrastructure, Validate Hardware. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Breach Prevention Recognition Security Training Program Frameworks Contd Template PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe-inspiring pitch with this creative data breach prevention recognition security training program frameworks contd template pdf bundle. Topics like measures, instruction information sources, target audience can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Network Awareness Staff Learning Security Training Program Frameworks Contd Formats PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe-inspiring pitch with this creative organizational network awareness staff learning security training program frameworks contd formats pdf bundle. Topics like target audience for training, source content, metrics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
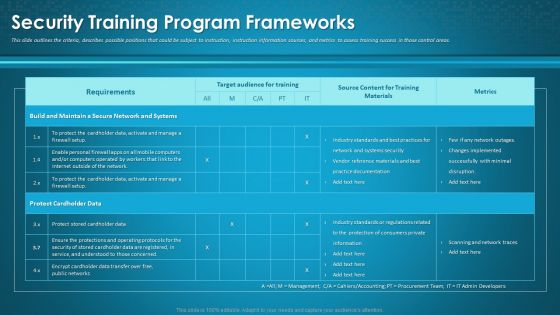
Organizational Network Awareness Staff Learning Security Training Program Frameworks Sample PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this organizational network awareness staff learning security training program frameworks sample pdf. Use them to share invaluable insights on target audience for training, source content, metrics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Investment Banking Security Underwriting Pitchbook IPO Timeline Pre IPO To Post IPO Pictures PDF
The slide provides the timeline of IPO issue and covers the five steps i.e. Pre-IPO planning, Preparation for Filing, SEC Review, Road Show, and Post IPODeliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook IPO Timeline Pre IPO To Post IPO Pictures PDF bundle. Topics like Organizational Meeting, Preparation Filling, Internal Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
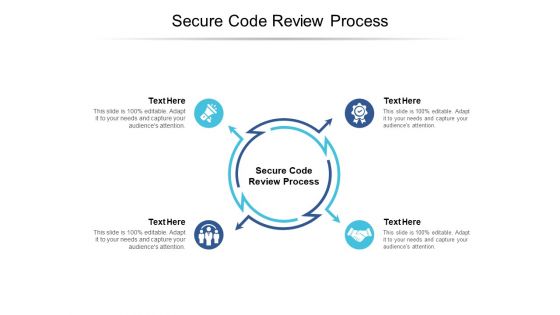
Secure Code Review Process Ppt PowerPoint Presentation Layouts Examples Cpb
Presenting this set of slides with name secure code review process ppt powerpoint presentation layouts examples cpb. This is an editable Powerpoint four stages graphic that deals with topics like secure code review process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
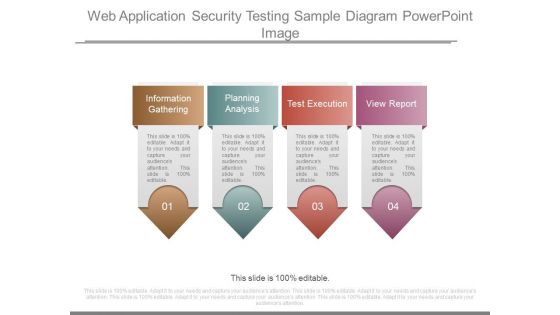
Web Application Security Testing Sample Diagram Powerpoint Image
This is a web application security testing sample diagram powerpoint image. This is a four stage process. The stages in this process are information gathering, planning analysis, test execution, view report.
Stock Photo 3d Folders With Key And Lock PowerPoint Slide
Concept of data security has been displayed in this power point image template with suitable graphics. This image contains the graphics of 3d folders and key with lock. Use this PPT image for your data related presentations.
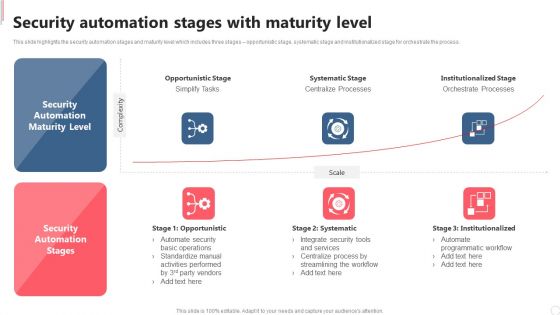
Cyber Security Automation Framework Security Automation Stages With Maturity Level Clipart PDF
This slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cyber Security Automation Framework Security Automation Stages With Maturity Level Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cyber Security Automation Framework Security Automation Stages With Maturity Level Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Security Automation To Analyze And Mitigate Cyberthreats Determine Ideal Tasks For Security Clipart PDF
This slide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section.Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Security Automation To Analyze And Mitigate Cyberthreats Determine Ideal Tasks For Security Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Security Automation To Analyze And Mitigate Cyberthreats Determine Ideal Tasks For Security Clipart PDF today and make your presentation stand out from the rest.
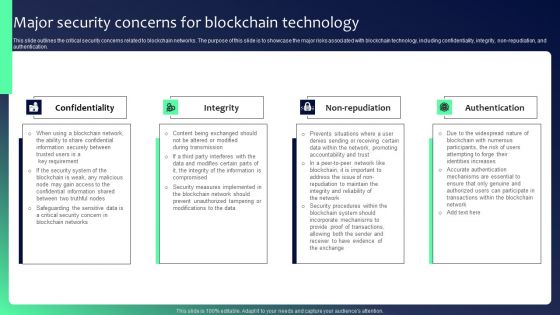
Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF
This slide outlines the critical security concerns related to blockchain networks. The purpose of this slide is to showcase the major risks associated with blockchain technology, including confidentiality, integrity, non-repudiation, and authentication. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF today and make your presentation stand out from the rest
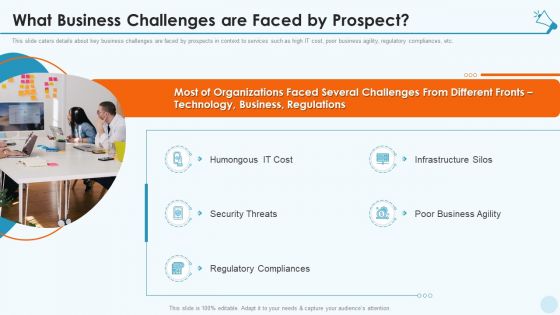
Services Marketing Sales What Business Challenges Are Faced By Prospect Ppt Icon Diagrams PDF
This slide caters details about key business challenges are faced by prospects in context to services such as high IT cost, poor business agility, regulatory compliances, etc. This is a services marketing sales what business challenges are faced by prospect ppt icon diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like humongous it cost, infrastructure silos, security threats, regulatory compliances, poor business agility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Services Promotion Investor Financing Elevator What Business Challenges Are Faced By Prospect Designs PDF
This slide caters details about key business challenges are faced by prospects in context to services such as high IT cost, poor business agility, regulatory compliances, etc. Presenting services promotion investor financing elevator what business challenges are faced by prospect designs pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like humongous it cost, security threats, regulatory compliances, infrastructure silos, poor business agility. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Services Sales Capital Investment Pitch Deck Value Proposition Of Firm In Leveraging Customer Relationships Background PDF
This slide caters details about key business challenges are faced by prospects in context to services such as high IT cost, poor business agility, regulatory compliances, etc. This is a services sales capital investment pitch deck what business challenges are faced by prospect icons pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like humongous it cost, infrastructure silos, security threats, regulatory compliances, poor business agilit. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

5G Network Operations Security In 5G Technology Architecture Template PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download 5G Network Operations Security In 5G Technology Architecture Template PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the 5G Network Operations Security In 5G Technology Architecture Template PDF.

How Does Cloud Security Work Data Retention And Business Continuity Planning Template PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. Presenting How Does Cloud Security Work Data Retention And Business Continuity Planning Template PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Business Continuity, Recovery Strategies, Plan Development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Onboarding Service Providers For Internal Operations Betterment Business Offshoring Roadmap Ideas PDF
This is a onboarding service providers for internal operations betterment business offshoring roadmap ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, service, customer, market analysis . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
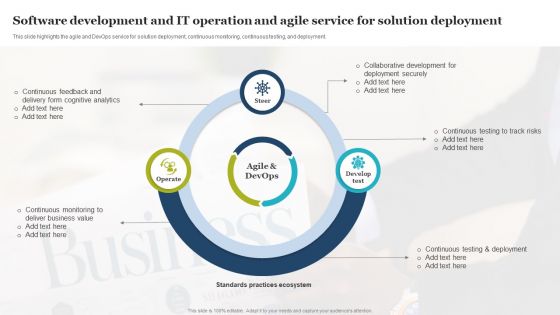
Software Development And IT Operation And Agile Service For Solution Deployment Portrait PDF
This slide highlights the agile and DevOps service for solution deployment, continuous monitoring, continuous testing, and deployment. Presenting Software Development And IT Operation And Agile Service For Solution Deployment Portrait PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Deployment Securely, Collaborative Development, Deliver Business Value. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
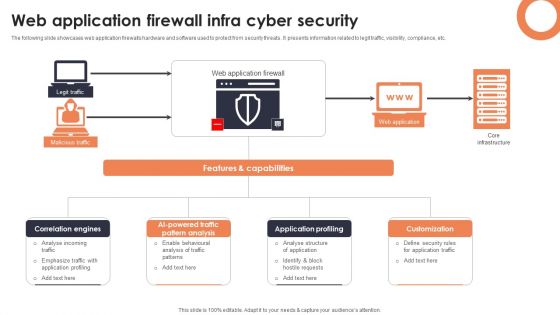
Web Application Firewall Infra Cyber Security Designs PDF
The following slide showcases web application firewalls hardware and software used to protect from security threats. It presents information related to legit traffic, visibility, compliance, etc. Showcasing this set of slides titled Web Application Firewall Infra Cyber Security Designs PDF. The topics addressed in these templates are Correlation Engines, AI Powered Traffic Pattern, Application Profiling. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
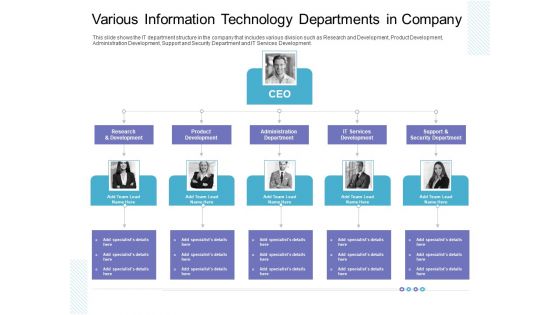
Various Information Technology Departments In Company Slides PDF
This slide shows the IT department structure in the company that includes various division such as Research and Development, Product Development, Administration Development, Support and Security Department and IT Services Development. This is a various information technology departments in company slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like product development, administration department, research and development, support and security department. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
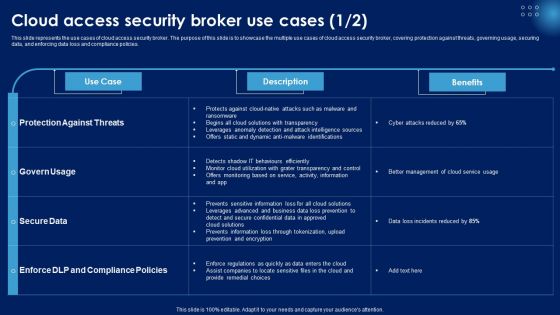
Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. This Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Impact Of Cyber Security Breach General Consequences Ideas PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. This is a Impact Of Cyber Security Breach General Consequences Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Reputational Damage, Monetary Penalty, Operational Disruption. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
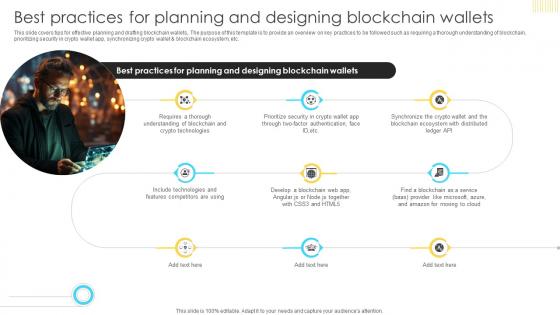
Mastering Blockchain Wallets Best Practices For Planning And Designing Blockchain BCT SS V
This slide covers tips for effective planning and drafting blockchain wallets,. The purpose of this template is to provide an overview on key practices to be followed such as requiring a thorough understanding of blockchain, prioritizing security in crypto wallet app, synchronizing crypto wallet and blockchain ecosystem, etc. Want to ace your presentation in front of a live audience Our Mastering Blockchain Wallets Best Practices For Planning And Designing Blockchain BCT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Growth Bar Graph With Success Key PowerPoint Templates Ppt Backgrounds For Slides 0613
Analyse ailments on our Growth Bar Graph With Success Key PowerPoint Templates PPT Backgrounds For Slides. Bring out the thinking doctor in you. Dock your thoughts with our Security PowerPoint Templates. They will launch them into orbit. Get out of the dock with our Process and Flows PowerPoint Templates. Your mind will be set free.

Business Bar Graph With Success Key PowerPoint Templates Ppt Backgrounds For Slides 0613
Give them a dose of your ability. It will go down well with our Business Bar Graph With Success Key PowerPoint Templates PPT Backgrounds For Slides. Connect the dots with our Security PowerPoint Templates. Watch the whole picture clearly emerge. Dot your thoughts with our Process and Flows PowerPoint Templates. Give your demeanour that Propah look.
Business Growth Is Key Of Profit PowerPoint Templates Ppt Backgrounds For Slides 0613
Open up doors that lead to success. Our Business Growth Is Key Of Profit PowerPoint Templates PPT Backgrounds For Slides provide the handles. Oppurtunity will come knocking at your door. Welcome it with our Process and Flows PowerPoint Templates. Our Security PowerPoint Templates abhor doodling. They never let the interest flag.

Risign Graph Key Illustration PowerPoint Templates Ppt Backgrounds For Slides 0813
Display your drive on our Risign Graph Key Illustration PowerPoint Templates PPT Backgrounds For Slides. Invigorate the audience with your fervour. Drive your team towards excellence. Steer them there with our Process and Flows PowerPoint Templates. Drive your passion with our Security PowerPoint Templates. Steer yourself to achieve your aims.

Golden Key And Euro Symbol PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Golden Key And Euro Symbol PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Security PowerPoint Templates because You can Score a slam dunk with our PowerPoint Templates and Slides. Watch your audience hang onto your every word. Download our Signs PowerPoint Templates because It will get your audience in sync. Download our Business PowerPoint Templates because You can Rise to the occasion with our PowerPoint Templates and Slides. You will bring your audience on their feet in no time. Download our Money PowerPoint Templates because You can Be the star of the show with our PowerPoint Templates and Slides. Rock the stage with your ideas. Use our Success PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home.Use these PowerPoint slides for presentations relating to Key euro, security, signs, business, money, success. The prominent colors used in the PowerPoint template are Yellow, Red, Black.

Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF
This slide represents various types of information and communication technology ICT securities used by businesses. It covers network security, endpoint security, access security, and data encryption. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Execution Of ICT Strategic Plan Most Commonly Types Of ICT Securities Used By Businesses Microsoft PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
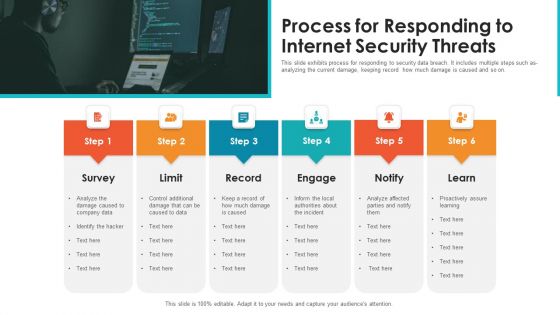
Process For Responding To Internet Security Threats Template PDF
This slide exhibits process for responding to security data breach. It includes multiple steps such as- analyzing the current damage, keeping record how much damage is caused and so on. Pitch your topic with ease and precision using this process for responding to internet security threats template pdf. This layout presents information on process for responding to internet security threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
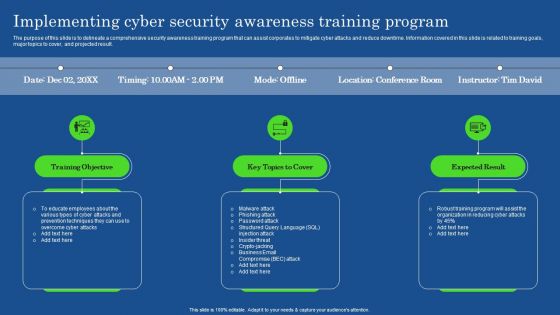
Implementing Cyber Security Awareness Training Program Professional PDF
The purpose of this slide is to delineate a comprehensive security awareness training program that can assist corporates to mitigate cyber attacks and reduce downtime. Information covered in this slide is related to training goals, major topics to cover, and projected result. Make sure to capture your audiences attention in your business displays with our gratis customizable Implementing Cyber Security Awareness Training Program Professional PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cyber Exploitation IT Ethical Hacker And Why We Need Ethical Hacker Information PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development and quality control, and evaluation of the companys security and regulatory compliance. This is a cyber exploitation it ethical hacker and why we need ethical hacker information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security flaws, development and quality control, evaluate security and regulatory compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Qualified Traffic Generation Through Search Engines How An Ad Auction Works To Secure Structure PDF
This Qualified Traffic Generation Through Search Engines How An Ad Auction Works To Secure Structure PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Qualified Traffic Generation Through Search Engines How An Ad Auction Works To Secure Structure PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Steps To Ensure Robotic Process Automated Security Ideas PDF
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development. This is a Steps To Ensure Robotic Process Automated Security Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Guarantee Accountability, Protect Log Respectability, Empower Secure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Grow Your Business Step By Step PowerPoint Templates Ppt Backgrounds For Slides 0513
Drink from the fountain of our Grow Your Business Step By Step PowerPoint Templates PPT Backgrounds For Slides. Refresh your audience with your bubbling ideas. Bottle your thoughts in our security PowerPoint Templates. Pass it around for your audience to sip. Let your audience drink in your thoughts. Our finance PowerPoint Templates will pick up the tab.
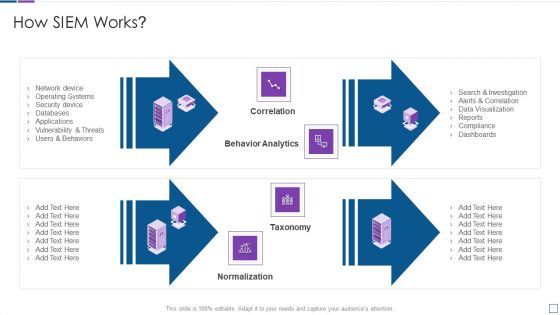
Real Time Assessment Of Security Threats How SIEM Works Inspiration PDF
Presenting real time assessment of security threats how siem works inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like correlation, behavior analytics, taxonomy, normalization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home