Safety Management Strategy Ppt

Corporate Security And Risk Management How Financial Risk Can Be Controlled Infographics PDF
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Presenting corporate security and risk management how financial risk can be controlled infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like handling liquidity risk, handling foreign exchange risk, handling credit exchange risk . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
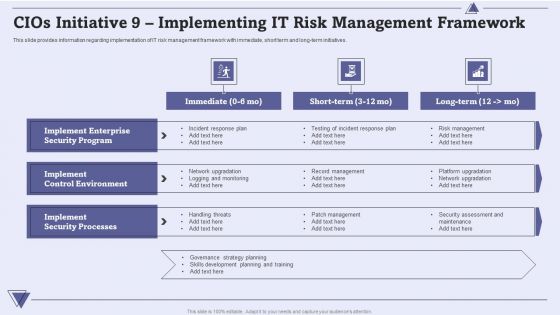
CIO For IT Cost Optimization Techniques Cios Initiative 9 Implementing IT Risk Management Framework Graphics PDF
This slide provides information regarding implementation of IT risk management framework with immediate, short term and long-term initiatives. Presenting CIO For IT Cost Optimization Techniques Cios Initiative 9 Implementing IT Risk Management Framework Graphics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Implement Control Environment, Implement Enterprise Security, Implement Security Processes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Implementing Integrated Software Why Do We Need Hospital Management System Themes PDF
This slide illustrates the need for hospital management system such as cost effectiveness, reduction in errors, maintains security of information, improves patient care, etc.Presenting Implementing Integrated Software Why Do We Need Hospital Management System Themes PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Cost Effective, Reduction Errors, Information Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Determine Sequence Phases For Threat Attack Contd Mockup PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. This is a corporate security and risk management determine sequence phases for threat attack contd mockup pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Project Security Administration IT Addressing Frequent Communication For Project Quality Management Icons PDF
This slide provides information regarding meetings that held in order to keep consistent quality entire project. These meetings are held on quarterly, annual basis. Presenting project security administration it addressing frequent communication for project quality management icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like executive, leaders, coordinators, initiation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mobile Device Management For Improving IT Operations Determining Roles And Responsibilities Themes PDF
This slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Key people involved in risk handling are chief risk officer, chief information security officer, senior management and executives and line managers. Get a simple yet stunning designed Mobile Device Management For Improving IT Operations Determining Roles And Responsibilities Themes PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Mobile Device Management For Improving IT Operations Determining Roles And Responsibilities Themes PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
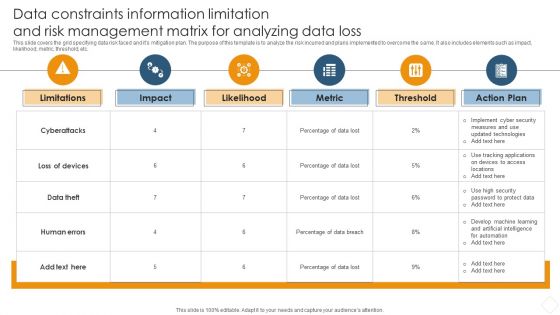
Data Constraints Information Limitation And Risk Management Matrix For Analyzing Data Loss Brochure PDF
This slide covers the grid specifying data risk faced and its mitigation plan. The purpose of this template is to analyze the risk incurred and plans implemented to overcome the same. It also includes elements such as impact, likelihood, metric, threshold, etc.Showcasing this set of slides titled Data Constraints Information Limitation And Risk Management Matrix For Analyzing Data Loss Brochure PDF. The topics addressed in these templates are Data Distribution, Secure Computation, Verifiable Computation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
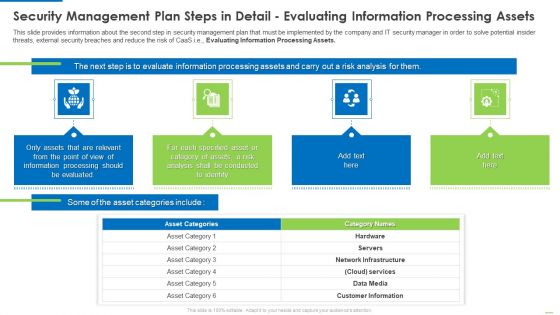
Security Management Plan Steps In Detail Evaluating Information Processing Assets Summary PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e.Evaluating Information Processing Assets. This is a security management plan steps in detail evaluating information processing assets summary pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like processing should be evaluated, conducted to identify, category of assets You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Evaluating Information Processing Assets Demonstration PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Evaluating Information Processing Assets. This is a security management plan steps in detail evaluating information processing assets demonstration pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluate information, conducted to identify, specified asset You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail System Maintenance And Monitoring Summary PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., System Maintenance and Monitoring. Presenting security management plan steps in detail system maintenance and monitoring summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like types of system maintenance, installation costs, types of system monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
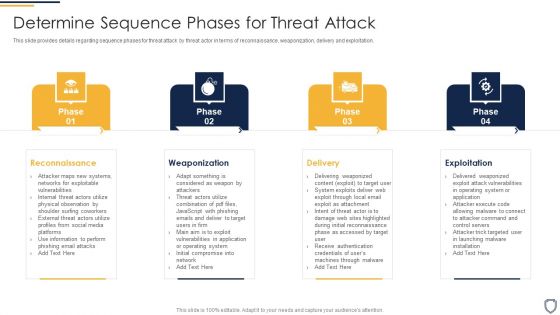
Corporate Security And Risk Management Determine Sequence Phases For Threat Attack Ideas PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting corporate security and risk management determine sequence phases for threat attack ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, delivery, exploitation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
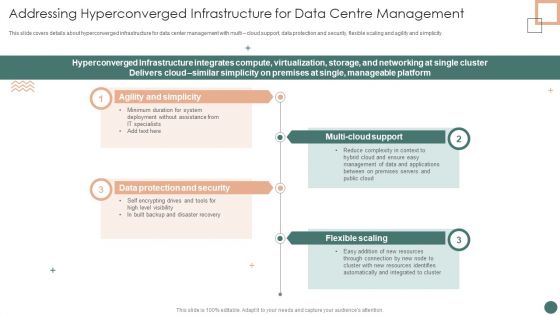
Improved Digital Expenditure Addressing Hyperconverged Infrastructure For Data Centre Management Introduction PDF
This slide covers details about hyperconverged infrastructure for data center management with multi cloud support, data protection and security, flexible scaling and agility and simplicity. Presenting Improved Digital Expenditure Addressing Hyperconverged Infrastructure For Data Centre Management Introduction PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Minimum Duration, Complexity Context, Resources Identifies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
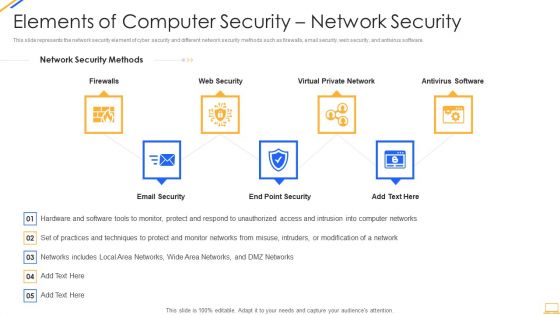
Desktop Security Management Elements Of Computer Security Network Security Infographics PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting desktop security management elements of computer security network security infographics pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like network, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Dashboard For Insider Threat In Cyber Security Cases Management Background PDF
This slide shows insider threat dashboard for managing multiple cases. It provides information such as active and closed, high and low risk cases, status, user, case time, policy alerts, content update, etc. Showcasing this set of slides titled Dashboard For Insider Threat In Cyber Security Cases Management Background PDF. The topics addressed in these templates are Total Policy Alerts, High, Low, Time Case Opened. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Security Assessment How Does Cloud Security Work Identity And Access Management IAM Background PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored.Presenting Cloud Security Assessment How Does Cloud Security Work Identity And Access Management IAM Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Accessibility, Knowledge, Technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain
This slide represents an overview and working of 2-factor authentication2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security it is user-friendly, etc.Get a simple yet stunning designed Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Overview And Working Of Two Factor Authentication Cryptocurrency Management With Blockchain can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Iot Digital Twin Technology Post Covid Expenditure Management Consideration Points Prior Implementing Digital Twins Rules PDF
This slide shows the three points that needs to be considered before implementing digital twin such as updating data security protocols, managing data quality and team training. Presenting iot digital twin technology post covid expenditure management consideration points prior implementing digital twins rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security, protocols, data, training, managing, quality . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
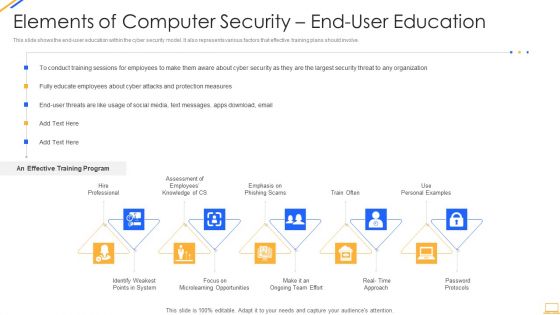
Desktop Security Management Elements Of Computer Security End User Education Background PDF
This slide shows the end user education within the cyber security model. It also represents various factors that effective training plans should involve. This is a desktop security management elements of computer security end user education background pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, opportunities, security, organization, measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

How Does Cloud Security Work Identity And Access Management IAM Professional PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. This is a How Does Cloud Security Work Identity And Access Management IAM Professional PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Accessibility, Security, Quality. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
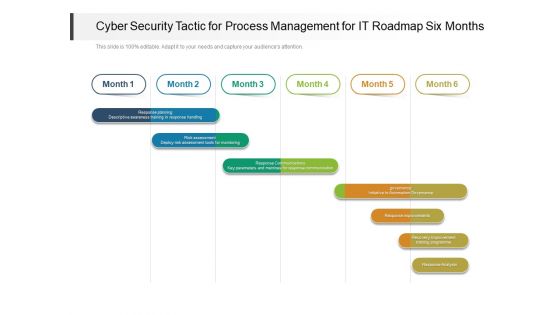
Cyber Security Tactic For Process Management For IT Roadmap Six Months Clipart
Presenting the cyber security tactic for process management for it roadmap six months clipart. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Asset Identification For Information Security Risk Management Cybersecurity Risk Assessment Inspiration PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help form to monitor the asset in real time for any data breach or cyber attack. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 parcent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Asset Identification For Information Security Risk Management Cybersecurity Risk Assessment Inspiration PDF from Slidegeeks and deliver a wonderful presentation.
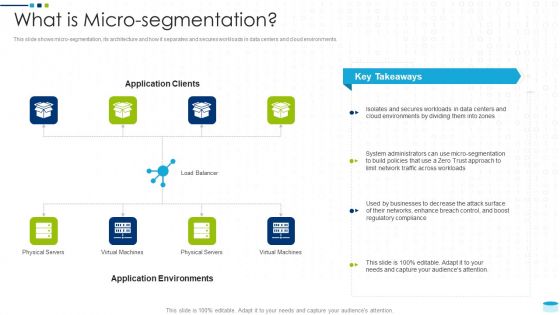
Data Center Infrastructure Management IT What Is Micro Segmentation Slides PDF
This slide shows micro segmentation, its architecture and how it separates and secures workloads in data centers and cloud environments. This is a data center infrastructure management it what is micro segmentation slides pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cloud environments, secures, businesses, policies, administrators. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Spend Management Priorities By Cios Addressing Critical IT Budgeting Measures Checklist Diagrams PDF
This slide provides information regarding critical IT budgeting measures checklist comprising of categorizing IT expenses, focus on IT security and disaster recovery risks, budget planning for work from home scenario, tax calculation, etc. This is a IT Spend Management Priorities By Cios Addressing Critical IT Budgeting Measures Checklist Diagrams PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Budget Planning, Recurring Costs Monitoring, Tax Calculation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
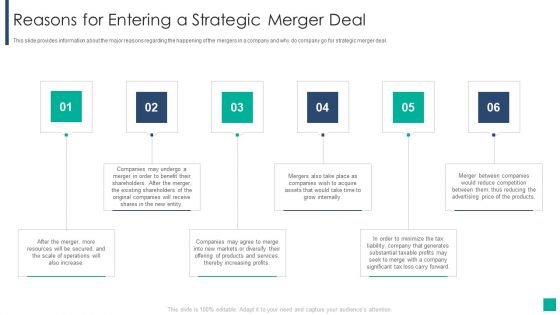
Drivers Influencing The Execution Of Merger And Acquisition Strategy Reasons For Entering A Strategic Merger Deal Designs PDF
This slide provides information about the major reasons regarding the happening of the mergers in a company and why do company go for strategic merger deal.This is a drivers influencing the execution of merger and acquisition strategy reasons for entering a strategic merger deal designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like resources will be secured, existing shareholders, increasing profits You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
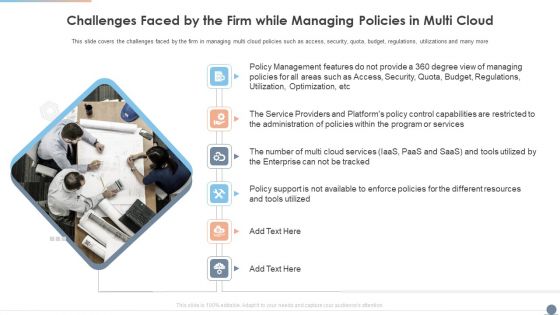
Multi Cloud Complexity Management Challenges Faced By The Firm While Managing Policies In Multi Cloud Topics PDF
This slide covers the challenges faced by the firm in managing multi cloud policies such as access, security, quota, budget, regulations, utilizations and many more. Presenting Multi Cloud Complexity Management Challenges Faced By The Firm While Managing Policies In Multi Cloud Topics PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Service, Budget, Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Project Management Professional Documentation Requirements IT Issues Faced By Company Due To Poorly Managed Project Documents Mockup PDF
This slide provides the glimpse about the issues faced by the company due to poorly managed project documents such as lack of visibility, weak security, data loss, and limited collaboration. Presenting project management professional documentation requirements it issues faced by company due to poorly managed project documents mockup pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like lack of visibility, weak security, limited collaboration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data 30 60 90 Days Plan Brochure PDF
Presenting Executing security management program to mitigate threats and safeguard confidential organizational data 30 60 90 days plan brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like 30 60 90 days plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data Poste It Notes Clipart PDF
This is a Executing security management program to mitigate threats and safeguard confidential organizational data poste it notes clipart pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like poste it notes. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Systems Security And Risk Management Plan Current Information And Data Security Capabilities Of Firm Diagrams PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. Boost your pitch with our creative Information Systems Security And Risk Management Plan Current Information And Data Security Capabilities Of Firm Diagrams PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

IT Security Risk Management Approach Introduction Key Security Controls To Be Addressed In The Program Formats PDF
Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Key Security Controls To Be Addressed In The Program Formats PDF. Use them to share invaluable insights on Application Whitelisting, Patch Applications, User Application Hardening and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Systems Security And Risk Management Plan Risk Assessment Matrix With Vulnerability And Threat Level Background PDF
This slide showcases assessment matrix to identify risk associated with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level. Explore a selection of the finest Information Systems Security And Risk Management Plan Risk Assessment Matrix With Vulnerability And Threat Level Background PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Information Systems Security And Risk Management Plan Risk Assessment Matrix With Vulnerability And Threat Level Background PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Information Systems Security And Risk Management Plan Analysing The Impact On Assets Due To Information Breach Introduction PDF
This slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets. This Information Systems Security And Risk Management Plan Analysing The Impact On Assets Due To Information Breach Introduction PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
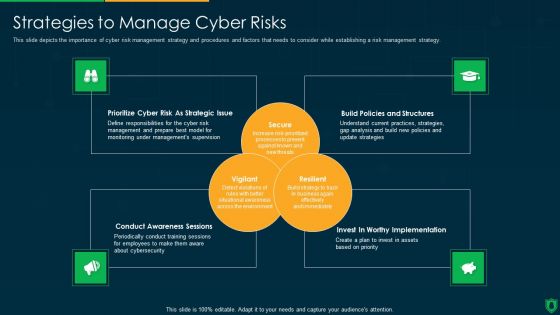
Info Security Strategies To Manage Cyber Risks Ppt PowerPoint Presentation Gallery Graphics Design PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. This is a info security strategies to manage cyber risks ppt powerpoint presentation gallery graphics design pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like prioritize cyber risk as strategic issue, build policies and structures, conduct awareness sessions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
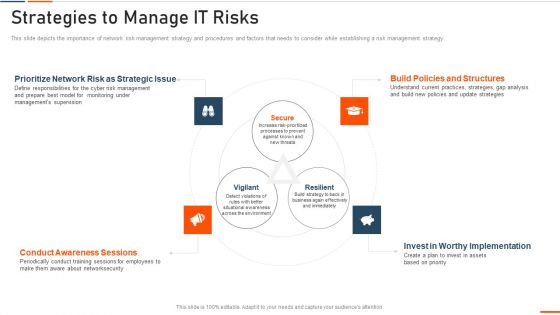
Information Technology Security Strategies To Manage IT Risks Ppt Infographic Template Guidelines PDF
This slide depicts the importance of network risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. This is a information technology security strategies to manage it risks ppt infographic template guidelines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like conduct awareness sessions, invest in worthy implementation, build policies and structures, prioritize network . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security Strategies To Manage Cyber Risks Ppt Icon Gallery PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Presenting it security strategies to manage cyber risks ppt icon gallery pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like conduct awareness sessions, prioritize cyber risk as strategic issue, build policies and structures, invest in worthy implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies To Manage Cyber Risks IT Security IT Ppt Visual Aids Portfolio PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Presenting strategies to manage cyber risks it security it ppt visual aids portfolio pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like prioritize cyber risk as strategic issue, conduct awareness sessions, build policies and structures, invest in worthy implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
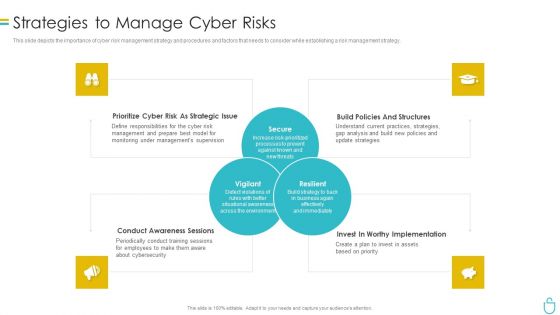
Information Security Strategies To Manage Cyber Risks Ppt Layouts Gridlines PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. This is a information security strategies to manage cyber risks ppt layouts gridlines pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk, management, strategies, analysis. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
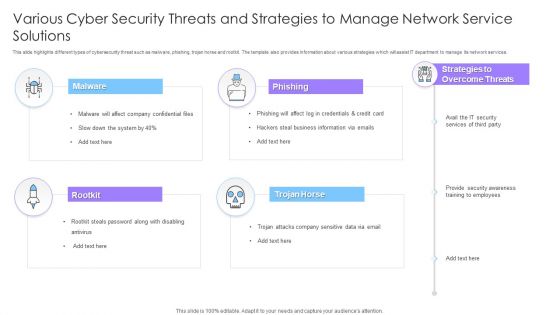
Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF
This slide highlights different types of cybersecurity threat such as malware, phishing, trojan horse and rootkit. The template also provides information about various strategies which will assist IT department to manage its network services. Persuade your audience using this Various Cyber Security Threats And Strategies To Manage Network Service Solutions Ppt File Portrait PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Malware, Phishing, Rootkit, Trojan Horse. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
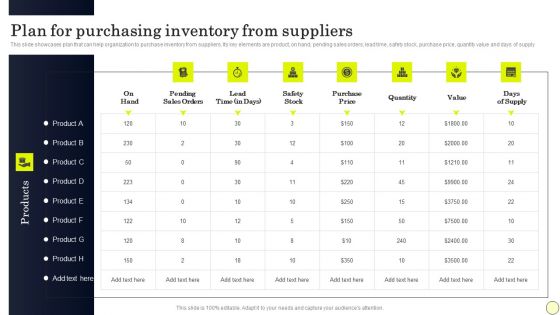
Strategies To Order And Manage Ideal Inventory Levels Plan For Purchasing Inventory From Suppliers Topics PDF

Enterprise Architecture Reference Framework Entities Ppt Show Gallery PDF
The following slide showcases overview of layers and entities in enterprise architecture model. It includes supply chain, human capital, finance, safety and security. Pitch your topic with ease and precision using this Enterprise Architecture Reference Framework Entities Ppt Show Gallery PDF. This layout presents information on Enterprise Governance, Safety And Security, Supply Chain. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Employee Health And Risk Key Performance Indicator Dashboard Ppt Layouts Brochure PDF
The following slide highlights the employee health and safety key performance indicator dashboard illustrating narrow escapes, potential hazards, improvement opportunity, total incidents, health and safety learning, safety visit by management, ltir and trir, severe injuries and fatalities and safety goals. Showcasing this set of slides titled Employee Health And Risk Key Performance Indicator Dashboard Ppt Layouts Brochure PDF. The topics addressed in these templates are Narrow Escapes, Potential Hazards, Improvement Opportunity. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Strategies To Mitigate Cyber Security Risks Essential Contingency Plan Strategies Ppt Pictures Themes PDF
Presenting this set of slides with name strategies to mitigate cyber security risks essential contingency plan strategies ppt pictures themes pdf. The topics discussed in these slides are contingency considerations, contingency solutions, technologies integration, vendors coordination. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Lime Investor Fundraising Elevator Safe Reliable And Smart Ppt Summary Gallery PDF
Mentioned slide displays details about the lime bikes safety and reliability. Key points covered in the slide are green, smart IoT technology, safety tested, low maintenance and easier to ride. Deliver an awe inspiring pitch with this creative lime investor fundraising elevator safe reliable and smart ppt summary gallery pdf bundle. Topics like consumer product safety commission cpsc and iso certified, solar panel can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Hedge Funds Trading And Investing Strategies Hedge Fund Investor And Manager Tool Kit Themes PDF
This slide highlights the tool kit for investor and manager for investing in hedge funds which includes short selling, active hedging, leverage, dynamic risk management, concentration and litigation techniques. Deliver and pitch your topic in the best possible manner with this Hedge Funds Trading And Investing Strategies Hedge Fund Investor And Manager Tool Kit Themes PDF. Use them to share invaluable insights on Dynamic Risk Management, Application, Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Upskilling Strategies For Upgrading Digital Transformation Journey PPT Template DT SS V
This slide presents various upskilling and reskilling strategies for existing employees of energy and utilities industry. It includes areas workforce, maintenance, safety and compliance, field technicians, operations, and leaderships. Presenting this PowerPoint presentation, titled Safety And Compliance, Field Technicians, Operations, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Safety And Compliance, Field Technicians, Operations. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Safety And Compliance, Field Technicians, Operations that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
Infrastructure Strategies IT Infrastructure Optimization Ppt Icon Information PDF
Deliver an awe inspiring pitch with this creative infrastructure strategies it infrastructure optimization ppt icon information pdf bundle. Topics like identity and access management, data protection and recovery, security process, management process and governance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
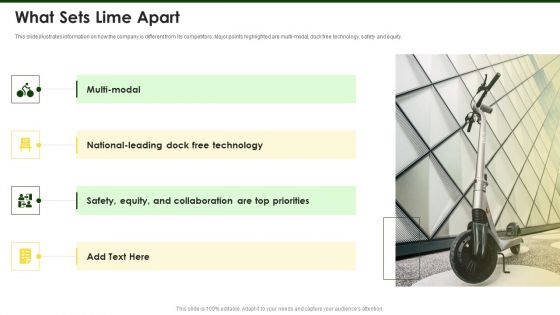
Lime Investor Fundraising Elevator What Sets Lime Apart Ppt File Example Topics PDF
This slide illustrates information on how the company is different from its competitors. Major points highlighted are multi-modal, dock free technology, safety and equity. Deliver and pitch your topic in the best possible manner with this lime investor fundraising elevator what sets lime apart ppt file example topics pdf. Use them to share invaluable insights on multi modal, national leading dock free technology, safety, equity, collaboration top priorities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
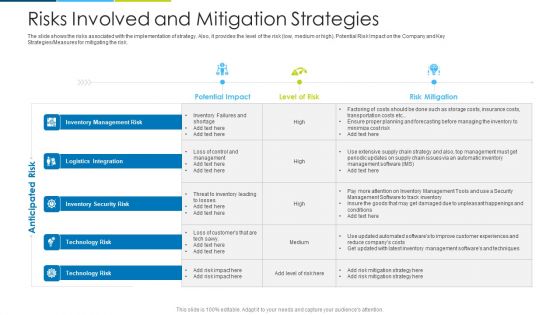
Risks Involved And Mitigation Strategies Ppt Design Templates PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, Potential Risk Impact on the Company and Key Strategies or Measures for mitigating the risk. Deliver an awe inspiring pitch with this creative risks involved and mitigation strategies ppt design templates pdf bundle. Topics like inventory management risk, inventory management risk, inventory security risk, technology risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
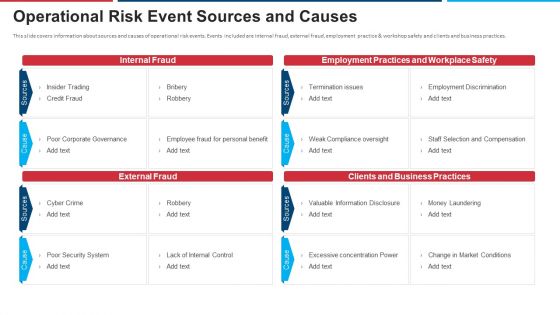
Mitigation Strategies For Operational Threat Operational Risk Event Sources And Causes Ppt Inspiration Introduction PDF
This slide covers information about sources and causes of operational risk events. Events included are internal fraud, external fraud, employment practice and workshop safety and clients and business practices. Deliver an awe inspiring pitch with this creative mitigation strategies for operational threat operational risk event sources and causes ppt inspiration introduction pdf bundle. Topics like internal fraud, external fraud, employment practices and workplace safety, clients and business practices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Healthcare Hospital Performance Data Scorecard With Financial Perspective Ppt Portfolio Tips PDF
Deliver and pitch your topic in the best possible manner with this Healthcare Hospital Performance Data Scorecard With Financial Perspective Ppt Portfolio Tips PDF. Use them to share invaluable insights on Increase Hospital Revenue, Growth Financial Perspective, Administered Medication Safety and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
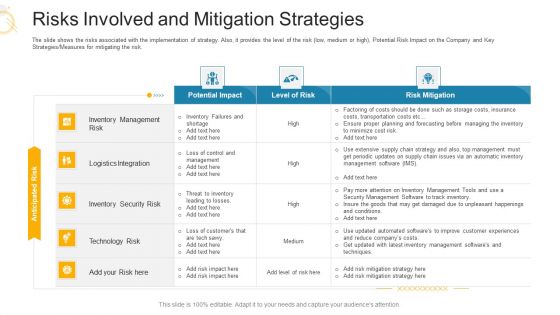
Risks Involved And Mitigation Strategies Ppt Professional Graphics PDF
The slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, Potential Risk Impact on the Company and Key Strategies Measures for mitigating the risk. Deliver and pitch your topic in the best possible manner with this risks involved and mitigation strategies ppt professional graphics pdf. Use them to share invaluable insights on inventory management risk, technology, automated softwares, inventory security, planning and forecasting and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Assessment And Mitigation Plan Strategies To Overcome Labor Shortages Ppt Portfolio Shapes PDF
This slide shows key strategies to overcome labor shortages. It covers expanding recruitment drive, labor safety improvement, process automation and other financial incentives to enhance labor retention. Presenting risk assessment and mitigation plan strategies to overcome labor shortages ppt portfolio shapes pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like construction material, prioritize labor safety, offer financial incentives, expand recruitment drive, automate processes, increase connectivity, better retention. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Governance And Risk Tokenization Strategies For Data Security PPT Sample
This slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization. Boost your pitch with our creative Governance And Risk Tokenization Strategies For Data Security PPT Sample. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Latest Market Trend Prevailing In Construction Industry Ppt PowerPoint Presentation Gallery Graphic Images PDF
Pitch your topic with ease and precision using this latest market trend prevailing in construction industry ppt powerpoint presentation gallery graphic images pdf. This layout presents information on more technology integration, increase in modular construction projects, increased safety equipment, increase regulatory burdens, labor crisis. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF
The following slide highlights the six strategies for cyber security threat mitigation illustrating risk assessment, access control, security solution, patch management, traffic monitoring and incident response. Presenting Digital Risk Assessment Threat Mitigation Strategies Ppt Show Images PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Access Control, Patch Management, Security Solution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
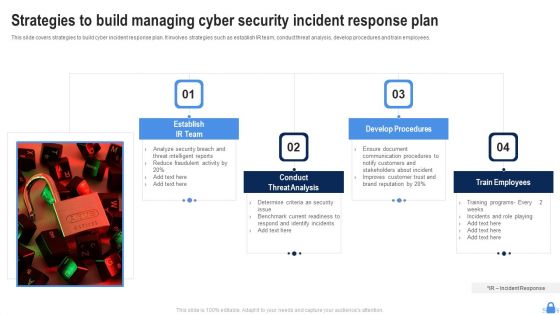
Strategies To Build Managing Cyber Security Incident Response Plan Demonstration PDF
This slide covers strategies to build cyber incident response plan. It involves strategies such as establish IR team, conduct threat analysis, develop procedures and train employees. Persuade your audience using this Strategies To Build Managing Cyber Security Incident Response Plan Demonstration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Establish IR Team, Conduct Threat Analysis, Develop Procedures. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
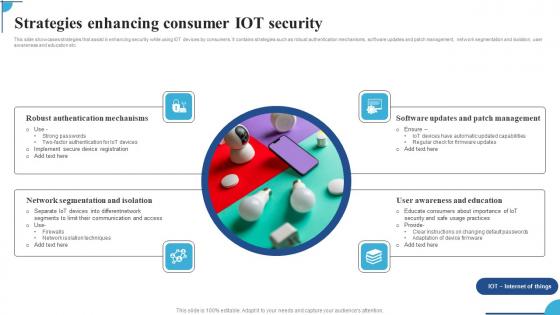
Strategies Enhancing Consumer IOT Security Ppt Pictures Graphic Images Pdf
This slide showcases strategies that assist in enhancing security while using IOT devices by consumers. It contains strategies such as robust authentication mechanisms,software updates and patch management,network segmentation and isolation,user awareness and education etc. Pitch your topic with ease and precision using this Strategies Enhancing Consumer IOT Security Ppt Pictures Graphic Images Pdf. This layout presents information on Robust Authentication Mechanisms,Network Segmentation Isolation,Software Updates. It is also available for immediate download and adjustment. So,changes can be made in the color,design,graphics or any other component to create a unique layout.

Role Of Utility Tokenization Strategies For Data Security PPT Presentation
This slide discusses the objective of utility tokens in block chain. The purpose of this slide is to highlight the role of utility tokens which include decentralized storage, exchange value for service, etc. Find a pre-designed and impeccable Role Of Utility Tokenization Strategies For Data Security PPT Presentation. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Workplace Risk Mitigation Strategies For HR Security Portrait PDF
This slide highlights techniques for minimizing risk factors in the workplace. the purpose of this template is to employ effective strategies for ensuring workforce safety eventually enhancing overall productivity and efficiency. It also provides details regarding the status of performance along with insights. Showcasing this set of slides titled Workplace Risk Mitigation Strategies For HR Security Portrait PDF. The topics addressed in these templates are Risk Assessment Management, Safety Training And Education, Compliance Regulations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Steps Involved In Food Product Effective Strategies For Strengthening Food Ppt Sample
The slide exhibits steps involved in food safety and hygiene evaluation process in an organization. It contains points such as clean, cook, store, separate. There are so many reasons you need a Steps Involved In Food Product Effective Strategies For Strengthening Food Ppt Sample. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

 Home
Home