Safety Improvement Plan

Revolution In Online Business Steps Required To Demonstrating Cybersecurity Risk Mitigation Template PDF
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver and pitch your topic in the best possible manner with this Revolution In Online Business Steps Required To Demonstrating Cybersecurity Risk Mitigation Template PDF. Use them to share invaluable insights on Enforcing Security Policy, Providing Security Appropriate, Funding Mandating Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Strategies To Mitigate Cyber Security Risks Determining Roles And Responsibilities For Risk Handling Ideas PDF
Presenting this set of slides with name strategies to mitigate cyber security risks determining roles and responsibilities for risk handling ideas pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management and executive, line management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
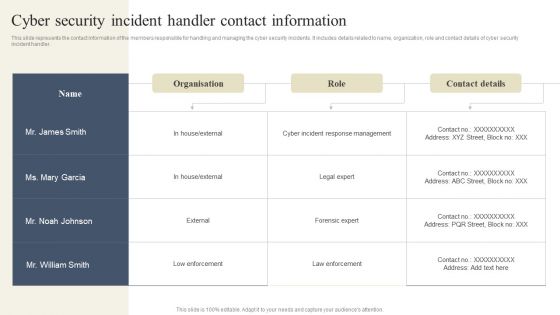
CYBER Security Breache Response Strategy Cyber Security Incident Handler Contact Information Summary PDF
This slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. Slidegeeks is here to make your presentations a breeze with CYBER Security Breache Response Strategy Cyber Security Incident Handler Contact Information Summary PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Strategies To Mitigate Cyber Security Risks Selecting Security Incident Management Software Ppt Styles Influencers PDF
Presenting this set of slides with name strategies to mitigate cyber security risks selecting security incident management software ppt styles influencers pdf. This is a one stage process. The stages in this process are security incident forms, automated workflows, centralized platform, access rights, api integration, information security prevention, cost. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
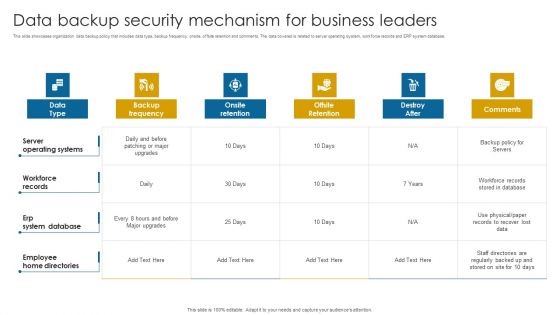
Data Backup Security Mechanism For Business Leaders Infographics PDF
This slide showcases organization data backup policy that includes data type, backup frequency, onsite, offsite retention and comments. The data covered is related to server operating system, workforce records and ERP system database.Showcasing this set of slides titled Data Backup Security Mechanism For Business Leaders Infographics PDF. The topics addressed in these templates are Operating Systems, Workforce Records, Employee Home Directories. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Prevention Of Information Evaluating IT System Security Using Swot Analysis Download PDF today and make your presentation stand out from the rest

Certified Information Systems Security Professional Cissp Examination Details Elements PDF
This slide covers information about CISSP Examination such as weight of each domain in exams, prep courses details, qualification details etc. Deliver an awe inspiring pitch with this creative certified information systems security professional cissp examination details elements pdf bundle. Topics like requirements, network security, security engineering, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
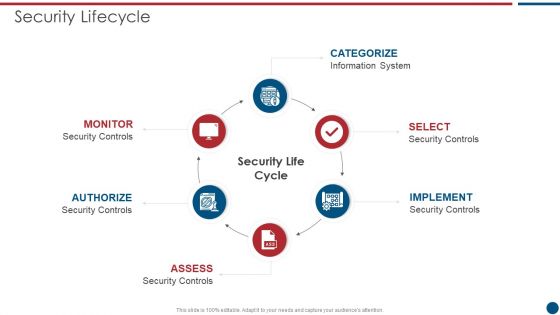
Risk Based Procedures To IT Security Security Lifecycle Ppt PowerPoint Presentation File Rules PDF
This is a Risk Based Procedures To IT Security Security Lifecycle Ppt PowerPoint Presentation File Rules PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information System, Security Controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategies To Mitigate Cyber Security Risks Business Impact Assessment Ppt Pictures Summary PDF
Presenting this set of slides with name strategies to mitigate cyber security risks business impact assessment ppt pictures summary pdf. This is a three stage process. The stages in this process are strengths, weaknesses, loss impact, primary business function, bcp representative, number employees, executive dexter hastings, department, function. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
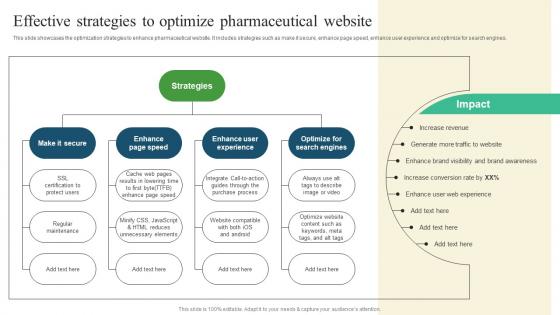
Effective Strategies To Optimize Pharmaceutical Promotional Strategies To Drive Business Sale Download Pdf
This slide showcases the optimization strategies to enhance pharmaceutical website. It includes strategies such as make it secure, enhance page speed, enhance user experience and optimize for search engines. If you are looking for a format to display your unique thoughts, then the professionally designed Effective Strategies To Optimize Pharmaceutical Promotional Strategies To Drive Business Sale Download Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Effective Strategies To Optimize Pharmaceutical Promotional Strategies To Drive Business Sale Download Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Locked Money Business PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Locked Money Business PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Security PowerPoint Templates because this diagram provides range of options to garner your interest. Download our Future PowerPoint Templates because let this slide illustrates others piggyback on you to see well over the horizon. Download our Government PowerPoint Templates because this Diagram pinpoints the critical paths and areas in your process and set the timelines for their completion. Download and present our Money PowerPoint Templates because Our PowerPoint Templates and Slides will provide weight to your words. They will bring out the depth of your thought process. Present our Finance PowerPoint Templates because you envisage some areas of difficulty in the near future. The overall financial situation could be a source of worry.Use these PowerPoint slides for presentations relating to Secure money price lock, security, future, government, money, finance. The prominent colors used in the PowerPoint template are Green, Brown, Gray. Professionals tell us our Locked Money Business PowerPoint Templates PPT Backgrounds For Slides 1212 provide great value for your money. Be assured of finding the best projection to highlight your words. Use our security PowerPoint templates and PPT Slides are Fabulous. We assure you our Locked Money Business PowerPoint Templates PPT Backgrounds For Slides 1212 are Romantic. We assure you our finance PowerPoint templates and PPT Slides are Dynamic. Presenters tell us our Locked Money Business PowerPoint Templates PPT Backgrounds For Slides 1212 are Flirty. PowerPoint presentation experts tell us our government PowerPoint templates and PPT Slides are Awesome.
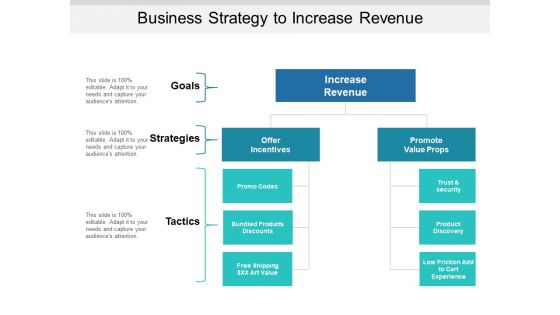
Business Strategy To Increase Revenue Ppt PowerPoint Presentation Pictures Show PDF
Presenting this set of slides with name business strategy to increase revenue ppt powerpoint presentation pictures show pdf. This is a five stage process. The stages in this process are increase revenue, offer, incentives, promote, value props, promo codes, bundled products discounts, free shipping, trust And security, product discovery, low friction add to cart experience. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
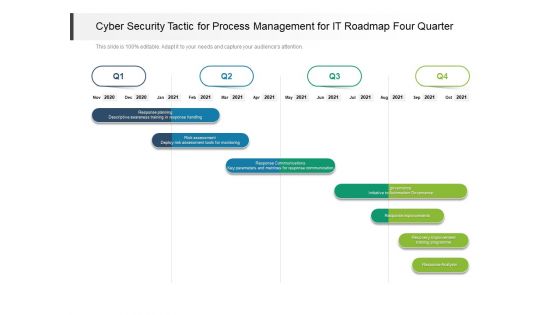
Cyber Security Tactic For Process Management For IT Roadmap Four Quarter Pictures
Presenting our innovatively structured cyber security tactic for process management for it roadmap four quarter pictures Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Tools Used In Cloud Security Cloud Computing Security IT Ppt Background Images PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. This is a tools used in cloud security cloud computing security it ppt background images pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like silver sky, centrify, doc tracker, proofpoint, whitehat. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Knowledge Management System Structure Ppt Powerpoint Image
This is a knowledge management system structure ppt powerpoint image. This is a three stage process. The stages in this process are knowledge delivery, access control, application methods, storage and security, knowledge creation, processing for acquisition, manipulation and modeling, creation of kdb, identification of knowledge, definition and categorization, surveying and locating, build knowledge structure, kms.
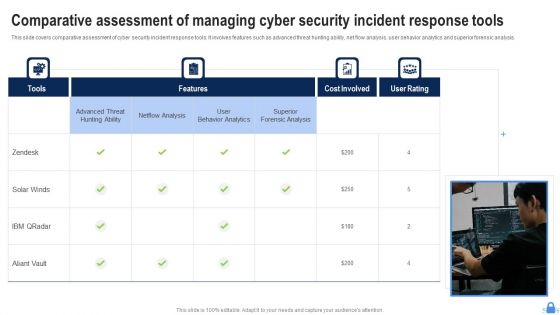
Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF
This slide covers comparative assessment of cyber security incident response tools. It involves features such as advanced threat hunting ability, net flow analysis, user behavior analytics and superior forensic analysis. Presenting Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Superior Forensic Analysis, User Behavior Analytics, Netflow Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Program Evaluation Templates Bundle Security Checklist Ppt Outline Graphics Tutorials PDF
Deliver and pitch your topic in the best possible manner with this program evaluation templates bundle security checklist ppt outline graphics tutorials pdf. Use them to share invaluable insights on project it project, human threats, general threats and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Key Rewards And Recognition Strategies For Employee Growth Ppt PowerPoint Presentation Icon Graphics Design PDF
Persuade your audience using this key rewards and recognition strategies for employee growth ppt powerpoint presentation icon graphics design pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including health insurance, social security, on job training, pay raise, achievement awards, employee allowance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
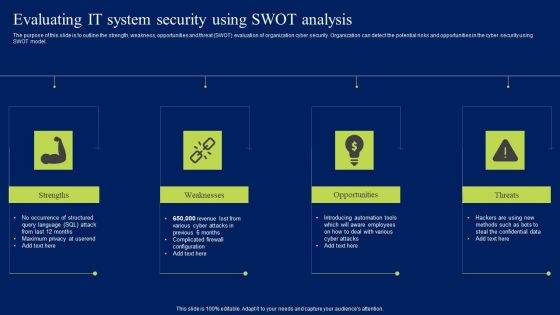
Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF
The purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Evaluating IT System Security Using Swot Analysis Ppt Pictures Clipart Images PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Core Team Online Medication Management Platform Pitch Deck
This slide provides information regarding key leaders involved in investment decisions. It includes founder, chief executive officer, and corporate security. Find highly impressive Core Team Online Medication Management Platform Pitch Deck on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Core Team Online Medication Management Platform Pitch Deck for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Quarterly Cybersecurity Training Program And Assessment Schedule Sheet Elements PDF
This slide covers annual awareness training program schedule for employees. It includes training for network security, cyber security fundamentals, insider threats, malicious code, etc.Showcasing this set of slides titled Quarterly Cybersecurity Training Program And Assessment Schedule Sheet Elements PDF. The topics addressed in these templates are Insider Threats, Network Security, Risk Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Picture Showing Man With Digital Binary Code Language Ppt PowerPoint Presentation File Outline PDF
Persuade your audience using this picture showing man with digital binary code language ppt powerpoint presentation file outline pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including picture showing man with digital binary code language. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Ensure Security And Access Controls Ppt PowerPoint Presentation Portfolio Images
This is a ensure security and access controls ppt powerpoint presentation portfolio images. This is a two stage process. The stages in this process are icons, strategy, business, management, marketing.
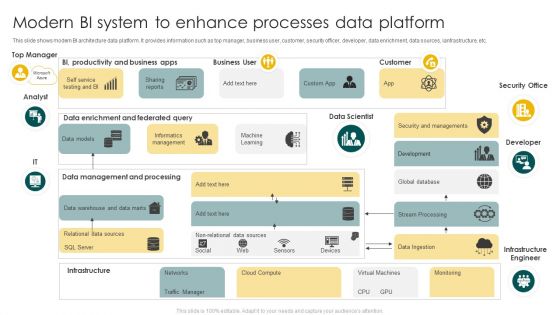
Modern BI System To Enhance Processes Data Platform Ppt Summary Shapes PDF
This slide shows modern BI architecture data platform. It provides information such as top manager, business user, customer, security officer, developer, data enrichment, data sources, ianfrastructure, etc. Presenting Modern BI System To Enhance Processes Data Platform Ppt Summary Shapes PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Business User, Customer, Security Office. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF
This slide shows insider threat detection process flow. It contains information such as administrator, personal devices, behavior, detection system, behavior analysis, security auditing, terminating user access, etc. Presenting Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Authentication, Insider Attacker, Administrator, Controlled Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Analysis Summary Chart Presentation Images
This is a security analysis summary chart presentation images. This is a one stage process. The stages in this process are ev ebitda, ev sales, div yield, open, pt close, high, low, mcap, eps.

Data Breach Prevention Strategies For Enterprises Data Fortification Strengthening Defenses
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Breach Prevention Strategies For Enterprises Data Fortification Strengthening Defenses. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Dollar Bills Locked With Chain Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Dollar Bills Locked With Chain Security PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Security PowerPoint Templates because You should Throw the gauntlet with our PowerPoint Templates and Slides. They are created to take up any challenge. Present our Chains PowerPoint Templates because You can Score a slam dunk with our PowerPoint Templates and Slides. Watch your audience hang onto your every word. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides offer you the widest possible range of options. Download and present our Money PowerPoint Templates because Our PowerPoint Templates and Slides will give you great value for your money. Be assured of finding the best projection to highlight your words. Present our Finance PowerPoint Templates because You can Bask in the warmth of our PowerPoint Templates and Slides. Enjoy the heartfelt glowing response of your listeners.Use these PowerPoint slides for presentations relating to Dollar bill locked with lock, security, chains, business, money, finance. The prominent colors used in the PowerPoint template are Yellow, Gray, Black.
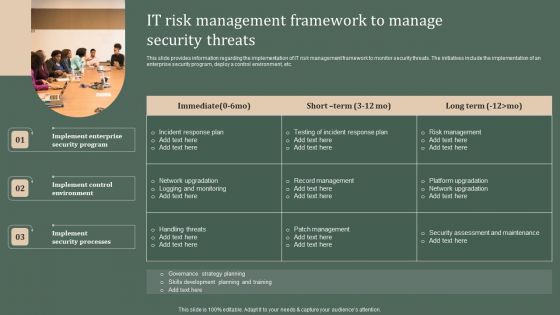
Deploying Corporate Aligned IT Strategy IT Risk Management Framework To Manage Security Threats Pictures PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Create an editable Deploying Corporate Aligned IT Strategy IT Risk Management Framework To Manage Security Threats Pictures PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Deploying Corporate Aligned IT Strategy IT Risk Management Framework To Manage Security Threats Pictures PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF today and make your presentation stand out from the rest.
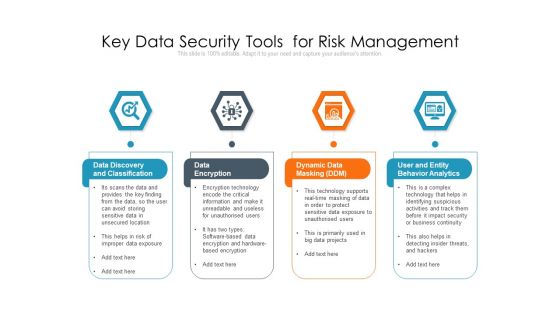
Key Data Security Tools For Risk Management Ppt PowerPoint Presentation Outline Guide PDF
Persuade your audience using this key data security tools for risk management ppt powerpoint presentation outline guide pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including data discovery and classification, data encryption, dynamic data masking ddm, user and entity behavior analytics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Us Dollars Chained And Locked Saving PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our US Dollars Chained And Locked Saving PowerPoint Templates PPT Backgrounds For Slides 1212.Present our Money PowerPoint Templates because to achieve sureshot success you need to come together at the right time, place and manner. Download and present our Finance PowerPoint Templates because let this slide illustrates others piggyback on you to see well over the horizon. Use our Security PowerPoint Templates because the gears of youthful minds are useful, therefore set them in motion. Use our Business PowerPoint Templates because project your ideas to you colleagues and complete the full picture. Download and present our Success PowerPoint Templates because the success of your venture depends on the performance of every team member.Use these PowerPoint slides for presentations relating to Us dollars chained and locked, money, finance, security, business, success. The prominent colors used in the PowerPoint template are Yellow, Gray, Black. Customers tell us our US Dollars Chained And Locked Saving PowerPoint Templates PPT Backgrounds For Slides 1212 are Reminiscent. Presenters tell us our security PowerPoint templates and PPT Slides are Perfect. Use our US Dollars Chained And Locked Saving PowerPoint Templates PPT Backgrounds For Slides 1212 are Clever. PowerPoint presentation experts tell us our business PowerPoint templates and PPT Slides are Precious. Customers tell us our US Dollars Chained And Locked Saving PowerPoint Templates PPT Backgrounds For Slides 1212 are Stylish. Presenters tell us our locked PowerPoint templates and PPT Slides are readymade to fit into any presentation structure.

Successful Corporate Technique Enhancing Firms Performance Role Of Management In Security Governance Across Firm Background PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Get a simple yet stunning designed Successful Corporate Technique Enhancing Firms Performance Role Of Management In Security Governance Across Firm Background PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Successful Corporate Technique Enhancing Firms Performance Role Of Management In Security Governance Across Firm Background PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Website Programming IT What Is The Cyber Security Ppt PowerPoint Presentation Gallery Example File PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks. This is a website programming it what is the cyber security ppt powerpoint presentation gallery example file pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect information, digital assets, computers, servers, mobile devices, networks, and resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
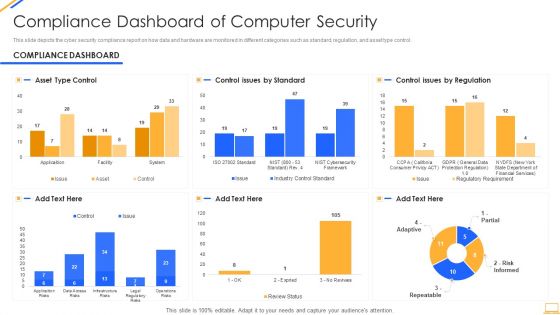
Desktop Security Management Compliance Dashboard Of Computer Security Graphics PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative desktop security management compliance dashboard of computer security graphics pdf bundle. Topics like compliance dashboard of computer security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Two Golden Keys With Words Business PowerPoint Templates And PowerPoint Themes 1012
Two Golden Keys With Words Business PowerPoint Templates And PowerPoint Themes 1012-Create visually stunning Microsoft office PPT Presentations with our above template consists of two golden keys with business words. This image depicts the business concept. Adjust the above image in your PPT presentations to visually support your content in your Leadership and teamwork PPT slideshows security, strategy and success. Create captivating presentations to deliver comparative and weighted arguments.-Two Golden Keys With Words Business PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Two golden keys with words, security, success, business, marketing, finance

Cybersecurity Compliance Dashboard Of Electronic Information Security Ppt Outline Graphic Tips PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative cybersecurity compliance dashboard of electronic information security ppt outline graphic tips pdf bundle. Topics like compliance dashboard of electronic information security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Smartphone Operating System Development IT Top Benefits Of Ios App Development For Business Infographics PDF
This slide depicts the top benefits of iOS app development for business, including high security, upgraded user experience, increased return on investment, etc.Presenting smartphone operating system development it top benefits of ios app development for business infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like high security, increased return on investment, upgraded user experience In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Formation Of Acquired Entities Security Ppt PowerPoint Presentation Portfolio Images
Presenting this set of slides with name formation of acquired entities security ppt powerpoint presentation portfolio images. This is a four stage process. The stages in this process are formation, entities, business, development, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
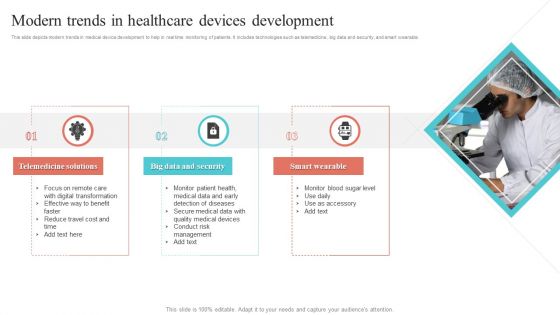
Modern Trends In Healthcare Devices Development Ppt Infographic Template Styles PDF
This slide depicts modern trends in medical device development to help in real time monitoring of patients. It includes technologies such as telemedicine, big data and security, and smart wearable. Showcasing this set of slides titled Modern Trends In Healthcare Devices Development Ppt Infographic Template Styles PDF. The topics addressed in these templates are Telemedicine Solutions, Big, Data And Security, Smart Wearable. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

AIOPS Implementation Artificial Intelligence For IT Operations In Financial Services Portrait PDF
This slide represents the application of AIOps in financial service that includes defending against complex cybercrimes, analyzing past customer information, data security and regulatory compliance, and so on. Presenting AIOPS Implementation Artificial Intelligence For IT Operations In Financial Services Portrait PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Customer Expectations, Mobile And Digital Banking, Business Opportunities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
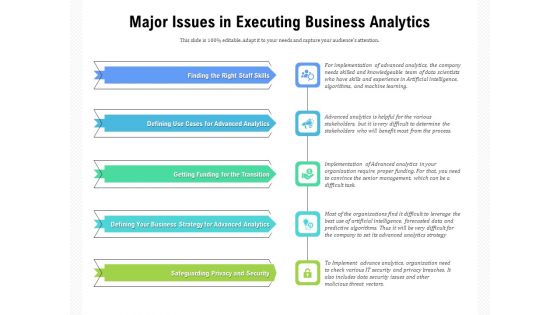
Major Issues In Executing Business Analytics Ppt PowerPoint Presentation Infographic Template Ideas PDF
Persuade your audience using this major issues in executing business analytics ppt powerpoint presentation infographic template ideas pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including finding the right staff skills, defining use cases for advanced analytics, getting funding for the transition, safeguarding privacy and security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
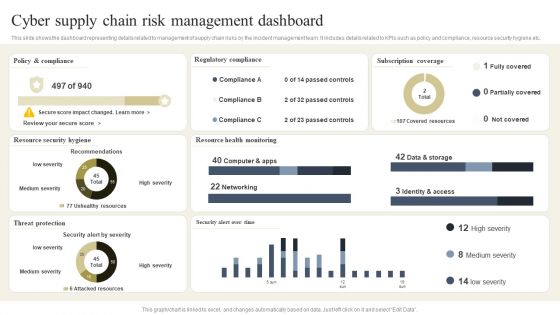
CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. The CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Six Months Security Business Growth Assessment Roadmap Topics
Presenting our jaw-dropping six months security business growth assessment roadmap topics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.

Three Months Security Business Growth Assessment Roadmap Formats
Presenting our jaw-dropping three months security business growth assessment roadmap formats. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.

Checklist For Responding To A Data Breach Attack Data Breach Prevention Microsoft Pdf
This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Responding To A Data Breach Attack Data Breach Prevention Microsoft Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
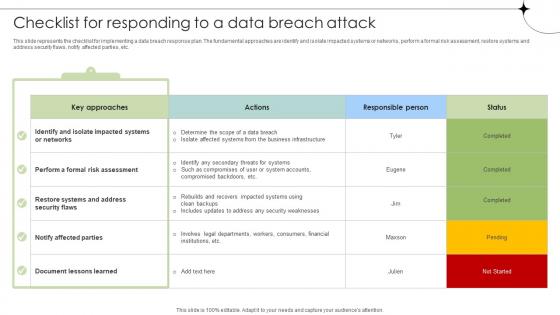
Checklist For Responding To A Data Breach Attack Data Fortification Strengthening Defenses
This slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Checklist For Responding To A Data Breach Attack Data Fortification Strengthening Defenses will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Market Growth Of Information Security Industry Cybersecurity Risk Assessment Portrait PDF
This slide showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compounded annual growth rate of industry. Do you know about Slidesgeeks Market Growth Of Information Security Industry Cybersecurity Risk Assessment Portrait PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Integrating Data Privacy System Five Data Privacy Rules Ppt Outline Show PDF
This slide outlines the five data privacy rules, which are consent, purpose, disposal and destruction, access and security, accountability and disclosure. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Integrating Data Privacy System Five Data Privacy Rules Ppt Outline Show PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides
Using this ready-made PowerPoint slide, you can incorporate your own data to make an impact with your business innovation and clarity of goals. Use this brilliantly designed Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides to showcase how ultimately all business concepts are related. This presentation template can also be used to record resource allocation in a visual form. The twenty one Slide Workplace Security Management Program Ppt PowerPoint Presentation Complete Deck With Slides is suitable for all your business needs, where you need to make sure that all bases are covered. Download this PPT template now to start a journey on your chosen business, with customer satisfaction the key aim.

Profitability Comparison Of Business Investments In Securities Ppt PowerPoint Presentation Outline Deck PDF
This slide shows graphical report to analyze market timing and fluctuations in returns to gain maximum from the funds invested in share market. It includes details about most profitable ones, average and least growth. Pitch your topic with ease and precision using this Profitability Comparison Of Business Investments In Securities Ppt PowerPoint Presentation Outline Deck PDF. This layout presents information on Most Profitable, Least Profitable, Least Profitable. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Strategies To Mitigate Cyber Security Risks Backup Maintenance Developing Alternate Sites Ppt Templates PDF
Presenting this set of slides with name strategies to mitigate cyber security risks backup maintenance developing alternate sites ppt templates pdf. This is a five stage process. The stages in this process are cold sites, hot sites, warm sites, mobile site, mirrored site. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Project Change Management Team Org Chart Strategies For Success In Digital
This slide represents details related to org chart of project change management team. It includes details related to steering committee, sponsor, project security officer, etc. Presenting this PowerPoint presentation, titled Project Change Management Team Org Chart Strategies For Success In Digital, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Project Change Management Team Org Chart Strategies For Success In Digital. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Project Change Management Team Org Chart Strategies For Success In Digital that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
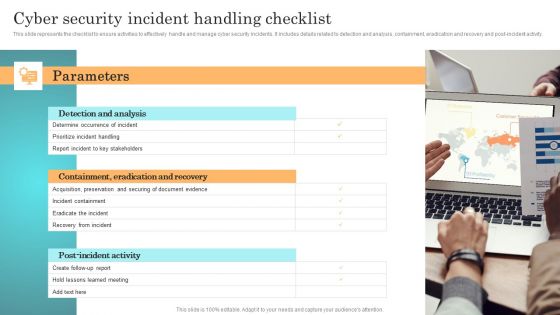
Incident Response Techniques Deployement Cyber Security Incident Handling Checklist Infographics PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF
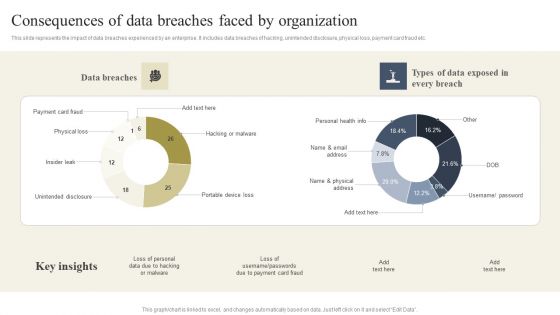
Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Boost your pitch with our creative Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cloud Security Assessment SMB Cloud Security Solutions Diagrams PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment SMB Cloud Security Solutions Diagrams PDF. Use them to share invaluable insights on Cloud Frameworks, Information Division, Cautious Scaling and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Security Challenges Template Powerpoint Templates
This is a data security challenges template powerpoint templates. This is a four stage process. The stages in this process are policy compliance, data management, data privacy, infrastructure security.

Information Technology Job Progression Matrix With Functions Graphics PDF
This slide presents IT career matrix that highlights departmental roles and their required certifications, helpful in determining their importance for organisations. It includes departments such as systems and infrastructure, network security and software development. Showcasing this set of slides titled Information Technology Job Progression Matrix With Functions Graphics PDF. The topics addressed in these templates are Systems And Infrastructure, Network Security, Software Development. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Implementation Framework Determining Firm Current Capabilities Ppt Outline Shapes PDF
Presenting this set of slides with name cyber security implementation framework determining firm current capabilities ppt outline shapes pdf. The topics discussed in these slides are identify, protect, detect, response, recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Access Regulations Technology Five Years Roadmap With Security Solution Inspiration
Presenting our innovatively structured access regulations technology five years roadmap with security solution inspiration Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

 Home
Home