Safety Improvement Plan

Secure Six Steps Of Growth With Report Analysis Template PDF
Presenting secure six steps of growth with report analysis template pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including inventory, analysis, global. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Organizing Security Awareness Security Awareness Training Program Challenges Formats PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Organizing Security Awareness Security Awareness Training Program Challenges Formats PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Methods To Develop Cybersecurity Monitoring Best Practices To Be Followed By The Company Demonstration PDF
This slide provides information about some of the best practices related to security monitoring that must be followed by the company. Presenting methods to develop cybersecurity monitoring best practices to be followed by the company demonstration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like practice description, gather monitoring data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Piggy Over A Stack Of Books PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Piggy Over A Stack Of Books PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Education PowerPoint Templates because It is Aesthetically crafted by artistic young minds. Our PowerPoint Templates and Slides are designed to display your dexterity. Download our Future PowerPoint Templates because Our PowerPoint Templates and Slides are the chords of your song. String them along and provide the lilt to your views. Use our Success PowerPoint Templates because Our PowerPoint Templates and Slides will let your team Walk through your plans. See their energy levels rise as you show them the way. Download and present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Present our Finance PowerPoint Templates because our PowerPoint Templates and Slides are the string of your bow. Fire of your ideas and conquer the podium.Use these PowerPoint slides for presentations relating to Piggy bank over a stack of colorful books, education, future, success, security, finance. The prominent colors used in the PowerPoint template are Green, Red, Green. You can be sure our Piggy Over A Stack Of Books PowerPoint Templates PPT Backgrounds For Slides 0113 are visually appealing. Use our colorful PowerPoint templates and PPT Slides look good visually. You can be sure our Piggy Over A Stack Of Books PowerPoint Templates PPT Backgrounds For Slides 0113 will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Customers tell us our books PowerPoint templates and PPT Slides have awesome images to get your point across. People tell us our Piggy Over A Stack Of Books PowerPoint Templates PPT Backgrounds For Slides 0113 are designed by professionals People tell us our over PowerPoint templates and PPT Slides are topically designed to provide an attractive backdrop to any subject.
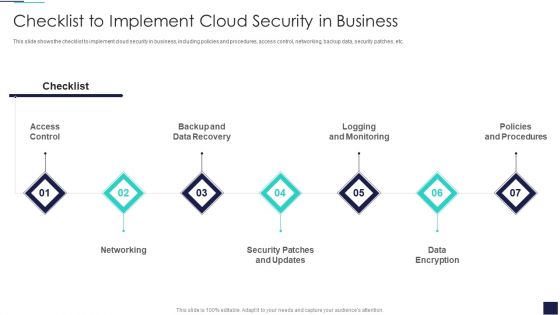
Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. This is a Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Policies And Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
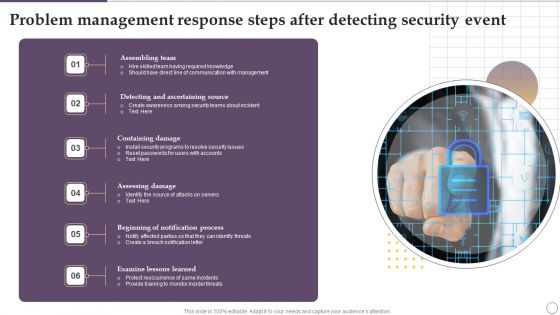
Problem Management Response Steps After Detecting Security Event Ppt Outline Brochure PDF
Presenting Problem Management Response Steps After Detecting Security Event Ppt Outline Brochure PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Assembling Team, Containing Damage, Assessing Damage, Examine Lessons Learned. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Based Procedures To IT Security Categorization Worksheet For Assets Owned By Organization Microsoft PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Categorization Worksheet For Assets Owned By Organization Microsoft PDF. Use them to share invaluable insights on Server Computer, System Location, System Accessibility and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
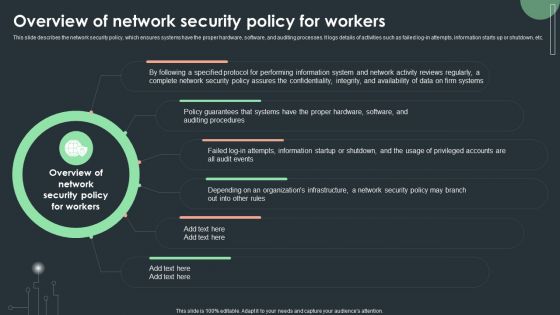
Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Boost your pitch with our creative Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Global Spending On Industrial Internet Of Things Technologies Elements PDF
This slide depicts the global spending on the industrial internet of things technologies from 2019 to 2027. The market is segmented as IoT security, IoT hardware, IoT services, IoT software and total. Boost your pitch with our creative Global Spending On Industrial Internet Of Things Technologies Elements PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
Biometric Lock Vector Icon Ppt PowerPoint Presentation Outline Gallery
Presenting this set of slides with name biometric lock vector icon ppt powerpoint presentation outline gallery. This is a one stage process. The stage in this process is biometric lock vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cryptocurrency Digital Lock Vector Icon Ppt PowerPoint Presentation Infographics Outline
Presenting this set of slides with name cryptocurrency digital lock vector icon ppt powerpoint presentation infographics outline. This is a one stage process. The stage in this process is cryptocurrency digital lock vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Benefits Of Desktop As A Service With Operational Savings Ppt PowerPoint Presentation Gallery Visual Aids PDF
Persuade your audience using this benefits of desktop as a service with operational savings ppt powerpoint presentation gallery visual aids pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including operational savings, better security, business continuity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Camera System Company Profile Executive Leadership And Management Team Designs PDF
This slide highlights the security company leadership and management team which includes president CEO, executive vice president of finance, EVP home security, chief administration officer. This is a Security Camera System Company Profile Executive Leadership And Management Team Designs PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Business Security, Southern University, Management Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Find The Right Key Of Success In Business PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Find The Right Key Of Success In Business PowerPoint Templates PPT Backgrounds For Slides 0413.Download and present our Security PowerPoint Templates because They will Put your wonderful verbal artistry on display. Our PowerPoint Templates and Slides will provide you the necessary glam and glitter. Download and present our Success PowerPoint Templates because They will Put the wind in your sails. Skim smoothly over the choppy waters of the market. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are aesthetically designed to attract attention. We gaurantee that they will grab all the eyeballs you need. Download our Future PowerPoint Templates because Our PowerPoint Templates and Slides will definately Enhance the stature of your presentation. Adorn the beauty of your thoughts with their colourful backgrounds. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will weave a web of your great ideas. They are gauranteed to attract even the most critical of your colleagues.Use these PowerPoint slides for presentations relating to Success team innovation vision influence strategy key, security, success, business, future, shapes. The prominent colors used in the PowerPoint template are Black, Orange, Yellow.

Cyber Security Tactic For Process Management For IT Roadmap Five Year Designs
We present our cyber security tactic for process management for it roadmap five year designs. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cyber security tactic for process management for it roadmap five year designs in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Asset Identification For Information Security Risk Management Cybersecurity Risk Assessment Inspiration PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help form to monitor the asset in real time for any data breach or cyber attack. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 parcent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Asset Identification For Information Security Risk Management Cybersecurity Risk Assessment Inspiration PDF from Slidegeeks and deliver a wonderful presentation.

Features Of Successful Banking Application Development Ppt Example PDF
This slide provide various feature of a successful banking application to transfer funds to third party without any inconvenience. It includes elements such as bank account management, advanced security, core features and inbuilt chatbot. Persuade your audience using this Features Of Successful Banking Application Development Ppt Example PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Bank Account Management, Advanced Security, Core Features, Inbuilt Chatbot. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icons Slide For Risk Based Procedures To IT Security Ppt PowerPoint Presentation Gallery Vector PDF
Presenting our innovatively structured Icons Slide For Risk Based Procedures To IT Security Ppt PowerPoint Presentation Gallery Vector PDF set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.

Insider Threat In Cyber Security Protection Process With Defensive Controls Template PDF
This slide shows insider threat protection process with usage of defensive controls. It provides information about indicators, prevent, detect, respond, recruitment, scouting, collection, elimination, etc. Showcasing this set of slides titled Insider Threat In Cyber Security Protection Process With Defensive Controls Template PDF. The topics addressed in these templates are Recruitment, Scouting, Collection, Elimination. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
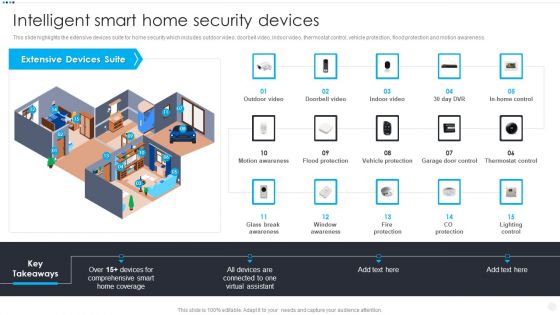
Smart Home Security Solutions Company Profile Intelligent Smart Home Security Devices Inspiration PDF
This slide highlights the extensive devices suite for home security which includes outdoor video, doorbell video, indoor video, thermostat control, vehicle protection, flood protection and motion awareness. Deliver an awe inspiring pitch with this creative Smart Home Security Solutions Company Profile Intelligent Smart Home Security Devices Inspiration PDF bundle. Topics like Extensive Devices Suite, Comprehensive Smart Home, Glass Break Awareness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
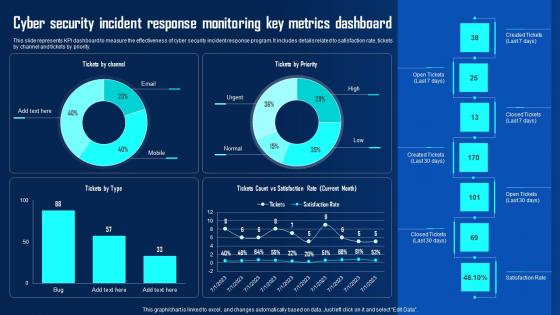
Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf
This slide represents KPI dashboard to measure the effectiveness of cyber security incident response program. It includes details related to satisfaction rate, tickets by channel and tickets by priority. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Incident Response Monitoring Key Ppt Powerpoint Presentation File Example File Pdf

Product Launch Process With Marketing Strategy Ppt PowerPoint Presentation Model Microsoft PDF
Presenting this set of slides with name product launch process with marketing strategy ppt powerpoint presentation model microsoft pdf. This is a six stage process. The stages in this process are evaluate the value and market potential of the product, choosing the right development team, building an effective marketing strategy, validate and ensure security, show and tell about the product. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
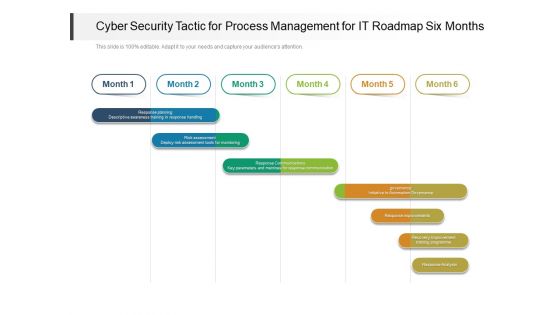
Cyber Security Tactic For Process Management For IT Roadmap Six Months Clipart
Presenting the cyber security tactic for process management for it roadmap six months clipart. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Advantages And Working Of Secure SDLC Phases Of Software Development Procedure Professional PDF
This slide represents the advantages and working of secure software development life cycle, including its various phases, such as concept, planning, design and development, testing, release, sustain, and disposal.Create an editable Advantages And Working Of Secure SDLC Phases Of Software Development Procedure Professional PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Advantages And Working Of Secure SDLC Phases Of Software Development Procedure Professional PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Next Steps For Security Camera Services One Pager Sample Example Document
This slide indicates the next steps to execute post acceptance of business proposal with signatures of both project lead and client. Presenting you an exemplary Next Steps For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Next Steps For Security Camera Services One Pager Sample Example Document brilliant piece now.

Statistics Of Cloud Data Security Client Side Encryption PPT Slide
This slide summarizes data security attacks across different organizational departments, such as sales, IT department, finance, marketing, operations, etc. The outlined attacks are data interception, unauthorized access, data breaches, etc. This Statistics Of Cloud Data Security Client Side Encryption PPT Slide from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Securing Market Leadership Through Competitive Excellence Pros And Cons Of Red Ocean Strategy Microsoft PDF
The following slide exhibits the advantages and disadvantages of red ocean strategy. The advantages mentioned in the slide are no need to create new marketplace, high demand of products and services etc. The disadvantages are difficult to survive in the existing market, no extraordinary profits etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Securing Market Leadership Through Competitive Excellence Pros And Cons Of Red Ocean Strategy Microsoft PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Securing Market Leadership Through Competitive Excellence Pros And Cons Of Red Ocean Strategy Microsoft PDF today and make your presentation stand out from the rest.
Confidential Computing Performance Tracking Dashboard Secure Multi Party Portrait Pdf
This slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Confidential Computing Performance Tracking Dashboard Secure Multi Party Portrait Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Cyber Security Risk Management Icon In IT Risk Control Strategies Sample PDF
Showcasing this set of slides titled Cyber Security Risk Management Icon In IT Risk Control Strategies Sample PDF. The topics addressed in these templates are Cyber Security, Risk Management, Icon, IT Risk, Control Strategies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Global Internet Of Things Security Technology Market Infographics Pdf
The following slide provides an overview of global IoT cybersecurity market in different geographical areas that helps to understand the rapid growth of IoT in multiple domains. The different regions are North America, Europe, Asia Pacific, etc. Showcasing this set of slides titled Global Internet Of Things Security Technology Market Infographics Pdf The topics addressed in these templates are Cyber Security, Market Size, Technology Market All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Roles And Responsibilities Of Digitization Of Security Systems Team Graphics PDF
The following slide highlights key responsibilities of the digitization of security systems team with the position level and requirements. The various positions mentioned in the slide are security engineer, senior security engineer, distinguished security engineer and digitization of security systems manager. Showcasing this set of slides titled Roles And Responsibilities Of Digitization Of Security Systems Team Graphics PDF. The topics addressed in these templates are Security Engineer, Senior Security Engineer, Security Automation Manager. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
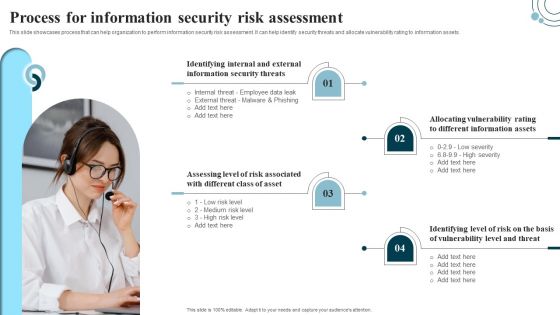
Developing IT Security Strategy Process For Information Security Risk Assessment Graphics PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Developing IT Security Strategy Process For Information Security Risk Assessment Graphics PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Developing IT Security Strategy Process For Information Security Risk Assessment Graphics PDF.
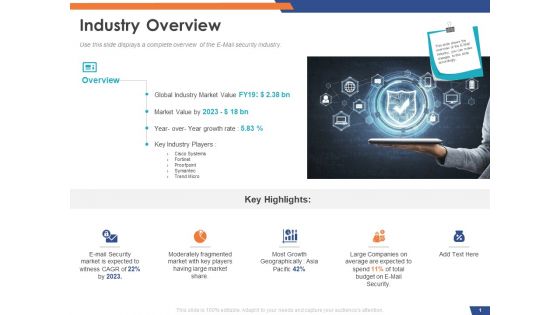
Email Security Market Research Report Industry Overview Ppt Outline Graphic Images PDF
Presenting this set of slides with name email security market research report industry overview ppt outline graphic images pdf. This is a two stage process. The stages in this process are moderately fragmented market with key players having large market share, global industry market value, key industry players. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Types Security Threats Organizations Ppt PowerPoint Presentation Layouts Designs Cpb
Presenting this set of slides with name types security threats organizations ppt powerpoint presentation layouts designs cpb. This is an editable Powerpoint four stages graphic that deals with topics like types security threats organizations to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Cyber Security Implementation Framework Staff Training Schedule With Cost Ppt PowerPoint Presentation Pictures Slideshow PDF
Presenting this set of slides with name cyber security implementation framework staff training schedule with cost ppt powerpoint presentation pictures slideshow pdf. This is a one stage process. The stages in this process are advanced skills training, advanced software training, training module, supplier relationship management, risk management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Scan Principle For Smart Phone Security Model Clipart PDF
This slide shows SCAN framework for securing phone against possible threats to prevent loss of business data. It include components such as system, configuration, application and network, etc. Persuade your audience using this Scan Principle For Smart Phone Security Model Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including System, Configuration, App. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
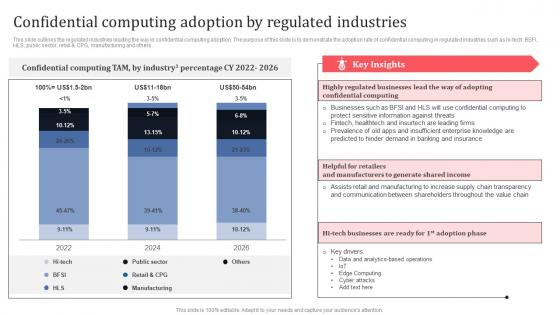
Confidential Computing Adoption By Regulated Industries Secure Multi Party Professional Pdf
This slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Get a simple yet stunning designed Confidential Computing Adoption By Regulated Industries Secure Multi Party Professional Pdf It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Confidential Computing Adoption By Regulated Industries Secure Multi Party Professional Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Security KPI Dashboard With Various Charts And Graphs Ppt Summary Background Image PDF
Persuade your audience using this Security KPI Dashboard With Various Charts And Graphs Ppt Summary Background Image PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Various Charts, Security KPI Dashboard, Graphs. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Network Threat Prevention And Security Vector Icon Ppt PowerPoint Presentation Outline Example Introduction PDF
Presenting network threat prevention and security vector icon ppt powerpoint presentation outline example introduction pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including network threat prevention and security vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
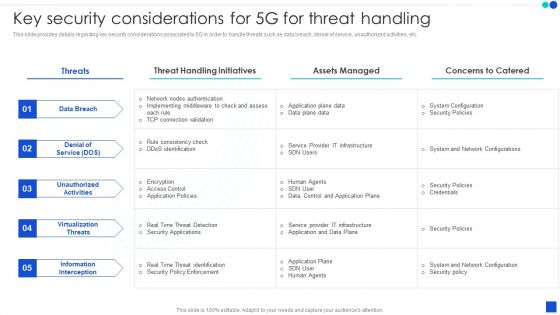
5G Technology Development For Digital Transformation Key Security Considerations For 5G For Threat Handling Themes PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download 5G Technology Development For Digital Transformation Key Security Considerations For 5G For Threat Handling Themes PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the 5G Technology Development For Digital Transformation Key Security Considerations For 5G For Threat Handling Themes PDF.

Developing IT Security Strategy Checklist For Information Security Risk Management Pictures PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Explore a selection of the finest Developing IT Security Strategy Checklist For Information Security Risk Management Pictures PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Developing IT Security Strategy Checklist For Information Security Risk Management Pictures PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Key To Growing Business Success PowerPoint Templates Ppt Backgrounds For Slides 0413
We present our Key To Growing Business Success PowerPoint Templates PPT Backgrounds For Slides 0413.Download and present our Security PowerPoint Templates because It will Raise the bar of your Thoughts. They are programmed to take you to the next level. Download and present our Future PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Download our Success PowerPoint Templates because Our PowerPoint Templates and Slides are created with admirable insight. Use them and give your group a sense of your logical mind. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience. Use our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides team portray an attitude of elegance. Personify this quality by using them regularly.Use these PowerPoint slides for presentations relating to Concept for business key, security, future, success, business, marketing. The prominent colors used in the PowerPoint template are White, Gray, Black.
Vector Illustration Of IT Security Measures For Strong Protection Ppt PowerPoint Presentation File Outline PDF
Persuade your audience using this vector illustration of it security measures for strong protection ppt powerpoint presentation file outline pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including vector illustration of it security measures for strong protection. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Risk Management Methodology In IT Risk Control Strategies Security Ppt Inspiration Background PDF
This slide focuses on the risk management methodology in information technology security which includes three different phases such as assessment, mitigation and continual evaluation assessment that are helpful in effective management of security risks and hazards. Showcasing this set of slides titled Risk Management Methodology In IT Risk Control Strategies Security Ppt Inspiration Background PDF. The topics addressed in these templates are Assessment, Mitigation, Continual Evaluation Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
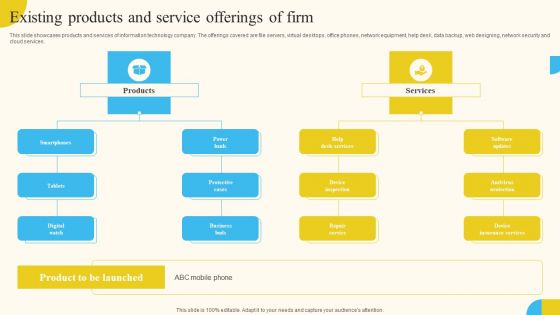
Existing Products And Service Offerings Of Firm Activities For Successful Launch Event Professional PDF
This slide showcases products and services of information technology company. The offerings covered are file servers, virtual desktops, office phones, network equipment, help desk, data backup, web designing, network security and cloud services. Want to ace your presentation in front of a live audience Our Existing Products And Service Offerings Of Firm Activities For Successful Launch Event Professional PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
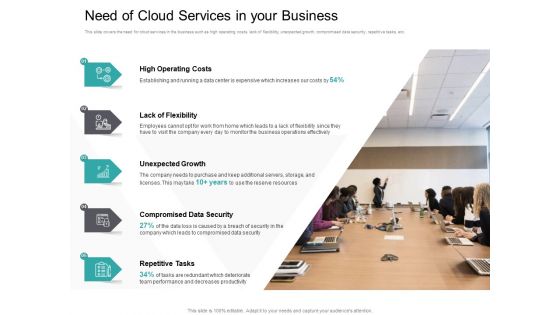
Cloud Based Marketing Need Of Cloud Services In Your Business Ppt PowerPoint Presentation Professional Show PDF
This slide covers the need for cloud services in the business such as high operating costs, lack of flexibility, unexpected growth, compromised data security, repetitive tasks, etc. Presenting cloud based marketing need of cloud services in your business ppt powerpoint presentation professional show pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like high operating costs, lack flexibility, unexpected growth, compromised data security, repetitive tasks. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Silver Trophy Under Safeguard PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Silver Trophy Under Safeguard PowerPoint Templates PPT Backgrounds For Slides 0213.Use our Competition PowerPoint Templates because Our PowerPoint Templates and Slides will let your team Walk through your plans. See their energy levels rise as you show them the way. Present our Security PowerPoint Templates because You are well armed with penetrative ideas. Our PowerPoint Templates and Slides will provide the gunpowder you need. Use our Success PowerPoint Templates because you can Break through with our PowerPoint Templates and Slides. Bring down the mental barriers of your audience. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will give you great value for your money. Be assured of finding the best projection to highlight your words. Use our Signs PowerPoint Templates because You can Be the star of the show with our PowerPoint Templates and Slides. Rock the stage with your ideas.Use these PowerPoint slides for presentations relating to Silver Trophy cup with Life Buoy, competition, business, security, success, signs. The prominent colors used in the PowerPoint template are Red, Gray, White.

Four Computer Security Processes Portrait PDF
This slide shows the four step by step processes used in information technology security. It includes penetration testing, VPN configuration, network security audit checklist and privileged password management. Presenting Four Computer Security Processes Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Penetration Testing, Configuration, Password Management This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Analysis Ppt PowerPoint Presentation Infographics
This is a security analysis ppt powerpoint presentation infographics. This is a two stage process. The stages in this process are business, finance, growth, analysis, success.
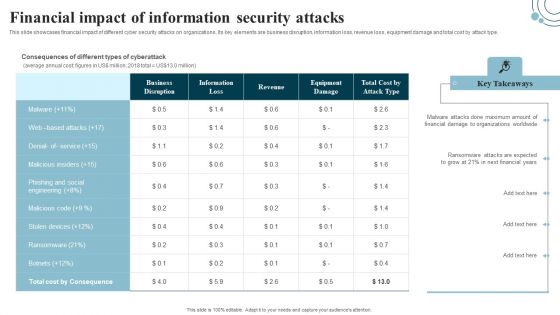
Developing IT Security Strategy Financial Impact Of Information Security Attacks Rules PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type. Boost your pitch with our creative Developing IT Security Strategy Financial Impact Of Information Security Attacks Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
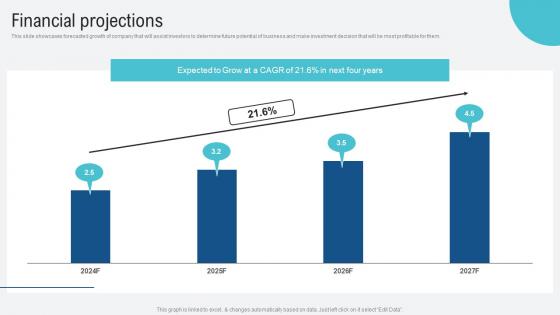
Financial Projections Voice Assistance Security Platform Investor Funding Presentation Ideas Pdf
This slide showcases forecasted growth of company that will assist investors to determine future potential of business and make investment decision that will be most profitable for them. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Financial Projections Voice Assistance Security Platform Investor Funding Presentation Ideas Pdf from Slidegeeks and deliver a wonderful presentation.

Monetary Investment Portfolio Growth And Administration Risk Free Rate Of Return Model Rules PDF
This slide represents risk free rate of return model. It highlights return on investment, portfolio risk, securities, equity, stocks etc. that enable portfolio analysis. Presenting Monetary Investment Portfolio Growth And Administration Risk Free Rate Of Return Model Rules PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Absolute Risk, Relative Risk, Default Risk. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
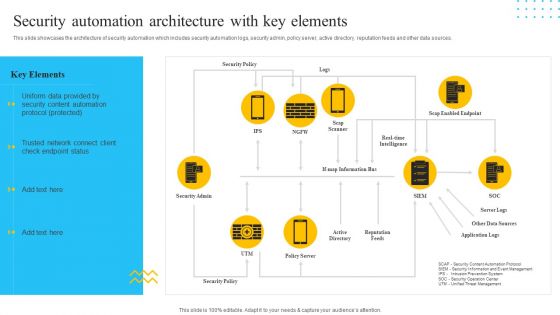
IT Security Automation Tools Integration Security Automation Architecture With Key Elements Mockup PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Presenting IT Security Automation Tools Integration Security Automation Architecture With Key Elements Mockup PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Security Policy, Security Admin, Reputation Feeds. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
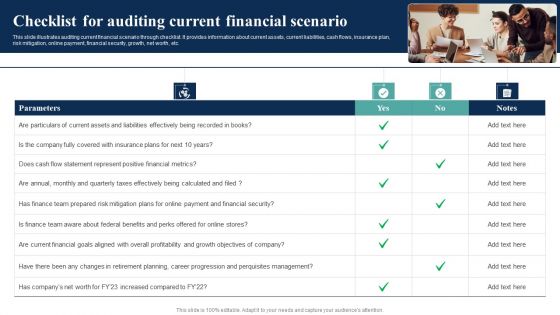
How Electronic Commerce Financial Procedure Can Be Enhanced Checklist For Auditing Current Mockup PDF
This slide illustrates auditing current financial scenario through checklist. It provides information about current assets, current liabilities, cash flows, insurance plan, risk mitigation, online payment, financial security, growth, net worth, etc. Take your projects to the next level with our ultimate collection of How Electronic Commerce Financial Procedure Can Be Enhanced Checklist For Auditing Current Mockup PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they all make your projects stand out from the rest.

Cloud Computing Infrastructure Reference Framework Ppt Layouts Maker PDF
The following slide showcases reference model that provides insight of cloud computing. Main layers covered are service management, business continuity, security, service, control and physical layer. Pitch your topic with ease and precision using this Cloud Computing Infrastructure Reference Framework Ppt Layouts Maker PDF. This layout presents information on Service Management, Operation Management, Portfolio Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V
This slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview Need For Implementing Data Security Across Optimizing Retail Operations With Digital DT SS V.
IT Security Automation Tools Integration Security Automation Stages With Maturity Level Icons PDF
This slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Security Automation Stages With Maturity Level Icons PDF bundle. Topics like Security Automation, Maturity Level, Security Automation, Stages Opportunistic can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing IT Security Strategy Mitigation Strategies To Tackle Information Security Sample PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and maintain reputation of business. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Developing IT Security Strategy Mitigation Strategies To Tackle Information Security Sample PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Developing IT Security Strategy Mitigation Strategies To Tackle Information Security Sample PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
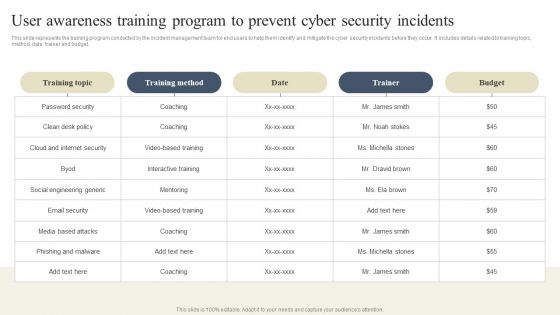
CYBER Security Breache Response Strategy User Awareness Training Program Prevent Cyber Security Incidents Demonstration PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Find a pre designed and impeccable CYBER Security Breache Response Strategy User Awareness Training Program Prevent Cyber Security Incidents Demonstration PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
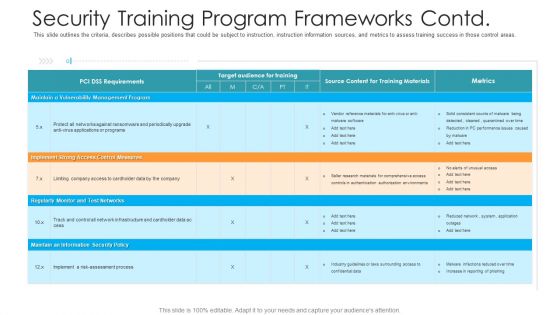
Security Training Program Frameworks Contd Hacking Prevention Awareness Training For IT Security Background PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe inspiring pitch with this creative security training program frameworks contd hacking prevention awareness training for it security background pdf bundle. Topics like management, implement, security policy, monitor can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home