Safety Improvement Plan
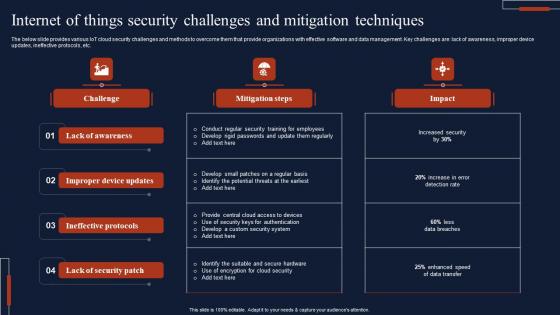
Internet Of Things Security Challenges And Mitigation Techniques Mockup Pdf
The below slide provides various IoT cloud security challenges and methods to overcome them that provide organizations with effective software and data management. Key challenges are lack of awareness, improper device updates, ineffective protocols, etc. Pitch your topic with ease and precision using this Internet Of Things Security Challenges And Mitigation Techniques Mockup Pdf This layout presents information on Lack Of Awareness, Ineffective Protocols, Lack Of Security Patch It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
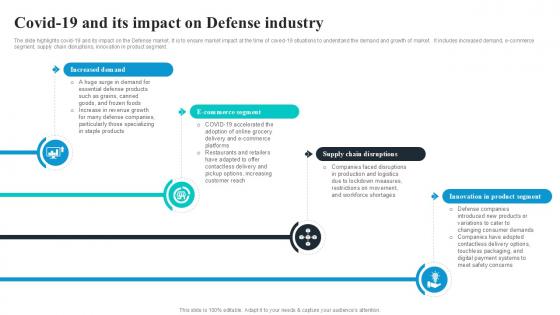
Covid19 And Its Impact On Defense Global Security Industry PPT Example IR SS V
The slide highlights covid-19 and its impact on the Defense market. It is to ensure market impact at the time of coved-19 situations to understand the demand and growth of market. It includes increased demand, e-commerce segment, supply chain disruptions, innovation in product segment. Get a simple yet stunning designed Covid19 And Its Impact On Defense Global Security Industry PPT Example IR SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Covid19 And Its Impact On Defense Global Security Industry PPT Example IR SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Secure Attachment Psychology In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Secure Attachment Psychology In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Secure Attachment Psychology that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Cyber Security Milestones In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Cyber Security Milestones In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Cyber Security Milestones that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
Firewall Security Audit Checklist In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Firewall Security Audit Checklist In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Firewall Security Audit Checklist that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Multiparty Privacy Preserving Computation Architecture Design Secure Multi Party Demonstration Pdf
This slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on. Create an editable Multiparty Privacy Preserving Computation Architecture Design Secure Multi Party Demonstration Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Multiparty Privacy Preserving Computation Architecture Design Secure Multi Party Demonstration Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
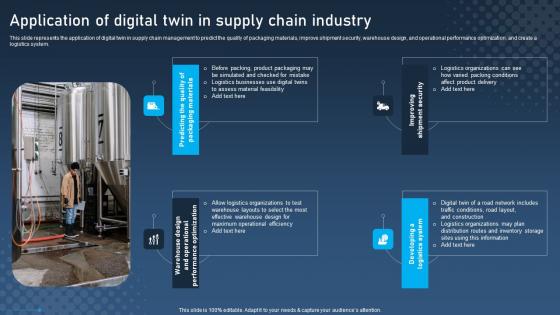
Application Of Digital Twin In Supply Chain Digital Twins For Enhanced Industrial Download Pdf
This slide represents the application of digital twin in supply chain management to predict the quality of packaging materials, improve shipment security, warehouse design, and operational performance optimization, and create a logistics system. Want to ace your presentation in front of a live audience Our Application Of Digital Twin In Supply Chain Digital Twins For Enhanced Industrial Download Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
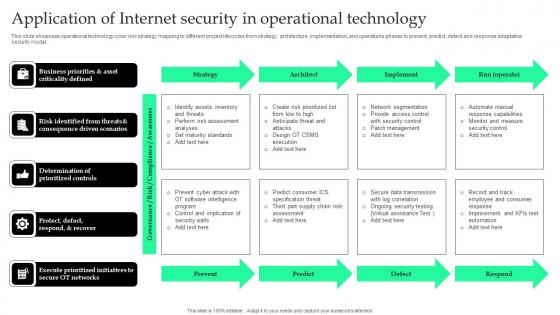
Application Of Internet Security In Operational Technology Pictures Pdf
This slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model.Showcasing this set of slides titled Application Of Internet Security In Operational Technology Pictures Pdf The topics addressed in these templates are Consequence Driven Scenarios, Execute Prioritized, Risk Identified All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

CASB 2 0 IT Cloud Access Security Broker Working Process
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download CASB 2 0 IT Cloud Access Security Broker Working Process to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the CASB 2 0 IT Cloud Access Security Broker Working Process.
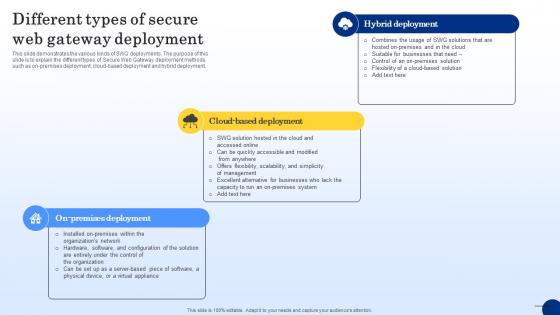
Different Types Of Secure Web Gateway Deployment Web Threat Protection System
This slide demonstrates the various kinds of SWG deployments. The purpose of this slide is to explain the different types of Secure Web Gateway deployment methods such as on-premises deployment, cloud-based deployment and hybrid deployment. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Different Types Of Secure Web Gateway Deployment Web Threat Protection System. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Different Types Of Secure Web Gateway Deployment Web Threat Protection System today and make your presentation stand out from the rest

Key Categories Of Distributed Ledger Security Levels Portrait Pdf
This slide illustrates categories of blockchain security levels aimed at integrating their operations to deliver highest possible security strengthening public confidence. It covers five levels transaction, account, programming, distributed organisations and network Pitch your topic with ease and precision using this Key Categories Of Distributed Ledger Security Levels Portrait Pdf This layout presents information on Transaction Level, Account Level, Programming Level It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Online Payment Techniques Impact Assessment Of Mobile Wallet Application
Mentioned slide provides information about mobile wallet payment implementation impact on business activities. It includes impacts such as easy customer data analytics, offer reward and loyalty points, smooth workflow, and improved security. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Online Payment Techniques Impact Assessment Of Mobile Wallet Application for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
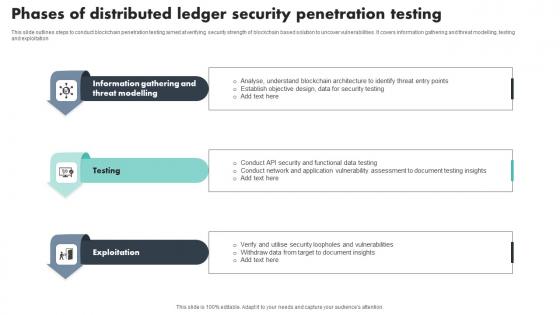
Phases Of Distributed Ledger Security Penetration Testing Download Pdf
This slide outlines steps to conduct blockchain penetration testing aimed at verifying security strength of blockchain based solution to uncover vulnerabilities. It covers information gathering and threat modelling, testing and exploitation Showcasing this set of slides titled Phases Of Distributed Ledger Security Penetration Testing Download Pdf The topics addressed in these templates are Information Gathering, Threat Modelling, Exploitation All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
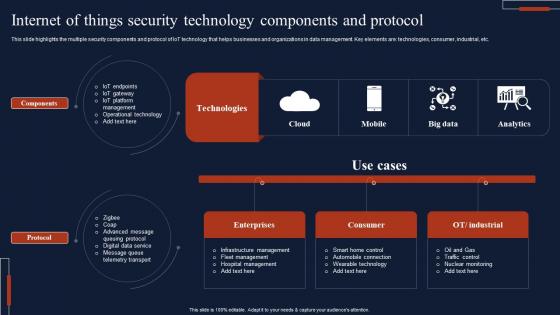
Internet Of Things Security Technology Components And Protocol Rules Pdf
This slide highlights the multiple security components and protocol of IoT technology that helps businesses and organizations in data management. Key elements are technologies, consumer, industrial, etc. Pitch your topic with ease and precision using this Internet Of Things Security Technology Components And Protocol Rules Pdf This layout presents information on Components, Protocol, Technologies, Consumer It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
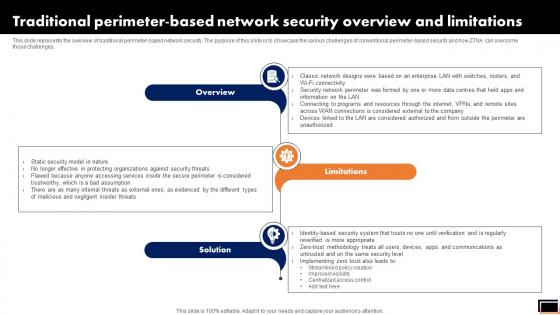
Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. If you are looking for a format to display your unique thoughts, then the professionally designed Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Traditional Perimeter-Based Network Security Overview And Limitations Software Defined Perimeter SDP and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Challenges For New Entrants In Global Security Industry PPT Example IR SS V
The slide showcases the barriers to entry in Defense industry. The main purpose of this slide is to recognize the variables that may impede or make it difficult for new entrants to enter the market successfully. By identifying these impediments, aspiring Defense companies can make educated judgements and establish appropriate strategies to overcome or manage them efficiently. Want to ace your presentation in front of a live audience Our Challenges For New Entrants In Global Security Industry PPT Example IR SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
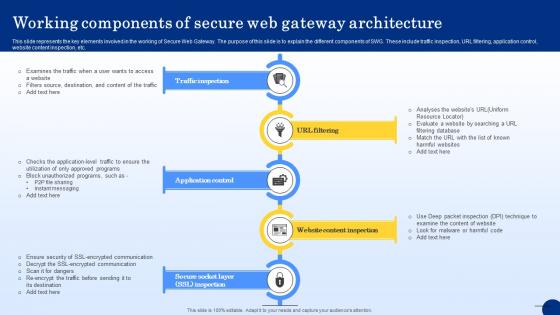
Working Components Of Secure Web Gateway Architecture Web Threat Protection System
This slide represents the key elements involved in the working of Secure Web Gateway. The purpose of this slide is to explain the different components of SWG. These include traffic inspection, URL filtering, application control, website content inspection, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Working Components Of Secure Web Gateway Architecture Web Threat Protection System and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
Lifeshield Security Projects Johannesburg In Powerpoint And Google Slides Cpb
Introducing our well-designed Lifeshield Security Projects Johannesburg In Powerpoint And Google Slides Cpb. This PowerPoint design presents information on topics like Lifeshield Security Projects Johannesburg. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.
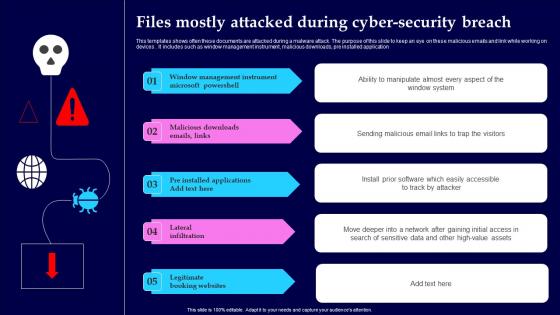
Files Mostly Attacked During Cyber Security Breach Structure Pdf
This templates shows often these documents are attacked during a malware attack. The purpose of this slide to keep an eye on these malicious emails and link while working on devices. It includes such as window management instrument, malicious downloads, pre installed application Showcasing this set of slides titled Files Mostly Attacked During Cyber Security Breach Structure Pdf The topics addressed in these templates are Window Management, Instrument Microsoft, Lateral Infiltration All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Reason For Cyber Security Breach On Target Audience Microsoft Pdf
This templates shows the reason for the malware attack on the target audience. The purpose of this slide to ensure the reason why attacker easily access the software . It includes various challenges such as weak passwords, lack of encryption, backdoors, etc. Showcasing this set of slides titled Reason For Cyber Security Breach On Target Audience Microsoft Pdf The topics addressed in these templates are Weak Passwords, Lack Of Encryption, Backdoors All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
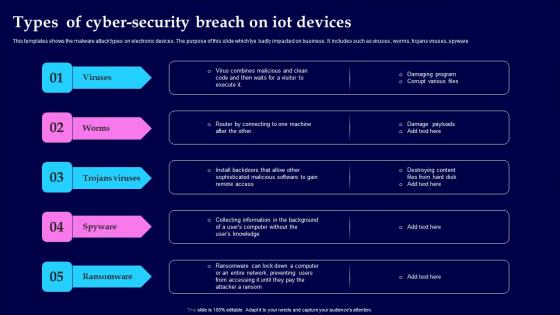
Types Of Cyber Security Breach On IOT Devices Themes Pdf
This templates shows the malware attack types on electronic devices. The purpose of this slide which tye badly impacted on business. It includes such as viruses, worms, trojans viruses, spyware Pitch your topic with ease and precision using this Types Of Cyber Security Breach On IOT Devices Themes Pdf This layout presents information on Viruses, Trojans Viruses, Spyware, Ransomware It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
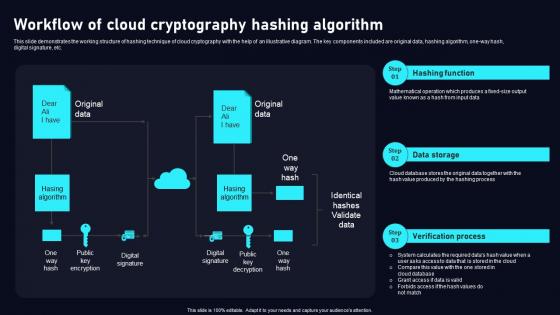
Workflow Of Cloud Cryptography Cloud Data Security Using Cryptography Clipart Pdf
This slide demonstrates the working structure of hashing technique of cloud cryptography with the help of an illustrative diagram. The key components included are original data, hashing algorithm, one way hash, digital signature, etc. Find a pre designed and impeccableWorkflow Of Cloud Cryptography Cloud Data Security Using Cryptography Clipart Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Complete Beginners Guide Popular Types Of Bitcoin Security Frauds Fin SS V
This slide shows information regarding various types of threats associated with Bitcoins security which can result in theft of Bitcoin . These frauds are malware attacks, fake wallets, SIM swapping, phishing attacks, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Complete Beginners Guide Popular Types Of Bitcoin Security Frauds Fin SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Complete Beginners Guide Popular Types Of Bitcoin Security Frauds Fin SS V.

Working Of Common Data Encryption Cloud Data Security Using Cryptography Demonstration Pdf
This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Boost your pitch with our creativeWorking Of Common Data Encryption Cloud Data Security Using Cryptography Demonstration Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
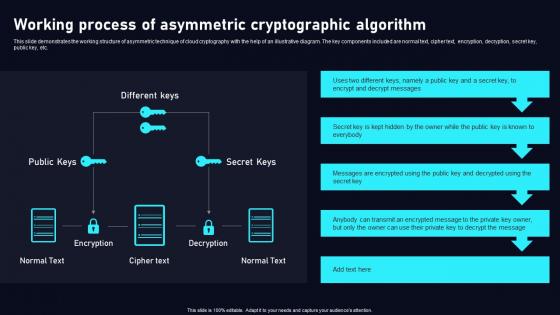
Working Process Of Asymmetric Cloud Data Security Using Cryptography Demonstration Pdf
This slide demonstrates the working structure of asymmetric technique of cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, public key, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulateWorking Process Of Asymmetric Cloud Data Security Using Cryptography Demonstration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
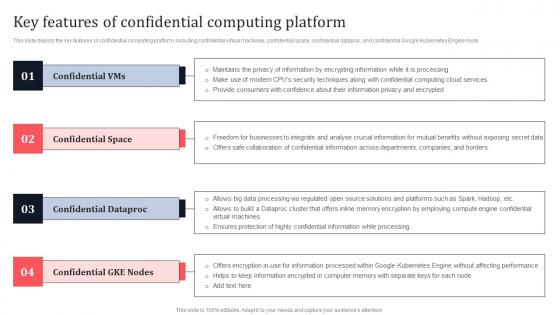
Key Features Of Confidential Computing Platform Secure Multi Party Background Pdf
This slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential Google Kubernetes Engine node. Find a pre-designed and impeccable Key Features Of Confidential Computing Platform Secure Multi Party Background Pdf The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
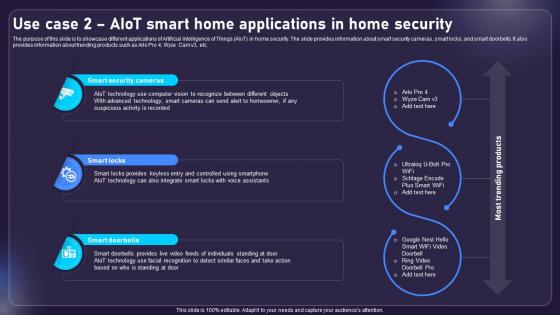
Use Case 2 AIOT Smart Home Applications In Home Security AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to showcase different applications of Artificial Intelligence of Things AIoT in home security. The slide provides information about smart security cameras, smart locks, and smart doorbells. It also provides information about trending products such as Arlo Pro 4, Wyze Cam v3, etc. Slidegeeks has constructed Use Case 2 AIOT Smart Home Applications In Home Security AIOT Applications For Various Industries IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Market Restraints Impacting The Global Security Industry PPT Template IR SS V
The slide provides an insight on the market restraints existing in the Defense market. The purpose of this slide is to aware about the different areas of Defense which are impacted. It capture the information related to short comings faced in the industry. This modern and well-arranged Market Restraints Impacting The Global Security Industry PPT Template IR SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
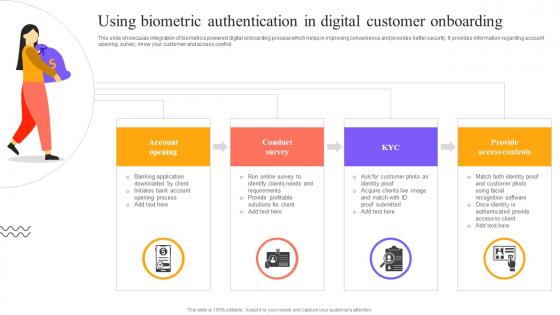
Digital Approach To Client Using Biometric Authentication In Digital Customer Onboarding
This slide showcases integration of biometrics powered digital onboarding process which helps in improving convenience and provides better security. It provides information regarding account opening, survey, know your customer and access control. Take your projects to the next level with our ultimate collection of Digital Approach To Client Using Biometric Authentication In Digital Customer Onboarding. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
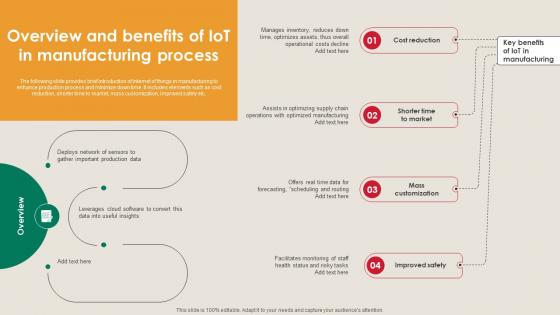
Overview And Benefits Of IoT In Manufacturing Process Manufacturing Strategy Driving Industry 4 0
The following slide provides brief introduction of internet of things in manufacturing to enhance production process and minimize down time. It includes elements such as cost reduction, shorter time to market, mass customization, improved safety etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Overview And Benefits Of IoT In Manufacturing Process Manufacturing Strategy Driving Industry 4 0 for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Overview And Benefits Of IoT In Manufacturing Automating Production Process Strategy SS V
The following slide provides brief introduction of internet of things in manufacturing to enhance production process and minimize down time. It includes elements such as cost reduction, shorter time to market, mass customization, improved safety etc. This modern and well-arranged Overview And Benefits Of IoT In Manufacturing Automating Production Process Strategy SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Overview And Benefits Of IoT In Manufacturing Implementing Manufacturing Strategy SS V
The following slide provides brief introduction of internet of things in manufacturing to enhance production process and minimize down time. It includes elements such as cost reduction, shorter time to market, mass customization, improved safety etc. This modern and well-arranged Overview And Benefits Of IoT In Manufacturing Implementing Manufacturing Strategy SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
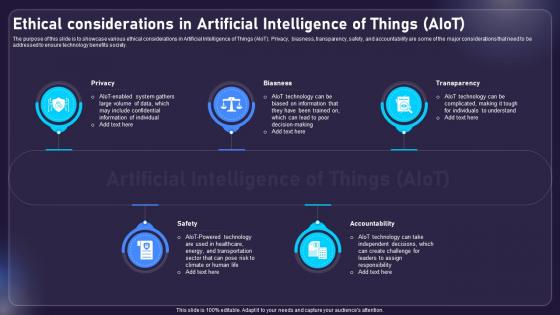
Ethical Considerations In Artificial Intelligence Of Things AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to showcase various ethical considerations in Artificial Intelligence of Things AIoT. Privacy, biasness, transparency, safety, and accountability are some of the major considerations that need to be addressed to ensure technology benefits society. Make sure to capture your audiences attention in your business displays with our gratis customizable Ethical Considerations In Artificial Intelligence Of Things AIOT Applications For Various Industries IoT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
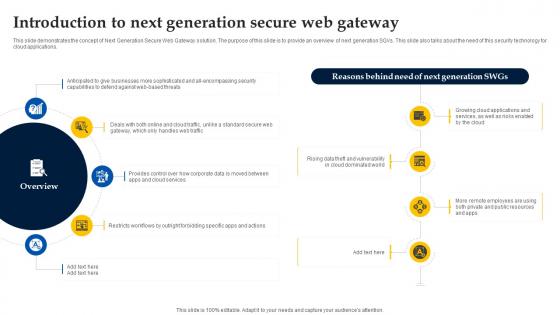
Web Access Control Solution Introduction To Next Generation Secure Web Gateway
This slide demonstrates the concept of Next Generation Secure Web Gateway solution. The purpose of this slide is to provide an overview of next generation SGVs. This slide also talks about the need of this security technology for cloud applications. Are you searching for a Web Access Control Solution Introduction To Next Generation Secure Web Gateway that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Web Access Control Solution Introduction To Next Generation Secure Web Gateway from Slidegeeks today.

Key Elements Of Enterprise Control Structure PDF
This is a key elements of enterprise control structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like enterprise resource planning, environment and safety systems, asset management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Unlocking The Potential Of Ways Blockchain Will Revolutionize Esports Industry BCT SS V
This slide mentions various ways through which blockchain integration will revolutionize esports industry ecosystem. It includes providing decentralized platform, improving trust, levelling playing field, securing payments, securing in app purchases etc. Do you know about Slidesgeeks Unlocking The Potential Of Ways Blockchain Will Revolutionize Esports Industry BCT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
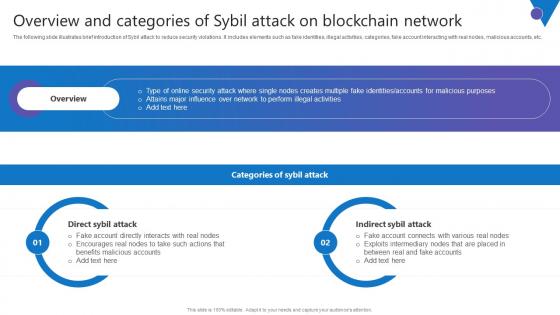
Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf
The following slide illustrates brief introduction of Sybil attack to reduce security violations. It includes elements such as fake identities, illegal activities, categories, fake account interacting with real nodes, malicious accounts, etc. Are you searching for a Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Overview Categories Sybil Comprehensive Guide To Blockchain Digital Security Elements Pdf from Slidegeeks today.

Comprehensive Look At Blockchain Use Cases Of Blockchain In Cybersecurity BCT SS V
This slide highlights various use cases of integrating blockchain technology in cybersecurity. It includes edge computing with authentication, advance confidentiality, secured private messaging, improved PKI and intact domain systems. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Comprehensive Look At Blockchain Use Cases Of Blockchain In Cybersecurity BCT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Comprehensive Look At Blockchain Use Cases Of Blockchain In Cybersecurity BCT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Impact Of 51 Percent Attack Comprehensive Guide To Blockchain Digital Security Infographics Pdf
The following slide depicts the key effect of 51percent attack on bitcoin and blockchain technology to plan actions and minimize its impact. It includes element such as delayed transactions, network disruption, low miner rewards, market volatility, reputation, credibility, etc. Present like a pro with Impact Of 51 Percent Attack Comprehensive Guide To Blockchain Digital Security Infographics Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Impact Of Eclipse Attack Comprehensive Guide To Blockchain Digital Security Demonstration Pdf
The following slide illustrates the impact of eclipse attack on functioning of blockchain network to plan strategies and action steps. It includes elements such as leading to double spending, centralization, disrupting mining power, network instability, monetary loss, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Impact Of Eclipse Attack Comprehensive Guide To Blockchain Digital Security Demonstration Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Impact Of Eclipse Attack Comprehensive Guide To Blockchain Digital Security Demonstration Pdf today and make your presentation stand out from the rest

IAC Governance Policy Principle IAC Tools For Performance Analysis PPT Sample
This slide discusses the governance policies principle framework of infrastructure as code. The purpose of this slide is to outline the principles such as security and compliance management, financial management, operational management, etc. Are you searching for a IAC Governance Policy Principle IAC Tools For Performance Analysis PPT Sample that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download IAC Governance Policy Principle IAC Tools For Performance Analysis PPT Sample from Slidegeeks today.
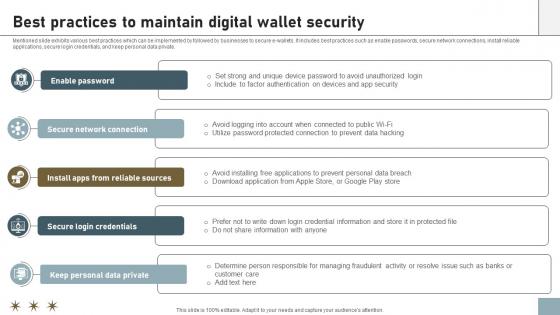
Online Payment Techniques Best Practices To Maintain Digital Wallet Security
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Online Payment Techniques Best Practices To Maintain Digital Wallet Security template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Online Payment Techniques Best Practices To Maintain Digital Wallet Security that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Zero Trust Network Access System Use Cases Software Defined Perimeter SDP
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Are you searching for a Zero Trust Network Access System Use Cases Software Defined Perimeter SDP that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Zero Trust Network Access System Use Cases Software Defined Perimeter SDP from Slidegeeks today.
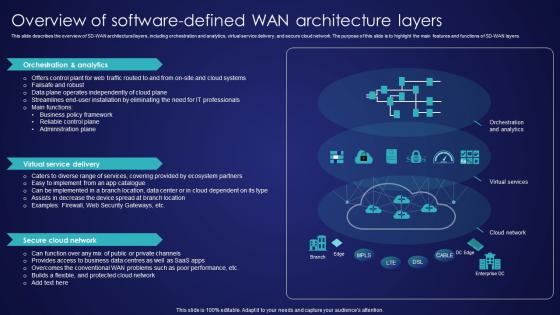
Overview Of Software Defined Wan Architecture Layers Wide Area Network Services Rules Pdf
This slide describes the overview of SD-WAN architectural layers, including orchestration and analytics, virtual service delivery, and secure cloud network. The purpose of this slide is to highlight the main features and functions of SD-WAN layers. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview Of Software Defined Wan Architecture Layers Wide Area Network Services Rules Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview Of Software Defined Wan Architecture Layers Wide Area Network Services Rules Pdf
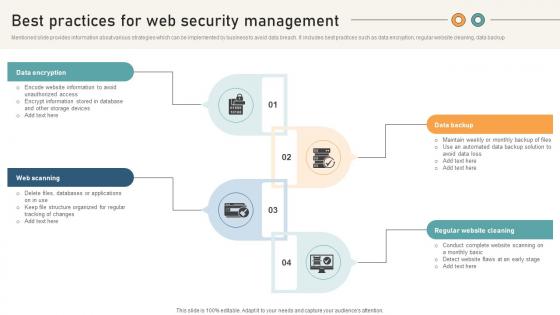
Comprehensive Guide For Website Development Best Practices For Web Security Management
Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup This modern and well-arranged Comprehensive Guide For Website Development Best Practices For Web Security Management provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
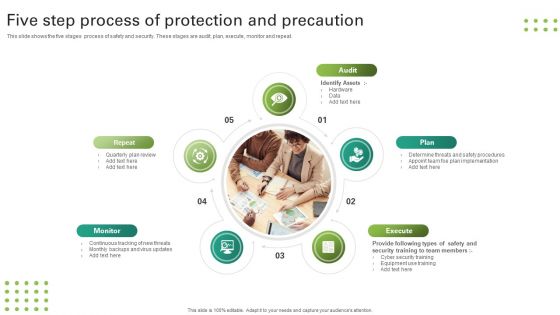
Five Step Process Of Protection And Precaution Formats PDF
This slide shows the five stages process of safety and security. These stages are audit, plan, execute, monitor and repeat. Persuade your audience using this Five Step Process Of Protection And Precaution Formats PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Audit, Plan, Execute. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Need Of Implementing Ble Maximizing Efficiency With Asset Tracking Solutions Themes Pdf
This slide covers key benefits of implementing Bluetooth low energy method in asset tracking and management. It involves advantages such as high return on investment, enhanced security and high broadcast capacity. Are you searching for a Need Of Implementing Ble Maximizing Efficiency With Asset Tracking Solutions Themes Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Need Of Implementing Ble Maximizing Efficiency With Asset Tracking Solutions Themes Pdf from Slidegeeks today.
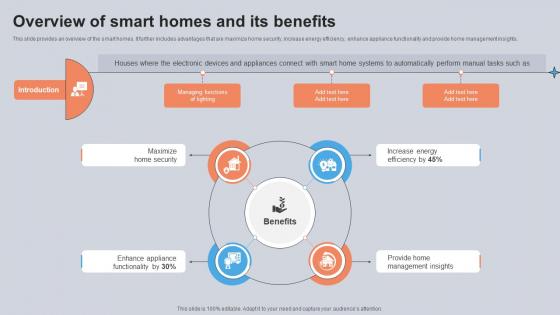
Overview Of Smart Homes And Its Benefits Utilizing Smart Appliances IoT SS V
This slide provides an overview of the smart homes. It further includes advantages that are maximize home security, increase energy efficiency, enhance appliance functionality and provide home management insights. Are you searching for a Overview Of Smart Homes And Its Benefits Utilizing Smart Appliances IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Overview Of Smart Homes And Its Benefits Utilizing Smart Appliances IoT SS V from Slidegeeks today.

Seamless Integration The Power Key Features Of Cross Chain Technology BCT SS V
This slide showcases various key features of cross chain technology aimed for enhancing blockchain interoperability. It includes consistency for accurate network state representation, distribution across platforms, frictionless interoperability, increased security and scalability. Are you searching for a Seamless Integration The Power Key Features Of Cross Chain Technology BCT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Seamless Integration The Power Key Features Of Cross Chain Technology BCT SS V from Slidegeeks today.

Integrating AI With IoT Use Case 2 AIoT Energy Applications In Predictive Maintenance IoT SS V
The purpose of this slide is to showcase Artificial Intelligence of Things AIoT use cases in predictive maintenance that can be helpful in improving equipment reliability and enhanced safety. It also provides information about example of predictive maintenance in energy sector. This Integrating AI With IoT Use Case 2 AIoT Energy Applications In Predictive Maintenance IoT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Integrating AI With IoT Use Case 2 AIoT Energy Applications In Predictive Maintenance IoT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Key Benefits Of Global Positioning System Tech Asset Management Portrait Pdf
This slide covers implementing global positioning system to improves asset management. It involves key benefits such as real time information, saving fuel costs and better safety.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Key Benefits Of Global Positioning System Tech Asset Management Portrait Pdf can be your best option for delivering a presentation. Represent everything in detail using Key Benefits Of Global Positioning System Tech Asset Management Portrait Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Key Features Of Good Crowdfunding Platform Crowdfunding For Nonprofits To Support Fin SS V
This slide shows detailed information regarding the key characteristics a good crowdfunding platform should have. It includes features such as user friendly interface, multiple funding models, secure payment processing, etc. Are you searching for a Key Features Of Good Crowdfunding Platform Crowdfunding For Nonprofits To Support Fin SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Key Features Of Good Crowdfunding Platform Crowdfunding For Nonprofits To Support Fin SS V from Slidegeeks today.
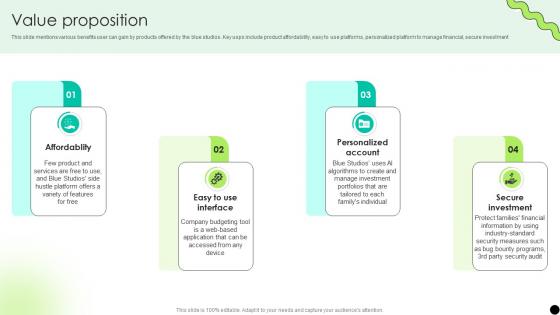
Value Proposition Digital Payment Platform Pitch Deck
This slide mentions various benefits user can gain by products offered by the blue studios. Key usps include product affordability, easy to use platforms, personalized platform to manage financial, secure investment. Welcome to our selection of the Value Proposition Digital Payment Platform Pitch Deck. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
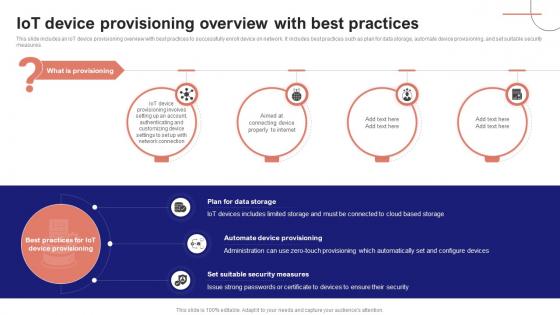
IoT Device Management Fundamentals IoT Device Provisioning Overview With Best Practices IoT Ss V
This slide includes an IoT device provisioning overview with best practices to successfully enroll device on network. It includes best practices such as plan for data storage, automate device provisioning, and set suitable security measures. Whether you have daily or monthly meetings, a brilliant presentation is necessary. IoT Device Management Fundamentals IoT Device Provisioning Overview With Best Practices IoT SS V can be your best option for delivering a presentation. Represent everything in detail using IoT Device Management Fundamentals IoT Device Provisioning Overview With Best Practices IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
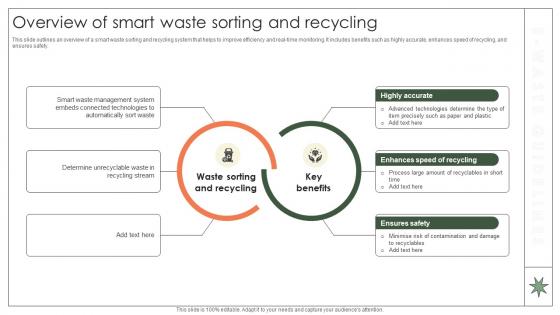
Overview Of Smart Waste Sorting And Recycling Implementation Of E Waste Guidelines
This slide outlines an overview of a smart waste sorting and recycling system that helps to improve efficiency and real-time monitoring. It includes benefits such as highly accurate, enhances speed of recycling, and ensures safety. This Overview Of Smart Waste Sorting And Recycling Implementation Of E Waste Guidelines from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

System Deployment Project Checklist Representing Requirements Of Effective Software Mockup PDF
This slide represents the checklist to analyze the key requirements of an effective software. It includes key requirements such as does system provides AI, applicable safety requirements are identified etc. There are so many reasons you need a System Deployment Project Checklist Representing Requirements Of Effective Software Mockup PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Integrating AI With IoT Use Case 2 AIoT Smart Home Applications In Home Security IoT SS V
The purpose of this slide is to showcase different applications of Artificial Intelligence of Things AIoT in home security. The slide provides information about smart security cameras, smart locks, and smart doorbells. It also provides information about trending products such as Arlo Pro 4, Wyze Cam v3, etc. The Integrating AI With IoT Use Case 2 AIoT Smart Home Applications In Home Security IoT SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
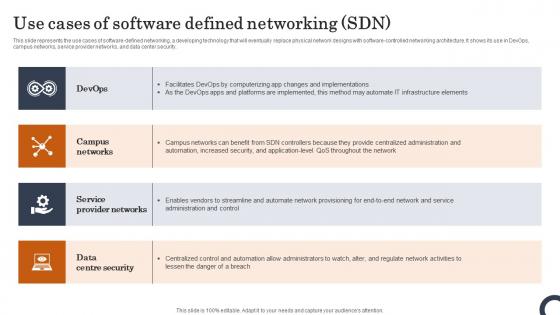
Use Cases Of Software Defined Networking SDN Evolution Of SDN Controllers Download Pdf
This slide represents the use cases of software-defined networking, a developing technology that will eventually replace physical network designs with software-controlled networking architecture. It shows its use in DevOps, campus networks, service provider networks, and data center security. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Use Cases Of Software Defined Networking SDN Evolution Of SDN Controllers Download Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Use Cases Of Software Defined Networking SDN Evolution Of SDN Controllers Download Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Bid Response Management Initial Tender Analysis Ppt PowerPoint Presentation Show Guidelines PDF
Presenting bid response management initial tender analysis ppt powerpoint presentation show guidelines pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like requirement evaluation, quality requirements, health and safety measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
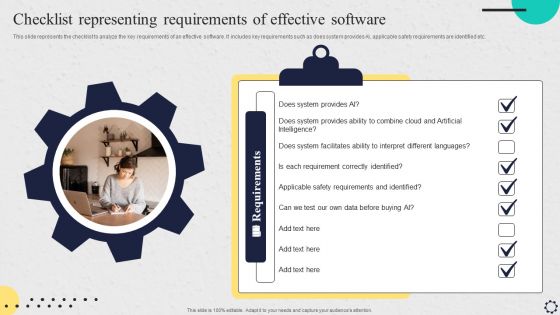
Software Implementation Strategy Checklist Representing Requirements Of Effective Software Portrait PDF
This slide represents the checklist to analyze the key requirements of an effective software. It includes key requirements such as does system provides AI, applicable safety requirements are identified etc. There are so many reasons you need a Software Implementation Strategy Checklist Representing Requirements Of Effective Software Portrait PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

 Home
Home