Safety Dashboard

Seven Steps Of Incident Response Digital Risk Assessment Cycle Ppt Portfolio Introduction PDF
The following slide highlights the sevens steps of incident cyber security cycle illustrating detection, communication channel, impact assessment, communication, escalation, delegation and resolution, Persuade your audience using this Seven Steps Of Incident Response Digital Risk Assessment Cycle Ppt Portfolio Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Resolution, Detection, Communication Channels, Impact Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Internet Of Things Concept Analysis Sample Diagram Sample Of Ppt
This is a internet of things concept analysis sample diagram sample of ppt. This is a seven stage process. The stages in this process are network, business, information, consumers, standards, security, big data.

Business Intelligence And Big Vendor Data Profile For Data Analytics Software Formats PDF
This slide represents the list of vendors along with accompanying information including the key features, pros and cons of each vendor software. Presenting business intelligence and big vendor data profile for data analytics software formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like data support, technology support, predictive applications, reporting features, security features. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
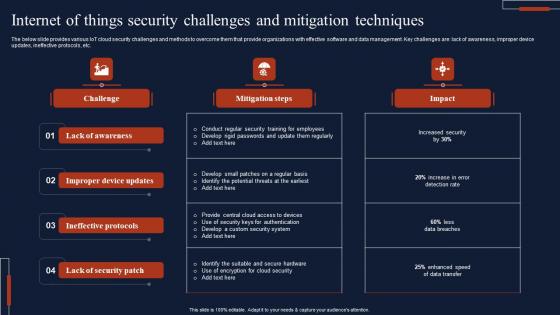
Internet Of Things Security Challenges And Mitigation Techniques Mockup Pdf
The below slide provides various IoT cloud security challenges and methods to overcome them that provide organizations with effective software and data management. Key challenges are lack of awareness, improper device updates, ineffective protocols, etc. Pitch your topic with ease and precision using this Internet Of Things Security Challenges And Mitigation Techniques Mockup Pdf This layout presents information on Lack Of Awareness, Ineffective Protocols, Lack Of Security Patch It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
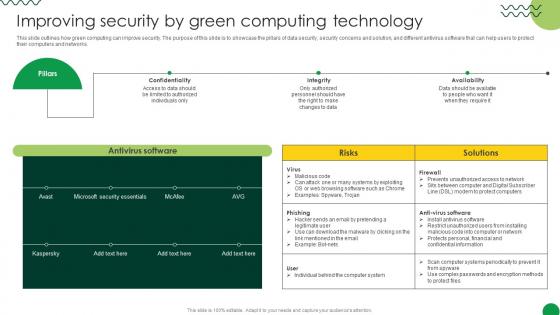
Sustainable Improving Security By Green Computing Technology
This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Create an editable Sustainable Improving Security By Green Computing Technology that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Sustainable Improving Security By Green Computing Technology is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Global Internet Of Things Security Market Spending Download Pdf
This slide represents the global spending on IoT cybersecurity market of five years that provides an overview of rising potential of IoT in terms of data transmission an security. The data of five years is taken into account. Pitch your topic with ease and precision using this Global Internet Of Things Security Market Spending Download Pdf This layout presents information on IOT Security, Market Total, Key Takeaways It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Challenges And Solutions In Data Requirements For Analytics Slides PDF
The following slide indicates multiple challenges in data requirement analysis such as security gaps, complex data system, low quality data etc. With solutions to overcome those challenges. Presenting challenges and solutions in data requirements for analytics slides pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including security gaps, complex data system, low quality data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Management Model For Data Security Risk Reporting And Likelihood Infographics PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Risk Reporting And Likelihood Infographics PDF bundle. Topics like Risk Encountered, Frequency, Attack Scenario, Affected Asset can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
ESO System Icon Ppt PowerPoint Presentation Gallery Slides PDF
Persuade your audience using this ESO System Icon Ppt PowerPoint Presentation Gallery Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including ESO System, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
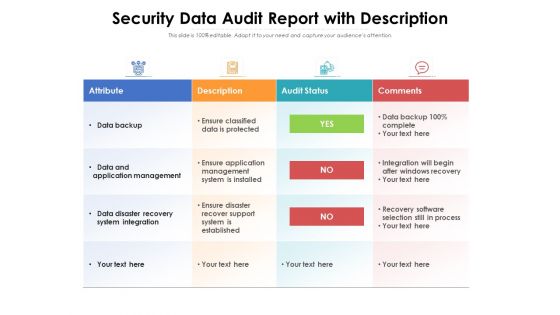
Security Data Audit Report With Description Ppt PowerPoint Presentation Inspiration Example PDF
Showcasing this set of slides titled security data audit report with description ppt powerpoint presentation inspiration example pdf. The topics addressed in these templates are attribute, description, audit status, comments, data backup, data and application management, data disaster recovery system integration. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Various KPI For Cyber Security Breach Worldwide Pictures Pdf
This template shows the various key performance indicators for malware attacks around the world. The purpose of this slide is to evaluated how much devices get affected within 24 hours The various KPI such as streaming, worldwide, mode of attacks, etc. Showcasing this set of slides titled Various KPI For Cyber Security Breach Worldwide Pictures Pdf The topics addressed in these templates are Cyber Security Breach, Worldwide All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

CASB 2 0 IT Cloud Access Security Broker Pillar Overview
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Are you searching for a CASB 2 0 IT Cloud Access Security Broker Pillar Overview that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download CASB 2 0 IT Cloud Access Security Broker Pillar Overview from Slidegeeks today.

Addressing Challenges In IoT Based Satellite Security IoT In Orbit Unleashing The Power IoT SS V
This slide highlights mitigation strategies to address satellite network security challenges to ensure data integrity and safeguarding communication. It includes challenges such as satellite network jamming, device damage, and unauthorized access. Find a pre-designed and impeccable Addressing Challenges In IoT Based Satellite Security IoT In Orbit Unleashing The Power IoT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

CASB 2 0 IT Cloud Access Security Broker CASB Introduction
This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. This CASB 2 0 IT Cloud Access Security Broker CASB Introduction is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The CASB 2 0 IT Cloud Access Security Broker CASB Introduction features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Methods To Implement Security Policies On Web Threat Protection System
This slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc. Are you searching for a Methods To Implement Security Policies On Web Threat Protection System that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Methods To Implement Security Policies On Web Threat Protection System from Slidegeeks today.
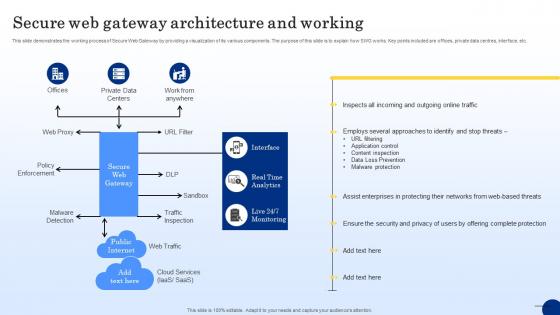
Secure Web Gateway Architecture And Working Web Threat Protection System
This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. This Secure Web Gateway Architecture And Working Web Threat Protection System from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
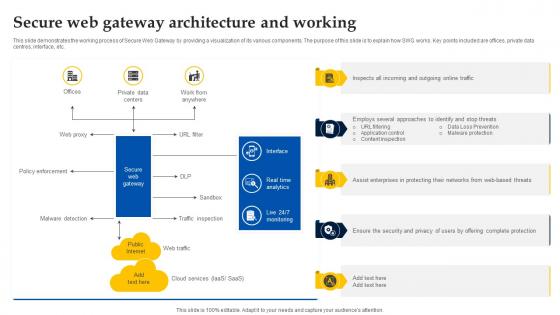
Web Access Control Solution Secure Web Gateway Architecture And Working
This slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Web Access Control Solution Secure Web Gateway Architecture And Working for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
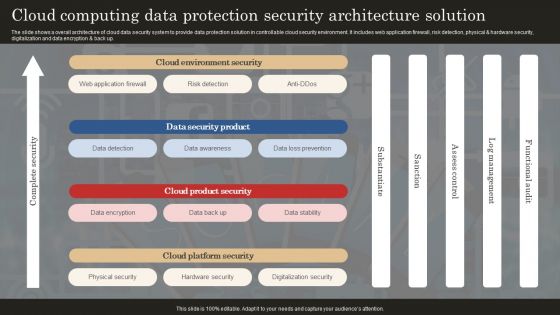
Cloud Computing Data Protection Security Architecture Solution Professional PDF
The slide shows a overall architecture of cloud data security system to provide data protection solution in controllable cloud security environment. It includes web application firewall, risk detection, physical and hardware security, digitalization and data encryption and back up. Showcasing this set of slides titled Cloud Computing Data Protection Security Architecture Solution Professional PDF. The topics addressed in these templates are Web Application Firewall, Data Detection, Data Awareness. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
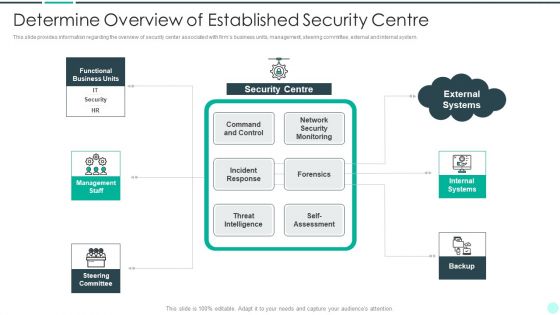
Executing Advance Data Analytics At Workspace Determine Overview Of Established Topics PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver an awe inspiring pitch with this creative executing advance data analytics at workspace determine overview of established topics pdf bundle. Topics like determine overview of established security centre can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Most Common KPIs To Assess Cybersecurity Performance Slides Pdf
Showcasing this set of slides titled Most Common KPIs To Assess Cybersecurity Performance Slides Pdf The topics addressed in these templates are Intrusion Response, Phishing Test Success, Security Rating All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Reverse Proxy Server IT Secure Client Connection To Proxy And Secure Proxy Connection Ppt Infographic Template Design Inspiration PDF
This slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely. This is a reverse proxy server it secure client connection to proxy and secure proxy connection ppt infographic template design inspiration pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like server outside firewall, encrypted, secure, proxy, client. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
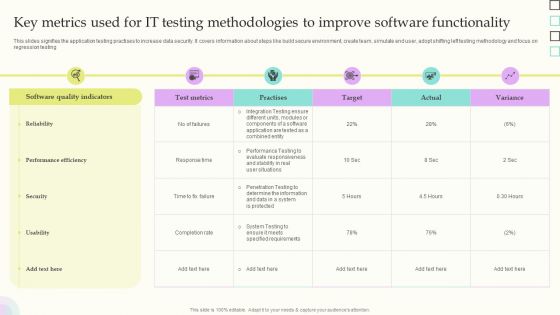
Key Metrics Used For IT Testing Methodologies To Improve Software Functionality Slides PDF
This slides signifies the application testing practises to increase data security. It covers information about steps like build secure environment, create team, simulate end user, adopt shifting left testing methodology and focus on regression testing. Showcasing this set of slides titled Key Metrics Used For IT Testing Methodologies To Improve Software Functionality Slides PDF. The topics addressed in these templates are Software Quality Indicators, Reliability, Performance Efficiency. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Factors For Cloud Computing Security Assessment Ppt Gallery Deck PDF
Presenting Factors For Cloud Computing Security Assessment Ppt Gallery Deck PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Factors For, Cloud Computing, Security Assessment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
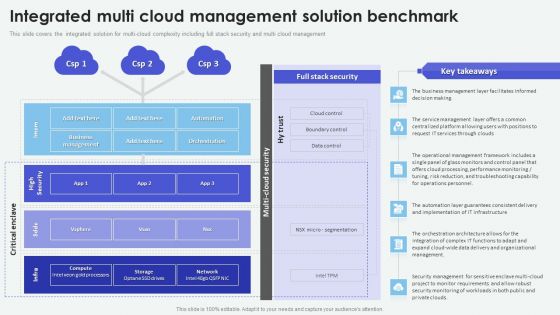
Cloud Based Computing Analysis Integrated Multi Cloud Management Solution Inspiration PDF
This slide covers the integrated solution for multi-cloud complexity including full stack security and multi cloud management. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cloud Based Computing Analysis Integrated Multi Cloud Management Solution Inspiration PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
Data Warehouse Security Mechanism And Procedure Icon Demonstration PDF
Showcasing this set of slides titled Data Warehouse Security Mechanism And Procedure Icon Demonstration PDF. The topics addressed in these templates are Data Warehouse, Security Mechanism, Procedure Icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
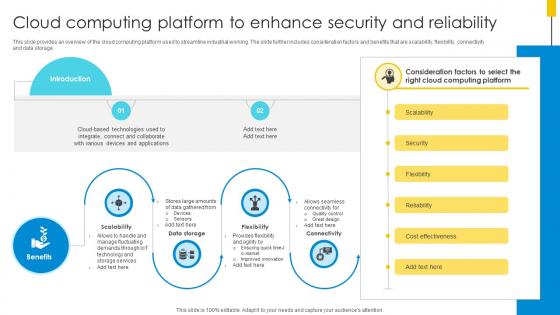
Cloud Computing Platform To Enhance Security And Reliability Optimizing Inventory Management IoT SS V
This slide provides an overview of the cloud computing platform used to streamline industrial working. The slide further includes consideration factors and benefits that are scalability, flexibility, connectivity and data storage. This Cloud Computing Platform To Enhance Security And Reliability Optimizing Inventory Management IoT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cloud Computing Platform To Enhance Security And Reliability Optimizing Inventory Management IoT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Role Of Ztna To Improve Business Operations And Security Software Defined Perimeter SDP
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Take your projects to the next level with our ultimate collection of Role Of Ztna To Improve Business Operations And Security Software Defined Perimeter SDP. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
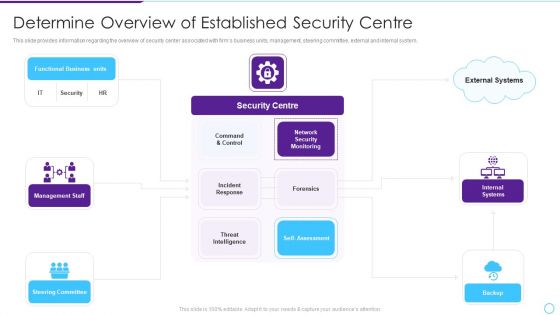
Intelligent Infrastructure Determine Overview Of Established Security Centre Introduction PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a Intelligent Infrastructure Determine Overview Of Established Security Centre Introduction PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Functional Business Units, Security Centre, Internal Systems, Self Assessment, Steering Committee. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security Awareness Training Program Icons Ppt Layouts Structure PDF
Persuade your audience using this IT Security Awareness Training Program Icons Ppt Layouts Structure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including IT Security Awareness, Training Program, Icons. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
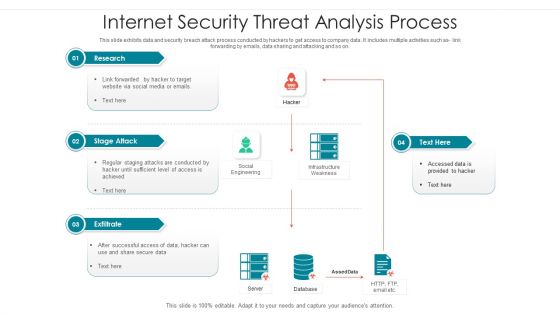
Internet Security Threat Analysis Process Brochure PDF
Following slide showcase how a data breach process is performed by hacker to collect and utilize company data. It includes following activities such as code integration with company software, so on. Showcasing this set of slides titled internet security threat analysis process brochure pdf. The topics addressed in these templates are supply chain attack, execution persistence, defense evasion, exfiltration, keyboard attack. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Customer Relationship Management Implementation Steps Enable Data Security Pictures PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver and pitch your topic in the best possible manner with this Customer Relationship Management Implementation Steps Enable Data Security Pictures PDF. Use them to share invaluable insights on Factor Authentication, Phishing Malware, Accessing Organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
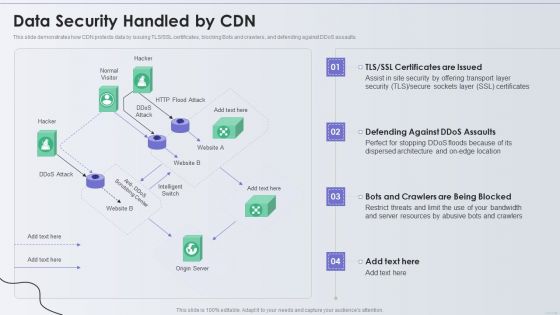
Distribution Network Data Security Handled By CDN Topics PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Deliver an awe inspiring pitch with this creative Distribution Network Data Security Handled By CDN Topics PDF bundle. Topics like Security, Resources, Location can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global And Regional Market Performance Global Security Industry PPT Slide IR SS V
The slide highlights the geographical summary of current state of defense industry with its aim to provide insights on defense sector landscape, trends, development at both global and regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities. If you are looking for a format to display your unique thoughts, then the professionally designed Global And Regional Market Performance Global Security Industry PPT Slide IR SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Global And Regional Market Performance Global Security Industry PPT Slide IR SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Distributed Ledger Security Protocol List Icon Structure Pdf
Pitch your topic with ease and precision using this Distributed Ledger Security Protocol List Icon Structure Pdf This layout presents information on Data Transfer Security, Distributed Ledger, Technology Icon It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Trends In Technology Template Presentation Powerpoint Example
This is a trends in technology template presentation powerpoint example. This is a four stage process. The stages in this process are building management, security, innovation, actuator.

Digital Trends To Optimize Technology Adoption In Banking Sector Themes Pdf
This slide represents the digital trends that helps banking sector industries in enhancing customer satisfaction and data security. It includes various trends such as contactless payment, mobile banking, open finance, etc. Showcasing this set of slides titled Digital Trends To Optimize Technology Adoption In Banking Sector Themes Pdf. The topics addressed in these templates are Contactless Payments, Mobile Banking, Open Finance. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Project Security Administration IT Information Security Process To Manage Firms Sensitive Data Summary PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an awe inspiring pitch with this creative project security administration it information security process to manage firms sensitive data summary pdf bundle. Topics like privileged password management, daily tasks performed by network administrator, network security audit checklist can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Analytics In Business Sector Ppt Show Smartart PDF
This slide represents the data science application in business and its benefits, such as gaining customer insights, increased security, streamlining manufacturing, and predicting future market trends. This is a data analytics in business sector ppt show smartart pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like demographic, target, business services, management, financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
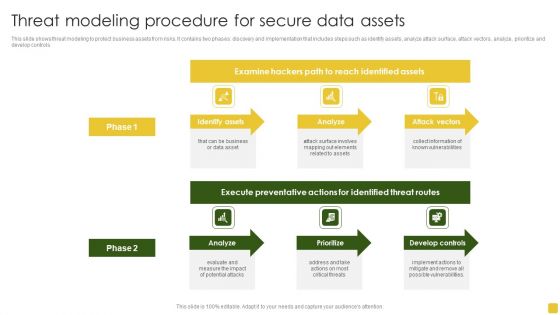
Threat Modeling Procedure For Secure Data Assets Formats PDF
This slide shows threat modeling to protect business assets from risks. It contains two phases discovery and implementation that includes steps such as identify assets, analyze attack surface, attack vectors, analyze, prioritize and develop controls. Pitch your topic with ease and precision using this Threat Modeling Procedure For Secure Data Assets Formats PDF. This layout presents information on Execute Preventative, Identified Threat, Develop Controls. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Project Security Administration IT Information Security Process To Manage Firms Sensitive Data Contd Graphics PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Deliver and pitch your topic in the best possible manner with this project security administration it information security process to manage firms sensitive data contd graphics pdf. Use them to share invaluable insights on firewall audit checklist, vpn configuration, penetrating testing and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Prospects And Growth Potential In Global Security Industry PPT Sample IR SS V
This slide highlights the different prospects responsible for growth of Defense market. The purpose of this slide is to cover different prospects related to growth of the industry. It covers digital and technological transformation, sustainable and climate concerns, product development innovation, and data-driven decision making. The Prospects And Growth Potential In Global Security Industry PPT Sample IR SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
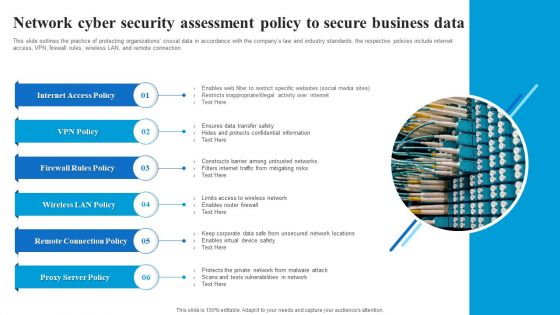
Network Cyber Security Assessment Policy To Secure Business Data Microsoft PDF
This slide outlines the practice of protecting organizations crucial data in accordance with the companys law and industry standards. the respective policies include internet access, VPN, firewall rules, wireless LAN, and remote connection. Showcasing this set of slides titled Network Cyber Security Assessment Policy To Secure Business Data Microsoft PDF. The topics addressed in these templates are Internet Access Policy, Firewall Rules Policy, Wireless LAN Policy, Remote Connection Policy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
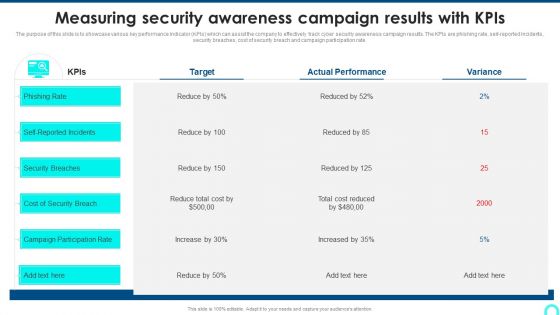
Measuring Security Awareness Campaign Results With Kpis Template PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self reported incidents, security breaches, cost of security breach and campaign participation rateDeliver an awe inspiring pitch with this creative Measuring Security Awareness Campaign Results With Kpis Template PDF bundle. Topics like Security Breaches, Cost Of Security, Campaign Participation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Strategies To Develop Effective Cyber Security Plan Ppt Powerpoint Presentation File Icon Pdf
This slide represents the techniques to be adopted by administration to effectively manage cyber security incidents in order to reduce their impact on business operations. It includes strategies to develop cyber security plan such as establish IR team, conduct threat analysis etc. The Strategies To Develop Effective Cyber Security Plan Ppt Powerpoint Presentation File Icon Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Solutions To Overcome Business Issues In Data Analytics Infographics PDF
Following slide includes challenges faced by business in data analysis with respective solutions for accurate data collection. It includes problems such as data interpretation, tool selection, data consolidation, data security and data interpretation Presenting Solutions To Overcome Business Issues In Data Analytics Infographics PDF to dispense important information. This template comprises Three stages. It also presents valuable insights into the topics including Issues, Action Plan, Comments. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Customer Support Services Company Profile Integrated Performance Of The Company Infographics PDF
This slide highlights the integrated performance of call center which covers different elements such as jobs created, percentage of women, renewable energy consumption, employees trained on data security and code of conduct Presenting Customer Support Services Company Profile Integrated Performance Of The Company Infographics PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Technology, Analytics Experts, Data Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Major Types Of Distributed Ledger Security Methods Portrait Pdf
This slide highlights types of blockchain security methods aimed at efficiently storing data to execute transaction and perform functions in an open environment. It covers three types public blockchain, private blockchain and consortium blockchain Showcasing this set of slides titled Major Types Of Distributed Ledger Security Methods Portrait Pdf The topics addressed in these templates are Public Blockchain, Private Blockchain, Consortium Blockchain All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
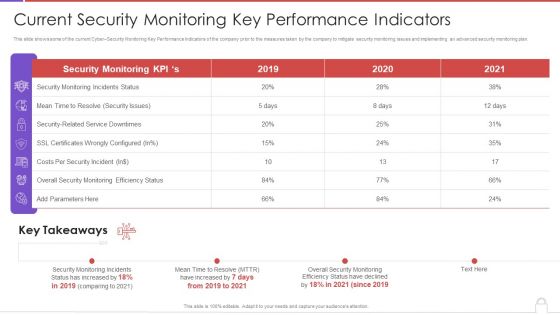
Methods To Develop Advanced Current Security Monitoring Key Performance Indicators Formats PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver an awe inspiring pitch with this creative methods to develop advanced current security monitoring key performance indicators formats pdf bundle. Topics like monitoring incidents status, security issues, costs per security incident, 2019 to 2020 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Big Data Architect Security Of Information In Big Data Graphics PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.Deliver an awe inspiring pitch with this creative Big Data Architect Security Of Information In Big Data Graphics PDF bundle. Topics like Most Challenging, Securing Massive, Data Collections can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Business Diagram Three Staged Key Text Diagram For Data Representation PowerPoint Template
Three staged key and text diagram has been used to design this power point template. This PPT contains the concept of data representation. Use this PPT diagram to represent the marketing and business data in any presentation.
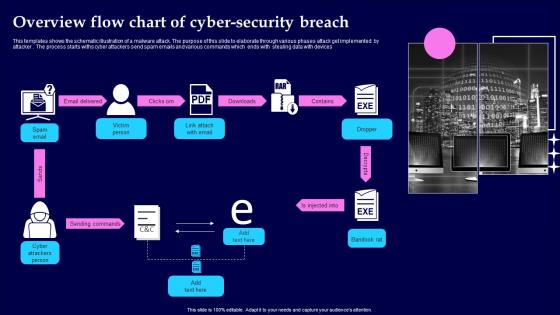
Overview Flow Chart Of Cyber Security Breach Summary Pdf
This templates shows the schematic illustration of a malware attack. The purpose of this slide to elaborate through various phases attack get implemented by attacker . The process starts withs cyber attackers send spam emails and various commands which ends with stealing data with devices Pitch your topic with ease and precision using this Overview Flow Chart Of Cyber Security Breach Summary Pdf This layout presents information on Email Delivered, Sending Commands, Injected Into It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
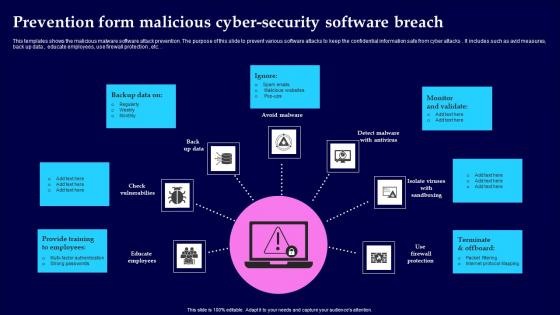
Prevention Form Malicious Cyber Security Software Breach Portrait Pdf
This templates shows the malicious malware software attack prevention. The purpose of this slide to prevent various software attacks to keep the confidential information safe from cyber attacks. It includes such as avid measures, back up data , educate employees, use firewall protection , etc. Showcasing this set of slides titled Prevention Form Malicious Cyber Security Software Breach Portrait Pdf The topics addressed in these templates are Provide Training, Monitor And Validate, Terminate And Offboard All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IOT Technology Trends In Cybersecurity Management Inspiration Pdf
This slide addresses the latest trends of IoT security that enables businesses and organizations to regulation and protect their privacy from malware attacks. The major trends are cybersecurity mesh, security at manufacturing, and network protection. Pitch your topic with ease and precision using this IOT Technology Trends In Cybersecurity Management Inspiration Pdf This layout presents information on Cybersecurity Mesh, Security At Manufacturing, Network Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Biometric Technology To Enhance Card Security Swipe Smartly A Practical Guide Fin SS V
This slide shows information which can be used by organizations to get insights about biometric technology growth in digital banking. It includes details about process of biometric data verification. There are so many reasons you need a Biometric Technology To Enhance Card Security Swipe Smartly A Practical Guide Fin SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
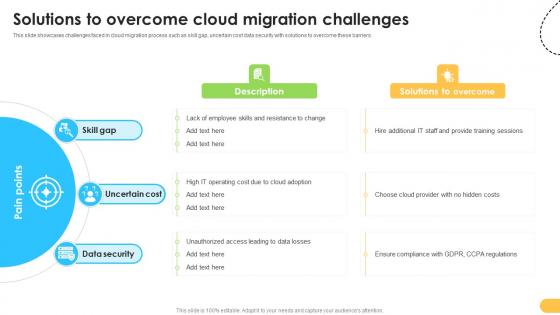
Solutions To Overcome Cloud Migration Challenges Data Migration From On Premises
This slide showcases challenges faced in cloud migration process such as skill gap, uncertain cost data security with solutions to overcome these barriers. Slidegeeks has constructed Solutions To Overcome Cloud Migration Challenges Data Migration From On Premises after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
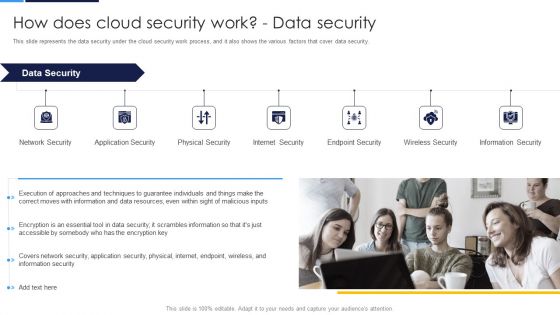
Cloud Security Assessment How Does Cloud Security Work Data Security Diagrams PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan.Presenting Cloud Security Assessment How Does Cloud Security Work Data Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Impact Analysis, Recovery Strategies, Plan Development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
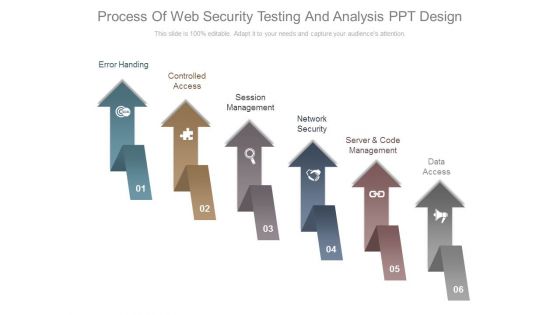
Process Of Web Security Testing And Analysis Ppt Design
This is a process of web security testing and analysis ppt design. This is a six stage process. The stages in this process are error handing, controlled access, session management, network security, server and code management, data access.
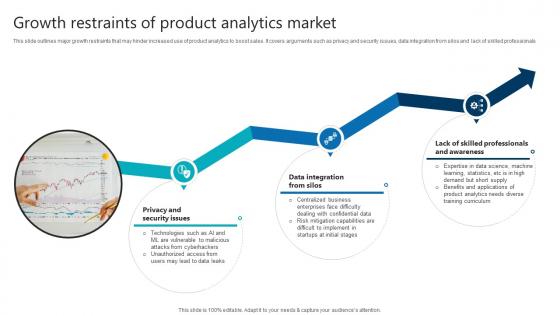
Growth Restraints Of Product Analytics Market Product Analytics Implementation Data Analytics V
This slide outlines major growth restraints that may hinder increased use of product analytics to boost sales. It covers arguments such as privacy and security issues, data integration from silos and lack of skilled professionals This Growth Restraints Of Product Analytics Market Product Analytics Implementation Data Analytics V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Growth Restraints Of Product Analytics Market Product Analytics Implementation Data Analytics V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
Email Security Market Research Report Industry Overview Ppt Outline Graphic Images PDF
Presenting this set of slides with name email security market research report industry overview ppt outline graphic images pdf. This is a two stage process. The stages in this process are moderately fragmented market with key players having large market share, global industry market value, key industry players. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Integration Of Paas Whats Included In A Platform As A Service Paas Icons PDF
This slide describes the working of the platform as a service framework and it includes components such as users, applications, software, operating system, integrated development environment, network access, database, data security, data backup, application hosting, and hardware.. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Integration Of Paas Whats Included In A Platform As A Service Paas Icons PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

 Home
Home