Risk Mitigation
Risk Assessment Methods Real Estate Development Project Overall Impact Of Improvement Professional PDF
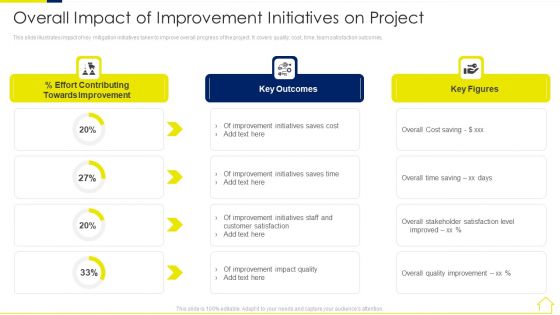
This slide illustrates impact of key mitigation initiatives taken to improve overall progress of the project. It covers quality, cost, time, team satisfaction outcomes. Deliver an awe inspiring pitch with this creative risk assessment methods real estate development project overall impact of improvement professional pdf bundle. Topics like overall impact of improvement initiatives on project can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF
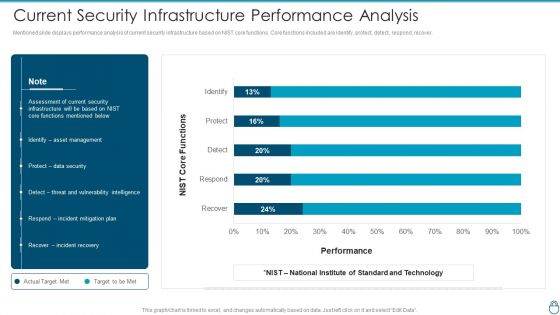
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF bundle. Topics like Asset Management, Protect Data Security, Incident Mitigation Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Commercial Real Estate Project Risk Management Overall Impact Of Improvement Initiatives On Project Mockup PDF
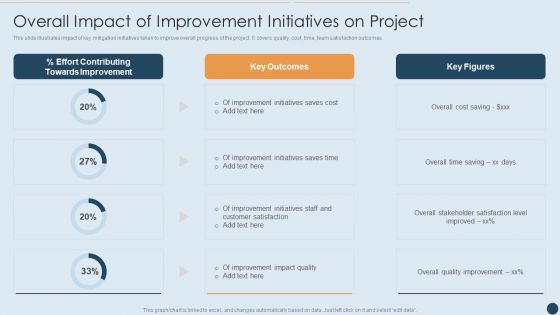
This slide illustrates impact of key mitigation initiatives taken to improve overall progress of the project. It covers quality, cost, time, team satisfaction outcomes. Deliver an awe inspiring pitch with this creative Commercial Real Estate Project Risk Management Overall Impact Of Improvement Initiatives On Project Mockup PDF bundle. Topics like Contributing Towards, Improvement Initiatives, Project can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Management Consulting Sample Diagram Powerpoint Images
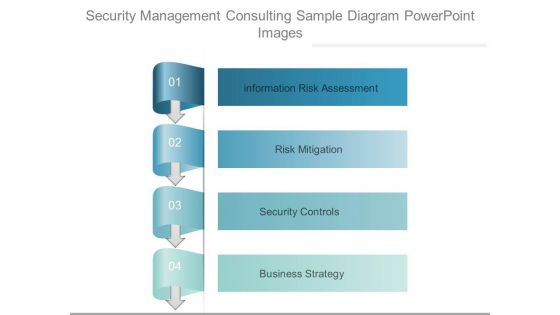
This is a security management consulting sample diagram powerpoint images. This is a four stage process. The stages in this process are information risk assessment, risk mitigation, security controls, business strategy.

Cryptocurrency Transaction Monitoring Mitigating Corporate Scams And Robberies Inspiration Pdf
This slide showcases cryptocurrency transaction monitoring with alert status. It provides information about address, risk level, currencies, bitcoin, Ethereum, date added, deposits, case status, alerts, deposits, darknet, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Cryptocurrency Transaction Monitoring Mitigating Corporate Scams And Robberies Inspiration Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
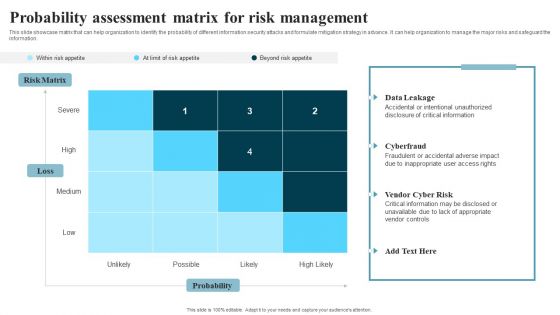
Developing IT Security Strategy Probability Assessment Matrix For Risk Management Formats PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information. Make sure to capture your audiences attention in your business displays with our gratis customizable Developing IT Security Strategy Probability Assessment Matrix For Risk Management Formats PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
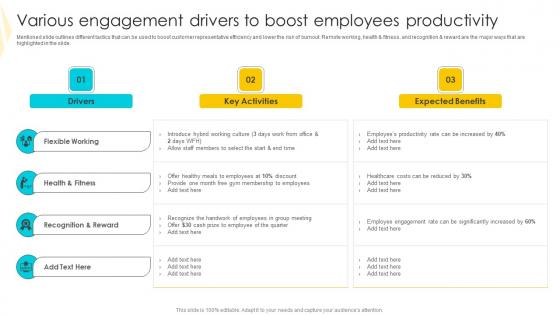
Various Engagement Drivers Strategies To Mitigate Customer Churn Microsoft Pdf
Mentioned slide outlines different tactics that can be used to boost customer representative efficiency and lower the risk of burnout. Remote working, health and fitness, and recognition and reward are the major ways that are highlighted in the slide. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Various Engagement Drivers Strategies To Mitigate Customer Churn Microsoft Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
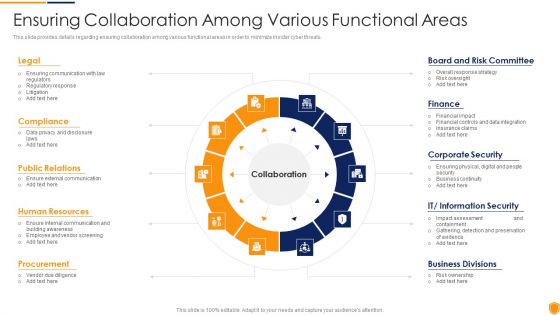
Mitigating Cybersecurity Threats And Vulnerabilities Ensuring Collaboration Among Elements PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting mitigating cybersecurity threats and vulnerabilities ensuring collaboration among elements pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like compliance, public relations, human resources, procurement, board and risk committee. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Overview Of Organizational Developing Financial Contingency Plan To Mitigate Ideas PDF
The following slide outlines a contingency plan which will assist the company to overcome financial crisis. The slide covers information about risk types, description, probability, impact and mitigation strategies. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Overview Of Organizational Developing Financial Contingency Plan To Mitigate Ideas PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Overview Of Organizational Developing Financial Contingency Plan To Mitigate Ideas PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
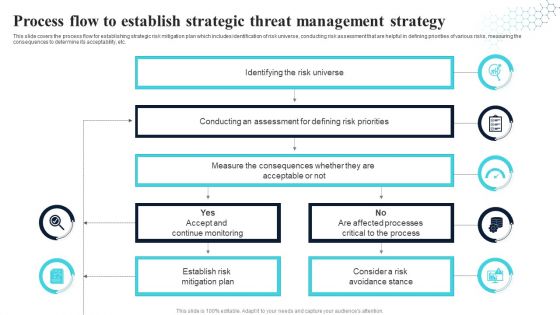
Process Flow To Establish Strategic Threat Management Strategy Professional PDF
This slide covers the process flow for establishing strategic risk mitigation plan which includes identification of risk universe, conducting risk assessment that are helpful in defining priorities of various risks, measuring the consequences to determine its acceptability, etc. Showcasing this set of slides titled Process Flow To Establish Strategic Threat Management Strategy Professional PDF. The topics addressed in these templates are Measure, Risk Universe, Establish Risk Mitigation Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
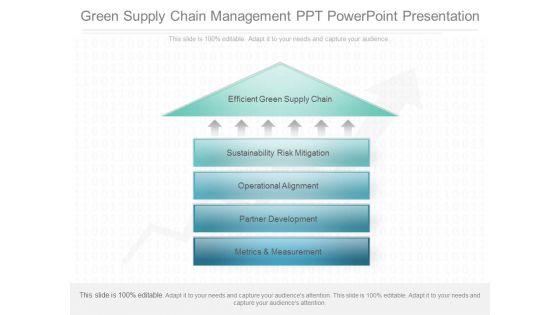
Green Supply Chain Management Ppt Powerpoint Presentation
This is a green supply chain management ppt powerpoint presentation. This is a five stage process. The stages in this process are efficient green supply chain, sustainability risk mitigation, operational alignment, partner development, metrics and measurement.\n\n\n

Cost Of Poor Quality In Quality Management Systems Diagram Example
This is a cost of poor quality in quality management systems diagram example. This is a three stage process. The stages in this process are operational efficiency, risk mitigation, continuous improvement, cost of poor quality.
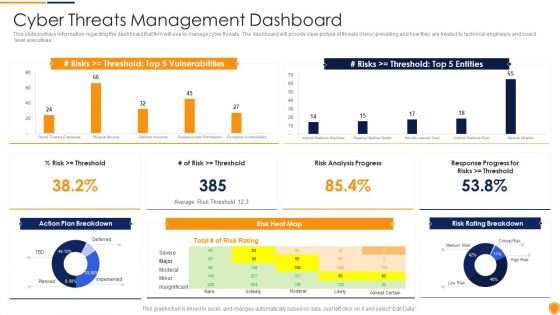
Mitigating Cybersecurity Threats And Vulnerabilities Cyber Threats Management Slides PDF
This slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver and pitch your topic in the best possible manner with this mitigating cybersecurity threats and vulnerabilities cyber threats management slides pdf. Use them to share invaluable insights on cyber threats management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Threat Management Strategy With Possible Actions Background PDF
This slide focuses on the risk mitigation plan which shows the risk matrix covering likelihood and impacted sections with risk mitigation based upon grade covering grades and its possible actions to be taken at the different stages of the project management. Pitch your topic with ease and precision using this Threat Management Strategy With Possible Actions Background PDF. This layout presents information on Reduce Risk, Implement, Required. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
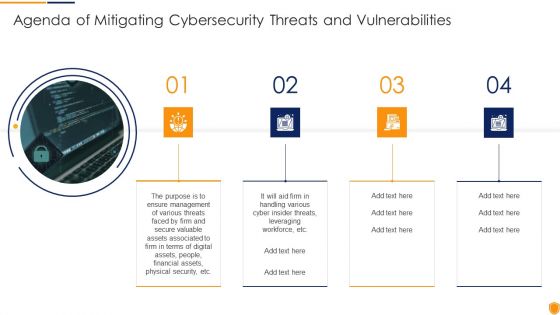
Agenda Of Mitigating Cybersecurity Threats And Vulnerabilities Guidelines PDF
Presenting agenda of mitigating cybersecurity threats and vulnerabilities guidelines pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like agenda of mitigating cybersecurity threats and vulnerabilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
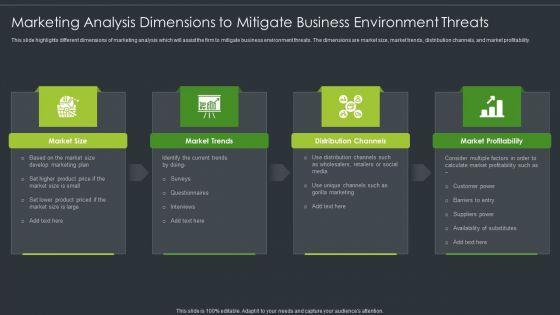
Marketing Analysis Dimensions To Mitigate Business Environment Threats Clipart PDF
This slide highlights different dimensions of marketing analysis which will assist the firm to mitigate business environment threats. The dimensions are market size, market trends, distribution channels, and market profitability. Persuade your audience using this Marketing Analysis Dimensions To Mitigate Business Environment Threats Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Market Size, Market Trends, Distribution Channels. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Icons Slide For Mitigating Cybersecurity Threats And Vulnerabilities Microsoft PDF
Introducing our well designed icons slide for mitigating cybersecurity threats and vulnerabilities microsoft pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
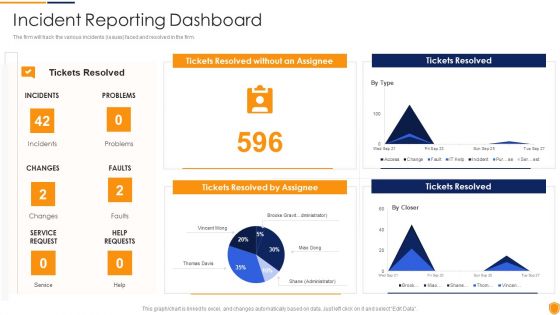
Mitigating Cybersecurity Threats And Vulnerabilities Incident Reporting Dashboard Demonstration PDF
The firm will track the various incidents issues faced and resolved in the firm. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities incident reporting dashboard demonstration pdf bundle. Topics like incident reporting dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mitigating Cybersecurity Threats And Vulnerabilities Determine Threat Scenario Rules PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities determine threat scenario rules pdf bundle. Topics like determine threat scenario analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
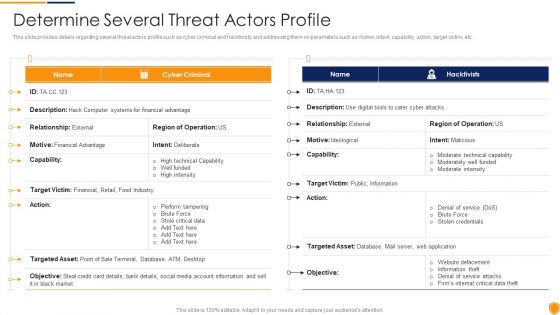
Mitigating Cybersecurity Threats And Vulnerabilities Determine Several Threat Structure PDF
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities determine several threat structure pdf bundle. Topics like determine several threat actors profile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mitigating Cybersecurity Threats And Vulnerabilities Addressing Natural Calamities Template PDF
This slide provides details regarding natural calamities posing as threat to organization and threat management checklist during nature crisis. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities addressing natural calamities template pdf bundle. Topics like threat management checklist can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Indicators Associated Icons PDF
This slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Presenting mitigating cybersecurity threats and vulnerabilities addressing indicators associated icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like user accounts, authentication levels, data exfiltration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents Mitigating Cybersecurity Threats And Vulnerabilities Portrait PDF
Presenting table of contents mitigating cybersecurity threats and vulnerabilities portrait pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, secure digital assets, physical security, natural calamity threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigating Cybersecurity Threats And Vulnerabilities Addressing Critical Business Information PDF
This slide provides details regarding business functions recovery as firm needs to retrieve the crucial information based on priorities in various departments and time taken to retrieve the information. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities addressing critical business information pdf bundle. Topics like addressing critical business functions recovery priorities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user

Mitigating Cybersecurity Threats And Vulnerabilities Evaluating Financial Practices Themes PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities evaluating financial practices themes pdf bundle. Topics like evaluating financial practices in firm can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Mitigating Cybersecurity Threats And Vulnerabilities Financial Performance Tracking Designs PDF
This slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver and pitch your topic in the best possible manner with this mitigating cybersecurity threats and vulnerabilities financial performance tracking designs pdf. Use them to share invaluable insights on receivables analysis, revenue and expense trends and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Table Of Contents Infographics PDF
Presenting mitigating cybersecurity threats and vulnerabilities table of contents infographics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like leveraging workforce, budget assessment, dashboard, impact assessment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
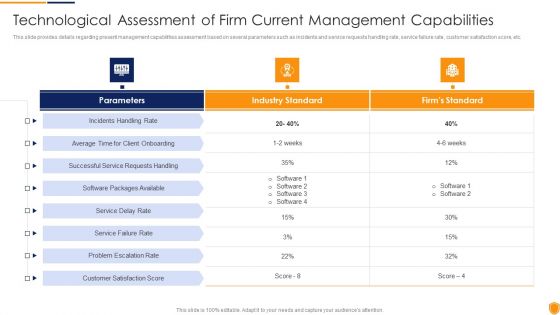
Mitigating Cybersecurity Threats And Vulnerabilities Technological Assessment Sample PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities technological assessment sample pdf bundle. Topics like Industry Standard, Firms Standard, Client Onboarding, Service Failure Rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mitigating Cybersecurity Threats And Vulnerabilities Threat Management Action Graphics PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities threat management action graphics pdf bundle. Topics like threat management action plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mitigating Cybersecurity Threats And Vulnerabilities Determine Threat Management Brochure PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting mitigating cybersecurity threats and vulnerabilities determine threat management brochure pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like determine threat management team structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigating Cybersecurity Threats And Vulnerabilities Selecting Secured Threat Formats PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities selecting secured threat formats pdf bundle. Topics like information security prevention, api integration, security incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
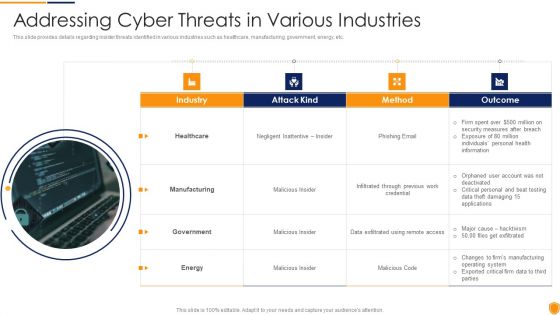
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Cyber Threats Portrait PDF
This slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. This is a mitigating cybersecurity threats and vulnerabilities addressing cyber threats portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like healthcare, manufacturing, government, energy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
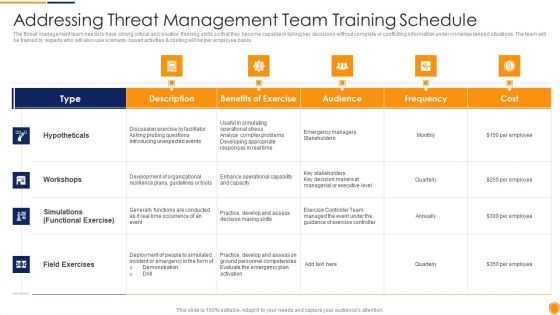
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Threat Management Download PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario- based activities and costing will be per employee basis. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities addressing threat management download pdf bundle. Topics like hypotheticals, workshops, field exercises can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user

Communication Problem And Strategies To Mitigate In Workplace Infographics PDF
This slide covers communication Problem in office and virtual meetings and strategies to overcome it. It involves organizational, cultural and time challenges. Presenting Communication Problem And Strategies To Mitigate In Workplace Infographics PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Organizational, Strategies, Teams. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Measures And Ways To Mitigate Security Management Challenges Formats PDF
Deliver an awe inspiring pitch with this creative measures and ways to mitigate security management challenges formats pdf bundle. Topics like potential insider threats, external security breaches, security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mitigating Cybersecurity Threats And Vulnerabilities Current Potential Implications Formats PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities current potential implications formats pdf bundle. Topics like employees, increase security threats, data breaches and records exposed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
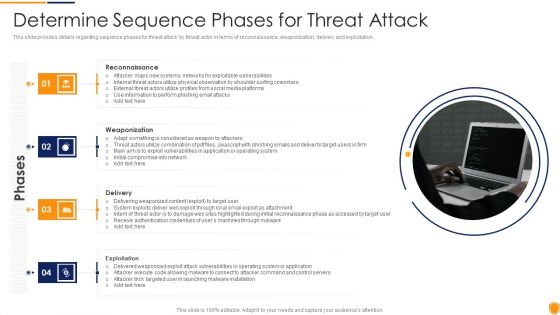
Mitigating Cybersecurity Threats And Vulnerabilities Determine Sequence Phases Elements PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a mitigating cybersecurity threats and vulnerabilities determine sequence phases elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reconnaissance, weaponization, delivery, exploitation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Statistics Associated Mockup PDF
This slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. This is a mitigating cybersecurity threats and vulnerabilities statistics associated mockup pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like statistics associated to workplace threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
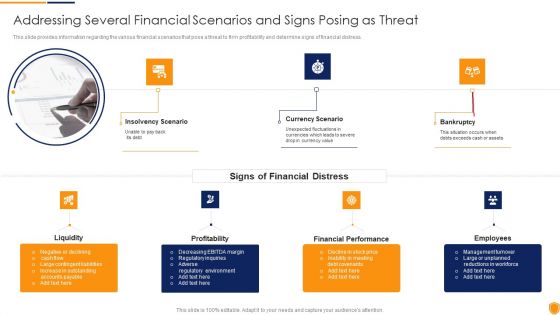
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Several Financial Diagrams PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. This is a mitigating cybersecurity threats and vulnerabilities addressing several financial diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like insolvency scenario, currency scenario, bankruptcy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
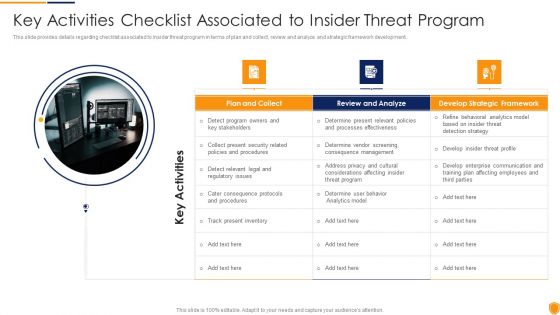
Mitigating Cybersecurity Threats And Vulnerabilities Key Activities Checklist Diagrams PDF
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. This is a mitigating cybersecurity threats and vulnerabilities key activities checklist diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plan and collect, review and analyze, develop strategic framework. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
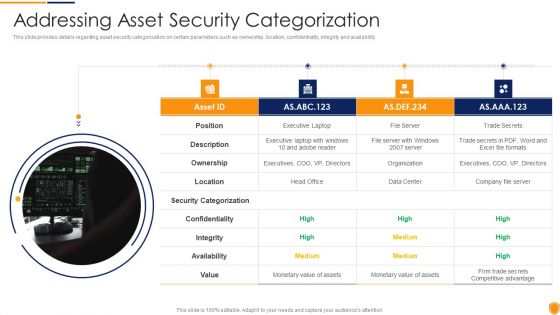
Mitigating Cybersecurity Threats And Vulnerabilities Addressing Asset Security Elements PDF
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. This is a mitigating cybersecurity threats and vulnerabilities addressing asset security elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ownership, location, integrity, security categorization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
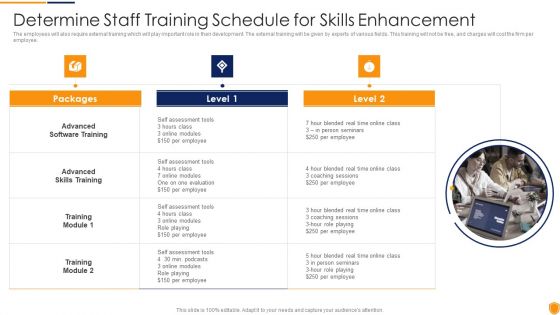
Mitigating Cybersecurity Threats And Vulnerabilities Determine Staff Training Rules PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. This is a mitigating cybersecurity threats and vulnerabilities determine staff training rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like advanced software training, advanced skills training, training module. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
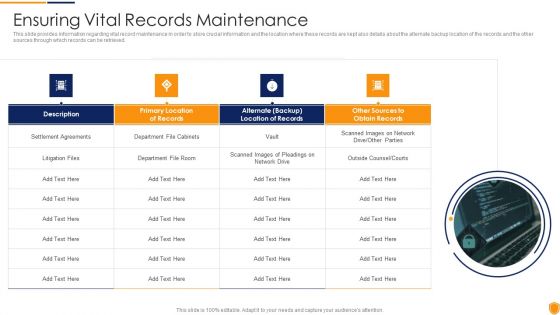
Mitigating Cybersecurity Threats And Vulnerabilities Ensuring Vital Records Inspiration PDF
This slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. This is a mitigating cybersecurity threats and vulnerabilities ensuring vital records inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring vital records maintenance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Incident Reporting Themes PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Presenting mitigating cybersecurity threats and vulnerabilities incident reporting themes pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like incident reporting by different departments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Mitigating Cybersecurity Threats And Vulnerabilities Roles And Responsibilities Introduction PDF
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. This is a mitigating cybersecurity threats and vulnerabilities roles and responsibilities introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, manager responsibilities, unit responsibilities, human resources responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mitigating Cybersecurity Threats And Vulnerabilities Workplace Employee Rules PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Presenting mitigating cybersecurity threats and vulnerabilities workplace employee rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like clinical services, work and life services, employer services. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
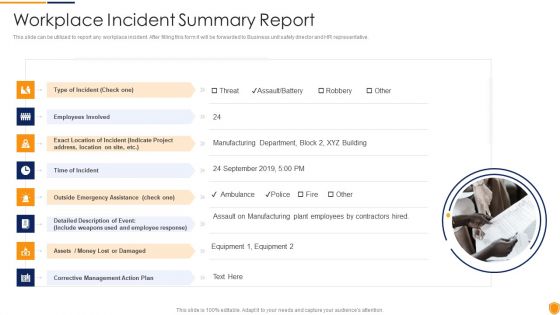
Mitigating Cybersecurity Threats And Vulnerabilities Workplace Incident Summary PDF
This slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. This is a mitigating cybersecurity threats and vulnerabilities workplace incident summary pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like type of incident, time of incident, corrective management action plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Measures And Ways To Mitigate Security Management Challenges Background PDF
This slide provides information about the ways and measures through which the company and IT security managers can overcome the problems and issues related to Security Management. Deliver an awe inspiring pitch with this creative measures and ways to mitigate security management challenges background pdf bundle. Topics like potential insider threats, external security breaches, weak links in the supply chain can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Measures And Ways To Mitigate Security Management Challenges Icons PDF
This slide provides information about the ways and measures through which the company and IT security managers can overcome the problems and issues related to Security Management. Deliver and pitch your topic in the best possible manner with this measures and ways to mitigate security management challenges icons pdf. Use them to share invaluable insights on information, security training, implementing, technologies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Measures And Ways To Mitigate Security Management Challenges Structure PDF
This slide provides information about the ways and measures through which the company and IT security managers can overcome the problems and issues related to Security Management.This is a Measures and ways to mitigate security management challenges structure pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential insider threats, external security breaches, weak links in the supply chain. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Threat Management Strategy Framework To Minimize Threats Portrait PDF
This slide shows the risk mitigation plan framework to minimize threats which includes definition of risks, probability and consequences, business impact analysis, risk management strategies, risk mitigation action planning, plan execution and monitoring, etc. Pitch your topic with ease and precision using this Threat Management Strategy Framework To Minimize Threats Portrait PDF. This layout presents information on Developing Risk Management Committee, Developing Risk Management Committee, Defining Risks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Addressing Various Risks And Uncertainties Associated To Firm One Pager Documents
This slide covers details regarding the several risks and uncertainties associated to business with key risks and mitigation strategies. Presenting you an exemplary Addressing Various Risks And Uncertainties Associated To Firm One Pager Documents. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Addressing Various Risks And Uncertainties Associated To Firm One Pager Documents brilliant piece now.
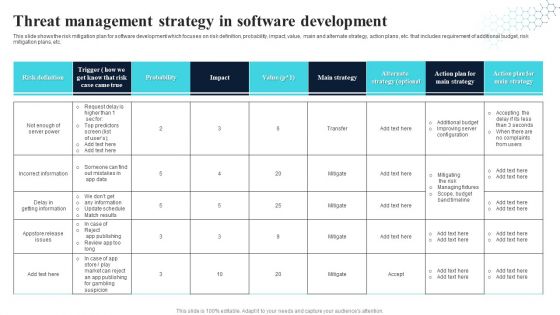
Threat Management Strategy In Software Development Download PDF
This slide shows the risk mitigation plan for software development which focuses on risk definition, probability, impact, value, main and alternate strategy, action plans, etc. that includes requirement of additional budget, risk mitigation plans, etc. Pitch your topic with ease and precision using this Threat Management Strategy In Software Development Download PDF. This layout presents information on Probability, Main Strategy, Alternate Strategy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Table Of Contents Information Security Risk Evaluation And Administration Plan Slide Slides PDF
Presenting Table Of Contents Information Security Risk Evaluation And Administration Plan Slide Slides PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Process Formulate, Management Plan, Mitigating Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Types Of Strategy Risks In Organisational Management Formats Pdf
This template covers the different types of strategic risks. The purpose of this slide is to recognize internal and external risks take action to mitigate costly problems. It also includes risks such as regulatory risks, competitors risk etc. Showcasing this set of slides titled Types Of Strategy Risks In Organisational Management Formats PDF. The topics addressed in these templates are Operational Risk, Governance Risk, Financial Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
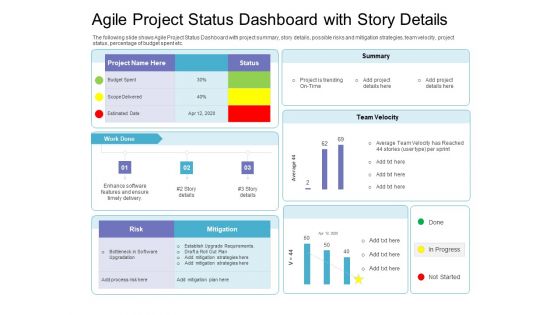
Agile Project Status Dashboard With Story Details Portrait PDF
The following slide shows Agile Project Status Dashboard with project summary, story details, possible risks and mitigation strategies, team velocity, project status, percentage of budget spent etc. Deliver and pitch your topic in the best possible manner with this agile project status dashboard with story details portrait pdf. Use them to share invaluable insights on risk, mitigation, team velocity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
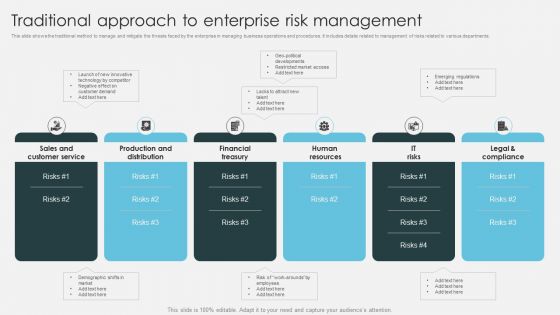
Traditional Approach To Enterprise Risk Management Introduction To ERM Topics PDF
This slide shows the traditional method to manage and mitigate the threats faced by the enterprise in managing business operations and procedures. It includes details related to management of risks related to various departments.Make sure to capture your audiences attention in your business displays with our gratis customizable Traditional Approach To Enterprise Risk Management Introduction To ERM Topics PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
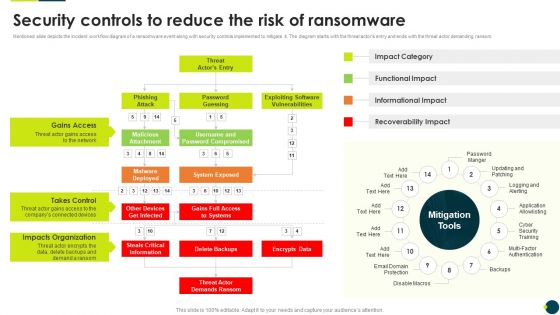
IT Threats Response Playbook Security Controls To Reduce The Risk Of Ransomware Information PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Security Controls To Reduce The Risk Of Ransomware Information PDF bundle. Topics like Gains Access, Takes Control, Impacts Organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
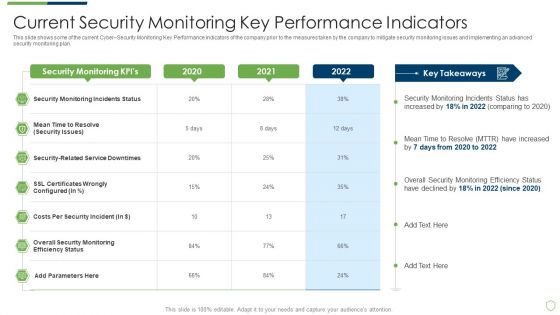
Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Security Monitoring Pictures PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver and pitch your topic in the best possible manner with this modern security observation plan to eradicate cybersecurity risk and data breach current security monitoring pictures pdf. Use them to share invaluable insights on current security monitoring key performance indicators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Strategic Financial Planning And Administration Developing Strategies To Mitigate Financial Portrait PDF
This slide provides glimpse about multiple strategies required to reduce and eliminate all financial risks. It includes risks such as liquidity risk, taxation risk, cost risk, etc. This Strategic Financial Planning And Administration Developing Strategies To Mitigate Financial Portrait PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Strategic Financial Planning And Administration Developing Strategies To Mitigate Financial Portrait PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

 Home
Home