Risk And Assumptions
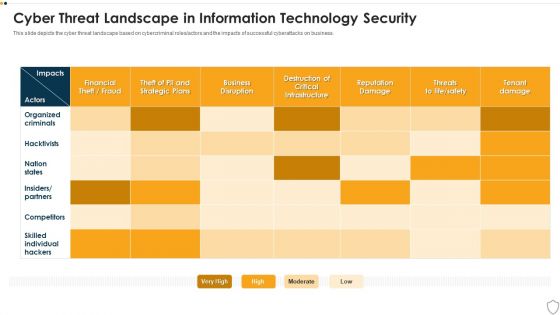
IT Security Cyber Threat Landscape In Information Technology Security Download PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this it security cyber threat landscape in information technology security download pdf. Use them to share invaluable insights on business, competitors, reputation damage, organized criminals and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
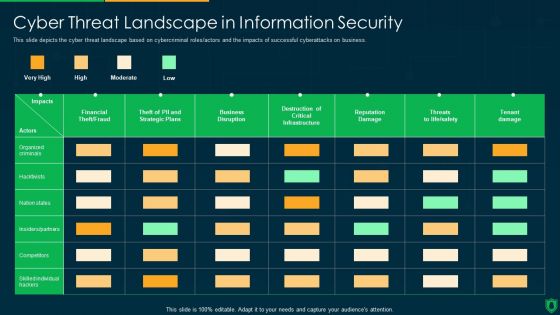
Info Security Cyber Threat Landscape In Information Security Ppt PowerPoint Presentation File Slides PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver and pitch your topic in the best possible manner with this info security cyber threat landscape in information security ppt powerpoint presentation file slides pdf. Use them to share invaluable insights on business disruption, financial theft, fraud, reputation damage, tenant damage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Facilitating IT Intelligence Architecture Contingency Plan For Threat Handling In Security Centre Professional PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations Deliver and pitch your topic in the best possible manner with this Facilitating IT Intelligence Architecture Contingency Plan For Threat Handling In Security Centre Professional PDF Use them to share invaluable insights on Contingency Solutions, Contingency Considerations, Information Documentation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
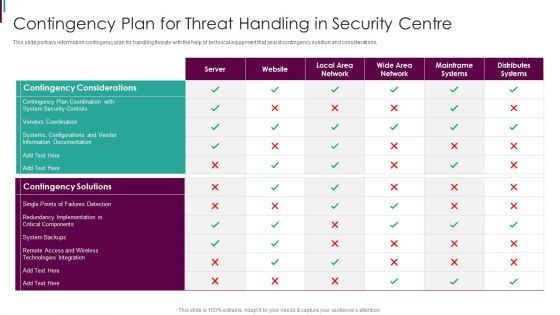
Developing Business Analytics Framework Contingency Plan For Threat Handling Mockup PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver and pitch your topic in the best possible manner with this Developing Business Analytics Framework Contingency Plan For Threat Handling Mockup PDF Use them to share invaluable insights on Contingency Considerations, Contingency Solutions, Technologies Integration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Problem 2 Declining Market Share Ppt Show Example PDF
The slides shows the market share of company A from the years 2012 to 2021. It also provides key insights such as CAGR growth, key reasons for the decline etc. Deliver and pitch your topic in the best possible manner with this problem 2 declining market share ppt show example pdf. Use them to share invaluable insights on problem 2 declining market share, 2012 to 2021 and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Problem And Solution 2 Decline In Company Sales Mockup PDF
This slide shows the problem that the company is facing related to fall in sales of the company due to lost of existing subscribers decreased Customer Retention Rate that is effecting the company growth along with the solution that the company must adopt.Deliver and pitch your topic in the best possible manner with this problem and solution 2 decline in company sales mockup pdf. Use them to share invaluable insights on revenue, 2017 to 2021 and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
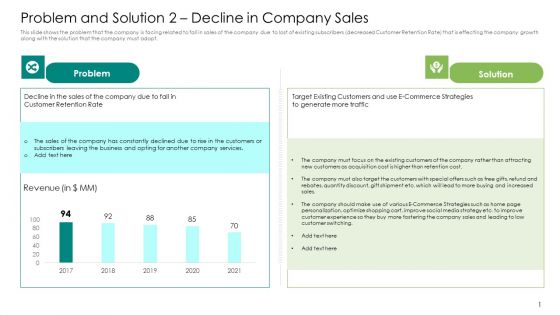
Problem And Solution 2 Decline In Company Sales Clipart PDF
This slide shows the problem that the company is facing related to fall in sales of the company due to lost of existing subscribers decreased Customer Retention Rate that is effecting the company growth along with the solution that the company must adopt.Deliver and pitch your topic in the best possible manner with this problem and solution 2 decline in company sales clipart pdf. Use them to share invaluable insights on revenue, 2017 to 2021 and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Problem And Recommendation 2 Changing Customer Preferences Brochure PDF
This slide shows the problem that the company is facing related to changing customer buying preferences online shopping instead of buying from retail store that is effecting the company growth along with the solution stating that the company must adopt latest E Commerce trends and prefer online sales. Deliver and pitch your topic in the best possible manner with this problem and recommendation 2 changing customer preferences brochure pdf. Use them to share invaluable insights on product sales, company sales, preferences, social media, online advertising, e commerce and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Problem And Solution 3 Reduced Repeat Order Rate Rules PDF
This slide shows the problem that the company is facing related to purchase rate that is constantly declining as customers are leaving the company services and opting for another service provider. The solution is to provide incentives to the customers and use email targeting to win customers back.Deliver and pitch your topic in the best possible manner with this problem and solution 3 reduced repeat order rate rules pdf. Use them to share invaluable insights on customer repeat order rate , 2017 to 2021 and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
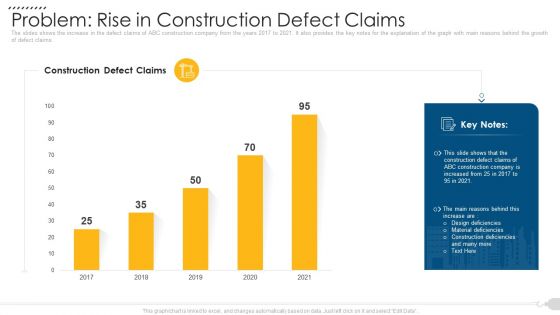
Problem Rise In Construction Defect Claims Demonstration PDF
The slides shows the increase in the defect claims of ABC construction company from the years 2017 to 2021. It also provides the key notes for the explanation of the graph with main reasons behind the growth of defect claims. Deliver and pitch your topic in the best possible manner with this problem rise in construction defect claims demonstration pdf. Use them to share invaluable insights on problem rise in construction defect claims and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Problem Rise In Construction Defect Claims Topics PDF
The slides shows the increase in the defect claims of ABC construction company from the years 2017 to 2021. It also provides the key notes for the explanation of the graph with main reasons behind the growth of defect claims.Deliver and pitch your topic in the best possible manner with this problem rise in construction defect claims topics pdf. Use them to share invaluable insights on problem rise in construction defect claims and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
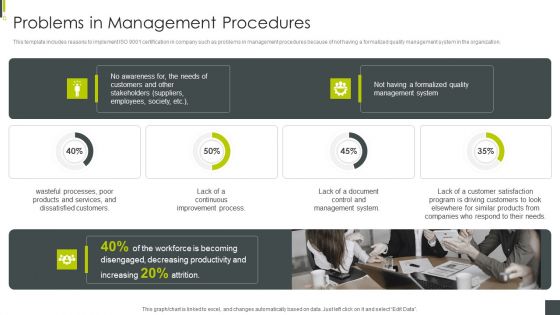
ISO 9001 Certification Procedure Problems In Management Procedures Professional PDF
This template includes reasons to implement ISO 9001 certification in company such as problems in management procedures because of not having a formalized quality management system in the organization. Deliver and pitch your topic in the best possible manner with this ISO 9001 Certification Procedure Problems In Management Procedures Professional PDF. Use them to share invaluable insights on Products And Services, Management System, Decreasing Productivity and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
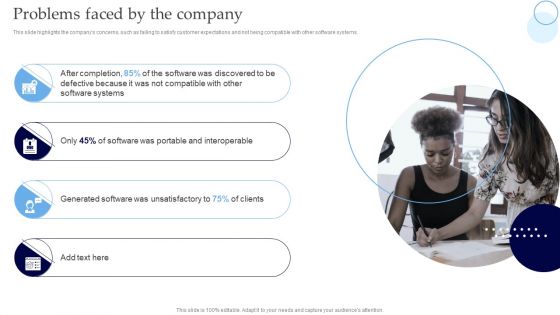
Interoperability Software Testing Problems Faced By The Company Ideas PDF
This slide highlights the companys concerns, such as failing to satisfy customer expectations and not being compatible with other software systems. Explore a selection of the finest Interoperability Software Testing Problems Faced By The Company Ideas PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Interoperability Software Testing Problems Faced By The Company Ideas PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
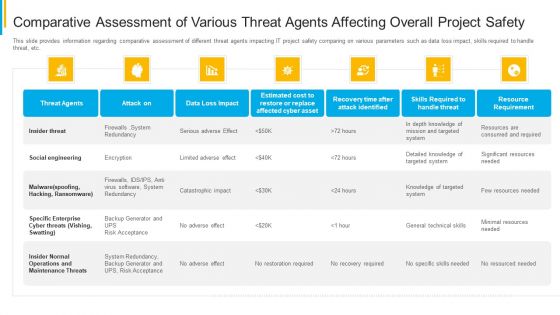
Project Security Administration IT Comparative Assessment Of Various Threat Agents Affecting Overall Project Safety Background PDF
This slide provides information regarding comparative assessment of different threat agents impacting IT project safety comparing on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this project security administration it comparative assessment of various threat agents affecting overall project safety background pdf. Use them to share invaluable insights on resource requirement, maintenance threats, cyber threats, social engineering and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Swot Analysis Of XYZ Logistics Company Threats Ppt Infographic Template Icons PDF
This slide shows some threats that may effect the company in future course of time and impact the company profits. Some potential threats are Rising Fuel Costs, Intense Competition, Government Regulations and Currency Fluctuations etc. Deliver and pitch your topic in the best possible manner with this swot analysis of xyz logistics company threats ppt infographic template icons pdf. Use them to share invaluable insights on rising fuel costs, intense competition, government regulations and currency fluctuations, threat and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
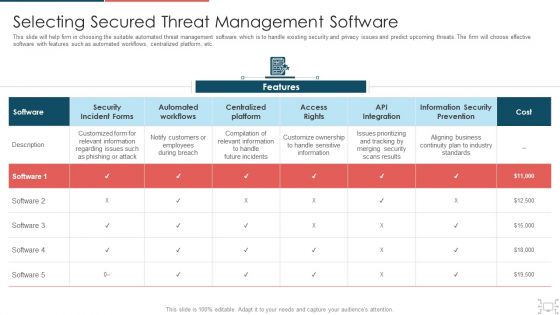
Cyber Security Administration In Organization Selecting Secured Threat Management Software Themes PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization selecting secured threat management software themes pdf. Use them to share invaluable insights on selecting secured threat management software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Problem Statement Highlighting Customers Having Difficulties In Commuting Clipart PDF
Following slide illustrates the information about the major points faced by users such as difficulty in commuting from one place to another due to growing transit use. Deliver and pitch your topic in the best possible manner with this problem statement highlighting customers having difficulties in commuting clipart pdf. Use them to share invaluable insights on growing urban population, rising cost of gasoline, carbon footprints and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
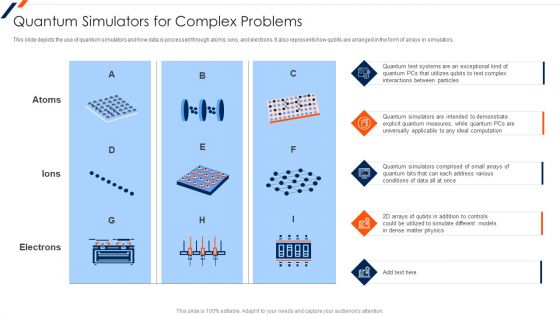
Quantum Simulators For Complex Problems Quantum Computing Elements PDF
This slide depicts the use of quantum simulators and how data is processed through atoms, ions, and electrons. It also represents how qubits are arranged in the form of arrays in simulators. Deliver and pitch your topic in the best possible manner with this Quantum Simulators For Complex Problems Quantum Computing Elements PDF. Use them to share invaluable insights on Quantum Tools, Cirq And CirqProjectQ and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
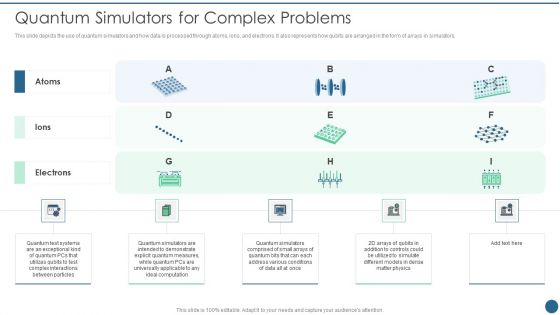
Quantum Key Distribution Quantum Simulators For Complex Problems Information PDF
This slide depicts the use of quantum simulators and how data is processed through atoms, ions, and electrons. It also represents how qubits are arranged in the form of arrays in simulators. Deliver and pitch your topic in the best possible manner with this Quantum Key Distribution Quantum Simulators For Complex Problems Information PDF Use them to share invaluable insights on Complex Interactions, Quantum Simulators, Quantum Measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
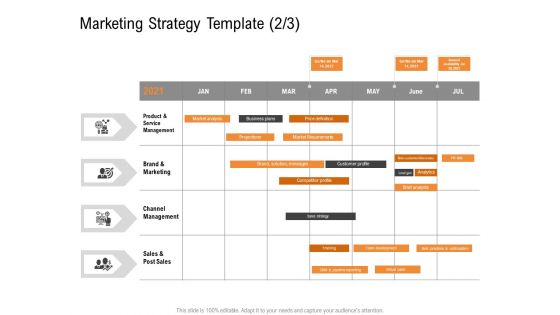
Opportunities And Threats For Penetrating In New Market Segments Marketing Strategy Template Channel Diagrams PDF
Product Launch marketing Plan schedule. Deliver and pitch your topic in the best possible manner with this opportunities and threats for penetrating in new market segments marketing strategy template channel diagrams pdf. Use them to share invaluable insights on product and service management, brand and marketing, channel management, sales and post sales and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

How To Intensify Project Threats Project Validation And Prioritization Brochure PDF
This slide provides the glimpse about the second step of issue and escalation process which covers the project validation and prioritization along with the features and different projects initiatives. Deliver and pitch your topic in the best possible manner with this how to intensify project threats project validation and prioritization brochure pdf. Use them to share invaluable insights on strategic fit, economic impact, feasibility and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
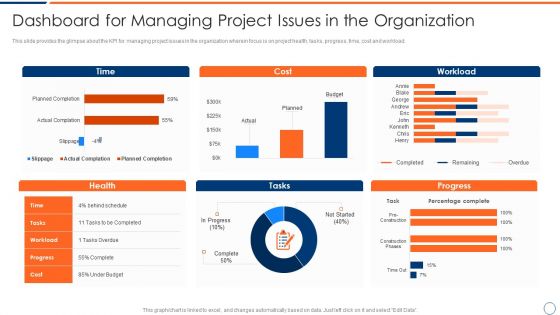
How To Intensify Project Threats Dashboard For Managing Project Issues Inspiration PDF
This slide provides the glimpse about the KPI for managing project issues in the organization wherein focus is on project health, tasks, progress, time, cost and workload. Deliver and pitch your topic in the best possible manner with this how to intensify project threats dashboard for managing project issues inspiration pdf. Use them to share invaluable insights on time, cost, workload, progress, tasks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
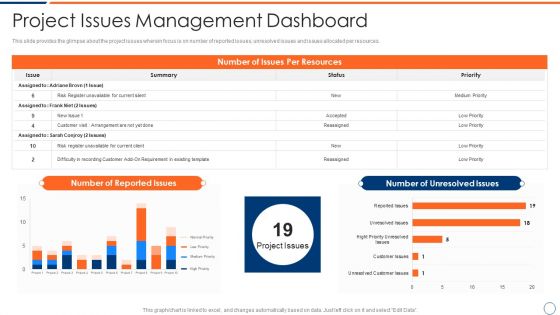
How To Intensify Project Threats Project Issues Management Dashboard Clipart PDF
This slide provides the glimpse about the project issues wherein focus is on number of reported issues, unresolved issues and issues allocated per resources. Deliver and pitch your topic in the best possible manner with this how to intensify project threats project issues management dashboard clipart pdf. Use them to share invaluable insights on project issues management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
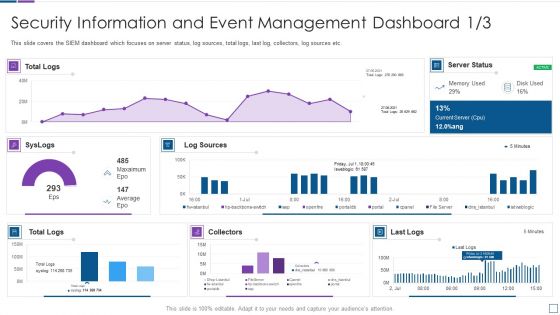
Real Time Assessment Of Security Threats Security Information And Event Management Microsoft PDF
This slide covers the SIEM dashboard which focuses on server status, log sources, total logs, last log, collectors, log sources etc. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats security information and event management microsoft pdf. Use them to share invaluable insights on security information and event management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Addressing The Companies Digitization Ppt Portfolio Smartart PDF
Mentioned slide provides information about the companys digitalization levels by sectors. Digitalization level is measured based on asset, usage and labor. Deliver and pitch your topic in the best possible manner with this andling cyber threats digital era addressing the companies digitization ppt portfolio smartart pdf. Use them to share invaluable insights on addressing the companies digitization levels by sectors and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
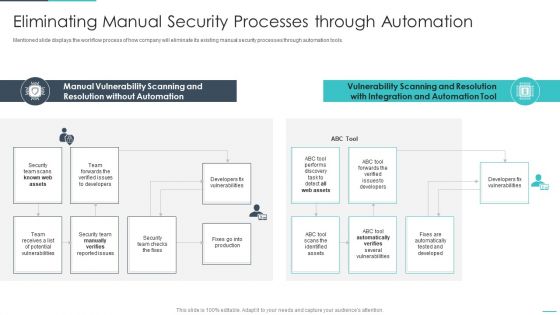
Handling Cyber Threats Digital Era Eliminating Manual Security Processes Ppt Show Influencers PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era eliminating manual security processes ppt show influencers pdf. Use them to share invaluable insights on eliminating manual security processes through automation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
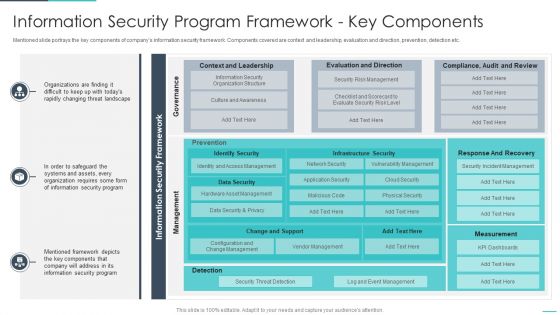
Handling Cyber Threats Digital Era Information Security Program Framework Ppt Model Summary PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era information security program framework ppt model summary pdf. Use them to share invaluable insights on information security program framework key components and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
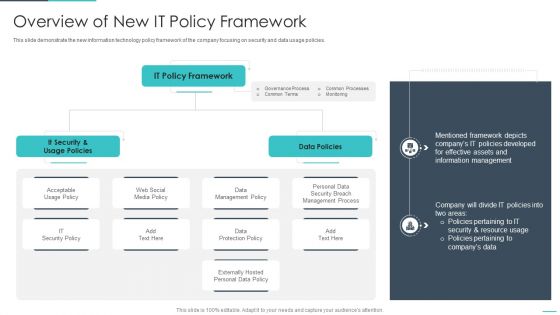
Handling Cyber Threats Digital Era Overview Of New IT Policy Framework Ppt Summary Guidelines PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era overview of new it policy framework ppt summary guidelines pdf. Use them to share invaluable insights on overview of new it policy framework and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
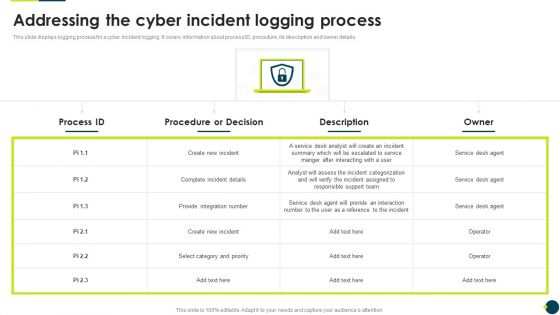
IT Threats Response Playbook Addressing The Cyber Incident Logging Process Introduction PDF
This slide displays logging process for a cyber incident logging. It covers information about process ID, procedure, its description and owner details.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Addressing The Cyber Incident Logging Process Introduction PDF. Use them to share invaluable insights on Provide Integration, Responsible Support, Assess The Incident and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
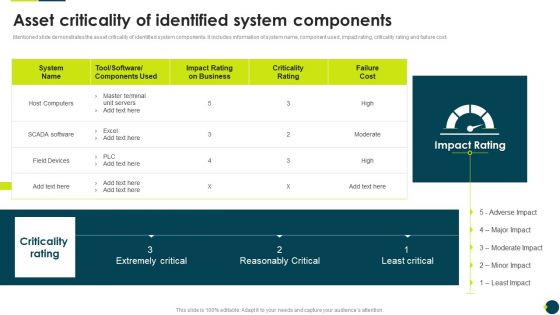
IT Threats Response Playbook Asset Criticality Of Identified System Components Themes PDF
Mentioned slide demonstrates the asset criticality of identified system components. It includes information of system name, component used, impact rating, criticality rating and failure cost.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Asset Criticality Of Identified System Components Themes PDF. Use them to share invaluable insights on Master Terminal, Extremely Critical, Reasonably Critical and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Threats Response Playbook Classifying Various Security Issues And Attacks Professional PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Classifying Various Security Issues And Attacks Professional PDF. Use them to share invaluable insights on External Issues, Audio Steganography, Malware Injection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF. Use them to share invaluable insights on Cryptographic Administration, Security Management, System Protection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
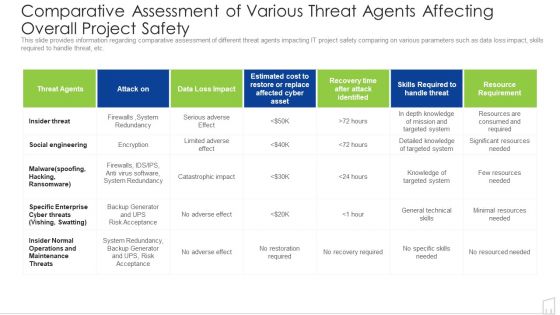
Comparative Assessment Of Various Threat Agents Affecting Overall Project Safety Ppt Ideas Outfit PDF
This slide provides information regarding comparative assessment of different threat agents impacting IT project safety comparing on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this comparative assessment of various threat agents affecting overall project safety ppt ideas outfit pdf. Use them to share invaluable insights on system, required, resources, social and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Determine Several Threat Actors Profile Sample PDF
This slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization determine several threat actors profile sample pdf. Use them to share invaluable insights on determine several threat actors profile and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
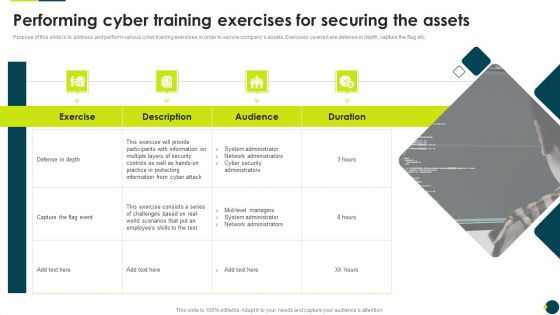
IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver and pitch your topic in the best possible manner with this IT Threats Response Playbook Performing Cyber Training Exercises For Securing The Assets Clipart PDF. Use them to share invaluable insights on Participants Information, System Administrator, Network Administrators and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
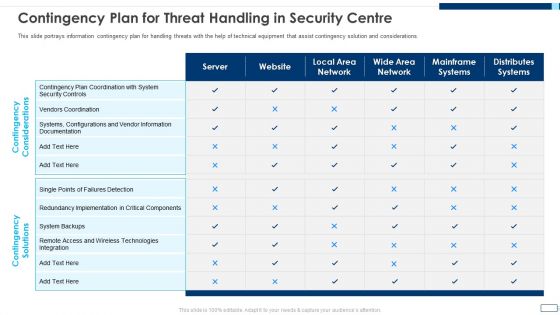
Evolving BI Infrastructure Contingency Plan For Threat Handling In Security Centre Pictures PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver and pitch your topic in the best possible manner with this evolving bi infrastructure contingency plan for threat handling in security centre pictures pdf. Use them to share invaluable insights on server, website, local area network, wide area network, mainframe systems, distributes systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Addressing Threat Management Team Training Schedule Inspiration PDF
The threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization addressing threat management team training schedule inspiration pdf. Use them to share invaluable insights on probing, unexpected, decision, skills, managerial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
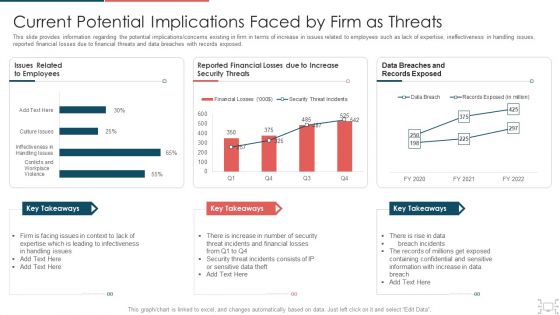
Cyber Security Administration In Organization Current Potential Implications Faced By Firm As Threats Clipart PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization current potential implications faced by firm as threats clipart pdf. Use them to share invaluable insights on infectiveness, expertise, issues, security, increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
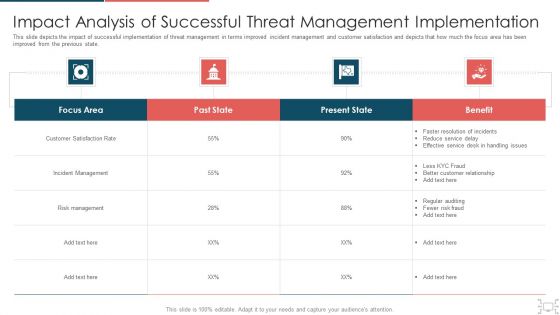
Cyber Security Administration In Organization Impact Analysis Of Successful Threat Management Ideas PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization impact analysis of successful threat management ideas pdf. Use them to share invaluable insights on handling, service, resolution, customer, relationship and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
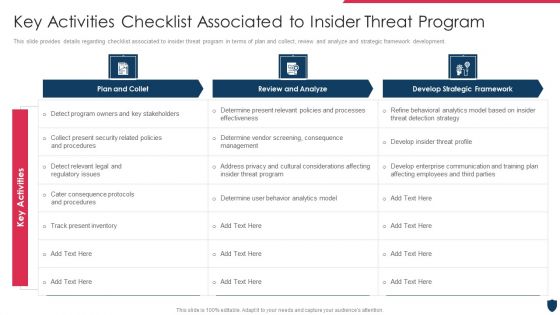
Cyber Safety Incident Management Key Activities Checklist Associated To Insider Threat Program Download PDF
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Deliver and pitch your topic in the best possible manner with this cyber safety incident management key activities checklist associated to insider threat program download pdf. Use them to share invaluable insights on plan and collet, review and analyze, develop strategic framework, key activities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
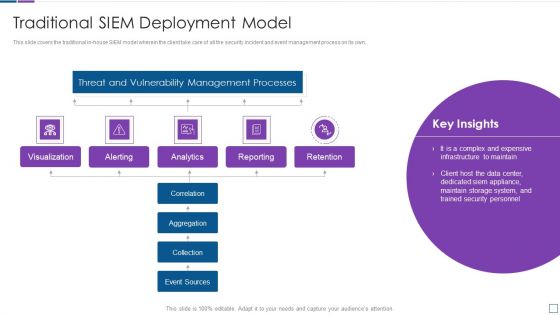
Real Time Assessment Of Security Threats Traditional SIEM Deployment Model Background PDF
This slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats traditional siem deployment model background pdf. Use them to share invaluable insights on threat and vulnerability management processes, visualization, retention, analytics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Real Time Assessment Of Security Threats Cloud SIEM Model Icons PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats cloud siem model icons pdf. Use them to share invaluable insights on threat and vulnerability management processes, aggregation, collection, correlation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this 5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF Use them to share invaluable insights on Concerns To Catered, Handling Initiatives, Implementing Middleware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF. Use them to share invaluable insights on Nodes Authentication, Rule Consistency, Policy Enforcement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Automation Tools Integration Time To Fix Security Threat With Manual Testing Template PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Deliver and pitch your topic in the best possible manner with this IT Security Automation Tools Integration Time To Fix Security Threat With Manual Testing Template PDF. Use them to share invaluable insights on Manual Testing, Fix Error, 3 Working Days and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Catering Business Investment Funding Deck Problem Statement Template PDF
Following slide showcases major challenge faced by industry in ordering food services. It highlights major issues such as broken state of ordering food in offices, managing customer expectations etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Catering Business Investment Funding Deck Problem Statement Template PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
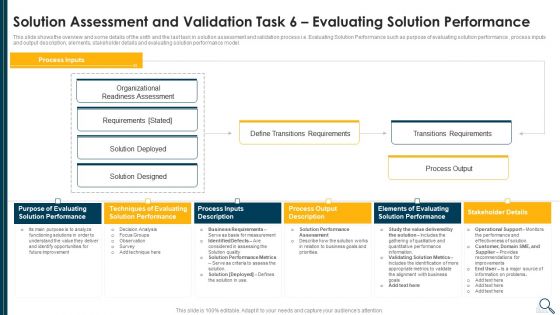
Solution Evaluation Criteria Assessment And Threat Impact Matrix Solution Assessment And Validation Task Ideas PDF
This slide shows the solution assessment and validation model or framework which helps to assess and determine that which solution best fits the business requirements along with the model inputs and outputs. Deliver and pitch your topic in the best possible manner with this solution evaluation criteria assessment and threat impact matrix solution assessment and validation task ideas pdf. Use them to share invaluable insights on solution assessment and validation model of the company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
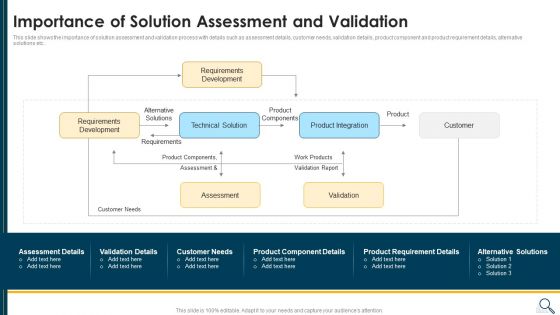
Solution Evaluation Criteria Assessment And Threat Impact Matrix Importance Of Solution Assessment Clipart PDF
This slide shows the importance of solution assessment and validation process with details such as assessment details, customer needs, validation details, product component and product requirement details, alternative solutions etc. Deliver and pitch your topic in the best possible manner with this solution evaluation criteria assessment and threat impact matrix importance of solution assessment clipart pdf. Use them to share invaluable insights on requirements development, product integration, customer, product components and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
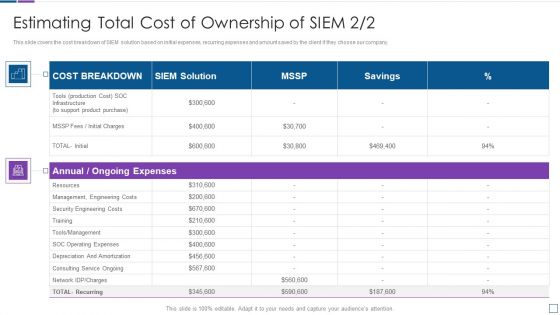
Estimating Total Cost Of Ownership Of SIEM Real Time Assessment Of Security Threats Infographics PDF
This slide covers the cost breakdown of SIEM solution based on initial expenses, recurring expenses and amount saved by the client if they choose our company. Deliver and pitch your topic in the best possible manner with this estimating total cost of ownership of siem real time assessment of security threats infographics pdf. Use them to share invaluable insights on ongoing expenses, cost breakdown, siem solution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Gap Identification Current Approach Process Ppt Outline Objects PDF
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era gap identification current approach process ppt outline objects pdf. Use them to share invaluable insights on gap identification current approach process flaws and cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Handling Cyber Threats Digital Era Communication Plan For Cyber Breaches Ppt Icon Background Images PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era communication plan for cyber breaches ppt icon background images pdf. Use them to share invaluable insights on communication plan for cyber breaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
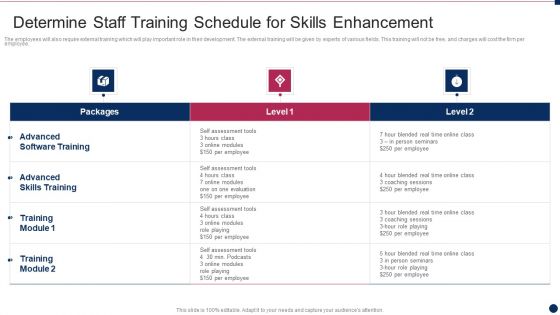
Threat Management At Workplace Determine Staff Training Schedule For Skills Enhancement Graphics Pdf
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver and pitch your topic in the best possible manner with this threat management at workplace determine staff training schedule for skills enhancement graphics pdf. Use them to share invaluable insights on advanced skills training, advanced software training, blended real time and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
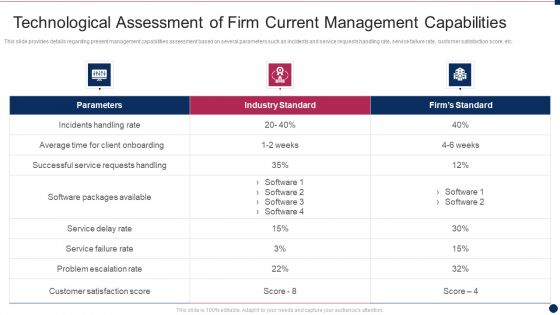
Threat Management At Workplace Technological Assessment Of Firm Current Management Structure PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver and pitch your topic in the best possible manner with this threat management at workplace technological assessment of firm current management structure pdf. Use them to share invaluable insights on service delay rate, average time for client onboarding, successful service requests handling and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Corporate Fraud Overview Types Facts And Statistics Fraud Threat Administration Guide Icons PDF
This slide provides an overview about corporate frauds along with the factual information of global fraud events. It also includes the statistics on fraud volume as well as fraud value.Deliver and pitch your topic in the best possible manner with this Corporate Fraud Overview Types Facts And Statistics Fraud Threat Administration Guide Icons PDF. Use them to share invaluable insights on Experienced Fraud, Event Past, Experienced Organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
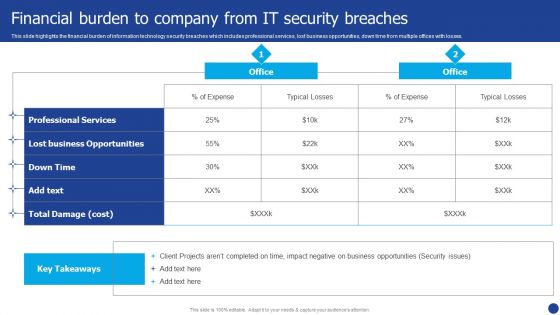
Information Technology Threat Mitigation Methods Financial Burden To Company From IT Security Breaches Formats PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Financial Burden To Company From IT Security Breaches Formats PDF. Use them to share invaluable insights on Professional Services, Lost Business Opportunities, Expense and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Major Strategies To Nurture Effective Vendor Association What Are The Problems Demonstration PDF
This slide covers the problem areas of the suppliers such as unclear expectations, poor governance, poor cultural fir, miscommunication, not mutually beneficial etc. Deliver and pitch your topic in the best possible manner with this major strategies to nurture effective vendor association what are the problems demonstration pdf. Use them to share invaluable insights on unclear expectations, poor governance, coordinated management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Supplier Relationship Management What Are The Problems With Suppliers Topics PDF
This slide covers the problem areas of the suppliers such as unclear expectations, poor governance, poor cultural fir, miscommunication, not mutually beneficial etc. Deliver and pitch your topic in the best possible manner with this Supplier Relationship Management What Are The Problems With Suppliers Topics PDF Use them to share invaluable insights on Unclear Expectations, Suppliers Miscommunicate, Coordinated Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
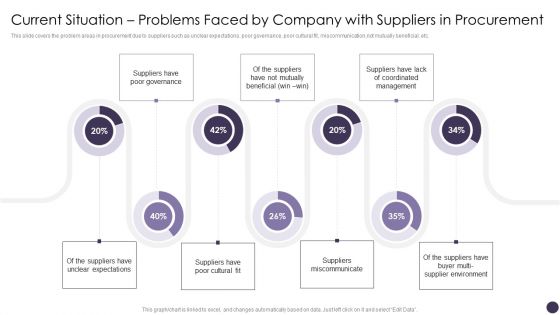
Current Situation Problems Faced By Company With Suppliers In Procurement Professional PDF
This slide covers the problem areas in procurement due to suppliers such as unclear expectations, poor governance, poor cultural fit, miscommunication,not mutually beneficial, etc. Deliver and pitch your topic in the best possible manner with this Current Situation Problems Faced By Company With Suppliers In Procurement Professional PDF. Use them to share invaluable insights on Poor Governance, Unclear Expectations, Supplier Environment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Global Cyber Terrorism Incidents On The Rise IT Dashboard For Threat Tracking Of Cyber Terrorism Clipart PDF
This slide depicts the dashboard for threat tracking of cyber terrorism by covering top threats, threats by class name, etc. Deliver and pitch your topic in the best possible manner with this global cyber terrorism incidents on the rise it dashboard for threat tracking of cyber terrorism clipart pdf. Use them to share invaluable insights on dashboard for threat tracking of cyber terrorism and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Footwear And Accessories Business Pitch Deck Major Problems Faced By The Customers Summary PDF
Following slide displays the major problems faced by the customers. Major problems consists of low quality of raw materials, meeting the diverse expectations of customers, etc.Deliver and pitch your topic in the best possible manner with this footwear and accessories business pitch deck major problems faced by the customers summary pdf. Use them to share invaluable insights on low quality of raw materials, meeting, expectations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

 Home
Home