Process Safety Dashboard

Circular Chart 9 Distinct Views On Single Issue Charts And Networks PowerPoint Templates
We present our circular chart 9 distinct views on single issue Charts and Networks PowerPoint templates.Present our Circle Charts PowerPoint Templates because analyse your plans with equal sincerity. Use our Arrows PowerPoint Templates because the structure of our templates allows you to effectively highlight the key issues concerning the growth of your business. Use our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Download our Shapes PowerPoint Templates because you should explain the process by which you intend to right it. Download our Flow Charts PowerPoint Templates because the great Bald headed Eagle embodies your personality. the eagle eye to seize upon the smallest of oppurtunities.Use these PowerPoint slides for presentations relating to abstract, arrow, art, background, ball, blue, business, button, chart, circle, circular, clip, company, concept, cycle, diagram, edit, editable, element, green, guide, icon, leader, management, marketing, model, numbers, organization, plans, point, presentation, purple, red, report, representation, seven, sphere, stakeholder, team, text, tool, vector, white. The prominent colors used in the PowerPoint template are Purple, Green, Yellow. Customers tell us our circular chart 9 distinct views on single issue Charts and Networks PowerPoint templates are Charming. PowerPoint presentation experts tell us our ball PowerPoint templates and PPT Slides are Dazzling. People tell us our circular chart 9 distinct views on single issue Charts and Networks PowerPoint templates are Magical. People tell us our blue PowerPoint templates and PPT Slides will impress their bosses and teams. Customers tell us our circular chart 9 distinct views on single issue Charts and Networks PowerPoint templates are Graceful. People tell us our chart PowerPoint templates and PPT Slides are Dynamic.

IT And Cloud Facilities Management Content Ppt PowerPoint Presentation Infographics Layouts PDF
Presenting it and cloud facilities management content ppt powerpoint presentation infographics layouts pdf to provide visual cues and insights. Share and navigate important information on eleven stages that need your due attention. This template can be used to pitch topics like optimization and decision making, performance and cost functions, capital budgeting, kpi metrics and dashboard, contract and workflow management, interdependence, resiliency and security. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
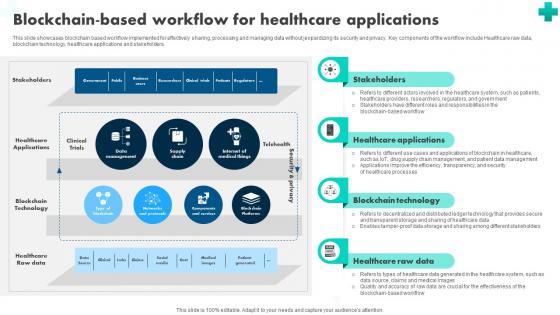
A56 How Blockchain Is Reshaping Blockchain Based Workflow For Healthcare BCT SS V
This slide showcases blockchain based workflow implemented for effectively sharing, processing and managing data without jeopardizing its security and privacy. Key components of the workflow include Healthcare raw data, blockchain technology, healthcare applications and stakeholders. Want to ace your presentation in front of a live audience Our A56 How Blockchain Is Reshaping Blockchain Based Workflow For Healthcare BCT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

User Experience Framework Of Digital Insurance Portal Brochure PDF
This slide illustrates user experience framework of digital insurance portal. It provides information about enterprise application integration, external system integration, secured messaging, website content management, etc. Showcasing this set of slides titled User Experience Framework Of Digital Insurance Portal Brochure PDF. The topics addressed in these templates are Management, Customized Dashboards, Policy Administration System. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Table Of Contents Risk Management For Organization Essential Assets Priorities Infographics PDF
This is a table of contents risk management for organization essential assets priorities infographics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like leveraging workforce, dashboard, impact assessment, budget assessment, ensuring financial assets security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Functions Management Table Of Content Ppt Model Files PDF
This is a information technology functions management table of content ppt model files pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like introduction to infrastructure, asset management process, inventory and condition assessment, deterioration modeling, optimization and decision making, performance and cost functions, interdependence, resiliency and security, contract and workflow management, commissioning new facilities, capital budgeting, metrics and dashboard. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Products And Services Offered Manufacturing Control Software Company Investor PPT Template
This slide caters to details related to a company that provides solutions to manufacturers unique problems, creating secure, well-designed solutions, and generating data-driven insights. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Manufacturing Control Software Company Investor PPT Template to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Web Access Control Solution Importance Of Secure Web Gateway For Businesses
This slide talks about the role of Secure Web Gateway in organizations. The purpose of this slide is to explain why companies require SWG. The components covered are ID provider, data center, client connector, global policy engine, real-time analytics, etc. Explore a selection of the finest Web Access Control Solution Importance Of Secure Web Gateway For Businesses here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Web Access Control Solution Importance Of Secure Web Gateway For Businesses to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf
This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. This Ack Tee Introduction And Version 1 0 Secure Multi Party Slides Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
Confidential Computing Architecture Based On Azure Services Secure Multi Party Icons Pdf
This slide represents the architecture of confidential computing based on Azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Confidential Computing Architecture Based On Azure Services Secure Multi Party Icons Pdf With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Confidential Computing Architecture Based On Azure Services Secure Multi Party Icons Pdf today and make your presentation stand out from the rest.
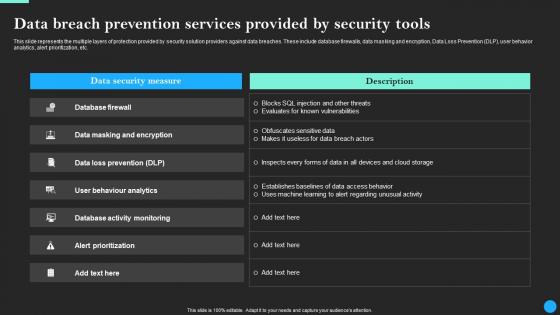
Data Breach Prevention Services Provided Data Breach Prevention Graphics Pdf
This slide represents the multiple layers of protection provided by security solution providers against data breaches. These include database firewalls, data masking and encryption, Data Loss Prevention DLP, user behavior analytics, alert prioritization, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Data Breach Prevention Services Provided Data Breach Prevention Graphics Pdfand observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
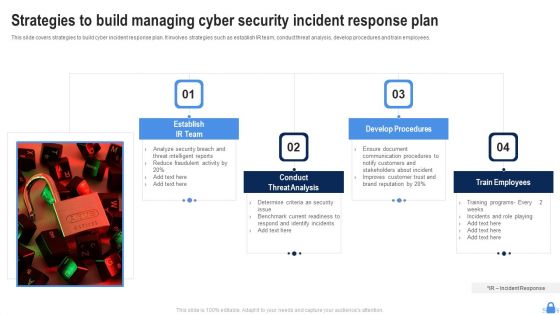
Strategies To Build Managing Cyber Security Incident Response Plan Demonstration PDF
This slide covers strategies to build cyber incident response plan. It involves strategies such as establish IR team, conduct threat analysis, develop procedures and train employees. Persuade your audience using this Strategies To Build Managing Cyber Security Incident Response Plan Demonstration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Establish IR Team, Conduct Threat Analysis, Develop Procedures. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Officer Service Company Profile Corporate And Industrial Security Services Demonstration PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Presenting Security Officer Service Company Profile Corporate And Industrial Security Services Demonstration PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Corporate Security, Industrial Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Applications Of Standard For Advanced Data Security In Cloud Computing Ppt Presentation
This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc. Slidegeeks is here to make your presentations a breeze with Applications Of Standard For Advanced Data Security In Cloud Computing Ppt Presentation With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
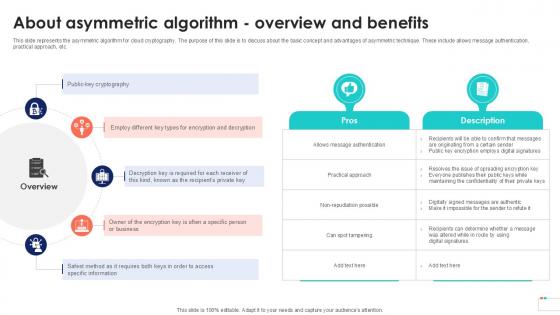
About Asymmetric Algorithm Overview Data Security In Cloud Computing Ppt Template
This slide represents the asymmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the basic concept and advantages of asymmetric technique. These include allows message authentication, practical approach, etc. Boost your pitch with our creative About Asymmetric Algorithm Overview Data Security In Cloud Computing Ppt Template. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
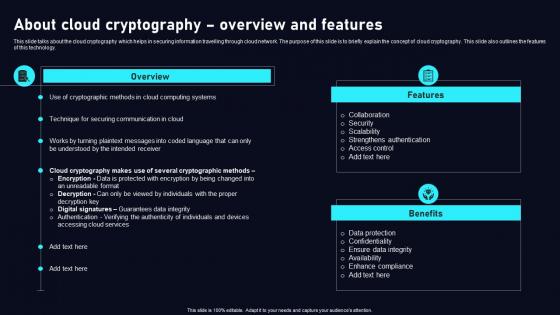
About Cloud Cryptography Cloud Data Security Using Cryptography Mockup Pdf
This slide talks about the cloud cryptography which helps in securing information travelling through cloud network. The purpose of this slide is to briefly explain the concept of cloud cryptography. This slide also outlines the features of this technology. Present like a pro with About Cloud Cryptography Cloud Data Security Using Cryptography Mockup Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
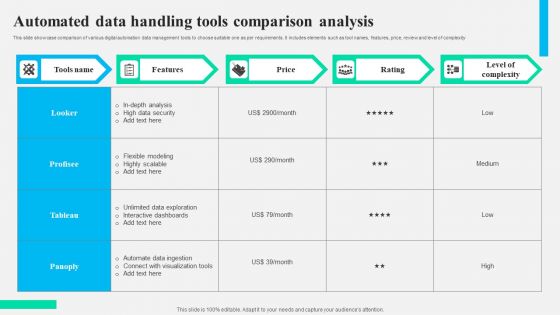
Automated Data Handling Tools Comparison Analysis Formats PDF
This slide showcase comparison of various digital automation data management tools to choose suitable one as per requirements. It includes elements such as tool names, features, price, review and level of complexity. Showcasing this set of slides titled Automated Data Handling Tools Comparison Analysis Formats PDF. The topics addressed in these templates are High Data Security, Analysis, Interactive Dashboards. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Financial Services And Healthcare Industry Scenario Analysis Secure Multi Party Sample Pdf
This slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario. The Financial Services And Healthcare Industry Scenario Analysis Secure Multi Party Sample Pdf is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
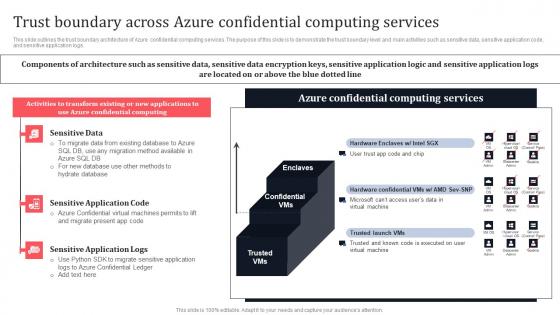
Trust Boundary Across Azure Confidential Computing Services Secure Multi Party Ideas Pdf
This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Trust Boundary Across Azure Confidential Computing Services Secure Multi Party Ideas Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
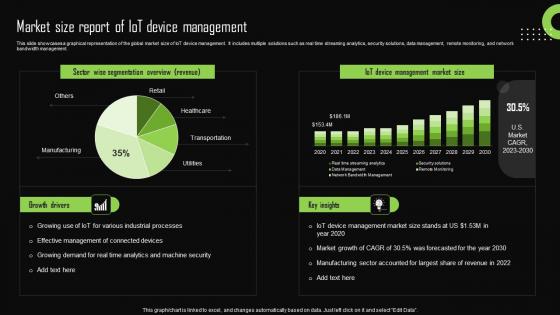
Market Size Report Of Iot Device Management Iot Device Management Demonstration Pdf
This slide showcases a graphical representation of the global market size of IoT device management. It includes multiple solutions such as real time streaming analytics, security solutions, data management, remote monitoring, and network bandwidth management. If you are looking for a format to display your unique thoughts, then the professionally designed Market Size Report Of Iot Device Management Iot Device Management Demonstration Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Market Size Report Of Iot Device Management Iot Device Management Demonstration Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
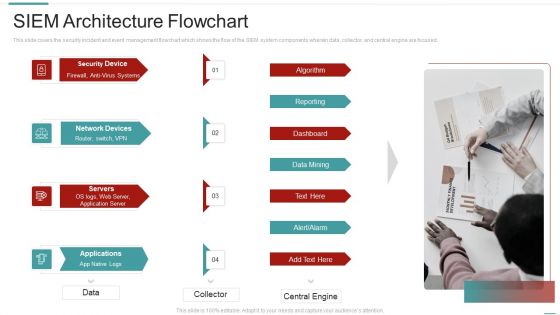
Risk Recognition Automation Siem Architecture Flowchart Ppt Summary Example File PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Presenting risk recognition automation siem architecture flowchart ppt summary example file pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reporting, dashboard, data mining, algorithm. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Threats Management Of Confidential Data Reports Icon Ppt Ideas Summary PDF
Persuade your audience using this Threats Management Of Confidential Data Reports Icon Ppt Ideas Summary PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Threats Management, Confidential Data Reports, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IoT Device Management Fundamentals Market Size Report Of IoT Device Management IoT Ss V
This slide showcases a graphical representation of the global market size of IoT device management. It includes multiple solutions such as real time streaming analytics, security solutions, data management, remote monitoring, and network bandwidth management. Slidegeeks has constructed IoT Device Management Fundamentals Market Size Report Of IoT Device Management IoT SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses
This slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc. Are you searching for a Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Immediate And Long Term Impact Of Data Security Breach Data Fortification Strengthening Defenses from Slidegeeks today.
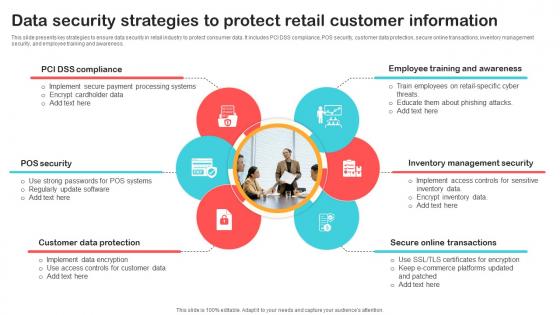
Data Security Strategies To Protect Retail Customer Optimizing Retail Operations With Digital DT SS V
This slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Security Strategies To Protect Retail Customer Optimizing Retail Operations With Digital DT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cyber Security Asset Risk Analysis Software Report Pictures PDF
This slide covers the risk identification status report for different cyber incidents. It includes malicious insider activity, confidential data loss, system failure and denial of service attacks. Pitch your topic with ease and precision using this Cyber Security Asset Risk Analysis Software Report Pictures PDF. This layout presents information on Cyber Security Asset Risk, Analysis Software Report. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Technology Analytics Using Splunk Big Data Microsoft Pdf
Following slide highlights technology analysis with splunk big data. The purpose of this slide is to improve the user experience by enhancing security and improving the user interface. It includes elements such as customer experience, IT performance, compliance, etc. Pitch your topic with ease and precision using this Technology Analytics Using Splunk Big Data Microsoft Pdf This layout presents information on Customer Experience, Security, Compliance It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Strategic Tips To Improve Physical Data Center Management Security Download PDF
This slide highlights tips to improve security of physical datacentre by having a thorough understanding of security measures and service level agreements. It covers secure location, physical access controls with building management security. Presenting Strategic Tips To Improve Physical Data Center Management Security Download PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Secure Location, Physical Access Controls, Secure Building Management Systems. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Officer Service Company Profile Employees Rules And Regulations Inspiration PDF
This slide highlights the security guard company rules and regulations which showcases In and out time, note visitor name, and wear uniform at working hours. This is a Security Officer Service Company Profile Employees Rules And Regulations Inspiration PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Officer, Employees, Security Officer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Officer Service Company Profile Mission Vision And Core Values Sample PDF
This slide highlights the security company long term and short term objectives which includes trust, collaboration, service, and innovation as base of core values. Presenting Security Officer Service Company Profile Mission Vision And Core Values Sample PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Core Values, Integrity, Commitment, Passion, Team work. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
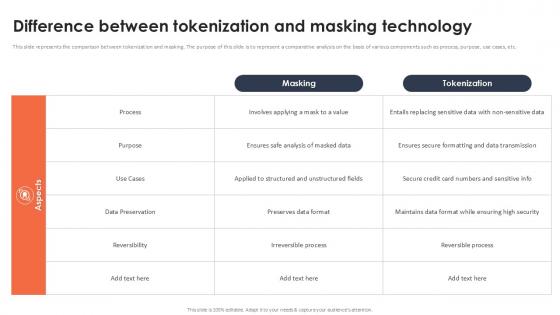
Difference Between Tokenization And Masking Technology Securing Your Data Ppt Powerpoint
This slide represents the comparison between tokenization and masking. The purpose of this slide is to represent a comparative analysis on the basis of various components such as process, purpose, use cases, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Difference Between Tokenization And Masking Technology Securing Your Data Ppt Powerpoint and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Real Time Assessment Of Security Threats Fully Managed Service Model Demonstration PDF
This slide covers the SIEM as a service model wherein all the steps are taken care by our company and the client just have to provide us the relevant data. Deliver an awe inspiring pitch with this creative real time assessment of security threats fully managed service model demonstration pdf bundle. Topics like threat and vulnerability management processes, reporting, retention, correlation, collection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Datafy Measures To Maintain Data Security In Datafication Diagrams PDF
This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls. Welcome to our selection of the Datafy Measures To Maintain Data Security In Datafication Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Data Analysis Reporting Tools Ppt PowerPoint Presentation Professional Layout Cpb Pdf
Presenting this set of slides with name data analysis reporting tools ppt powerpoint presentation professional layout cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like cyber security detection response to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Cloud Security Checklist Access Control Cloud Computing Security IT Ppt Show PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. Deliver and pitch your topic in the best possible manner with this cloud security checklist access control cloud computing security it ppt show pdf. Use them to share invaluable insights on cloud services, security, privileged credentials, administrative and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
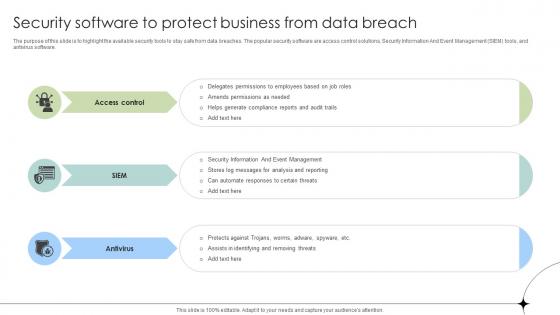
Security Software To Protect Business From Data Breach Data Fortification Strengthening Defenses
The purpose of this slide is to highlight the available security tools to stay safe from data breaches. The popular security software are access control solutions, Security Information And Event Management SIEM tools, and antivirus software. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Security Software To Protect Business From Data Breach Data Fortification Strengthening Defenses for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Architecture Of Cloud Security Cloud Information Security Ppt Inspiration Samples PDF
This slide defines the architecture of the cloud security system and how data is kept, managed, and secured based on customer and service providers responsibilities. This is a Architecture Of Cloud Security Cloud Information Security Ppt Inspiration Samples PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customer Responsibility, Cloud Service, Provider Responsibility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
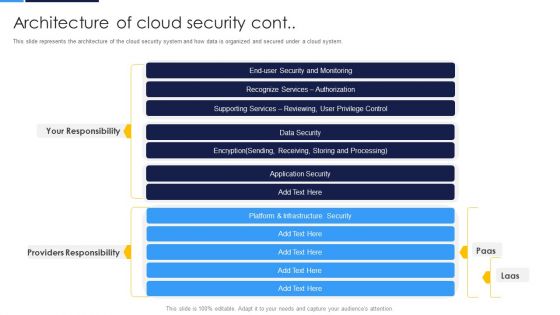
Cloud Security Assessment Architecture Of Cloud Security Cont Diagrams PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Architecture Of Cloud Security Cont Diagrams PDF bundle. Topics like Security And Monitoring, Recognize Services, Supporting Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
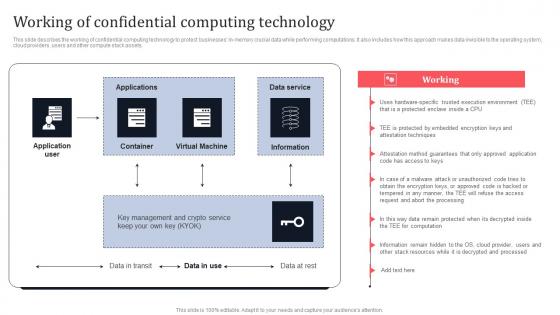
Working Of Confidential Computing Technology Secure Multi Party Information Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Of Confidential Computing Technology Secure Multi Party Information Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
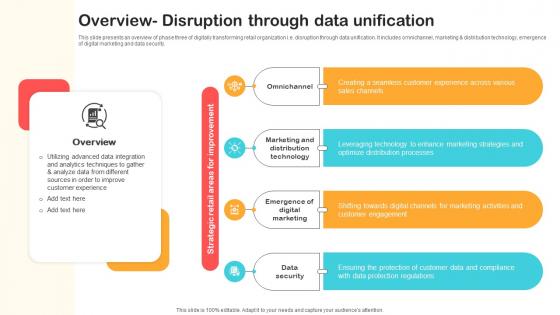
Overview Disruption Through Data Unification Optimizing Retail Operations With Digital DT SS V
This slide presents an overview of phase three of digitally transforming retail organization i.e. disruption through data unification. It includes omnichannel, marketing and distribution technology, emergence of digital marketing and data security.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Overview Disruption Through Data Unification Optimizing Retail Operations With Digital DT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Hashing Implementation Using Cloud Data Security Using Cryptography Ideas Pdf
This slide explain the working of hashing technique. The purpose of this slide is to demonstrate the procedure of hashing algorithm using hash table. The key points discussed are hash table, hash function, hash value and key value pairs. Find a pre designed and impeccable Hashing Implementation Using Cloud Data Security Using Cryptography Ideas Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Web Access Control Solution Integration Of Swg Inside Sase Architecture
This slide represents the architecture of Relationship between Secure Access Service Edge and Secure Web Gateway integration. The purpose of this slide is to illustrate the collaboration of SASE and SWG inside a network. Key components included are websites, cloud apps, etc. The Web Access Control Solution Integration Of Swg Inside Sase Architecture is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Data Security In Cloud Computing Cloud Data Security Using Cryptography Formats Pdf
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues. Retrieve professionally designed Data Security In Cloud Computing Cloud Data Security Using Cryptography Formats Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Hashing Implementation Using Data Security In Cloud Computing Ppt Powerpoint
This slide explain the working of hashing technique. The purpose of this slide is to demonstrate the procedure of hashing algorithm using hash table. The key points discussed are hash table, hash function, hash value and key-value pairs. Retrieve professionally designed Hashing Implementation Using Data Security In Cloud Computing Ppt Powerpoint to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

CASB 2 0 IT Cloud Access Security Broker Pillar Data Security
This slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. The CASB 2 0 IT Cloud Access Security Broker Pillar Data Security is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Big Data Analytics Service Framework Graphics PDF
Mentioned slide illustrates big data managed services which can be used by business to gather real time company analytics. It includes services such as data acquisition, storage, testing, monitoring, data security, analysis, architecture, development, migration and optimization. Persuade your audience using this Big Data Analytics Service Framework Graphics PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Data Analysis, Assessment Of Business, Management Infrastructure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
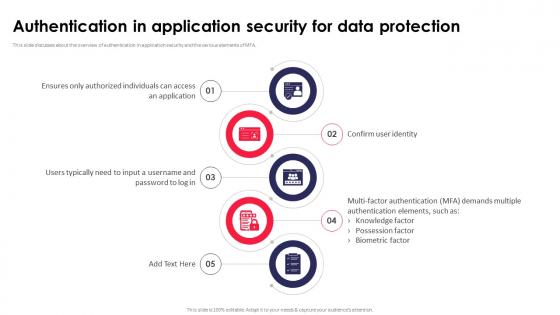
Authentication In Application Security For Data Protection Application Security Testing
This slide discusses about the overview of authentication in application security and the various elements of MFA. Present like a pro with Authentication In Application Security For Data Protection Application Security Testing. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

The Ultimate Guide To KPMG Business Canvas Model Value Proposition Strategy SS V
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements This slide covers key elements of value proposition under KPMG canvas business model. The purpose of this template is to provide an overview on elements such as industry expertise, global reach, integrated services, technology enabled solutions, risk management expertise, etc. contributing towards executing KPMG operations effectively of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. The Ultimate Guide To KPMG Business Canvas Model Value Proposition Strategy SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
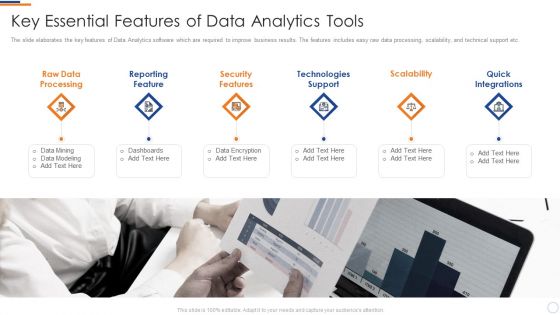
Business Intelligence And Big Key Essential Features Of Data Analytics Tools Topics PDF
The slide elaborates the key features of Data Analytics software which are required to improve business results. The features includes easy raw data processing, scalability, and technical support etc. This is a business intelligence and big key essential features of data analytics tools topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like raw data processing, reporting feature, security features, technologies support, scalability quick integrations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
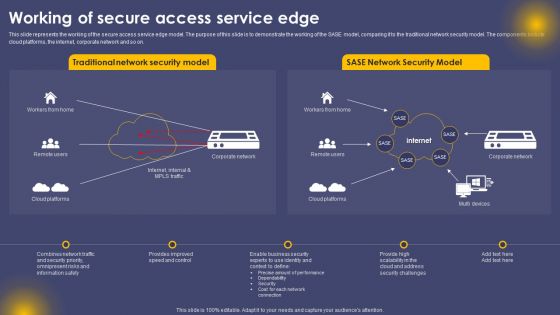
Working Of Secure Access Service Edge Ppt Summary Ideas PDF
This slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. The Working Of Secure Access Service Edge Ppt Summary Ideas PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
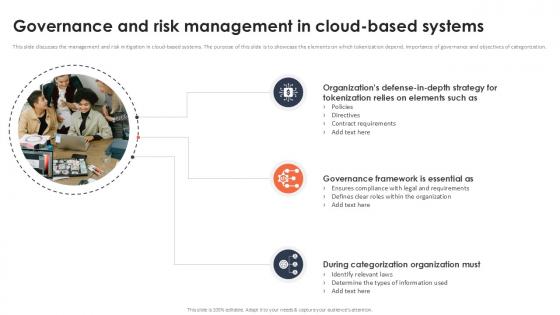
Governance And Risk Management In Cloud Based Systems Securing Your Data Ppt Example
This slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization. This modern and well-arranged Governance And Risk Management In Cloud Based Systems Securing Your Data Ppt Example provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Trend 1 Increase In Adoption Of Edge Developing Strategic Insights Using Big Data Analytics SS V
This slide showcases emerging trend of adoption of edge computing technology which helps in improving data integration processes. It provides information regarding market size, edge infrastructure, virtual reality, data security and AIoT devices etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Trend 1 Increase In Adoption Of Edge Developing Strategic Insights Using Big Data Analytics SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Trend 1 Increase In Adoption Of Edge Developing Strategic Insights Using Big Data Analytics SS V.

Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf
This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf from Slidegeeks and deliver a wonderful presentation.
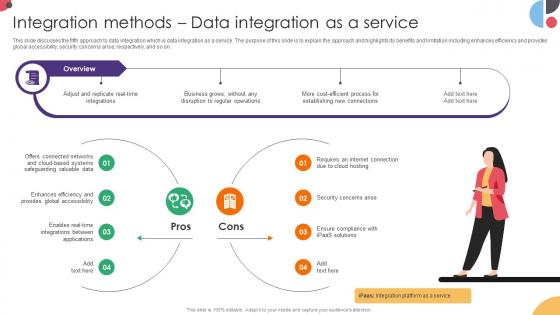
Integration Methods Data Integration As A Service Data Integration Strategies For Business
This slide discusses the fifth approach to data integration which is data integration as a service. The purpose of this slide is to explain the approach and highlights its benefits and limitation including enhances efficiency and provides global accessibility, security concerns arise, respectively, and so on. Boost your pitch with our creative Integration Methods Data Integration As A Service Data Integration Strategies For Business. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example
This slide demonstrates the working structure of hashing technique of cloud cryptography with the help of an illustrative diagram. The key components included are original data, hashing algorithm, one-way hash, digital signature, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Workflow Of Cloud Cryptography Data Security In Cloud Computing Ppt Example and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
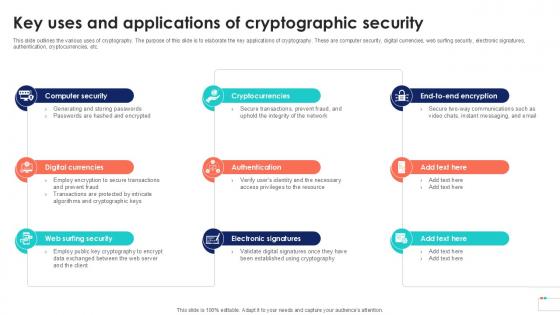
Key Uses And Applications Of Data Security In Cloud Computing Ppt Slide
This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc. Take your projects to the next level with our ultimate collection of Key Uses And Applications Of Data Security In Cloud Computing Ppt Slide. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
Security Techniques For Digital Terrorism Icon Elements PDF
Persuade your audience using this Security Techniques For Digital Terrorism Icon Elements PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Digital Terrorism Icon, Security Techniques. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
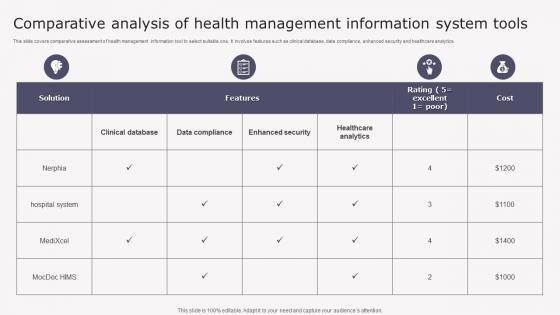
Transforming Medicare Services Using Health Comparative Analysis Health Background Pdf
This slide covers comparative assessment of health management information tool to select suitable one. It involves features such as clinical database, data compliance, enhanced security and healthcare analytics. Want to ace your presentation in front of a live audience Our Transforming Medicare Services Using Health Comparative Analysis Health Background Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
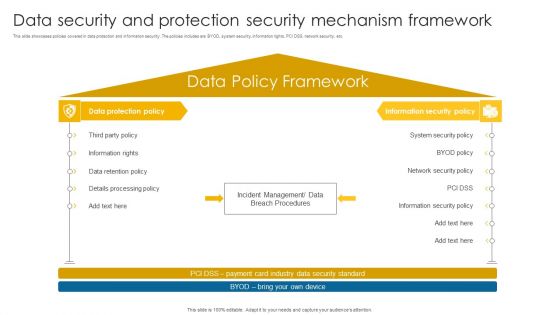
Data Security And Protection Security Mechanism Framework Background PDF
This slide showcases policies covered in data protection and information security. The policies includes are BYOD, system security, information rights, PCI DSS, network security, etc.Pitch your topic with ease and precision using this Data Security And Protection Security Mechanism Framework Background PDF. This layout presents information on Information Rights, Retention Policy, Details Processing. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Naas Architectural Framework Naas And Secure Access Service Edge Sase Professional PDF
This slide talks about the relationship between network as a service and secure access service edge. The SAFE provides DNS filtering, secure web gateway, anti-malware, file sandboxing, cloud-delivered firewall, app visibility and control, and so on. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Naas Architectural Framework Naas And Secure Access Service Edge Sase Professional PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Naas Architectural Framework Naas And Secure Access Service Edge Sase Professional PDF.

 Home
Home