Phishing

Developing Firm Security Strategy Plan Facilities Offered By Implementation Of Security Centre Formats PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a developing firm security strategy plan facilities offered by implementation of security centre formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
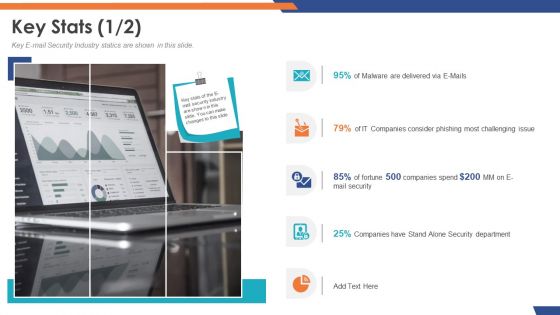
Email Security Market Research Report Key Stats Department Topics PDF
Presenting this set of slides with name email security market research report key stats department topics pdf. This is a five stage process. The stages in this process are 95 percent of malware are delivered via e mails, 79 percent of it companies consider phishing most challenging issue. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
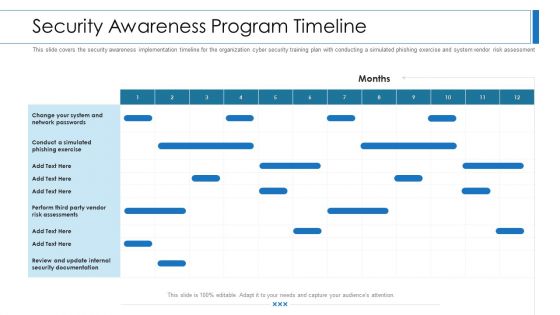
Workforce Security Realization Coaching Plan Security Awareness Program Timeline Topics PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan security awareness program timeline topics pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
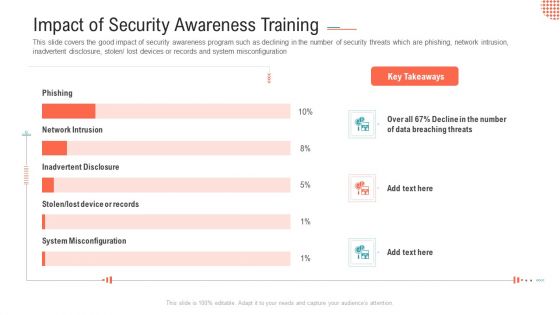
Impact Of Security Awareness Training Ppt Pictures Design Templates PDF
This slide covers the budget to improve Cyber threat detection rates, reduce downtime due to network unavailability and keeping business secure against cyber attacks Deliver and pitch your topic in the best possible manner with this impact of security awareness training ppt pictures design templates pdf. Use them to share invaluable insights on phishing breakdown, network intrusion breakdown, system misconfiguration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security Awareness Tracking Kpis Ppt Layouts Graphics Template PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction.Deliver an awe-inspiring pitch with this creative security awareness tracking kpis ppt layouts graphics template pdf. bundle. Topics like phishing informants, social engineering, refresher training scores can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Network Staff Learning Security Awareness Program Timeline Portrait PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe-inspiring pitch with this creative organizational network staff learning security awareness program timeline portrait pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Awareness Program Timeline Ppt Outline Introduction PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver an awe inspiring pitch with this creative Security Awareness Program Timeline Ppt Outline Introduction Pdf bundle. Topics like security awareness program timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Business Internet Security Threat Analysis Slides PDF
This slide exhibits major enterprise security breach incidents . it includes multiple breaches such as staff responding to phishing mail and website application affected. Presenting key business internet security threat analysis slides pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including key business internet security threat analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Facilities Rendered By Security Centre Implementation Ppt Pictures Design Templates PDF
This slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Deliver an awe inspiring pitch with this creative facilities rendered by security centre implementation ppt pictures design templates pdf bundle. Topics like Determine, organization, Security, Systems, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Timeline For The Implementation Of IT Security IT Ppt Inspiration Portrait PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative timeline for the implementation of it security it ppt inspiration portrait pdf bundle. Topics like network, internal security, perform, phishing exercise can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Detail Impact Data Security Plan Can Reduce The Risk Of Data Breach In Organization Ppt Slides Influencers PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this information security detail impact data security plan can reduce the risk of data breach in organization ppt slides influencers pdf. Use them to share invaluable insights on phishing breakdown, network intrusion breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Global Cyber Terrorism Incidents On The Rise IT Trojans As Cyber Terrorism Tool Graphics PDF
This slide depicts the Trojans as a cyber terrorism tool in which phishing is used to manipulate a user into executing the infected file. Deliver an awe inspiring pitch with this creative global cyber terrorism incidents on the rise it trojans as cyber terrorism tool graphics pdf bundle. Topics like trojans as cyber terrorism tool can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
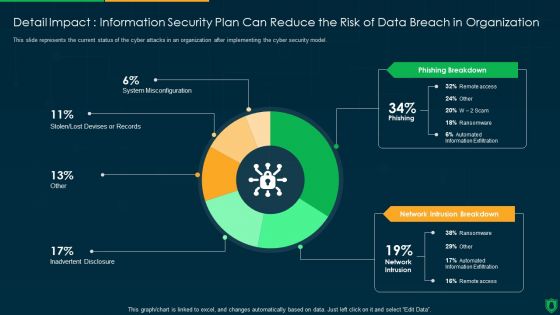
Detail Impact Information Security Plan Can Reduce The Risk Of Data Breach Ppt PowerPoint Presentation File Visual Aids PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver an awe inspiring pitch with this creative detail impact information security plan can reduce the risk of data breach ppt powerpoint presentation file visual aids pdf bundle. Topics like phishing breakdown, network intrusion breakdown, inadvertent desclosure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
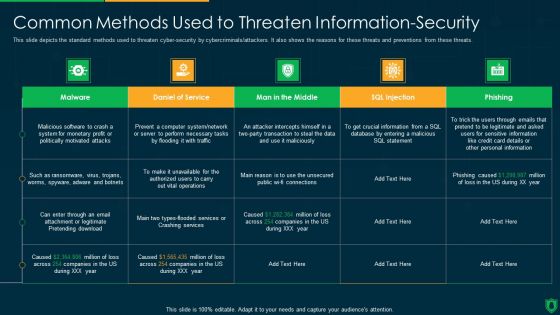
Info Security Common Methods Used To Threaten Information Security Ppt PowerPoint Presentation Gallery Clipart Images PDF
This slide depicts the standard methods used to threaten cyber-security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Deliver an awe inspiring pitch with this creative info security common methods used to threaten information security ppt powerpoint presentation gallery clipart images pdf bundle. Topics like personal information, phishing caused, sql statement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Terrorism Assault Trojans As Cyber Terrorism Tool Brochure PDF
This slide depicts the Trojans as a cyber terrorism attacks tool in which phishing is used to manipulate a user into executing the infected file.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault trojans as cyber terrorism tool brochure pdf Use them to share invaluable insights on trojans as cyber terrorism tool and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
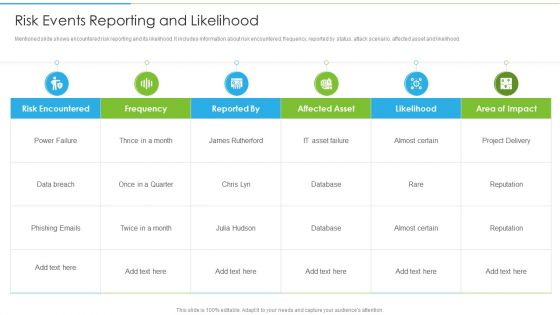
Ways To Accomplish ISO 27001 Accreditation Risk Events Reporting And Likelihood Guidelines PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver and pitch your topic in the best possible manner with this Ways To Accomplish ISO 27001 Accreditation Risk Events Reporting And Likelihood Guidelines PDF. Use them to share invaluable insights on Risk Encountered, Affected Asset, Phishing Emails and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Four Computer Security Threats Rules PDF
This slide shows the 4 threats to cyber security. It includes phishing attacks, cloud jacking, IoT devices and insider threats.Pitch your topic with ease and precision using this Four Computer Security Threats Rules PDF This layout presents information on Data Manipulation, Attacker Attempts, Sensitive Information It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
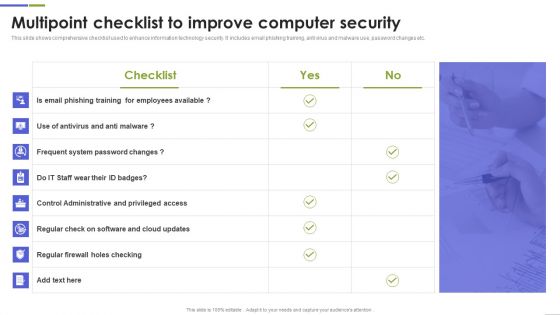
Multipoint Checklist To Improve Computer Security Guidelines PDF
This slide shows comprehensive checklist used to enhance information technology security. It includes email phishing training, anti virus and malware use, password changes etc. Showcasing this set of slides titled Multipoint Checklist To Improve Computer Security Guidelines PDF The topics addressed in these templates are Frequent System, Control Administrative, System Password All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Risk Events Reporting And Likelihood Topics PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an awe inspiring pitch with this creative Risk Events Reporting And Likelihood Topics PDF bundle. Topics like Risk Encountered, Phishing Emails, Affected Asset can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Information Security Risk Evaluation Gap Assessment Of Organization Information Security Icons PDF
This slide showcases gap assessment of information security capabilities of organization. It also provides solutions to tackle the problems faced by company like, frequent malware attacks and lack of awareness among employees.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Gap Assessment Of Organization Information Security Icons PDF bundle. Topics like Frequent Malware, Phishing Attacks, Ransomware Attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
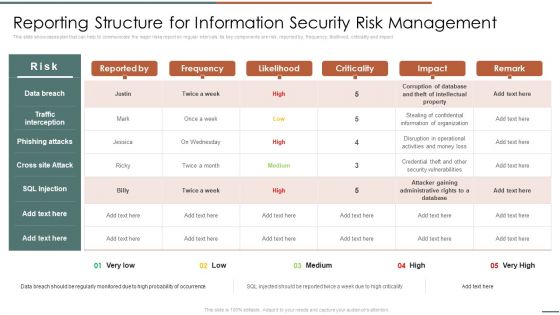
Information Security Risk Evaluation Reporting Structure For Information Security Risk Management Guidelines PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Reporting Structure For Information Security Risk Management Guidelines PDF bundle. Topics like Phishing Attacks, Cross Attack, Security Vulnerabilities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
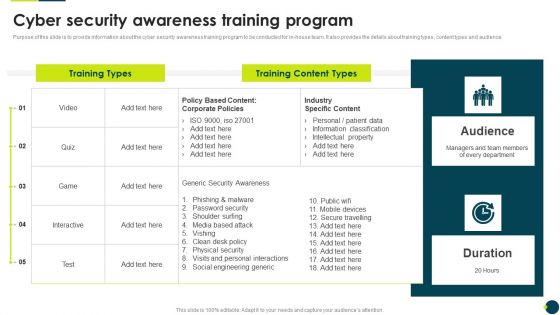
IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF
Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Cyber Security Awareness Training Program Graphics PDF bundle. Topics like Phishing Malware, Password Security, Shoulder Surfing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Customer Relationship Management Implementation Steps Enable Data Security Pictures PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver and pitch your topic in the best possible manner with this Customer Relationship Management Implementation Steps Enable Data Security Pictures PDF. Use them to share invaluable insights on Factor Authentication, Phishing Malware, Accessing Organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
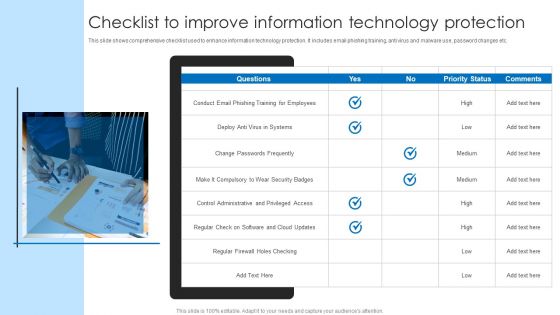
Checklist To Improve Information Technology Protection Inspiration PDF
This slide shows comprehensive checklist used to enhance information technology protection. It includes email phishing training, anti virus and malware use, password changes etc. Presenting Checklist To Improve Information Technology Protection Inspiration PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Security, Employees, Information Technology Protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Protection Improvement Plan Impact On Business Designs PDF
This slide shows difference between before and after implementing cyber protection improvement plan in business. It includes types phishing attacks, malware attacks, data breaches, etc. Showcasing this set of slides titled Cyber Protection Improvement Plan Impact On Business Designs PDF. The topics addressed in these templates are Cyber Protection Improvement, Plan Impact On Business. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Various Information Technology Faced By Software Company Slides PDF
This slide illustrates various pain points faced by IT software company, their impact and strategies adopted to overcome these obstacle for increased software functionality and efficiency. Pitch your topic with ease and precision using this Various Information Technology Faced By Software Company Slides PDF. This layout presents information on Software Company, Phishing Attacks, Massive Expenditure. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Email Security Encryption And Data Loss Prevention Your Problem E Mail Security Proposal Rules PDF
This slide covers the problems that are faced by the clients. Presenting email security encryption and data loss prevention your problem e mail security proposal rules pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security confidential data, protection against malware, protection phishing scams, threat weak password. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
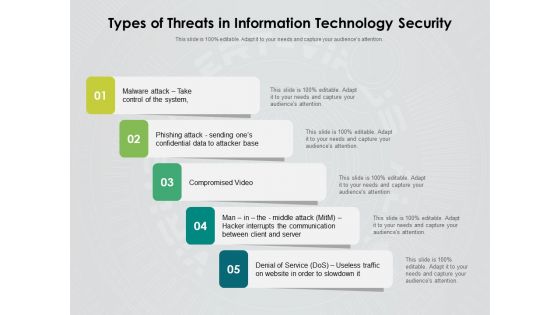
Types Of Threats In Information Technology Security Ppt PowerPoint Presentation Inspiration Rules PDF
Persuade your audience using this types of threats in information technology security ppt powerpoint presentation inspiration rules pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including malware attack take control of the system, phishing attack sending ones confidential data to attacker base, compromised video, man in the middle attack hacker interrupts the communication between client and server, denial of service dos, useless traffic on website in order to slowdown it. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Cloud Based Email Security Market Report Issues Faced By Companies Data Ppt Icon Templates PDF
Various issues faced by the end user in E Mail marketing Industry are shown in this slide. Presenting cloud based email security market report issues faced by companies data ppt icon templates pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Private Funding In The Age Of COVID 19 Addressing Response Initiatives By PE Firms To Combat Pandemic Infographics PDF
This slide provides details about different response initiatives by PE firms to combat pandemic by developing crisis response plan, implementing phishing measures, etc. Presenting private funding in the age of covid 19 addressing response initiatives by pe firms to combat pandemic infographics pdf to provide visual cues and insights. Share and navigate important information on eleven stages that need your due attention. This template can be used to pitch topics like potential, infrastructure, digital capabilities, communication, develop. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
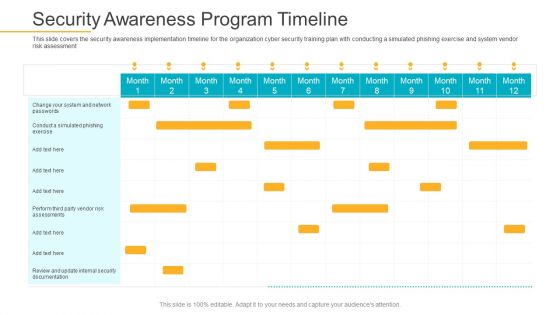
Data Breach Prevention Recognition Security Awareness Program Timeline Inspiration PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition security awareness program timeline inspiration pdf. Use them to share invaluable insights on security awareness, implementation timeline, organization, cyber security training plan, risk assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Awareness Program Timeline Hacking Prevention Awareness Training For IT Security Professional PDF
This slide covers the security awareness implementation timeline for the organization cyber security training plan with conducting a simulated phishing exercise and system vendor risk assessment. This is a security awareness program timeline hacking prevention awareness training for it security professional pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like perform, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
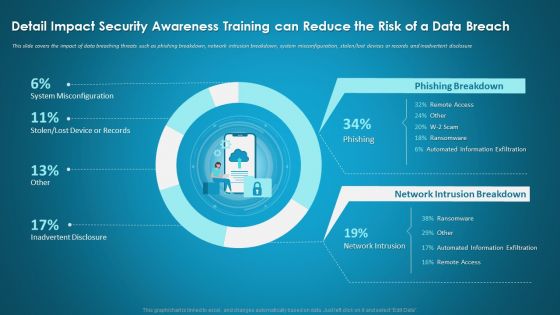
Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Ppt Model Guidelines PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver and pitch your topic in the best possible manner with this detail impact security awareness training can reduce the risk of a data breach ppt model guidelines pdf. Use them to share invaluable insights on network intrusion breakdown, automated information, security awareness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
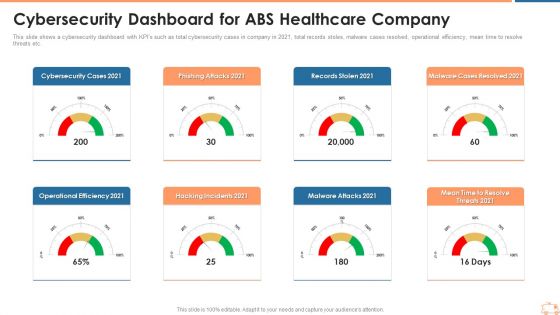
Cybersecurity Dashboard For ABS Healthcare Company Ppt Themes PDF
This slide shows a cybersecurity dashboard with KPIs such as total cybersecurity cases in company in 2021, total records stoles, malware cases resolved, operational efficiency, mean time to resolve threats etc. Presentingcybersecurity dashboard for abs healthcare company ppt themes pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like phishing attacks 2021, records stolen 2021, malware cases resolved 2021, malware attacks 2021, hacking incidents 2021. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Functioning Centre Facilities Offered By Successful Implementation Infographics PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting security functioning centre facilities offered by successful implementation infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like risk mitigation, investigations, employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
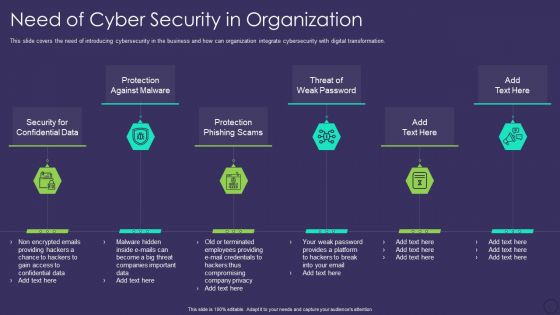
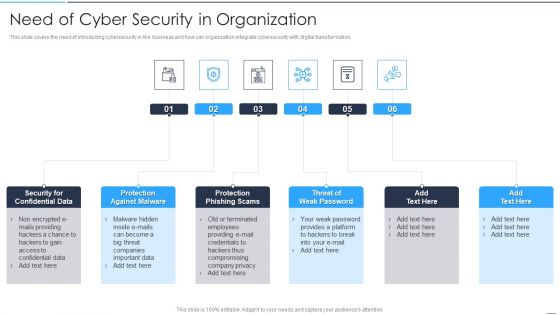
Comprehensive Business Digitization Deck Need Of Cyber Security In Organization Formats PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting comprehensive business digitization deck need of cyber security in organization formats pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

International Organization Standardization 270001 Percent Of Risk Events Occurred Over Last Two Years Demonstration PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors. Deliver an awe inspiring pitch with this creative international organization standardization 270001 percent of risk events occurred over last two years demonstration pdf bundle. Topics like percent of risk events occurred over last two years can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
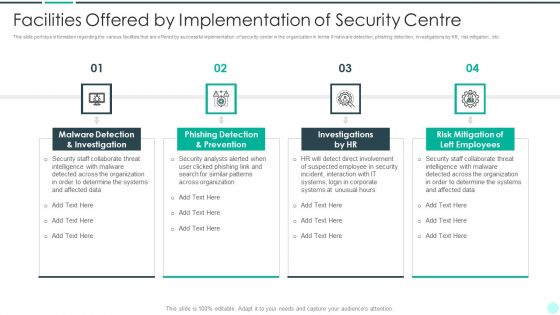
Executing Advance Data Analytics At Workspace Facilities Offered By Implementation Sample PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting executing advance data analytics at workspace facilities offered by implementation sample pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like investigation, prevention, organization, intelligence, collaborate . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
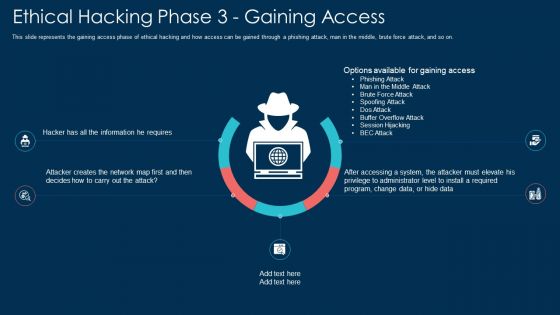
Ethical Hacking Phase 3 Gaining Access Ppt Pictures Vector PDF
This slide represents the gaining access phase of ethical hacking and how access can be gained through a phishing attack, man in the middle, brute force attack, and so on. This is a ethical hacking phase 3 gaining access ppt pictures vector pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, required. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
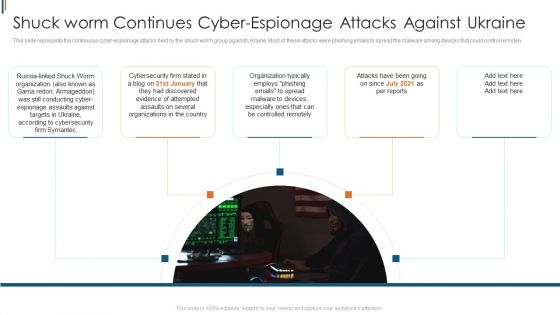
Ukraine Cyberwarfare Shuck Worm Continues Cyber Espionage Attacks Against Ukraine Pictures Pdf
This slide represents the continuous cyber espionage attacks held by the shuck worm group against Ukraine. Most of these attacks were phishing emails to spread the malware among devices that could control remotely. Presenting ukraine cyberwarfare shuck worm continues cyber espionage attacks against ukraine pictures pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization typically, cybersecurity, evidence of attempted assaults. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
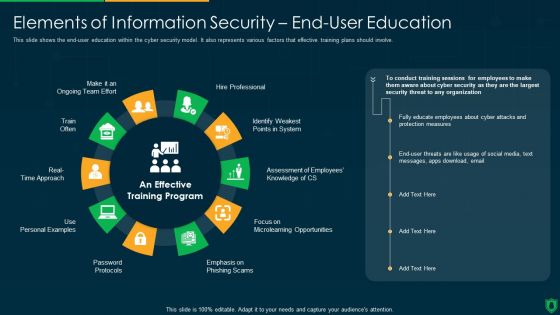
Info Security Elements Of Information Security End User Education Ppt PowerPoint Presentation File Example File PDF
This slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve. Presenting info security elements of information security end user education ppt powerpoint presentation file example file pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like hire professional, emphasis on phishing scam, password protocols, train often. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Wiper Spyware Attack Shuckworm Continues Cyber Espionage Attacks Against Ukraine Diagrams PDF
This slide represents the continuous cyber-espionage attacks held by the Shuckworm group against Ukraine. Most of these attacks were phishing emails to spread the malware among devices that could control remotely.Deliver an awe inspiring pitch with this creative data wiper spyware attack shuckworm continues cyber espionage attacks against ukraine diagrams pdf bundle. Topics like shuckworm continues cyber espionage attacks against ukraine can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
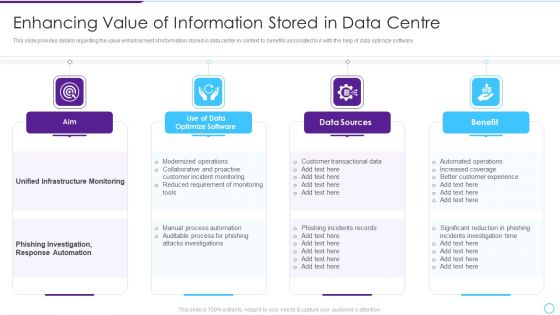
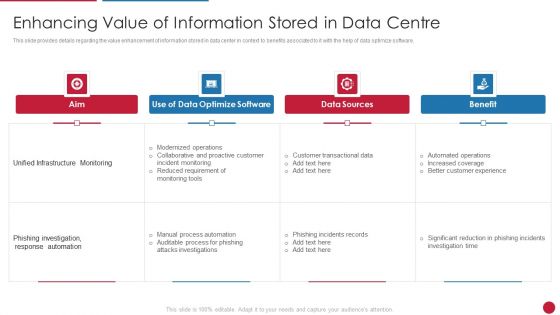
Intelligent Infrastructure Enhancing Value Of Information Stored In Data Centre Download PDF
This slide provides details regarding the value enhancement of information stored in data center in context to benefits associated to it with the help of data optimize software. This is a Intelligent Infrastructure Enhancing Value Of Information Stored In Data Centre Download PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Unified Infrastructure Monitoring, Phishing Investigation, Response Automation, Customer Transactional Data, Data Sources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Facilitating IT Intelligence Architecture Enhancing Value Of Information Stored In Data Centre Themes PDF
This slide provides details regarding the value enhancement of information stored in data center in context to benefits associated to it with the help of data optimize software. This is a Facilitating IT Intelligence Architecture Enhancing Value Of Information Stored In Data Centre Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Unified Infrastructure Monitoring, Phishing Investigation, Response Automation You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Revolution In Online Business Need Of Cyber Security In Organization Professional PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Revolution In Online Business Need Of Cyber Security In Organization Professional PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Confidential Data, Protection Against Malware, Protection Phishing Scams, Threat Weak Password. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
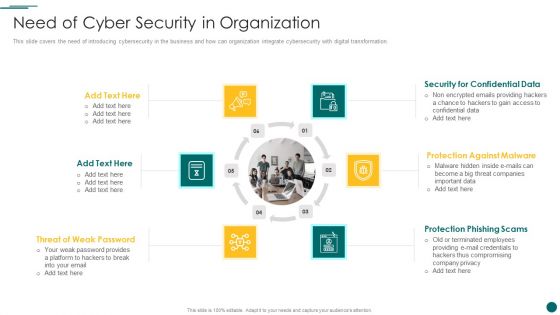
Accelerate Online Journey Now Need Of Cyber Security In Organization Professional PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation.Presenting Accelerate Online Journey Now Need Of Cyber Security In Organization Professional PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Confidential Data, Against Malware, Phishing Scams In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Organization Reinvention Need Of Cyber Security In Organization Graphics PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting Organization Reinvention Need Of Cyber Security In Organization Graphics PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Protection Against Malware, Protection Phishing Scams, Security Confidential Data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Cyber Security Plan Road Map Of A Company Ppt PowerPoint Presentation Icon Show PDF
This slide represents 3 year cyber security plan road map of a company for website enhancement and implementing security to operational work with specific standards. It consists security standards, training and awareness phishing users and sensitive data management. Showcasing this set of slides titled Cyber Security Plan Road Map Of A Company Ppt PowerPoint Presentation Icon Show PDF. The topics addressed in these templates are Website Enhancement, Governance Subcommittee, Security Standards. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
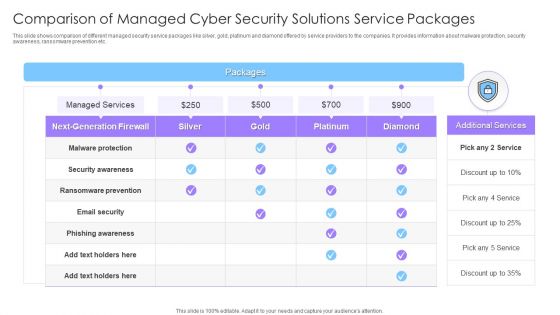
Comparison Of Managed Cyber Security Solutions Service Packages Ppt Ideas Mockup PDF
This slide shows comparison of different managed security service packages like silver, gold, platinum and diamond offered by service providers to the companies. It provides information about malware protection, security awareness, ransomware prevention etc. Pitch your topic with ease and precision using this Comparison Of Managed Cyber Security Solutions Service Packages Ppt Ideas Mockup PDF. This layout presents information on Email Security, Phishing Awareness, Security Awareness. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
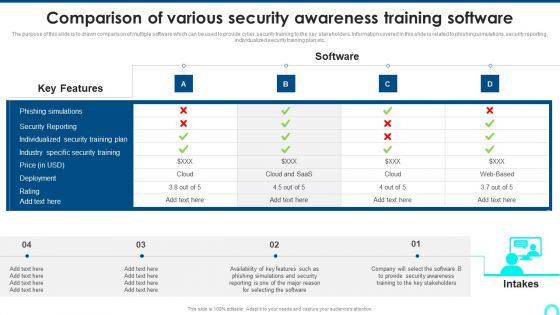
Comparison Of Various Security Awareness Training Software Elements PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Deliver and pitch your topic in the best possible manner with this Comparison Of Various Security Awareness Training Software Elements PDF. Use them to share invaluable insights on Individualized Security, Industry Specific, Deployment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
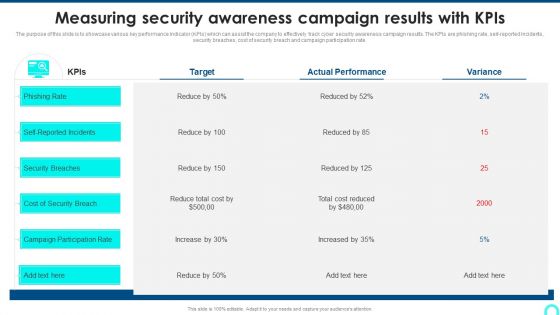
Measuring Security Awareness Campaign Results With Kpis Template PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self reported incidents, security breaches, cost of security breach and campaign participation rateDeliver an awe inspiring pitch with this creative Measuring Security Awareness Campaign Results With Kpis Template PDF bundle. Topics like Security Breaches, Cost Of Security, Campaign Participation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Percent Of Risk Events Occurred Over Last Two Years Inspiration PDF
This slide portrays informational stats about risk events encountered by the firm over last two years. Risk events included in the slide are data breaching, cyber attacks, phishing emails, technical failures and human errors.Deliver and pitch your topic in the best possible manner with this Percent Of Risk Events Occurred Over Last Two Years Inspiration PDF. Use them to share invaluable insights on Data Breaching, Key Takeaways, Faced An Increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Three Layers Of Digital Risk Assessment Management Process Ppt Summary Visual Aids PDF
The following slide highlights the three layers of cyber security management process which are dependent on people, process and technology, it helps company to manage cyber risks such as phishing attacks, data loss and exposed vulnerabilities. Presenting Three Layers Of Digital Risk Assessment Management Process Ppt Summary Visual Aids PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including People, Process, Technology. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Threats Response Playbook Cyber Threat Facts Figures And Statistics Themes PDF
This slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack.This is a IT Threats Response Playbook Cyber Threat Facts Figures And Statistics Themes PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Ransomware Attacks, Cyberthreat Complaints, Trillion Annually. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
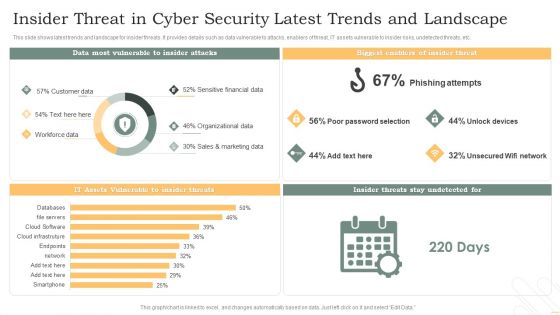
Insider Threat In Cyber Security Latest Trends And Landscape Pictures PDF
This slide shows latest trends and landscape for insider threats. It provides details such as data vulnerable to attacks, enablers of threat, IT assets vulnerable to insider risks, undetected threats, etc. Showcasing this set of slides titled Insider Threat In Cyber Security Latest Trends And Landscape Pictures PDF. The topics addressed in these templates are Phishing Attempts, Unlock Devices, Unsecured Wifi Network. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
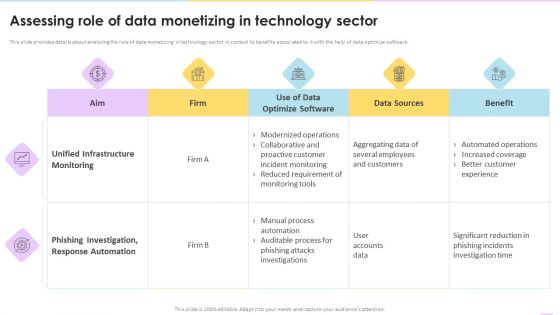
Data Valuation And Monetization Assessing Role Of Data Monetizing In Technology Sector Pictures PDF
This slide provides details about analyzing the role of data monetizing in technology sector in context to benefits associated to it with the help of data optimize software.Deliver and pitch your topic in the best possible manner with this Data Valuation And Monetization Assessing Role Of Data Monetizing In Technology Sector Pictures PDF. Use them to share invaluable insights on Unified Infrastructure, Phishing Investigation, Response Automation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
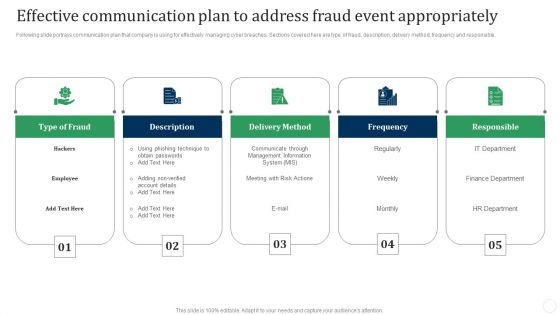
Effective Communication Plan To Address Fraud Event Appropriately Fraud Threat Administration Guide Template PDF
Following slide portrays communication plan that company is using for effectively managing cyber breaches. Sections covered here are type of fraud, description, delivery method, frequency and responsible.This is a Effective Communication Plan To Address Fraud Event Appropriately Fraud Threat Administration Guide Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Phishing Technique, Obtain Passwords, Communicate Through. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Graphics PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti phishing add ons, using a customized web application firewall etc. Deliver and pitch your topic in the best possible manner with this Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Graphics PDF. Use them to share invaluable insights on Goal, Security System, Reduce and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

 Home
Home