Operational Readiness

Latest Market Developments In Consumer Electronics Smartphones Industry Report PPT PowerPoint IR SS V
The slide presents the latest market trends in the global consumer electronics industry. These trends are having a significant impact on the way the industry operates, and they are likely to continue in the years to come. It includes trends such as the rise of smart homes and internet of things, etc. Explore a selection of the finest Latest Market Developments In Consumer Electronics Smartphones Industry Report PPT PowerPoint IR SS V here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Latest Market Developments In Consumer Electronics Smartphones Industry Report PPT PowerPoint IR SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
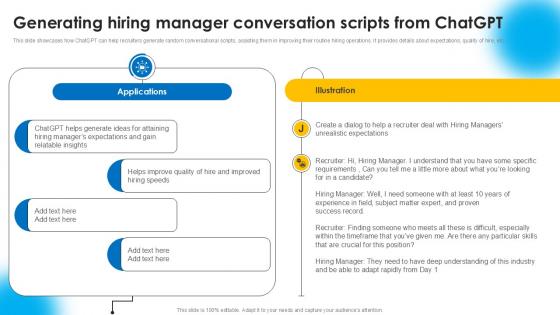
Generating Hiring Manager Conversation AI Powered Recruitment Enhancing Ppt Slide AI SS V
This slide showcases how ChatGPT can help recruiters generate random conversational scripts, assisting them in improving their routine hiring operations. It provides details about expectations, quality of hire, etc.Find highly impressive Generating Hiring Manager Conversation AI Powered Recruitment Enhancing Ppt Slide AI SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Generating Hiring Manager Conversation AI Powered Recruitment Enhancing Ppt Slide AI SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Key Benefits Of Generative Ai For Recruitment AI Powered Recruitment Enhancing Ppt Template AI SS V
This slide showcases major benefits of generative artificial intelligence which can help recruiters ease their routine operations. It provides details about automation, reach and predictive analysis.Explore a selection of the finest Key Benefits Of Generative Ai For Recruitment AI Powered Recruitment Enhancing Ppt Template AI SS V here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Key Benefits Of Generative, Assessing Potential Candidates, Onboarding Experience to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
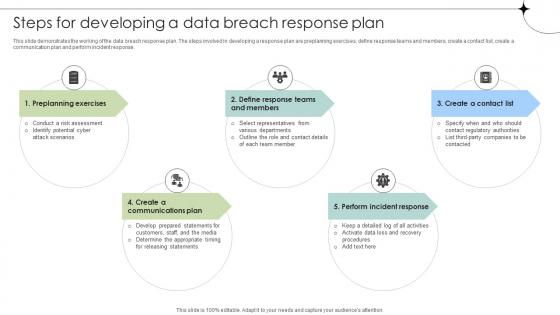
Steps For Developing A Data Breach Response Plan Data Fortification Strengthening Defenses
This slide demonstrates the working of the data breach response plan. The steps involved in developing a response plan are preplanning exercises, define response teams and members, create a contact list, create a communication plan and perform incident response. Want to ace your presentation in front of a live audience Our Steps For Developing A Data Breach Response Plan Data Fortification Strengthening Defenses can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
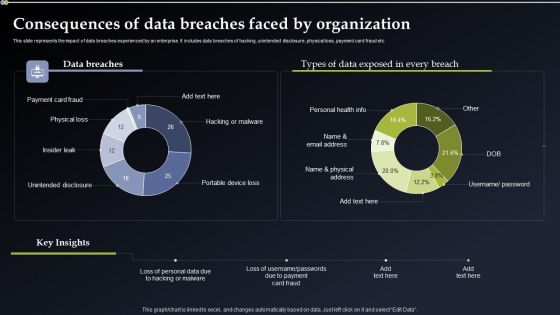
Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
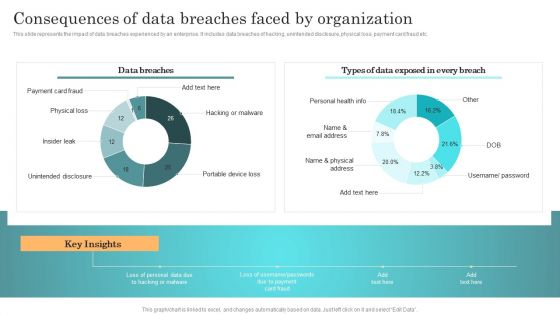
Incident Response Techniques Deployement Consequences Of Data Breaches Faced By Organization Structure PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. There are so many reasons you need a Incident Response Techniques Deployement Consequences Of Data Breaches Faced By Organization Structure PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Incident Response Techniques Deployement Benefits Of Implementing Web Application Firewall Brochure PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Find a pre designed and impeccable Incident Response Techniques Deployement Benefits Of Implementing Web Application Firewall Brochure PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
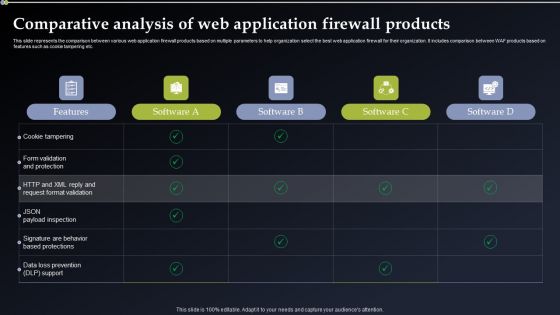
Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. This Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
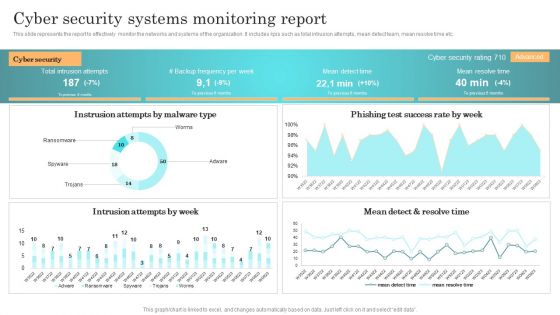
Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes kpis such as total intrusion attempts, mean detect team, mean resolve time etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF today and make your presentation stand out from the rest.
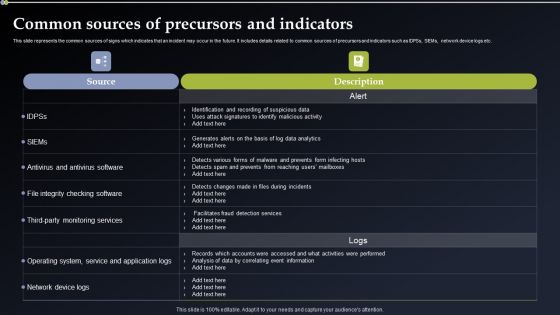
Deploying Cyber Security Incident Response Administration Common Sources Of Precursors Diagrams PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. This modern and well arranged Deploying Cyber Security Incident Response Administration Common Sources Of Precursors Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
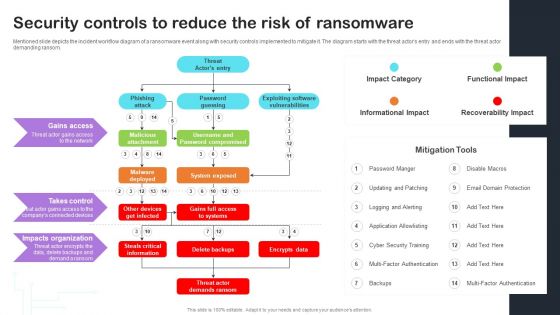
Cyber Risks And Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware Themes PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Take your projects to the next level with our ultimate collection of Cyber Risks And Incident Response Playbook Security Controls To Reduce The Risk Of Ransomware Themes PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.
Transformation Plan Incident Management Chart For Transition Project Ppt Icon Visuals PDF
This slide illustrates the incidents of the transition project. It covers the details such as explanation, status, priority, and resolution of the incident to ensure that technological change is successfully completed in the organization. Deliver an awe inspiring pitch with this creative transformation plan incident management chart for transition project ppt icon visuals pdf bundle. Topics like incident, priority, feature enhancement, cyber attack can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Incident Management Chart Change Execution Plan Ppt PowerPoint Presentation Icon Diagrams PDF
This slide illustrates the incidents of the transition project. It covers the details such as explanation, status, priority, and resolution of the incident to ensure that technological change is successfully completed in the organization. Deliver and pitch your topic in the best possible manner with this Incident Management Chart Change Execution Plan Ppt PowerPoint Presentation Icon Diagrams PDF. Use them to share invaluable insights on Incident Status Priority, Cyber Attack Sensitive, Added Data Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
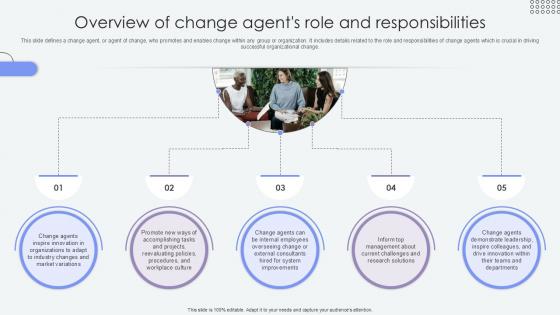
Overview Of Change Agents Role Agents Of Change Pioneers PPT Template CM SS V
This slide defines a change agent, or agent of change, who promotes and enables change within any group or organization. It includes details related to the role and responsibilities of change agents which is crucial in driving successful organizational change. The Overview Of Change Agents Role Agents Of Change Pioneers PPT Template CM SS V is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Active Incident Dashboard Ppt Powerpoint Slide Background Image
This is a active incident dashboard ppt powerpoint slide background image. This is a three stage process. The stages in this process are status, priority, aging, receivers by volume, renee, hssadmin, chris, administrator, admin, category, email, employee setup, equipment, general, literature, no category, breck fix, change management, general, active incident created this week, oldest active priority, active incident created this month, thursday.

Process Flow For Incident Investigation With Trend Data Sample PDF
This slide represents the flowchart for evaluation of incident at workplace for process upgradations and improvements implementations. Persuade your audience using this process flow for incident investigation with trend data sample pdf. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including investigation, recommend improvements, document finding. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Deploying Cyber Security Incident Response Administration Cyber Security Systems Monitoring Report Microsoft PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Slidegeeks is here to make your presentations a breeze with Deploying Cyber Security Incident Response Administration Cyber Security Systems Monitoring Report Microsoft PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
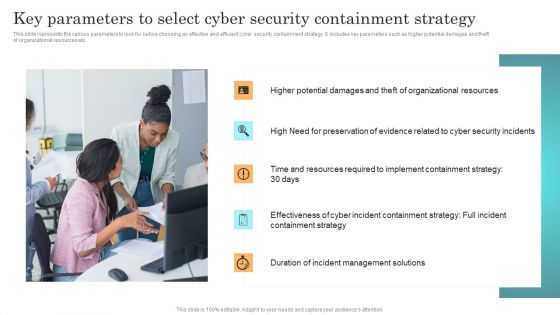
Incident Response Techniques Deployement Key Parameters To Select Cyber Security Containment Strategy Information PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Present like a pro with Incident Response Techniques Deployement Key Parameters To Select Cyber Security Containment Strategy Information PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
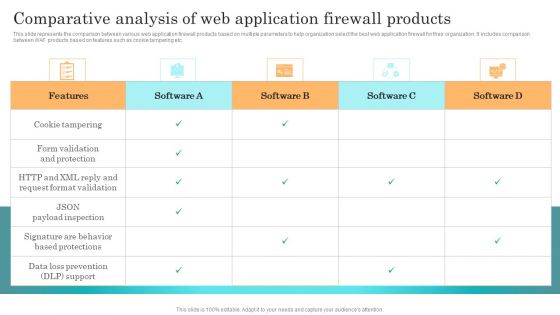
Incident Response Techniques Deployement Comparative Analysis Of Web Application Firewall Products Infographics PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. Want to ace your presentation in front of a live audience Our Incident Response Techniques Deployement Comparative Analysis Of Web Application Firewall Products Infographics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
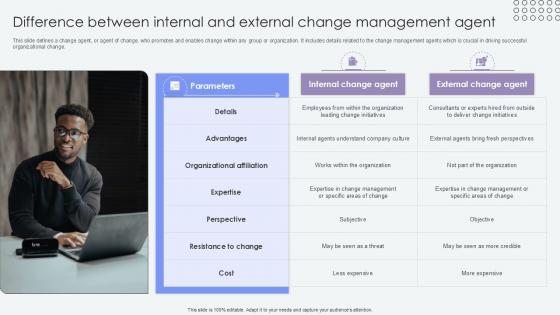
Difference Between Internal And External Agents Of Change Pioneers PPT Template CM SS V
This slide defines a change agent, or agent of change, who promotes and enables change within any group or organization. It includes details related to the change management agents which is crucial in driving successful organizational change. Find highly impressive Difference Between Internal And External Agents Of Change Pioneers PPT Template CM SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Difference Between Internal And External Agents Of Change Pioneers PPT Template CM SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
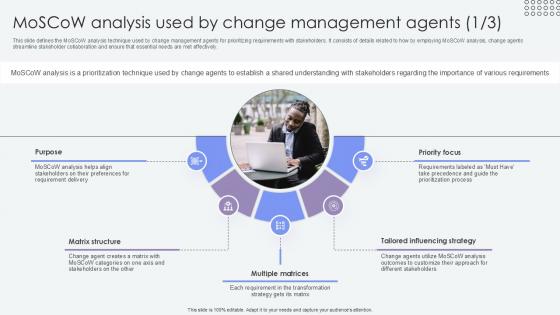
Moscow Analysis Used By Agents Of Change Pioneers PPT Sample CM SS V
This slide defines the MoSCoW analysis technique used by change management agents for prioritizing requirements with stakeholders. It consists of details related to how by employing MoSCoW analysis, change agents streamline stakeholder collaboration and ensure that essential needs are met effectively. Explore a selection of the finest Moscow Analysis Used By Agents Of Change Pioneers PPT Sample CM SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Moscow Analysis Used By Agents Of Change Pioneers PPT Sample CM SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
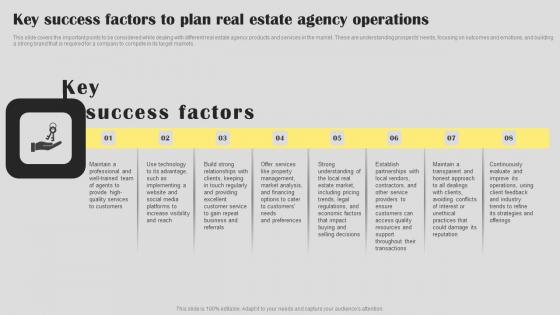
Real Estate Agent Business Plan Go To Market Strategy Key Success Factors To Plan Infographics Pdf
This slide covers the important points to be considered while dealing with different real estate agency products and services in the market. These are understanding prospects needs, focusing on outcomes and emotions, and building a strong brand that is required for a company to compete in its target markets. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Real Estate Agent Business Plan Go To Market Strategy Key Success Factors To Plan Infographics Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Real Estate Agent Business Plan Go To Market Strategy Key Success Factors To Plan Infographics Pdf.

Overview Of Course Selected For Real Estate Agents Out Of The Box Real Download Pdf
The following slide outlines introduction to lead generation course selected by company for realtors. The course covers information about key description, attendees, learning outcome, and instructor details. Find highly impressive Overview Of Course Selected For Real Estate Agents Out Of The Box Real Download Pdf on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Overview Of Course Selected For Real Estate Agents Out Of The Box Real Download Pdf for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Global Cyber Terrorism Incidents On The Rise IT How To Protect Company From Trojan Attacks Summary PDF
This slide explains how to protect the company from trojan attacks which include procedures such as installing advanced antivirus software. This is a global cyber terrorism incidents on the rise it how to protect company from trojan attacks summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like install a good antivirus programm, web application firewall waf, stick to reliable sources, avoid third party downloads. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF
The following slide depicts the number of cyber-attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
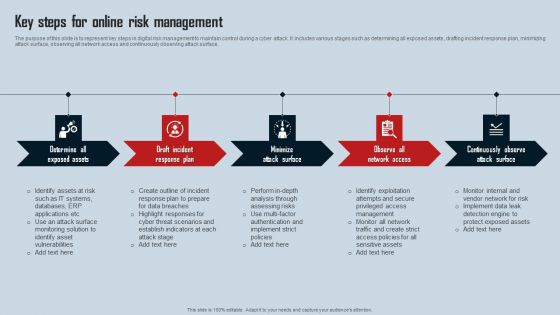
Key Steps For Online Risk Management Ideas PDF
The purpose of this slide is to represent key steps in digital risk management to maintain control during a cyber attack. It includes various stages such as determining all exposed assets, drafting incident response plan, minimizing attack surface, observing all network access and continuously observing attack surface. Presenting Key Steps For Online Risk Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Draft Incident Response Plan, Minimize Attack Surface, Observe All Network Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Brand Positioning And Launch Plan For Emerging Markets Allocating Responsibilities Pictures PDF
This slide showcases roles and responsibilities to be allocated to employees for running brand marketing and advertisement campaigns. Employees involved in brand marketing are - content creator, content manager, marketing executive and brand manager. Find a pre designed and impeccable Brand Positioning And Launch Plan For Emerging Markets Allocating Responsibilities Pictures PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
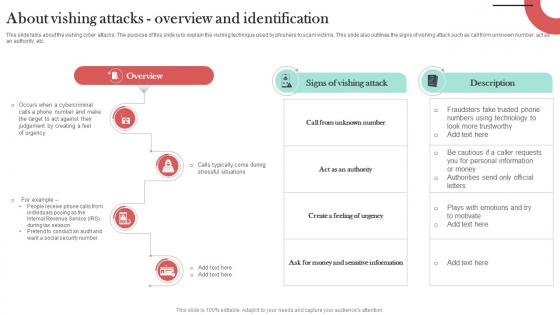
About Vishing Attacks Overview And Identification Man In The Middle Phishing IT
This slide talks about the vishing cyber attacks. The purpose of this slide is to explain the vishing technique used by phishers to scam victims. This slide also outlines the signs of vishing attack such as call from unknown number, act as an authority, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. About Vishing Attacks Overview And Identification Man In The Middle Phishing IT can be your best option for delivering a presentation. Represent everything in detail using About Vishing Attacks Overview And Identification Man In The Middle Phishing IT and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
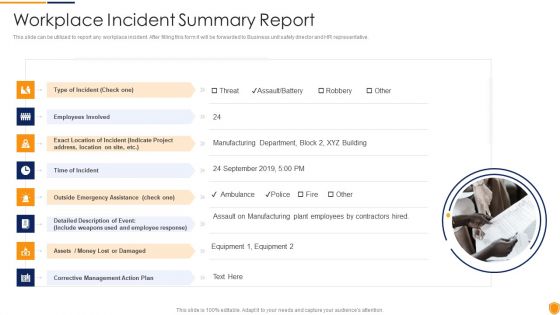
Mitigating Cybersecurity Threats And Vulnerabilities Workplace Incident Summary PDF
This slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. This is a mitigating cybersecurity threats and vulnerabilities workplace incident summary pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like type of incident, time of incident, corrective management action plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Comparative Analysis Of Cyber Security Incident Mitigation Software Diagrams PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Presenting this PowerPoint presentation, titled Comparative Analysis Of Cyber Security Incident Mitigation Software Diagrams PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Comparative Analysis Of Cyber Security Incident Mitigation Software Diagrams PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Comparative Analysis Of Cyber Security Incident Mitigation Software Diagrams PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
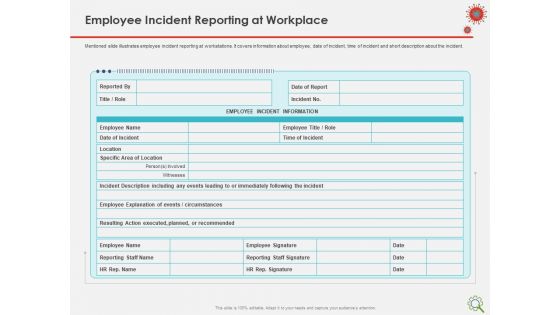
COVID Implications On Manufacturing Business Employee Incident Reporting At Workplace Portrait PDF
Presenting this set of slides with name covid implications on manufacturing business employee incident reporting at workplace portrait pdf. The topics discussed in these slides are employee, reporting, hr, information, time. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Implementing Cyber Security Incident Enterprise Cyber Risk Dashboard Professional PDF today and make your presentation stand out from the rest.
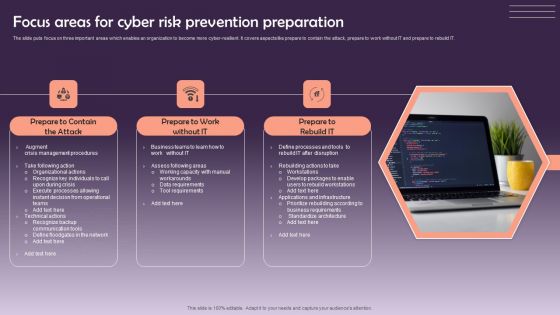
Focus Areas For Cyber Risk Prevention Preparation Pictures PDF
The slide puts focus on three important areas which enables an organization to become more cyber-resilient. It covers aspects like prepare to contain the attack, prepare to work without IT and prepare to rebuild IT. Persuade your audience using this Focus Areas For Cyber Risk Prevention Preparation Pictures PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Prepare To Contain, Prepare To Work, Prepare To Rebuild. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
7 Stages Concentric Proces System Sample Business Plans PowerPoint Templates
We present our 7 stages concentric proces system sample business plans PowerPoint templates.Download and present our Business PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges. Use our Circle Charts PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Download our Layers PowerPoint Templates because you can Add colour to your speech with our PowerPoint Templates and Slides. Your presentation will leave your audience speechless. Download and present our Shapes PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Present our Leadership PowerPoint Templates because Your success is our commitment. Our PowerPoint Templates and Slides will ensure you reach your goal.Use these PowerPoint slides for presentations relating to flow, process, chart, concentric, around, sequence, collective, loop, graphic element, step, community, advertise, retail, business, blank, concept, arrow, vector, rotation, presentation, teamwork, diagram, circle, old, flowchart, abstract, wheel, pie, object, system, relationship, round, retro, brand, direction, production, motion, operation, organization, organize, movement, vintage, background, grunge, financial, repetitive, communication. The prominent colors used in the PowerPoint template are Green, Black, Gray.
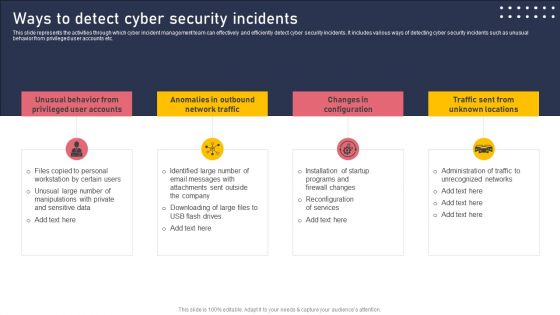
Ways To Detect Cyber Security Incidents Template PDF
This slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Ways To Detect Cyber Security Incidents Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Ways To Detect Cyber Security Incidents Template PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
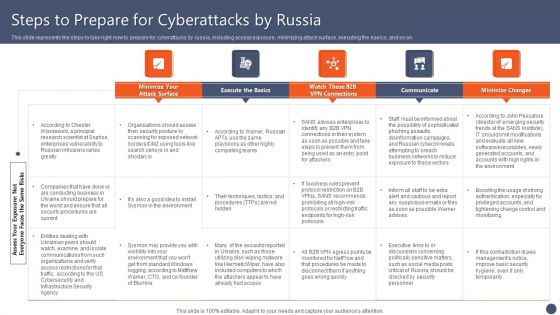
Series Of Cyber Security Attacks Against Ukraine 2022 Steps To Prepare For Cyberattacks By Russia Microsoft PDF
This slide represents the steps to take right now to prepare for cyberattacks by russia, including access exposure, minimizing attack surface, executing the basics, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Series Of Cyber Security Attacks Against Ukraine 2022 Steps To Prepare For Cyberattacks By Russia Microsoft PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

How Does Vishing Attack Works Man In The Middle Phishing IT
This slide illustrates the working procedure of a vishing attack. The purpose of this slide is to explain the working flow of vishing cyber attack. The key components include attacker, target, spoofed caller ID, SMS to victim, file execution confirmation, etc. The How Does Vishing Attack Works Man In The Middle Phishing IT is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Incident Management Process Safety How Many Employees Require Training Brochure PDF
The purpose the following slide is to show to total number of employees I the organization that require safety training, this slide also highlights multiple departments, number of employees they have and what sort of training they require. Deliver and pitch your topic in the best possible manner with this incident management process safety how many employees require training brochure pdf. Use them to share invaluable insights on finance, marketing, construction, engineering, architecture and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Funnel Shaped Process Flow Diagram With 8 Stages Ppt Developing Business Plan PowerPoint Slides
We present our funnel shaped process flow diagram with 8 stages ppt developing business plan PowerPoint Slides.Download and present our Flow Charts PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges. Download our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides are aesthetically designed to attract attention. We gaurantee that they will grab all the eyeballs you need. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides team portray an attitude of elegance. Personify this quality by using them regularly. Download and present our Marketing PowerPoint Templates because You should Kick up a storm with our PowerPoint Templates and Slides. The heads of your listeners will swirl with your ideas. Download and present our Shapes PowerPoint Templates because It can be used to Set your controls for the heart of the sun. Our PowerPoint Templates and Slides will be the propellant to get you there.Use these PowerPoint slides for presentations relating to Action, badge, blank, business, button, collection, concern, connect, continue, correlate, decoration, design, direction, element, empty,financial, flow, graph, green, instruction, involve, label, link, manual, method, navigation, operate, order, phase, plan, procedure, proceed,process, relate, sequence, sequent, series, shape, stage, step, successive, technique. The prominent colors used in the PowerPoint template are Green, Blue, Black.
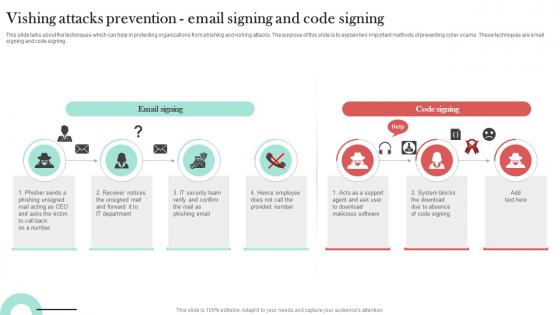
Vishing Attacks Prevention Email Signing Man In The Middle Phishing IT
This slide talks about the techniques which can help in protecting organizations from phishing and vishing attacks. The purpose of this slide is to explain two important methods of preventing cyber scams. These techniques are email signing and code signing. The Vishing Attacks Prevention Email Signing Man In The Middle Phishing IT is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
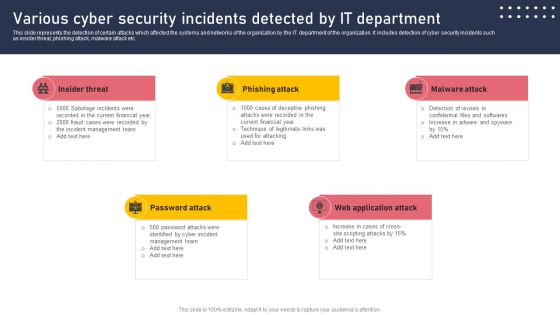
Various Cyber Security Incidents Detected By It Department Sample PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Various Cyber Security Incidents Detected By It Department Sample PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
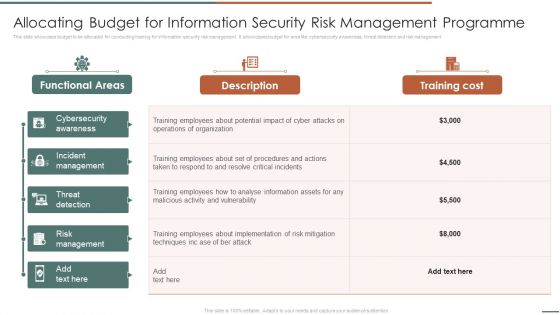
Allocating Budget For Information Security Risk Management Programme Sample PDF
This slide showcase budget to be allocated for conducting training for information security risk management. It showcases budget for area like cybersecurity awareness, threat detection and risk management.Deliver an awe inspiring pitch with this creative Allocating Budget For Information Security Risk Management Programme Sample PDF bundle. Topics like Incident Management, Threat Detection, Risk Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
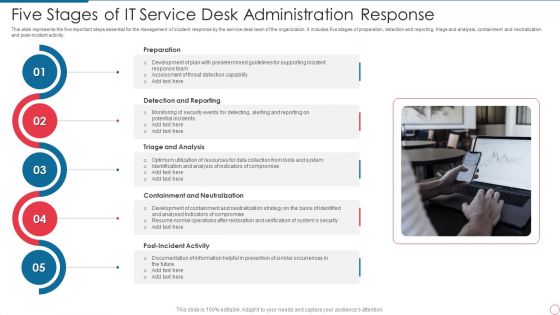
Five Stages Of IT Service Desk Administration Response Inspiration PDF
This slide represents the five important steps essential for the management of incident response by the service desk team of the organization. It includes five stages of preparation, detection and reporting, triage and analysis, containment and neutralization and post incident activity. Persuade your audience using this Five Stages Of IT Service Desk Administration Response Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Analysis, Potential, Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Global Cyber Terrorism Incidents On The Rise IT Employee Access Control Protocols Download PDF
This slide highlights how it is critical to limit employee rights and access in order to keep data safe and prevent it from being deleted or manipulated. Presenting global cyber terrorism incidents on the rise it employee access control protocols download pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like employee access control protocols. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Curriculum Employee Workplace Managing Risks And Establishing Trust Through Efficient Elements Pdf
This slide outlines a training plan on workplace health and safety improvement. It includes training on equipment safety, chemical handling, emergency response and general safety. Retrieve professionally designed Curriculum Employee Workplace Managing Risks And Establishing Trust Through Efficient Elements Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
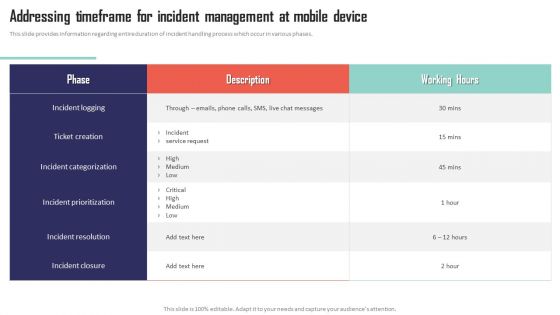
Mobile Device Management Addressing Timeframe For Incident Management At Mobile Slides PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Mobile Device Management Addressing Timeframe For Incident Management At Mobile Slides PDF can be your best option for delivering a presentation. Represent everything in detail using Mobile Device Management Addressing Timeframe For Incident Management At Mobile Slides PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
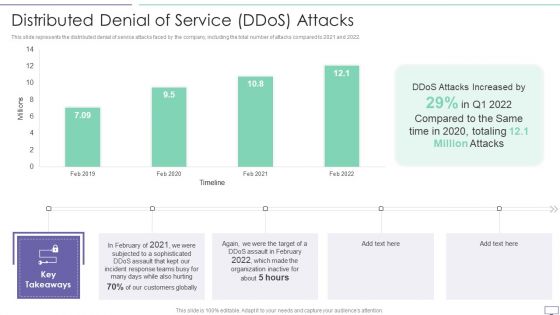
IT Security Hacker Distributed Denial Of Service Ddos Attacks Template PDF
This slide represents the distributed denial of service attacks faced by the company, including the total number of attacks compared to 2021 and 2022.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Distributed Denial Of Service Ddos Attacks Template PDF. Use them to share invaluable insights on Attacks Increased, Incident Response, Customers Globally and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Management Model For Data Security Incident Management Tool We Will Use Diagrams PDF
Mentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Incident Management Tool We Will Use Diagrams PDFbundle. Topics like Cost, Employee, Mobile Support, Automated Workflow, User Access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Plan Slides PDF
This slide provides information about the eighth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring plan slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
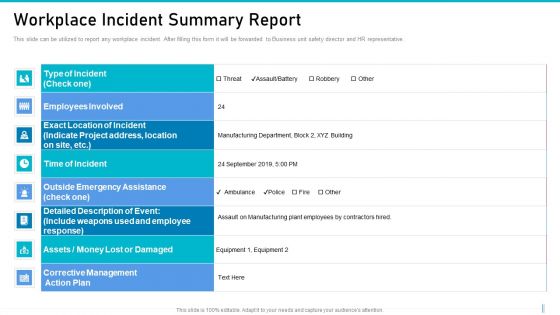
Risk Management For Organization Essential Assets Workplace Incident Summary Report Summary PDF
This slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. Deliver an awe inspiring pitch with this creative risk management for organization essential assets workplace incident summary report summary pdf bundle. Topics like corrective management, manufacturing, employees involved can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Playbook For Managing Information IT Infrastructure Management Dashboard To Track Incidents Icons PDF
This slide provides information regarding IT infrastructure management dashboard to track incidents, address servers performance, track unexpected problems, etc. Deliver and pitch your topic in the best possible manner with this Playbook For Managing Information IT Infrastructure Management Dashboard To Track Incidents Icons PDF. Use them to share invaluable insights on Downtime Issues, IT Support, Employee Per and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Crisis Management Program Presentation Workplace Crisis Incident Summary Report Demonstration PDF
This slide can be utilized to report any workplace violence. After filling this form it will be forwarded to Business unit safety director and HR representative. Deliver and pitch your topic in the best possible manner with this crisis management program presentation workplace crisis incident summary report demonstration pdf. Use them to share invaluable insights on manufacturing department, assistance, corrective management, employees contractors hired, XYZ building and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
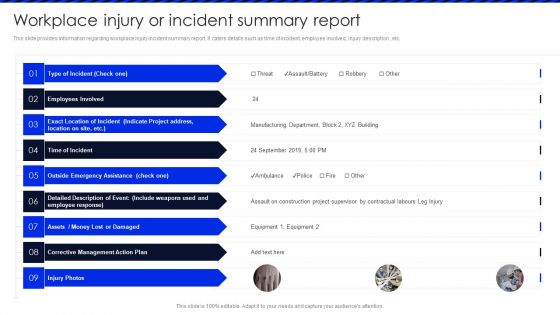
Embracing Construction Project Playbook Workplace Injury Or Incident Summary Report Template PDF
This slide provides information regarding workplace injury incident summary report. It caters details such as time of incident, employee involved, injury description , etc. There are so many reasons you need a Embracing Construction Project Playbook Workplace Injury Or Incident Summary Report Template PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Incident And Issue Management Procedure Escalation Team Management Ppt Portfolio Layout PDF
This slide provides the glimpse about the project based escalation team management which is created based on hierarchical and functional teams. This is a incident and issue management procedure escalation team management ppt portfolio layout pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project, manager, member, functional, committee. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Incident Management Solution Investor Funding Pitch Deck Value Proposition USP Rules PDF
This slide showcases unique selling propositions of solutions offered by a company that provides an incident management platform with intelligent slack integration. It consists of USP such as AI powered incident management, real time incident monitoring and seamless integrations. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Real Time Incident Management Solution Investor Funding Pitch Deck Value Proposition USP Rules PDF can be your best option for delivering a presentation. Represent everything in detail using Real Time Incident Management Solution Investor Funding Pitch Deck Value Proposition USP Rules PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT
This slide talks about the damage caused by phishing attacks. The purpose of this slide is to explain the impact of phishing scams on organizations. The key points included are information loss, damaged credibility, direct financial loss and productivity loss. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Impact Of Phishing Cyber Scams On Man In The Middle Phishing IT.

Rebuilding Travel Industry After COVID 19 Incident Management Summary Report Sample PDF
This slide can be utilized to report any workplace incidents. After filling this form it will be forwarded to Business unit safety director and HR representative. This is a rebuilding travel industry after COVID 19 incident management summary report sample pdf. template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employees involved, time of incident, detailed description of event, corrective management, action plan, action duration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Incident Management Solution Investor Funding Pitch Deck Company Introduction Introduction PDF
This slide represents the overview of company which provides an incident management platform with intelligent slack integration. It showcases industry, business model, customer, headquarters, type, founded year and founders. Create an editable Real Time Incident Management Solution Investor Funding Pitch Deck Company Introduction Introduction PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Real Time Incident Management Solution Investor Funding Pitch Deck Company Introduction Introduction PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
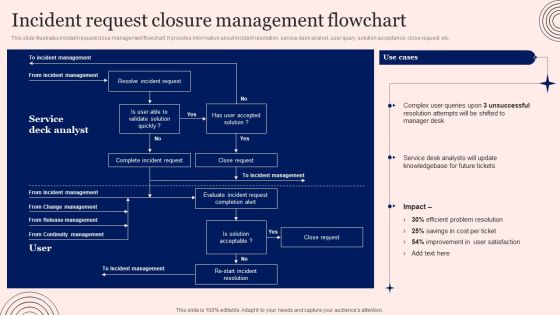
Implementing Advanced Service Help Desk Administration Program Incident Request Closure Management Flowchart Inspiration PDF
This slide illustrates incident request close management flowchart. It provides information about incident resolution, service desk analyst, user query, solution acceptance, close request, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Advanced Service Help Desk Administration Program Incident Request Closure Management Flowchart Inspiration PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Advanced Service Help Desk Administration Program Incident Request Closure Management Flowchart Inspiration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

 Home
Home