Network Access Control

Information Security System Ppt Powerpoint Topics
This is a information security system ppt powerpoint topics. This is a seven stage process. The stages in this process are network security, access control, security management, physical security, business continuity and dr planning, operations security, application system security, information.
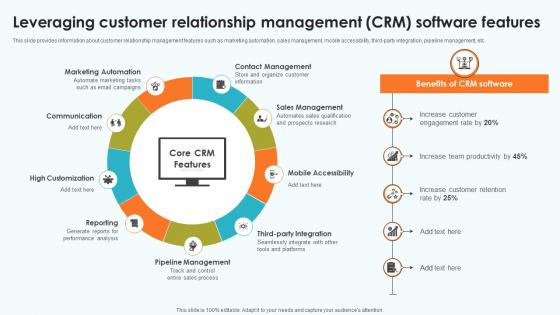
Elevating Sales Networks Leveraging Customer Relationship Management CRM SA SS V
This slide provides information about customer relationship management features such as marketing automation, sales management, mobile accessibility, third-party integration, pipeline management, etc. Slidegeeks has constructed Elevating Sales Networks Leveraging Customer Relationship Management CRM SA SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Smart Wireless Sensor Networks Logical Framework Of Spectrum Management Ideas PDF
This slide talks about the logical framework of spectrum management. The components of the logical framework include spectrum opportunity manager, scheduling, radio frequency environment, spectrum access, negotiation, information sharing, and sensing. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Smart Wireless Sensor Networks Logical Framework Of Spectrum Management Ideas PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Smart Wireless Sensor Networks Logical Framework Of Spectrum Management Ideas PDF
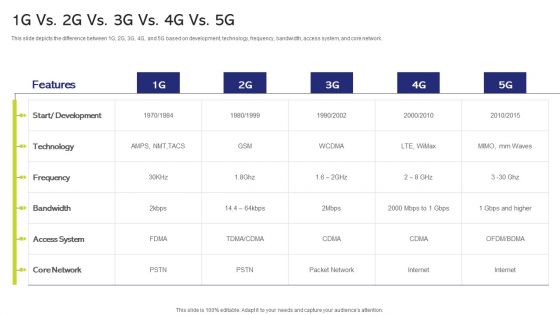
5G And 4G Networks Comparative Analysis 1G Vs 2G Vs 3G Vs 4G Vs 5G Template PDF
This slide depicts the difference between 1G, 2G, 3G, 4G, and 5G based on development, technology, frequency, bandwidth, access system, and core network. Deliver an awe inspiring pitch with this creative 5G And 4G Networks Comparative Analysis 1G Vs 2G Vs 3G Vs 4G Vs 5G Template PDF bundle. Topics like Technology, Frequency, Development can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
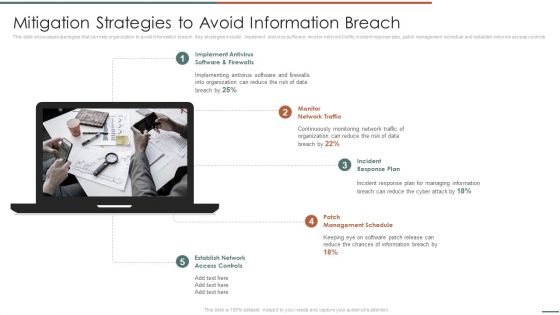
Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls .This is a Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Schedule, Incident Response, Implement Antivirus . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
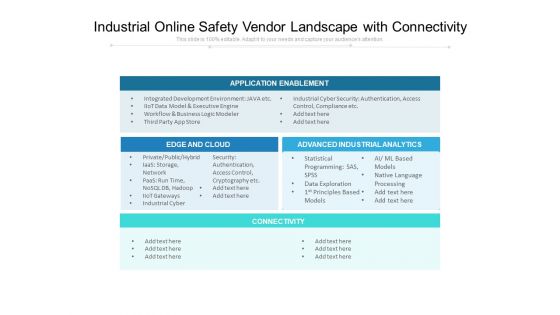
Industrial Online Safety Vendor Landscape With Connectivity Ppt PowerPoint Presentation Infographic Template Graphics Download PDF
Showcasing this set of slides titled industrial online safety vendor landscape with connectivity ppt powerpoint presentation infographic template graphics download pdf. The topics addressed in these templates are network, security,authentication, access control, cryptography, processing, business, analytics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF
This slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Explore a selection of the finest Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls. Presenting this PowerPoint presentation, titled Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Developing IT Security Strategy Mitigation Strategies To Avoid Information Breach Sample PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Developing IT Security Strategy Mitigation Strategies To Avoid Information Breach Sample PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Assessment Professional PDF
This slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Present like a pro with Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Assessment Professional PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
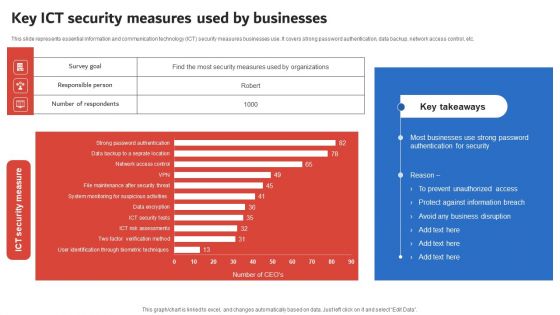
Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF
This slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Create an editable Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Information Security And Policy Example Ppt Design
This is a information security and policy example ppt design. This is a six stage process. The stages in this process are client and operation structure, training and presentation, information flow, aggregation control, department size vs operation size, access control and network infrastructure.

Key Strategies For Data Protection And Privacy Rules PDF
The following slide showcases some techniques to ensure data security and privacy. It includes elements such as authentication, data encryption, network security, access controls etc. Persuade your audience using this Key Strategies For Data Protection And Privacy Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Authentication, Data Encryption, Network Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
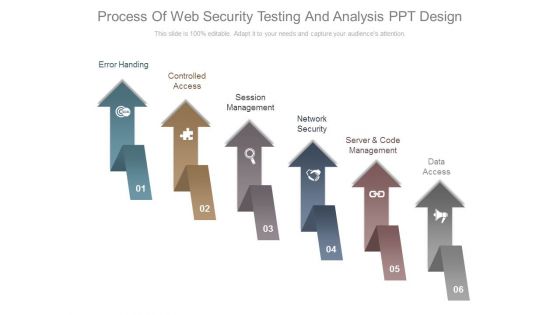
Process Of Web Security Testing And Analysis Ppt Design
This is a process of web security testing and analysis ppt design. This is a six stage process. The stages in this process are error handing, controlled access, session management, network security, server and code management, data access.

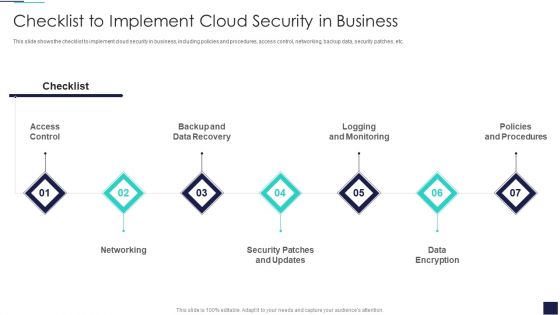
Checklist To Implement Cloud Security In Business Microsoft PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Presenting Checklist To Implement Cloud Security In Business Microsoft PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Access Control, Networking, Security Patches And Updates. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
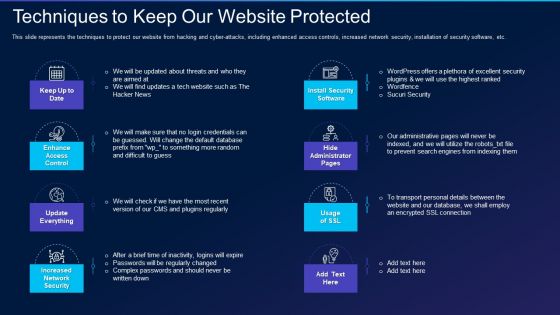
Cyber Exploitation IT Techniques To Keep Our Website Protected Brochure PDF
This slide represents the techniques to protect our website from hacking and cyber-attacks, including enhanced access controls, increased network security, installation of security software, etc. This is a cyber exploitation it techniques to keep our website protected brochure pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like install security software, hide administrator pages, enhance access control, update everything, increased network security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
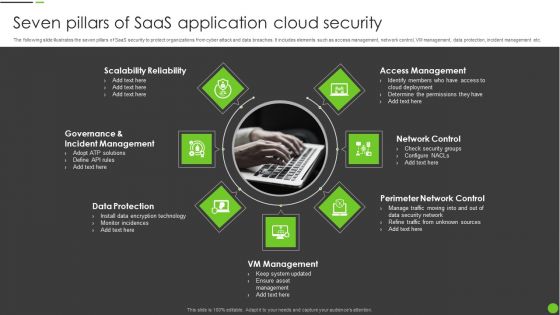
Seven Pillars Of Saas Application Cloud Security Ppt PowerPoint Presentation File Tips PDF
The following slide illustrates the seven pillars of SaaS security to protect organizations from cyber attack and data breaches. It includes elements such as access management, network control, VM management, data protection, incident management etc. Presenting Seven Pillars Of Saas Application Cloud Security Ppt PowerPoint Presentation File Tips PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including VM Management, Data Protection, Network Control, Perimeter Network Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Considerations For Technology Transformation In Local Administration Topics pdf
This slide highlights cybersecurity factors for local governments digital transformation. The purpose of this template is to protect digital assets and data during the conversion processes. It includes elements such as risk assessment, access controls, network security, etc. Showcasing this set of slides titled Cybersecurity Considerations For Technology Transformation In Local Administration Topics pdf. The topics addressed in these templates are Risk Assessment, Cybersecurity Governance, Access Controls. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IoT Security Best Practices In Banking Sector IoT In Banking For Digital Future IoT SS V
Following slide represents best practices to be followed while using IoT in banking services to ensure enhanced security and maintain client confidence. It includes pointers such as access control, network secure infrastructure, regular updates, zero trust approach, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable IoT Security Best Practices In Banking Sector IoT In Banking For Digital Future IoT SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Security Training Program Frameworks Cont Ppt File Slideshow PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas.Deliver and pitch your topic in the best possible manner with this security training program frameworks cont ppt file slideshow pdf. Use them to share invaluable insights on implement strong access control measures, regularly monitor and test networks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF
This slide covers security system evaluation checklist to enhance effectiveness. It involves aspects such as vulnerability analysis, database hardening procedures, configuration management, access controls and network segmentation procedures. Showcasing this set of slides titled Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF. The topics addressed in these templates are Checklist, Vulnerability Scan Analysis, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
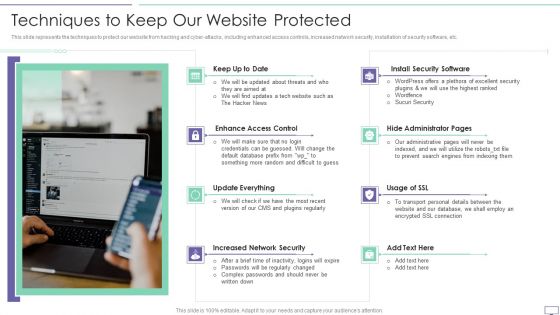
IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF
This slide represents the techniques to protect our website from hacking and cyber attacks, including enhanced access controls, increased network security, installation of security software, etc.This is a IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Software, Enhance Access, Update Everything. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc.This is a Cloud Security Assessment Checklist To Implement Cloud Security In Business Ideas PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Logging And Monitoring You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. This is a Cloud Information Security Checklist To Implement Cloud Security In Business Ppt Ideas Background Image PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Data Encryption, Policies And Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Checklist To Implement Cloud Security In Business Cloud Computing Security IT Ppt Infographic Template Example File
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Deliver an awe inspiring pitch with this creative checklist to implement cloud security in business cloud computing security it ppt infographic template example file bundle. Topics like networking, policies and procedures, logging and monitoring, data encryption, security patches and updates can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Cyber Terrorism Incidents On The Rise IT Techniques To Protect SCADA Elements PDF
This slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls. This is a global cyber terrorism incidents on the rise it techniques to protect scada elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security training of employee, access controls, strict firewalls, network security procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
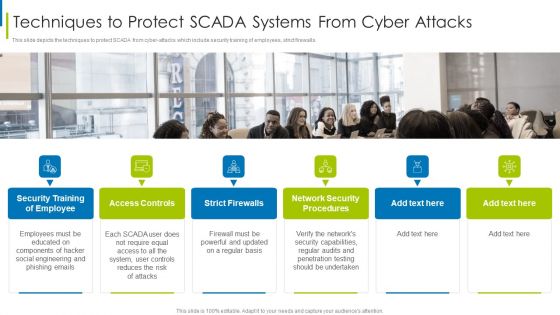
Cyber Terrorism Assault Techniques To Protect SCADA Systems From Cyber Attacks Demonstration PDF
This slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls.Presenting cyber terrorism assault techniques to protect scada systems from cyber attacks demonstration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like access controls, strict firewalls, network security procedures In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IoT Security Best Practices In Banking Future With IoT Ppt Example IoT SS V
Following slide represents best practices to be followed while using IoT in banking services to ensure enhanced security and maintain client confidence. It includes pointers such as access control, network secure infrastructure, regular updates, zero trust approach, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IoT Security Best Practices In Banking Future With IoT Ppt Example IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IoT Security Best Practices In Banking Future With IoT Ppt Example IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Data Breach Prevention Strategies For Enterprises Data Fortification Strengthening Defenses
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Data Breach Prevention Strategies For Enterprises Data Fortification Strengthening Defenses. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
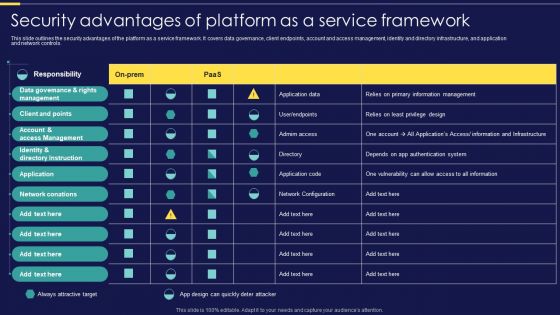
Integration Of Paas Security Advantages Of Platform As A Service Framework Elements PDF
This slide outlines the security advantages of the platform as a service framework. It covers data governance, client endpoints, account and access management, identity and directory infrastructure, and application and network controls. Make sure to capture your audiences attention in your business displays with our gratis customizable Integration Of Paas Security Advantages Of Platform As A Service Framework Elements PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf
The purpose of this slide is to outline the data breach mitigation strategies for businesses. These include access control, encryption, web security solutions, network security, up-to-date software and hardware, preparation, training employees and users, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Data Breach Prevention Strategies For Enterprises Data Breach Prevention Slides Pdf
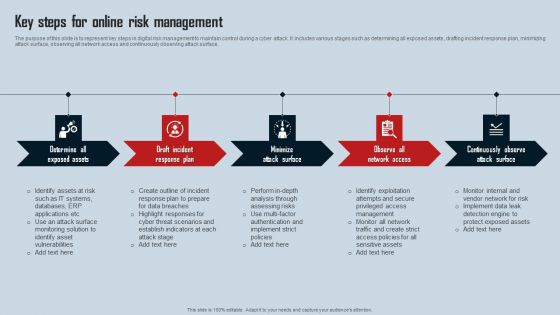
Key Steps For Online Risk Management Ideas PDF
The purpose of this slide is to represent key steps in digital risk management to maintain control during a cyber attack. It includes various stages such as determining all exposed assets, drafting incident response plan, minimizing attack surface, observing all network access and continuously observing attack surface. Presenting Key Steps For Online Risk Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Draft Incident Response Plan, Minimize Attack Surface, Observe All Network Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Distributed Computing IT Cloud Computing Environment Of Business Inspiration PDF
This slide depicts the cloud computing environment of the organization that covers the details of LAN networks, IoT networks, radio access networks, and cloud data centers. Deliver an awe inspiring pitch with this creative distributed computing it cloud computing environment of business inspiration pdf bundle. Topics like communicating, computing environment, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
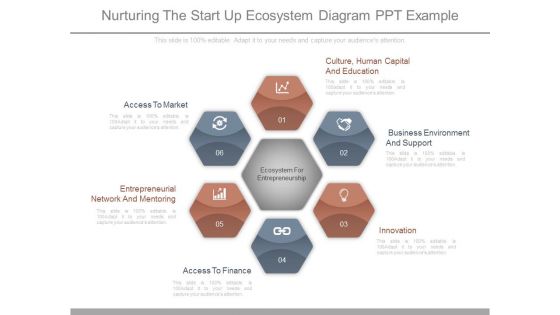
Nurturing The Start Up Ecosystem Diagram Ppt Example
This is a nurturing the start up ecosystem diagram ppt example. This is a six stage process. The stages in this process are access to market, entrepreneurial network and mentoring, access to finance, innovation, business environment and support, culture human capital and education.

Integrating Naas Service Model Comparison Between Service Models Of Naas Ppt Styles Graphic Images PDF
This slide depicts the comparison between different service models of the network as a service, including bandwidth-on-demand, virtual private network, and mobile network virtualization. The virtual private network is of two types remote access and site-to-site connection. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Integrating Naas Service Model Comparison Between Service Models Of Naas Ppt Styles Graphic Images PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Cubeit Venture Capitalist Financing Elevator Pitch Deck Competitive Assessment Of Existing Inspiration PDF
This slide shows the competitive assessment of existing players in market on the basis of local network transfer, multiple device connectivity, file accessibility with other systems, etc.Deliver and pitch your topic in the best possible manner with this Cubeit Venture Capitalist Financing Elevator Pitch Deck Competitive Assessment Of Existing Inspiration PDF Use them to share invaluable insights on Multiple Connectivity, Accessibility Systems, Offline Access and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
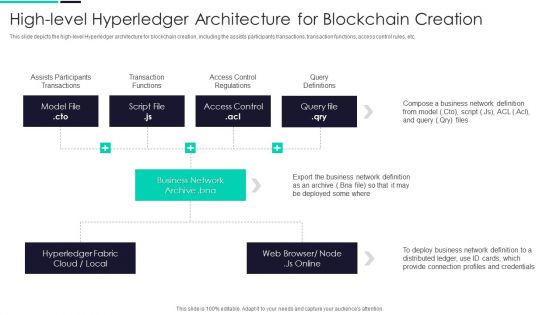
Blockchain And DLT Framework High Level Hyperledger Architecture For Blockchain Creation Graphics PDF
This slide depicts the high-level Hyperledger architecture for blockchain creation, including the assists participants transactions, transaction functions, access control rules, etc. This is a Blockchain And DLT Framework High Level Hyperledger Architecture For Blockchain Creation Graphics PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Assists Participants Transactions, Transaction Functions, Access Control Regulations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security Hacker Costs Of Repairing Damages Icons PDF
This slide depicts the increased additional costs caused by cyber-attacks to the organization, such as DDOS attacks, hacking of the website, email domain, and ransom money.Deliver an awe inspiring pitch with this creative IT Security Hacker Costs Of Repairing Damages Icons PDF bundle. Topics like Network Equipment, Network Accounts, Regain Access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
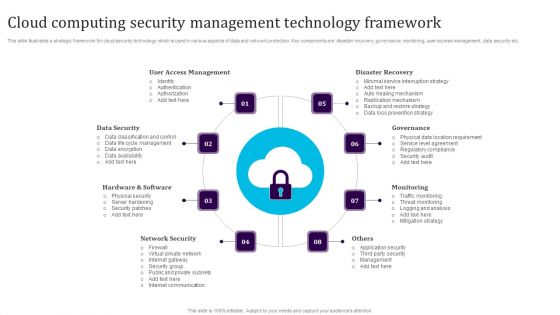
Cloud Computing Security Management Technology Framework Elements PDF
This slide illustrates a strategic framework for cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security etc. Persuade your audience using this Cloud Computing Security Management Technology Framework Elements PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including User Access Management, Data Security, Hardware And Software, Network Security, Monitoring, Governance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
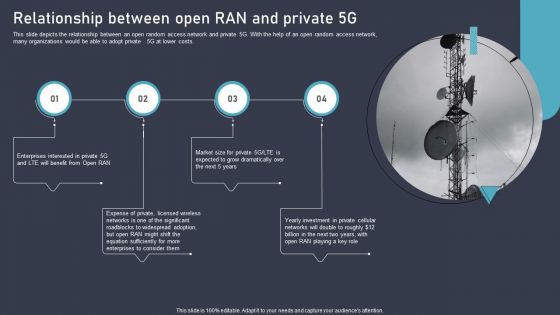
O RAN Architecture Relationship Between Open Ran And Private 5G Ppt Show Ideas PDF
This slide depicts the relationship between an open random access network and private 5G. With the help of an open random access network, many organizations would be able to adopt private 5G at lower costs. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download O RAN Architecture Relationship Between Open Ran And Private 5G Ppt Show Ideas PDF from Slidegeeks and deliver a wonderful presentation.

O RAN Architecture Difference Between 5G Vran And Open Ran Professional PDF
This slide represents the difference between the 5G virtualized random access network and open random access network, including the components of traditional RAN, vRAN,and open RAN. The components include antennas, radio, centralized, and distributed units. Want to ace your presentation in front of a live audience Our O RAN Architecture Difference Between 5G Vran And Open Ran Professional PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Comparative Assessment Of ZTNA Version 10 And 20 Template PDF
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Comparative Assessment Of ZTNA Version 10 And 20 Template PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
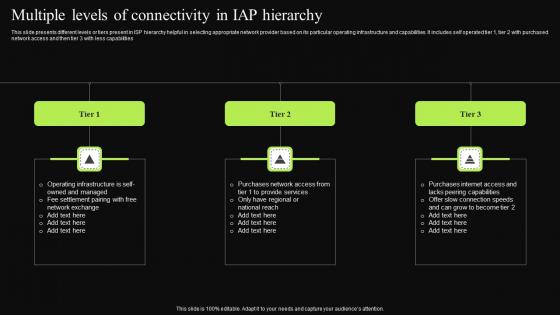
Multiple Levels Of Connectivity In IAP Hierarchy Rules Pdf
This slide presents different levels or tiers present in ISP hierarchy helpful in selecting appropriate network provider based on its particular operating infrastructure and capabilities. It includes self operated tier 1, tier 2 with purchased network access and then tier 3 with less capabilities Pitch your topic with ease and precision using this Multiple Levels Of Connectivity In IAP Hierarchy Rules Pdf. This layout presents information on Operating Infrastructure, Network Exchange, Services. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Deploying Docker Container And Kubernetes Within Organization Best Security Measures In Kubernetes Ppt PowerPoint Presentation PDF
Presenting this set of slides with name deploying docker container and kubernetes within organization best security measures in kubernetes ppt powerpoint presentation pdf. This is a ten stage process. The stages in this process are enables auditing provide limited direct access kubernetes nodes, resources quota, authorized repository, rules resources, implement, network segmentation, log everything production environment, restrict access to etcd. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Ways To Prevent Blockchain Comprehensive Guide To Blockchain Digital Security Icons Pdf
The following slide illustrates some methods to minimize blockchain routing attacks to safeguard network from wrong routing table. It includes elements such as strong passwords, updating firmware, managing access control lists, monitoring logs, etc. Slidegeeks is here to make your presentations a breeze with Ways To Prevent Blockchain Comprehensive Guide To Blockchain Digital Security Icons Pdf With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
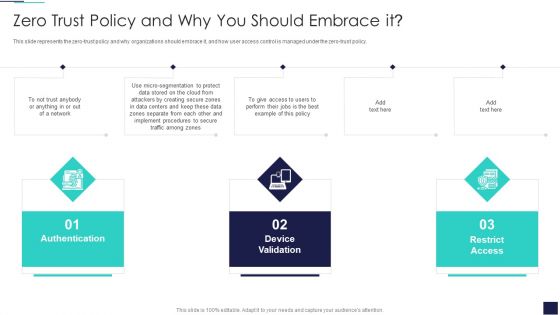
Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF
This slide represents the zero-trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy. This is a Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Authentication Device, Validation Network, Restrict Access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
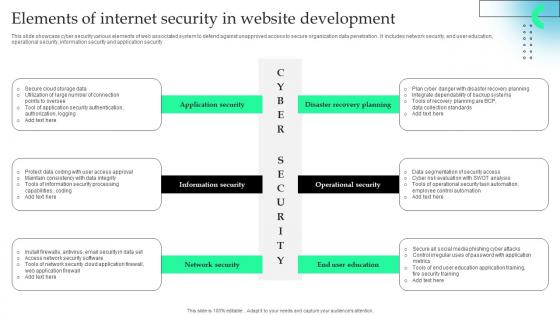
Elements Of Internet Security In Website Development Formats Pdf
This slide showcase cyber security various elements of web associated system to defend against unapproved access to secure organization data penetration . It includes network security, end user education, operational security, information security and application security.Pitch your topic with ease and precision using this Elements Of Internet Security In Website Development Formats Pdf This layout presents information on Information Security, Network Security, Operational Security It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
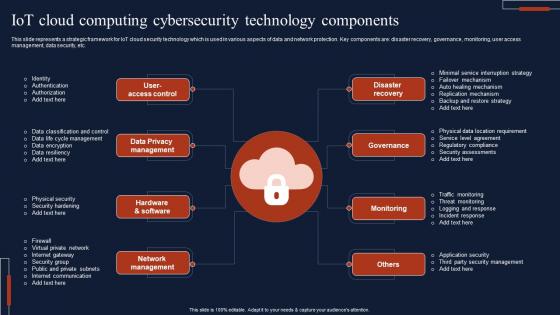
IOT Cloud Computing Cybersecurity Technology Components Template Pdf
This slide represents a strategic framework for IoT cloud security technology which is used in various aspects of data and network protection. Key components are disaster recovery, governance, monitoring, user access management, data security, etc. Pitch your topic with ease and precision using this IOT Cloud Computing Cybersecurity Technology Components Template Pdf This layout presents information on Privacy Management, Hardware And Software, Network Management It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
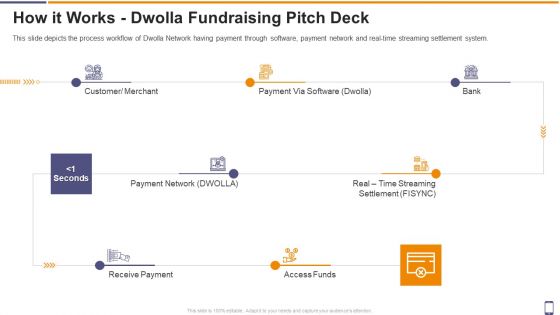
How It Works Dwolla Fundraising Pitch Deck Ppt Pictures Deck PDF
This slide depicts the process workflow of Dwolla Network having payment through software, payment network and real-time streaming settlement system. This is a how it works dwolla fundraising pitch deck ppt pictures deck pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like customer, payment, software, access funds. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

O RAN Architecture Considerations For Open Ran Implementation Brochure PDF
This slide represents the considerations for open RAN implementation, including network security, authentication and verification, integration, compatibility, and testing of commoditized random access network components. Create an editable O RAN Architecture Considerations For Open Ran Implementation Brochure PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. O RAN Architecture Considerations For Open Ran Implementation Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
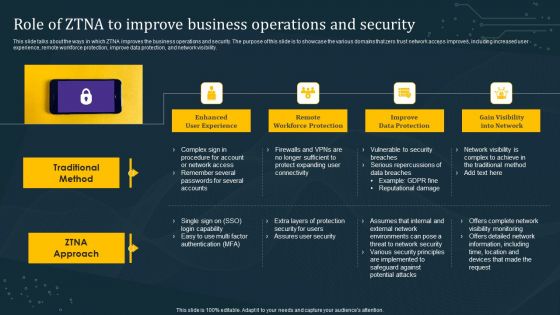
Role Of ZTNA To Improve Business Operations And Security Slides PDF
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. There are so many reasons you need a Role Of ZTNA To Improve Business Operations And Security Slides PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
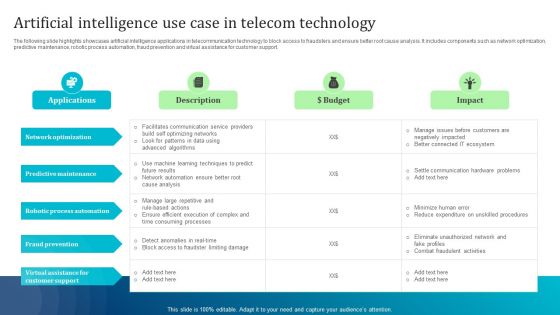
Artificial Intelligence Use Case In Telecom Technology Inspiration PDF
The following slide highlights showcases artificial intelligence applications in telecommunication technology to block access to fraudsters and ensure better root cause analysis. It includes components such as network optimization, predictive maintenance, robotic process automation, fraud prevention and virtual assistance for customer support. Showcasing this set of slides titled Artificial Intelligence Use Case In Telecom Technology Inspiration PDF. The topics addressed in these templates are Robotic Process Automation, Predictive Maintenance, Network Optimization. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

RBAC Framework Showing Multiple Assigned Roles Download PDF
This slide represents the framework of role based access control showing different access permissions for resources according to the roles in organization. It includes details related to user, roles, privileges and resource URI and action. Pitch your topic with ease and precision using this RBAC Framework Showing Multiple Assigned Roles Download PDF. This layout presents information on Catalogue Associate, Financial Manager, Sales Manager. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
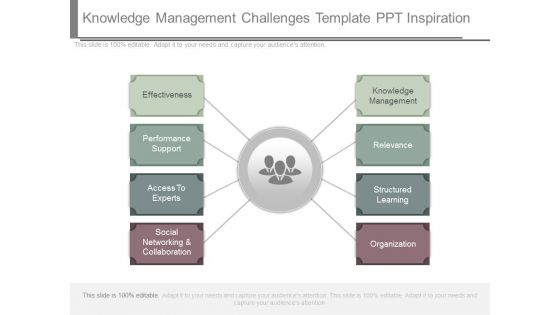
Knowledge Management Challenges Template Ppt Inspiration
This is a knowledge management challenges template ppt inspiration. This is a eight stage process. The stages in this process are effectiveness, performance support, access to experts, social networking and collaboration, knowledge management, relevance, structured learning, organization.

Small Business Management Diagram Presentation Pictures
This is a small business management diagram presentation pictures. This is a seven stage process. The stages in this process are output and exports, taxes govt revenues, poverty alleviation, youth entrepreneurship, networks mentoring and coaching, supportive environment, access to capital.

Learning Solutions Layout Powerpoint Shapes
This is a learning solutions layout powerpoint shapes. This is a six stage process. The stages in this process are structured learning, management, organization, learning solutions layout, social networking and collaboration, performance support, access to experts.
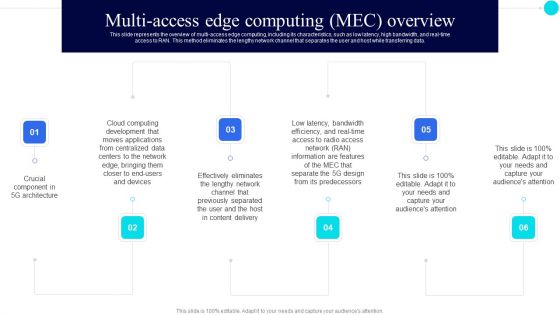
Multiaccess Edge Computing Mec Overview 5G Functional Architecture Themes PDF
This slide represents the overview of multi-access edge computing, including its characteristics, such as low latency, high bandwidth, and real-time access to RAN. This method eliminates the lengthy network channel that separates the user and host while transferring data.This is a Multiaccess Edge Computing Mec Overview 5G Functional Architecture Themes PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Previously Separated, Centralized Data, Low Latency. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
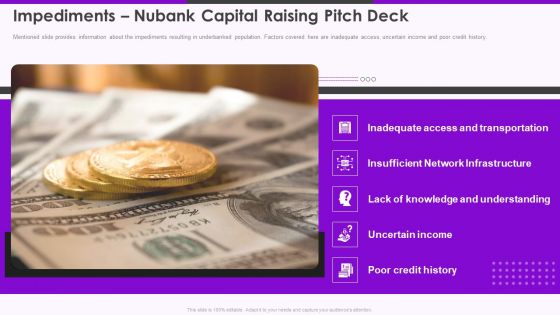
Impediments Nubank Capital Raising Pitch Deck Slide2 Ppt Slides Template PDF
Mentioned slide provides information about the impediments resulting in underbanked population. Factors covered here are inadequate access, uncertain income and poor credit history. This is a impediments nubank capital raising pitch deck slide2 ppt slides template pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like insufficient network infrastructure, inadequate access and transportation, lack of knowledge and understanding, uncertain income, poor credit history. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
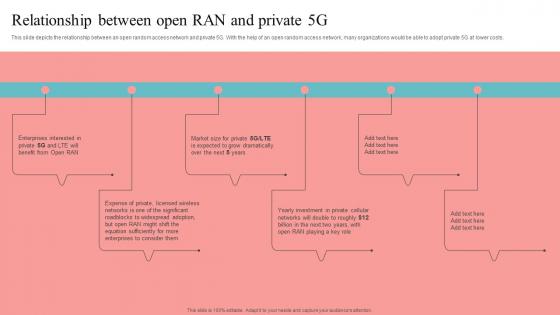
Relationship Between Open RAN And Private Unlocking The Potential Of Open RAN Download Pdf
This slide depicts the relationship between an open random access network and private 5G. With the help of an open random access network, many organizations would be able to adopt private 5G at lower costs. Welcome to our selection of the Relationship Between Open RAN And Private Unlocking The Potential Of Open RAN Download Pdf. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Project Management Modelling Techniques IT Project Management Weekly Check Sheet Inspiration PDF
This slide provides the glimpse about the software project management weekly tally sheet which focuses on issues faced during project management on 4 weeks of the month. Deliver and pitch your topic in the best possible manner with this project management modelling techniques it project management weekly check sheet inspiration pdf. Use them to share invaluable insights on network problem, server problem, server access and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

 Home
Home