Internet Security

Integrating Naas Service Model To Enhance Virtual Private Network VPN Model Background PDF
This slide represents the overview of the virtual private network, including its benefits, such as protecting customer information from hackers, preventing internet service provider companies and websites from selling customer data, and so on. Are you searching for a Integrating Naas Service Model To Enhance Virtual Private Network VPN Model Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Integrating Naas Service Model To Enhance Virtual Private Network VPN Model Background PDF from Slidegeeks today.
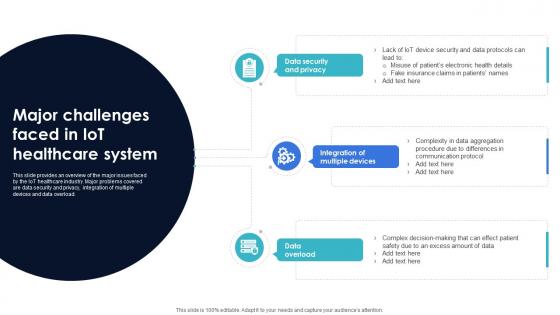
Optimization Of IoT Remote Monitoring Major Challenges Faced In IoT Healthcare System IoT SS V
This slide provides an overview of the major issues faced by the IoT healthcare industry. Major problems covered are data security and privacy, integration of multiple devices and data overload. Find highly impressive Optimization Of IoT Remote Monitoring Major Challenges Faced In IoT Healthcare System IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Optimization Of IoT Remote Monitoring Major Challenges Faced In IoT Healthcare System IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Optimization Of IoT Remote Monitoring Factors To Consider While Selecting IoT Monitoring Devices IoT SS V
This slide provides an overview of the consideration factors for choosing IoT devices. Major factors covered are security and compliance, user-friendly interface, maintenance service, budget and deployment. Are you searching for a Optimization Of IoT Remote Monitoring Factors To Consider While Selecting IoT Monitoring Devices IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Optimization Of IoT Remote Monitoring Factors To Consider While Selecting IoT Monitoring Devices IoT SS V from Slidegeeks today.
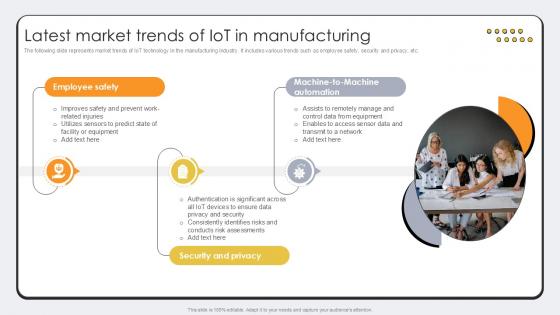
Latest Market Trends Of IoT In Revolutionizing Production IoT Ppt Example
The following slide represents market trends of IoT technology in the manufacturing industry. It includes various trends such as employee safety, security and privacy, etc. Presenting this PowerPoint presentation, titled Latest Market Trends Of IoT In Revolutionizing Production IoT Ppt Example, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Latest Market Trends Of IoT In Revolutionizing Production IoT Ppt Example. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Latest Market Trends Of IoT In Revolutionizing Production IoT Ppt Example that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
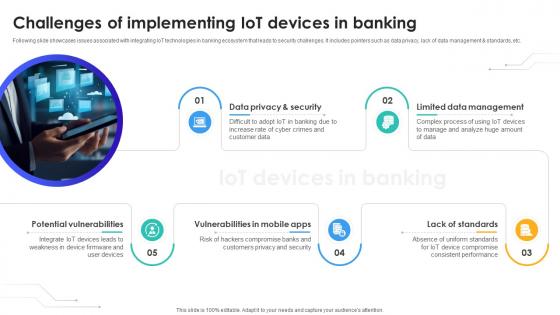
Challenges Of Implementing IoT Devices In Banking IoT In Banking For Digital Future IoT SS V
Following slide showcases issues associated with integrating IoT technologies in banking ecosystem that leads to security challenges. It includes pointers such as data privacy, lack of data management and standards, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Challenges Of Implementing IoT Devices In Banking IoT In Banking For Digital Future IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
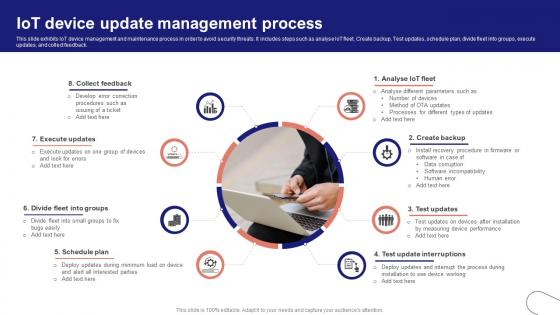
IoT Device Management Fundamentals IoT Device Update Management Process IoT Ss V
This slide exhibits IoT device management and maintenance process in order to avoid security threats. It includes steps such as analyse IoT fleet, Create backup, Test updates, schedule plan, divide fleet into groups, execute updates, and collect feedback. Find highly impressive IoT Device Management Fundamentals IoT Device Update Management Process IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download IoT Device Management Fundamentals IoT Device Update Management Process IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
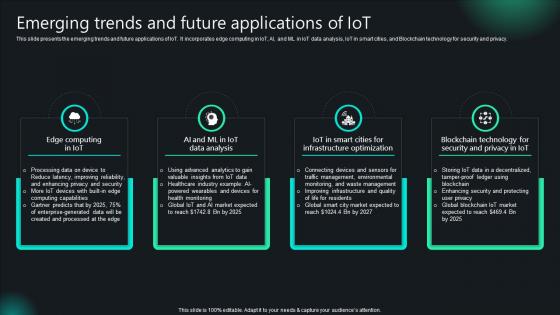
Unlocking Potential IoTs Application Emerging Trends And Future Applications Of IoT SS V
This slide presents the emerging trends and future applications of IoT. It incorporates edge computing in IoT, AI, and ML in IoT data analysis, IoT in smart cities, and Blockchain technology for security and privacy. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Unlocking Potential IoTs Application Emerging Trends And Future Applications Of IoT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Unlocking Potential IoTs Application Emerging Trends And Future Applications Of IoT SS V.
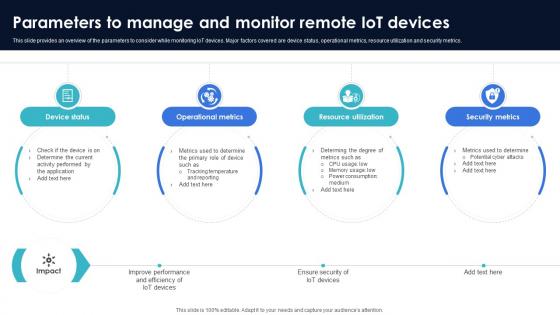
Optimization Of IoT Remote Monitoring Parameters To Manage And Monitor Remote IoT Devices IoT SS V
This slide provides an overview of the parameters to consider while monitoring IoT devices. Major factors covered are device status, operational metrics, resource utilization and security metrics. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Optimization Of IoT Remote Monitoring Parameters To Manage And Monitor Remote IoT Devices IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Optimization Of IoT Remote Monitoring Parameters To Manage And Monitor Remote IoT Devices IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Major Challenges Of IoT Deployment In Education Impact Of IoT Technology On Education IoT SS V
Following slide showcases issues faced by educational institutions during implementation of intent of things IoT technologies. It includes challenges such as high cost infrastructure, security challenges and complexity. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Major Challenges Of IoT Deployment In Education Impact Of IoT Technology On Education IoT SS V to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Major Challenges Of IoT Deployment In Education Impact Of IoT Technology On Education IoT SS V.
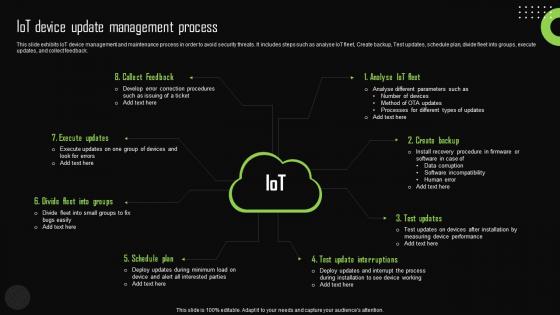
Iot Device Update Management Process Iot Device Management Background Pdf
This slide exhibits IoT device management and maintenance process in order to avoid security threats. It includes steps such as analyse IoT fleet, Create backup, Test updates, schedule plan, divide fleet into groups, execute updates, and collect feedback. This Iot Device Update Management Process Iot Device Management Background Pdf from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Optimization Of IoT Remote Monitoring Blockchain In IoT Remote Monitoring To Share And Access IoT SS V
This slide provides an overview of the blockchain technology used for remote monotiling. It also includes the benefits that are it allows device communication, enhance security and provides authorization access. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Optimization Of IoT Remote Monitoring Blockchain In IoT Remote Monitoring To Share And Access IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Optimization Of IoT Remote Monitoring Blockchain In IoT Remote Monitoring To Share And Access IoT SS V today and make your presentation stand out from the rest
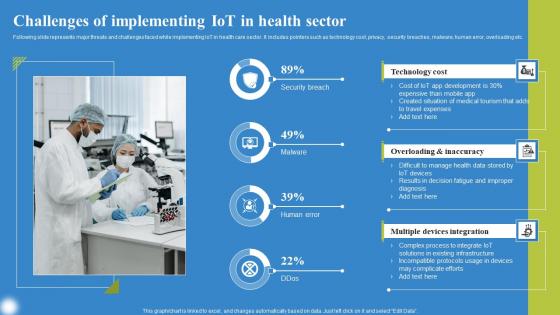
Challenges Of Implementing IoT Deploying IoT Solutions For Enhanced Healthcare Background Pdf
Following slide represents major threats and challenges faced while implementing IoT in health care sector. It includes pointers such as technology cost, privacy, security breaches, malware, human error, overloading etc. Retrieve professionally designed Challenges Of Implementing IoT Deploying IoT Solutions For Enhanced Healthcare Background Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Challenges Of Implementing Banking Future With IoT Ppt Powerpoint IoT SS V
Following slide showcases issues associated with integrating IoT technologies in banking ecosystem that leads to security challenges. It includes pointers such as data privacy, lack of data management and standards, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Challenges Of Implementing Banking Future With IoT Ppt Powerpoint IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Integrating AI With IoT Use Case 1 AIoT Healthcare Applications In Wearable Devices IoT SS V
The purpose of this slide is to showcase various applications of Artificial Intelligence of Things AIoT in wearable devices. Health monitoring, customized recommendations, smart home integration, and safety and security are the use cases that are mentioned in slide along with examples. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Integrating AI With IoT Use Case 1 AIoT Healthcare Applications In Wearable Devices IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Integrating AI With IoT Use Case 1 AIoT Healthcare Applications In Wearable Devices IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Unlocking Potential IoTs Application Use Case Of Various IoT Devices In Smart Home Applications IoT SS V
This slide highlights the various applications of IoT usage in smart homes and the devices used. It includes applications such as temperature control, electricity, bathroom, kitchen, garden, security system, door and window, and home routine. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Unlocking Potential IoTs Application Use Case Of Various IoT Devices In Smart Home Applications IoT SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
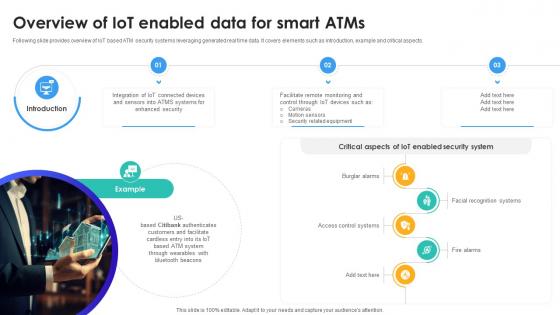
Overview Of IoT Enabled Data For Smart Atms IoT In Banking For Digital Future IoT SS V
Following slide provides overview of IoT based ATM security systems leveraging generated real time data. It covers elements such as introduction, example and critical aspects. Retrieve professionally designed Overview Of IoT Enabled Data For Smart Atms IoT In Banking For Digital Future IoT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Challenges Of Iot Device Deployment In Iot Device Management Guidelines Pdf
This slide highlights the key challenges of IoT devices in the manufacturing industry. These challenges include heavy investment, data security issues, lack of qualified staff, and integration with existing operational technologies. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Challenges Of Iot Device Deployment In Iot Device Management Guidelines Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Challenges Of Iot Device Deployment In Iot Device Management Guidelines Pdf today and make your presentation stand out from the rest
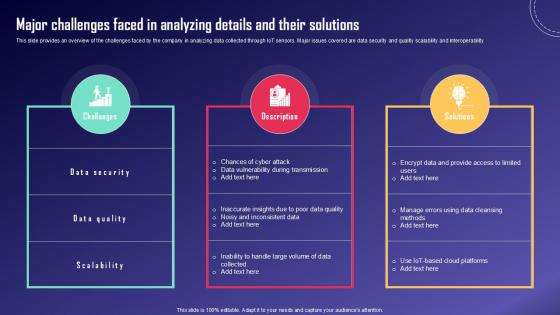
Major Challenges Faced In IoT Fleet Monitoring Ppt Presentation IoT SS V
This slide provides an overview of the challenges faced by the company in analyzing data collected through IoT sensors. Major issues covered are data security and quality scalability and interoperability. Get a simple yet stunning designed Major Challenges Faced In IoT Fleet Monitoring Ppt Presentation IoT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Major Challenges Faced In IoT Fleet Monitoring Ppt Presentation IoT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Integrating AI With IoT Challenges Faced By Companies In Implementing AIoT Solutions IoT SS V
The purpose of this slide is to showcase different issues faced by enterprises in implementing Artificial Intelligence of Things AIoT solutions. It covers information about higher cost, security concern, complexity, and compatibility. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Integrating AI With IoT Challenges Faced By Companies In Implementing AIoT Solutions IoT SS V can be your best option for delivering a presentation. Represent everything in detail using Integrating AI With IoT Challenges Faced By Companies In Implementing AIoT Solutions IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
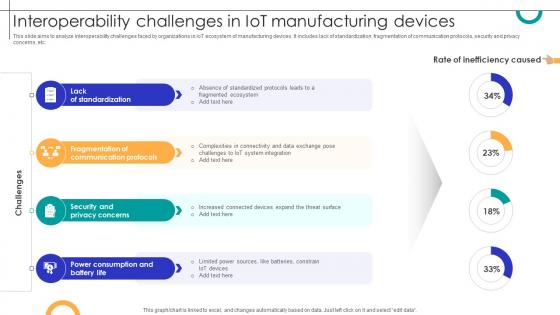
Interoperability Challenges In IOT Manufacturing Devices Streamlining Production Ppt Presentation
This slide aims to analyze interoperability challenges faced by organizations in IoT ecosystem of manufacturing devices. It includes lack of standardization, fragmentation of communication protocols, security and privacy concerns, etc. Do you know about Slidesgeeks Interoperability Challenges In IOT Manufacturing Devices Streamlining Production Ppt Presentation These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Integrating Naas Service Model Types Of Virtual Private Network Vpn Ppt Professional Examples PDF
This slide outlines the two types of the virtual private network, including remote access and site-to-site connection. The remote access connection works as a link between a computer and internet and the site-to-site connection works as a network-to-network. Slidegeeks is here to make your presentations a breeze with Integrating Naas Service Model Types Of Virtual Private Network Vpn Ppt Professional Examples PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
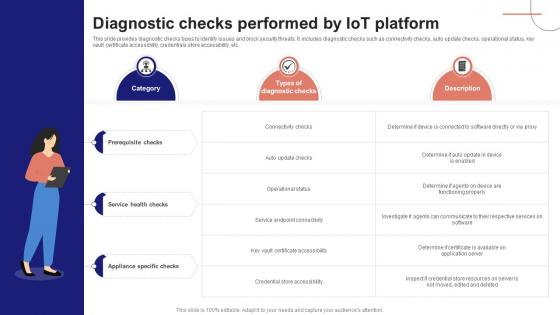
IoT Device Management Fundamentals Diagnostic Checks Performed By IoT Platform IoT Ss V
This slide provides diagnostic checks types to identify issues and block security threats. It includes diagnostic checks such as connectivity checks, auto update checks, operational status, key vault certificate accessibility, credentials store accessibility, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IoT Device Management Fundamentals Diagnostic Checks Performed By IoT Platform IoT SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IoT Device Management Fundamentals Diagnostic Checks Performed By IoT Platform IoT SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
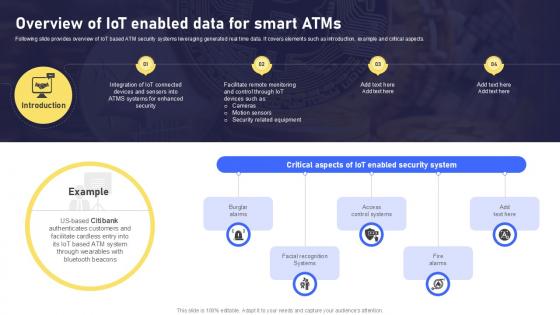
Overview Of IoT Enabled Data Banking Future With IoT Ppt Slide IoT SS V
Following slide provides overview of IoT based ATM security systems leveraging generated real time data. It covers elements such as introduction, example and critical aspects. Are you searching for a Overview Of IoT Enabled Data Banking Future With IoT Ppt Slide IoT SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Overview Of IoT Enabled Data Banking Future With IoT Ppt Slide IoT SS V from Slidegeeks today.

Optimization Of IoT Remote Monitoring Edge Ai Used To Reduce Cost And Bandwidth IoT SS V
This slide provides an overview of the edge AI used to enhance data security and improve monitoring. The slide further covers working and benefits that are it provide greater speed, and provides real-time insights. This modern and well-arranged Optimization Of IoT Remote Monitoring Edge Ai Used To Reduce Cost And Bandwidth IoT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cyber Supply Chain Risk Management Dashboard Structure PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Supply Chain Risk Management Dashboard Structure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Naas Architectural Framework Virtual Private Network VPN Model Overview Portrait PDF
This slide represents the overview of the virtual private network, including its benefits, such as protecting customer information from hackers, preventing internet service provider companies and websites from selling customer data, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Naas Architectural Framework Virtual Private Network VPN Model Overview Portrait PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
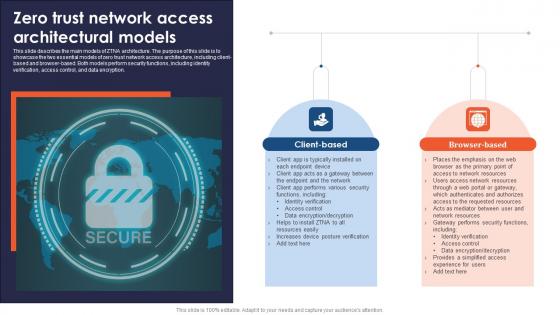
A48 Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Boost your pitch with our creative A48 Zero Trust Network Access Architectural Models. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

In House Training Schedule We Will Implement Ppt Pictures Slide Portrait PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and IoT-Based attack. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download In House Training Schedule We Will Implement Ppt Pictures Slide Portrait PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
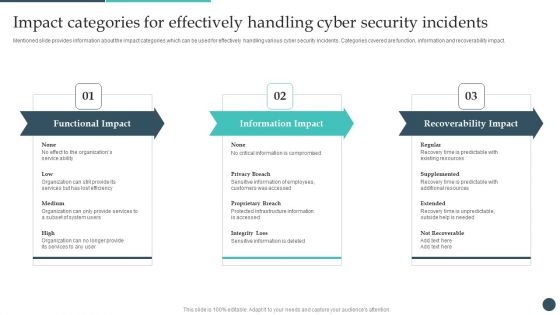
Safety Breach Response Playbook Impact Categories For Effectively Handling Cyber Demonstration PDF
Mentioned slide provides information about the impact categories which can be used for effectively handling various cyber security incidents. Categories covered are function, information and recoverability impact. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Safety Breach Response Playbook Impact Categories For Effectively Handling Cyber Demonstration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Safety Breach Response Playbook Impact Categories For Effectively Handling Cyber Demonstration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Improving Corporate Performance Key Trends That Drive The Industry Graphics PDF
Mentioned slide shows various key trends that are driving many industries. Trends covered in the slide are IoT, smarter business system with AI, cyber security and improved employee engagement through technology. If you are looking for a format to display your unique thoughts, then the professionally designed Improving Corporate Performance Key Trends That Drive The Industry Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Improving Corporate Performance Key Trends That Drive The Industry Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
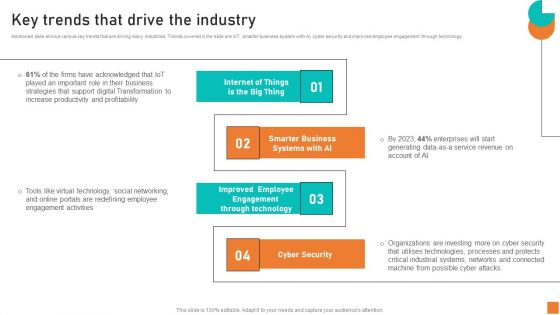
Key Trends That Drive The Industry Ppt Layouts Images PDF
Mentioned slide shows various key trends that are driving many industries. Trends covered in the slide are IoT, smarter business system with AI, cyber security and improved employee engagement through technology. Get a simple yet stunning designed Key Trends That Drive The Industry Ppt Layouts Images PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Key Trends That Drive The Industry Ppt Layouts Images PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
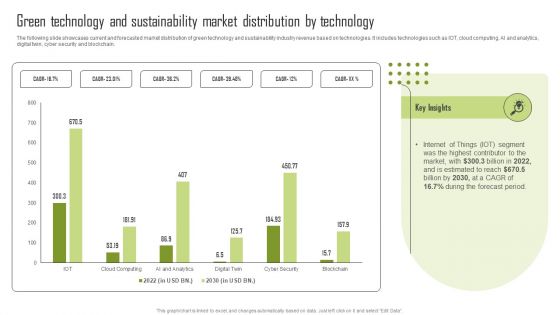
Green Technology And Sustainability Market Distribution By Technology Pictures PDF
The following slide showcases current and forecasted market distribution of green technology and sustainability industry revenue based on technologies. It includes technologies such as IOT, cloud computing, AI and analytics, digital twin, cyber security and blockchain. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Green Technology And Sustainability Market Distribution By Technology Pictures PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Green Technology And Sustainability Market Distribution By Technology Pictures PDF.
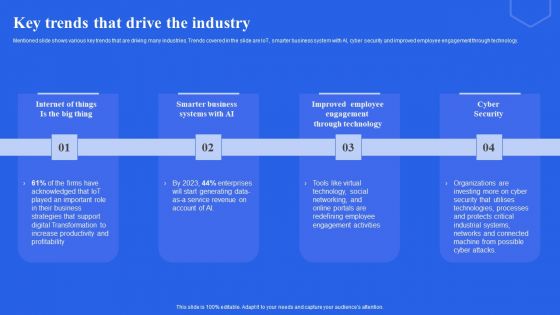
Key Trends That Drive The Industry Ppt Professional Templates PDF
Mentioned slide shows various key trends that are driving many industries. Trends covered in the slide are IoT, smarter business system with AI, cyber security and improved employee engagement through technology. If you are looking for a format to display your unique thoughts, then the professionally designed Key Trends That Drive The Industry Ppt Professional Templates PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key Trends That Drive The Industry Ppt Professional Templates PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Eco Friendly Technology And Sustainability Market Distribution By Technology Pictures PDF
The following slide showcases current and forecasted market distribution of green technology and sustainability industry revenue based on technologies. It includes technologies such as IOT, cloud computing, AI and analytics, digital twin, cyber security and blockchain. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Eco Friendly Technology And Sustainability Market Distribution By Technology Pictures PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Optimizing Business Integration Key Trends That Drive The Industry Information Pdf
Mentioned slide shows various key trends that are driving many industries. Trends covered in the slide are IoT, smarter business system with AI, cyber security and improved employee engagement through technology. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Optimizing Business Integration Key Trends That Drive The Industry Information Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Cyber Attacks Faced By Different Departments Cybersecurity Risk Assessment Themes PDF
This slide showcases information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Are you searching for a Cyber Attacks Faced By Different Departments Cybersecurity Risk Assessment Themes PDF that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cyber Attacks Faced By Different Departments Cybersecurity Risk Assessment Themes PDF from Slidegeeks today.

Sensing Components Of Cyber Physical Systems Ppt PowerPoint Presentation Diagram Images PDF
This slide depicts the sensing components of cyber security systems, including sensors, aggregators, actuators, and their operations and position on the architecture. Find highly impressive Sensing Components Of Cyber Physical Systems Ppt PowerPoint Presentation Diagram Images PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Sensing Components Of Cyber Physical Systems Ppt PowerPoint Presentation Diagram Images PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
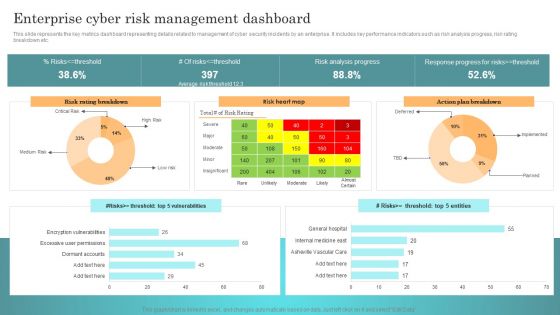
Incident Response Techniques Deployement Enterprise Cyber Risk Management Dashboard Rules PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Find highly impressive Incident Response Techniques Deployement Enterprise Cyber Risk Management Dashboard Rules PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Incident Response Techniques Deployement Enterprise Cyber Risk Management Dashboard Rules PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Analyse And Rank Impact Of Cyber Threat Ppt PowerPoint Presentation Diagram PDF
The following slide highlights the prioritization of cyber security threats to minimize possibility of likelihood and severity. It mainly includes elements such as vulnerability, threat, source, likelihood, impact and ranking etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Analyse And Rank Impact Of Cyber Threat Ppt PowerPoint Presentation Diagram PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Analyse And Rank Impact Of Cyber Threat Ppt PowerPoint Presentation Diagram PDF today and make your presentation stand out from the rest.
Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF
The following slide depicts the number of cyber-attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cyber Attack Incident Tracking Dashboard Ppt PowerPoint Presentation File Styles PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
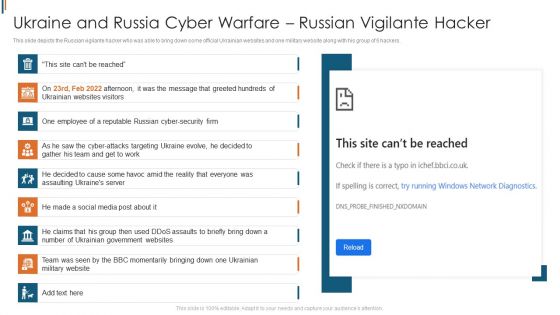
Ukraine Cyberwarfare Ukraine And Russia Cyber Warfare Russian Vigilante Hacker Inspiration Pdf
This slide depicts the Russian vigilante hacker who was able to bring down some official Ukrainian websites and one military website along with his group of 6 hackers. This is a ukraine cyberwarfare ukraine and russia cyber warfare russian vigilante hacker inspiration pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like he made a social media post about it, one employee of a reputable russian cyber security firm, team was seen by the bbc momentarily bringing down one ukrainian military website. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Attacks Faced By Organization In Previous Financial Year Cybersecurity Risk Assessment Background PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Retrieve professionally designed Cyber Attacks Faced By Organization In Previous Financial Year Cybersecurity Risk Assessment Background PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Cyber Risks And Incident Response Playbook Categorization Worksheet For System Components Structure PDF
This slide illustrates categorization worksheet that can be used to categorize system components. It includes information about security system such as system name, its version, system location and other general information. Get a simple yet stunning designed Cyber Risks And Incident Response Playbook Categorization Worksheet For System Components Structure PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Cyber Risks And Incident Response Playbook Categorization Worksheet For System Components Structure PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for. Grab this template today.
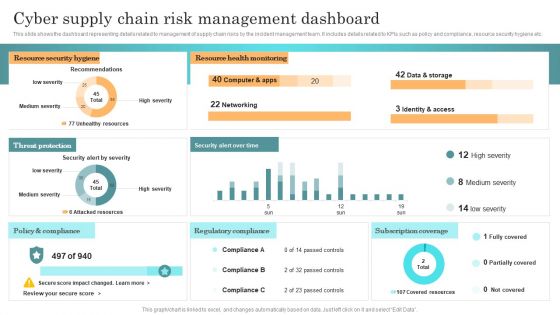
Incident Response Techniques Deployement Cyber Supply Chain Risk Management Dashboard Topics PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Incident Response Techniques Deployement Cyber Supply Chain Risk Management Dashboard Topics PDF can be your best option for delivering a presentation. Represent everything in detail using Incident Response Techniques Deployement Cyber Supply Chain Risk Management Dashboard Topics PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Activity Structure PDF
This slide provides information about the fourth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Monitoring User Activity. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring activity structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail monitoring user activity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
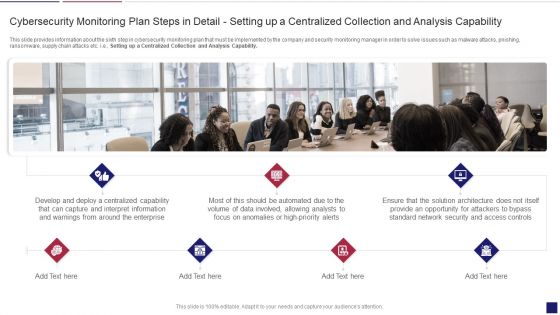
Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Apability Inspiration PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Setting up a Centralized Collection and Analysis Capability. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring apability inspiration pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail setting up a centralized collection and analysis capability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring Plan Slides PDF
This slide provides information about the eighth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring plan slides pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Cybersecurity Monitoring System Formats PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a continuous development evaluation plan eliminate cyber attacks cybersecurity monitoring system formats pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
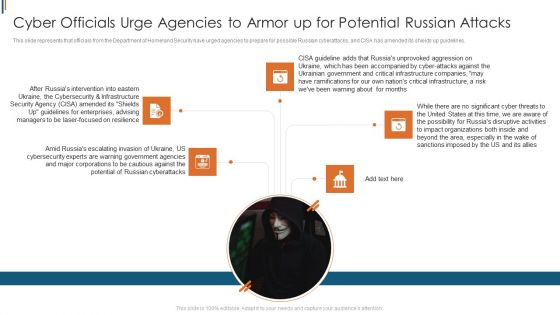
Ukraine Cyberwarfare Cyber Officials Urge Agencies To Armor Up For Potential Russian Attacks Guidelines Pdf
This slide represents that officials from the Department of Homeland Security have urged agencies to prepare for possible Russian cyberattacks, and CISA has amended its shields up guidelines. Presenting ukraine cyberwarfare cyber officials urge agencies to armor up for potential russian attacks guidelines pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like amid russias escalating invasion of ukraine, us cybersecurity experts are warning government agencies, major corporations to be cautious against the potential of russian cyberattacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Roadmap To Implement Zero Trust Network Access Model Software Defined Perimeter SDP
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. This Roadmap To Implement Zero Trust Network Access Model Software Defined Perimeter SDP from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Before Vs After Zero Trust Network Access Brochure Pdf
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Create an editable Before Vs After Zero Trust Network Access Brochure Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Before Vs After Zero Trust Network Access Brochure Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
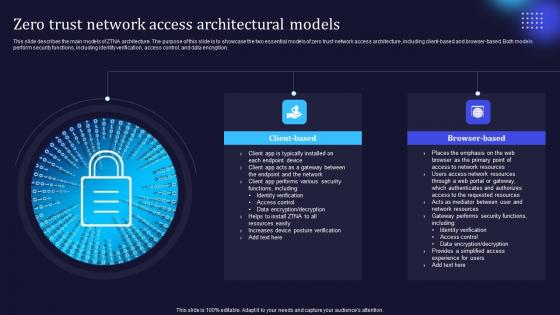
Zero Trust Model Zero Trust Network Access Architectural Models
This slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. This Zero Trust Model Zero Trust Network Access Architectural Models is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Zero Trust Model Zero Trust Network Access Architectural Models features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
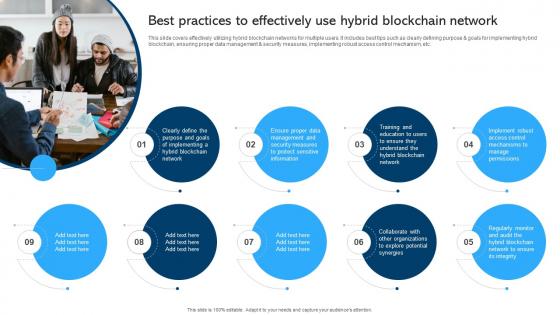
Comprehensive Manual For Blockchain Networks Best Practices To Effectively BCT SS V
This slide covers effectively utilizing hybrid blockchain networks for multiple users. It includes best tips such as clearly defining purpose and goals for implementing hybrid blockchain, ensuring proper data management and security measures, implementing robust access control mechanism, etc. Welcome to our selection of the Comprehensive Manual For Blockchain Networks Best Practices To Effectively BCT SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
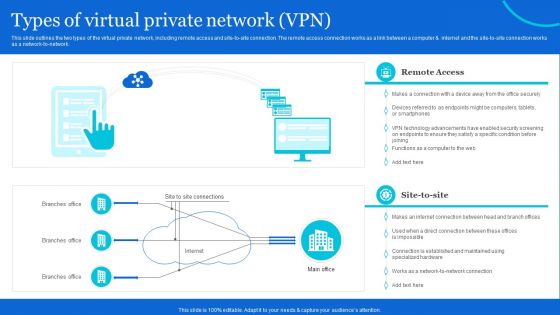
Naas Architectural Framework Types Of Virtual Private Network VPN Mockup PDF
This slide outlines the two types of the virtual private network, including remote access and site-to-site connection. The remote access connection works as a link between a computer and internet and the site-to-site connection works as a network-to-network. Create an editable Naas Architectural Framework Types Of Virtual Private Network VPN Mockup PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Naas Architectural Framework Types Of Virtual Private Network VPN Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Integrating Naas Service Model To Enhance Types Of Virtual Private Network VPN Introduction PDF
This slide outlines the two types of the virtual private network, including remote access and site-to-site connection. The remote access connection works as a link between a computer and internet and the site-to-site connection works as a network-to-network. The Integrating Naas Service Model To Enhance Types Of Virtual Private Network VPN Introduction PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

WAF Introduction Best Practices For Successful Web Application Firewall Implementation Brochure PDF
This slide represents the steps to be considered by organizations to maximize the benefits of WAF. The purpose of this slide is to showcase the best practices businesses can consider for successful web application firewall implementation, such as support for app security goals, evaluation and testing, and resource listing. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward WAF Introduction Best Practices For Successful Web Application Firewall Implementation Brochure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal WAF Introduction Best Practices For Successful Web Application Firewall Implementation Brochure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
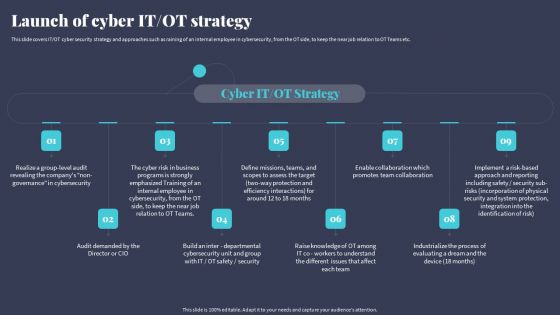
Tactics For Incorporating OT And IT With The Latest PI System Launch Of Cyber IT OT Strategy Brochure PDF
This slide covers IT OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT Teams etc. Explore a selection of the finest Tactics For Incorporating OT And IT With The Latest PI System Launch Of Cyber IT OT Strategy Brochure PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Tactics For Incorporating OT And IT With The Latest PI System Launch Of Cyber IT OT Strategy Brochure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
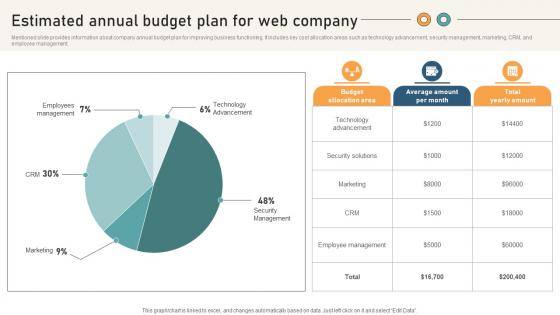
Comprehensive Guide For Website Estimated Annual Budget Plan For Web Company
Mentioned slide provides information about company annual budget plan for improving business functioning. It includes key cost allocation areas such as technology advancement, security management, marketing, CRM, and employee management. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Comprehensive Guide For Website Estimated Annual Budget Plan For Web Company to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Comprehensive Guide For Website Estimated Annual Budget Plan For Web Company.
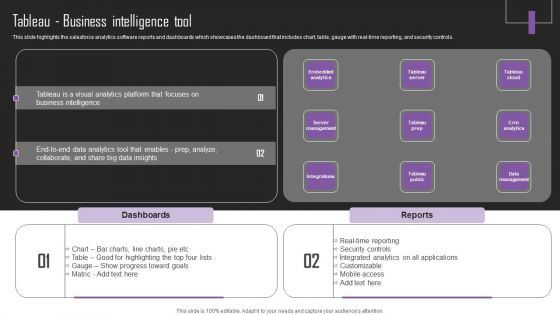
Web Hosting Software Company Outline Tableau Business Intelligence Tool Sample PDF
This slide highlights the salesforce analytics software reports and dashboards which showcases the dashboard that includes chart, table, gauge with real-time reporting, and security controls. This Web Hosting Software Company Outline Tableau Business Intelligence Tool Sample PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Zero Trust Network Access Steps To Implement Zero Trust Network Access Model
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Zero Trust Network Access Steps To Implement Zero Trust Network Access Model template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Zero Trust Network Access Steps To Implement Zero Trust Network Access Model that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

 Home
Home