Internet Security

Global Cyber Terrorism Incidents On The Rise IT Impact Of Implementing Cyber Background PDF
This slide represents the current state of cyber assaults in a business after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this global cyber terrorism incidents on the rise it impact of implementing cyber background pdf. Use them to share invaluable insights on impact of implementing cyber security measures in the company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Cyber Protection And Precaution Tracking Dashboard Designs PDF
This slide shows the dashboard of cyber safety and security of an organization. It includes risk level, compliance status, tracking and security budget. Showcasing this set of slides titled Cyber Protection And Precaution Tracking Dashboard Designs PDF. The topics addressed in these templates are Risk, Compliance Status, Risk Level. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
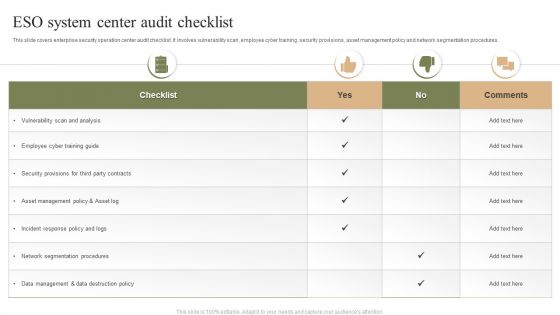
ESO System Center Audit Checklist Ppt PowerPoint Presentation Gallery Clipart Images PDF
This slide covers enterprise security operation center audit checklist. It involves vulnerability scan, employee cyber training, security provisions, asset management policy and network segmentation procedures. Showcasing this set of slides titled ESO System Center Audit Checklist Ppt PowerPoint Presentation Gallery Clipart Images PDF. The topics addressed in these templates are Checklist, Employee Cyber, Training Guide. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Terrorism Assault Managing Cyber Terrorism 30 Days Plan Infographics PDF
This slide demonstrates how the cyber security model would operate in the first 30 days and the duties that the company should concentrate on.Deliver an awe inspiring pitch with this creative cyber terrorism assault managing cyber terrorism 30 days plan infographics pdf bundle. Topics like facility physical security, phishing repeat offenders, phishing reporting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Page Experience Signals In Google Search Console Training Ppt
This slide covers search signals for page experience largely known as core web vitals. It also includes KPIs such as mobile-friendly experience, safe browsing experience, HTTPS security and no intrusive interstitials.

Agenda Of Enhancing Cyber Safety With Vulnerability Administratio Professional PDF
This is a agenda of enhancing cyber safety with vulnerability administratio professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security intelligence, log management and compliance, provides security services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Safety Awareness Program Plan Ppt Icon Smartart PDF
This slide covers plan related to cyber security awareness. It includes timeline pertaining to preparation, detection, analysis, eradication, recover and post incident of a security lapse. Presenting Cyber Safety Awareness Program Plan Ppt Icon Smartart PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Post Inside, Eradicate and Recover, Detection, Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Monitor And Assess Vendor Risk Management Ppt PowerPoint Presentation File Infographics PDF
The following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. The following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Boost your pitch with our creative Monitor And Assess Vendor Risk Management Ppt PowerPoint Presentation File Infographics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Stock Photo Ball With Big Data Text For Data Protection Concept PowerPoint Slide
Graphic of ball with big data text has been used to craft this power point template. This image template contains the concept of data protection. Use this image for data security related topics in any presentation.
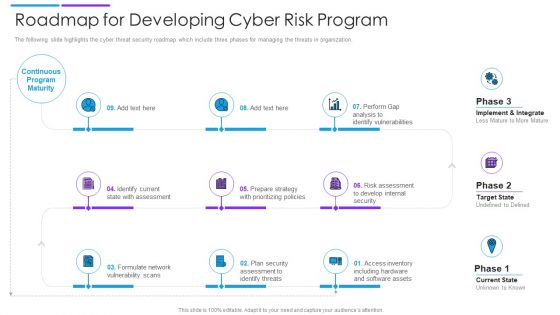
Roadmap For Developing Cyber Risk Program Download PDF
The following slide highlights the cyber threat security roadmap which include three phases for managing the threats in organization. Persuade your audience using this roadmap for developing cyber risk program download pdf. This PPT design covers nine stages, thus making it a great tool to use. It also caters to a variety of topics including internal security, software assets, identify threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Connecting Link Process For Start Up Ppt PowerPoint Presentation Summary
This is a connecting link process for start up ppt powerpoint presentation summary. This is a five stage process. The stages in this process are computer configuration, windows settings, security settings, local policies, audit policy.

Cyber Exploitation IT Budget For New Recruited Professionals Demonstration PDF
This slide represents the budget for newly recruited professionals, including new professionals, number of total posts, annual salaries, and total funding for salaries. Deliver and pitch your topic in the best possible manner with this cyber exploitation it budget for new recruited professionals demonstration pdf. Use them to share invaluable insights on it security analyst, certified ethical hacker, security consultant and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
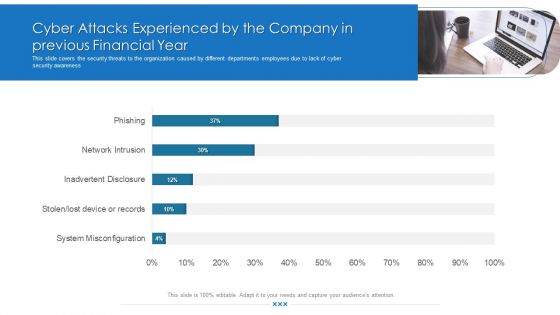
Cyber Attacks Experienced By The Company In Previous Financial Year Download PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this cyber attacks experienced by the company in previous financial year download pdf. Use them to share invaluable insights on cyber attacks experienced by the company in previous financial year and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Stacks Experienced By The Company In Previous Financial Year Ppt Summary PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative cyber stacks experienced by the company in previous financial year ppt summary pdf bundle. Topics like cyber stacks experienced by the company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
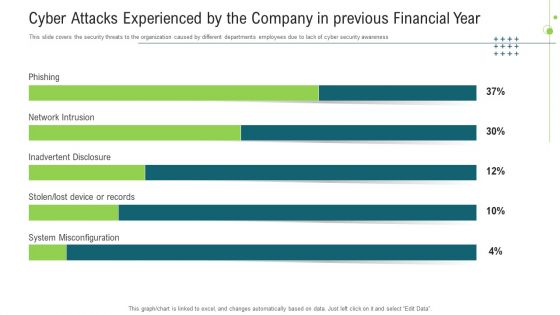
Cyber Attacks Experienced By The Company In Previous Financial Year Ppt Infographics PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative cyber attacks experienced by the company in previous financial year ppt infographics pdf bundle. Topics like cyber attacks experienced by the company in previous financial year can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
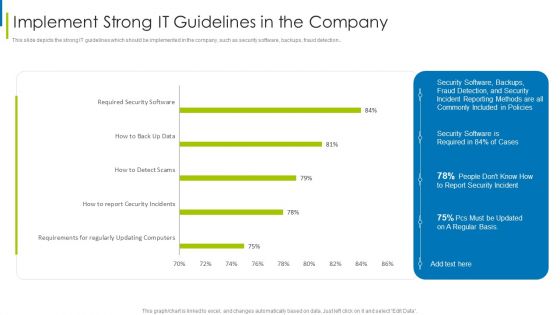
Cyber Terrorism Assault Implement Strong IT Guidelines In The Company Themes PDF
This slide depicts the strong IT guidelines which should be implemented in the company, such as security software, backups, fraud detection.Deliver and pitch your topic in the best possible manner with this cyber terrorism assault implement strong it guidelines in the company themes pdf Use them to share invaluable insights on requirements regularly, updating computers, required security software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
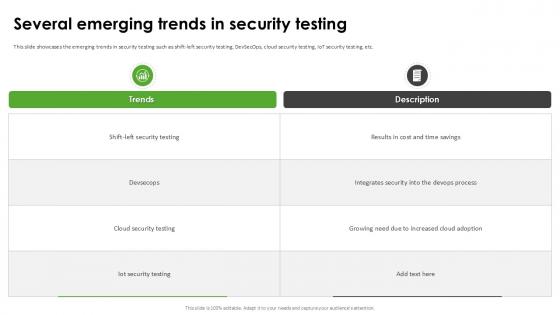
Several Emerging Trends In Harnessing The World Of Ethical Ppt Powerpoint
This slide showcases the emerging trends in security testing such as shift-left security testing, DevSecOps, cloud security testing, IoT security testing, etc. Are you searching for a Several Emerging Trends In Harnessing The World Of Ethical Ppt Powerpoint that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Several Emerging Trends In Harnessing The World Of Ethical Ppt Powerpoint from Slidegeeks today.

It Infrastructure Template Example Of Ppt
This is a it infrastructure template example of ppt. This is a ten stage process. The stages in this process are data management, network management, monitoring and notification, application management, security management.

1 Computers Behind A Firewall Connected To A Centralized Server Ppt Slides
This image slide displays computer behind a firewall connected to a centralized server. This image slide has been crafted with graphic of laptops, server and firewall icon connected. This image slide depicts security in networking. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template, in your presentations to explain concepts technology, networking and security. This image slide will enhance the quality of your presentations.
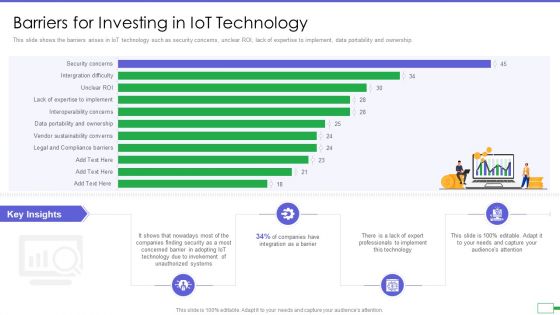
Iot And Digital Twin To Reduce Costs Post Covid Barriers For Investing In Iot Technology Sample PDF
This slide shows the barriers arises in IoT technology such as security concerns, unclear ROI, lack of expertise to implement, data portability and ownership. Deliver and pitch your topic in the best possible manner with this iot and digital twin to reduce costs post covid barriers for investing in iot technology sample pdf. Use them to share invaluable insights on security, technology, integration, implement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Online Gaming Funding Pitch Deck Rendering Unified Solutions To Handle Concerns Faced By Prospect Download PDF
This slide caters details about unified solutions to address concerns faced by clients in terms of game engine, security enhancement, revolutionary gameplay, absolute control. Deliver an awe inspiring pitch with this creative online gaming funding pitch deck rendering unified solutions to handle concerns faced by prospect download pdf bundle. Topics like game engine, revolutionary gameplay, security enhancement, absolute control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Online Gaming Funding Pitch Deck What Video Game Experience Challenges Are Faced By Prospect Portrait PDF
This slide caters details about key business challenges are faced by prospects in terms of security threats, regulatory compliances. Deliver an awe inspiring pitch with this creative online gaming funding pitch deck what video game experience challenges are faced by prospect portrait pdf bundle. Topics like security threats, regulatory compliances can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Online Gaming Fundraising Pitch Deck What Video Game Experience Challenges Are Faced By Prospect Slides PDF
This slide caters details about key business challenges are faced by prospects in terms of security threats, regulatory compliances. Deliver and pitch your topic in the best possible manner with this online gaming fundraising pitch deck what video game experience challenges are faced by prospect slides pdf. Use them to share invaluable insights on security threats, regulatory compliances and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

AI Applications In Banking And Financial Services Formats PDF
This slide covers use of artificial intelligence in banking and financial services. It involves applications such as customer engagement, predictive analytics, cyber security and credit scoring.Presenting AI Applications In Banking And Financial Services Formats PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Customer Engagement, Predictive Analytics, Cyber Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Detail Impact Electronic Information Ppt Portfolio Rules PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this cybersecurity detail impact electronic information ppt portfolio rules pdf. Use them to share invaluable insights on detail impact electronic information security plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Digital Risk Assessment Transformation Strategy With Implementation Slides PDF
The following slide highlights the cyber security transformation strategy with implementation illustrating benchmark, analysis, vision, roadmap, mobilization, and implementation which assists in transforming cyber security of organisation. Presenting Digital Risk Assessment Transformation Strategy With Implementation Slides PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Implementation, Benchmark, Analysis, Vision. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Enterprise Workforce Software Development Roadmap Microsoft PDF
This slide shows extended team software development timeline. It provides information about cyber security, front end, back end, coding, integration, feasibility, vulnerability, backup, etc. Pitch your topic with ease and precision using this Enterprise Workforce Software Development Roadmap Microsoft PDF. This layout presents information on Extended Cyber, Security Team, Vulnerability Scan, Feasibility Analysis. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

AI Applications Use To Improve Business Operations Diagrams PDF
This slide signifies the artificial intelligence software used to increase organisation operations. It covers information about hiring, market prediction, customer analysis and cyber security Presenting AI Applications Use To Improve Business Operations Diagrams PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Market Prediction, Customer Analysis, Cyber Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Best Practices For Cyber Safety At Job Safety Infographics PDF
This slide covers the best practices for cyber safety at workplace which includes protecting the data, using strong password protection, connecting to the secure wi-fi, investing in security systems, etc. Presenting best practices for cyber safety at job safety infographics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including protecting data, connect to secure wi fi, invest in security systems, strong password protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Safety Initiatives Setting Scenario For Cybersecurity Control Inspiration PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Deliver an awe inspiring pitch with this creative data safety initiatives setting scenario for cybersecurity control inspiration pdf bundle. Topics like scenario, technical controls, management controls, operational controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Companys Data Safety Recognition Highest Number Of Malware Attacks On Departments Sample PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative companys data safety recognition highest number of malware attacks on departments sample pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Highest Number Of Malware Attacks On Departments Ppt Inspiration Deck PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness Deliver an awe-inspiring pitch with this creative highest number of malware attacks on departments ppt inspiration deck pdf. bundle. Topics like r ans d department, sales department, accounts department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
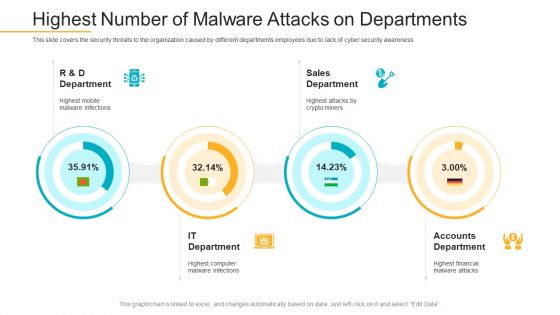
Data Breach Prevention Recognition Highest Number Of Malware Attacks On Departments Pictures PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition highest number of malware attacks on departments pictures pdf. Use them to share invaluable insights on sales department, accounts department, it department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Highest Number Of Malware Attacks On Departments Ppt Gallery Ideas PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative highest number of malware attacks on departments ppt gallery ideas pdf bundle. Topics like accounts department, sales department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
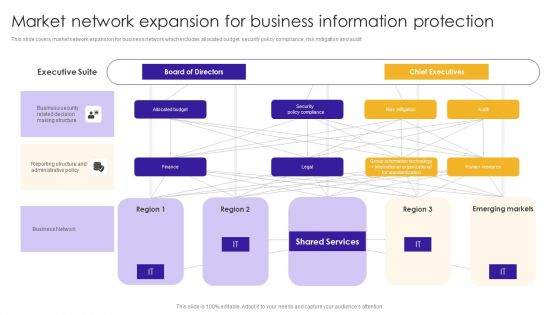
Market Network Expansion For Business Information Protection Sample PDF
This slide covers market network expansion for business network which includes allocated budget, security policy compliance, risk mitigation and audit. Showcasing this set of slides titled Market Network Expansion For Business Information Protection Sample PDF. The topics addressed in these templates are Business Security, Related Decision, Making Structure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Various Consumer Service Strategy Vendor Evaluation Matrix Rules PDF
This slide provides information regarding the evaluation matrix of various CRM vendors which are assessed on various parameters such as web security, etc. Deliver and pitch your topic in the best possible manner with this Various Consumer Service Strategy Vendor Evaluation Matrix Rules PDF. Use them to share invaluable insights on Activity Planning, Email Integration, Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
1 Icon Of A Firewall To Separate The Internal Network From The External World Ppt Slides
This image slide displays icon of firewall. This image slide has been crafted with graphic of firewall icon to separate internal network from the external world. This image slide depicts security on network. You may change size, color and orientation of any icon to your liking. Use this PowerPoint template, in your presentations to explain concepts like networking and security. This image slide will enhance the quality of your presentations.

Ensuring Food Quality Assurance Uplift Food Production Company Quality Standards Slides PDF
This slide provides information regarding food quality assurance by implementing food quality management system, digitalization of food security and safety data, food product quality assurance checklist. Deliver and pitch your topic in the best possible manner with this ensuring food quality assurance uplift food production company quality standards slides pdf. Use them to share invaluable insights on management, implementing, digitalization, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
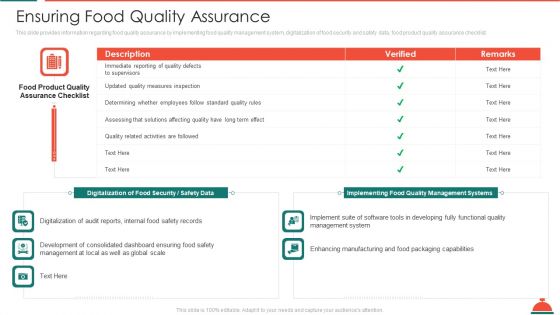
Ensuring Food Quality Assurance Increased Superiority For Food Products Professional PDF
This slide provides information regarding food quality assurance by implementing food quality management system, digitalization of food security and safety data, food product quality assurance checklist. Deliver and pitch your topic in the best possible manner with this ensuring food quality assurance increased superiority for food products professional pdf. Use them to share invaluable insights on management, implementing, digitalization, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
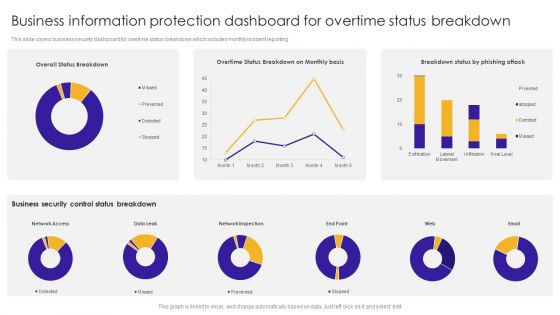
Business Information Protection Dashboard For Overtime Status Breakdown Introduction PDF
This slide covers business security dashboard for overtime status breakdown which includes monthly incident reporting.Pitch your topic with ease and precision using this Business Information Protection Dashboard For Overtime Status Breakdown Introduction PDF. This layout presents information on Business Security, Control Status Breakdown, Network Inspection. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
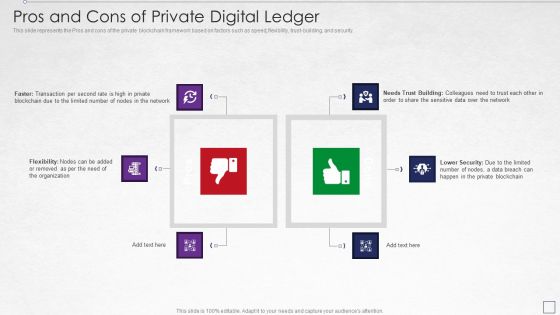
Digitized Record Book Technology Pros And Cons Of Private Digital Ledger Download PDF
This slide represents the Pros and cons of the private blockchain framework based on factors such as speed, flexibility, trust-building, and security. Deliver an awe inspiring pitch with this creative digitized record book technology pros and cons of private digital ledger download pdf bundle. Topics like network, organization, data, lower security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
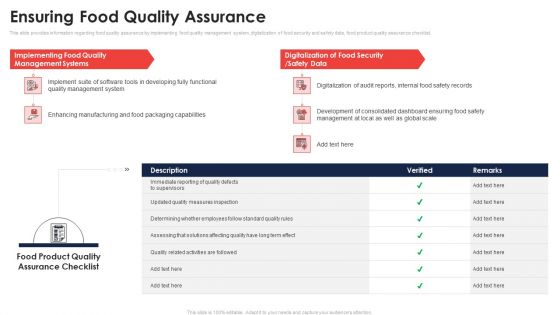
Ensuring Food Quality Assurance Application Of Quality Management For Food Processing Companies Guidelines PDF
This slide provides information regarding food quality assurance by implementing food quality management system, digitalization of food security and safety data, food product quality assurance checklist. Deliver and pitch your topic in the best possible manner with this ensuring food quality assurance application of quality management for food processing companies guidelines pdf. Use them to share invaluable insights on management, implementing, digitalization, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Ensuring Food Quality Assurance Assuring Food Quality And Hygiene Designs PDF
This slide provides information regarding food quality assurance by implementing food quality management system, digitalization of food security and safety data, food product quality assurance checklist. Deliver and pitch your topic in the best possible manner with this ensuring food quality assurance assuring food quality and hygiene designs pdf. Use them to share invaluable insights on management, implementing, digitalization, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
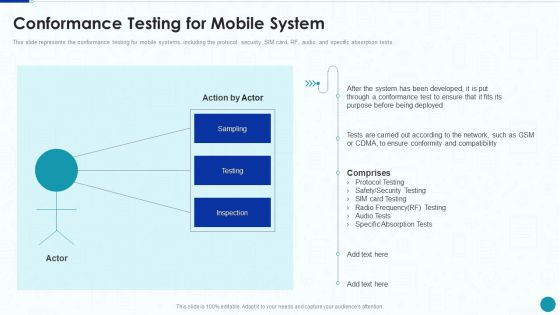
Compliance Testing IT Conformance Testing For Mobile System Microsoft PDF
This slide represents the conformance testing for mobile systems, including the protocol, security, SIM card, RF, audio, and specific absorption tests. Deliver an awe inspiring pitch with this creative Compliance Testing IT Conformance Testing For Mobile System Microsoft PDF bundle. Topics like Network, System, Security Testing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Distributed Computing IT Dashboard For Edge Computing Tracking Template PDF
This slide depicts the edge computing dashboard to monitor the security of networks and devices in the organization by covering threat prevention and detection details. Deliver and pitch your topic in the best possible manner with this distributed computing it dashboard for edge computing tracking template pdf. Use them to share invaluable insights on monitoring, security, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Integrating AI With IoT Role Of Edge Computing In AIoT IoT SS V
The purpose of this slide is to highlight importance of edge computing in Artificial Internet of Things AIoT. The slide cover information about reduced latency, bandwidth optimization, and improving data security and privacy. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Integrating AI With IoT Role Of Edge Computing In AIoT IoT SS V. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Integrating AI With IoT Role Of Edge Computing In AIoT IoT SS V today and make your presentation stand out from the rest

IoT Solutions For Oil IoT Implementation Challenges In Oil And Gas Industry IoT SS V
This slide discusses internet of things implementation challenges with solutions to ensure successful implementation. It includes challenges such as data security and privacy, integration issues, data overload, scalability and maintenance, etc. Explore a selection of the finest IoT Solutions For Oil IoT Implementation Challenges In Oil And Gas Industry IoT SS V here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our IoT Solutions For Oil IoT Implementation Challenges In Oil And Gas Industry IoT SS V to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Role Of Edge Computing In AIOT Applications For Various Industries IoT SS V
The purpose of this slide is to highlight importance of edge computing in Artificial Internet of Things AIoT. The slide cover information about reduced latency, bandwidth optimization, and improving data security and privacy. Find highly impressive Role Of Edge Computing In AIOT Applications For Various Industries IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Role Of Edge Computing In AIOT Applications For Various Industries IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Comparative Impact Of Iot Implementation On Retail Market Clipart PDF
The following slide highlights the impact of Internet of things implementation in retail sector. It also compares impact of IoT on manufacturing and business, healthcare, security and transportation. Welcome to our selection of the Comparative Impact Of Iot Implementation On Retail Market Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today

Building Cyber Risk Prevention In Financial Services Sector Elements PDF
The slide showcases the steps to develop the cyber resiliency of financial services industry. It covers steps like secure by design, zero trust, third party cyber risk assessment, security awareness training and cyber insurance. Persuade your audience using this Building Cyber Risk Prevention In Financial Services Sector Elements PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Secure By Design, Zero Trust, Security Awareness Training. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Benefits Of Educational Blogging Sample Diagram Ppt Images
This is a benefits of educational blogging sample diagram ppt images. This is a nine stage process. The stages in this process are global connection, classroom community, literacy, maths, ict skills, social skills, authentic audience, internet safety, home school, benefits.

Electronic Learning Playbook Best Practices To Protect Technology Systems Cont Introduction PDF
This slide provides information regarding best practices to protect technology systems in terms of compliance with legal regulations on student privacy, internet and content filtering. Deliver an awe inspiring pitch with this creative electronic learning playbook best practices to protect technology systems cont introduction pdf bundle. Topics like deploy internet content, approve applications websites, suitable school devices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
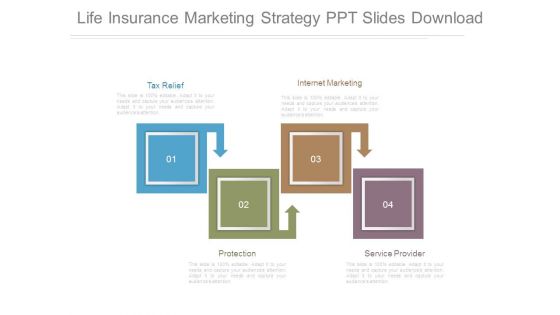
Life Insurance Marketing Strategy Ppt Slides Download
This is a life insurance marketing strategy ppt slides download. This is a four stage process. The stages in this process are tax relief, protection, internet marketing, service provider.

Web Marketing Planning Diagram Powerpoint Templates
This is a web marketing planning diagram powerpoint templates. This is a seven stage process. The stages in this process are product, e mail, blog, viral, networking, web site, online, internet marketing.

Cyber Physical Systems Architecture Network Layer Ppt Layouts Outline PDF
This slide describes the network layer of cyber physical system architecture, including the tasks performed and protocols used at this level, such as IPv6, LTE, IR, and so on. Deliver an awe inspiring pitch with this creative Cyber Physical Systems Architecture Network Layer Ppt Layouts Outline PDF bundle. Topics like Internet Connected Devices, Internet Protocol, Evolution can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Working Ecosystem Of Technological Smart Homes Automation Elements PDF
This side showcase the eco system of smart home and its working capabilities which helps in controlling energy use and maximize home security. It include the tools such as door lock, thermostat, security camera, smart light, smart plug and smart sensors. Showcasing this set of slides titled Working Ecosystem Of Technological Smart Homes Automation Elements PDF. The topics addressed in these templates are Internet, Gateway, Thermostats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
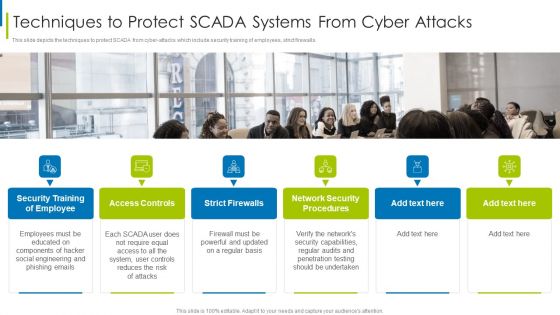
Cyber Terrorism Assault Techniques To Protect SCADA Systems From Cyber Attacks Demonstration PDF
This slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls.Presenting cyber terrorism assault techniques to protect scada systems from cyber attacks demonstration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like access controls, strict firewalls, network security procedures In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Checklist For Web Application Development Process Ppt Infographic Template Clipart Pdf
This slide represents the process checklist in order to develop web applications. It further includes activities such as design, UX, SEO checks, readability checks, performance checks, security checks, etc. Showcasing this set of slides titled Checklist For Web Application Development Process Ppt Infographic Template Clipart Pdf. The topics addressed in these templates are Readability Checks, Performance Checks, Security Checks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
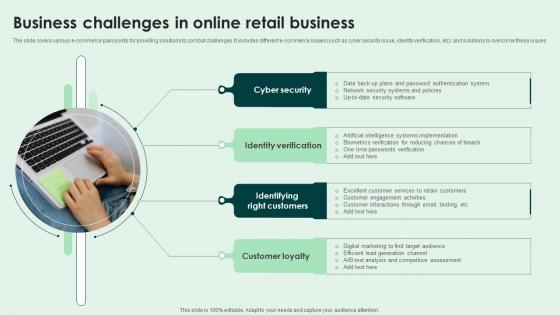
Business Challenges In Online Retail Business Introduction Pdf
The slide covers various e-commerce pain points for providing solutions to combat challenges. It includes different e-commerce issues such as cyber security issue, identity verification, etc and solutions to overcome these issues. Showcasing this set of slides titled Business Challenges In Online Retail Business Introduction Pdf. The topics addressed in these templates are Cyber Security, Identity Verification, Customer Loyalty. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Strategic Cyber Assessment And Assurance Model Microsoft PDF
The following slide illustrates cyber assessment framework aimed at analysing the extent to which cyber risks from functions are being managed by organisations. It covers roles and responsibilities under NIS objectives and principles. Showcasing this set of slides titled Strategic Cyber Assessment And Assurance Model Microsoft PDF. The topics addressed in these templates are Security Cases, System Security, Network And Systems. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

 Home
Home