Industrial Safety

Digitization Of Security Systems Ppt PowerPoint Presentation Complete Deck With Slides
This Digitization Of Security Systems Ppt PowerPoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing sixteen slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Digitization Of Security Systems Ppt PowerPoint Presentation Complete Deck With Slides PPT slideshow.

Managing Cyber Security Incident Ppt PowerPoint Presentation Complete Deck With Slides
This Managing Cyber Security Incident Ppt PowerPoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twenty slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Managing Cyber Security Incident Ppt PowerPoint Presentation Complete Deck With Slides PPT slideshow.

Information Technology Security KPI Ppt PowerPoint Presentation Complete Deck With Slides
This Information Technology Security KPI Ppt PowerPoint Presentation Complete Deck With Slides acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twelve slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this Information Technology Security KPI Ppt PowerPoint Presentation Complete Deck With Slides PPT slideshow.

Challenges Of Iot Device Deployment In Iot Device Management Guidelines Pdf
This slide highlights the key challenges of IoT devices in the manufacturing industry. These challenges include heavy investment, data security issues, lack of qualified staff, and integration with existing operational technologies. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Challenges Of Iot Device Deployment In Iot Device Management Guidelines Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Challenges Of Iot Device Deployment In Iot Device Management Guidelines Pdf today and make your presentation stand out from the rest

Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Technical Security Control Model With Supporting Function Introduction PDF. Use them to share invaluable insights on Cryptographic Administration, Security Management, System Protection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Unlocking Potential IoTs Application Major Application Of IoT In Transportation IoT SS V
This slide provides various applications of IoT techniques in various aspects of the transportation industry. It covers the application of IoT for traffic management, autonomous or self-driving cars, automated tolls or ticketing, vehicle tracking, and improving security. Create an editable Unlocking Potential IoTs Application Major Application Of IoT In Transportation IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Unlocking Potential IoTs Application Major Application Of IoT In Transportation IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Significance Of Technical SEO And Techniques Training Ppt
This slide provides information regarding technical SEO along with its significance. It also provides information regarding multiple techniques to make a website technical SEO-friendly, such as creating a website XML sitemap, using a secure sockets layer SSL, increasing website loading speed, etc.

Role Of Technical Competence In Organizational Cloud Security Architect Skills Scope Portrait PDF
This slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational technical, etc.Deliver an awe inspiring pitch with this creative Role Of Technical Competence In Organizational Cloud Security Architect Skills Scope Portrait PDF bundle. Topics like Architecture And Strategy, Technical, Leadership can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
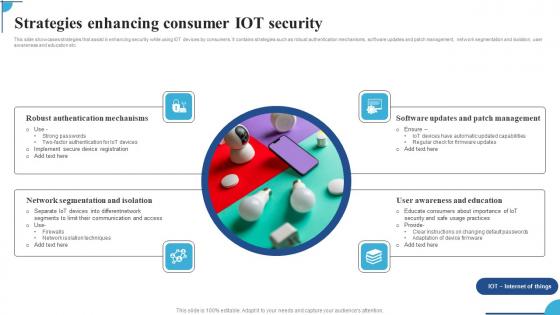
Strategies Enhancing Consumer IOT Security Ppt Pictures Graphic Images Pdf
This slide showcases strategies that assist in enhancing security while using IOT devices by consumers. It contains strategies such as robust authentication mechanisms,software updates and patch management,network segmentation and isolation,user awareness and education etc. Pitch your topic with ease and precision using this Strategies Enhancing Consumer IOT Security Ppt Pictures Graphic Images Pdf. This layout presents information on Robust Authentication Mechanisms,Network Segmentation Isolation,Software Updates. It is also available for immediate download and adjustment. So,changes can be made in the color,design,graphics or any other component to create a unique layout.
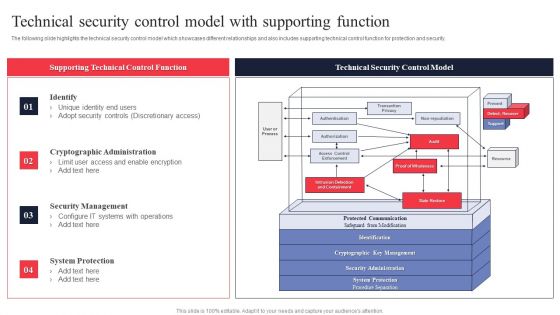
IT System Risk Management Guide Technical Security Control Model With Supporting Function Themes PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Slidegeeks has constructed IT System Risk Management Guide Technical Security Control Model With Supporting Function Themes PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
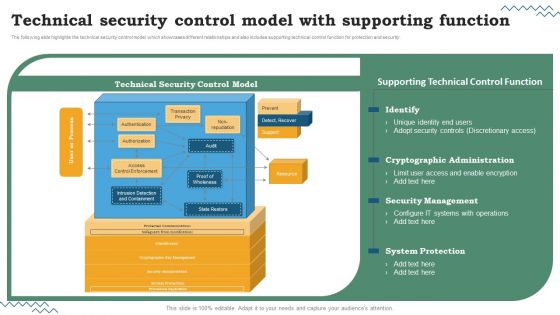
Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Are you searching for a Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF that is uncluttered, straightforward, and original. Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF from Slidegeeks today.

Machine Learning Applications In Different Areas Hyperautomation Software Solutions IT Designs PDF
This slide represents the applications of machine learning algorithms in different areas such as banking and finance, fraud detection, data security, the retail sector, and the healthcare industry. It also includes how these business operations the technology and its impact.Slidegeeks has constructed Machine Learning Applications In Different Areas Hyperautomation Software Solutions IT Designs PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Digital Trading Platform Fundraising Pitch Deck Problem Statement Template PDF
Following slide showcases major challenges faced by crypto currency trading industry. It includes issues such as complex interfaces, presence of illegal activities, security risks, lack of scalability and regulatory frameworks. Are you searching for a Digital Trading Platform Fundraising Pitch Deck Problem Statement Template PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Digital Trading Platform Fundraising Pitch Deck Problem Statement Template PDF from Slidegeeks today.

Role Of Hyperautomation In Redefining Business Machine Learning Applications Professional PDF
This slide represents the applications of machine learning algorithms in different areas such as banking and finance, fraud detection, data security, the retail sector, and the healthcare industry. It also includes how these business operations the technology and its impact. Get a simple yet stunning designed Role Of Hyperautomation In Redefining Business Machine Learning Applications Professional PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Role Of Hyperautomation In Redefining Business Machine Learning Applications Professional PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
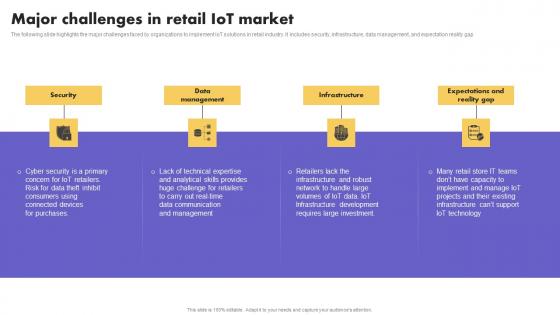
IoT Application In Global Major Challenges In Retail IoT Market Mockup Pdf
The following slide highlights the major challenges faced by organizations to implement IoT solutions in retail industry. It includes security, infrastructure, data management, and expectation reality gap. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward IoT Application In Global Major Challenges In Retail IoT Market Mockup Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal IoT Application In Global Major Challenges In Retail IoT Market Mockup Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
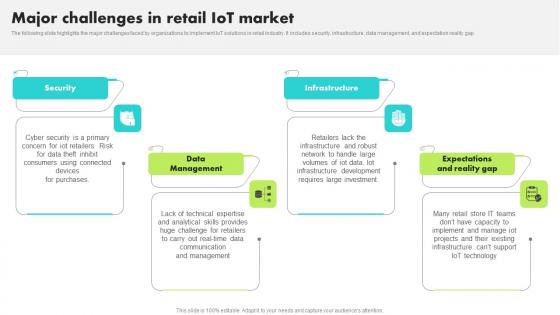
Major Challenges In Retail IoT Market Guide For Retail IoT Solutions Analysis Download Pdf
The following slide highlights the major challenges faced by organizations to implement IoT solutions in retail industry. It includes security, infrastructure, data management, and expectation reality gap Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Major Challenges In Retail IoT Market Guide For Retail IoT Solutions Analysis Download Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
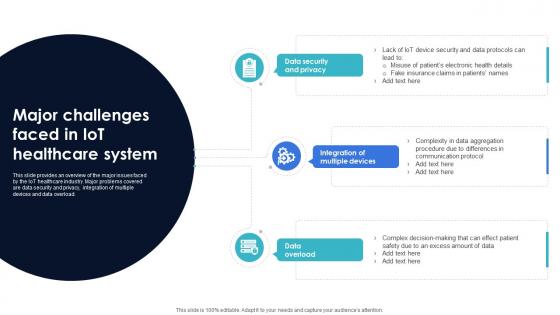
Optimization Of IoT Remote Monitoring Major Challenges Faced In IoT Healthcare System IoT SS V
This slide provides an overview of the major issues faced by the IoT healthcare industry. Major problems covered are data security and privacy, integration of multiple devices and data overload. Find highly impressive Optimization Of IoT Remote Monitoring Major Challenges Faced In IoT Healthcare System IoT SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Optimization Of IoT Remote Monitoring Major Challenges Faced In IoT Healthcare System IoT SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Key Drivers For Encouraging Adoption Of Complete Roadmap To Blockchain BCT SS V
This slide covers critical factors that encourages widespread adoption of blockchain technology across various industries. It includes drivers such as efficiency and cost savings, security and data integrity, disintermediation and decentralization, etc. This Key Drivers For Encouraging Adoption Of Complete Roadmap To Blockchain BCT SS V from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Impact Of IoT Platforms On Different Businesses Exploring Google Cloud IoT Platform
This slide showcases the after IoT platform impact on industries. It highlights the various factors that have improved which include energy efficiency, average revenue, productivity, security, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Impact Of IoT Platforms On Different Businesses Exploring Google Cloud IoT Platform to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
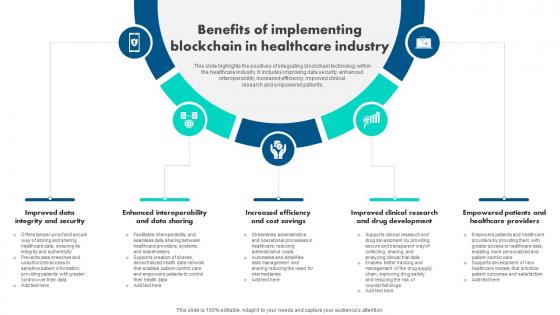
How Blockchain Is Reshaping Benefits Of Implementing Blockchain In Healthcare BCT SS V
This slide highlights the positives of integrating blockchain technology within the healthcare industry. It includes improving data security, enhanced interoperability, increased efficiency, improved clinical research and empowered patients. Slidegeeks is here to make your presentations a breeze with How Blockchain Is Reshaping Benefits Of Implementing Blockchain In Healthcare BCT SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first

Value Proposition CRMS Platform Business Model BMC SS V
This slide showcases the unique selling proposition offered by the company to its consumers. It includes industry-leading technology, complete suite of solutions, security, and compliance. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Value Proposition CRMS Platform Business Model BMC SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

IoT Solutions For Oil IoT Applications In Asset Management Within Oil And Gas IoT SS V
This slide consist of Internet of things use cases in asset management to improve the monitoring an maintenance of assets in the oil and gas industry. It covers real time monitoring of asset, remote management, and asset security. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download IoT Solutions For Oil IoT Applications In Asset Management Within Oil And Gas IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
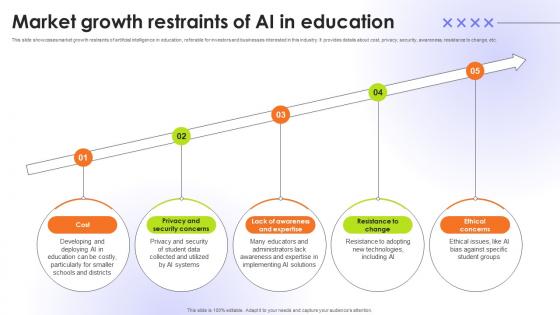
Market Growth Restraints Of AI In Education Educational Transformation Through AI SS V
This slide showcases market growth restraints of artificial intelligence in education, referable for investors and businesses interested in this industry. It provides details about cost, privacy, security, awareness, resistance to change, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Market Growth Restraints Of AI In Education Educational Transformation Through AI SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Company Introduction Email And Data Protection Platform Capital Funding Pitch Deck PPT Example
This slide covers a company overview of email security enterprise. It includes information such as foundation date, company status, employee count, headquarters, website, and industry. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Company Introduction Email And Data Protection Platform Capital Funding Pitch Deck PPT Example a try. Our experts have put a lot of knowledge and effort into creating this impeccable Company Introduction Email And Data Protection Platform Capital Funding Pitch Deck PPT Example. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
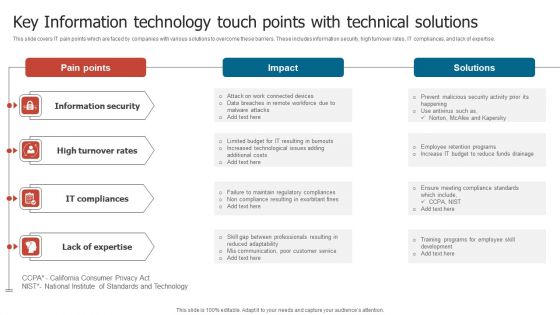
Key Information Technology Touch Points With Technical Solutions Topics PDF
This slide covers IT pain points which are faced by companies with various solutions to overcome these barriers. These includes information security, high turnover rates, IT compliances, and lack of expertise. Pitch your topic with ease and precision using this Key Information Technology Touch Points With Technical Solutions Topics PDF. This layout presents information on Information Security, High Turnover Rates, Lack Expertise. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Product Technical Assistant Engineer Task Management Plan Background PDF
Showcasing this set of slides titled Product Technical Assistant Engineer Task Management Plan Background PDF. The topics addressed in these templates are Securing Computer Systems, Organizing Workforce, Telecommunication. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
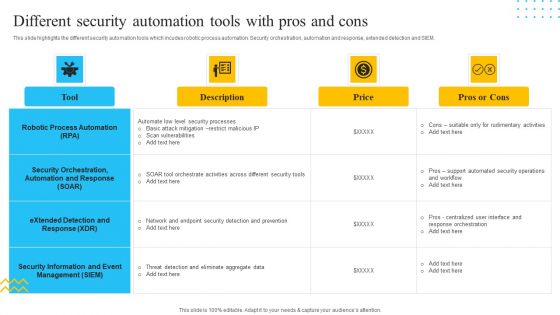
IT Security Automation Tools Integration Different Security Automation Tools With Pros And Cons Summary PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Deliver and pitch your topic in the best possible manner with this IT Security Automation Tools Integration Different Security Automation Tools With Pros And Cons Summary PDF. Use them to share invaluable insights on Robotic Process Automation, Security Orchestration, Price and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizations Risk Management And IT Security Identification And Recovery Of Technical Controls Introduction PDF
This slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Organizations Risk Management And IT Security Identification And Recovery Of Technical Controls Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
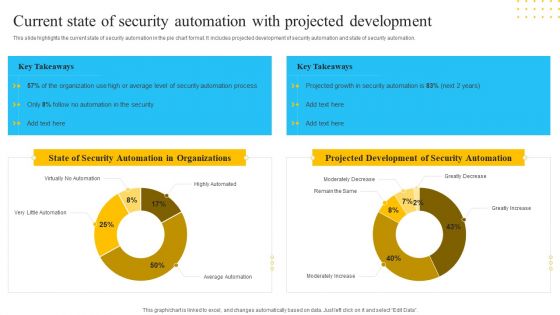
IT Security Automation Tools Integration Current State Of Security Automation With Projected Introduction PDF
This slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. Deliver and pitch your topic in the best possible manner with this IT Security Automation Tools Integration Current State Of Security Automation With Projected Introduction PDF. Use them to share invaluable insights on State Security, Automation Organizations, Projected Development, Security Automation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
IT Security Automation Tools Integration Security Automation Stages With Maturity Level Icons PDF
This slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Security Automation Stages With Maturity Level Icons PDF bundle. Topics like Security Automation, Maturity Level, Security Automation, Stages Opportunistic can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
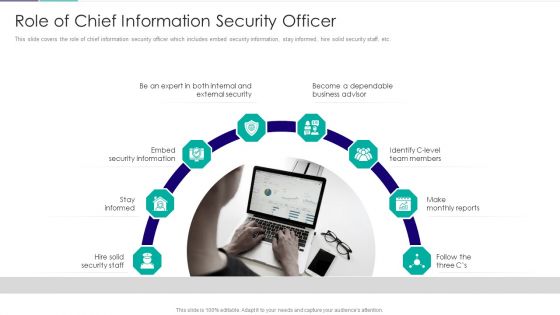
Role Of Technical Competence In Organizational Role Of Chief Information Security Officer Introduction PDF
This slide covers the role of chief information security officer which includes embed security information, stay informed, hire solid security staff, etc.This is a Role Of Technical Competence In Organizational Role Of Chief Information Security Officer Introduction PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Become A Dependable, Identify C Level Team Members, Make Monthly Reports You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
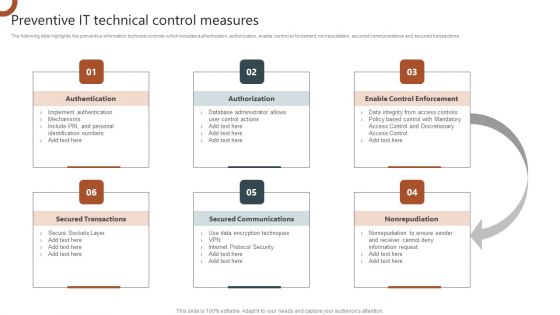
Organizations Risk Management And IT Security Preventive IT Technical Control Measures Topics PDF
The following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. Slidegeeks is here to make your presentations a breeze with Organizations Risk Management And IT Security Preventive IT Technical Control Measures Topics PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Enterprise Technical Challenges Managing Organizational Transformation Summary PDF
This slide covers technical challenges such as environmental, compatibility, skills shortage and security in enterprise while making IT OT convergence. Presenting Enterprise Technical Challenges Managing Organizational Transformation Summary PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Environmental, Compatibility, Skills Shortage. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
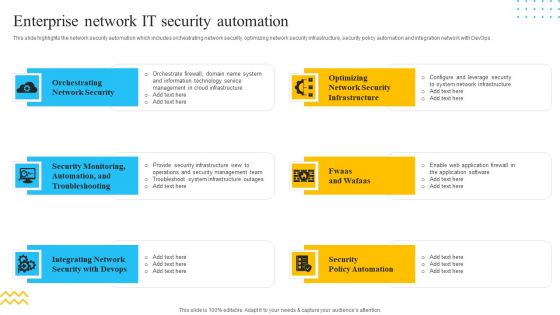
IT Security Automation Tools Integration Enterprise Network IT Security Automation Download PDF
This slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. This is a IT Security Automation Tools Integration Enterprise Network IT Security Automation Download PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Orchestrating Network Security, Integrating Network, Security Policy Automation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
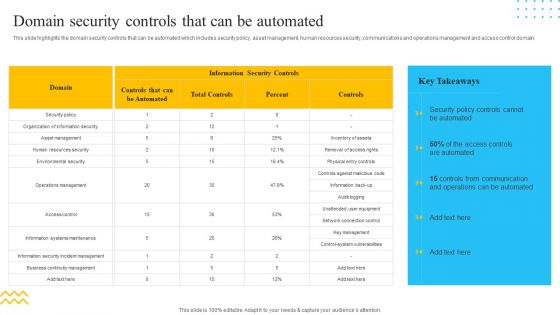
IT Security Automation Tools Integration Domain Security Controls That Can Be Automated Information PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Domain Security Controls That Can Be Automated Information PDF bundle. Topics like Information Security Controls, Controls, Security Policy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Automation Tools Integration Security Automation Dashboard Highlighting Network Portrait PDF
This slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Security Automation Dashboard Highlighting Network Portrait PDF bundle. Topics like Records Created, All Time, Hours Saved, Cost Savings can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Automation Framework Security Orchestration Automation And Response Layer Graphics PDF
This slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention. Get a simple yet stunning designed Cyber Security Automation Framework Security Orchestration Automation And Response Layer Graphics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cyber Security Automation Framework Security Orchestration Automation And Response Layer Graphics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
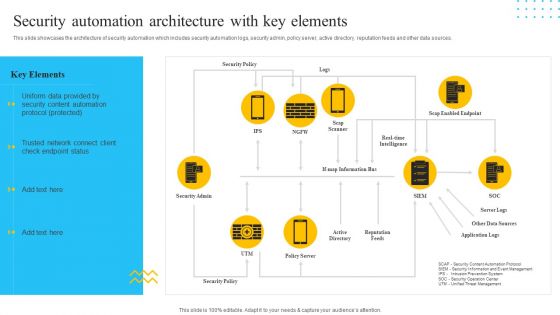
IT Security Automation Tools Integration Security Automation Architecture With Key Elements Mockup PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Presenting IT Security Automation Tools Integration Security Automation Architecture With Key Elements Mockup PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Security Policy, Security Admin, Reputation Feeds. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
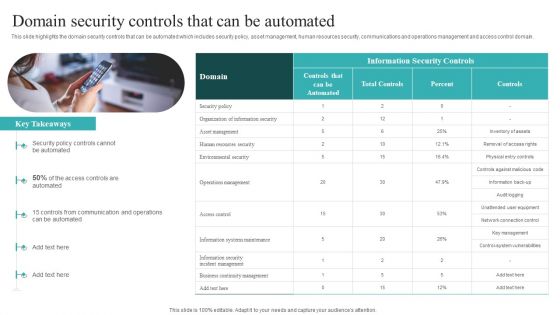
IT Security Automation Systems Guide Domain Security Controls That Can Be Automated Sample PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. There are so many reasons you need a IT Security Automation Systems Guide Domain Security Controls That Can Be Automated Sample PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
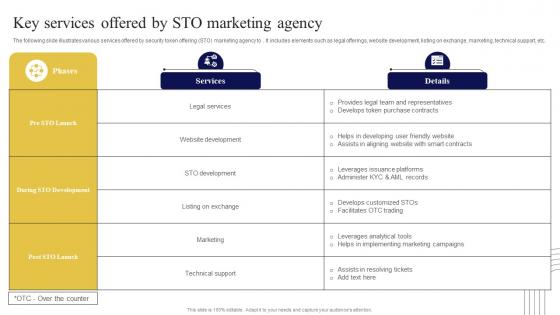
Key Services Offered By STO Exploring Investment Opportunities Topics Pdf
The following slide illustrates various services offered by security token offering STO marketing agency to. It includes elements such as legal offerings, website development, listing on exchange, marketing, technical support, etc. Slidegeeks has constructed Key Services Offered By STO Exploring Investment Opportunities Topics Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
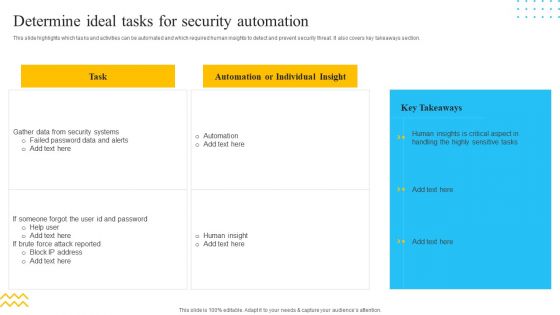
IT Security Automation Tools Integration Determine Ideal Tasks For Security Automation Template PDF
This slide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Determine Ideal Tasks For Security Automation Template PDF bundle. Topics like Automation, Individual Insight, Gather Data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
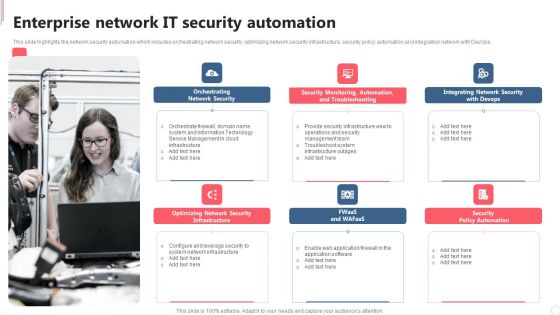
Cyber Security Automation Framework Enterprise Network IT Security Automation Background PDF
This slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Boost your pitch with our creative Cyber Security Automation Framework Enterprise Network IT Security Automation Background PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
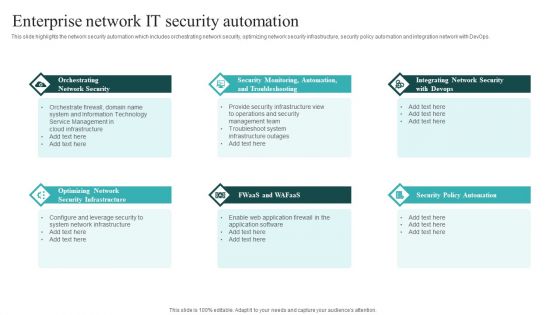
IT Security Automation Systems Guide Enterprise Network It Security Automation Sample PDF
This slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give IT Security Automation Systems Guide Enterprise Network It Security Automation Sample PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable IT Security Automation Systems Guide Enterprise Network It Security Automation Sample PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cyber Security Automation Framework Different Security Automation Tools With Pros And Cons Clipart PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Security Automation Framework Different Security Automation Tools With Pros And Cons Clipart PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
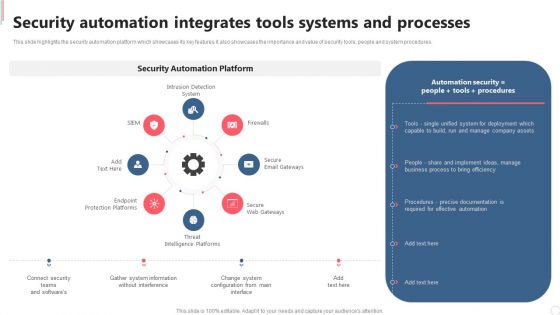
Cyber Security Automation Framework Security Automation Integrates Tools Systems And Processes Formats PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. There are so many reasons you need a Cyber Security Automation Framework Security Automation Integrates Tools Systems And Processes Formats PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM.Whether you have daily or monthly meetings, a brilliant presentation is necessary. Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF can be your best option for delivering a presentation. Represent everything in detail using Security Automation To Analyze And Mitigate Cyberthreats Different Security Automation Tools Information PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

IT Security Automation Tools Integration Right Time To Add Automation In Security Summary PDF
This slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. This is a IT Security Automation Tools Integration Right Time To Add Automation In Security Summary PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Failed Human Insights, Right Time Automation, High Time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
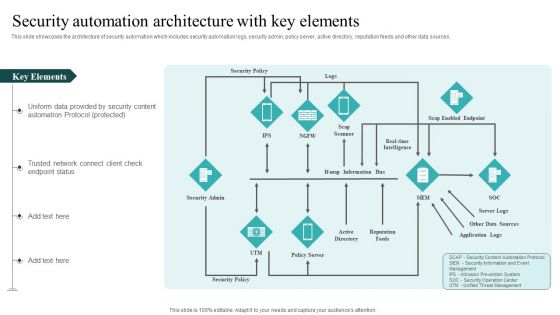
IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Make sure to capture your audiences attention in your business displays with our gratis customizable IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
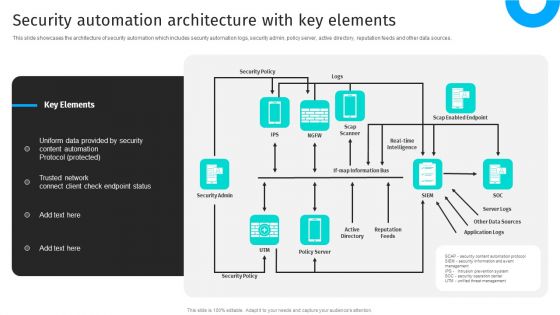
Security Automation To Analyze And Mitigate Cyberthreats Security Automation Architecture Topics PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources.This modern and well-arranged Security Automation To Analyze And Mitigate Cyberthreats Security Automation Architecture Topics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

IT Security Automation Tools Integration Measure Security Automation Metrics For Operations Template PDF
This slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Deliver and pitch your topic in the best possible manner with this IT Security Automation Tools Integration Measure Security Automation Metrics For Operations Template PDF. Use them to share invaluable insights on Metric, Operation Performance Improvements, Success and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
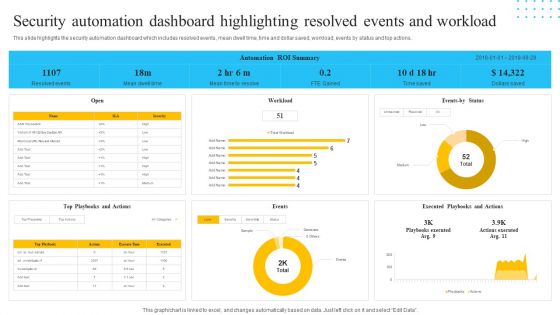
IT Security Automation Tools Integration Security Automation Dashboard Highlighting Resolved Inspiration PDF
This slide highlights the security automation dashboard which includes resolved events, mean dwell time, time and dollar saved, workload, events by status and top actions. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Security Automation Dashboard Highlighting Resolved Inspiration PDF bundle. Topics like Events Status, Workload, Events, Open can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
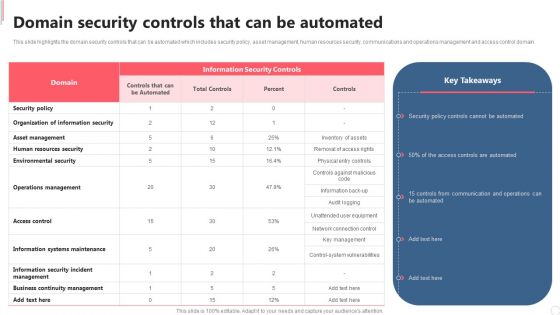
Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF.

Cloud Computing Business Driven Security Architecture Introduction PDF
The slide shows a security framework of business driven services. It highlight cloud computing services such as SaaS, PaaS and IaaS and security services such as data security management, software and service assertion, technical service control, risk management infrastructure management, etc. Showcasing this set of slides titled Cloud Computing Business Driven Security Architecture Introduction PDF. The topics addressed in these templates are Strategies, Delegation Authority, Service Goals. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
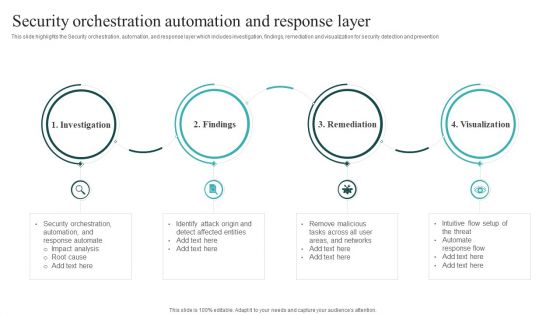
IT Security Automation Systems Guide Security Orchestration Automation And Response Layer Themes PDF
This slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention. Whether you have daily or monthly meetings, a brilliant presentation is necessary. IT Security Automation Systems Guide Security Orchestration Automation And Response Layer Themes PDF can be your best option for delivering a presentation. Represent everything in detail using IT Security Automation Systems Guide Security Orchestration Automation And Response Layer Themes PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

IT Security Automation Tools Integration Criteria To Automate Security Analysis And Response Portrait PDF
This slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Criteria To Automate Security Analysis And Response Portrait PDF bundle. Topics like Responses, Criteria, Activities Repeatable can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Automation Tools Integration Security Automation Integrates Tools Systems Summary PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. This is a IT Security Automation Tools Integration Security Automation Integrates Tools Systems Summary PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intrusion Detection System, Firewalls, Secure Email Gateways. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
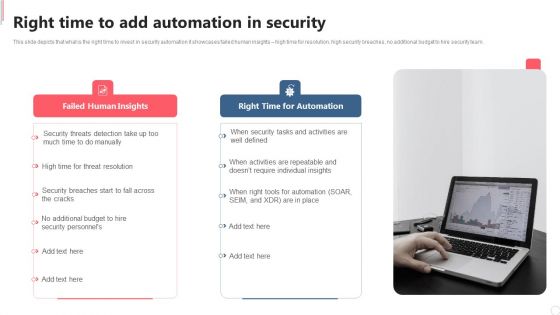
Cyber Security Automation Framework Right Time To Add Automation In Security Microsoft PDF
This slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. Want to ace your presentation in front of a live audience Our Cyber Security Automation Framework Right Time To Add Automation In Security Microsoft PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
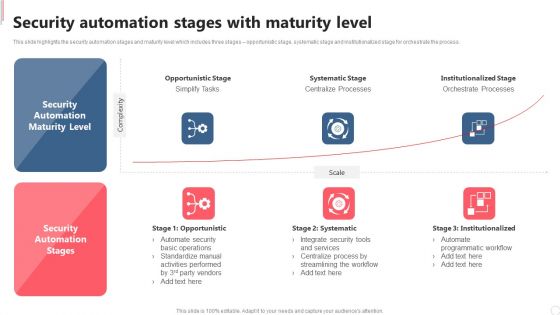
Cyber Security Automation Framework Security Automation Stages With Maturity Level Clipart PDF
This slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cyber Security Automation Framework Security Automation Stages With Maturity Level Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cyber Security Automation Framework Security Automation Stages With Maturity Level Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
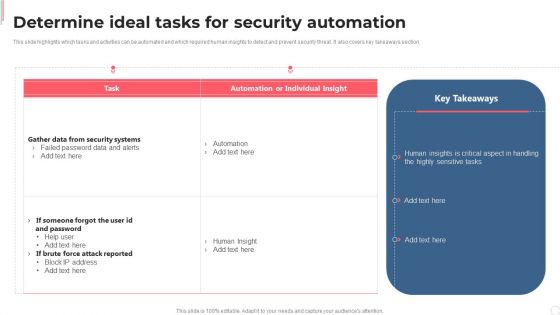
Cyber Security Automation Framework Determine Ideal Tasks For Security Automation Demonstration PDF
This slide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cyber Security Automation Framework Determine Ideal Tasks For Security Automation Demonstration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cyber Security Automation Framework Determine Ideal Tasks For Security Automation Demonstration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
IT Security Automation Systems Guide Security Automation Stages With Maturity Level Icons PDF
This slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than IT Security Automation Systems Guide Security Automation Stages With Maturity Level Icons PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab IT Security Automation Systems Guide Security Automation Stages With Maturity Level Icons PDF today and make your presentation stand out from the rest.

 Home
Home