Incident
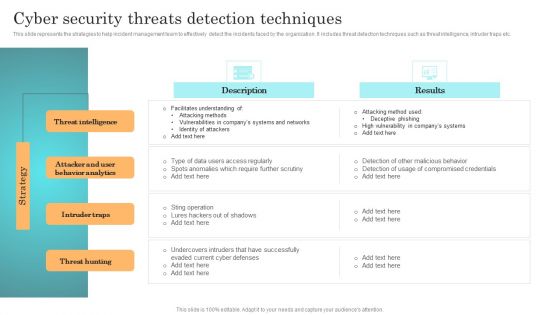
Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Are you searching for a Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Incident Response Techniques Deployement Cyber Security Threats Detection Techniques Portrait PDF from Slidegeeks today.

CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF today and make your presentation stand out from the rest.

Pyramid For Safety Incident Reporting Ppt PowerPoint Presentation Summary Professional PDF
Presenting pyramid for safety incident reporting ppt powerpoint presentation summary professional pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including incidents pyramid report, fatality, serious injuries, lost time incidents, minor incidents, medical aids, first aids, modified work. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Implementing Cyber Security Incident Cyber Security Crisis Action Plan Timeline Summary PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Implementing Cyber Security Incident Cyber Security Crisis Action Plan Timeline Summary PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Implementing Cyber Security Incident Cyber Security Crisis Action Plan Timeline Summary PDF

CYBER Security Breache Response Strategy Cyber Security Incident Response Plan Timeline Demonstration PDF
This slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our CYBER Security Breache Response Strategy Cyber Security Incident Response Plan Timeline Demonstration PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into CYBER Security Breache Response Strategy Cyber Security Incident Response Plan Timeline Demonstration PDF

CYBER Security Breache Response Strategy Cyber Security Incident Response Process Flow Chart Background PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created CYBER Security Breache Response Strategy Cyber Security Incident Response Process Flow Chart Background PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Rebuilding Travel Industry After COVID 19 Incident Management Summary Report Sample PDF
This slide can be utilized to report any workplace incidents. After filling this form it will be forwarded to Business unit safety director and HR representative. This is a rebuilding travel industry after COVID 19 incident management summary report sample pdf. template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employees involved, time of incident, detailed description of event, corrective management, action plan, action duration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
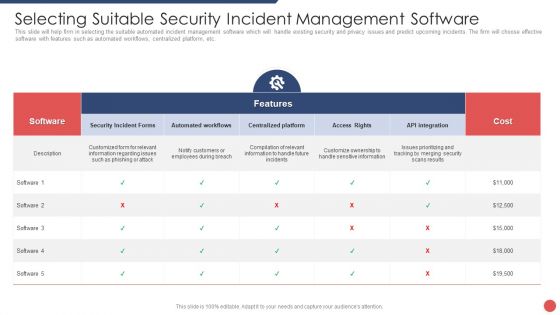
Security Functioning Centre Selecting Suitable Security Incident Management Software Introduction PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative security functioning centre selecting suitable security incident management software introduction pdf bundle. Topics like prioritizing, customers, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
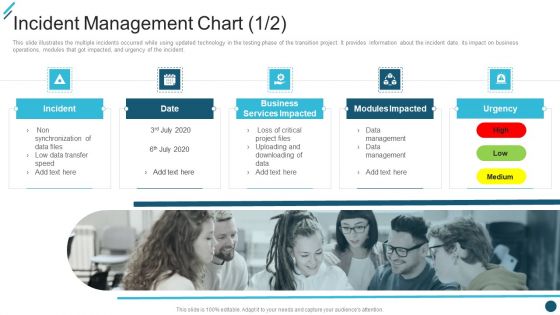
Change Execution Plan Incident Management Chart Ppt PowerPoint Presentation File Graphics Template PDF
This slide illustrates the multiple incidents occurred while using updated technology in the testing phase of the transition project. It provides information about the incident date, its impact on business operations, modules that got impacted, and urgency of the incident. This is a Change Execution Plan Incident Management Chart Ppt PowerPoint Presentation File Graphics Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Business Services Impacted, Modules Impacted Urgency, High Low Medium. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Are you searching for a Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Implementing Cyber Security Incident Cyber Security Threats Detection Techniques Slides PDF from Slidegeeks today.

Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Find highly impressive Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
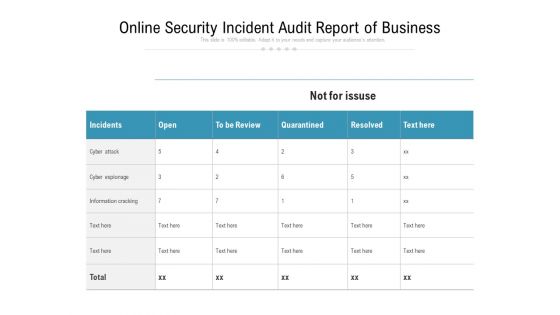
Online Security Incident Audit Report Of Business Ppt PowerPoint Presentation Inspiration Layout Ideas PDF
Pitch your topic with ease and precision using this online security incident audit report of business ppt powerpoint presentation inspiration layout ideas pdf. This layout presents information on incidents, cyber attack, cyber espionage, information cracking. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
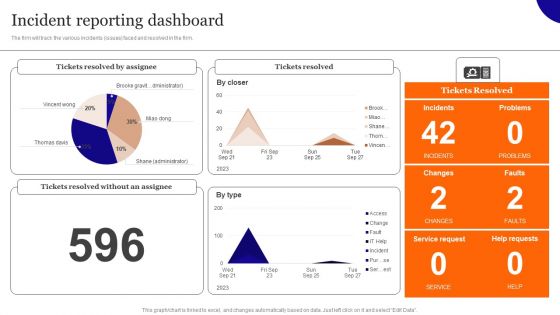
Overview On Mitigating Workplace IT Threats Incident Reporting Dashboard Professional PDF
The firm will track the various incidents issues faced and resolved in the firm. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Overview On Mitigating Workplace IT Threats Incident Reporting Dashboard Professional PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Overview On Mitigating Workplace IT Threats Incident Reporting Dashboard Professional PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
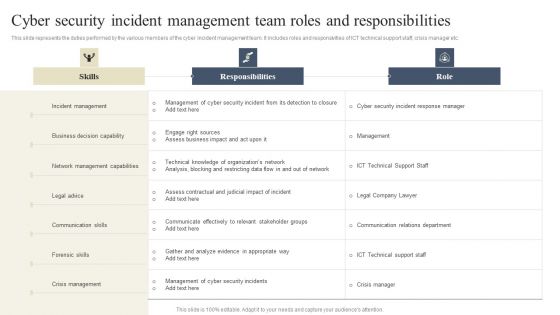
CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. If you are looking for a format to display your unique thoughts, then the professionally designed CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Deploying Cyber Security Incident Response Administration Cyber Supply Chain Risk Management Dashboard Themes PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Deploying Cyber Security Incident Response Administration Cyber Supply Chain Risk Management Dashboard Themes PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Deploying Cyber Security Incident Response Administration Cyber Supply Chain Risk Management Dashboard Themes PDF today and make your presentation stand out from the rest.
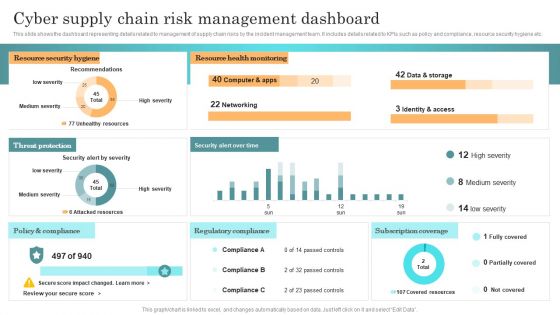
Incident Response Techniques Deployement Cyber Supply Chain Risk Management Dashboard Topics PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Incident Response Techniques Deployement Cyber Supply Chain Risk Management Dashboard Topics PDF can be your best option for delivering a presentation. Represent everything in detail using Incident Response Techniques Deployement Cyber Supply Chain Risk Management Dashboard Topics PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

CYBER Security Breache Response Strategy Budget Allocation For Cyber Incident Management Training Topics PDF
This slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. Create an editable CYBER Security Breache Response Strategy Budget Allocation For Cyber Incident Management Training Topics PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. CYBER Security Breache Response Strategy Budget Allocation For Cyber Incident Management Training Topics PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF.

CYBER Security Breache Response Strategy Comparative Analysis Of Cyber Security Incident Mitigation Guidelines PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Want to ace your presentation in front of a live audience Our CYBER Security Breache Response Strategy Comparative Analysis Of Cyber Security Incident Mitigation Guidelines PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
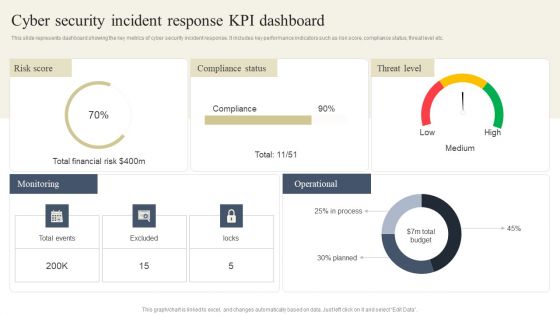
CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
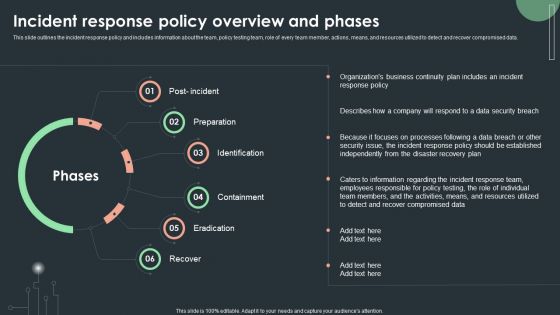
Cybersecurity Guidelines IT Incident Response Policy Overview And Phases Template PDF
This slide outlines the incident response policy and includes information about the team, policy testing team, role of every team member, actions, means, and resources utilized to detect and recover compromised data. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cybersecurity Guidelines IT Incident Response Policy Overview And Phases Template PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cybersecurity Guidelines IT Incident Response Policy Overview And Phases Template PDF.

Information Technology Policy And Processes Incident Response Policy Overview And Phases Sample PDF
This slide outlines the incident response policy and includes information about the team, policy testing team, role of every team member, actions, means, and resources utilized to detect and recover compromised data. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Information Technology Policy And Processes Incident Response Policy Overview And Phases Sample PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Information Technology Policy And Processes Incident Response Policy Overview And Phases Sample PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
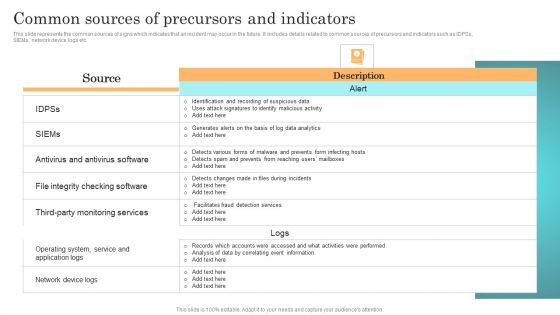
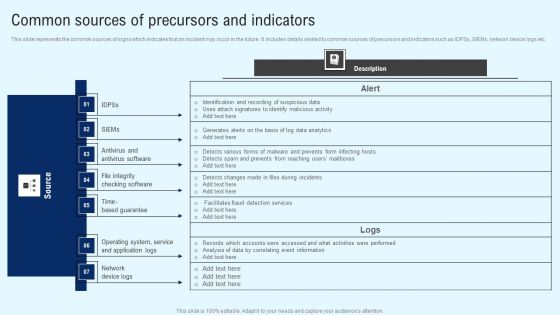
Incident Response Techniques Deployement Common Sources Of Precursors And Indicators Diagrams PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Create an editable Incident Response Techniques Deployement Common Sources Of Precursors And Indicators Diagrams PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Incident Response Techniques Deployement Common Sources Of Precursors And Indicators Diagrams PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
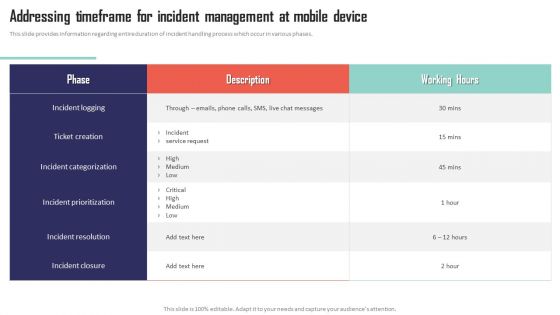
Mobile Device Management Addressing Timeframe For Incident Management At Mobile Slides PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Mobile Device Management Addressing Timeframe For Incident Management At Mobile Slides PDF can be your best option for delivering a presentation. Represent everything in detail using Mobile Device Management Addressing Timeframe For Incident Management At Mobile Slides PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Mobile Device Management For Improving IT Operations Addressing Timeframe For Incident Management Microsoft PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Mobile Device Management For Improving IT Operations Addressing Timeframe For Incident Management Microsoft PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Mobile Device Management For Improving IT Operations Addressing Timeframe For Incident Management Microsoft PDF.

Key Lessons Learned By Organization From Cyber Security Incident Management Designs PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Key Lessons Learned By Organization From Cyber Security Incident Management Designs PDF can be your best option for delivering a presentation. Represent everything in detail using Key Lessons Learned By Organization From Cyber Security Incident Management Designs PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Real Time Incident Management Solution Investor Funding Pitch Deck Company Introduction Introduction PDF
This slide represents the overview of company which provides an incident management platform with intelligent slack integration. It showcases industry, business model, customer, headquarters, type, founded year and founders. Create an editable Real Time Incident Management Solution Investor Funding Pitch Deck Company Introduction Introduction PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Real Time Incident Management Solution Investor Funding Pitch Deck Company Introduction Introduction PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Real Time Incident Management Solution Investor Funding Pitch Deck Financial Performance Information PDF
This slide showcases the financial performance of the company which provides an incident management platform with intelligent slack integration. It include graph that shows the annualized revenue of the company and NPS Net Promoter Score. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Real Time Incident Management Solution Investor Funding Pitch Deck Financial Performance Information PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Real Time Incident Management Solution Investor Funding Pitch Deck Financial Performance Information PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
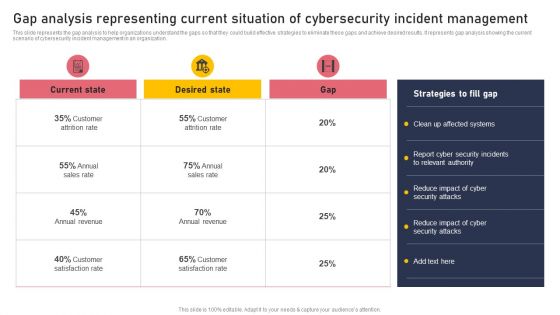
Gap Analysis Representing Current Situation Of Cybersecurity Incident Management Clipart PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Get a simple yet stunning designed Gap Analysis Representing Current Situation Of Cybersecurity Incident Management Clipart PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Gap Analysis Representing Current Situation Of Cybersecurity Incident Management Clipart PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
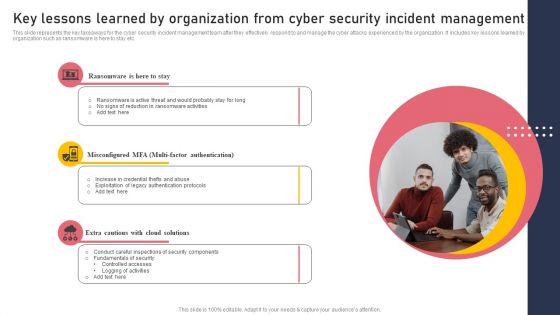
Key Lessons Learned By Organization From Cyber Security Incident Management Graphics PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Key Lessons Learned By Organization From Cyber Security Incident Management Graphics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Key Lessons Learned By Organization From Cyber Security Incident Management Graphics PDF today and make your presentation stand out from the rest.

Real Time Incident Management Solution Investor Funding Pitch Deck Problem Statement Information PDF
This slide showcases identified problems that are commonly faced by developers for incident management. Challenges includes lack of timely incident alerting, fragmented communication and collaboration, manual escalation and notification processes, lack of insights and analytics, etc. Slidegeeks is here to make your presentations a breeze with Real Time Incident Management Solution Investor Funding Pitch Deck Problem Statement Information PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
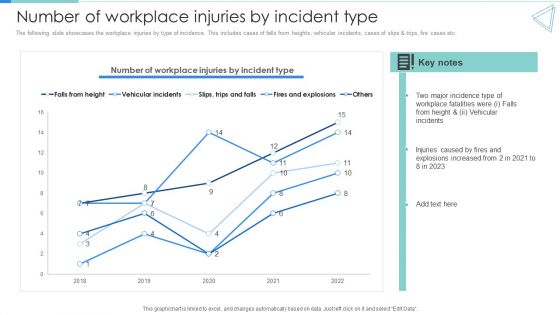
Deployment Of Workplace Safety Management Program Number Of Workplace Injuries By Incident Type Themes PDF
The following slide showcases the workplace injuries by type of incidence. This includes cases of falls from heights, vehicular incidents, cases of slips And trips, fire cases etc. There are so many reasons you need a Deployment Of Workplace Safety Management Program Number Of Workplace Injuries By Incident Type Themes PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Managing Cyber Security Incident Response KPI Dashboard Ppt Layouts Shapes PDF
This slide covers cyber security incident response KPI dashboard. It involves details such as intent alarm, event trend sources, event trend, sensor activity, major operating systems and asset information. Pitch your topic with ease and precision using this Managing Cyber Security Incident Response KPI Dashboard Ppt Layouts Shapes PDF. This layout presents information on Top Alarms Method, Alarms Intent, Timely Event Trend. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
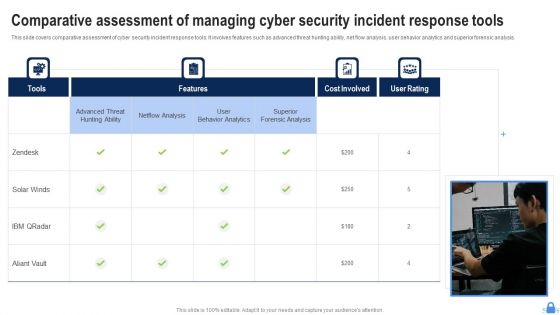
Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF
This slide covers comparative assessment of cyber security incident response tools. It involves features such as advanced threat hunting ability, net flow analysis, user behavior analytics and superior forensic analysis. Presenting Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Superior Forensic Analysis, User Behavior Analytics, Netflow Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
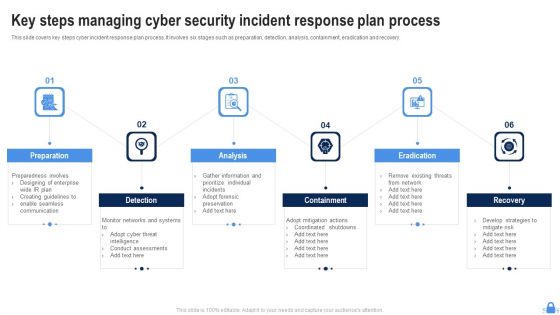
Key Steps Managing Cyber Security Incident Response Plan Process Portrait PDF
This slide covers key steps cyber incident response plan process. It involves six stages such as preparation, detection, analysis, containment, eradication and recovery. Persuade your audience using this Key Steps Managing Cyber Security Incident Response Plan Process Portrait PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Preparation, Detection, Analysis, Eradication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
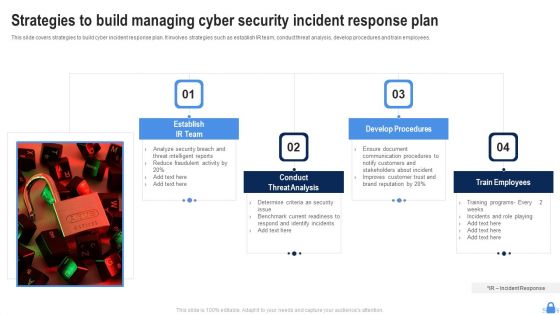
Strategies To Build Managing Cyber Security Incident Response Plan Demonstration PDF
This slide covers strategies to build cyber incident response plan. It involves strategies such as establish IR team, conduct threat analysis, develop procedures and train employees. Persuade your audience using this Strategies To Build Managing Cyber Security Incident Response Plan Demonstration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Establish IR Team, Conduct Threat Analysis, Develop Procedures. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Table Of Contents For Deploying Cyber Security Incident Response Administration Gap Sample PDF
Find highly impressive Table Of Contents For Deploying Cyber Security Incident Response Administration Gap Sample PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents For Deploying Cyber Security Incident Response Administration Gap Sample PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
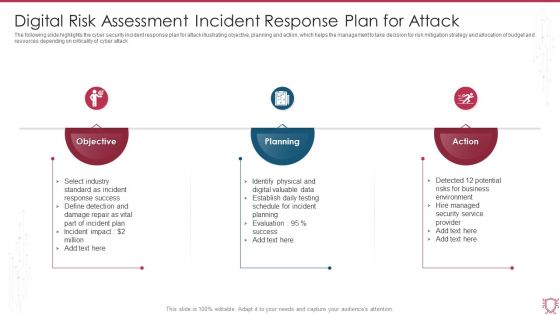
Digital Risk Assessment Incident Response Plan For Attack Ppt Backgrounds PDF
The following slide highlights the cyber security incident response plan for attack illustrating objective, planning and action, which helps the management to take decision for risk mitigation strategy and allocation of budget and resources depending on criticality of cyber attack. Persuade your audience using this Digital Risk Assessment Incident Response Plan For Attack Ppt Backgrounds PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Objective, Planning, Action. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
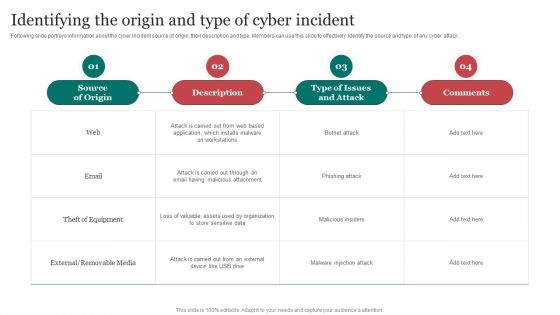
Identifying The Origin And Type Of Cyber Improving Cybersecurity With Incident Summary PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack.Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Identifying The Origin And Type Of Cyber Improving Cybersecurity With Incident Summary PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Identifying The Origin And Type Of Cyber Improving Cybersecurity With Incident Summary PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Are you searching for a Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF from Slidegeeks today.

5 Stage Process Of Critical Incident Technique Quality Control Planning Templates Set 1 Diagrams PDF
This slide displays five staged process of critical incident technique. Stages covered in the slide are establish aims, planning, collect data, analyze data and interpret share findings. Whether you have daily or monthly meetings, a brilliant presentation is necessary. 5 Stage Process Of Critical Incident Technique Quality Control Planning Templates Set 1 Diagrams PDF can be your best option for delivering a presentation. Represent everything in detail using 5 Stage Process Of Critical Incident Technique Quality Control Planning Templates Set 1 Diagrams PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Implementing Cyber Security Incident Common Sources Of Precursors And Indicators Inspiration PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Target Groups Involved In Project Communication Critical Incident Communication Graphics Pdf
This template covers target groups members involved in project communication such as general public and other organizations. It also includes list of target groups such as environmental agencies, local authorities, People from NGOs, etc. Presenting this PowerPoint presentation, titled Target Groups Involved In Project Communication Critical Incident Communication Graphics Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Target Groups Involved In Project Communication Critical Incident Communication Graphics Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Target Groups Involved In Project Communication Critical Incident Communication Graphics Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Cyber Safety Incident Management Determine Threat Management Team Structure Professional PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a cyber safety incident management determine threat management team structure professional pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine threat management team structure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
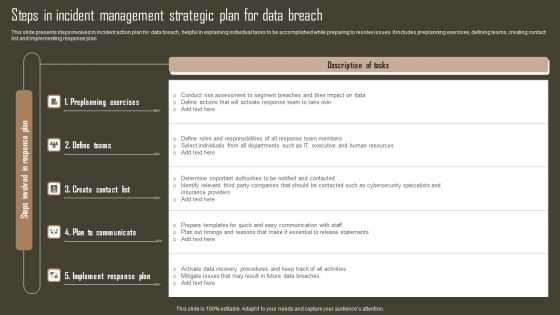
Steps In Incident Management Strategic Plan For Data Breach Pictures PDF
This slide presents steps involved in incident action plan for data breach, helpful in explaining individual tasks to be accomplished while preparing to resolve issues. It includes preplanning exercises, defining teams, creating contact list and implementing response plan. Showcasing this set of slides titled Steps In Incident Management Strategic Plan For Data Breach Pictures PDF. The topics addressed in these templates are Preplanning Exercises, Plan To Communicate, Implement Response Plan. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
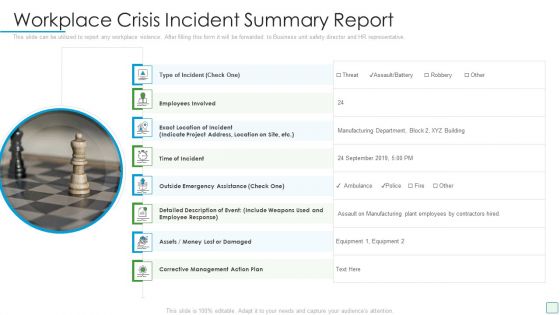
Developing Firm Security Strategy Plan Workplace Crisis Incident Summary Report Professional PDF
This slide can be utilized to report any workplace violence. After filling this form it will be forwarded to Business unit safety director and HR representative. Presenting developing firm security strategy plan workplace crisis incident summary report professional pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like management action plan, time of incident, employees involved, outside emergency assistance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Safety Initiatives Flow Diagram Of Incident Response Process Designs PDF
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. Presenting data safety initiatives flow diagram of incident response process designs pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like preparatory, core response, close down, escalate, kick off response, analyse. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
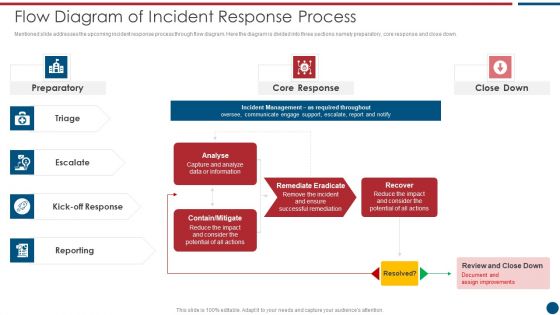
Risk Based Procedures To IT Security Flow Diagram Of Incident Response Process Themes PDF
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. This is a Risk Based Procedures To IT Security Flow Diagram Of Incident Response Process Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Core Response, Contain Mitigate, Remediate Eradicate. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Phases Of Digital Risk Assessment Incident Response Cycle Ppt Gallery Format Ideas PDF
The following slide highlights the phase of cyber security incident response cycle depicting preparation phase, analysis phase, response phase, and post event phase. Persuade your audience using this Phases Of Digital Risk Assessment Incident Response Cycle Ppt Gallery Format Ideas PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Post Event Phase, Response Phase, Preparation Phase, Analysis Phase. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Five Yearly Life Science Incident Response And Recovery Process Roadmap Demonstration
We present our five yearly life science incident response and recovery process roadmap demonstration. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched five yearly life science incident response and recovery process roadmap demonstration in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
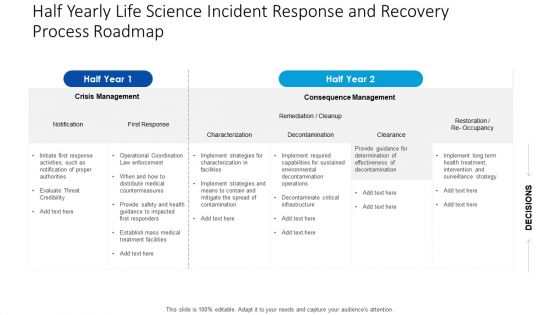
Half Yearly Life Science Incident Response And Recovery Process Roadmap Designs
We present our half yearly life science incident response and recovery process roadmap designs. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly life science incident response and recovery process roadmap designs in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
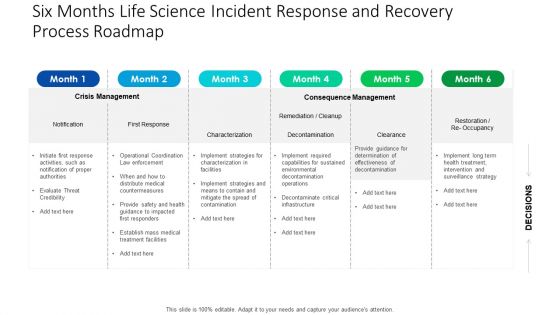
Six Months Life Science Incident Response And Recovery Process Roadmap Ideas
We present our six months life science incident response and recovery process roadmap ideas. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months life science incident response and recovery process roadmap ideas in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
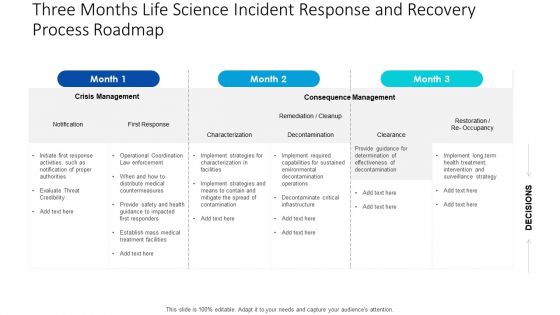
Three Months Life Science Incident Response And Recovery Process Roadmap Inspiration
We present our three months life science incident response and recovery process roadmap inspiration. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched three months life science incident response and recovery process roadmap inspiration in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
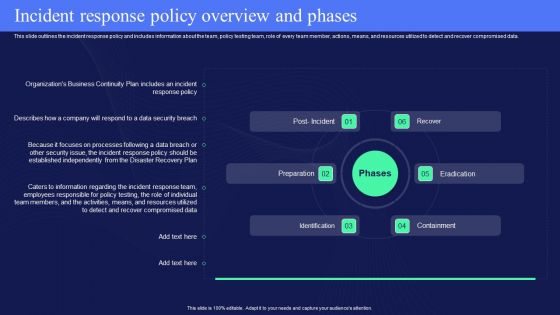
IT Policies And Procedures Incident Response Policy Overview And Phases Portrait PDF
This slide outlines the incident response policy and includes information about the team, policy testing team, role of every team member, actions, means, and resources utilized to detect and recover compromised data. Make sure to capture your audiences attention in your business displays with our gratis customizable IT Policies And Procedures Incident Response Policy Overview And Phases Portrait PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cyber Risks And Incident Response Playbook Meet Are Awesome Team Rules PDF
Are you searching for a Cyber Risks And Incident Response Playbook Meet Are Awesome Team Rules PDF that is uncluttered, straightforward, and original. Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cyber Risks And Incident Response Playbook Meet Are Awesome Team Rules PDFfrom Slidegeeks today.
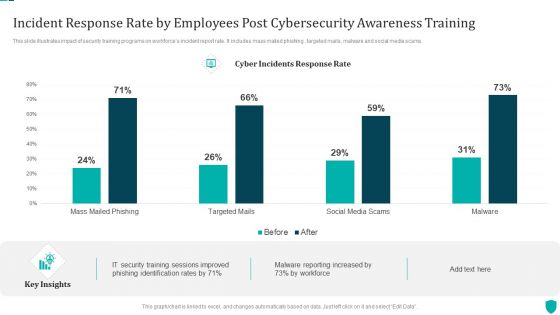
Incident Response Rate By Employees Post Cybersecurity Awareness Training Demonstration PDF
This slide illustrates impact of security training programs on workforces incident report rate. It includes mass mailed phishing , targeted mails, malware and social media scams.Pitch your topic with ease and precision using this Incident Response Rate By Employees Post Cybersecurity Awareness Training Demonstration PDF. This layout presents information on Training Sessions, Phishing Identification, Malware Reporting. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Seven Steps Of Incident Response Digital Risk Assessment Cycle Ppt Portfolio Introduction PDF
The following slide highlights the sevens steps of incident cyber security cycle illustrating detection, communication channel, impact assessment, communication, escalation, delegation and resolution, Persuade your audience using this Seven Steps Of Incident Response Digital Risk Assessment Cycle Ppt Portfolio Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Resolution, Detection, Communication Channels, Impact Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Threats Response Playbook Identifying The Origin And Type Of Cyber Incident Rules PDF
Following slide portrays information about the cyber incident source of origin, their description and type. Members can use this slide to effectively identify the source and type of any cyber attack.This is a IT Threats Response Playbook Identifying The Origin And Type Of Cyber Incident Rules PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like External Removable, Malicious Attachment, Loss Valuable. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
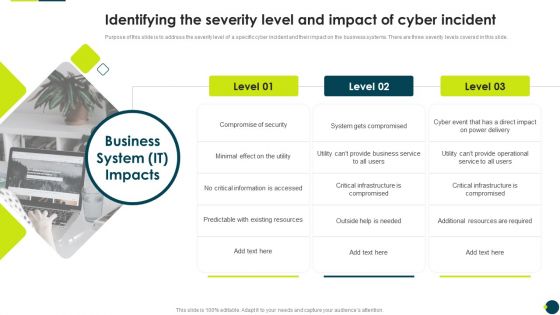
IT Threats Response Playbook Identifying The Severity Level And Impact Of Cyber Incident Portrait PDF
Purpose of this slide is to address the severity level of a specific cyber incident and their impact on the business systems. There are three severity levels covered in this slide.Presenting IT Threats Response Playbook Identifying The Severity Level And Impact Of Cyber Incident Portrait PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Compromise Security, Information Accessed, Existing Resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Safety Breach Response Playbook Addressing The Cyber Incident Logging Process Ideas PDF
This slide displays logging process for a cyber incident logging. It covers information about process ID, procedure, its description and owner details. Make sure to capture your audiences attention in your business displays with our gratis customizable Safety Breach Response Playbook Addressing The Cyber Incident Logging Process Ideas PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

 Home
Home