Incident
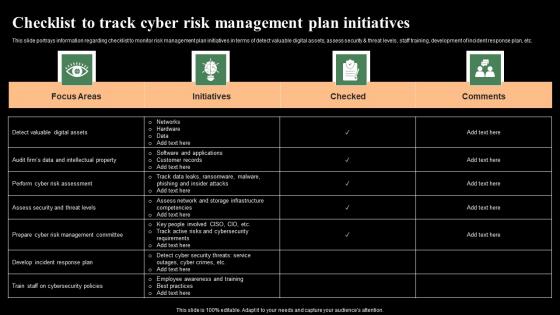
Checklist To Track Cyber Risk Management Plan Initiatives Monitoring Digital Assets Themes Pdf
This slide portrays information regarding checklist to monitor risk management plan initiatives in terms of detect valuable digital assets, assess security and threat levels, staff training, development of incident response plan, etc. Do you know about Slidesgeeks Checklist To Track Cyber Risk Management Plan Initiatives Monitoring Digital Assets Themes Pdf These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
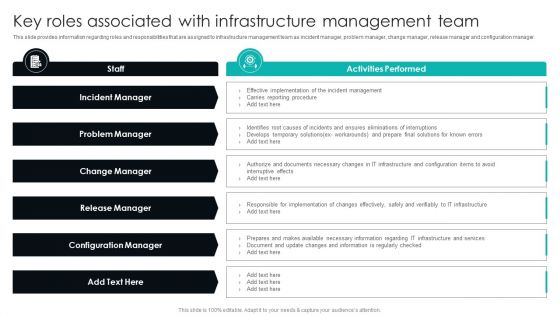
IT Infrastructure Library Procedure Management Playbook Key Roles Associated With Infrastructure Management Team Introduction PDF
This slide provides information regarding roles and responsibilities that are assigned to infrastructure management team as incident manager, problem manager, change manager, release manager and configuration manager. Welcome to our selection of the IT Infrastructure Library Procedure Management Playbook Key Roles Associated With Infrastructure Management Team Introduction PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
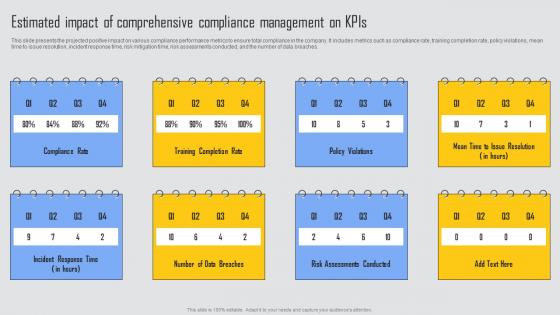
Estimated Impact Of Comprehensive Managing Risks And Establishing Trust Through Efficient Slides Pdf
This slide presents the projected positive impact on various compliance performance metrics to ensure total compliance in the company. It includes metrics such as compliance rate, training completion rate, policy violations, mean time to issue resolution, incident response time, risk mitigation time, risk assessments conducted, and the number of data breaches. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Estimated Impact Of Comprehensive Managing Risks And Establishing Trust Through Efficient Slides Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
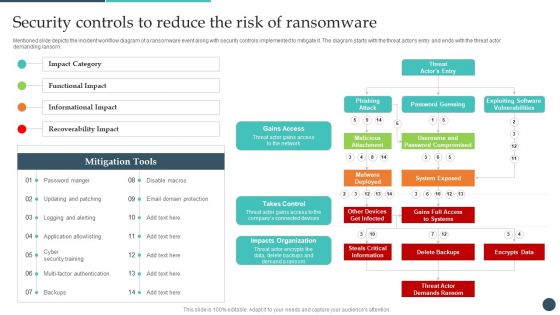
Safety Breach Response Playbook Security Controls To Reduce The Risk Topics PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Presenting this PowerPoint presentation, titled Safety Breach Response Playbook Security Controls To Reduce The Risk Topics PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Safety Breach Response Playbook Security Controls To Reduce The Risk Topics PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Safety Breach Response Playbook Security Controls To Reduce The Risk Topics PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
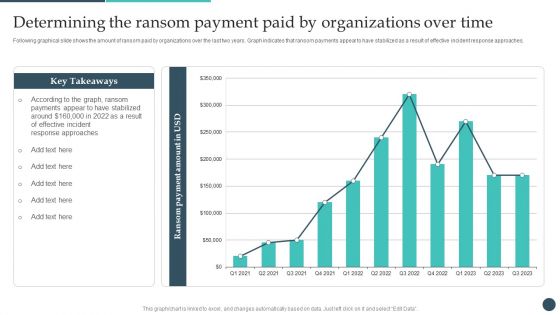
Safety Breach Response Playbook Determining The Ransom Payment Paid Structure PDF
Following graphical slide shows the amount of ransom paid by organizations over the last two years. Graph indicates that ransom payments appear to have stabilized as a result of effective incident response approaches. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Safety Breach Response Playbook Determining The Ransom Payment Paid Structure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
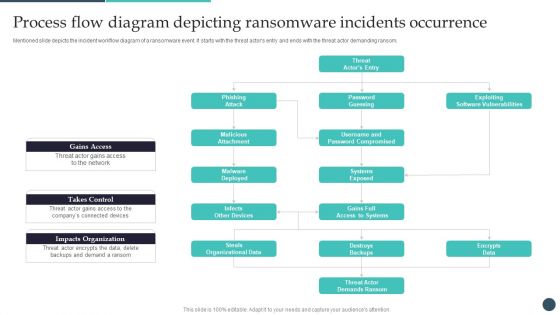
Safety Breach Response Playbook Process Flow Diagram Depicting Ransomware Ideas PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event. It starts with the threat actors entry and ends with the threat actor demanding ransom. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Safety Breach Response Playbook Process Flow Diagram Depicting Ransomware Ideas PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Safety Breach Response Playbook Process Flow Diagram Depicting Ransomware Ideas PDF today and make your presentation stand out from the rest.

CYBER Security Breache Response Strategy Common Sources Of Precursors And Indicators Elements PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CYBER Security Breache Response Strategy Common Sources Of Precursors And Indicators Elements PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Major Techniques For Project Safety IT Determine Project Safety Management Team Structure Pictures PDF
This slide provides information regarding project safety management team generally comprise of senior management personnel that have authority and resources to accelerate IT projects incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting major techniques for project safety it determine project safety management team structure pictures pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like public affair advisor, legal advisor, security manager, crisis management advisor, medical advisor. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Project Security Administration IT Determine Project Safety Management Team Structure Sample PDF
This slide provides information regarding project safety management team generally comprise of senior management personnel that have authority and resources to accelerate IT projects incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a project security administration it determine project safety management team structure sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like public affair advisor, security manager, legal advisor, medical advisor, crisis management advisor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Upgrading Total Project Safety IT Determine Project Safety Management Team Structure Introduction PDF
This slide provides information regarding project safety management team generally comprise of senior management personnel that have authority and resources to accelerate IT projects incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a upgrading total project safety it determine project safety management team structure introduction pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like legal advisor, medical advisor, crisis management advisor, security manager, public affair advisor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
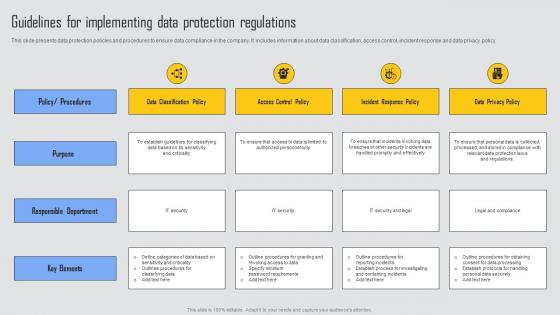
Guidelines For Implementing Managing Risks And Establishing Trust Through Efficient Formats Pdf
This slide presents data protection policies and procedures to ensure data compliance in the company. It includes information about data classification, access control, incident response and data privacy policy. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Guidelines For Implementing Managing Risks And Establishing Trust Through Efficient Formats Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Guidelines For Implementing Managing Risks And Establishing Trust Through Efficient Formats Pdf today and make your presentation stand out from the rest

Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF
This slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Explore a selection of the finest Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Deploying EGIT To Ensure Optimum Risk Management ITIL Service Operation Overview Sample PDF
This slide represents the overview of ITIL service operation, including service monitoring, incident resolution, request fulfillment, operational responsibilities, process, functions, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Deploying EGIT To Ensure Optimum Risk Management ITIL Service Operation Overview Sample PDF can be your best option for delivering a presentation. Represent everything in detail using Deploying EGIT To Ensure Optimum Risk Management ITIL Service Operation Overview Sample PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Assessment Professional PDF
This slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Present like a pro with Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Assessment Professional PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
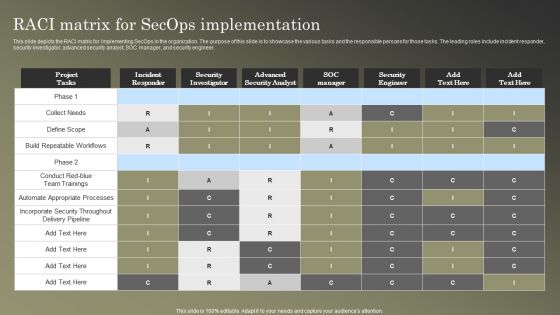
Cybersecurity Operations Cybersecops RAC Matrix For Secops Implementation Inspiration PDF
This slide depicts the RACI matrix for implementing SecOps in the organization. The purpose of this slide is to showcase the various tasks and the responsible persons for those tasks. The leading roles include incident responder, security investigator, advanced security analyst, SOC manager, and security engineer. Present like a pro with Cybersecurity Operations Cybersecops RAC Matrix For Secops Implementation Inspiration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
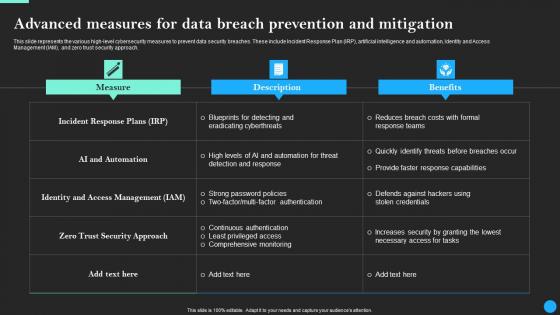
Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Deploying Data Governance Digital Transformation Journey PPT PowerPoint DT SS V
This slide presents strategies for ensuring data governance and compliance in a regulated energy and utilities industry. It includes data governance, access controls, audit trail and reporting, vendor management, regulatory compliance monitoring and data incident response. This modern and well-arranged Deploying Data Governance Digital Transformation Journey PPT PowerPoint DT SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

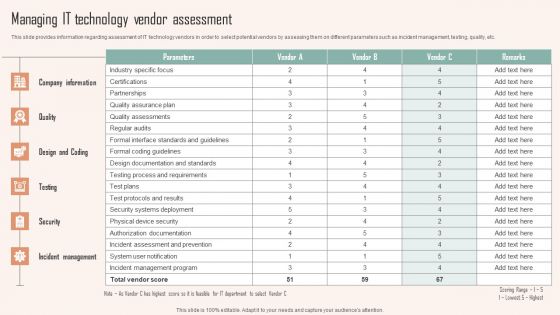
Managing IT Technology Vendor Assessment Microsoft PDF
This slide provides information regarding assessment of IT technology vendors in order to select potential vendors by assessing them on different parameters such as incident management, testing, quality, etc. Explore a selection of the finest Managing IT Technology Vendor Assessment Microsoft PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Managing IT Technology Vendor Assessment Microsoft PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Managing IT Technology Vendor Assessment Formats PDF
This slide provides information regarding assessment of IT technology vendors in order to select potential vendors by assessing them on different parameters such as incident management, testing, quality, etc. Slidegeeks is here to make your presentations a breeze with Managing IT Technology Vendor Assessment Formats PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
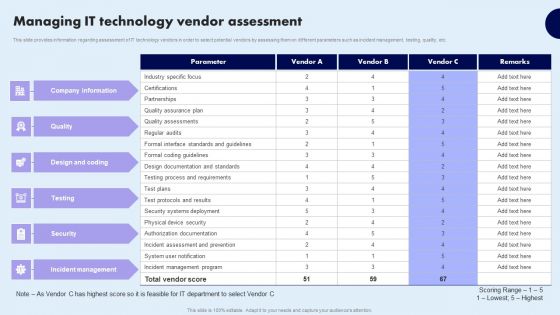
Managing IT Technology Vendor Assessment Summary PDF
This slide provides information regarding assessment of IT technology vendors in order to select potential vendors by assessing them on different parameters such as incident management, testing, quality, etc. Do you know about Slidesgeeks Managing IT Technology Vendor Assessment Summary PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Integrating ITSM To Enhance Service Organizational Framework For Handling Service Desks Introduction PDF
This slide showcases organizational framework for handling service desks. It provides information about end user interaction, incident management, request fulfilment, network management, end user computing, etc. This modern and well-arranged Integrating ITSM To Enhance Service Organizational Framework For Handling Service Desks Introduction PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
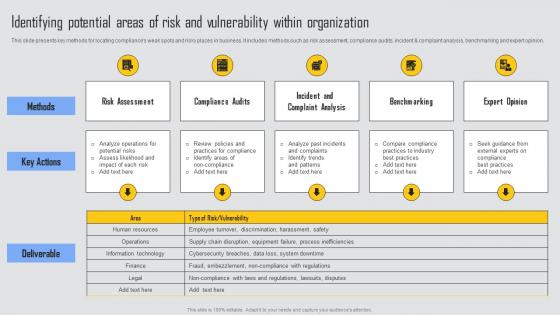
Identifying Potential Areas Risk Managing Risks And Establishing Trust Through Efficient Ideas Pdf
This slide presents key methods for locating compliances weak spots and risky places in business. It includes methods such as risk assessment, compliance audits, incident and complaint analysis, benchmarking and expert opinion. If you are looking for a format to display your unique thoughts, then the professionally designed Identifying Potential Areas Risk Managing Risks And Establishing Trust Through Efficient Ideas Pdf is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Identifying Potential Areas Risk Managing Risks And Establishing Trust Through Efficient Ideas Pdf and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
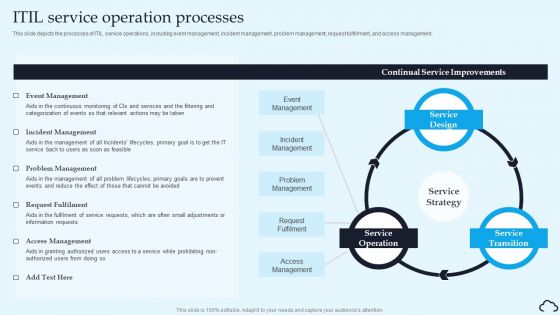
ITIL Service Operation Processes IT Service Management Framework Infographics PDF
This slide depicts the processes of ITIL service operations, including event management, incident management, problem management, request fulfillment, and access management.Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than ITIL Service Operation Processes IT Service Management Framework Infographics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab ITIL Service Operation Processes IT Service Management Framework Infographics PDF today and make your presentation stand out from the rest.
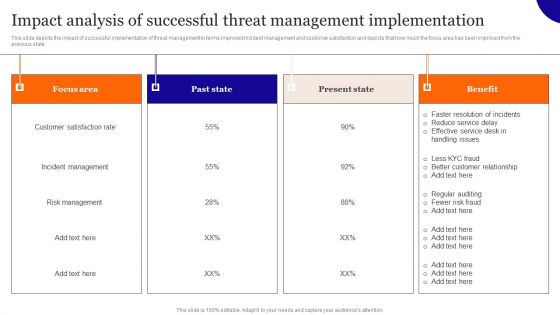
Impact Analysis Of Successful Threat Management Implementation Background PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Impact Analysis Of Successful Threat Management Implementation Background PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Impact Analysis Of Successful Threat Management Implementation Background PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Cyber Supply Chain Risk Management Dashboard Structure PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Supply Chain Risk Management Dashboard Structure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
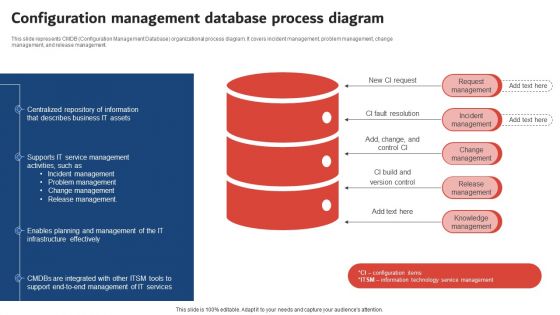
Execution Of ICT Strategic Plan Configuration Management Database Process Diagram Ideas PDF
This slide represents CMDB Configuration Management Database organizational process diagram. It covers incident management, problem management, change management, and release management. Presenting this PowerPoint presentation, titled Execution Of ICT Strategic Plan Configuration Management Database Process Diagram Ideas PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Execution Of ICT Strategic Plan Configuration Management Database Process Diagram Ideas PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Execution Of ICT Strategic Plan Configuration Management Database Process Diagram Ideas PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Providing Vendor Management Solutions To End Customer Ppt Pictures Graphics Template PDF
The vendor management process allows technology solution provider in management of all interactions with end users or clients infrastructure vendors. The service desk will document incident resolution activities conducted by infrastructure vendors by service automation solution. The firm will proactively manage all infrastructure vendor activity. This is a providing vendor management solutions to end customer ppt pictures graphics template pdf template with various stages. Focus and dispense information on fourteen stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like structured cabling vendors, business, location vendors. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Facilities Governance Providing Vendor Management Solutions To End Customer Introduction PDF
The vendor management process allows technology solution provider in management of all interactions with end- users or clients infrastructure vendors. The service desk will document incident resolution activities conducted by infrastructure vendors by service automation solution. The firm will proactively manage all infrastructure vendor activity. This is a information technology facilities governance providing vendor management solutions to end customer introduction pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like business software vendors, application development, cellular service vendors. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
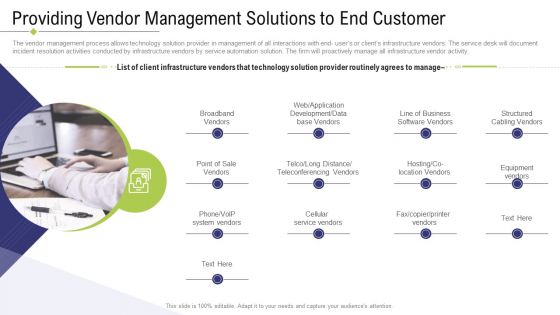
Technology Facility Maintenance And Provider Providing Vendor Management Solutions To End Customer Clipart PDF
The vendor management process allows technology solution provider in management of all interactions with end- users or clients infrastructure vendors. The service desk will document incident resolution activities conducted by infrastructure vendors by service automation solution. The firm will proactively manage all infrastructure vendor activity. This is a technology facility maintenance and provider providing vendor management solutions to end customer clipart pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like business software vendors, structured cabling vendors, development, database vendors. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Providing Vendor Management Solutions To End Customer Ppt Layouts Guidelines PDF
The vendor management process allows technology solution provider in management of all interactions with end users or clients infrastructure vendors. The service desk will document incident resolution activities conducted by infrastructure vendors by service automation solution. The firm will proactively manage all infrastructure vendor activity. This is a providing vendor management solutions to end customer ppt layouts guidelines pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like equipment vendors, location vendors, structured cabling vendors. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Building An IT Strategy Plan For Business Expansion Managing IT Technology Vendor Assessment Sample PDF
This slide provides information regarding assessment of IT technology vendors in order to select potential vendors by assessing them on different parameters such as incident management, testing, quality, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Building An IT Strategy Plan For Business Expansion Managing IT Technology Vendor Assessment Sample PDF can be your best option for delivering a presentation. Represent everything in detail using Building An IT Strategy Plan For Business Expansion Managing IT Technology Vendor Assessment Sample PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
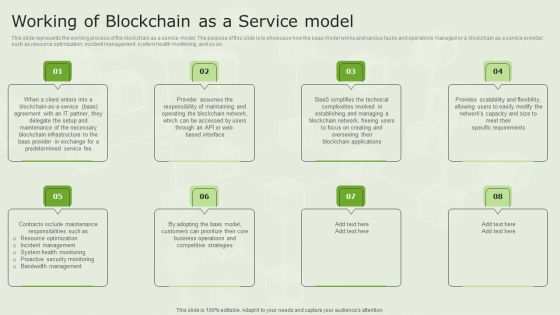
Managed Blockchain Service Working Of Blockchain As A Service Model Brochure PDF
This slide represents the working process of the blockchain as a service model. The purpose of this slide is to showcase how the baas model works and various tasks and operations managed by a blockchain as a service provider, such as resource optimization, incident management, system health monitoring, and so on. Retrieve professionally designed Managed Blockchain Service Working Of Blockchain As A Service Model Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Deploying Corporate Aligned IT Strategy Managing IT Technology Vendor Assessment Demonstration PDF
This slide provides information regarding assessment of IT technology vendors in order to select potential vendors by assessing them on different parameters such as incident management, testing, quality, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Deploying Corporate Aligned IT Strategy Managing IT Technology Vendor Assessment Demonstration PDF can be your best option for delivering a presentation. Represent everything in detail using Deploying Corporate Aligned IT Strategy Managing IT Technology Vendor Assessment Demonstration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Enhancing Information Technology With Strategic Managing IT Technology Vendor Professional PDF
This slide provides information regarding assessment of IT technology vendors in order to select potential vendors by assessing them on different parameters such as incident management, testing, quality, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Enhancing Information Technology With Strategic Managing IT Technology Vendor Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Enhancing Information Technology With Strategic Managing IT Technology Vendor Professional PDF today and make your presentation stand out from the rest.
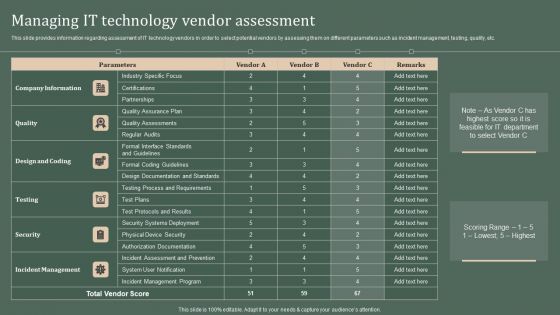
Managing IT Technology Vendor Assessment Ppt PowerPoint Presentation File Ideas PDF
This slide provides information regarding assessment of IT technology vendors in order to select potential vendors by assessing them on different parameters such as incident management, testing, quality, etc. This Managing IT Technology Vendor Assessment Ppt PowerPoint Presentation File Ideas PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Chief Information Officers Guide On Technology Plan Managing IT Technology Vendor Rules PDF
This slide provides information regarding assessment of IT technology vendors in order to select potential vendors by assessing them on different parameters such as incident management, testing, quality, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Chief Information Officers Guide On Technology Plan Managing IT Technology Vendor Rules PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
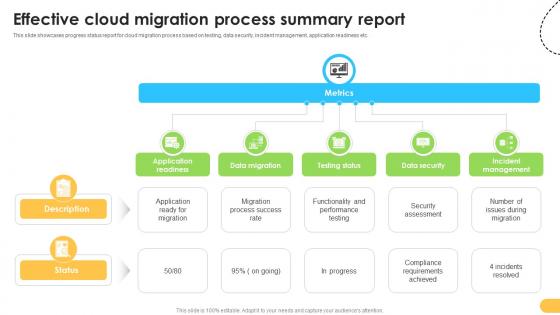
Effective Cloud Migration Process Summary Report Data Migration From On Premises
This slide showcases progress status report for cloud migration process based on testing, data security, incident management, application readiness etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Effective Cloud Migration Process Summary Report Data Migration From On Premises and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
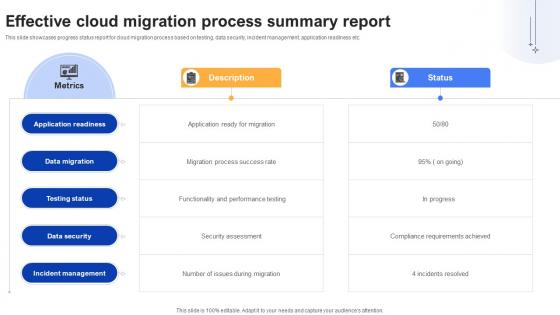
Effective Data Migration Effective Cloud Migration Process Summary Report
This slide showcases progress status report for cloud migration process based on testing, data security, incident management, application readiness etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Effective Data Migration Effective Cloud Migration Process Summary Report and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF
This slide describes the overview of the command security operations center, including its advantages and disadvantages. The purpose of this slide is to demonstrate the pros, cons and main responsibilities of command SOC. The main tasks include monitoring and analyzing security events, coordinating incident response, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF
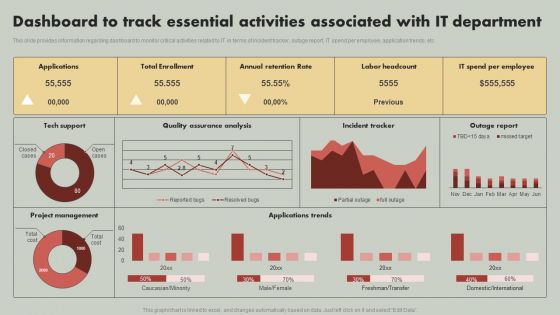
IT Reducing Costs And Management Tips Dashboard To Track Essential Activities Associated With IT Department Summary PDF
This slide provides information regarding dashboard to monitor critical activities related to IT in terms of incident tracker, outage report, IT spend per employee, application trends, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download IT Reducing Costs And Management Tips Dashboard To Track Essential Activities Associated With IT Department Summary PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Developing IT Security Strategy Mitigation Strategies To Avoid Information Breach Sample PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Developing IT Security Strategy Mitigation Strategies To Avoid Information Breach Sample PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
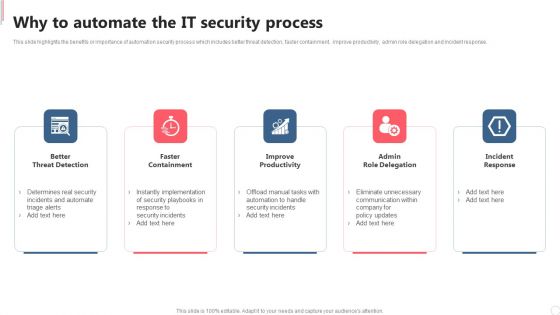
Cyber Security Automation Framework Why To Automate The IT Security Process Graphics PDF
This slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Slidegeeks is here to make your presentations a breeze with Cyber Security Automation Framework Why To Automate The IT Security Process Graphics PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

IT Security Automation Systems Guide Why To Automate The IT Security Process Pictures PDF
This slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created IT Security Automation Systems Guide Why To Automate The IT Security Process Pictures PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

ICT Governance ITIL Service Operation Overview Ppt PowerPoint Presentation Gallery Ideas PDF
This slide represents the overview of ITIL service operation, including service monitoring, incident resolution, request fulfillment, operational responsibilities, process, functions, and so on. Do you know about Slidesgeeks ICT Governance ITIL Service Operation Overview Ppt PowerPoint Presentation Gallery Ideas PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Security Automation To Analyze And Mitigate Cyberthreats Why To Automate The It Security Process Summary PDF
This slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response.Are you searching for a Security Automation To Analyze And Mitigate Cyberthreats Why To Automate The It Security Process Summary PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Automation To Analyze And Mitigate Cyberthreats Why To Automate The It Security Process Summary PDF from Slidegeeks today.

Determining The Ransom Payment Paid By Organizations Over Time Information PDF
Following graphical slide shows the amount of ransom paid by organizations over the last two years. Graph indicates that ransom payments appear to have stabilized as a result of effective incident response approaches.If you are looking for a format to display your unique thoughts, then the professionally designed Determining The Ransom Payment Paid By Organizations Over Time Information PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Determining The Ransom Payment Paid By Organizations Over Time Information PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
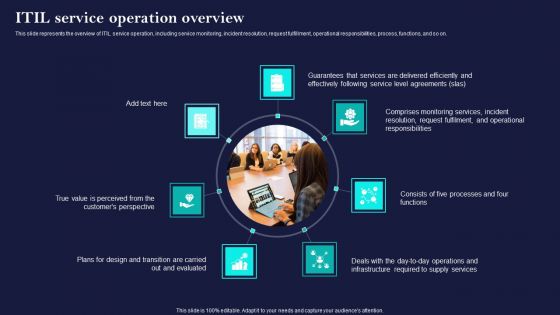
Corporate Governance Of ICT ITIL Service Operation Overview Rules PDF
This slide represents the overview of ITIL service operation, including service monitoring, incident resolution, request fulfillment, operational responsibilities, process, functions, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Corporate Governance Of ICT ITIL Service Operation Overview Rules PDF can be your best option for delivering a presentation. Represent everything in detail using Corporate Governance Of ICT ITIL Service Operation Overview Rules PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF
This slide describes the critical functions of security operations. The purpose of this slide is to demonstrate the various functions performed by SecOps teams in an organization. The main functions include threat intelligence, security monitoring, incident response, forensics and root cause analysis, etc. Boost your pitch with our creative Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
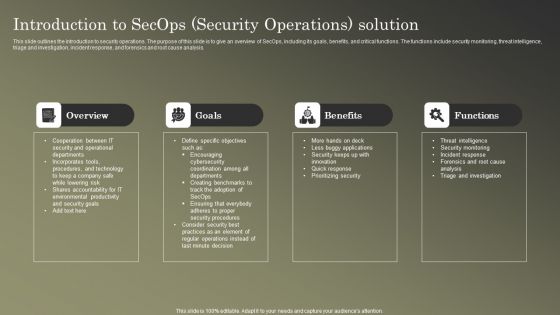
Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF
This slide outlines the introduction to security operations. The purpose of this slide is to give an overview of SecOps, including its goals, benefits, and critical functions. The functions include security monitoring, threat intelligence, triage and investigation, incident response, and forensics and root cause analysis. Want to ace your presentation in front of a live audience Our Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Best Practices For Improving Role Serverless Computing Modern Technology Infographics Pdf
The purpose of this slide is to discuss the best practices to enhance the security of serverless applications. These are safeguard critical data, add an incident response strategy, use appropriate security logging and dependence on external parties. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Best Practices For Improving Role Serverless Computing Modern Technology Infographics Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Best Practices For Improving Role Serverless Computing Modern Technology Infographics Pdf that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
Information Technology Infrastructure Library Service Lifecycle Ppt Infographics Icon PDF
This slide talks about the service lifecycle of ITIL and it includes service design, service operations, service transition, change management, service strategy, knowledge management, availability management, service level management, incident management, and so on. If you are looking for a format to display your unique thoughts, then the professionally designed Information Technology Infrastructure Library Service Lifecycle Ppt Infographics Icon PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Information Technology Infrastructure Library Service Lifecycle Ppt Infographics Icon PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
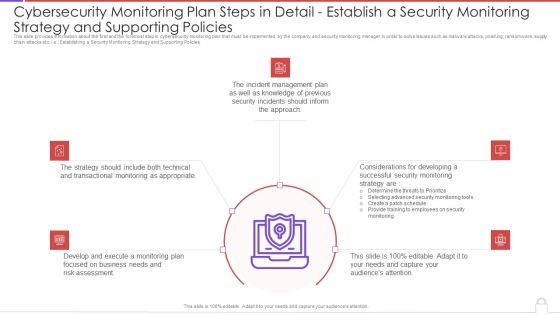
Cybersecurity Monitoring Plan Steps In Detail Establish A Security Monitoring Strategy And Pictures PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Establishing a Security Monitoring Strategy and Supporting Policies. This is a cybersecurity monitoring plan steps in detail establish a security monitoring strategy and pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident management, transactional monitoring, monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Integrating ITSM To Enhance Service Training Program For Service Desk Teams Themes PDF
This slide showcases training program for service desk department. It provides information about activities, trainer, time, outcomes, incident management, request management, implementation plan, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Integrating ITSM To Enhance Service Training Program For Service Desk Teams Themes PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Organizational Framework For Handling Service Desks Ppt PowerPoint Presentation File Example PDF
This slide showcases organizational framework for handling service desks. It provides information about end user interaction, incident management, request fulfilment, network management, end user computing, etc. This modern and well arranged Organizational Framework For Handling Service Desks Ppt PowerPoint Presentation File Example PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
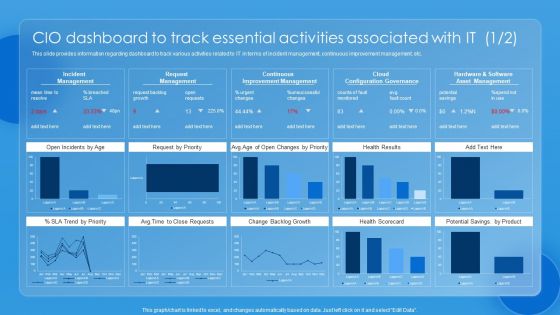
Key CIO Initiatives CIO Dashboard To Track Essential Activities Associated With IT Portrait PDF
This slide provides information regarding dashboard to track various activities related to IT in terms of incident management, continuous improvement management, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Key CIO Initiatives CIO Dashboard To Track Essential Activities Associated With IT Portrait PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Key CIO Initiatives CIO Dashboard To Track Essential Activities Associated With IT Portrait PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Implementing Advanced Service Help Desk Administration Program Organizational Framework For Handling Service Desks Topics PDF
This slide showcases organizational framework for handling service desks. It provides information about end user interaction, incident management, request fulfilment, network management, end user computing, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Implementing Advanced Service Help Desk Administration Program Organizational Framework For Handling Service Desks Topics PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
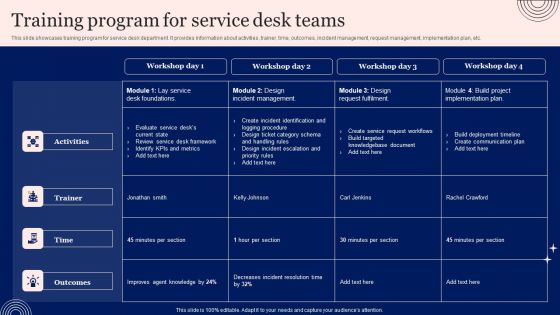
Implementing Advanced Service Help Desk Administration Program Training Program For Service Desk Teams Microsoft PDF
This slide showcases training program for service desk department. It provides information about activities, trainer, time, outcomes, incident management, request management, implementation plan, etc. This Implementing Advanced Service Help Desk Administration Program Training Program For Service Desk Teams Microsoft PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing Advanced Service Help Desk Administration Program Training Program For Service Desk Teams Microsoft PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today
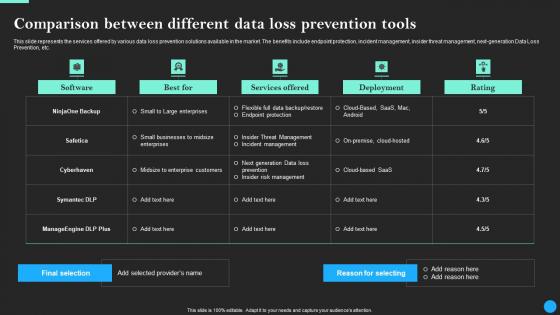
Comparison Between Different Data Loss Prevention Data Breach Prevention Themes Pdf
This slide represents the services offered by various data loss prevention solutions available in the market. The benefits include endpoint protection, incident management, insider threat management, next-generation Data Loss Prevention, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Comparison Between Different Data Loss Prevention Data Breach Prevention Themes Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Comparison Between Different Data Loss Prevention Data Breach Prevention Themes Pdf today and make your presentation stand out from the rest

Comparison Between Different Data Loss Prevention Tools Data Fortification Strengthening Defenses
This slide represents the services offered by various data loss prevention solutions available in the market. The benefits include endpoint protection, incident management, insider threat management, next-generation Data Loss Prevention, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Comparison Between Different Data Loss Prevention Tools Data Fortification Strengthening Defenses. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Comparison Between Different Data Loss Prevention Tools Data Fortification Strengthening Defenses today and make your presentation stand out from the rest

 Home
Home