Identity Access Management
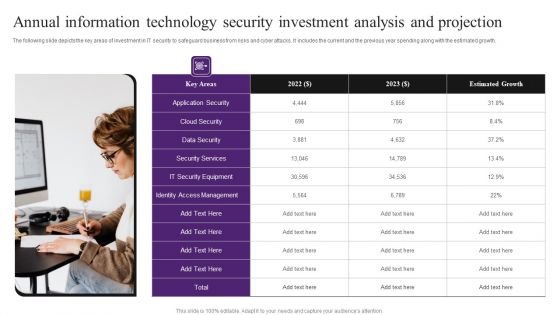
Annual Information Technology Security Investment Analysis And Projection Portrait PDF
The following slide depicts the key areas of investment in IT security to safeguard business from risks and cyber attacks. It includes the current and the previous year spending along with the estimated growth. Presenting Annual Information Technology Security Investment Analysis And Projection Portrait PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Cloud Security, Security Services, Identity Access Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
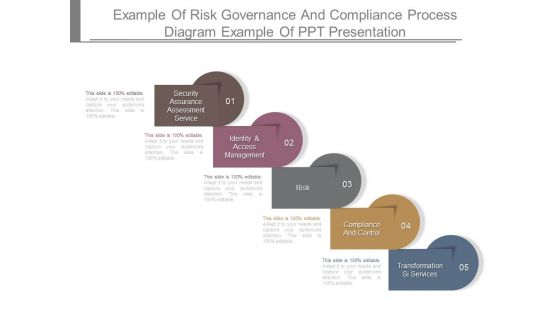
Example Of Risk Governance And Compliance Process Diagram Example Of Ppt Presentation
This is a example of risk governance and compliance process diagram example of ppt presentation. This is a five stage process. The stages in this process are security assurance assessment service, identity and access management, risk, compliance and control, transformation si services.
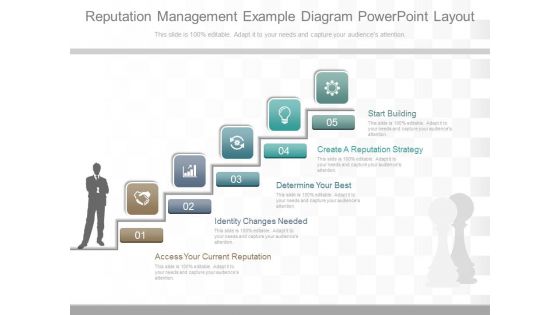
Reputation Management Example Diagram Powerpoint Layout
This is a reputation management example diagram powerpoint layout. This is a five stage process. The stages in this process are start building, create a reputation strategy, determine your best, identity changes needed, access your current reputation.

ITIL Authorization Management Industry Process Slides Pdf
This slide showcase the process of ITIL access management which ensures that workers have required level of access to complete job effectively. It include pointer such as requesting access, verification, providing rights, monitoring identity status and tracking access. Pitch your topic with ease and precision using this ITIL Authorization Management Industry Process Slides Pdf This layout presents information on Requesting Access, Verification, Providing Rights It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
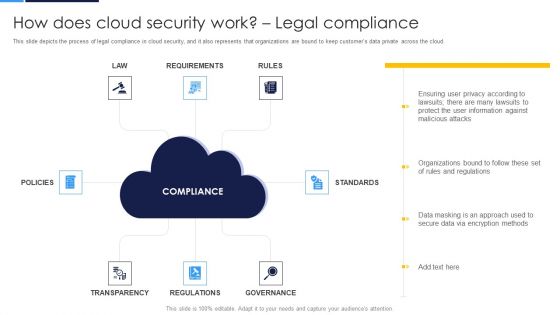
Cloud Security Assessment How Does Cloud Security Work Legal Compliance Microsoft PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository.Deliver an awe inspiring pitch with this creative Cloud Security Assessment How Does Cloud Security Work Legal Compliance Microsoft PDF bundle. Topics like Provide Limited, Personnel To Protect, Authentication Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
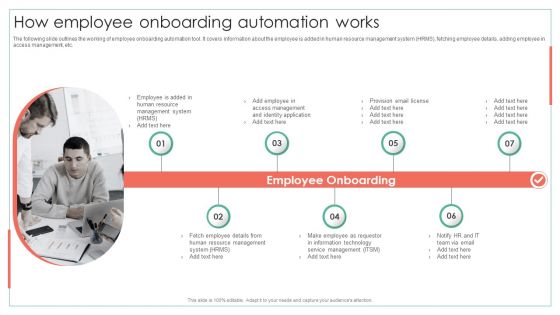
How Employee Onboarding Automation Works Achieving Operational Efficiency Slides PDF
The following slide outlines the working of employee onboarding automation tool. It covers information about the employee is added in human resource management system HRMS, fetching employee details, adding employee in access management, etc. This is a How Employee Onboarding Automation Works Achieving Operational Efficiency Slides PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management System, Identity Application, Access Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
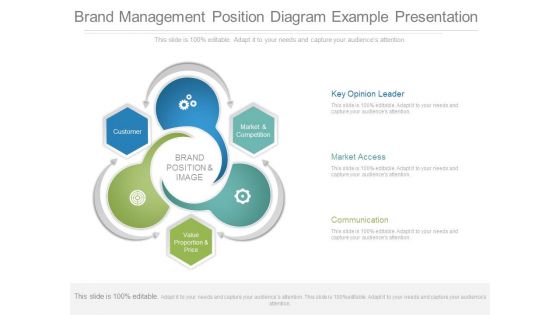
Brand Management Position Diagram Example Presentation
This is a brand management position diagram example presentation. This is a three stage process. The stages in this process are brand position and image, customer, value proportion and price, market and competition, key opinion leader, market access, communication.
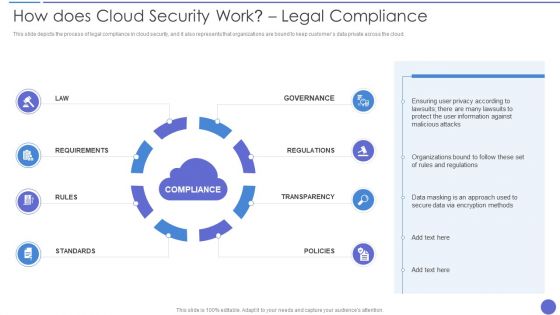
How Does Cloud Security Work Legal Compliance Background PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting How Does Cloud Security Work Legal Compliance Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Authorization, Authentication, Access Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
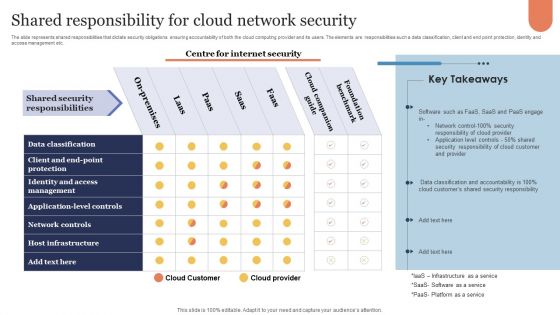
Shared Responsibility For Cloud Network Security Microsoft PDF
The slide represents shared responsibilities that dictate security obligations ensuring accountability of both the cloud computing provider and its users. The elements are responsibilities such a data classification, client and end point protection, identity and access management etc. Showcasing this set of slides titled Shared Responsibility For Cloud Network Security Microsoft PDF. The topics addressed in these templates are Cloud Companion Guide, Foundation Benchmark, On Premises. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
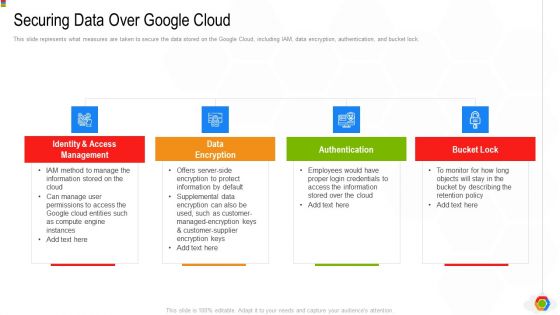
Google Cloud Console IT Securing Data Over Google Cloud Ppt Pictures Slides PDF
This slide represents what measures are taken to secure the data stored on the Google Cloud, including IAM, data encryption, authentication, and bucket lock. This is a google cloud console it securing data over google cloud ppt pictures slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identity and access management, data encryption, authentication, bucket lock. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf
This slide talks about the cloud access control methods. The purpose of this slide is to briefly explain cloud access control techniques such as Identity and Access Management IAM, Multi Factor Authentication MFA, Role based access control RBAC, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab About Cryptography Techniques Cloud Data Security Using Cryptography Background Pdf today and make your presentation stand out from the rest

Overview Of Zero Trust Solution Categories Background PDF
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Boost your pitch with our creative Overview Of Zero Trust Solution Categories Background PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Overview Of Zero Trust Solution Categories Zero Trust Network Security Microsoft Pdf
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks has constructed Overview Of Zero Trust Solution Categories Zero Trust Network Security Microsoft Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Zero Trust Model Overview Of Zero Trust Solution Categories
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and access management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. This Zero Trust Model Overview Of Zero Trust Solution Categories from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
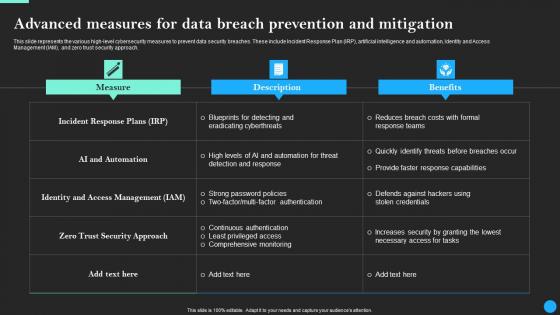
Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention Data Breach Prevention Inspiration Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses
This slide represents the various high-level cybersecurity measures to prevent data security breaches. These include Incident Response Plan IRP, artificial intelligence and automation, Identity and Access Management IAM, and zero trust security approach.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Advanced Measures For Data Breach Prevention And Mitigation Data Fortification Strengthening Defenses for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Integration Of Paas Services And Processes Of Paas Cloud Framework Brochure PDF
This slide represents the services and processes of the PaaS cloud framework. It includes identity and access management, accounting, lifecycle management, monitoring, data virtualization, information analysis, data transformation, integration service, and so on. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Integration Of Paas Services And Processes Of Paas Cloud Framework Brochure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Integration Of Paas Services And Processes Of Paas Cloud Framework Brochure PDF.
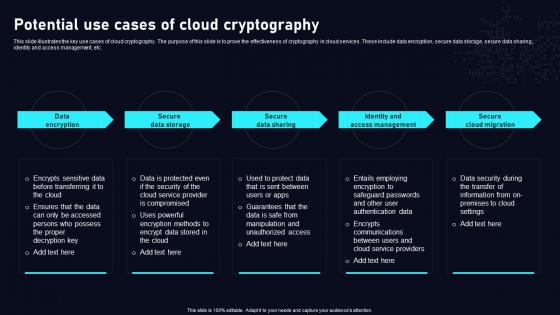
Potential Use Cases Of Cloud Cryptography Cloud Data Security Using Cryptography Information Pdf
This slide illustrates the key use cases of cloud cryptography. The purpose of this slide is to prove the effectiveness of cryptography in cloud services. These include data encryption, secure data storage, secure data sharing, identity and access management, etc. Present like a pro with Potential Use Cases Of Cloud Cryptography Cloud Data Security Using Cryptography Information Pdf Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Potential Use Cases Of Cloud Data Security In Cloud Computing Ppt Sample
This slide illustrates the key use cases of cloud cryptography. The purpose of this slide is to prove the effectiveness of cryptography in cloud services. These include data encryption, secure data storage, secure data sharing, identity and access management, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Potential Use Cases Of Cloud Data Security In Cloud Computing Ppt Sample for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Strategic IT Initiatives With Key Priorities Diagrams PDF
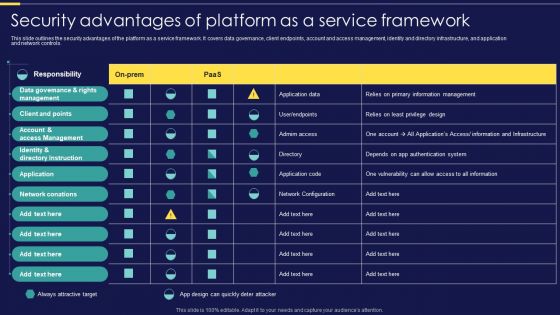
Integration Of Paas Security Advantages Of Platform As A Service Framework Elements PDF
This slide outlines the security advantages of the platform as a service framework. It covers data governance, client endpoints, account and access management, identity and directory infrastructure, and application and network controls. Make sure to capture your audiences attention in your business displays with our gratis customizable Integration Of Paas Security Advantages Of Platform As A Service Framework Elements PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Information Technology Compliance Procedure Checklist Icons PDF
This slide presents information technology checklist, helpful in defining key tasks to be accomplished for successful completion of compliance process and management. It includes Access and identity control, incident response, disaster recovery, data loss prevention and protection against malware Showcasing this set of slides titled Information Technology Compliance Procedure Checklist Icons PDF. The topics addressed in these templates are Key Elements, Activities Accomplished, Status. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Overview Of Zero Trust Solution Categories Software Defined Perimeter SDP
This slide represents the overview of zero-trust solution categories, including MFA, SSO, identity and acce ss management, zero-trust network access and secure access service edge. The purpose of this slide is to give an overview of zero-trust technologies and their benefits. Slidegeeks has constructed Overview Of Zero Trust Solution Categories Software Defined Perimeter SDP after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
Reverse Proxy Server IT Anonymous Proxy Server And Its Architecture Ppt Infographic Template Icon PDF
The following slide showcases the anonymous proxy server, how it hides the users identity and how it helps users access the restricted data by avoiding firewall settings. Deliver an awe inspiring pitch with this creative reverse proxy server it anonymous proxy server and its architecture ppt infographic template icon pdf bundle. Topics like proxy server, access restricted recreational, pornographic can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Solution Roadmap Auditing And Reporting Ppt PowerPoint Presentation Portfolio Styles PDF
Pitch your topic with ease and precision using this solution roadmap auditing and reporting ppt powerpoint presentation portfolio styles pdf. This layout presents information on access management, provisioning process automation, auditing and reporting, program mgmt governance, enterprise identity management idm foundation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Reverse Proxy Web Server Anonymous Proxy Server And Its Architecture Icons PDF
The following slide showcases the anonymous proxy server, how it hides the users identity and how it helps users access the restricted data by avoiding firewall settings. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Reverse Proxy Web Server Anonymous Proxy Server And Its Architecture Icons PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Online Security Expert Certification System Ppt PowerPoint Presentation Professional Themes PDF
Presenting this set of slides with name online security expert certification system ppt powerpoint presentation professional themes pdf. This is a ten stage process. The stages in this process are social network program, information security program, online trading security program, web protection program, unauthorized access protection program, virus protection program, password security program, wireless security program, identity protection program, spyware protection program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

How Employee Onboarding Automation Works Sample PDF
The following slide outlines the working of employee onboarding automation tool. It covers information about the employee is added in human resource management system HRMS, fetching employee details, adding employee in access management, etc. Presenting How Employee Onboarding Automation Works Sample PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Human Resource, Management System, Identity Application, Information Technology Service. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Example Of Information Technology Environment Sample Diagram Powerpoint Slides
This is a example of information technology environment sample diagram powerpoint slides. This is a seven stage process. The stages in this process are identity lifecycle, password, requests, access, modify, disable, retire, provision.

Other ZTNA Architecture Deployment Approaches Formats PDF
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Find a pre-designed and impeccable Other ZTNA Architecture Deployment Approaches Formats PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Key Initiatives For Iam App Onboarding Success Inspiration PDF
This slide shows initiatives for IAM application onboarding success to ensure every identity has access to right resources. It includes steps such as application migration factory, business experienced stakeholders, communicate with application owners, and application requirements guidelines. Persuade your audience using this Key Initiatives For Iam App Onboarding Success Inspiration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Application Migration Factory, Business Experienced Stakeholders, Application Requirements Guidelines. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Talent Retention Initiatives For New Hire Onboarding Tools And Technologies For Automating Summary PDF
This slide presents various solutions and systems for digitizing the employee onboarding experience. It includes information about tools such as learning management systems, digital adaptation platforms, identity verification and authentication, and chatbots. Retrieve professionally designed Talent Retention Initiatives For New Hire Onboarding Tools And Technologies For Automating Summary PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Comprehensive Look At Blockchain Using Smart Contracts For Authentication BCT SS V
This slide highlights the concept of smart contracts used for cybersecurity authentication and its use cases. It includes access control in shared spaces, identity verification, supply chain authentication and medical record access. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Comprehensive Look At Blockchain Using Smart Contracts For Authentication BCT SS V was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Comprehensive Look At Blockchain Using Smart Contracts For Authentication BCT SS V

Visionary Guide To Blockchain Using Smart Contracts For Authentication BCT SS V
This slide highlights the concept of smart contracts used for cybersecurity authentication and its use cases. It includes access control in shared spaces, identity verification, supply chain authentication and medical record access. This Visionary Guide To Blockchain Using Smart Contracts For Authentication BCT SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Visionary Guide To Blockchain Using Smart Contracts For Authentication BCT SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
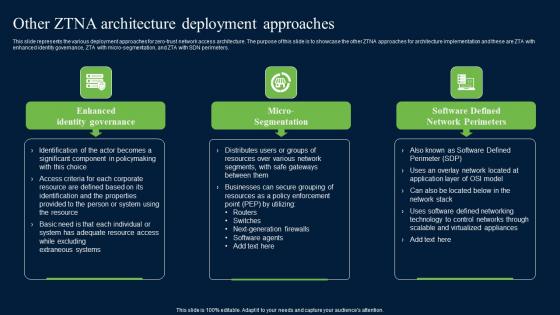
Other ZTNA Architecture Deployment Approaches Zero Trust Network Security Introduction Pdf
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Retrieve professionally designed Other ZTNA Architecture Deployment Approaches Zero Trust Network Security Introduction Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
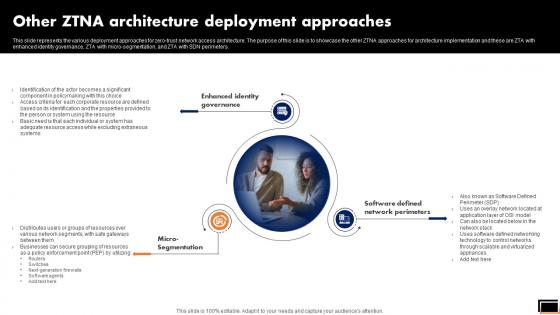
Other Ztna Architecture Deployment Approaches Software Defined Perimeter SDP
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Retrieve professionally designed Other Ztna Architecture Deployment Approaches Software Defined Perimeter SDP to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Zero Trust Model Other ZTNA Architecture Deployment Approaches
This slide represents the various deployment approaches for zero-trust network access architecture. The purpose of this slide is to showcase the other ZTNA approaches for architecture implementation and these are ZTA with enhanced identity governance, ZTA with micro-segmentation, and ZTA with SDN perimeters. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Zero Trust Model Other ZTNA Architecture Deployment Approaches to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Zero Trust Model Other ZTNA Architecture Deployment Approaches.

Environment And Data Security For Devsecops Process Role Of Devsecops Ppt Example
This slide discusses the environment and data security for DevSecOps. The purpose of this slide is to highlight the process, including standardizing and automating the environment, centralizing user identity and access control, isolating containers for security, and so on. The Environment And Data Security For Devsecops Process Role Of Devsecops Ppt Example is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
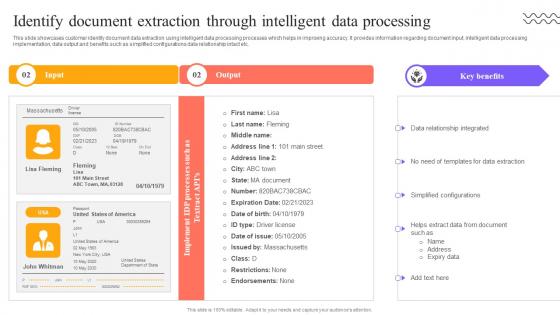
Digital Approach To Client Identify Document Extraction Through Intelligent Data Processing
This slide showcases customer identity document data extraction using intelligent data processing processes which helps in improving accuracy. It provides information regarding document input, intelligent data processing implementation, data output and benefits such as simplified configurations data relationship intact etc. Retrieve professionally designed Digital Approach To Client Identify Document Extraction Through Intelligent Data Processing to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
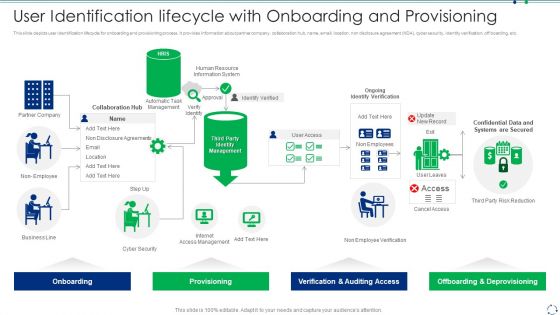
User Identification Lifecycle With Onboarding And Provisioning Introduction PDF
This slide depicts user identification lifecycle for onboarding and provisioning process. It provides information about partner company, collaboration hub, name, email, location, non disclosure agreement NDA cyber security, identity verification, off boarding, etc.Showcasing this set of slides titled user identification lifecycle with onboarding and provisioning introduction pdf The topics addressed in these templates are verification and auditing access, offboarding and deprovisioning, provisioning All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
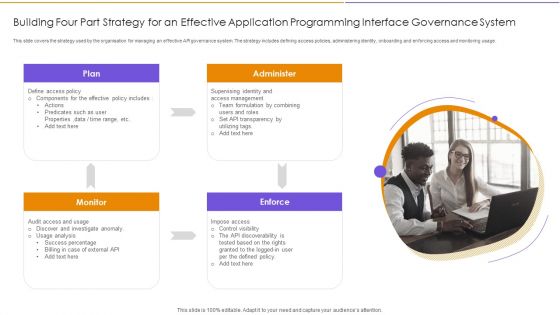
Building Four Part Strategy For An Effective Application Programming Interface Governance System Professional PDF
This slide covers the strategy used by the organisation for managing an effective API governance system. The strategy includes defining access policies, administering identity, onboarding and enforcing access and monitoring usage. Presenting Building Four Part Strategy For An Effective Application Programming Interface Governance System Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Monitor, Plan, Administer. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Various Tips For Improving Business Cloud Protection Diagrams PDF
This slide shows tips which can be used by IT department to enhance the cloud protection of organization. It includes protects used identity, train employees, improve password protection, etc. Presenting Various Tips For Improving Business Cloud Protection Diagrams PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Train Employees, Access Management, Improve Password Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
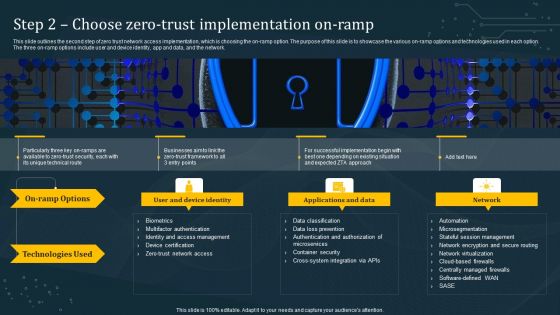
Step 2 Choose Zero Trust Implementation On Ramp Information PDF
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Slidegeeks is here to make your presentations a breeze with Step 2 Choose Zero Trust Implementation On Ramp Information PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
Proportional Symbol In Powerpoint And Google Slides Cpb
Presenting our innovatively-designed set of slides titled Proportional Symbol In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Proportional Symbol that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well-structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.
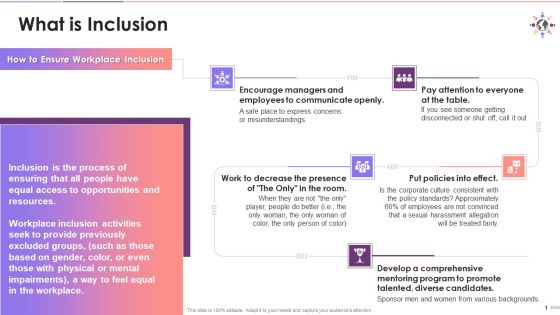
Concept Of Inclusion And Ways To Ensure It In Offices Training Ppt
This slide explains the meaning of Inclusion. It is the process of ensuring that all people have equal access to opportunities and resources. It also mentions strategies to ensure inclusion in the workplace.
Constant Proportionality In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Constant Proportionality In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Constant Proportionality that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Proportionality Constant In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Proportionality Constant In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Proportionality Constant that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Proportional Integral Derivative In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Proportional Integral Derivative In Powerpoint And Google Slides Cpb. This completely editable PowerPoint graphic exhibits Proportional Integral Derivative that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Proportional Hazards Assumption In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Proportional Hazards Assumption In Powerpoint And Google Slides Cpb This completely editable PowerPoint graphic exhibits Proportional Hazards Assumption that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Tools For Facilitating Efficient Trademark Strategy Infographics PDF
This slide showcases instruments which serve as good starting base for facilitating brand strategy. It guides business and includes all elements to make brands identity. It presents information related to functions, prices, case studies, etc. Showcasing this set of slides titled Tools For Facilitating Efficient Trademark Strategy Infographics PDF. The topics addressed in these templates are Instruction Based, Video Led Process, Access Case Studies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Outlining The Cost Brand Building Techniques To Gain Competitive Edge Introduction Pdf
The following slide outlines the budget sheet which will assist the marketing manager to calculate the total cost of brand development. It provides information about the sub costs such as brand identity, market research, logo design, visual style guide, editorial style guide and brand guidelines. Retrieve professionally designed Outlining The Cost Brand Building Techniques To Gain Competitive Edge Introduction Pdf to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Enhancing Digital Visibility Using SEO Content Strategy Quarterly SEO Content Audit Action Plan Microsoft PDF
The following slide highlights quarter wise SEO content audit approaches to optimize site reach. It includes major activities such as developing unique brand identity, drafting and executing strategy, planning administration framework etc. Retrieve professionally designed Enhancing Digital Visibility Using SEO Content Strategy Quarterly SEO Content Audit Action Plan Microsoft PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Step 2 Choose Zero Trust Implementation On Ramp Software Defined Perimeter SDP
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Want to ace your presentation in front of a live audience Our Step 2 Choose Zero Trust Implementation On Ramp Software Defined Perimeter SDP can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
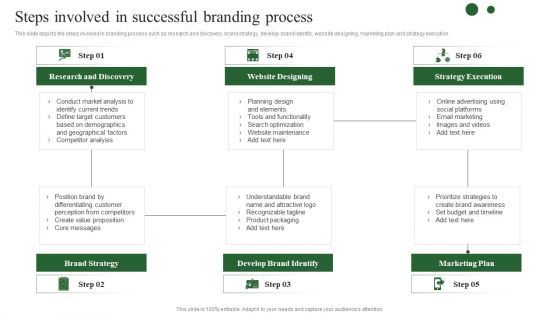
Brand Development Techniques To Increase Revenues Steps Involved In Successful Branding Brochure PDF
This slide depicts the steps involved in branding process such as research and discovery, brand strategy, develop brand identity, website designing, marketing plan and strategy execution. Retrieve professionally designed Brand Development Techniques To Increase Revenues Steps Involved In Successful Branding Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
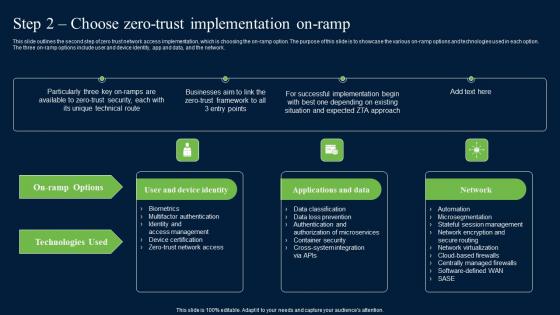
Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Network Security Introduction Pdf
This slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Network Security Introduction Pdf for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Developing The Personal Branding Canvas Comprehensive Personal Brand Building Guide For Social Media Slides PDF
Purpose of this slide is to showcase branding canvas that can be used by a person or an organization to define their personal brand. Elements covered in the canvas are identity, skills, profession, communication, positioning, audience etc.Retrieve professionally designed Developing The Personal Branding Canvas Comprehensive Personal Brand Building Guide For Social Media Slides PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
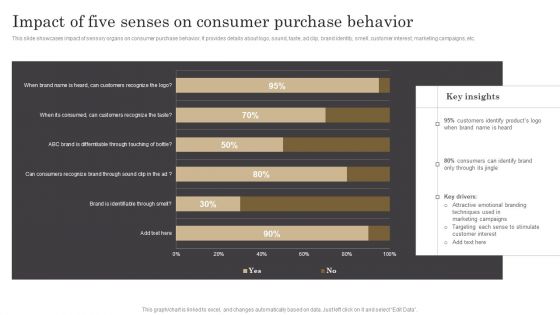
Impact Of Five Senses On Consumer Purchase Behavior Ppt Outline Gridlines PDF
This slide showcases impact of sensory organs on consumer purchase behavior. It provides details about logo, sound, taste, ad clip, brand identity, smell, customer interest, marketing campaigns, etc. Retrieve professionally designed Impact Of Five Senses On Consumer Purchase Behavior Ppt Outline Gridlines PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Elements Of Environmentalsocial And Governance Reporting Ideas PDF
This slide contains the elements which shows the impact and added value of a organization in three areas environment, society and corporate governance. It includes factors like corporate culture,carbon emission, labour management, health and safety etc. Persuade your audience using this Elements Of Environmentalsocial And Governance Reporting Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Laboure Management, Access Communication, Gender Equality. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Objective Of Corporate Communication Strategy Slides PDF
This template covers corporate communication objectives such as increase community awareness, proactively deliver information, provide accessible communication, strengthen relationships, and build company identity. Boost your pitch with our creative Objective Of Corporate Communication Strategy Slides PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Objective Of Corporate Communication Strategy Ppt File Sample PDF
This template covers corporate communication objectives such as increase community awareness, proactively deliver information, provide accessible communication, strengthen relationships, and build company identity. Welcome to our selection of the Objective Of Corporate Communication Strategy Ppt File Sample PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

 Home
Home