Health Safety Dashboard

Global Data Security Industry Report Growth And Future Prospects In The Cybersecurity Industry IR SS V
The slide highlights the future outlook and potential for the cybersecurity industry. The purpose of the slide is to inform stakeholders regarding growth opportunities, creating a compelling case for investment and collaboration. It covers drivers, trends, and the revolutionary impact of the industry. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Global Data Security Industry Report Growth And Future Prospects In The Cybersecurity Industry IR SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Building Trust With IoT Security Edge Computing Role In Securing IoT Data IoT SS V
This slide showcases the significant role of edge computing in enhancing IoT data security and privacy. It include role such as data filtering and processing, localised threat identification, and reduce attack surface. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Building Trust With IoT Security Edge Computing Role In Securing IoT Data IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
Icons Slide For Global Data Security Industry Report IR SS V
Introducing our well designed Icons Slide For Global Data Security Industry Report IR SS V set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
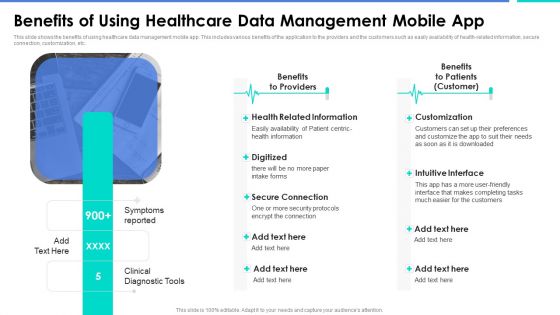
Benefits Of Using Healthcare Data Management Mobile App Demonstration PDF
This slide shows the benefits of using healthcare data management mobile app. This includes various benefits of the application to the providers and the customers such as easily availability of health-related information, secure connection, customization, etc.Deliver an awe inspiring pitch with this creative Benefits Of Using Healthcare Data Management Mobile App Demonstration PDF bundle. Topics like Related Information, Secure Connection, Intuitive Interface can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Factor To Consider While Selecting Cloud Data Migration From On Premises
This slide showcases checklist for evaluating and selecting suitable cloud service provider based on business health, costing, security requirements etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Factor To Consider While Selecting Cloud Data Migration From On Premises to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Global Data Security Industry Report Risk Evaluation Within Cybersecurity Industry IR SS V
The slide depicts risk assessment for the cybersecurity industry. It aims to educate the audience on the need of successfully recognizing and managing risks to maintain the stability. It covers potential hazards associated with data beaches, phishing attacks, malware, regulatory compliance, and IoT security issues. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Global Data Security Industry Report Risk Evaluation Within Cybersecurity Industry IR SS V from Slidegeeks and deliver a wonderful presentation.
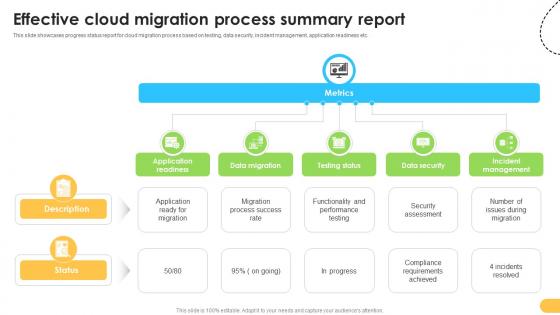
Effective Cloud Migration Process Summary Report Data Migration From On Premises
This slide showcases progress status report for cloud migration process based on testing, data security, incident management, application readiness etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Effective Cloud Migration Process Summary Report Data Migration From On Premises and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Global Data Security Industry Report Exploring Recent Developments In Cybersecurity Industry IR SS V
The slide highlights recent news and developments of major key players in the cybersecurity industry, enabling stakeholders to stay informed and make informed decisions. It covers developments related to acquisitions, collaborations, new product launches, and investments. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Global Data Security Industry Report Exploring Recent Developments In Cybersecurity Industry IR SS V can be your best option for delivering a presentation. Represent everything in detail using Global Data Security Industry Report Exploring Recent Developments In Cybersecurity Industry IR SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V
This slide presents an overview of data centres and its application in storing data , real-time monitoring, analytics and insights, and energy efficiency. It also mentions the components of data centre such as servers, networking infrastructure, storage systems, cooling and HVAC, power distribution, and security measures. If you are looking for a format to display your unique thoughts, then the professionally designed Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Building Data Centers For Effective Digital Transformation Journey PPT Slide DT SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Timeline To Implement Cloud Data Security Using Cryptography Download Pdf
This slide represents the timeline to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Timeline To Implement Cloud Data Security Using Cryptography Download Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Checklist To Implement Cloud Data Security Using Cryptography Brochure Pdf
This slide represents the checklist for integrating cloud cryptography into business. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Checklist To Implement Cloud Data Security Using Cryptography Brochure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
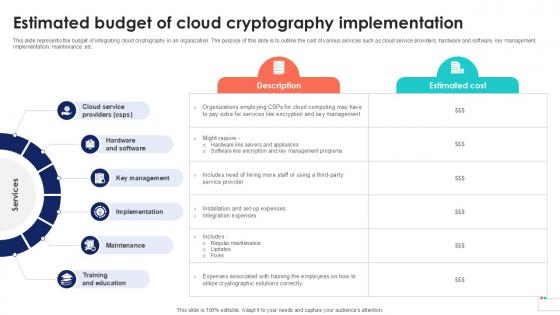
Estimated Budget Of Cloud Cryptography Data Security In Cloud Computing Ppt Slide
This slide represents the budget of integrating cloud cryptography in an organization. The purpose of this slide is to outline the cost of various services such as cloud service providers, hardware and software, key management, implementation, maintenance, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Estimated Budget Of Cloud Cryptography Data Security In Cloud Computing Ppt Slide from Slidegeeks and deliver a wonderful presentation.
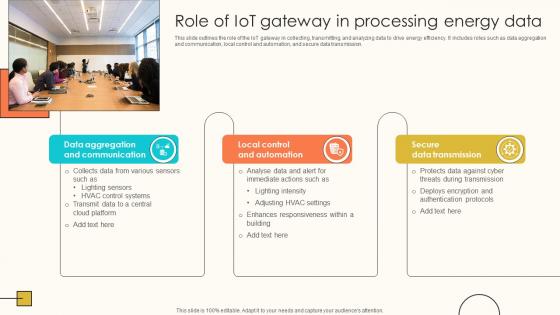
Role Of IoT Gateway In Processing Energy Data Internet Of Things Solutions To Enhance Energy IoT SS V
This slide outlines the role of the IoT gateway in collecting, transmitting, and analyzing data to drive energy efficiency. It includes roles such as data aggregation and communication, local control and automation, and secure data transmission. Do you know about Slidesgeeks Role Of IoT Gateway In Processing Energy Data Internet Of Things Solutions To Enhance Energy IoT SS V These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
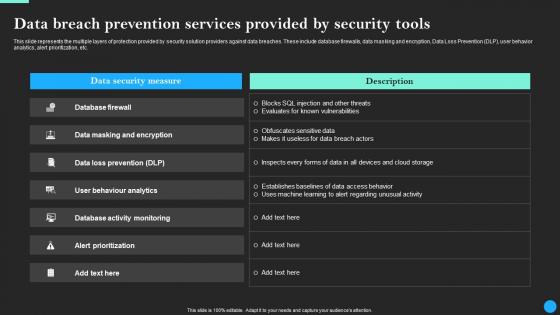
Data Breach Prevention Services Provided Data Breach Prevention Graphics Pdf
This slide represents the multiple layers of protection provided by security solution providers against data breaches. These include database firewalls, data masking and encryption, Data Loss Prevention DLP, user behavior analytics, alert prioritization, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Data Breach Prevention Services Provided Data Breach Prevention Graphics Pdfand observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example
This slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Working Of Common Data Encryption Data Security In Cloud Computing Ppt Example and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
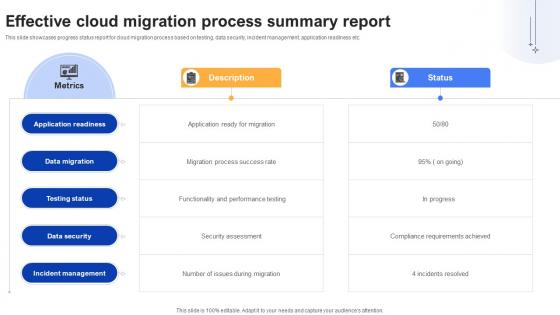
Effective Data Migration Effective Cloud Migration Process Summary Report
This slide showcases progress status report for cloud migration process based on testing, data security, incident management, application readiness etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Effective Data Migration Effective Cloud Migration Process Summary Report and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
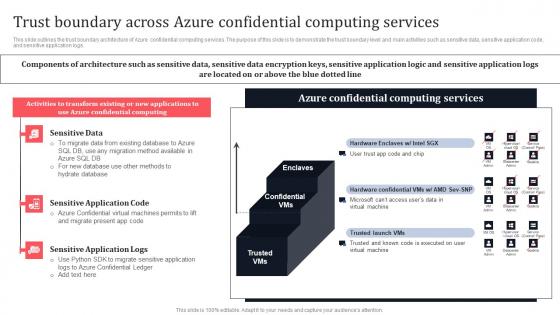
Trust Boundary Across Azure Confidential Computing Services Secure Multi Party Ideas Pdf
This slide outlines the trust boundary architecture of Azure confidential computing services. The purpose of this slide is to demonstrate the trust boundary level and main activities such as sensitive data, sensitive application code, and sensitive application logs. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Trust Boundary Across Azure Confidential Computing Services Secure Multi Party Ideas Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
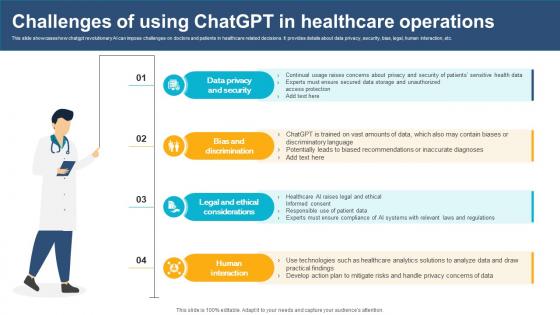
Challenges Of Using ChatGPT In Healthcare Operations ChatGPT And Healthcare Innovation Enhancing AI SS V
This slide showcases how chatgpt revolutionary AI can impose challenges on doctors and patients in healthcare related decisions. It provides details about data privacy, security, bias, legal, human interaction, etc. There are so many reasons you need a Challenges Of Using ChatGPT In Healthcare Operations ChatGPT And Healthcare Innovation Enhancing AI SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
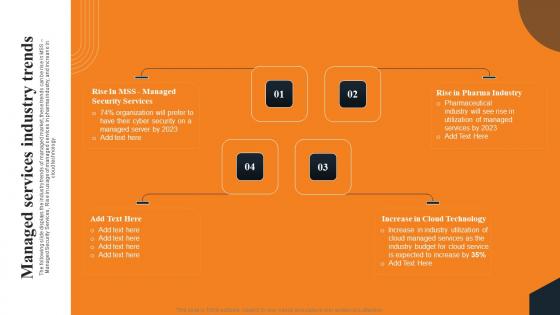
Managed Services Industry Trends Layered Pricing Strategy For Managed Services Brochure Pdf
The following slide displays the industry trends of managed market, these trends can be rise in MSS Managed Security Services, Rise in usage of managed services in pharma industry, and increase in cloud technology. This modern and well arranged Managed Services Industry Trends Layered Pricing Strategy For Managed Services Brochure Pdf provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
Steady Way To Represent 7 Diverging Steps Cycle Network PowerPoint Slides
We present our steady way to represent 7 diverging steps Cycle Network PowerPoint Slides.Present our Arrows PowerPoint Templates because you can Enlighten them with your brilliant understanding of mental health. Present our Flow Charts PowerPoint Templates because we provide the means to project your views. Present our Process and Flows PowerPoint Templates because readymade PowerPoint templates can prove best of your knowledge for your slides to show. Download and present our Business PowerPoint Templates because you have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries. Present our Shapes PowerPoint Templates because they help to lay the base of your trend of thought.Use these PowerPoint slides for presentations relating to Arrow, Background, Center, Chart, Clip, Communication, Competition, Computer, Concept, Connect, Connection, Diagram, Direction, Group, Illustration, Information, Network, Process, Progress, Purpose, Strategy, Symbol, Target. The prominent colors used in the PowerPoint template are Pink, Gray, White. People tell us our steady way to represent 7 diverging steps Cycle Network PowerPoint Slides are Attractive. People tell us our Communication PowerPoint templates and PPT Slides will impress their bosses and teams. The feedback we get is that our steady way to represent 7 diverging steps Cycle Network PowerPoint Slides are Majestic. Presenters tell us our Computer PowerPoint templates and PPT Slides are Amazing. Customers tell us our steady way to represent 7 diverging steps Cycle Network PowerPoint Slides are Romantic. The feedback we get is that our Computer PowerPoint templates and PPT Slides are second to none.
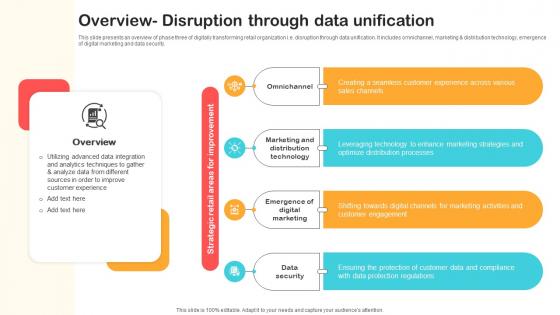
Overview Disruption Through Data Unification Optimizing Retail Operations With Digital DT SS V
This slide presents an overview of phase three of digitally transforming retail organization i.e. disruption through data unification. It includes omnichannel, marketing and distribution technology, emergence of digital marketing and data security.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Overview Disruption Through Data Unification Optimizing Retail Operations With Digital DT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf
This slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Cryptographic Algorithms Used In Cloud Data Security Using Cryptography Themes Pdf from Slidegeeks and deliver a wonderful presentation.
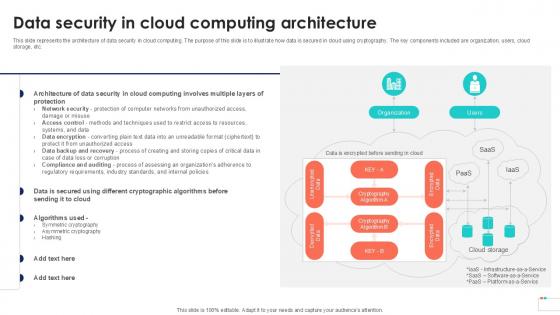
Data Security In Cloud Computing Data Security In Cloud Computing Ppt Example
This slide represents the architecture of data security in cloud computing. The purpose of this slide is to illustrate how data is secured in cloud using cryptography. The key components included are organization, users, cloud storage, etc. This modern and well-arranged Data Security In Cloud Computing Data Security In Cloud Computing Ppt Example provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template
This slide highlights the differences between security and utility tokens. The purpose of this slide is to compare security and utility tokens on various aspects such as purpose, expectations, scam potential, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template can be your best option for delivering a presentation. Represent everything in detail using Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
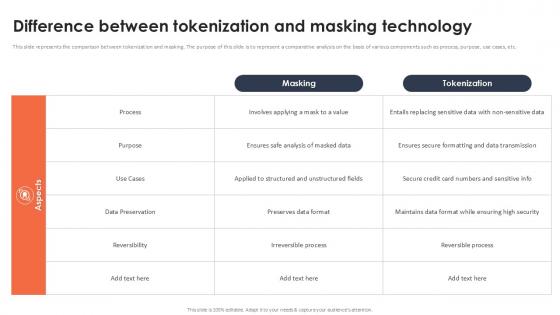
Difference Between Tokenization And Masking Technology Securing Your Data Ppt Powerpoint
This slide represents the comparison between tokenization and masking. The purpose of this slide is to represent a comparative analysis on the basis of various components such as process, purpose, use cases, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Difference Between Tokenization And Masking Technology Securing Your Data Ppt Powerpoint and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Verizon Security Report In Powerpoint And Google Slides Cpb
Presenting our innovatively designed set of slides titled Verizon Security Report In Powerpoint And Google Slides Cpb This completely editable PowerPoint graphic exhibits Verizon Security Report that will help you convey the message impactfully. It can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. Apart from this, you can download this well structured PowerPoint template design in different formats like PDF, JPG, and PNG. So, click the download button now to gain full access to this PPT design.

Naas Architectural Framework Naas As An Enabler For Cloud Transformation Brochure PDF
This slide talks about how NaaS works as a key driver for cloud transformation by providing secure and protected connectivity between businesses and their customers, internet of things devices with corporate applications, and so on. This modern and well-arranged Naas Architectural Framework Naas As An Enabler For Cloud Transformation Brochure PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cloud Security Enhancement Using Data Security In Cloud Computing Ppt Presentation
This slide talks about the various applications of hash algorithm in cloud cryptography. The purpose of this slide is to explain how hash technique can help in providing security in cloud computing. These are password storage, data integrity, digital signatures, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cloud Security Enhancement Using Data Security In Cloud Computing Ppt Presentation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Market Potential Email And Data Protection Platform Capital Funding Pitch Deck PPT Presentation
This slide covers the TAM SAM and SOM models of the company. It includes the values for on premises, cloud based email security market for small and medium sized businesses and USs security service market for SMBs. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Market Potential Email And Data Protection Platform Capital Funding Pitch Deck PPT Presentation and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
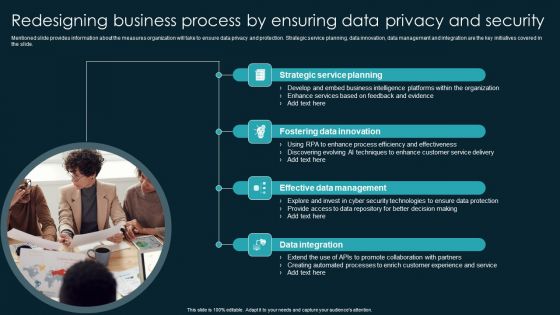
Redesigning Business Process By Ensuring Data Privacy And Security Infographics PDF
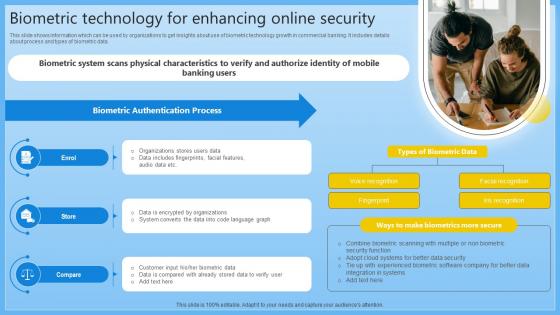
Biometric Technology For Enhancing Online Security Complete Guide On Managing Banking Fin SS V
This slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Biometric Technology For Enhancing Online Security Complete Guide On Managing Banking Fin SS V can be your best option for delivering a presentation. Represent everything in detail using Biometric Technology For Enhancing Online Security Complete Guide On Managing Banking Fin SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Introduction To Digital Banking Services Security Layers In Internet Banking System Guidelines PDF
This slide represents security layers in internet banking system. It covers data layer, application layer, platform layer, network layer and physical layer. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Introduction To Digital Banking Services Security Layers In Internet Banking System Guidelines PDF can be your best option for delivering a presentation. Represent everything in detail using Introduction To Digital Banking Services Security Layers In Internet Banking System Guidelines PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Products And Services Offered Manufacturing Control Software Company Investor PPT Template
This slide caters to details related to a company that provides solutions to manufacturers unique problems, creating secure, well-designed solutions, and generating data-driven insights. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Products And Services Offered Manufacturing Control Software Company Investor PPT Template to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Damage Security Insurance Proposal Gantt Chart Ppt Gallery Graphic Tips PDF
Your complex projects can be managed and organized simultaneously using this detailed damage security insurance proposal gantt chart ppt gallery graphic tips pdf template. Track the milestones, tasks, phases, activities, and subtasks to get an updated visual of your project. Share your planning horizon and release plan with this well crafted presentation template. This exemplary template can be used to plot various dependencies to distinguish the tasks in the pipeline and their impact on the schedules and deadlines of the project. Apart from this, you can also share this visual presentation with your team members and stakeholders. It a resourceful tool that can be incorporated into your business structure. Therefore, download and edit it conveniently to add the data and statistics as per your requirement.

Integrating Data Privacy System Importance Of Data Privacy Ppt Summary Shapes PDF
This slide illustrates the importance of data privacy in terms of developing trust with customers that value privacy and assisting with data management. This modern and well-arranged Integrating Data Privacy System Importance Of Data Privacy Ppt Summary Shapes PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
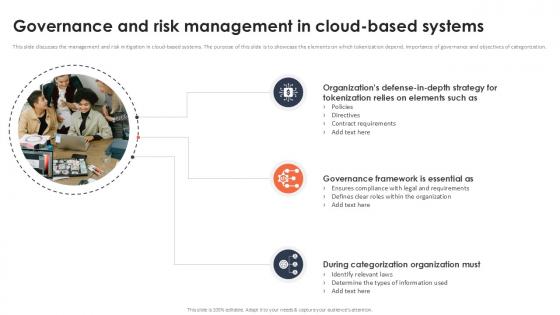
Governance And Risk Management In Cloud Based Systems Securing Your Data Ppt Example
This slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization. This modern and well-arranged Governance And Risk Management In Cloud Based Systems Securing Your Data Ppt Example provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Transactional Tokenization Of Debit And Credit Cards Securing Your Data Ppt Slide
This slide describes the tokenizing of debit and credit cards for transactional purposes. The purpose of this slide is to showcase the transactional tokenization of debit and credit cards. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Transactional Tokenization Of Debit And Credit Cards Securing Your Data Ppt Slide and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Two Year Comparative Analysis Of Information Technology Security Key Performance Indicators Graphics PDF
This slide contains the information related to the cyber security kpis and the issues that are been occurred in this year as well as the previous year to compare how the company is working and what needs to be done to make it even better. Showcasing this set of slides titled Two Year Comparative Analysis Of Information Technology Security Key Performance Indicators Graphics PDF. The topics addressed in these templates are Tested Readiness, Disaster Plans, Security Policy Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Customer Support Services Company Profile Integrated Performance Of The Company Infographics PDF
This slide highlights the integrated performance of call center which covers different elements such as jobs created, percentage of women, renewable energy consumption, employees trained on data security and code of conduct Presenting Customer Support Services Company Profile Integrated Performance Of The Company Infographics PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Technology, Analytics Experts, Data Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
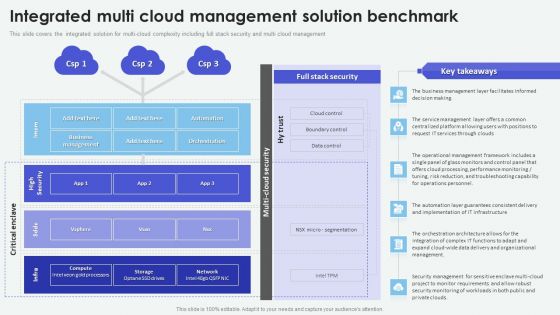
Cloud Based Computing Analysis Integrated Multi Cloud Management Solution Inspiration PDF
This slide covers the integrated solution for multi-cloud complexity including full stack security and multi cloud management. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cloud Based Computing Analysis Integrated Multi Cloud Management Solution Inspiration PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Technology Trends In Online Insurance Essential Personnel Required For Digital Transformation Team
The following slide outlines key personnel required to develop digital transformation team for converting insurer traditional to technology based. Team consists of members which are technologists, security and compliance specialists, business or technology liaisons, project managers, financial stakeholders, marketers, implementation leads and evangelists. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Technology Trends In Online Insurance Essential Personnel Required For Digital Transformation Team from Slidegeeks and deliver a wonderful presentation.

External Components Of Zero Trust Network Security Structure Pdf
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download External Components Of Zero Trust Network Security Structure Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Empowering The Future Security Issues In IoT Based Smart Grid IoT SS V
This slide exhibits security issues and vulnerabilities in IoT-based smart grids that may expose sensitive information to unauthorized parties. It covers issues such as data tampering, cyberattack, privacy issue, and identity spoofing. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Empowering The Future Security Issues In IoT Based Smart Grid IoT SS V and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
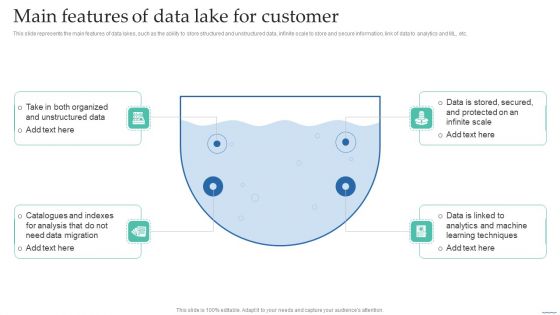
Main Features Of Data Lake For Customer Data Lake Creation With Hadoop Cluster Structure PDF
This slide represents the main features of data lakes, such as the ability to store structured and unstructured data, infinite scale to store and secure information, link of data to analytics and ML, etc.This modern and well-arranged Main Features Of Data Lake For Customer Data Lake Creation With Hadoop Cluster Structure PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
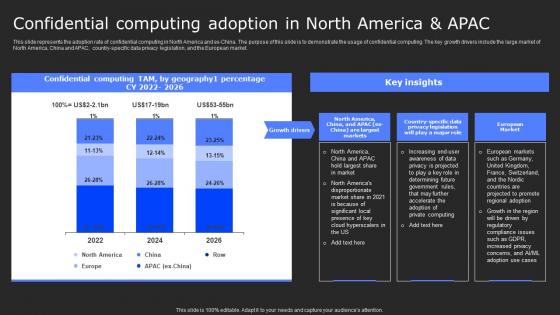
Confidential Computing Adoption In North Secure Computing Framework Template Pdf
This slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Confidential Computing Adoption In North Secure Computing Framework Template Pdf can be your best option for delivering a presentation. Represent everything in detail using Confidential Computing Adoption In North Secure Computing Framework Template Pdf and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Optimizing Business Integration Key Trends That Drive The Industry Information Pdf
Mentioned slide shows various key trends that are driving many industries. Trends covered in the slide are IoT, smarter business system with AI, cyber security and improved employee engagement through technology. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Optimizing Business Integration Key Trends That Drive The Industry Information Pdf and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
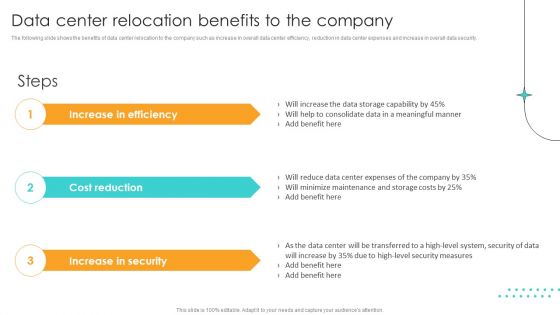
Cost Saving Benefits Of Implementing Data Center Data Center Relocation Benefits To The Company Designs PDF
The following slide shows the benefits of data center relocation to the company such as increase in overall data center efficiency, reduction in data center expenses and increase in overall data security. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cost Saving Benefits Of Implementing Data Center Data Center Relocation Benefits To The Company Designs PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Electronic Symbol Data Protection Security Ppt PowerPoint Presentation Complete Deck
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this electronic symbol data protection security ppt powerpoint presentation complete deck is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twelve slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Kpis To Measure Information Security Risk Management Information Security Risk Administration Mockup PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan.This modern and well-arranged Kpis To Measure Information Security Risk Management Information Security Risk Administration Mockup PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
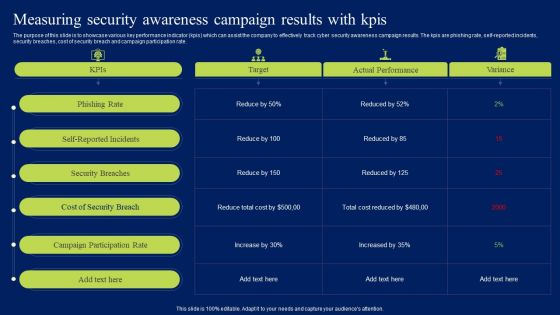
Measuring Security Awareness Campaign Results With Kpis Ppt Summary Sample PDF
The purpose of this slide is to showcase various key performance indicator kpis which can assist the company to effectively track cyber security awareness campaign results. The kpis are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. This modern and well-arranged Measuring Security Awareness Campaign Results With Kpis Ppt Summary Sample PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
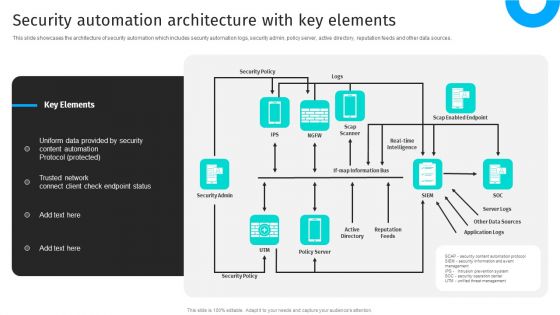
Security Automation To Analyze And Mitigate Cyberthreats Security Automation Architecture Topics PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources.This modern and well-arranged Security Automation To Analyze And Mitigate Cyberthreats Security Automation Architecture Topics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Individualized Pricing Approach For Managed Services Managed Services Industry Trends Infographics PDF
The following slide displays the industry trends of managed market, these trends can be rise in MSS Managed Security Services, Rise in usage of managed services in pharma industry, and increase in cloud technology. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Individualized Pricing Approach For Managed Services Managed Services Industry Trends Infographics PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Prevention Of Information Measuring Security Awareness Campaign Results Pictures PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Prevention Of Information Measuring Security Awareness Campaign Results Pictures PDF from Slidegeeks and deliver a wonderful presentation.

Cyber Security Automation Framework Security Automation Architecture With Key Elements Rules PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. This modern and well arranged Cyber Security Automation Framework Security Automation Architecture With Key Elements Rules PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring Security Awareness Campaign Icons PDF
The purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Implementing Cybersecurity Awareness Program To Prevent Attacks Measuring Security Awareness Campaign Icons PDF from Slidegeeks and deliver a wonderful presentation.
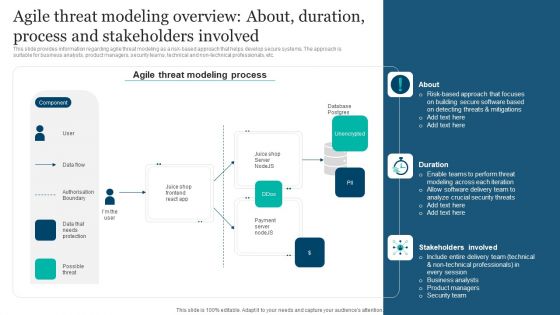
Responsible Technology Playbook Agile Threat Modeling Overview About Duration Process Elements PDF
This slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. This modern and well-arranged Responsible Technology Playbook Agile Threat Modeling Overview About Duration Process Elements PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
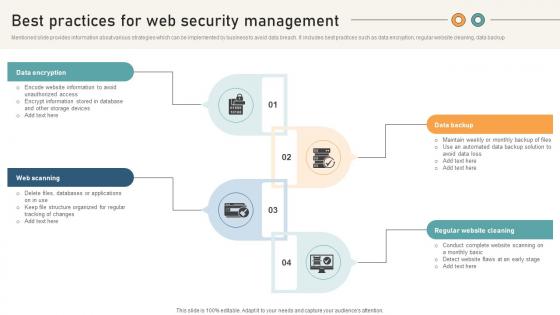
Comprehensive Guide For Website Development Best Practices For Web Security Management
Mentioned slide provides information about various strategies which can be implemented by business to avoid data breach. It includes best practices such as data encryption, regular website cleaning, data backup This modern and well-arranged Comprehensive Guide For Website Development Best Practices For Web Security Management provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
Icons Slide For Cloud Based Email Security Market Report Ppt Infographics Graphic Images PDF
Introducing our well designed icons slide for cloud based email security market report ppt infographics graphic images pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
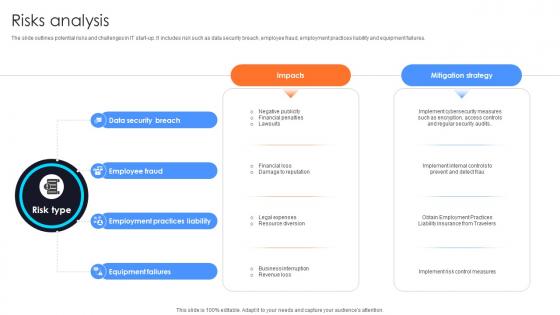
Risks Analysis Information Technology Startup Go To Market Strategy GTM SS V
The slide outlines potential risks and challenges in IT start-up. It includes risk such as data security breach, employee fraud, employment practices liability and equipment failures.This modern and well-arranged Risks Analysis Information Technology Startup Go To Market Strategy GTM SS V provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Information Security Lawfulness Fairness And Transparency Principle Slides PDF
This slide shows the lawfulness, fairness, and transparency concept, which establishes explanations for data processing and includes six legitimate basis for personal data. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Information Security Lawfulness Fairness And Transparency Principle Slides PDF from Slidegeeks and deliver a wonderful presentation.

 Home
Home