Headcount
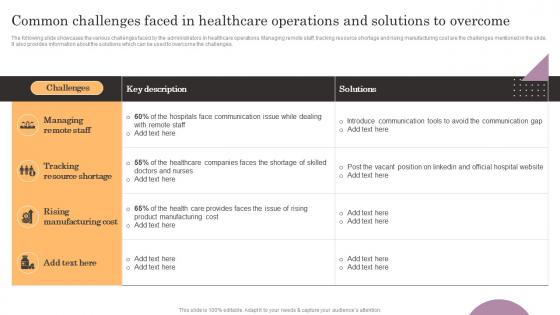
Common Challenges Faced In Healthcare Operations And General Management Microsoft Pdf
The following slide showcases the various challenges faced by the administrators in healthcare operations. Managing remote staff, tracking resource shortage and rising manufacturing cost are the challenges mentioned in the slide. It also provides information about the solutions which can be used to overcome the challenges. Get a simple yet stunning designed Common Challenges Faced In Healthcare Operations And General Management Microsoft Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Common Challenges Faced In Healthcare Operations And General Management Microsoft Pdfcan be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
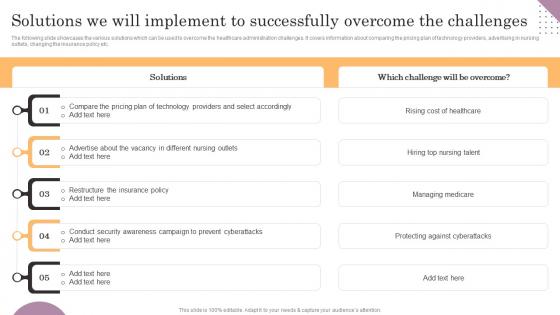
Solutions We Will Implement To Successfully Overcome General Management Structure Pdf
The following slide showcases the various solutions which can be used to overcome the healthcare administration challenges. It covers information about comparing the pricing plan of technology providers, advertising in nursing outlets, changing the insurance policy etc. There are so many reasons you need a Solutions We Will Implement To Successfully Overcome General Management Structure Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Sustainable Types Of Green Data Centers Water And Wastewater Management
This slide gives an overview of the water and wastewater management types of green data centers. The purpose of this slide is to showcase the essential water-related green data center initiatives and water withdrawal breakdown of Facebook. If you are looking for a format to display your unique thoughts, then the professionally designed Sustainable Types Of Green Data Centers Water And Wastewater Management is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Sustainable Types Of Green Data Centers Water And Wastewater Management and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Complete Guide To Launch Best Practices For Website Security Management
Following slide showcases best practices that can be used by business to protect website from cyber attacks and threats. It include pointers such as incest in SSL certifications, anti malware programs, regular backups etc. Get a simple yet stunning designed Complete Guide To Launch Best Practices For Website Security Management. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Complete Guide To Launch Best Practices For Website Security Management can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Customer Referral Program Campaign Efficient Sales Territory Management To Build SA SS V
This slide highlights customer referral program campaigns to attract new leads, including elements such as goals, target audience, timeline, referral program type, incentives, communication channels, etc. Present like a pro with Customer Referral Program Campaign Efficient Sales Territory Management To Build SA SS V. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Dedicated Outside Sales Team Roles Efficient Sales Territory Management To Build SA SS V
This slide showcases the CRM training program to encourage the sales team, including key elements such as training objective, target audience, deadline, training sessions, and resources and support provided. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Dedicated Outside Sales Team Roles Efficient Sales Territory Management To Build SA SS V can be your best option for delivering a presentation. Represent everything in detail using Dedicated Outside Sales Team Roles Efficient Sales Territory Management To Build SA SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
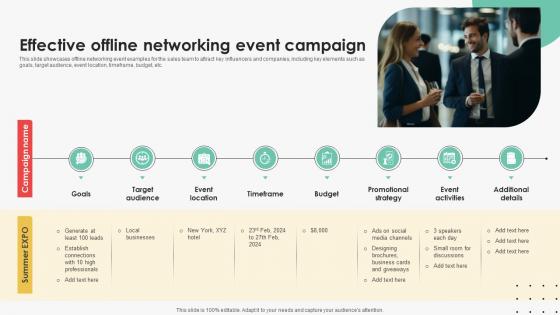
Effective Offline Networking Event Efficient Sales Territory Management To Build SA SS V
This slide showcases offline networking event examples for the sales team to attract key influencers and companies, including key elements such as goals, target audience, event location, timeframe, budget, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Effective Offline Networking Event Efficient Sales Territory Management To Build SA SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Effective Offline Networking Event Efficient Sales Territory Management To Build SA SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Implement Monthly Sales Scoreboard Efficient Sales Territory Management To Build SA SS V
This slide showcases the monthly scorecard of star sales representatives that helps managers to motivate the team, including key elements such as meeting set, deals closed, revenue generated, goals achieved, etc. Welcome to our selection of the Implement Monthly Sales Scoreboard Efficient Sales Territory Management To Build SA SS V. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
Core Team Investor Funding Elevator Pitch Deck For Ticketing Management Firm
This slide provides glimpse about core team of the company with their job titles including CEO, founder, MD, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Core Team Investor Funding Elevator Pitch Deck For Ticketing Management Firm a try. Our experts have put a lot of knowledge and effort into creating this impeccable Core Team Investor Funding Elevator Pitch Deck For Ticketing Management Firm. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Investor Funding Elevator Pitch Deck For Business Operations Management Platform Ppt Template
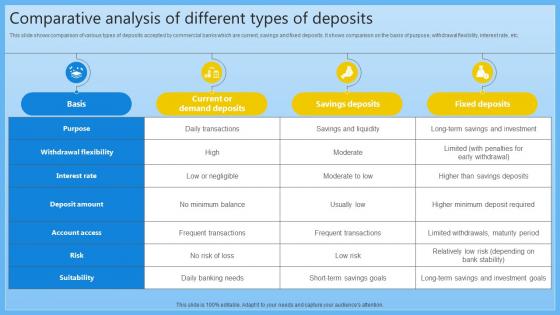
Comparative Analysis Of Different Types Of Complete Guide On Managing Banking Fin SS V
This slide shows comparison of various types of deposits accepted by commercial banks which are current, savings and fixed deposits. It shows comparison on the basis of purpose, withdrawal flexibility, interest rate, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Comparative Analysis Of Different Types Of Complete Guide On Managing Banking Fin SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
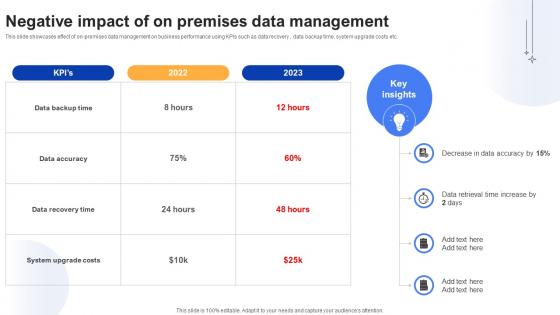
Effective Data Migration Negative Impact Of On Premises Data Management
This slide showcases effect of on-premises data management on business performance using KPIs such as data recovery , data backup time, system upgrade costs etc. Take your projects to the next level with our ultimate collection of Effective Data Migration Negative Impact Of On Premises Data Management. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
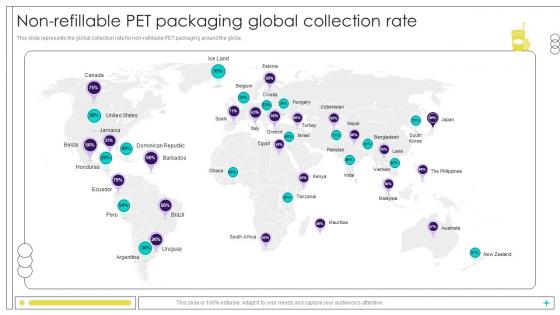
Non Refillable Pet Packaging Global Collection Rate Beverage Manufacturer Company Profile Ppt Slides CP SS V
This slide represents the global collection rate for non-refillable PET packaging around the globe. This Non Refillable Pet Packaging Global Collection Rate Beverage Manufacturer Company Profile Ppt Slides CP SS V is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Non Refillable Pet Packaging Global Collection Rate Beverage Manufacturer Company Profile Ppt Slides CP SS V features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Table Of Contents Streamlining Production Harnessing IOT For Manufacturing Optimization Ppt Slide
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Table Of Contents Streamlining Production Harnessing IOT For Manufacturing Optimization Ppt Slide a try. Our experts have put a lot of knowledge and effort into creating this impeccable Table Of Contents Streamlining Production Harnessing IOT For Manufacturing Optimization Ppt Slide You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Risk Tolerance And Appetite Assessment Matrix Mastering Risk Management Risk
Present like a pro with Risk Tolerance And Appetite Assessment Matrix Mastering Risk Management Risk. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
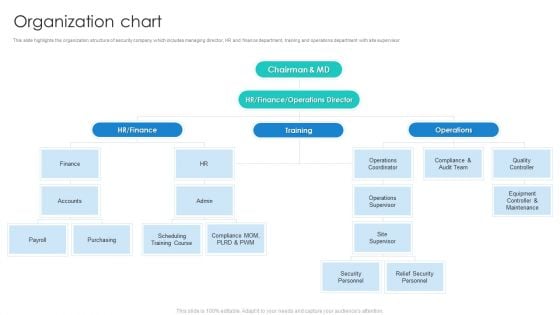
Manpower Corporate Security Business Profile Organization Chart Rules PDF
This slide highlights the organization structure of security company which includes managing director, HR and finance department, training and operations department with site supervisor. This is a Manpower Corporate Security Business Profile Organization Chart Rules PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Finance, Operations Supervisor, Audit Team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
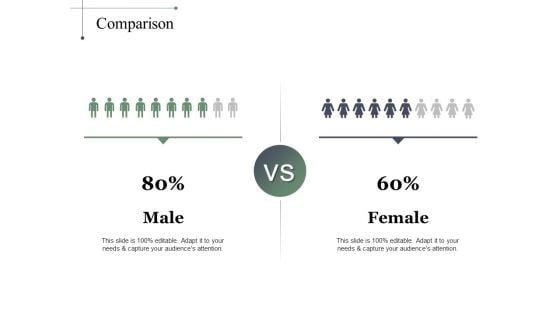
Comparison Male Ppt PowerPoint Presentation Inspiration Aids
This is a comparison male ppt powerpoint presentation inspiration aids. This is a two stage process. The stages in this process are comparison, male, female, marketing, management.
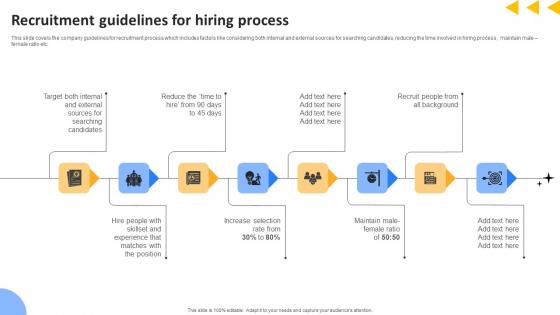
Workforce Productivity Improvement Recruitment Guidelines For Hiring Process Rules Pdf
This slide covers the company guidelines for recruitment process which includes factors like considering both internal and external sources for searching candidates, reducing the time involved in hiring process, maintain male female ratio etc. Get a simple yet stunning designed Workforce Productivity Improvement Recruitment Guidelines For Hiring Process Rules Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Workforce Productivity Improvement Recruitment Guidelines For Hiring Process Rules Pdf can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
Delegate Right Tasks To Right People PowerPoint Template
Visually support your presentation with our above template showing 3d men icons. This slide has been professionally designed to exhibit delegation of authority and responsibilities. This template offers an excellent background to build impressive presentation.

Disaster Management Plan And Strategies Ppt PowerPoint Presentation Complete Deck With Slides

About Man In The Middle Phishing Scams Man In The Middle Phishing IT
This slide demonstrates the idea behind man-in-the-middle phishing attacks. The purpose of this slide is to illustrate the concept of MITM attack by comparing normal scenario and MITM attack which includes attacker, proxy server, real website, etc. There are so many reasons you need a About Man In The Middle Phishing Scams Man In The Middle Phishing IT. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Agenda For Man In The Middle Phishing It Ppt Formates
If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Agenda For Man In The Middle Phishing It Ppt Formates and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Wireless Banking To Improve Man In The Middle Mobile Banking Attacking Fin SS V
This slide shows overview of popular cyberattack related to mobile banking which is man in the middle MiTM. It also includes popular types of this attack which are WIFI network interception, DNS spoofing, email interception and malware. There are so many reasons you need a Wireless Banking To Improve Man In The Middle Mobile Banking Attacking Fin SS V. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Table Of Contents Man In The Middle Phishing IT Ppt Formates
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Table Of Contents Man In The Middle Phishing IT Ppt Formates was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Table Of Contents Man In The Middle Phishing IT Ppt Formates

Male Handing Keys To Female Success PowerPoint Templates And PowerPoint Backgrounds 0311
Microsoft PowerPoint Template and Background with male hand handing keys to female hand over dramatic clouds and sun rays
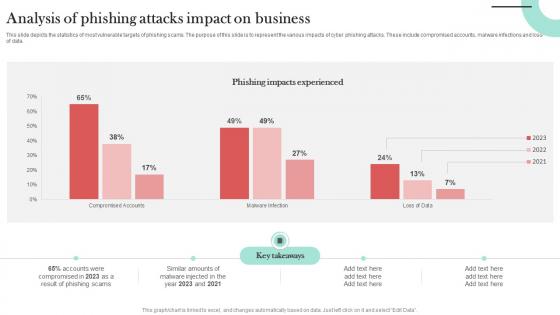
Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT
This slide depicts the statistics of most vulnerable targets of phishing scams. The purpose of this slide is to represent the various impacts of cyber phishing attacks. These include compromised accounts, malware infections and loss of data. If you are looking for a format to display your unique thoughts, then the professionally designed Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Analysis Of Phishing Attacks Impact Man In The Middle Phishing IT and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Cyber Phishing Attacks Tracking Dashboard Man In The Middle Phishing IT
This slide represents the dashboard to track cyber phishing attacks. The purpose of this slide is to provide a graphical representation of cyber attacks occurred in a specific time span. It also depicts the organizations health risk. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Phishing Attacks Tracking Dashboard Man In The Middle Phishing IT was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Phishing Attacks Tracking Dashboard Man In The Middle Phishing IT

Examples Of Clone Phishing Cyber Scams Man In The Middle Phishing IT
This slide demonstrates the various examples of clone phishing cyber scams. The purpose of this slide is to illustrate different types of clone phishing emails targeting different individuals. These include customer support scams, fake virus scams and refund scams. This Examples Of Clone Phishing Cyber Scams Man In The Middle Phishing IT is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Examples Of Clone Phishing Cyber Scams Man In The Middle Phishing IT features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
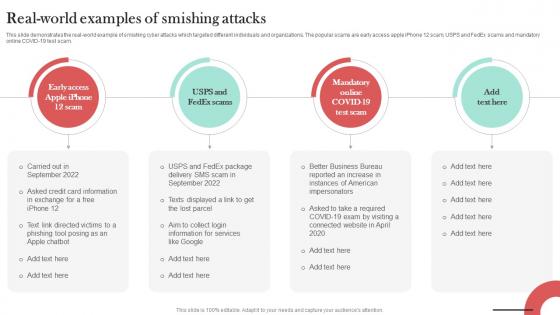
Real World Examples Of Smishing Attacks Man In The Middle Phishing IT
This slide demonstrates the real-world example of smishing cyber attacks which targeted different individuals and organizations. The popular scams are early access apple iPhone 12 scam, USPS and FedEx scams and mandatory online COVID-19 test scam. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Real World Examples Of Smishing Attacks Man In The Middle Phishing IT. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Real World Examples Of Smishing Attacks Man In The Middle Phishing IT today and make your presentation stand out from the rest

Real World Examples Of Watering Hole Attacks Man In The Middle Phishing IT
This slide describes the real-world examples of watering hole phishing scams. These include Facebook, Twitter, Microsoft, and Apple scam, LuckyMouse scam, International Civil Aviation OrganizationICAO scam, Ccleaner scam and Holy Water scam. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Real World Examples Of Watering Hole Attacks Man In The Middle Phishing IT can be your best option for delivering a presentation. Represent everything in detail using Real World Examples Of Watering Hole Attacks Man In The Middle Phishing IT and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Tricks Employed By Malicious Websites Man In The Middle Phishing IT
This slide talks about various tricks utilized by fraudulent websites to scam the visitors. The purpose of this slide is to make users aware of such different tricks such as free discount offers, low interest rates free credit cards, employment opportunities, etc. Explore a selection of the finest Tricks Employed By Malicious Websites Man In The Middle Phishing IT here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Tricks Employed By Malicious Websites Man In The Middle Phishing IT to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
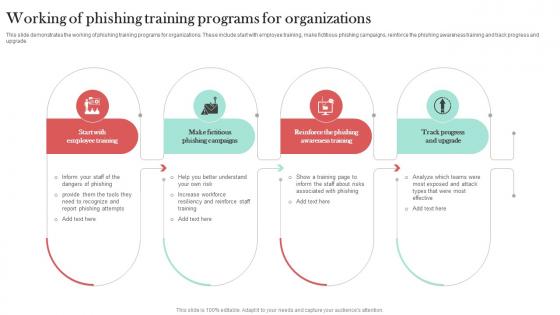
Working Of Phishing Training Programs Man In The Middle Phishing IT
This slide demonstrates the working of phishing training programs for organizations. These include start with employee training, make fictitious phishing campaigns, reinforce the phishing awareness training and track progress and upgrade. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Working Of Phishing Training Programs Man In The Middle Phishing IT to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Working Of Phishing Training Programs Man In The Middle Phishing IT.

Table Of Contents For Man In The Middle Phishing IT Ppt Information
Make sure to capture your audiences attention in your business displays with our gratis customizable Table Of Contents For Man In The Middle Phishing IT Ppt Information. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
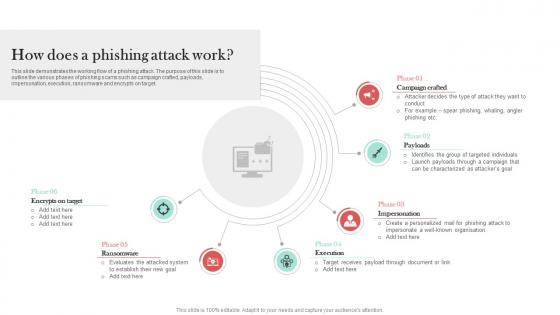
How Does A Phishing Attack Work Man In The Middle Phishing IT
This slide demonstrates the working flow of a phishing attack. The purpose of this slide is to outline the various phases of phishing scams such as campaign crafted, payloads, impersonation, execution, ransomware and encrypts on target. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download How Does A Phishing Attack Work Man In The Middle Phishing IT from Slidegeeks and deliver a wonderful presentation.
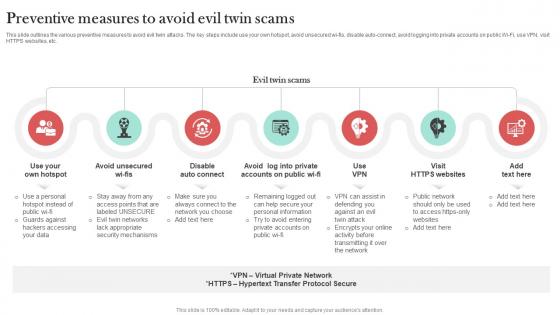
Preventive Measures To Avoid Evil Twin Scams Man In The Middle Phishing IT
This slide outlines the various preventive measures to avoid evil twin attacks. The key steps include use your own hotspot, avoid unsecured wi-fis, disable auto-connect, avoid logging into private accounts on public Wi-Fi, use VPN, visit HTTPS websites, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Preventive Measures To Avoid Evil Twin Scams Man In The Middle Phishing IT will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

About Identity Theft Overview And Techniques Man In The Middle Phishing IT
This slide talks about the major crime committed by phishers named as identity theft. The purpose of this slide is to outline the ways of stealing information such as robbery, computer fraud, social networking sites, mail theft and dumpster diving. Want to ace your presentation in front of a live audience Our About Identity Theft Overview And Techniques Man In The Middle Phishing IT can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Benefits Of Comprehensive Training Programs Man In The Middle Phishing IT
This slide outlines the benefits of comprehensive training programs in organizations. These include align with companys database, instructional library, auto-enrolment service, inform about real risks, track and evaluate and plan a year ahead. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Benefits Of Comprehensive Training Programs Man In The Middle Phishing IT and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Overview Of Different Types Of Phishing Attacks Man In The Middle Phishing IT
This slide outlines the various types of cyber phishing attacks. The types include email phishing, HTTPS phishing, whaling, smishing, angler phishing, pharming, spear phishing, pop-up phishing, clone phishing, evil twin scams, watering hole attacks, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Overview Of Different Types Of Phishing Attacks Man In The Middle Phishing IT for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
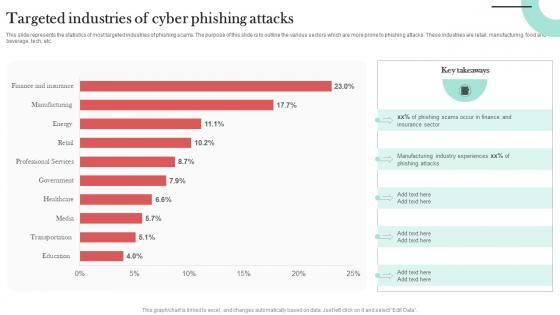
Targeted Industries Of Cyber Phishing Man In The Middle Phishing IT
This slide represents the statistics of most targeted industries of phishing scams. The purpose of this slide is to outline the various sectors which are more prone to phishing attacks. These industries are retail, manufacturing, food and beverage, tech, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Targeted Industries Of Cyber Phishing Man In The Middle Phishing IT to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Tools Provided By Google To Prevent Man In The Middle Phishing IT
This slide demonstrates the different tools provided by Google to prevent and report cyber phishing scams. These include to spot phishing mails with the help of Gmail, utilize safe browsing in chrome, look for unsafe saved passwords, password alert for chrome, etc. Welcome to our selection of the Tools Provided By Google To Prevent Man In The Middle Phishing IT. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
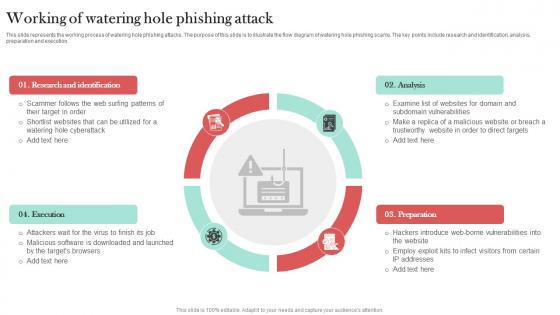
Working Of Watering Hole Phishing Attack Man In The Middle Phishing IT
This slide represents the working process of watering hole phishing attacks. The purpose of this slide is to illustrate the flow diagram of watering hole phishing scams. The key points include research and identification, analysis, preparation and execution. This Working Of Watering Hole Phishing Attack Man In The Middle Phishing IT from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Working Procedure Of Spear Phishing Attack Man In The Middle Phishing IT
This slide illustrates the structure of spear phishing attack. The purpose of this slide is to explain the working flow of spear phishing attack. The key components include attacker, phishing email, targeted users, exploited system, internal network, etc.Take your projects to the next level with our ultimate collection of Working Procedure Of Spear Phishing Attack Man In The Middle Phishing IT. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
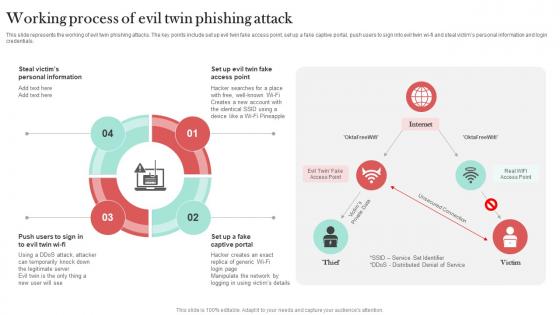
Working Process Of Evil Twin Phishing Attack Man In The Middle Phishing IT
This slide represents the working of evil twin phishing attacks. The key points include set up evil twin fake access point, set up a fake captive portal, push users to sign into evil twin wi-fi and steal victims personal information and login credentials. Take your projects to the next level with our ultimate collection of Working Process Of Evil Twin Phishing Attack Man In The Middle Phishing IT. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
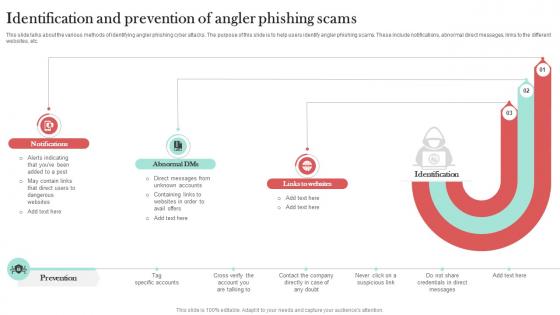
Identification And Prevention Of Angler Man In The Middle Phishing IT
This slide talks about the various methods of identifying angler phishing cyber attacks. The purpose of this slide is to help users identify angler phishing scams. These include notifications, abnormal direct messages, links to the different websites, etc. Slidegeeks has constructed Identification And Prevention Of Angler Man In The Middle Phishing IT after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
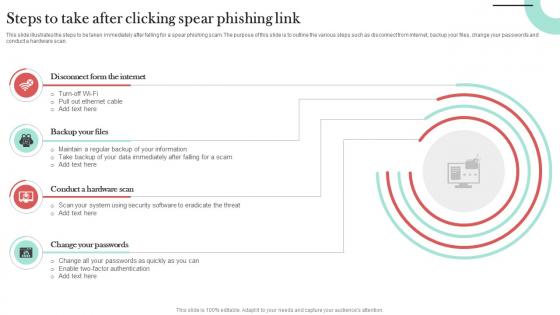
Steps To Take After Clicking Spear Phishing Link Man In The Middle Phishing IT
This slide illustrates the steps to be taken immediately after falling for a spear phishing scam. The purpose of this slide is to outline the various steps such as disconnect from internet, backup your files, change your passwords and conduct a hardware scan. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Steps To Take After Clicking Spear Phishing Link Man In The Middle Phishing IT and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT
This slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names. Retrieve professionally designed Warning Signs Of Pop Up Phishing Scams Man In The Middle Phishing IT to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
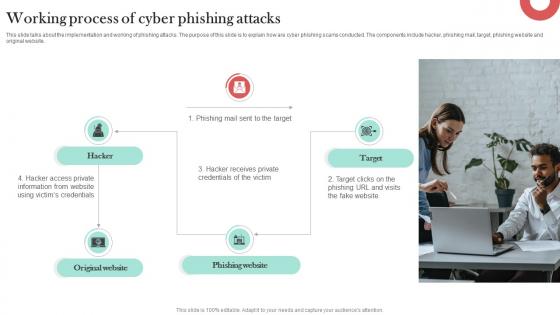
Working Process Of Cyber Phishing Attacks Man In The Middle Phishing IT
This slide talks about the implementation and working of phishing attacks. The purpose of this slide is to explain how are cyber phishing scams conducted. The components include hacker, phishing mail, target, phishing website and original website. Do you know about Slidesgeeks Working Process Of Cyber Phishing Attacks Man In The Middle Phishing IT These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
Agile Org Chart It Financial Mockup PDF
Deliver an awe inspiring pitch with this creative agile org chart it financial mockup pdf bundle. Topics like minimum, medium, maximum can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Male And Female Executives Vector Icon Ppt PowerPoint Presentation File Aids PDF
Presenting this set of slides with name male and female executives vector icon ppt powerpoint presentation file aids pdf. This is a three stage process. The stages in this process are male and female executives vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Male Female Same Salary Vector Icon Ppt PowerPoint Presentation File Show PDF
Presenting this set of slides with name male female same salary vector icon ppt powerpoint presentation file show pdf. This is a four stage process. The stages in this process are male female same salary vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Rules For Good Behavior For Male And Female Employees Ppt PowerPoint Presentation File Model PDF
Presenting this set of slides with name rules for good behavior for male and female employees ppt powerpoint presentation file model pdf. This is a five stage process. The stages in this process are rules for good behavior for male and female employees. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Sexual Equality Icon With Male And Female Signs Ppt PowerPoint Presentation Layouts Show PDF
Presenting this set of slides with name sexual equality icon with male and female signs ppt powerpoint presentation layouts show pdf. The topics discussed in these slide is sexual equality icon with male and female signs. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
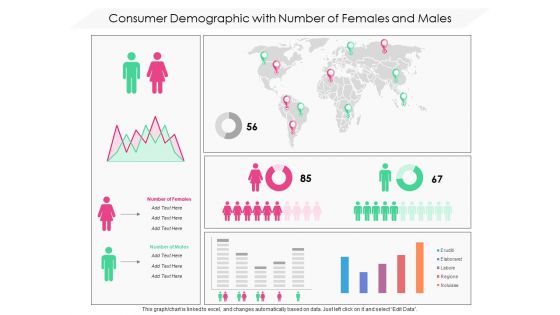
Consumer Demographic With Number Of Females And Males Ppt PowerPoint Presentation File Infographics PDF
Presenting this set of slides with name consumer demographic with number of females and males ppt powerpoint presentation file infographics pdf. The topics discussed in these slide is consumer demographic with number of females and males. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Female And Male Hairstyle Vector Icon Ppt PowerPoint Presentation File Gridlines PDF
Presenting this set of slides with name female and male hairstyle vector icon ppt powerpoint presentation file gridlines pdf. The topics discussed in these slide is female and male hairstyle vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Female And Male Human Head Vector Icon Ppt PowerPoint Presentation File Design Templates PDF
Presenting this set of slides with name female and male human head vector icon ppt powerpoint presentation file design templates pdf. The topics discussed in these slide is female and male human head vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
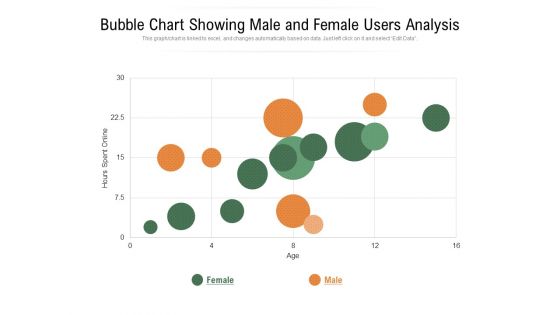
Bubble Chart Showing Male And Female Users Analysis Ppt PowerPoint Presentation Gallery Background PDF
Presenting this set of slides with name bubble chart showing male and female users analysis ppt powerpoint presentation gallery background pdf. The topics discussed in these slide is bubble chart showing male and female users analysis. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Icon Of Gender Equality Between Male And Female Ppt PowerPoint Presentation Slides Designs PDF
Presenting this set of slides with name icon of gender equality between male and female ppt powerpoint presentation slides designs pdf. The topics discussed in these slide is icon of gender equality between male and female. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Male And Female Executive At Business Meeting Ppt PowerPoint Presentation Gallery Visuals PDF
Presenting this set of slides with name male and female executive at business meeting ppt powerpoint presentation gallery visuals pdf. This is a one stage process. The stage in this process is male and female executive at business meeting. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Male And Female Persons Vector Icon Ppt PowerPoint Presentation Inspiration Layout PDF
Presenting this set of slides with name male and female persons vector icon ppt powerpoint presentation inspiration layout pdf. This is a three stage process. The stages in this process are male and female persons vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Motivation Saying On Male And Female Equality Rights Ppt PowerPoint Presentation Gallery Maker PDF
Presenting this set of slides with name motivation saying on male and female equality rights ppt powerpoint presentation gallery maker pdf. This is a three stage process. The stages in this process are motivation saying on male and female equality rights. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

 Home
Home