Ethical Hacking

Information Technology Certifications Advantages Training Cost And Exam Cost Demonstration PDF
This template covers training cost and exam cost for certified scrum developer CSD certification certified scrummaster CSM, AWS certified solutions architect certification etc. Deliver an awe inspiring pitch with this creative Information Technology Certifications Advantages Training Cost And Exam Cost Demonstration PDF bundle. Topics like Certified ScrumMaster, Certified Scrum Developer, Certified Ethical Hacker can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Certifications Advantages What Are Certification Themes PDF
This template covers IT certification such as certified scrum master CSM, AWS certified solutions architect certification, certified ethical hacker CEH etc, qualification and job description. Deliver and pitch your topic in the best possible manner with this Information Technology Certifications Advantages What Are Certification Themes PDF. Use them to share invaluable insights on Certified ScrumMaster, Architect Certification, ITIL Foundation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Certifications Advantages IT Certification Career Path Diagrams PDF
This template covers the career path to become a certified professional including available courses for certified scrum developer CSD certification certified scrum master CSM etc. Deliver an awe inspiring pitch with this creative Information Technology Certifications Advantages IT Certification Career Path Diagrams PDF bundle. Topics like Certified Scrum Developer, Certified ScrumMaster, Certified Ethical Hacker can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
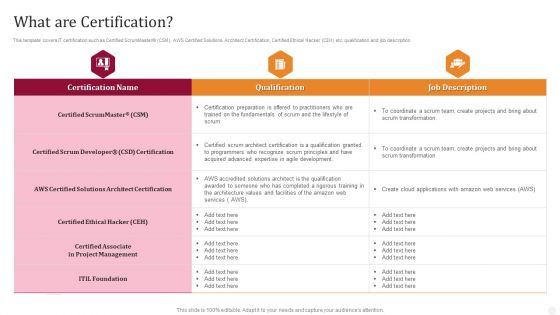
What Are Certification Technology License For IT Professional Background PDF
This template covers IT certification such as Certified ScrumMaster CSM, AWS Certified Solutions Architect Certification, Certified Ethical Hacker CEH etc, qualification and job description.Deliver and pitch your topic in the best possible manner with this What Are Certification Technology License For IT Professional Background PDF. Use them to share invaluable insights on Architect Certification, Accredited Solutions, Project Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
IT Security Hacker Dashboard For Threat Tracking Rules PDF
This slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report.Deliver an awe inspiring pitch with this creative IT Security Hacker Dashboard For Threat Tracking Rules PDF bundle. Topics like Threat Dashboard, Loss Of Information, Regulations And Contracts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
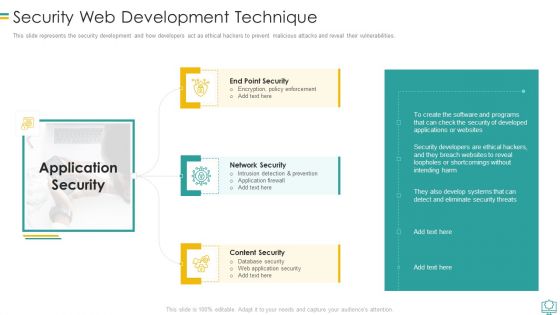
Security Web Development Technique Mockup PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.This is a Security Web Development Technique Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intrusion Detection And Prevention, Encryption Policy Enforcement, Database Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Website Programming IT Security Website Programming Technique Ppt PowerPoint Presentation File Infographics PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities. Presenting website programming it security website programming technique ppt powerpoint presentation file infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like end point security, network security, content security, application security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
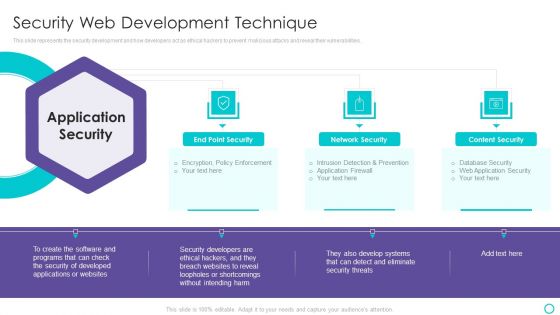
Website Designing And Development Service Security Web Development Technique Themes PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.This is a Website Designing And Development Service Security Web Development Technique Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security, Content Security, Loopholes Or Shortcomings You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Certification Information Technology Professionals Top Hiring Industries For IT Certification Icons PDF
This template covers top hiring industries for certification courses such as ITIL foundation certification, project management professional certification and many others This is a certification information technology professionals salary in different countries icons pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project management, ethical hacker, architect certification, developer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Certification Information Technology Professionals What Are Certification Infographics PDF
This template covers IT certification such as Certified ScrumMaster CSM, AWS Certified Solutions Architect Certification, Certified Ethical Hacker CEH etc, qualification and job description This is a certification information technology professionals what are certification infographics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like certification, preparation, fundamentals, practitioners. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
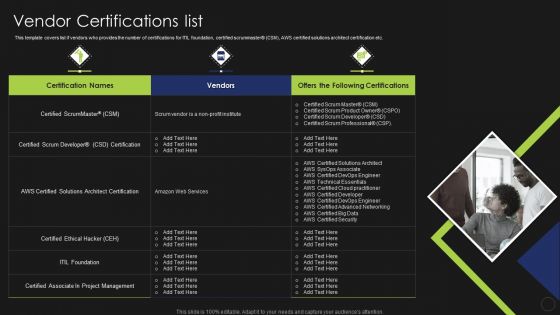
Information Technology Certifications Advantages Vendor Certifications List Graphics PDF
This template covers list if vendors who provides the number of certifications for ITIL foundation, certified scrummaster CSM, AWS certified solutions architect certification etc. This is a Information Technology Certifications Advantages Vendor Certifications List Graphics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Certified ScrumMaster, Certified Scrum Developer, Certified Ethical Hacker. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Certifications Advantages Who Should Take Which Cert Ideas PDF
This template covers details on who should take certified solutions and certification course for certified associate in project management, certified scrum developer CSD certification etc. Presenting Information Technology Certifications Advantages Who Should Take Which Cert Ideas PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Certified ScrumMaster, Certified Scrum Deve, Certified Ethical Hacker. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Certifications Advantages Why Companies Hire Professionals Sample PDF
This template covers reasons why company wants to hire certified professionals for ITIL Foundation certified scrummaster CSM,AWS Certififed solutions architect certification etc. This is a Information Technology Certifications Advantages Why Companies Hire Professionals Sample PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Certified ScrumMaster, Certified Scrum Developer, Certified Ethical Hacker. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Overview Of Grey Hat Hackers Ppt Infographics Pictures PDF
This slide depicts the grey hat hackers and how they first hack any system, computer, software, or network and then ask for permission. This is a overview of grey hat hackers ppt infographics pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like systems, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Ukraine Cyberwarfare Ongoing Onslaught Of Russia On Ukraine Brochure Pdf
This slide represents the ongoing onslaught of Russia on Ukraine from December 2015 to Jan 2022. Russia has attacked Ukraine and other countries in many ways. Presenting ukraine cyberwarfare ongoing onslaught of russia on ukraine brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like russian sponsored hack attacked microsoft exchange servers, hackers gained access to email accounts and networks worldwide, including in ukraine, the united states, and australia. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download

Security Web Development Role Web Designing User Engagement Topics PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities. Are you searching for a Security Web Development Role Web Designing User Engagement Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Web Development Role Web Designing User Engagement Topics PDF from Slidegeeks today.

Signs For Various Digital Terrorism Attacks Brochure PDF
This slide shows various cyber terrorism attacks along with signs associated with each cyber attack. It include various cyber terrorism attacks such as Blackmailing Email Demand, Social Accounts Hacked etc. Presenting Signs For Various Digital Terrorism Attacks Brochure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Attacked Network, Fraudulent Financial Transaction, Social Accounts Hacked. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Block To Multiple Values Lin Centre And On Arms Ppt Business Plan Template PowerPoint Slides
We present our block to multiple values lin centre and on arms ppt business plan template PowerPoint Slides.Download and present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are innately eco-friendly. Their high recall value negate the need for paper handouts. Download our Puzzles or Jigsaws PowerPoint Templates because You are an avid believer in ethical practices. Highlight the benefits that accrue with our PowerPoint Templates and Slides. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas. Download our Process and Flows PowerPoint Templates because You should Ascend the ladder of success with ease. Our PowerPoint Templates and Slides will provide strong and sturdy steps. Present our Leadership PowerPoint Templates because Our PowerPoint Templates and Slides will let Your superior ideas hit the target always and everytime.Use these PowerPoint slides for presentations relating to abstract, binary, business, code, commerce, communication, computer, concept, connect, connection, corporate, cyberspace, data, digital, download, ecommerce, electronic, futuristic, global, hacker, information, internet, multiple, network, networking, online, program, programming, security, software, tech, technology, values. The prominent colors used in the PowerPoint template are Blue, Gray, White.

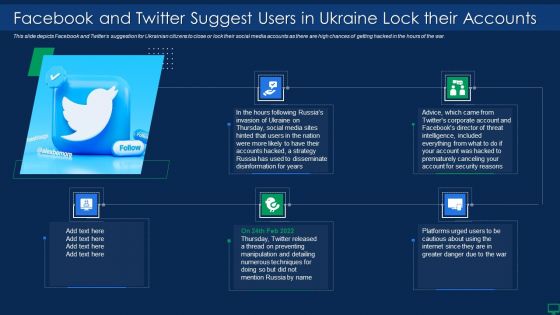
Ukraine Cyberwarfare Facebook And Twitter Suggest Users In Ukraine Lock Their Accounts Information Pdf
This slide depicts Facebook and Twitters suggestion for Ukrainian citizens to close or lock their social media accounts as there are high chances of getting hacked in the hours of the war. Presenting ukraine cyberwarfare facebook and twitter suggest users in ukraine lock their accounts information pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like platforms urged users to be cautious about using the internet since they are in greater danger due to the war, in the hours following russias invasion of ukraine on thursday, social media sites hinted that users in the nation were more likely to have their accounts hacked. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
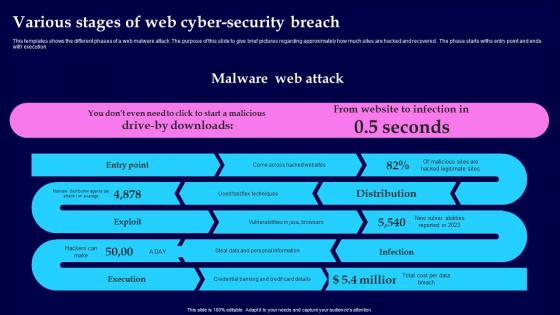
Various Stages Of Web Cyber Security Breach Introduction Pdf
This templates shows the different phases of a web malware attack. The purpose of this slide to give brief pictures regarding approximately how much sites are hacked and recovered. The phase starts withs entry point and ends with execution Pitch your topic with ease and precision using this Various Stages Of Web Cyber Security Breach Introduction Pdf This layout presents information on Malware Web Attack, Various Stages, Cyber Security Breach It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Five Steps For Cyber IT Security Risk Analysis Graphics PDF
This slide covers the steps for analysis of risk occurring in cyber security to reduce errors and system hacks so that the information of clients remain safe. It includes finding assets, identifying consequences, threats and assessing risk. Presenting Five Steps For Cyber IT Security Risk Analysis Graphics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Find Valuable Assets, Assess Risk, Identify Potential Consequences. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Russian Cyber Attacks On Ukraine IT Facebook And Twitter Suggest Rules PDF
This slide depicts Facebook and Twitters suggestion for Ukrainian citizens to close or lock their social media accounts as there are high chances of getting hacked in the hours of the war. This is a russian cyber attacks on ukraine it facebook and twitter suggest rules pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like social media, accounts, strategy, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Wiper Spyware Attack Facebook And Twitter Suggest Users In Ukraine Lock Their Accounts Clipart PDF
This slide depicts Facebook and Twitters suggestion for Ukrainian citizens to close or lock their social media accounts as there are high chances of getting hacked in the hours of the war.Deliver and pitch your topic in the best possible manner with this data wiper spyware attack facebook and twitter suggest users in ukraine lock their accounts clipart pdf Use them to share invaluable insights on disseminate disinformation, included everything, prematurely canceling and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

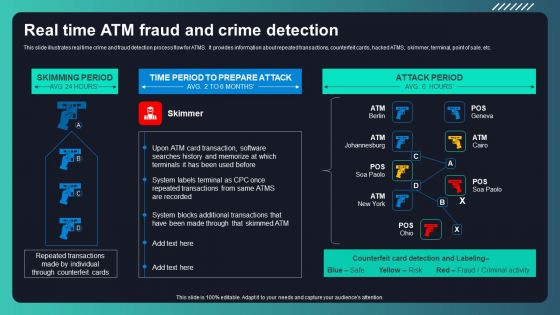
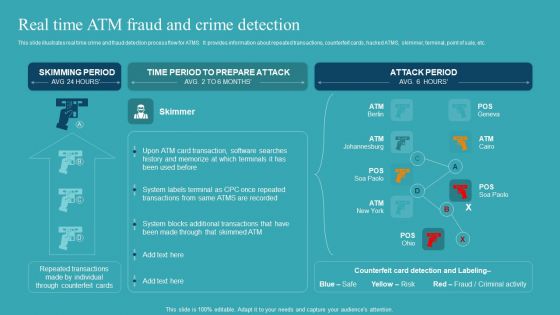
Techniques To Monitor Transactions Real Time Atm Fraud And Crime Detection Slides PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Take your projects to the next level with our ultimate collection of Techniques To Monitor Transactions Real Time Atm Fraud And Crime Detection Slides PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.
Deploying AML Transaction Monitoring Real Time ATM Fraud And Crime Detection Designs PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Boost your pitch with our creative Deploying AML Transaction Monitoring Real Time ATM Fraud And Crime Detection Designs PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
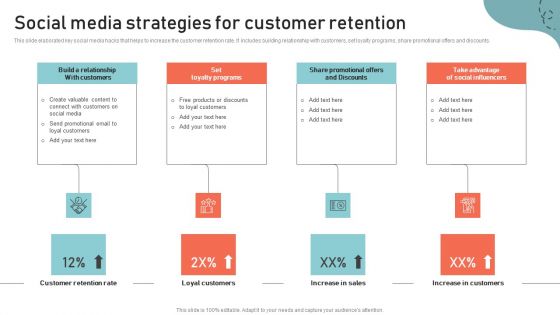
Optimizing Multichannel Strategy To Improve User Experience Social Media Strategies Ideas PDF
This slide elaborated key social media hacks that helps to increase the customer retention rate. It includes building relationship with customers, set loyalty programs, share promotional offers and discounts. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Optimizing Multichannel Strategy To Improve User Experience Social Media Strategies Ideas PDF from Slidegeeks and deliver a wonderful presentation.
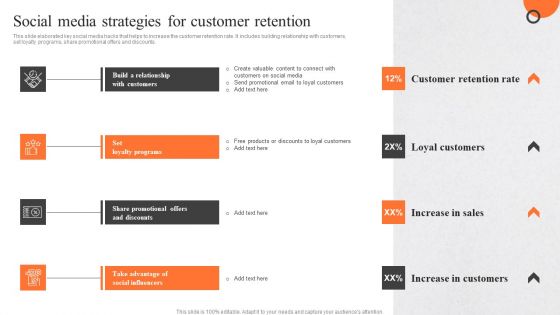
Enhancing Buyer Journey Social Media Strategies For Customer Retention Mockup PDF

Client Feedback Strategies Social Media Strategies For Customer Retention Infographics Pdf
This slide elaborated key social media hacks that helps to increase the customer retention rate. It includes building relationship with customers, set loyalty programs, share promotional offers and discounts. Find a pre designed and impeccable Client Feedback Strategies Social Media Strategies For Customer Retention Infographics Pdf. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Series Of Cyber Security Attacks Against Ukraine 2022 Facebook And Twitter Suggest Users In Ukraine Lock Their Accounts Professional PDF
This slide depicts facebook and twitters suggestion for ukrainian citizens to close or lock their social media accounts as there are high chances of getting hacked in the hours of the war. Present like a pro with Series Of Cyber Security Attacks Against Ukraine 2022 Facebook And Twitter Suggest Users In Ukraine Lock Their Accounts Professional PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
Integrating AML And Transaction Real Time ATM Fraud And Crime Detection Introduction PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Integrating AML And Transaction Real Time ATM Fraud And Crime Detection Introduction PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Integrating AML And Transaction Real Time ATM Fraud And Crime Detection Introduction PDF.

Enhancing CX Strategy Social Media Strategies For Customer Retention Pictures PDF
This slide elaborated key social media hacks that helps to increase the customer retention rate. It includes building relationship with customers, set loyalty programs, share promotional offers and discounts. Retrieve professionally designed Enhancing CX Strategy Social Media Strategies For Customer Retention Pictures PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Transaction Monitoring Real Time ATM Fraud And Crime Detection Infographics PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Transaction Monitoring Real Time ATM Fraud And Crime Detection Infographics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Transaction Monitoring Real Time ATM Fraud And Crime Detection Infographics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
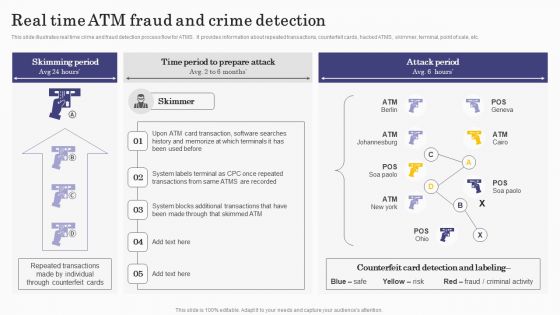
Deploying Banking Transaction Real Time Atm Fraud And Crime Detection Download PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Retrieve professionally designed Deploying Banking Transaction Real Time Atm Fraud And Crime Detection Download PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
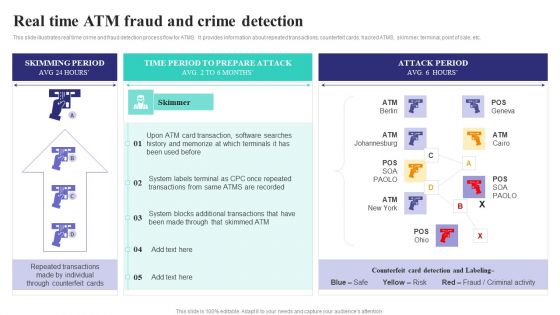
Formulating Money Laundering Real Time Atm Fraud And Crime Detection Brochure PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Slidegeeks has constructed Table Of Contents For Formulating Money Laundering Real Time Atm Fraud And Crime Detection Brochure PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Actual Time Transaction Monitoring Software And Strategies Real Time ATM Fraud And Crime Detection Elements PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Retrieve professionally designed Actual Time Transaction Monitoring Software And Strategies Real Time ATM Fraud And Crime Detection Elements PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
Creating Transaction Monitoring Real Time ATM Fraud And Crime Detection Icons PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Slidegeeks has constructed Creating Transaction Monitoring Real Time ATM Fraud And Crime Detection Icons PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Customer Experience Optimization Social Media Strategies For Customer Retention Pictures PDF
This slide elaborated key social media hacks that helps to increase the customer retention rate. It includes building relationship with customers, set loyalty programs, share promotional offers and discounts. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Customer Experience Optimization Social Media Strategies For Customer Retention Pictures PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Customer Experience Optimization Social Media Strategies For Customer Retention Pictures PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
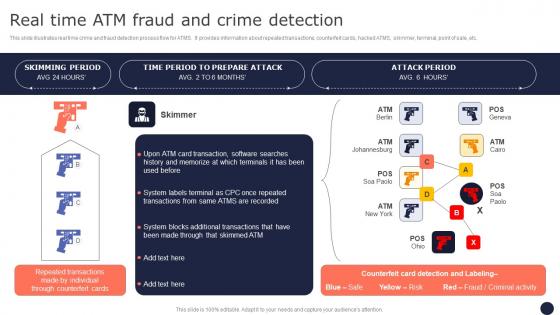
Real Time ATM Fraud And Crime Detection Mitigating Corporate Scams And Robberies Pictures Pdf
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Real Time ATM Fraud And Crime Detection Mitigating Corporate Scams And Robberies Pictures Pdf to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Real Time ATM Fraud And Crime Detection Mitigating Corporate Scams And Robberies Pictures Pdf.
Business And Threats Landscape In Business Cybersecurity Ppt Icon Example Introduction PDF
This slide showcases risk and threats landscape which can be referred by businesses to be aware of cybersecurity issues and attacks. It contains information about phishing, malware and blackmail hacking. Presenting Business And Threats Landscape In Business Cybersecurity Ppt Icon Example Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Phishing, Malware, Blackmail Hacking. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Client Acquisition Strategic Plan Activities In Marketing Microsoft Pdf
This slide presents B2B lead generation activities used by brands in marketing that helps them to generate business opportunities further utilized by sales team to convert potential customers into buyers. It includes growth hacking, content marketing and account based marketing. Showcasing this set of slides titled Client Acquisition Strategic Plan Activities In Marketing Microsoft Pdf. The topics addressed in these templates are Growth Hacking, Account Based Marketing, Content Marketing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Table Of Contents For IT Security Hacker Slide Introduction PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For IT Security Hacker Slide Introduction PDF bundle. Topics like Prevent Hacking, Strategies On Business, Implementation Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Cyber Exploitation IT Pictures PDF
Deliver an awe inspiring pitch with this creative table of contents for cyber exploitation it pictures pdf bundle. Topics like budget, implementation plan, strategies to prevent hacking, impact of new strategies on business, current situation of the business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
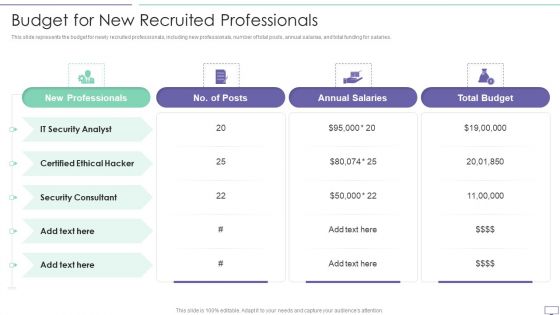
IT Security Hacker Budget For New Recruited Professionals Infographics PDF
This slide represents the budget for newly recruited professionals, including new professionals, number of total posts, annual salaries, and total funding for salaries.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Budget For New Recruited Professionals Infographics PDF. Use them to share invaluable insights on New Professionals, Certified Ethical, Annual Salaries and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

AI And ML Driving Monetary Value For Organization Required Manpower Skills Set Visualization Rules PDF
Following slide shows details about required manpower skills set. Skills set covered are domain knowledge, machine learning, data visualization and hacking. Deliver an awe inspiring pitch with this creative ai and ml driving monetary value for organization required manpower skills set visualization rules pdf bundle. Topics like domain knowledge, machine learning, machine learning, data visualization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For IT Security Hacker Background PDF
This is a Table Of Contents For IT Security Hacker Background PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Current Situation, Impact Of Hacking, Repairing Damages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Internet Security Threat Analysis With Attacks Target And Purpose Ppt PowerPoint Presentation Pictures Structure PDF
Presenting internet security threat analysis with attacks target and purpose ppt powerpoint presentation pictures structure pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including social and phishing, passwords and configs, smart and mobile hacking. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
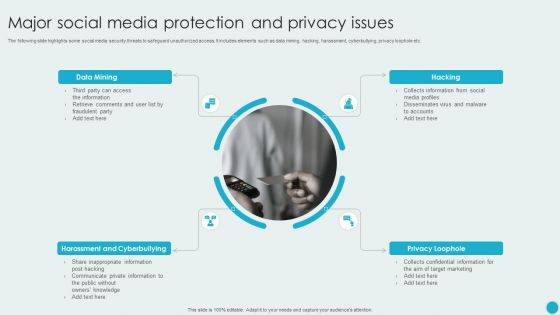
Major Social Media Protection And Privacy Issues Template PDF
The following slide highlights some social media security threats to safeguard unauthorized access. It includes elements such as data mining, hacking, harassment, cyberbullying, privacy loophole etc. Presenting Major Social Media Protection And Privacy Issues Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Mining, Harassment And Cyberbullying, Privacy Loophole. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
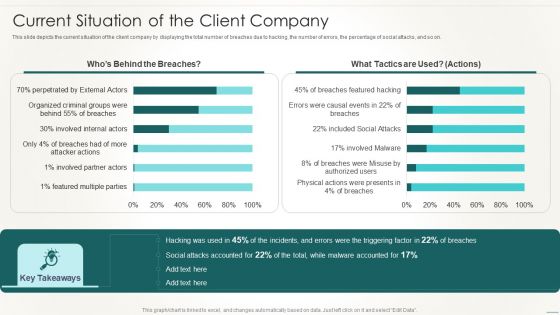
Information Technology Disaster Resilience Plan Current Situation Of The Client Company Designs PDF
This slide depicts the current situation of the client company by displaying the total number of breaches due to hacking, the number of errors, the percentage of social attacks, and so on.Deliver an awe inspiring pitch with this creative Information Technology Disaster Resilience Plan Current Situation Of The Client Company Designs PDF bundle. Topics like Disaster Recovery, Facilities Management, Collaboration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
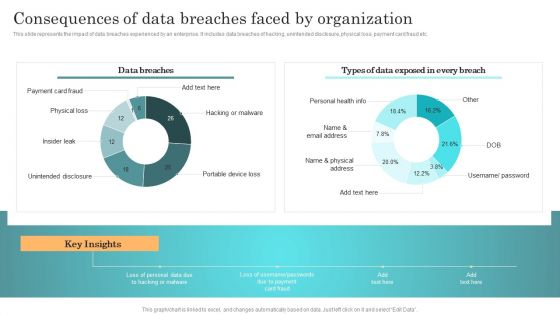
Incident Response Techniques Deployement Consequences Of Data Breaches Faced By Organization Structure PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. There are so many reasons you need a Incident Response Techniques Deployement Consequences Of Data Breaches Faced By Organization Structure PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
AI And ML Driving Monetary Value For Organization Required Manpower Skills Set Data Icons PDF
Following slide shows details about required manpower skills set. Skills set covered are domain knowledge, machine learning, data visualization and hacking. Deliver and pitch your topic in the best possible manner with this ai and ml driving monetary value for organization required manpower skills set data icons pdf. Use them to share invaluable insights on data engineer, data scientist, devops engineer, data visualization, machine learning and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
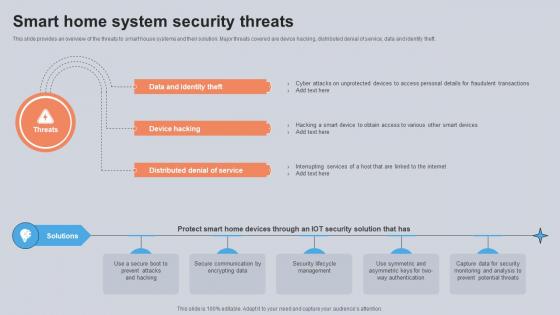
Smart Home System Security Threats Utilizing Smart Appliances IoT SS V
This slide provides an overview of the threats to smart house systems and their solution. Major threats covered are device hacking, distributed denial of service, data and identity theft. Take your projects to the next level with our ultimate collection of Smart Home System Security Threats Utilizing Smart Appliances IoT SS V. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Data Security And Privacy Audit Questionnaire Overview Report Survey SS
Following slides demonstrates data security evaluation summary report which can be used by business to reduce data hacking. It includes elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Pitch your topic with ease and precision using this Data Security And Privacy Audit Questionnaire Overview Report Survey SS. This layout presents information on Data Security Tools, Budget Allocated, Tools Performance, Data Security Tools Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Online Security Threat And Risk Assessment Matrix Formats PDF
This slide showcases digital safety risk assessment matrix which helps analyze impact of threat on business processes. It provides information regarding hacking, data breaches, information misuse, malicious attacks and system failure. Showcasing this set of slides titled Online Security Threat And Risk Assessment Matrix Formats PDF. The topics addressed in these templates are Information Misuse, Data Breaches, Malicious Attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
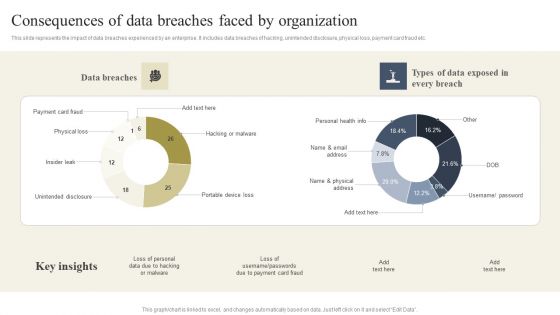
Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Boost your pitch with our creative Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
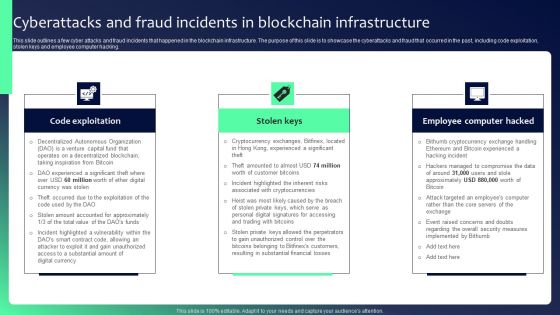
Blockchain Security Solutions Deployment Cyberattacks And Fraud Incidents In Blockchain Clipart PDF
This slide outlines a few cyber attacks and fraud incidents that happened in the blockchain infrastructure. The purpose of this slide is to showcase the cyberattacks and fraud that occurred in the past, including code exploitation, stolen keys and employee computer hacking. There are so many reasons you need a Blockchain Security Solutions Deployment Cyberattacks And Fraud Incidents In Blockchain Clipart PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Process Flow Of Botnet Malware Attack Icons PDF
This slide illustrates flowchart of attack through botnet malware hacking. It includes transmitting specific string to C and C, C and C authorizes bot connection, etc. Persuade your audience using this Process Flow Of Botnet Malware Attack Icons PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Malware In Victim, Hacker Launches, Malware Reads. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Managing Portfolio Growth Options Step 1 Define Your Market Ppt Outline Show PDF
Presenting this set of slides with name managing portfolio growth options step 1 define your market ppt outline show pdf. This is an editable Powerpoint two stages graphic that deals with topics like protection of data, protection from hacking, protection from all virus and malware, protection from anti virus, protection from identity theft, blocking objectionable content to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
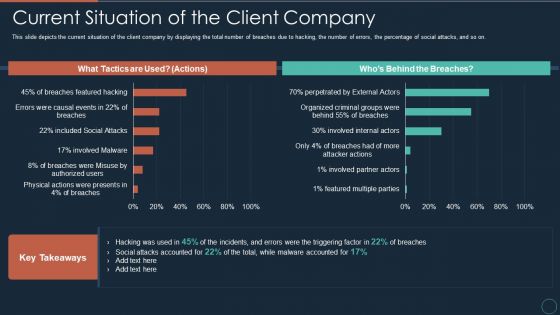
Implementing DRP IT Current Situation Of The Client Company Ppt PowerPoint Presentation Inspiration Deck PDF
This slide depicts the current situation of the client company by displaying the total number of breaches due to hacking, the number of errors, the percentage of social attacks, and so on.Deliver and pitch your topic in the best possible manner with this implementing drp it current situation of the client company ppt powerpoint presentation inspiration deck pdf Use them to share invaluable insights on featured multiple parties, involved partner actors, organized criminal groups and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Current Situation Of The Client Company Catastrophe Recovery Application Plan Guidelines PDF
This slide depicts the current situation of the client company by displaying the total number of breaches due to hacking, the number of errors, the percentage of social attacks, and so on. Deliver and pitch your topic in the best possible manner with this current situation of the client company catastrophe recovery application plan guidelines pdf. Use them to share invaluable insights on current situation of the client company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

 Home
Home