Data Security
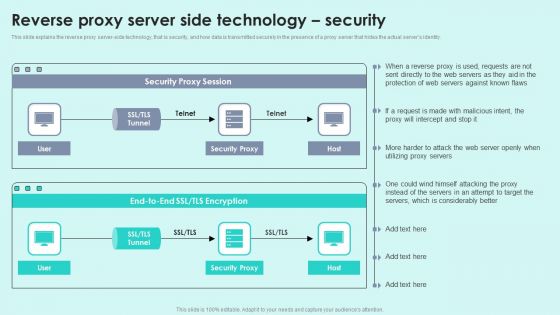
Reverse Proxy Server Side Technology Security Reverse Proxy For Load Balancing Portrait PDF
This slide explains the reverse proxy server-side technology, that is security, and how data is transmitted securely in the presence of a proxy server that hides the actual servers identity.Deliver and pitch your topic in the best possible manner with this Reverse Proxy Server Side Technology Security Reverse Proxy For Load Balancing Portrait PDF. Use them to share invaluable insights on Security Proxy, Protection Servers, Considerably Better and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Enhancing Cyber Safety With Vulnerability Administration Security Information And Event Formats PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative enhancing cyber safety with vulnerability administration security information and event formats pdf bundle. Topics like security events, event categories, data source, multiple events can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
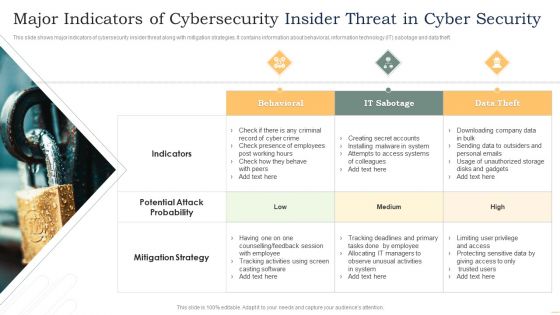
Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF
This slide shows major indicators of cybersecurity insider threat along with mitigation strategies. It contains information about behavioral, information technology IT sabotage and data theft. Presenting Major Indicators Of Cybersecurity Insider Threat In Cyber Security Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Behavioral, IT Sabotage, Data Theft. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information And Technology Security Operations Prerequisites For Effective Secops Implementation Designs PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a information and technology security operations prerequisites for effective secops implementation designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, data available, security with compliance, operations team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Process Integration Prerequisites For Effective Secops Implementation Microsoft PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a security and process integration prerequisites for effective secops implementation microsoft pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, data available, security with compliance, operations team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Stock Photo Ball With Big Data Text For Data Protection Concept PowerPoint Slide
Graphic of ball with big data text has been used to craft this power point template. This image template contains the concept of data protection. Use this image for data security related topics in any presentation.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Ways Through Which Security Clipart PDF
This slide provides information about some of the major ways through which security data can be compromised which could have a negative impact on security monitoring along with some measures to deal with them. Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks ways through which security clipart pdf bundle. Topics like attack description, ways to mitigate attack, external attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Enhancing Cyber Safety With Vulnerability Administration Security Information And Event Management Inspiration PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting enhancing cyber safety with vulnerability administration security information and event management inspiration pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like data retention, forensic analysis, dashboards, data correlation, data aggregation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
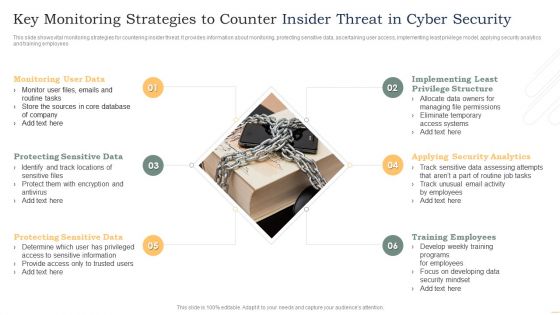
Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF
This slide shows vital monitoring strategies for countering insider threat. It provides information about monitoring, protecting sensitive data, ascertaining user access, implementing least privilege model, applying security analytics and training employees. Persuade your audience using this Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitoring User Data, Protecting Sensitive Data, Protecting Sensitive Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Information Security Phase 2 Secure Your Cloud Ppt Slides Guidelines PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Deliver an awe inspiring pitch with this creative Cloud Information Security Phase 2 Secure Your Cloud Ppt Slides Guidelines PDF bundle. Topics like Implement Information, Data Encryption, Implement Advanced can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
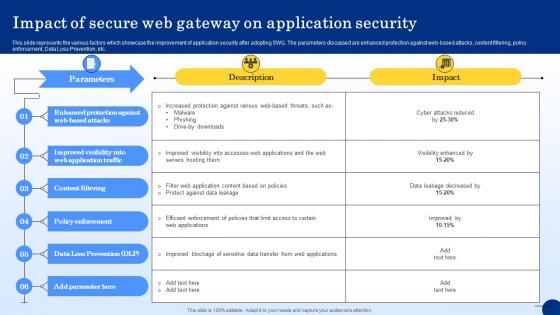
Impact Of Secure Web Gateway On Application Security Web Threat Protection System
This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Impact Of Secure Web Gateway On Application Security Web Threat Protection System template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Impact Of Secure Web Gateway On Application Security Web Threat Protection System that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
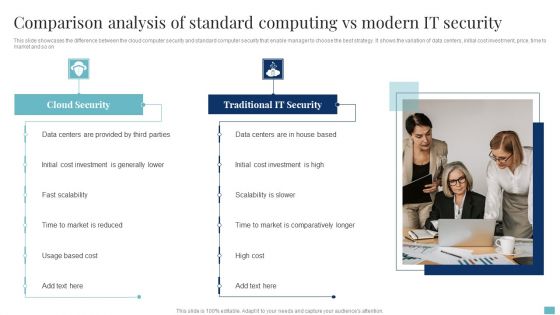
Comparison Analysis Of Standard Computing Vs Modern It Security Clipart PDF
This slide showcases the difference between the cloud computer security and standard computer security that enable manager to choose the best strategy. It shows the variation of data centers, initial cost investment, price, time to market and so on. Persuade your audience using this Comparison Analysis Of Standard Computing Vs Modern It Security Clipart PDF. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Data Centers, Cloud Security, Cost Investment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Essential Elements To Be Included In A Security Management Plan Elements PDF
This slide provides information about the essential elements or parts that must be included in security management plan by the company and IT security manager. Deliver an awe inspiring pitch with this creative essential elements to be included in a security management plan elements pdf bundle. Topics like risk, organization, security, systems, data communications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
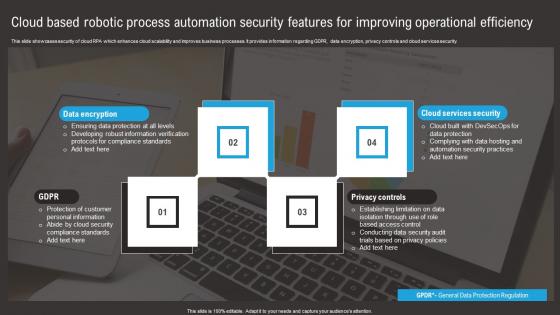
Cloud Based Robotic Process Automation Security Features For Improving Operational Efficiency Summary Pdf
This slide showcases security of cloud RPA which enhances cloud scalability and improves business processes. It provides information regarding GDPR, data encryption, privacy controls and cloud services security. Pitch your topic with ease and precision using this Cloud Based Robotic Process Automation Security Features For Improving Operational Efficiency Summary Pdf. This layout presents information on Data Encryption, Privacy Controls, Cloud Services Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Facilities Rendered By Security Centre Implementation Ppt Pictures Design Templates PDF
This slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Deliver an awe inspiring pitch with this creative facilities rendered by security centre implementation ppt pictures design templates pdf bundle. Topics like Determine, organization, Security, Systems, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
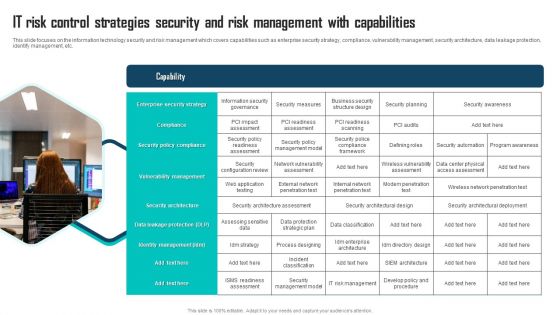
IT Risk Control Strategies Security And Risk Management With Capabilities Ppt Professional Graphics Example PDF
This slide focuses on the information technology security and risk management which covers capabilities such as enterprise security strategy, compliance, vulnerability management, security architecture, data leakage protection, identify management, etc. Presenting IT Risk Control Strategies Security And Risk Management With Capabilities Ppt Professional Graphics Example PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Enterprise Security Strategy, Compliance, Security Policy Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Web Access Control Solution Impact Of Secure Web Gateway On Application Security
This slide represents the various factors which showcase the improvement of application security after adopting SWG. The parameters discussed are enhanced protection against web-based attacks, content filtering, policy enforcement, Data Loss Prevention, etc. Welcome to our selection of the Web Access Control Solution Impact Of Secure Web Gateway On Application Security. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100Percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Building Trust With IoT Security IoT Device Updates And Maintenance Schedule IoT SS V
This slide exhibits device updates and maintenance task schedules that help to protect systems from vulnerabilities. It includes various tasks such as software updates, battery replacement, data backup, security audit, etc. Retrieve professionally designed Building Trust With IoT Security IoT Device Updates And Maintenance Schedule IoT SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Secure Access Service Edge Cloud Security Model Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.

Hardware And Software Update In Company IT Security IT Ppt Model Infographics PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Presenting hardware and software update in company it security it ppt model infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technology, security, data across. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

SDN Security Architecture Use Cases Of Software Defined Networking SDN Formats PDF
This slide represents the use cases of software defined networking, a developing technology that will eventually replace physical network designs with software controlled networking architecture. It shows its use in DevOps, campus networks, service provider networks, and data center security. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give SDN Security Architecture Use Cases Of Software Defined Networking SDN Formats PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable SDN Security Architecture Use Cases Of Software Defined Networking SDN Formats PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
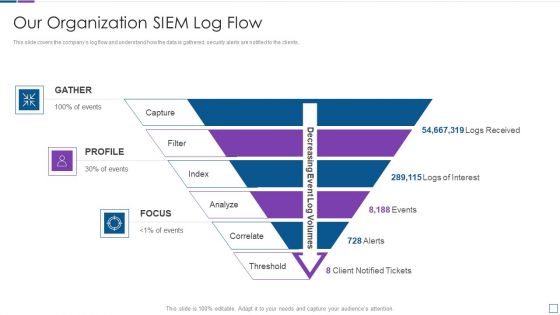
Real Time Assessment Of Security Threats Our Organization SIEM Log Flow Topics PDF
This slide covers the companys log flow and understand how the data is gathered, security alerts are notified to the clients. This is a real time assessment of security threats our organization siem log flow topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our organization siem log flow. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
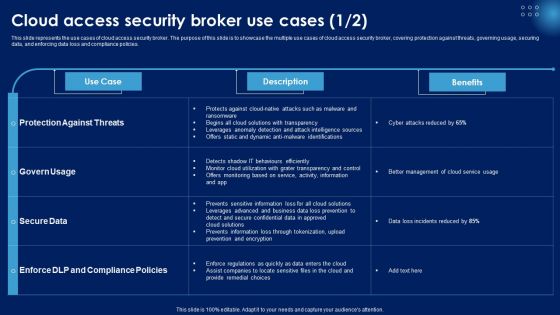
Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. This Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Effective Data Migration Challenges Faced In On Premises Data Storage
This slide showcases various pain points faced by business with on-premises data storage such as high costs, data security and limited accessibility. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Effective Data Migration Challenges Faced In On Premises Data Storage a try. Our experts have put a lot of knowledge and effort into creating this impeccable Effective Data Migration Challenges Faced In On Premises Data Storage. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Intelligent Architecture Growing Cyber Security Issues Ppt Professional Design Templates PDF
The slide provides the major cyber security issues Unprecedented Attacks, Cyber Espionage, and Data Theft along with the split of total information security incidents by the type of incident Deliver an awe inspiring pitch with this creative intelligent architecture growing cyber security issues ppt professional design templates pdf bundle. Topics like organizations, cyber security, business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway.
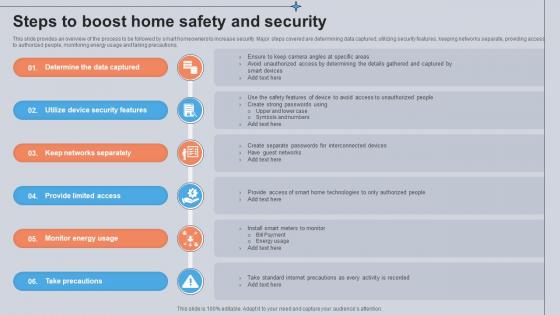
Steps To Boost Home Safety And Security Utilizing Smart Appliances IoT SS V
This slide provides an overview of the process to be followed by smart homeowners to increase security. Major steps covered are determining data captured, utilizing security features, keeping networks separate, providing access to authorized people, monitoring energy usage and taking precautions. Create an editable Steps To Boost Home Safety And Security Utilizing Smart Appliances IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Steps To Boost Home Safety And Security Utilizing Smart Appliances IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
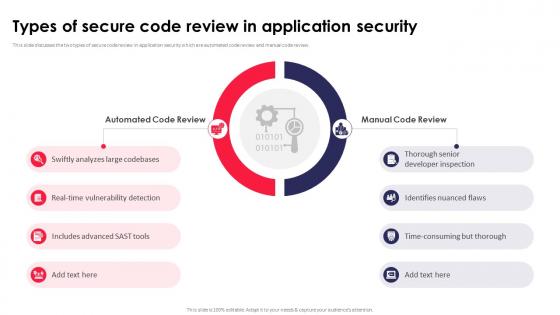
Types Of Secure Code Review In Application Security Testing Ppt Powerpoint Slides
This slide discusses the two types of secure code review in application security which are automated code review and manual code review. This Types Of Secure Code Review In Application Security Testing Ppt Powerpoint Slides from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Developing Business Analytics Framework Determine Role Of Security Centre In Firm Brochure PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver an awe inspiring pitch with this creative Developing Business Analytics Framework Determine Role Of Security Centre In Firm Brochure PDF bundle. Topics like Before Security, After Security, Towards Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
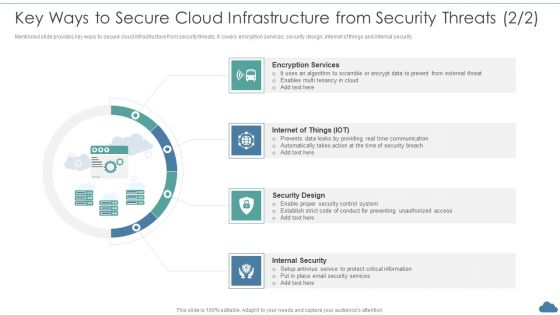
Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF
Mentioned slide provides key ways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Encryption Services, Security Design, Internal Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
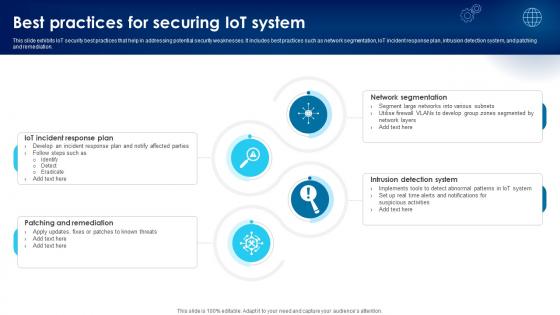
Building Trust With IoT Security Best Practices For Securing IoT System IoT SS V
This slide exhibits IoT security best practices that help in addressing potential security weaknesses. It includes best practices such as network segmentation, IoT incident response plan, intrusion detection system, and patching and remediation. Want to ace your presentation in front of a live audience Our Building Trust With IoT Security Best Practices For Securing IoT System IoT SS V can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Cloud Access Security Broker Use Cases Ppt Ideas Layout Ideas PDF
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Find highly impressive Cloud Access Security Broker Use Cases Ppt Ideas Layout Ideas PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Access Security Broker Use Cases Ppt Ideas Layout Ideas PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
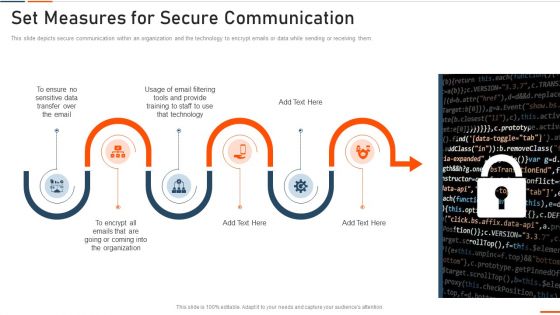
Information Technology Security Set Measures For Secure Communication Ppt Professional Portrait PDF
This is a information technology security set measures for secure communication ppt professional portrait pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sensitive data, transfer, technology, training, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
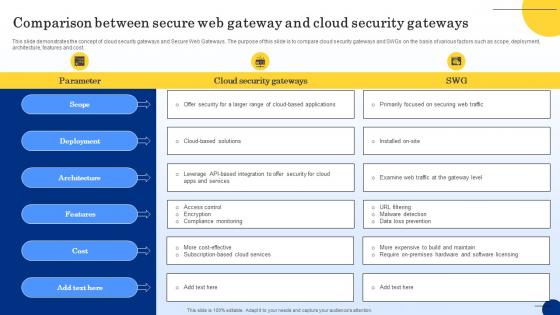
Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Comparison Between Secure Web Gateway And Cloud Security Gateways Web Threat Protection System will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
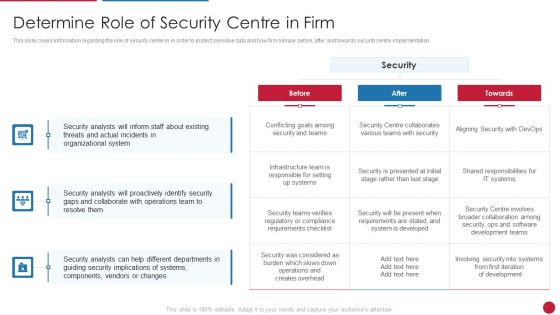
Facilitating IT Intelligence Architecture Determine Role Of Security Centre In Firm Demonstration PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Deliver an awe inspiring pitch with this creative Facilitating IT Intelligence Architecture Determine Role Of Security Centre In Firm Demonstration PDF bundle. Topics like Organizational System, Security Analysts, Collaborate With Operations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Evolving BI Infrastructure Determine Role Of Security Centre In Firm Summary PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Deliver an awe inspiring pitch with this creative evolving bi infrastructure determine role of security centre in firm summary pdf bundle. Topics like organizational, security analysts, collaborate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Intelligent Infrastructure Determine Role Of Security Centre In Firm Graphics PDF
This slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Deliver an awe inspiring pitch with this creative Intelligent Infrastructure Determine Role Of Security Centre In Firm Graphics PDF bundle. Topics like Security, Organizational System, Operations Team, Conflicting Goals can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V
The following slide highlights the security measures for IoT and digital wallet that ensure secure data transfer from one device to another. Key components are security credentials, device authentication, and consumer authentication. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Security In IoT Payment For Digital Wallet In Depth Guide To Digital Wallets Fin SS V that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
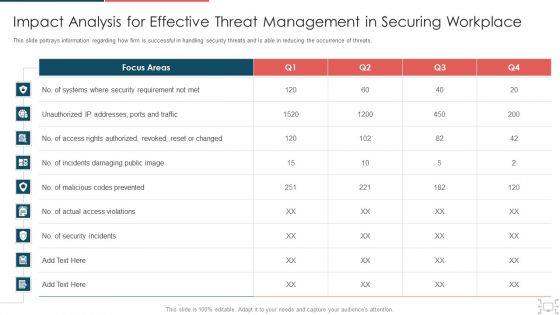
Cyber Security Administration In Organization Impact Analysis For Effective Threat Management Securing Rules PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Deliver an awe inspiring pitch with this creative cyber security administration in organization impact analysis for effective threat management securing rules pdf bundle. Topics like impact analysis for effective threat management in securing workplace can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
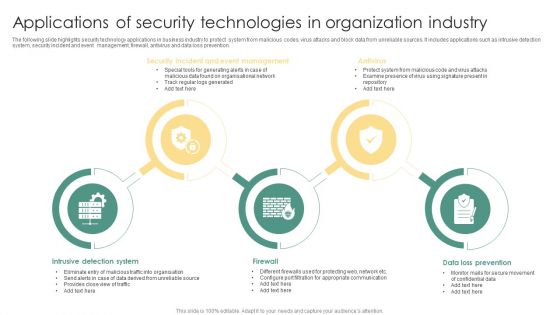
Applications Of Security Technologies In Organization Industry Ppt Summary Rules PDF
The following slide highlights security technology applications in business industry to protect system from malicious codes, virus attacks and block data from unreliable sources. It includes applications such as intrusive detection system, security incident and event management, firewall, antivirus and data loss prevention. Presenting Applications Of Security Technologies In Organization Industry Ppt Summary Rules PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Security Incident, Event Management, Antivirus, Firewall. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
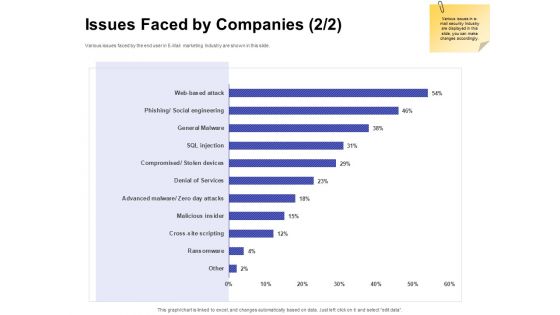
Global Cloud Based Email Security Market Issues Faced By Companies Services Portrait PDF
Presenting this set of slides with name global cloud based email security market issues faced by companies services portrait pdf. The topics discussed in these slides are security for confidential data, protection against malware, protection phishing scams, threat of weak password. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Email Security Market Research Report Issues Faced By Companies Professional PDF
Presenting this set of slides with name email security market research report issues faced by companies professional pdf. The topics discussed in these slides are security for confidential data, protection against malware, protection phishing scams, threat of weak password. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF today and make your presentation stand out from the rest.
Icons Slide For Secure Access Service Edge Cloud Security Model Ppt Gallery Layout PDF
Help your business to create an attention-grabbing presentation using our Icons Slide For Secure Access Service Edge Cloud Security Model Ppt Gallery Layout PDF set of slides. The slide contains innovative icons that can be flexibly edited. Choose this Icons Slide For Secure Access Service Edge Cloud Security Model Ppt Gallery Layout PDF template to create a satisfactory experience for your customers. Go ahead and click the download button.
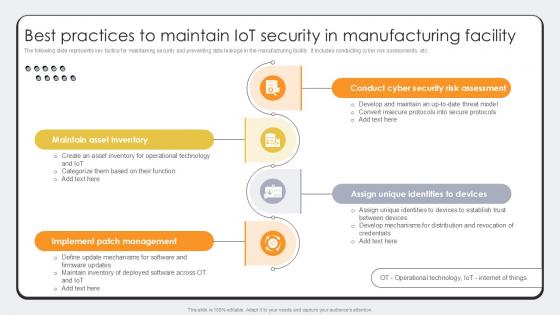
Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template
The following slide represents key tactics for maintaining security and preventing data leakage in the manufacturing facility. It includes conducting cyber risk assessments, etc. There are so many reasons you need a Best Practices To Maintain IoT Security Revolutionizing Production IoT Ppt Template. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
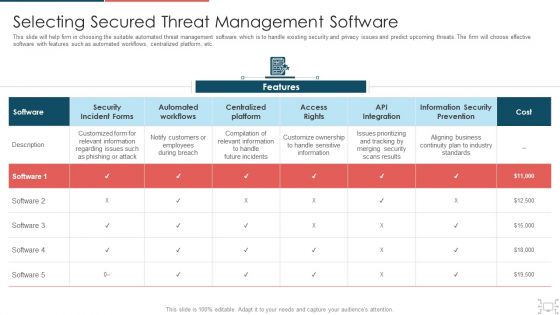
Cyber Security Administration In Organization Selecting Secured Threat Management Software Themes PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization selecting secured threat management software themes pdf. Use them to share invaluable insights on selecting secured threat management software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
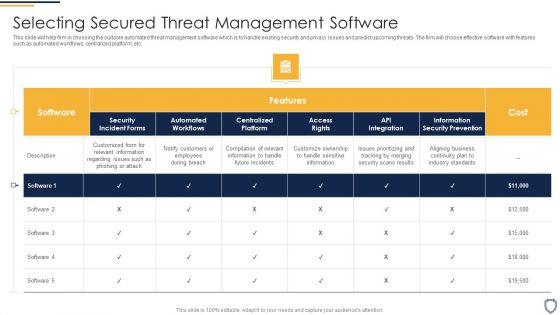
Corporate Security And Risk Management Selecting Secured Threat Management Software Introduction PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative corporate security and risk management selecting secured threat management software introduction pdf bundle. Topics like selecting secured threat management software can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
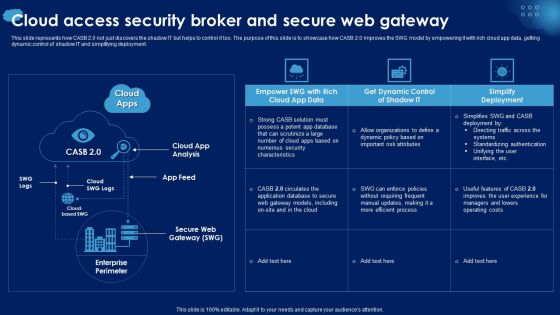
Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Secure Access Service Edge Cloud Security Model Table Of Contents Ppt Layouts Format Ideas PDF.

Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Agenda For Secure Access Service Edge Cloud Security Model Ppt Outline Maker PDF
Find a pre designed and impeccable Agenda For Secure Access Service Edge Cloud Security Model Ppt Outline Maker PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
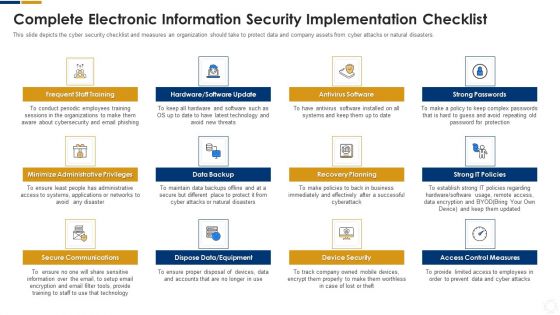
Cybersecurity Complete Electronic Information Security Implementation Checklist Ppt Inspiration Outline PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Presenting cybersecurity complete electronic information security implementation checklist ppt inspiration outline pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like technology, systems, equipment, secure communications, data backup. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Major Security Risks Associated With Digital Wallets In Depth Guide To Digital Wallets Fin SS V
This slide highlights the major risks associated with digital wallet adoption that lead to certain data and privacy issues. The different types of risks are inconsistent security, fraud risks, intercepted data, etc. Boost your pitch with our creative Major Security Risks Associated With Digital Wallets In Depth Guide To Digital Wallets Fin SS V. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
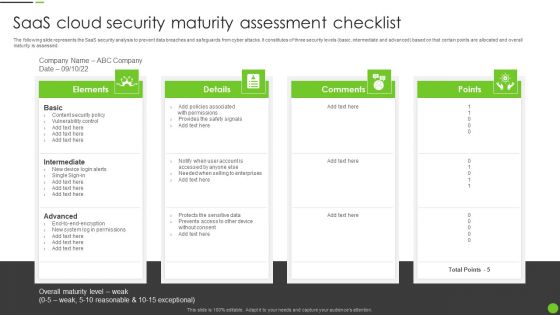
Saas Cloud Security Maturity Assessment Checklist Ppt PowerPoint Presentation File Portfolio PDF
The following slide represents the SaaS security analysis to prevent data breaches and safeguards from cyber attacks. It constitutes of three security levels basic, intermediate and advanced based on that certain points are allocated and overall maturity is assessed. Persuade your audience using this Saas Cloud Security Maturity Assessment Checklist Ppt PowerPoint Presentation File Portfolio PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Intermediate, Advanced, Content Security Policy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
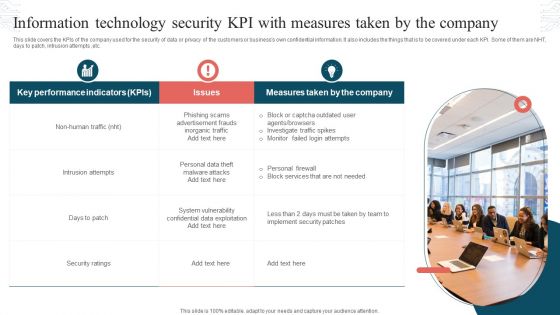
Information Technology Security KPI With Measures Taken By The Company Formats PDF
This slide covers the KPIs of the company used for the security of data or privacy of the customers or businesss own confidential information. It also includes the things that is to be covered under each KPI. Some of them are NHT, days to patch, intrusion attempts ,etc. Presenting Information Technology Security KPI With Measures Taken By The Company Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Key Performance Indicators, Measures Taken, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
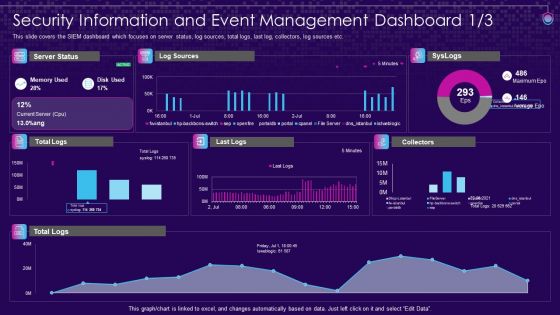
SIEM Services Security Information And Event Management Ppt File Objects PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative siem services security information and event management ppt file objects pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
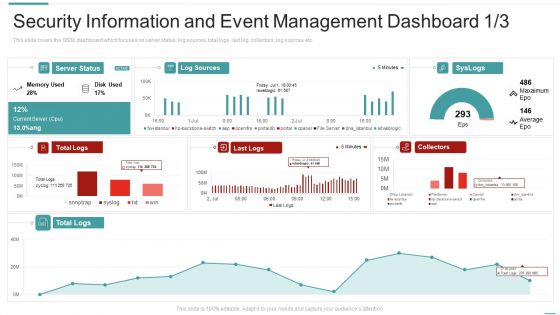
Risk Recognition Automation Security Information And Event Management Dashboard Ppt Model Elements PDF
This slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an awe inspiring pitch with this creative risk recognition automation security information and event management dashboard ppt model elements pdf bundle. Topics like security information and event management dashboard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

The Ultimate Guide To KPMG Overview Of Key KPMG Cyber Security Considerations Strategy SS V
This slide covers introduction of key cyber considerations for KPMG. The purpose for this template is to provide an overview on important aspects of deploying cyber security strategies to protect clients data and maintain their trust in operations of the company. It includes considerations such as maintaining digital trust, unobtrusive security drives secure behaviours, securing perimeter less and data centric future, etc. with description and insights Find a pre-designed and impeccable The Ultimate Guide To KPMG Overview Of Key KPMG Cyber Security Considerations Strategy SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Table Of Contents For Cloud Computing Security IT Monitoring Ppt Styles Introduction PDF
Presenting table of contents for cloud computing security it monitoring ppt styles introduction pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cloud security, business, implement, roadmap, data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home