Data Security

Data Security Is Must PowerPoint Templates Ppt Backgrounds For Slides 0913
Your ideas will do the trick. Wave the wand with our Data Security Is Must PowerPoint Templates PPT Backgrounds For Slides. Our Holidays PowerPoint Templates team are a dogged lot. They keep at it till they get it right. Dole it out with our AmericanaPowerPoint Templates. Your thoughts will get the right proportions.
Icons Slide For Risk Management Model For Data Security Elements PDF
Introducing our well designed Icons Slide For Risk Management Model For Data Security Elements PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Risk Management Model For Data Security Impact Assessment Matrix Formats PDF
Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Impact Assessment Matrix Formats PDF bundle. Topics like Financial, Reputation, Regulatory, Operational can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample
This slide talks about the Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different features of AES algorithm. These features are SP network, key expansion, byte data and key length. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample a try. Our experts have put a lot of knowledge and effort into creating this impeccable Standard For Advanced Encryption Data Security In Cloud Computing Ppt Sample. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Put Right Gears For Data Security PowerPoint Templates Ppt Backgrounds For Slides 0713
Double your chances with our Put Right Gears For Data Security PowerPoint Templates PPT Backgrounds For Slides 0713. The value of your thoughts will increase two-fold. Charm the audience with your thoughts. Add our Technology PowerPoint Templates and they will be dotty for you. Double up our Gear wheels PowerPoint Templates with your thoughts. They will make an awesome pair.

Risks Types Of Outsourcing Fraud Financial And Data Security Ppt PowerPoint Presentation File Example
Presenting this set of slides with name risks types of outsourcing fraud financial and data security ppt powerpoint presentation file example. This is a four stage process. The stages in this process are business process outsourcing, circular infographics, threats. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Your Investment For Company Online Database Proposal Infographics PDF
Presenting this set of slides with name best data security software your investment for company online database proposal infographics pdf. The topics discussed in these slides are project kickoff, planning, development and implementation, maintain and train. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Data Security Industry Report Global Cybersecurity Industry A Quick Snapshot IR SS V
This slide provides a glimpse of key highlights of the cybersecurity industry, enabling executives to grasp the main findings quickly. It serves as a snapshot highlighting revenue, CAGR, fastest growing region, segments, regional breakdown, and key market players. If you are looking for a format to display your unique thoughts, then the professionally designed Global Data Security Industry Report Global Cybersecurity Industry A Quick Snapshot IR SS V is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Global Data Security Industry Report Global Cybersecurity Industry A Quick Snapshot IR SS V and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
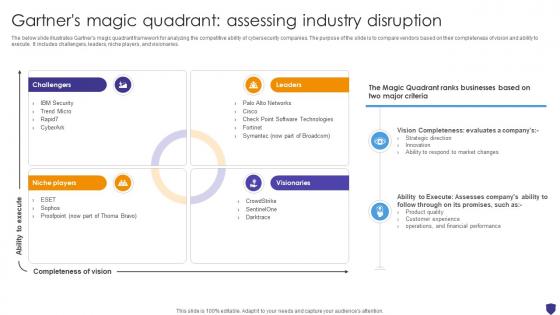
Global Data Security Industry Report Gartners Magic Quadrant Assessing Industry Disruption IR SS V
The below slide illustrates Gartners magic quadrant framework for analyzing the competitive ability of cybersecurity companies. The purpose of the slide is to compare vendors based on their completeness of vision and ability to execute. It includes challengers, leaders, niche players, and visionaries. Find highly impressive Global Data Security Industry Report Gartners Magic Quadrant Assessing Industry Disruption IR SS V on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Global Data Security Industry Report Gartners Magic Quadrant Assessing Industry Disruption IR SS V for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
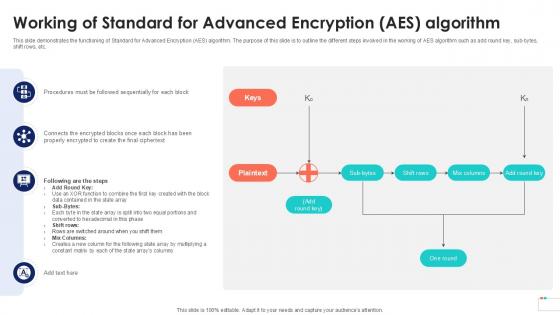
Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation
This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub-bytes, shift rows, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Working Of Standard For Advanced Encryption Data Security In Cloud Computing Ppt Presentation that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
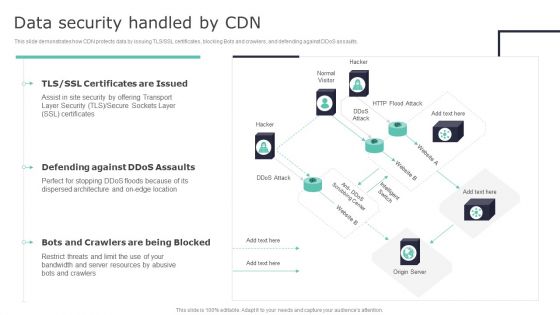
Deploying Content Distribution Network System Data Security Handled By CDN Sample PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Deploying Content Distribution Network System Data Security Handled By CDN Sample PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

About Cloud Computing Overview And Services Data Security In Cloud Computing Ppt Template
This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc. Create an editable About Cloud Computing Overview And Services Data Security In Cloud Computing Ppt Template that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. About Cloud Computing Overview And Services Data Security In Cloud Computing Ppt Template is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Key Benefits Of Cloud Computing Data Security In Cloud Computing Ppt Example
This slide demonstrates the various advantages of cloud computing. The purpose of this slide is to explain the importance of cloud computing services. The benefits are scalability, flexibility, cost savings, disaster recovery, etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Key Benefits Of Cloud Computing Data Security In Cloud Computing Ppt Example to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Key Benefits Of Cloud Computing Data Security In Cloud Computing Ppt Example.
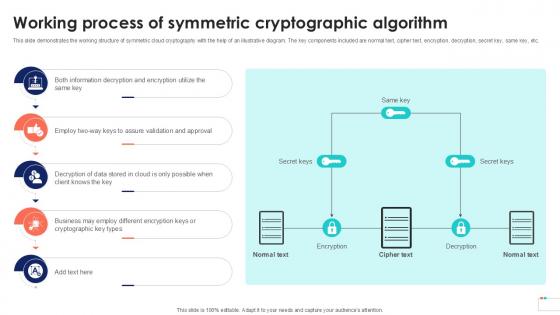
Working Process Of Symmetric Data Security In Cloud Computing Ppt Template
This slide demonstrates the working structure of symmetric cloud cryptography with the help of an illustrative diagram. The key components included are normal text, cipher text, encryption, decryption, secret key, same key, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Working Process Of Symmetric Data Security In Cloud Computing Ppt Template was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Working Process Of Symmetric Data Security In Cloud Computing Ppt Template
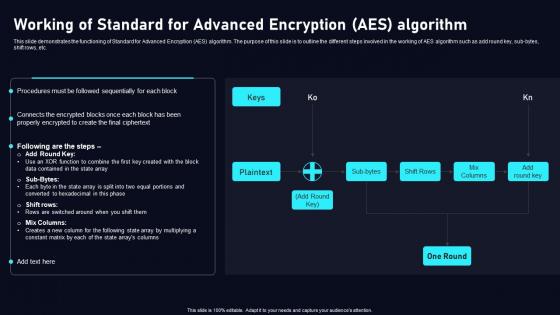
Working Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf
This slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub bytes, shift rows, etc. Create an editableWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save timeWorking Of Standard For Advanced Cloud Data Security Using Cryptography Diagrams Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
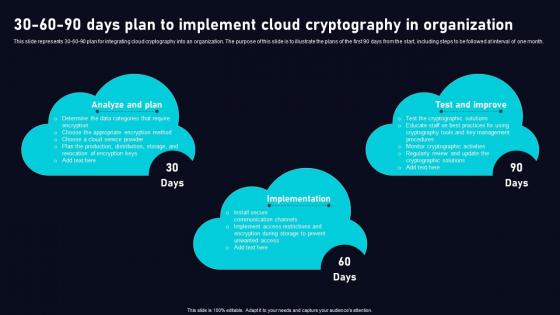
30 60 90 Days Plan To Implement Cloud Data Security Using Cryptography Slides Pdf
This slide represents 30 60 90 plan for integrating cloud cryptography into an organization. The purpose of this slide is to illustrate the plans of the first 90 days from the start, including steps to be followed at interval of one month. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give 30 60 90 Days Plan To Implement Cloud Data Security Using Cryptography Slides Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable 30 60 90 Days Plan To Implement Cloud Data Security Using Cryptography Slides Pdf You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
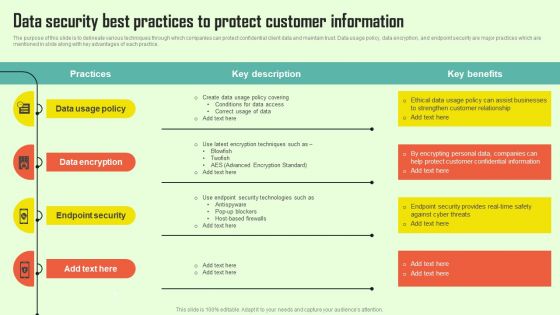
Increasing Consumer Engagement With Database Data Security Best Practices To Protect Microsoft PDF
The purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Create an editable Increasing Consumer Engagement With Database Data Security Best Practices To Protect Microsoft PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Increasing Consumer Engagement With Database Data Security Best Practices To Protect Microsoft PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
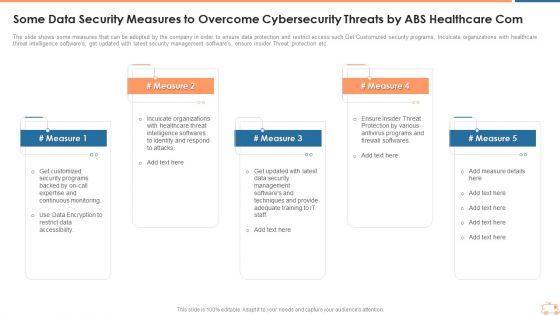
Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Template PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com template pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
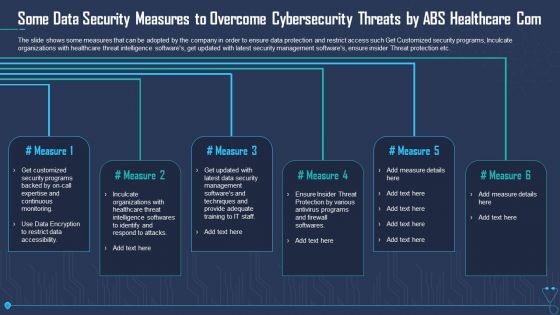
Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Com Sample PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. Presenting some data security measures to overcome cybersecurity threats by abs healthcare com sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like some data security measures to overcome cybersecurity threats by abs healthcare com. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
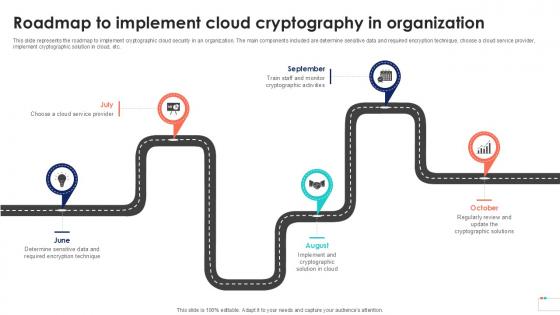
Roadmap To Implement Cloud Data Security In Cloud Computing Ppt Slide
This slide represents the roadmap to implement cryptographic cloud security in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement cryptographic solution in cloud, etc. There are so many reasons you need a Roadmap To Implement Cloud Data Security In Cloud Computing Ppt Slide. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Content Delivery Network Edge Server Data Security Handled By CDN Diagrams PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Deliver and pitch your topic in the best possible manner with this Content Delivery Network Edge Server Data Security Handled By CDN Diagrams PDF. Use them to share invaluable insights on Security, Location, Server Resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Key Uses And Applications Cryptographic Cloud Data Security Using Cryptography Sample Pdf
This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc. Want to ace your presentation in front of a live audience Our Key Uses And Applications Cryptographic Cloud Data Security Using Cryptography Sample Pdf can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

What Are Benefits Of Using Data Security In Cloud Computing Ppt Template
This slide talks about the advantages of cloud data encryption. The purpose of this slide is to outline the benefits of cloud cryptography. These key benefits include data protection, data privacy, trust, users, integrity, availability, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit What Are Benefits Of Using Data Security In Cloud Computing Ppt Template and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF
This is a IT Threats Response Playbook Checklist For Work From Home Data Security Inspiration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Policies, Incident Reporting, Remote Workstations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Management Model For Data Security Table Of Contents Brochure PDF
This is a Risk Management Model For Data Security Table Of Contents Brochure PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Managing Risks, Defining Risk Level, Setting Scenario, Security Control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
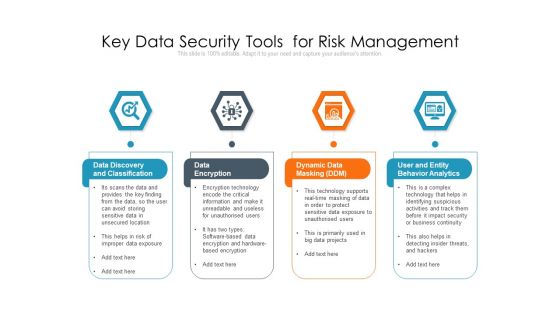
Key Data Security Tools For Risk Management Ppt PowerPoint Presentation Outline Guide PDF
Persuade your audience using this key data security tools for risk management ppt powerpoint presentation outline guide pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including data discovery and classification, data encryption, dynamic data masking ddm, user and entity behavior analytics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
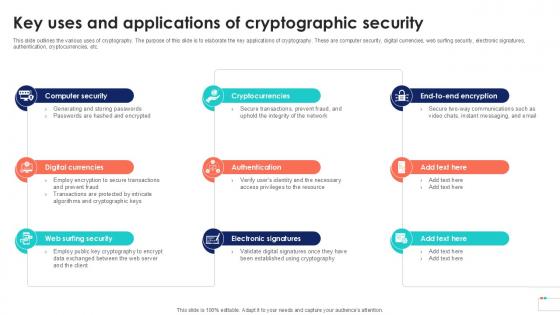
Key Uses And Applications Of Data Security In Cloud Computing Ppt Slide
This slide outlines the various uses of cryptography. The purpose of this slide is to elaborate the key applications of cryptography. These are computer security, digital currencies, web surfing security, electronic signatures, authentication, cryptocurrencies, etc. Take your projects to the next level with our ultimate collection of Key Uses And Applications Of Data Security In Cloud Computing Ppt Slide. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Ethical And Data Security Considerations For Digital Innovation DT SS V
This slide presents important ethical and legal considerations in the digital landscape. It mentions description, laws necessary for maintaining regulations including data privacy, cybersecurity and intellectual property.Find a pre-designed and impeccable Ethical And Data Security Considerations For Digital Innovation DT SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
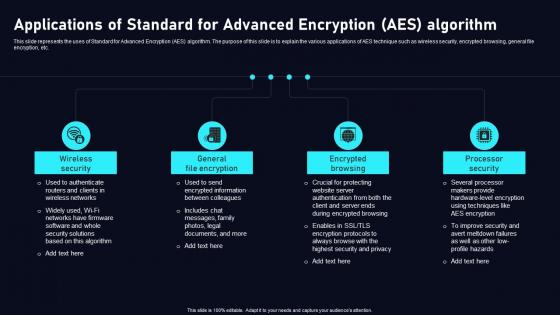
Applications Of Standard Advanced Cloud Data Security Using Cryptography Topics Pdf
This slide represents the uses of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to explain the various applications of AES technique such as wireless security, encrypted browsing, general file encryption, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Applications Of Standard Advanced Cloud Data Security Using Cryptography Topics Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Methods Used By Symmetric Algorithm Cloud Data Security Using Cryptography Topics Pdf
This slide talks about the various applications of symmetric algorithm in cloud cryptography. The purpose of this slide is to explain how this technique can help in providing security in cloud computing. These are encryption, access control, key management, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Methods Used By Symmetric Algorithm Cloud Data Security Using Cryptography Topics Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample
This slide compares the two important cloud cryptographic techniques, known as symmetric and asymmetric encryption. The purpose of this slide is to distinguish between these two cryptography methods on the basis of various factors such as size of cipher, key length, data size, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Comparative Analysis Of Symmetric Data Security In Cloud Computing Ppt Sample. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Types Of Attacks Prevented By Cloud Data Security Using Cryptography Guidelines Pdf
This purpose of this slide is to explain how cloud cryptography can help prevent several types of attacks that can compromise the confidentiality, integrity, and availability of data in cloud environments. These include Man in the middle MitM attacks, data breaches, insider attacks, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Types Of Attacks Prevented By Cloud Data Security Using Cryptography Guidelines Pdf. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
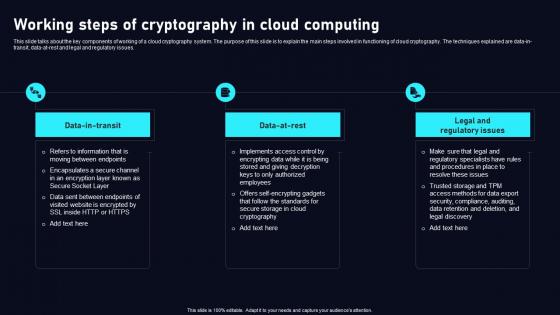
Working Steps Of Cryptography In Cloud Data Security Using Cryptography Infographics Pdf
This slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data in transit, data at rest and legal and regulatory issues. There are so many reasons you need aWorking Steps Of Cryptography In Cloud Data Security Using Cryptography Infographics Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Cloud Content Delivery Network Data Security Handled By CDN Guidelines PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Content Delivery Network Data Security Handled By CDN Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Content Delivery Network Data Security Handled By CDN Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Welcome to our selection of the Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 parcent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
Data Security Financial Services Ppt PowerPoint Presentation Styles Design Templates Cpb Pdf
Presenting this set of slides with name data security financial services ppt powerpoint presentation styles design templates cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like data metrics inside application to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

About Cryptography Overview And Key Data Security In Cloud Computing Ppt Example
This slide talks about the concept of cryptography to secure the information sent to the recipient. The purpose of this slide is to represent the various principles of cryptography such as confidentiality, integrity, authentication, etc. Want to ace your presentation in front of a live audience Our About Cryptography Overview And Key Data Security In Cloud Computing Ppt Example can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Table Of Contents Global Data Security Industry Report IR SS V
Slidegeeks has constructed Table Of Contents Global Data Security Industry Report IR SS V after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Cloud Data Security Using Cryptography Ppt Powerpoint Presentation Complete Deck With Slides
This incisive,comprehensive Cloud Data Security Using Cryptography Ppt Powerpoint Presentation Complete Deck With Slides details important features of running a business. One learns about things like result areas,planning and strategic framework just a glance of this comprehensive deck of eighty five slides. Use this PPT template to present your unique perspective of business technicalities and experience the way a good presentation can give new meaning to similarly placed facts. Use this template to leave a roomful of people wondering at the expert you have gathered in closing a business deal. The completely editable and customisable nature of the presentation is a unique bonus. Download now.

About Symmetric Algorithm Overview Data Security In Cloud Computing Ppt Template
This slide represents the symmetric algorithm for cloud cryptography. The purpose of this slide is to discuss about the advantages of symmetric algorithm. These include remarkably secure, speed, acceptance, requires low computer resources, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. About Symmetric Algorithm Overview Data Security In Cloud Computing Ppt Template will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Table Of Contents For Risk Management Model For Data Security Diagrams PDF
This is a Table Of Contents For Risk Management Model For Data Security Diagrams PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Present Scenario, Incident Management, Managing Risks, Dashboards, Training And Budget. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Global Data Security Industry Report Geographical Analysis For Cybersecurity Industry IR SS V
The slide highlights the geographical summary of current state of cybersecurity industry. The purpose of the slide is to provide insights on cybersecurity landscape, trends, development at regional levels. It helps stakeholders in understanding the market dynamics, regulatory environments and potential growth opportunities. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Global Data Security Industry Report Geographical Analysis For Cybersecurity Industry IR SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Risk Management Model For Data Security Multitiered Risk Management Framework Diagram Ideas PDF
This is a Risk Management Model For Data Security Multitiered Risk Management Framework Diagram Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strategic Risk, Mission, Business Processes, Information Systems, Organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Management Model For Data Security System Disposal Checklist Slides PDF
Mentioned slide shows system disposal checklist. It covers information such as system requirement, its compliance and remarks. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security System Disposal Checklist Slides PDF. Use them to share invaluable insights on Requirement, Compliance, All Information, Stored Information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
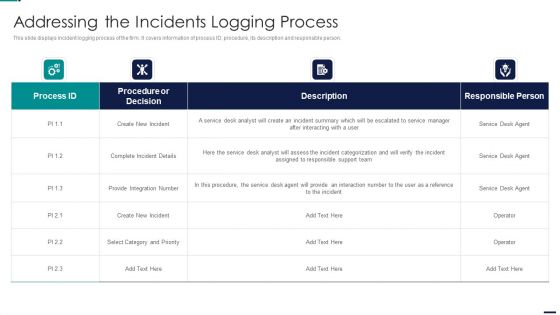
Risk Management Model For Data Security Addressing The Incidents Logging Process Professional PDF
This slide displays incident logging process of the firm. It covers information of process ID, procedure, its description and responsible person. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Addressing The Incidents Logging Process Professional PDF bundle. Topics like Procedure or Decision, Create New Incident, Integration Number can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Defining Vulnerability Rating With Criteria Mockup PDF
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Defining Vulnerability Rating With Criteria Mockup PDF. Use them to share invaluable insights on Vulnerability Ranking, High, LOW, MEDIUM, Attack Organization, Occurrence Attack and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Management Model For Data Security Risk Reporting And Likelihood Infographics PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Risk Reporting And Likelihood Infographics PDF bundle. Topics like Risk Encountered, Frequency, Attack Scenario, Affected Asset can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Online And Onsite Training Schedule For Employee Rules PDF
This slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Online And Onsite Training Schedule For Employee Rules PDF bundle. Topics like Course Type, Training Mode, Training Duration, Employee can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Practices For Data Security Management Ppt PowerPoint Presentation File Background Designs PDF
Persuade your audience using this key practices for data security management ppt powerpoint presentation file background designs pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including management, deployment, implementation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Risk Management Model For Data Security Incident Management Tool We Will Use Diagrams PDF
Mentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Incident Management Tool We Will Use Diagrams PDFbundle. Topics like Cost, Employee, Mobile Support, Automated Workflow, User Access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
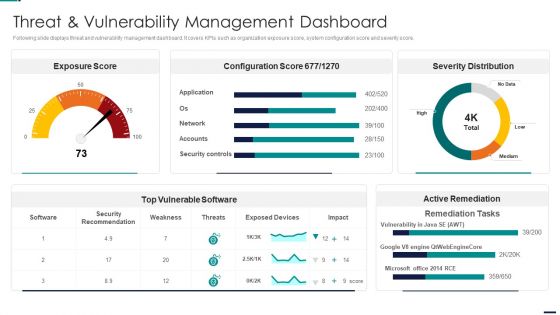
Risk Management Model For Data Security Threat And Vulnerability Management Dashboard Diagrams PDF
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Threat And Vulnerability Management Dashboard Diagrams PDF bundle. Topics like Exposure Score, Configuration Score, Severity Distribution, Top Vulnerable Software, Active Remediation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Impact Urgency Matrix For Incidents Risk Management Model For Data Security Pictures PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level. Deliver an awe inspiring pitch with this creative Impact Urgency Matrix For Incidents Risk Management Model For Data Security Pictures PDF bundle. Topics like Priority, Multiple Segments, Enterprise, Moderate Impact to Team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
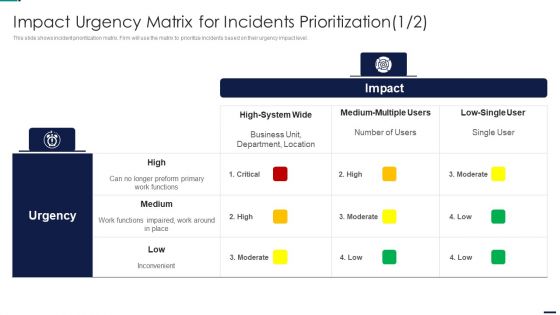
Risk Management Model For Data Security Impact Urgency Matrix For Incidents Prioritization Ideas PDF
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Impact Urgency Matrix For Incidents Prioritization Ideas PDF bundle. Topics like High System Wide, Medium Multiple Users, Low Single User, Inconvenient can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Global Data Security Industry Report Key Considerations Assumptions Of Cybersecurity Industry Report IR SS V
The slide represents key considerations and limitations while building the cybersecurity industry report. The purpose of this slide is to provide framework and context for analysis and projections in addition to acknowledging uncertainties and potential risks in the future. Make sure to capture your audiences attention in your business displays with our gratis customizable Global Data Security Industry Report Key Considerations Assumptions Of Cybersecurity Industry Report IR SS V. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Table Of Content For Data Security In Cloud Computing Ppt Slide
Present like a pro with Table Of Content For Data Security In Cloud Computing Ppt Slide. Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Padlock On Keyboard Data Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Padlock On Keyboard Data Security PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Computer PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune. Download our Technology PowerPoint Templates because Our PowerPoint Templates and Slides will help you be quick off the draw. Just enter your specific text and see your points hit home. Download our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides will Embellish your thoughts. They will help you illustrate the brilliance of your ideas. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let you Clearly mark the path for others to follow. Present our Success PowerPoint Templates because Our PowerPoint Templates and Slides has conjured up a web of all you need with the help of our great team. Use them to string together your glistening ideas.Use these PowerPoint slides for presentations relating to A padlock on keyboard, computer, technology, marketing, business, success. The prominent colors used in the PowerPoint template are Yellow, Blue navy, White. Professionals tell us our Padlock On Keyboard Data Security And Protection PowerPoint Templates PPT Backgrounds For Slides 0113 will save the presenter time. PowerPoint presentation experts tell us our marketing PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. You can be sure our Padlock On Keyboard Data Security And Protection PowerPoint Templates PPT Backgrounds For Slides 0113 will make the presenter look like a pro even if they are not computer savvy. PowerPoint presentation experts tell us our on PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. We assure you our Padlock On Keyboard Data Security And Protection PowerPoint Templates PPT Backgrounds For Slides 0113 will save the presenter time. PowerPoint presentation experts tell us our technology PowerPoint templates and PPT Slides look good visually.

Table Of Contents For Global Data Security Industry Report IR SS V
Retrieve professionally designed Table Of Contents For Global Data Security Industry Report IR SS V to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Table Of Contents For Data Security In Cloud Computing Ppt Slide
Slidegeeks is here to make your presentations a breeze with Table Of Contents For Data Security In Cloud Computing Ppt Slide With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
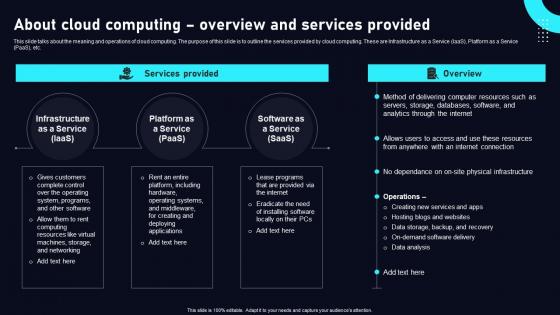
About Cloud Computing Overview Cloud Data Security Using Cryptography Pictures Pdf
This slide talks about the meaning and operations of cloud computing. The purpose of this slide is to outline the services provided by cloud computing. These are Infrastructure as a Service IaaS, Platform as a Service PaaS, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. About Cloud Computing Overview Cloud Data Security Using Cryptography Pictures Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
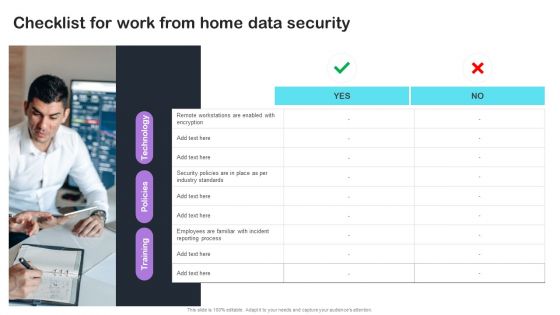
Cyber Risks And Incident Response Playbook Checklist For Work From Home Data Security Infographics PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Cyber Risks And Incident Response Playbook Checklist For Work From Home Data Security Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

 Home
Home